
Self-stabilizing TDMA Algorithms
for Dynamic Wireless Ad-hoc Networks
∗
Pierre Leone
1
and Elad M. Schiller
2
1
Computer Science Department, University of Geneva, Geneva Switzerland
2
Computer Science Department, Chalmers University of Technology, G
¨
oteborg, Sweden
Keywords:
Self-stabilization, Dynamic Networks, MANETs, VANETs, MAC.
Abstract:
In dynamic wireless ad-hoc networks (DynWANs), autonomous computing devices set up a network for the
communication needs of the moment. These networks require the implementation of a medium access control
(MAC) layer. We consider MAC protocols for DynWANs that need to be autonomous and robust as well as
have high bandwidth utilization, high predictability degree of bandwidth allocation, and low communication
delay in the presence of frequent topological changes to the communication network. Recent studies have
shown that existing implementations cannot guarantee the necessary satisfaction of these timing requirements.
We propose a self-stabilizing MAC algorithm for DynWANs that guarantees a short convergence period, and
by that, it can facilitate the satisfaction of severe timing requirements, such as the above. Besides the con-
tribution in the algorithmic front of research, we expect that our proposal can enable quicker adoption by
practitioners and faster deployment of DynWANs, such as the IEEE 802.11p for mobile ad hoc networks
(MANETs) and vehicular ad-hoc networks (VANETs).
1 INTRODUCTION
Dynamic wireless ad-hoc networks (DynWANs) are
autonomous and self-organizing systems where com-
puting devices require networking applications when
a fixed network infrastructure is not available or not
preferred to be used. In these cases, computing de-
vices may set up a short-lived network for the com-
munication needs of the moment, also known as, an
ad-hoc network. Ad-hoc networks are based on wire-
less communications that require implementation of a
Medium Access Control (MAC) layer. We consider
MAC protocols for DynWANs that need to be au-
tonomous, robust, and have high bandwidth utiliza-
tion, a high predictability degree of bandwidth al-
location, and low communication delay in the pres-
ence of frequent changes to the communication net-
work topology. Existing implementations cannot
guarantee the necessary satisfaction of timing require-
ments (Bilstrup et al., 2008; Bilstrup et al., 2009).
∗
This work was partially supported by the EC, through
project FP7-STREP-288195, KARYON (Kernel-based AR-
chitecture for safetY-critical cONtrol), see (Casimiro et al.,
2012). A technical report version of this work appears
in (Leone and Schiller, 2012a), and a brief announcement
version is in (Leone and Schiller, 2012b).
This work proposes an algorithmic design for self-
stabilizing MAC protocols that guarantees a short
convergence period, and by that, can facilitate the sat-
isfaction of severe timing requirements. The proposed
algorithm possesses a greater degree of predictabil-
ity, while maintaining low communication delays and
high throughput.
The dynamic and difficult-to-predict nature of
wireless ad-hoc networks gives rise to many fault-
tolerance issues and requires efficient solutions. Dyn-
WANs, for example, are subject to transient faults due
to hardware/software temporal malfunctions or short-
lived violations of the assumed settings for model-
ing the location of the mobile nodes. Fault tolerant
systems that are self-stabilizing (Dolev, 2000) can re-
cover after the occurrence of transient faults, which
can cause an arbitrary corruption of the system state
(so long as the program’s code is still intact), or the
model of dynamic networks in which communication
links and nodes may fail and recover during normal
operation (Dolev and Herman, 1997). The proof of
self-stabilization requires convergence from an arbi-
trary starting system state. Moreover, once the system
has converged and followed its specifications, it is re-
quired to do so forever. The self-stabilization design
criteria liberate the application designer from dealing
119
Leone P. and M. Schiller E..
Self-stabilizing TDMA Algorithms for Dynamic Wireless Ad-hoc Networks.
DOI: 10.5220/0004231401190124
In Proceedings of the 2nd International Conference on Sensor Networks (SENSORNETS-2013), pages 119-124
ISBN: 978-989-8565-45-7
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

with low-level complications, such as bandwidth allo-
cation in the presence of topology changes, and pro-
vide an important level of abstraction. Consequently,
the application design can easily focus on its task –
and knowledge-driven aspects.
MAC algorithms. ALOHAnet and its synchronized
version Slotted ALOHA (Abramson, 1985) are pio-
neering wireless systems that employ a strategy of
“random access”. Time division multiple access
(TDMA) (Schmidt, 1974) is another early approach,
where nodes transmit one after the other, each using
its own timeslot, say, according to a defined schedule.
The scheduled approach offers greater predictabil-
ity of bandwidth allocation and communication de-
lay, which can facilitate fairness (Herman and Tixeuil,
2004) and energy conservation (Ye et al., 2002).
There are two well-known approaches for deal-
ing with contention (timeslot exhaustion): (1) em-
ploying policies for administering message priority,
or (2) adjusting the nodes’ individual transmission
signal strength or carrier sense threshold (Yu and
Biswas, 2007; Scopigno and Cozzetti, 2009). The
former approach is widely accepted and adopted by
the IEEE 802.11p standard (see Section 4), whereas
the latter has only been evaluated via computer simu-
lations (Scopigno and Cozzetti, 2009).
STDMA (Yu and Biswas, 2007) and Viqar and
Welch (Viqar and Welch, 2009) consider scheduling
that is based on Global Navigation Satellite System
(GNSS).
Related Work. We propose a self-stabilizing TDMA
algorithm that does not require GNSS accessibility or
knowledge about the node trajectories. Rather it con-
siders an underlying self-stabilizing local pulse syn-
chronization, such as (Mustafa et al., 2012).
When using collision-detection at the receiving-
side (Scopigno and Cozzetti, 2009; Cozzetti and
Scopigno, 2009; Yu and Biswas, 2007; Tadokoro
et al., 2008; Lenoble et al., 2009), it is up to the
receiving-side to notify the sender about collisions
via another round of collision-prone transmissions,
and by using FI (frame information) payload fields
that includes T entries, where T is the TDMA frame
size. Thus far, FI-based protocols study the stochas-
tic resolution of message collision via computer net-
work simulations (Yu and Biswas, 2007; Abrate et al.,
2011; Scopigno and Cozzetti, 2010; Cozzetti et al.,
2009; Tadokoro et al., 2008; Lenoble et al., 2009).
Simulations are also used for evaluating the
heuristics of MS-ALOHA (Scopigno and Cozzetti,
2009) for dealing with contention (timeslot exhaus-
tion) by adjusting the nodes’ individual transmission
signal strength and / or carrier sense threshold.
We do not consider lengthy frame information (FI)
fields, which significantly increase the control infor-
mation overhead, and yet we provide provable guar-
antee regarding the convergence time. Further anal-
ysis validation of the proposed algorithm via simu-
lations and test bed implementation can be found in
Section 5, and respectively, in (Mustafa et al., 2012).
The proposed algorithm does not consider
collision-detection mechanisms that are based on sig-
nal processing or hardware support, as in (Demirbas
and Hussain, 2006). Rather, it employs a variation
on a well-known strategy for eventually avoiding con-
current transmissions among neighbors. This strategy
allows the sending-side to eventually observe the ex-
istence of interfering transmissions. Before sending,
the sender waits for a random duration while perform-
ing a clear channel assessment. A channel is consid-
ered to be used once the detected energy levels reach
a threshold in which the radio unit is expected to suc-
ceed in carrier sense locking (details appear in Sec-
tion 2 and (Leone and Schiller, 2012a)).
The proposed MAC algorithm can be entirely
based on the carrier sensing of message transmission,
as in (Cornejo and Kuhn, 2010), which focuses on fair
bandwidth allocation, but does not consider dynamic
networks or self-stabilization.
There are several proposals related to self-
stabilizing MAC algorithms (Kulkarni and Aru-
mugam, 2006; Arumugam and Kulkarni, 2005; Aru-
mugam and Kulkarni, 2006; Lagemann et al., 2009;
Herman and Tixeuil, 2004; Jhumka and Kulkarni,
2007); however, none of them consider dynamic net-
works and their frame control information is quite ex-
tensive. In (Leone et al., 2009a; Leone et al., 2010;
Mustafa et al., 2012; Leone et al., 2009b), we con-
sider a MAC algorithm that uses convergence from a
random starting state (inspired by self-stabilization),
were as here we consider self-stabilizing MAC algo-
rithms. An extended survey of the related work ap-
pears in (Leone and Schiller, 2012a).
Our Contribution. This work proposes a self-
stabilizing MAC algorithm that demonstrates rapid
convergence without the extensive use of frame con-
trol information (Section 2). Our analysis shows that
the algorithm facilitates the satisfaction of severe tim-
ing requirements for DynWANs (Section 3).
We start by considering transient faults and topo-
logical changes to the communication network, i.e.,
demonstrating self-stabilization. We then turn to fo-
cus on bounding the algorithm’s convergence time af-
ter an arbitrary and unbounded finite sequence of tran-
sient faults and changes to the network topology. In
particular, equation (2) shows that the expected lo-
cal convergence time is brief, and equation (3) for-
mulates the expected global convergence time. More-
SENSORNETS2013-2ndInternationalConferenceonSensorNetworks
120

Constants, variables, macros and external functions
2 MaxRnd (n in the proofs) : integer = bound on round number
s : [0, T-1] ∪ {⊥} = next timeslot to broadcast or null, ⊥
4 signal : boolean = trying to acquiring the channel
unused[0,T-1] : boolean = marking unused timeslots
6 unused set = { k : unused[k] = true } : unused timeslot set (macro)
MAC fetch()/MAC deliver() : MAC layer interface
8 transmit/receive/carrier sense : communication primitives
10 Upon receive(< DATA, m> ) do MAC deliver(< m> )
12 Upon carrier sense(t) (∗ defer transmission during t ∗)
if s = t ∧signal then s := ⊥ (∗ mark that the timeslot is not unique ∗)
14 (signal, unused[t ]) := (false, false) (∗ quit the competition ∗)
16 Function select unused(set) (∗ select an empty timeslot ∗)
if set =
/
0 then return ⊥ else return uni f orm select(set)
18
Upon timeslot(t)
20 if t = 0 ∧s = ⊥ then s := select unused(unused set)
(unused[t], signal) := (true, false) (∗ remove stale information ∗)
22 if s 6= ⊥∧t = s then send(MAC fetch())
24 Function send(m) (∗ send message m to p
0
i
s neighbors ∗)
for ((signal, k) := (true, 0); k := k + 1; k ≤ MaxRnd) do
26 if signal then with probability ρ(k) = 1/(MaxRnd −k) do
signal := false (∗ quit the competition ∗)
28 transmit(< BEACON> ) (∗ try acquiring the channel ∗)
wait until the end of competition round (∗ exposure period alignment ∗)
30 if s 6= ⊥ then transmit(< DATA, m> ) (∗ send the data packet ∗)
Figure 1: Self-stabilizing TDMA-based MAC algorithm, code of node p
i
.
over, for a given probability, the global convergence
time is calculated in equation (4).
We protocol implementations that deal with sit-
uations in which there is a non-constant number of
transmitting and neighboring terminals (Section 4).
Lastly (Section 5), we explain that when allow-
ing a fraction of the bandwidth to be spent on frame
control information and when considering any given
probability to converge within a bounded time, the
proposed algorithm demonstrates a low dependency
degree on the number of nodes in the network.
Due to the space limit, the proofs appear in (Leone
and Schiller, 2012a).
2 ALGORITHM DESCRIPTION
The system consists of a set, P, of N anonymous com-
municating entities, which we call nodes. Denote ev-
ery node p
i
∈ P with a unique index, i.
TDMA protocols divide the radio time into
frames, which are then divided in to T broadcasting
timeslots, where T is an upper bound on the number
of concurrently transmitting terminals in any given
neighborhood. We call N
i
the (interference) neigh-
borhood of node p
i
∈ P and d
i
= |N
i
| is named the
(interference) degree of node p
i
.
The MAC algorithm in Fig. 1 assigns timeslots to
nodes after the convergence period. We assume that
the MAC protocol is invoked periodically by synchro-
nized common pulse that aligns the starting time of
the TDMA frame (Mustafa et al., 2012). The term
(broadcasting) timeslot refers to the period between
two consecutive common pulses. In our pseudo-code,
we use the event timeslot(t) that is triggered by the
common pulse.
Nodes raise the event carrier sense() when they
detect that the received energy levels have reached a
threshold in which the radio unit is expected to suc-
ceed in carrier sense locking. We assume that times-
lots allow the transmission of DATA packets using the
transmit() and receive() primitives. Moreover, we
consider signaling (beacons) as short packets that in-
clude no data load, rather their carrier sense delivers
important information. Before the transmission of the
DATA packet in timeslot t, the scheme uses beacons
for singling the node intention to transmit the packet
within t.
During the convergence period several nodes can
be assigned to the same timeslot. The algorithm
solves such timeslot allocation conflicts by letting the
node p
i
and p
j
to go through a (listening/signaling)
competition before transmitting in its broadcasting
timeslot. The competition rules require each node
to choose one broadcasting timeslot out of n listen-
ing/signaling periods. This implies that among all
the nodes that attempt to broadcast in the same times-
lot, the ones that select the earliest listening/signaling
period win this broadcasting timeslot and access the
communication media. Before the winners access
their timeslots, they signal to their neighbors that they
won by sending beacons during their chosen signaling
periods. When a node receives a beacon, it does not
transmit during that timeslot, because it lost this com-
petition. Instead, it randomly selects another broad-
casting timeslot and competes for it on the next broad-
casting round.
3 CORRECTNESS
The proof starts by considering no changes to the net-
work topology and that the ratio between the node
extended degree and the frame size is less than one,
i.e., ∀p
i
∈P : 1 T /d
i
(see Section 4 for extensions).
We continue by focusing on the converge period for
a single neighborhood and the entire network. These
convergence estimations facilitate the exploration of
important properties for dealing with changes in the
Self-stabilizingTDMAAlgorithmsforDynamicWirelessAd-hocNetworks
121

5 10 15 20 25 30 35 40 45 50
0
0.2
0.4
0.6
0.8
1
max convergence time
probability
Observation of the max convergence time, N=500, r=0.1
empirical
theoretical bound
(a)
5 10 15 20 25 30 35 40 45 50
0
0.2
0.4
0.6
0.8
1
max convergence time
probability
Observation of the max convergence time, N=2500, r=0.1/sqrt(5)
empirical
theoretical bound
(b)
5 10 15 20 25 30 35 40 45 50
0
0.2
0.4
0.6
0.8
1
max convergence time
probability
Observation of the max convergence time, N=5000, r=0.1/sqrt(10)
empirical
theoretical bound
(c)
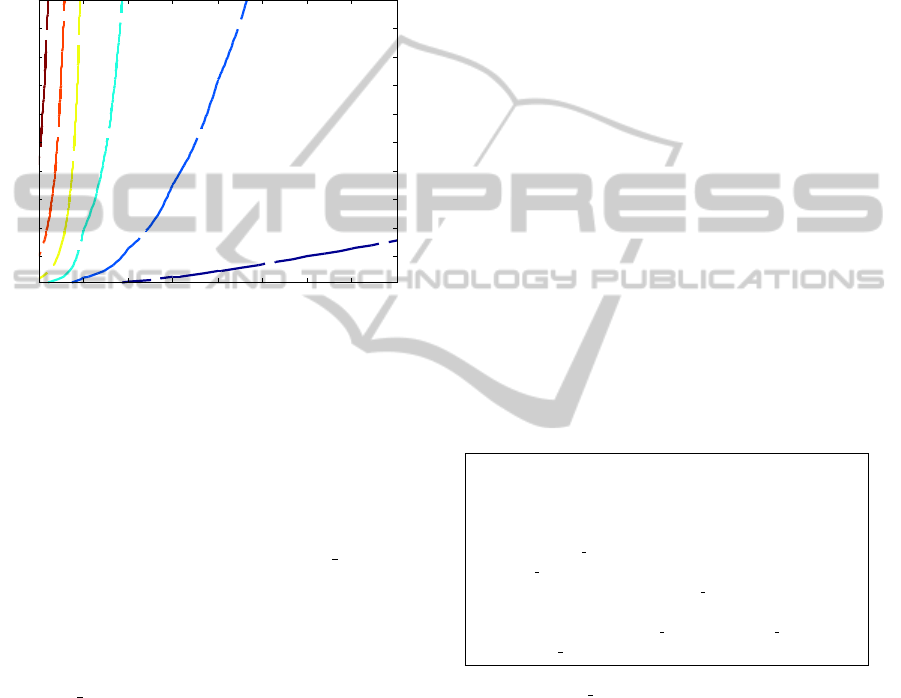
Figure 2: Numerical validation of equation (3), which bounds the network-wise convergence time. We compare the bound,
P(t
max
< k) = (1 −(1 −q)
k
)
N
, with the numerical results, which consider random geometric graphs in which the nodes are
randomly placed on the unit square. The charts considers N ∈ {500, 2500, 5000} nodes (from left to right). All experiments
considered 2 listening/signaling periods, interference range of 0.1/
p
(
N
500
), which result in an average extended degree of 15,
d
i
/T = 1 on average, and q
i
= 1/4.
network topology. Due to the space limit, the proofs
appear in (Leone and Schiller, 2012a).
The proof delineates the different states at which
a node can be in relation to its neighbors, and groups
these states into three categories of relative states: (1)
Ready to be allocated, when the node state depicts
correctly its neighbor states, (2) Obtaining a timeslot,
when the node is competing for one, but there is no
agreement with its neighbor states, and (3) Allocated
to a timeslot, when the node is the only one to be al-
located to a particular timeslot in its neighborhood.
The self-stabilization proof shows that, start-
ing from an arbitrary starting configuration, each
node eventually reaches the relative state Allocated.
OnlyOne
i
(x) is the probability that a node enters the
relative state Allocated from either Ready or Obtain-
ing, where n is the number of listening/signaling pe-
riods, T the TDMA frame size, d
i
is p
i
’s extended
degree, and ρ
k
= 1/MaxRnd = 1/n is p
i
’s probability
to select the k-th listening/signaling period for trans-
mitting its beacon.
OnlyOne
i
(x) ≥
n
∑
k=1
ρ
k
1 −
k
∑
`=1
ρ
k
!
d
i
T
(1)
Neighborhood Convergence The expected time, S
i
,
for node p
i
∈ P to reach the relative state Allocated
satisfies equation (2). Note that S
i
≤4 when the num-
ber of listening/signaling periods is n ≥ 2. Namely,
the proposed algorithm convergence with a neighbor-
hood is brief.
S
i
≤ min{
2n
n −1
d
i
T
,
d
i
T
+ 1
n
n
n −1
d
i
T
+1
} (2)
Network Convergence. The expected number of re-
transmissions is smaller than
2n
n−1
d/T
− 1, where
d = max({d
i
: p
i
∈ P}). Hence, we have that the ex-
pected number of broadcasting rounds, S, that guar-
antee that all nodes reach the relative state Allocated
satisfies equation (3).
S ≤
2n
n −1
d/T
(3)
Moreover, given that there are N nodes in the net-
work and α ∈ (0, 1), the network convergence time is
bounded by equation (4) with probability 1 −α.
k = 1 +
log
1 −
N
√
1 −α
log
1 −
n−1
2n
d
T
(4)
This means that with probability α all nodes are al-
located with timeslots in maximum k broadcasting
rounds, see Fig. (3).
We numerically validate equations (3) and (4) in
Fig. 2, and respectively, Fig. 3. Note that these exper-
iments show that the average convergence time of the
network is below the upper bound of equation (3).
4 IMPLEMENTATION
We mention mechanisms for dealing with timeslot ex-
haustion, see details in (Leone and Schiller, 2012a).
Peritonized Listening/Signaling Periods. One
can consider listening period parameters, [LSP
start
,
LSP
end
], that refer to the first, and respectively, the last
listening/signaling periods that a node can use when
attempting to acquire a broadcasting timeslot. E.g.,
suppose that there are six listening/signaling periods,
SENSORNETS2013-2ndInternationalConferenceonSensorNetworks
122
and that nodes with the highest priory may use the
first three listening/signaling periods, [0, 2], and nodes
with the lowest priority may use the last three, [3,5].
In the case of two neighbors with different listening
period parameters, say [0,2] and [3,5], that attempt
to acquire the same broadcasting timeslot, the highest
priority node always attempts to broadcast before the
lowest priority one.
20
20
20
25
25
25
30
30
30
35
35
35
40
40
40
45
45
n
N
Global convergence time if T=1 with prob. 0.99
2 3 4 5 6 7 8 9 10
1000
2000
3000
4000
5000
6000
7000
8000
9000
10000
Figure 3: Contour plot of equation (4) for s = d/T = 1. The
contour lines connect values of k(n,N) that are the same
(see the text tags along the Contour lines), where N is the
number of nodes and n is the number of signaling periods.
TDMA-based Back-off. Let us consider two back-
off parameters, CW
start
and CW
end
, that refer to the
maximal and minimal values of the contention win-
dow. Before selecting an unused timeslot, the proce-
dure counts a random number of unused ones. Fig. 4
presents an implementation of the select unused()
function that facilitates back-off strategies as an al-
ternative to the code presented in Fig. 1.
The statically allocated variable count records
the number of backoff steps that node p
i
takes un-
til it reaches the zero value. Whenever the func-
tion select unused() is invoked with count
i
= 0,
node p
i
assigns to count
i
a random integer from
[CW
start
,CW
end
]. Whenever the value of count
i
is not
greater than the number of unused timeslots, the re-
turned timeslot is selected uniformly at random. Oth-
erwise, a ⊥-value is returned after deducting the num-
ber of unused timeslots during the previous broadcast-
ing round.
5 DISCUSSION
Thus far, both schedule-based and non-schedule-
based MAC algorithms could not consider timing re-
quirements within a provably short recovery period
that follows (arbitrary) transient faults and network
topology changes. This work proposes the first self-
stabilizing TDMA algorithm for DynWANs that has
a provably short convergence period. Thus, the pro-
posed algorithm possesses a greater degree of pre-
dictability, while maintaining low communication de-
lays and high throughput.
In this discussion, we would like to point out
the algorithm’s ability to facilitate the satisfaction
of severe timing requirements for DynWANs by nu-
merically validating equations (3) and (4). As a
case study, we show that, for the considered settings
of Fig. 2, the global convergence time is brief and
definitive. Fig. 3 shows that the proposed algorithm
demonstrates a low dependency degree on the num-
ber of nodes in the network even when considering
10,000 nodes by merely using small fraction of the
bandwidth to be spent on frame control information
(say 3 listening/signaling periods) and when consid-
ering 99% probability to convergence within 30 to 35
TDMA frames.
We have implemented the proposed algorithm, ex-
tensively validated our analysis via computer simula-
tion, and tested it on a platform with more than two
dozen nodes, see (Mustafa et al., 2012). These results
indeed validate that the proposed algorithm can in-
deed facilitate the implementation of MAC protocols
that guarantee satisfying these severe timing require-
ments, such as MANETs and VANETs.
Addtional constants and variables
2 CW
start
and CW
end
: backoff parameters
count : statically allocated variable that counts the backoff steps
4
Function select unused(set)
6 let rtn val = ⊥v // indicate busy channel (default return value)
if count ≤ 0 then count ← uni f orm select([CW
start
,CW
end
])
8 count ← count− | set |
if count ≤ 0 then (count, rtn val) ←(0,uni f orm select(set))
10 return rtn val
Figure 4: select unused() with TDMA-based back-off
REFERENCES
Abramson, N. (1985). Development of the ALOHANET.
Info. Theory, IEEE Trans. on, 31(2):119–123.
Abrate, F., Vesco, A., and Scopigno, R. (2011). An analyti-
cal packet error rate model for wave receivers. In VTC
Fall, pages 1–5. IEEE.
Arumugam, M. and Kulkarni, S. (2006). Self-stabilizing
deterministic time division multiple access for sen-
sor networks. AIAA Journal of Aerospace Computing,
Info., and Comm. (JACIC), 3:403–419.
Arumugam, M. and Kulkarni, S. S. (2005). Self-
stabilizing deterministic TDMA for sensor networks.
Self-stabilizingTDMAAlgorithmsforDynamicWirelessAd-hocNetworks
123

In Chakraborty, G., editor, 2nd Inter. Conf. Distributed
Computing and Internet Technology (ICDCIT), vol-
ume 3816 of LNCS, pages 69–81. Springer.
Bilstrup, K., Uhlemann, E., Str
¨
om, E. G., and Bilstrup, U.
(2008). Evaluation of the IEEE 802.11p MAC method
for vehicle-to-vehicle communication. In VTC Fall,
pages 1–5. IEEE.
Bilstrup, K., Uhlemann, E., Str
¨
om, E. G., and Bilstrup,
U. (2009). On the ability of the 802.11p MAC
method and STDMA to support real-time vehicle-to-
vehicle communication. EURASIP Journal on Wire-
less Comm. & Net., 2009:1–13.
Casimiro, A., Kaiser, J., Karlsson, J., Schiller, E. M., Tsi-
gas, P., Costa, P., Parizi, J., Johansson, R., and Librino,
R. (2012). Brief announcement: Karyon: Towards
safety kernels for cooperative vehicular systems. In
Richa, A. W. and Scheideler, C., editors, SSS, volume
7596 of LNCS, pages 232–235. Springer.
Cornejo, A. and Kuhn, F. (2010). Deploying wireless net-
works with beeps. In Lynch, N. A. and Shvartsman,
A. A., editors, 24th Inter. Symp. on Distributed Com-
puting (DISC’10), volume 6343 of LNCS, pages 148–
162. Springer.
Cozzetti, H. A. and Scopigno, R. (2009). Rr-aloha+: A slot-
ted and distributed mac protocol for vehicular com-
munications. In Vehicular Networking Conference
(VNC), 2009 IEEE, pages 1 –8.
Cozzetti, H. A., Scopigno, R., Casone, L., and Barba, G.
(2009). Comparative analysis of ieee 802.11p and
ms-aloha in vanet scenarios. In Kirchberg, M., Hung,
P. C. K., Carminati, B., Chi, C.-H., Kanagasabai, R.,
Valle, E. D., Lan, K.-C., and Chen, L.-J., editors, AP-
SCC, pages 64–69. IEEE.
Demirbas, M. and Hussain, M. (2006). A MAC layer pro-
tocol for priority-based reliable multicast in wireless
ad hoc networks. In 3rd Inter. Conf. on Broadband
Comm., Net., and Systems (BROADNETS). IEEE.
Dolev, S. (2000). Self-Stabilization. MIT Press.
Dolev, S. and Herman, T. (1997). Superstabilizing protocols
for dynamic distributed systems. Chicago J. Theor.
Comput. Sci.
Herman, T. and Tixeuil, S. (2004). A distributed TDMA slot
assignment algorithm for wireless sensor networks. In
5th Inter. Workshop on Algo. Aspects of Wireless Sen-
sor Net. (ALGOSENSORS), volume 3121 of LNCS,
pages 45–58. Springer.
Jhumka, A. and Kulkarni, S. S. (2007). On the design
of mobility-tolerant TDMA-based media access con-
trol (MAC) protocol for mobile sensor networks. In
Janowski, T. and Mohanty, H., editors, ICDCIT, vol-
ume 4882 of LNCS, pages 42–53. Springer.
Kulkarni, S. S. and Arumugam, M. U. (2006). Sen-
sor Network Operations, chapter SS-TDMA: A self-
stabilizing MAC for sensor networks. IEEE Press.
Lagemann, A., Nolte, J., Weyer, C., and Turau,
V. (2009). Mission statement: Applying self-
stabilization to wireless sensor networks. In 8th
GI/ITG KuVS Fachgespr
¨
ach “Drahtlose Sensornetze”
(FGSN), pages 47–49.
Lenoble, M., Ito, K., Tadokoro, Y., Takanashi, M., and
Sanda, K. (2009). Header reduction to increase
the throughput in decentralized TDMA-based vehic-
ular networks. In Vehicular Networking Conference
(VNC), 2009 IEEE, pages 1–4. IEEE.
Leone, P., Papatriantafilou, M., and Schiller, E. M. (2009a).
Relocation analysis of stabilizing MAC algorithms for
large-scale mobile ad hoc networks. In 5th Inter.
Workshop on Algo. Aspects of Wireless Sensor Net.
(ALGOSENSORS), pages 203–217.
Leone, P., Papatriantafilou, M., Schiller, E. M., and Zhu, G.
(2009b). Analyzing protocols for media access control
in large-scale mobile ad hoc networks. In Workshop
on Self-Organising Wireless Sensor and Comm. Net.
(Somsed). Hamburg, Germany.
Leone, P., Papatriantafilou, M., Schiller, E. M., and Zhu, G.
(2010). Chameleon-MAC: Adaptive and self-? algo-
rithms for media access control in mobile ad hoc net-
works. In Dolev, S., Cobb, J. A., Fischer, M. J., and
Yung, M., editors, 12th Inter. Symp. on Stabilization,
Safety, and Security of Distributed Systems (SSS’10),
volume 6366 of LNCS, pages 468–488. Springer.
Leone, P. and Schiller, E. M. (2012a). Self-stabilizing
TDMA algorithms for dynamic wireless ad-hoc net-
works. CoRR, abs/1210.3061.
Leone, P. and Schiller, E. M. (2012b). Self-stabilizing
TDMA algorithms for dynamic wireless ad-hoc net-
works. In Bar-Noy, A. and Halld
´
orsson, M. M., edi-
tors, ALGOSENSORS, LNCS. Springer.
Mustafa, M., Papatriantafilou, M., Schiller, E. M., Tohidi,
A., and Tsigas, P. (2012). Autonomous TDMA align-
ment for VANETs. In IEEE 76th Vehicular Technol-
ogy Conference (VTC’12-Fall).
Schmidt, W. G. (1974). Satellite time-division multiple ac-
cess systems: Past, present and future. TeleComm.,
7:21–24.
Scopigno, R. and Cozzetti, H. A. (2009). Mobile slotted
aloha for VANETs. In VTC Fall, pages 1 – 5. IEEE.
Scopigno, R. and Cozzetti, H. A. (2010). Evaluation
of time-space efficiency in CSMA/CA and slotted
VANETs. In VTC Fall, pages 1–5. IEEE.
Tadokoro, Y., Ito, K., Imai, J., Suzuki, N., and Itoh, N.
(2008). Advanced transmission cycle control scheme
for autonomous decentralized TDMA protocol in safe
driving support systems. In Intelligent Vehicles Sym-
posium, 2008 IEEE, pages 1062 –1067.
Viqar, S. and Welch, J. L. (2009). Deterministic collision
free communication despite continuous motion. In 5th
Inter. Workshop on Algo. Aspects of Wireless Sensor
Net. (ALGOSENSORS), pages 218–229.
Ye, W., Heidemann, J. S., and Estrin, D. (2002). An energy-
efficient MAC protocol for wireless sensor networks.
In INFOCOM.
Yu, F. and Biswas, S. (2007). Self-configuring TDMA pro-
tocols for enhancing vehicle safety with dsrc based
vehicle-to-vehicle communications. Selected Areas
in Communications, IEEE Journal on, 25(8):1526 –
1537.
SENSORNETS2013-2ndInternationalConferenceonSensorNetworks
124
