
A Fuzzy Logic Model for Real-time Incident Detection in Urban Road
Network
Faisal Ahmed and Yaser E. Hawas
Department of Civil and Environmental Engineering, COE, United Arab Emirates (UAE) University, Al Ain, U.A.E.
Keywords: Fuzzy Logic and Systems, Intelligent Transport System, Urban Incident Detection, Neuro-Fuzzy, Detector
Count, Average Speed, Detection Rate, False Alarm Rate.
Abstract: Incident detection systems for the urban traffic network are still lacking efficient algorithms or models for
better performance. This paper presents a new urban incident detection system based on the application of
Fuzzy Logic modeling. Offline urban incident and corresponding non-incident scenarios are generated using
a microscopic simulation model assuming varying traffic link flows, phase timing, cycle times, and link
lengths. The traffic measures are extracted from three detectors on each link. Statistical significance analysis
was utilized to identify the significant input variables to be used in developing the Neuro-fuzzy model. A set
of data was generated and used for training of the proposed Neuro-fuzzy model, while another set was used
for validation. The performance of the proposed model is assessed using the success and the false alarm
rates of detecting an incident at a specific cycle time.
1 INTRODUCTION
The loop detector-based freeway incident detection
algorithms in literature could be generally
categorized into adopted analytical and heuristic-
based techniques (Parkany, 2005). Notable roadway
detector-based recent urban incident detection
models are mostly based on statistical regression
(Ahmed and Hawas, 2012), Bayesian network
(Zhang and Taylor, 2006) and fuzzy logic modeling
(Hawas, 2007) techniques. Non-parametric
optimization technique (Liu et al., 2007) and
discriminant analysis (Sermons and Koppelman,
1996) was used for the probe-vehicle based urban
incident detection system. Neural network models
were also developed (Dia and Thomas, 2011) using
both loop detector and probe-vehicle data.
Typically, the focus of these algorithms was
primarily on estimating the performance measures
using the percentage of the total number of incidents
detected or falsely identified incidents for the
simulated duration where the whole incident as a
single unit. These algorithms do not particularly
account for the true start or the terminating times of
individual incidents as a criterion of evaluation.
Moreover, these do not consider the effects of the
link lengths of the approaches, the hourly traffic
volumes, the signal settings and the cycle times of
the intersections. This study strives to fill in some of
these research gaps of urban incident detection areas
for more efficient detection model.
This study assumes that the duration of an
incident is divided into smaller time steps and the
algorithm is operated repeatedly each (shorter time
resolution) step to detect incidents. The proposed
fuzzy-model is capable of identifying whether there
is an incident or not during each time step. The
simulation period may be divided to hundreds of
such shorter time steps. With this approach the
actual incident start and clearance time could be
identified to a great extent.
Therefore, this paper comes up with a new form
of urban incident detection model using fuzzy-logic.
The model detects the incident status each time step,
under various signal cycle times, link lengths and
traffic volumes combinations.
2 METHODOLOGY
The conceptual assumption is that the average
detectors’ readings in the case of incident may
significantly vary from the counter readings in the
case of no incident. A micro-simulation based
methodology is adopted. A typical pre-timed urban
intersection network that consists of four links of
465
Ahmed F. and E. Hawas Y..
A Fuzzy Logic Model for Real-time Incident Detection in Urban Road Network.
DOI: 10.5220/0004239904650472
In Proceedings of the 5th International Conference on Agents and Artificial Intelligence (ICAART-2013), pages 465-472
ISBN: 978-989-8565-39-6
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)
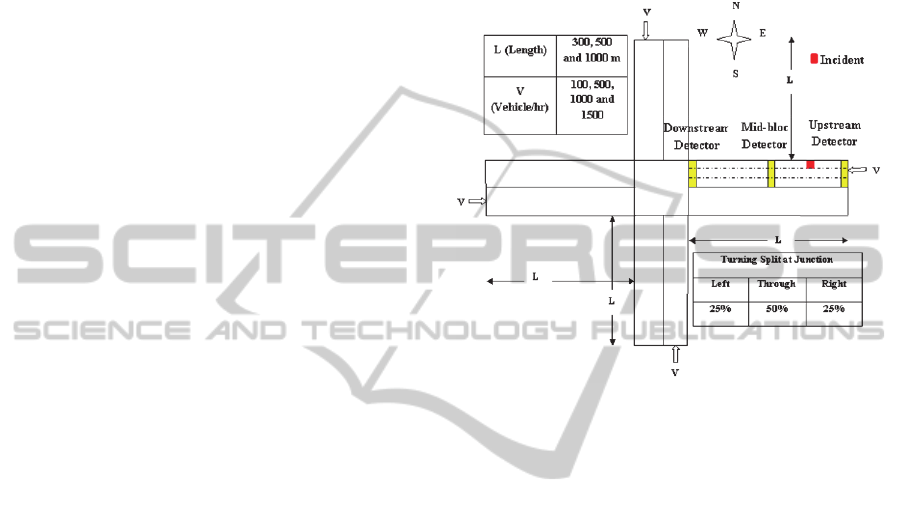
similar geometry and traffic conditions (Figure 1)
was selected as it represents the simplest case of a
signalized urban network. The overall methodology
that this study followed could be summarized as
with the following steps:
Step 1: Preparing a specific simulation test-bed (with
upstream, midblock and downstream detectors) for
the base inputs of a specific Cycle Time (sec) of
downstream signal, associated link length (m) and
hourly traffic volume (veh/hr) combination.
Step 2: Run this specific simulation model without
incident and extract the raw detectors count and
speed data (at every approach split time of the signal
cycle).
Step 3: Run this specific simulation model test-bed
again with an incident generated at a specific time
with specific incident duration, and hence extract the
raw detectors count and speed data.
Step 4: Estimate detectors count and speed data for
every analysis time step [analysis time step = cycle
time] for the both incident-free and incident-induced
runs.
Step 5: Estimate the traffic measures of interest (i.e.
independent variables) for every analysis time step.
Step 6: Repeat steps 1 to 5 for a different base input
specifics (cycle time, link length and hourly traffic
volume) and collect all the traffic measures of
interests for all analysis time-steps from all input
specific combinations.
Step 7: Develop some statistical significance tests
(ANOVA) for extracting the most significant
independent variables to be used in the proposed
incident detection model.
Step 8: Develop a Neuro-Fuzzy Model [A fuzzy
model for each specific base model that is trained
with neural net for calibrations.
Step 9: Validate this Neuro-Fuzzy Model with
validation data set. This data set is developed
following step 1 to step 5 for slightly altered input
specifics from the base cases.
Step 10: Comparison of the measures of
performance estimated by the calibrated models
using the validation data.
2.1 Experimental Set up of the Incident
Modeling
An incident is modeled here as a “lane-blocking”
event that persists at least for 6 minutes on a typical
three-lane urban arterials in the simulation models.
It is quite rational that longer time incidents,
reported in previous studies, could be detected easily
as these might have some significant impacts on the
traffic parameters. The true challenge (and that is
one of the premises of this work) is to detect the
incidents of relatively shorter times. Herein, we
focus on a single-lane blocking incidents of 6, 8 and
10 minutes incident clearance intervals. Such shorter
events will be harder to detect.
Figure 1: A simple signalized (pre-timed) urban
intersection: four approaches, detector placements and a
randomly generated incident on the Lane 1 (i.e. rightmost
lane in the direction of traffic flow) of the West bound
approach.
2.2 Incident Data Development
In the absence of detailed data of real-field detector-
based traffic measures, it is a common practice to
use well-validated simulation data to generate
incident scenarios. Previous studies ((Khan and
Ritchie, 1998); (Yuan and Cheu, 2003) and (Zhang
and Taylor, 2006)) also used simulation models to
generate the incident scenarios. However, these
studies used calibrated simulation models from the
field data. Similarly, this study also adopted
NETSIM to generate incident data. NETSIM places
the incidents randomly on the designated lane with
specific time duration; however, it cannot be
actually used to model an incident at a very specific
designated place (Yuan and Cheu, 2003).
2.3 Incident Data Analysis and Fuzzy
Models Development
The detector data were extracted for both incident
and non-incident simulation cases for various
operating configurations models. The term
‘operating configuration’ refers the combination of a
ICAART2013-InternationalConferenceonAgentsandArtificialIntelligence
466

specific cycle time, link length and traffic volume.
Specific traffic measures that are likely to vary
between incident and no incident cases were chosen
to develop the fuzzy-logic models. Incident
detection and false alarm rates were chosen as the
measures of effectiveness (MOEs) of the calibrated
fuzzy-logic models.
3 INCIDENT MODELING
For practicality issues herein, we assume that each
detector covers all the approaching lanes for
capturing the traffic data. Each detector was placed
perpendicularly to the direction of traffic flow. The
same logic could be easily adapted in case the
detectors are placed on individual lanes. When a
vehicle hits a detector, the corresponding detector’s
count is increased by one. The detector also captures
the vehicle’s speed.
Only for the simplicity and convenience of the
data extraction from the detectors, it is assumed that
incidents starting time is the start of the green phase
of the incident approach. The incident then lasts for
multiples of cycle times (based on the incident
duration). The incident terminates concurrently by
the end of a cycle time. However, this assumption
might have some impact on the time to detect of the
incidents.
The detector placements are kept fixed; near the
stop-line (downstream detector), at mid-block
position (mid-detector) and at end of the link
(upstream detector). The vehicle composition is kept
also fixed; private-cars 90% and heavy-vehicles
10%. The percentages for left, through and right
turns at each approach were fixed as 25%, 50%, and
25%, respectively. The operating speed limit was
fixed at 60 km/hr. The pre-timed signal operates on
split phase sequencing for the 4 approach legs.
The simulation test beds were varied to reflect
various signal cycle time (60, 80 or 100 seconds),
approach link length (300, 500 or 1000m) and
hourly traffic volumes (100, 500, 1000 or 1500
veh/hr). As the combination of link length of 300
and traffic volume of 1500 veh/hr resulted in link
spill back in the no-incident scenarios, and as such it
was excluded. We have 11 basic link and volume
(LV) combinations for each signal cycle to develop
simulation test beds and to extract the detector data
needed for model calibration. Thus, the LV
combinations, denoted by (Link length: Veh/hr), are
(300, 100), (300, 500), (300, 1000), (500, 100),
(500, 500), (500, 1000), (500, 1500), (1000, 100),
(1000, 500), (1000, 1000) and (1000, 1500). These
11 basic LV models for each cycle time also serve as
the base incident-free models. Then, incidents were
generated on these base test-beds with different
start-times for each incident model. The incident
models were run with the same random seed number
and initial warm-up period as of the corresponding
base incident-free models. Finally, we have 66
incident models for the 60-second cycle time cases,
55 incident models for the 80-second cycle time
cases, and 66 incident models for the 100-second
cycle time cases.
Each simulated incident model (also,
corresponding non-incident base model) was run for
the time-period of around ½ hour (i.e. 30 time steps,
23 time-steps and 18 time-steps for the 60, 80 and
100 sec signal cycle times, respectively, where a
time step is equal to a cycle time). The exact
incident specifics with the 60-second cycle time are
denoted here by the [run no: incident start time,
incident duration]. The exact runs are [R1: 2, 6],
[R2: 6, 6], [R3: 11, 6], [R4: 16, 6], [R5: 21, 6] and
[R6: 26, 5]. The 80-second runs are [R1: 2, 6], [R2:
6, 6], [R3: 11, 6], [R4: 16, 6] and [R5: 21, 3]. The
100-second runs are [R1: 2, 6], [R2: 6, 6], [R3: 11,
6], [R4: 16, 6], [R5: 21, 3] and [R6:17, 2].
4 DATA ANALYSIS
The approach used for the data analysis is based on
the assumption that it is likely that the traffic
measures (extracted from detectors) of the incident-
induced cycle-time will vary from the counter traffic
average values measured in no incident case. The
proposed model operates with a time step (cycle
time) resolution; to detect the incident status at every
cycle time.
The considered traffic measures are the
‘accumulated detector counts’ and the ‘average
detector speeds’ for all the three detectors. The data
extraction period is equal to the green split time of
that cycle. That is, for every cycle time, there are
four data extraction periods.
For the upstream detector and mid-lane
detectors, the traffic measures are estimated for each
cycle time including 4 split phases. For the
downstream detector, only the traffic measures
during the green phase are used. During the red
phases, it is expected that detectors will indicate
fixed counts and zero speed. Except for the front
leading vehicles near the STOP line (near the
downstream detector), no other vehicles would hit
the downstream detector during the red phases.
AFuzzyLogicModelforReal-timeIncidentDetectioninUrbanRoadNetwork
467

5 DEVELOPMENT OF
FUZZY-BASED INCIDENT
DETECTION MODEL
A neuro-fuzzy approach was adopted to develop the
incident status prediction models presented in this
paper. In developing the fuzzy model, the
independent variables (as indicated above in Table
1) are the traffic measures extracted from the
simulation detectors. The parameters UC, US, MC,
MS, DC and DS of Table 1 are the recorded detector
data for each of the simulation time-step of the
incident models or the operating time-step in reality.
The parameters C
1
, C
2
, C
3
, S
1
, S
2
and S
3
are also the
recorded detector data for each time step with no-
incident scenarios out of the corresponding base LV
model of each operating configuration. In reality,
based on the detector readings of (say) the previous
3 to 5 time steps, the model could identify the
closest base scenario for the retrieval of the
parameters.
After some comprehensive statistical
significance tests with Factor Analysis in Minitab, it
was observed that Y
1
, X
2
, Y
2
and Y
3
in Table 1 are
the most significant independent variables in
predicting the incident status by some general linear
regression (GLM) models. So, the same four
independent variables were considered as the input
membership functions for the fuzzy logic models.
The dependent variable of the fuzzy model is
either an incident status (yes) or a normal recurrent
traffic condition (no incident) of a single time-step.
Because of the unavailability of the neuro-fuzzy
training for the discrete binary dependent variables,
the dependent variable of the proposed fuzzy-logic
was considered as continuous variable while using
the program FuzzyTECH 5.5 (INFORM, 2001).
The ‘true’ range of the dependent variable of an
incident status is allocated the central value of 1 for
an incident, and the ‘false’ range of the dependent
variable of a non-incident status is allocated the
central value of 0.
In applying the fuzzy-logic model to predict the
incident status, a threshold value is utilized. If the
estimated dependent variable is higher that the
threshold value (say 0.500) an incident is indicated,
otherwise it's a normal condition. The threshold
value is chosen to maximize the incident detection
rate and minimize false alarms. Such threshold was
determined through comprehensive iterative
analyses. Initially, the value of 0.500 was set as the
intuitive separating point between incident and non-
incident status. Then, a brute-force search was
adopted with 0.001 units of increase/decrease for
next iteration until the improvement in the incident
detection rate is noticed, while keeping the false
alarm rate within some acceptable limits.
The adopted measures of effectiveness of this
model are as follows:
Incident Detection Rate: The percentage of time
steps that the FLM predicts the incident time steps
correctly. The true detection of incident status of a
time step is defined as the prediction of an incident
status by the model while this time step was truly an
incident-induced simulated time step.
False Alarm Rate: The percentage of time steps
that the FLM predicts an incident status out of all
normal incident-free time steps. The false detection
of a time step is defined as the prediction of an
incident status by the FLM while this time step was
truly incident free.
It is to be noted that the average time to detect the
incident is the duration of one time step (which is
equal to one cycle time) as this model detects
whether an individual time step is incident-induced
or incident-free.
6 FUZZY SYSTEM STRUCTURE
The simple FLM structure shown in Figure 2 was
adopted. The connecting lines symbolize the data
flow.
Four input variables with the associated
linguistic terms were identified for the logic as
shown in Table 2. The output ‘Incident_Status’ is an
index for incident possibility with two linguistic
terms (False and True); the higher the index the
higher the possibility of an incident.
6.1 Fuzzification
The linear (L-shaped) membership function (MBF)
was adopted for all variables. The membership
functions are initially set equally distributed over the
range of all possible values. Each variable’s term is
defined by that single value that corresponds to a
term membership value (µ) of 1 as shown in Figure
3.
The Neuro-Fuzzy training algorithm is used to
optimize these confidence levels and the
membership functions via data training as will be
explained later.
ICAART2013-InternationalConferenceonAgentsandArtificialIntelligence
468
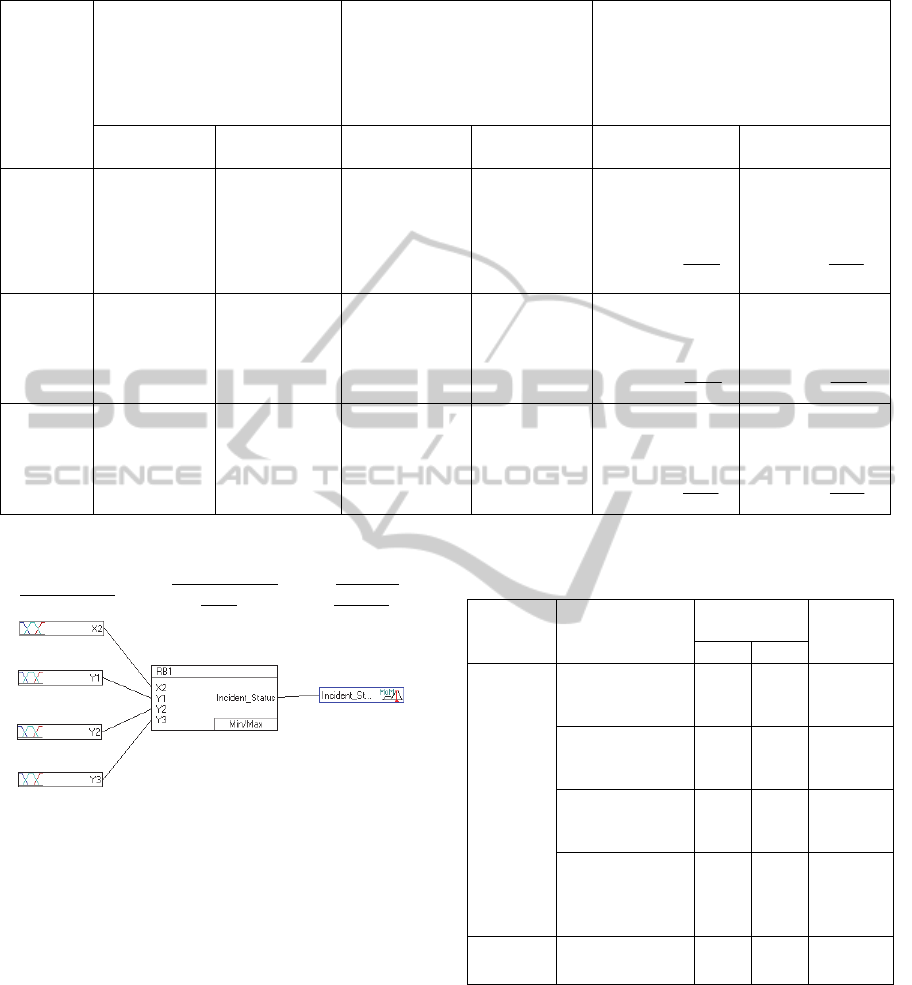
Table 1: Traffic measures used in the incident detection models.
Detector
Traffic measures of the incident
scenarios
[for each analysis
time-step (cycle time)]
Traffic measures of the no-
incident
scenarios
[for each analysis
time-step (cycle time)]
Parameters to be used in the models (for
each cycle time)
n: total number of simulated cycle times
for a specific combination
[n= 30, 23 and 18 for the cycles of 60 ,
80 and 100 seconds, respectively]
Vehicle count
measures
Speed measures
Vehicle count
measures
Speed measures
Vehicle count
measures
Speed measures
Upstream
detector
[data at each
cycle]
Total vehicle
count
(UC)
Average speed
(US)
Total vehicle
count
(C
1
)
Average speed
(S
1
)
deviation of
upstream detector
count:
n
C
UCX
1
1
deviation of
upstream detector
speed:
n
S
USY
1
1
Midblock
detector
[data at each
cycle]
Total vehicle
count
(MC)
Average speed
(MS)
Total vehicle
count
(C
2
)
Average speed
(S
2
)
deviation of
midblock detector
count:
n
C
MCX
2
2
deviation of
midblock detector
speed:
n
S
MSY
2
2
Downstrea
m
detector
[data at each
cycle]
Total vehicle
count [during
green phase]
(DC)
Average speed
[during green
phase]
(DS)
Total vehicle
count [during
green phase]
(C
3
)
Average speed
[during green
phase]
(S
3
)
deviation of
downstream
detector count:
n
C
DCX
3
3
deviation of
downstream
detector speed:
n
S
DSY
3
3
Input
(Fuzzification)
Inference Engine
(Inference Rule
Base)
Output
(Defuzzi-
fication)
Figure 2: The FLM structure of the urban incident
detection model.
6.2 Fuzzy Inference Process
The fuzzy inference consists of three computational
steps: Aggregation, Composition, and Result
Aggregation (INFORM, 2001). The rules (IF-THEN
logics) were generated to describe the logical
relationship between the input variables (IF part) and
the output variable (THEN part). Initially, all the
possible combinations of rules (3*3*3*3*2=162)
were set initially with equal degree of support (DoS)
of 0.5 as shown in Table 3. The initial value of the
DoS for each rule is adjusted by neuro-fuzzy
training.
Table 2: The FLM input and output variables, numerical
ranges, and linguistic terms.
Variable
category
Variable name
(Denoted in FLM)
Numerical
ranges
Linguistic
terms
Min Max
Input
variables
deviation of
upstream detector
speed (Y
1
)
-17.96 24.11
Low,
Medium,
High
deviation of
midblock detector
count (X
2
)
-14.56 42.28
Low,
Medium,
High
deviation of
midblock detector
speed (Y
2
)
-31.51 21.74
Low,
Medium,
High
deviation of
downstream
detector speed
(Y
3
)
-28.75 43.53
Low,
Medium,
High
Output
variable
Incident Status
(Incident_Status)
-1 +2
False,
True
Among the several available operators (such as
AND, OR, Min–Max, Min–Avg, Gamma), the
‘Min–Max’ operator resulted in minimum training
error.
AFuzzyLogicModelforReal-timeIncidentDetectioninUrbanRoadNetwork
469
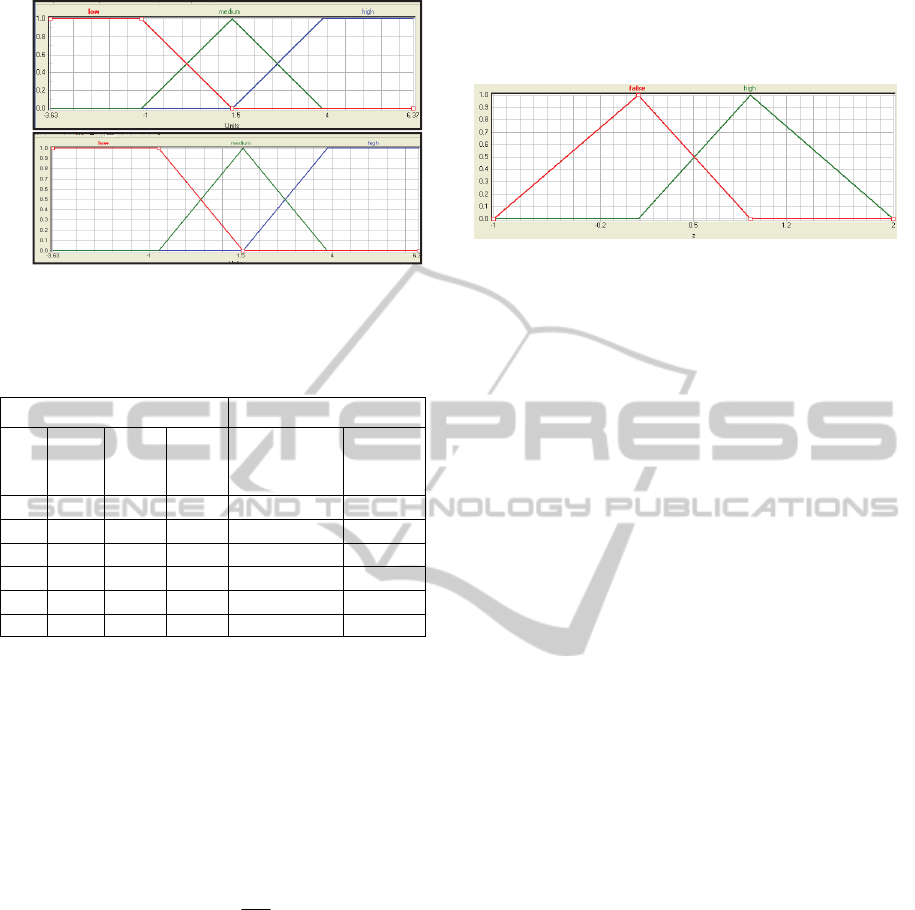
(a)
(b)
Figure 3: (a) the initial and (b) finally calibrated MBF of
input Y
2
(60-second cycle, 50-m link length and 1000
veh/hr scenario).
Table 3: Examples of sample IF-THEN rules.
IF THEN
Y
1
X
2
Y
2
Y
3
DoS
(initial:
final)
Incident_
Status
low low low low (0.50: 0.97) False
low low low low (0.50: 0.98) True
low low high low (0.50: 0.49) False
low low high low (0.50: 0.50) True
low low high high (0.50: 0.45) False
low low high high (0.50: 0.50) True
6.3 Defuzzification
Among the several defuzzification methods, the
adopted MoM (Mean-of-Maximum) method delivers
the "most plausible" result that is mostly used in
pattern recognition problems. The MoM method
generates the mean value (z
0
) of all output units,
whose membership functions (from Figure 4) reach
the maximum as follows:
k
j
j
o
k
z
z
1
Where
z
j
: output unit whose membership functions reach
the maximum
k: number of such output units.
6.4 Neuro-Fuzzy Data Training
The neuro-fuzzy system can be viewed as a three-
layer feed forward neural network similar to the
above traditional fuzzy system (Figure 2) with a
layer of hidden neurons used to perform each
process. The first layer represents the input variables
fuzzification process, the middle hidden layer
represents the fuzzy rule inference process and the
third layer represents the output variable
defuzzification process.
Figure 4: The final values of output (Incident_Status) after
nuero-fuzzy training of the MBF (60-second cycle, 500-
meter link length and 1000 veh/hr scenario).
The ‘calibration’ here refers to finding the
‘optimal’ fuzzy membership shape and the Degree
of Support (DoS) for the IF–THEN rules. In the first
step, all MBFs and rules were selected for the neuro-
fuzzy training to find the optimised FLM. Then, the
parameters (step width for DoS and terms) were
selected for the training. The whole neuro-fuzzy
training was carried out for five cycles with each
cycle for 1000 iterations.
The step width for the DoS values has been set to
0.1 for each cycle. The step width for the terms has
been set to 5% in the first cycle, which was
increased by 5% in later cycles. The maximum and
average deviations were observed after completion
of each cycle. The cycle, for which the deviation
values are less, was selected as the final FLM. After
the training phase, the MBFs and the DoS values
were determined as shown in Table 3 and Figure
3(b).
7 RESULTS
For the 60-second signal time models, the
performance measures, denoted by (FLM threshold,
incident detection rate, false alarm rate), for the
mentioned 11 LV combinations are (0.500, 26%,
10%), (0.500, 69%, 0%), (0.200, 77%, 24%), (0.200,
46%, 39%), (0.200, 46%, 15%), (0.500, 77%, 9%),
(0.500, 31%, 1%), (0.500, 40%, 19%), (0.500, 66%,
9%), (0.500, 34%, 9%) and (0.500, 43%, 9%),
respectively. With the 80-second signal time models,
the performance measures are (0.500, 41%, 8%),
(0.500, 96%, 0%), (0.500, 78%, 0%), (0.500, 22%,
5%), (0.500, 67%, 3%), (0.500, 85%, 6%), (0.500,
70%, 0%), (0.500, 56%, 51%), (0.500, 0%, 0%),
(0.500, 0%, 0%) and (0.500, 56%, 1%), respectively.
With the 100-second signal time models, the
performance measures are (0.500, 0%, 0%), (0.500,
ICAART2013-InternationalConferenceonAgentsandArtificialIntelligence
470

90%, 0%), (0.500, 90%, 0%), (0.500, 61%, 21%),
(0.500, 90%, 23%), (0.500, 77%, 17%), (0.500,
81%, 1%), (0.500, 48%, 9%), (0.500, 65%, 5%),
(0.500, 87%, 25%) and (0.500, 68%, 10%),
respectively. Thus, the incident detection rates range
from 0% to 96%, while the false alarm rates range
from 0% to 51%. Except for few operating
conditions, the average detection rate is mostly
above 55%.
The worst performance of the FLM (low
detection rate and/or very high false alarm rate) is
evident with low traffic volumes. At low traffic
volumes, incidents do not significantly impact the
detector readings or the adopted traffic measures
(especially for the cases of partial blockage). Even
with long incident durations, vehicles could easily
bypass the blocked lane through other free lanes.
This limitation (low detection rates at low traffic
volumes) is quite similar to that of the freeway
incident detection models. At such low traffic
volumes one may argue that traffic control centre
does not necessarily have to respond by control
adjustments as the incident does not impact the
traffic flow significantly. Also, for the case of 80-
second cycle time, the FLM for the case of long link
length (i.e. 1000 m) seems performing worse with
relatively low detection rates. This may be attributed
to the delay in detecting incidents caused by the
longer travel times on links.
By excluding the scenarios of low traffic volume
(100 veh/hr), the average detection rate of the
proposed FLM is 64.3% (55%, 57% and 81% for the
signal cycles of 60, 80 and 100 seconds,
respectively), and the average false alarm rate is 7%.
This FLM seems performing better with lower false
alarm rate (7%) as compared to the GLM based
regression models (11.7%) developed by Ahmed and
Hawas (2012). The average detection rate of the
GLM models (64.6%) is close to that of the FLM
(64.3%).
8 VALIDATION TESTS
Another set of different incident scenarios was
modeled with NETSIM for validation test. This
would also test the robustness of the devised FLMs.
Here, all scenarios were modeled with 8 time steps
incident duration (480, 640 and 800 seconds for the
cycle times of 60, 80 and 100 seconds, respectively),
where the incidents starting and ending time steps
were set to 9 and 16, respectively. The calibration
data set was from the lane 1 incidents only, but the
validation data set were generated from the incidents
of both lane 1 and lane 2. Thus, it reflects significant
changes to incident occurrence specifics as
compared to the data used for calibration. Some of
the lane-2 incidents were generated with hourly
traffic volumes of 500 and 1000 veh/hr with various
link lengths and cycle time of 60 seconds. Others
were generated with hourly traffic volumes of 100
and 1500 veh/hr, various link lengths and cycle time
of 80 seconds. Also, some incidents were generated
with hourly traffic volumes of 500 and 1500 veh/hr
with various link lengths and cycle time of 100
seconds.
The developed FLM of each specific
combination (i.e. from the 33 operating
configurations) was used to predict the incident
status using the data of the validation scenarios.
Lane-2 incident validation scenarios resulted in
average detection rate of 32% (standard deviation
20%), and average false alarm rate of 14% (standard
deviation 17%). Lane-1 validation scenarios resulted
in 19% average detection rate (standard deviation
21%) and 8% average false alarm rate (standard
deviation 12%).
It is to be noted that the lower detection rates of
the validation scenarios (as compared to the results
reported in the calibration of the FLM) might be
attributed to the insufficient data as for each specific
combination of cycle time, link length and volume;
only one incident scenario for each combination
whereas there were at least 5 incident scenarios in
calibration. Furthermore, the calibration data was
somehow limited in the sense that it did not consider
overall random variations in incident durations, start
and end times.
9 CONCLUSIONS
This paper presented an FLM approach that
combines simple fuzzy logic models and threshold
values for each specific combination of cycle time,
link length and hourly traffic volume. Except the
relatively lower hourly traffic volumes, the incident
detection and the false alarm rates were satisfactory
for all the cases.
There is still a significant room for improving the
presented FLM to obtain more efficient and robust
models. Also, further challenges remain in
predicting the incident status with significantly wide
variations of the input attributes accounting for other
aspects such as the malfunctioning of the detectors
and the variations with detector placements. Further
research is intended to focus on improving the FLM
by considering the impact of random incident
AFuzzyLogicModelforReal-timeIncidentDetectioninUrbanRoadNetwork
471

locations, durations, and different detector
placements. Other improvements could include the
generalization of the FLM to account for over-
saturated traffic conditions when link spill back
occurs. Further research would also consider
different settings of the FLM structure in terms of
reduced number of input parameters. Also, a general
FLM (for various operational conditions) will be
strongly needed.
REFERENCES
Ahmed, F., Hawas, Y. E., 2012. A threshold-based real-
time incident detection system for urban traffic
network. 4
th
International Conference: Transport
Research Arena (TRA) Europe, Athens, Greece, April
23-26, 2012.
Dia, H., Thomas, K., 2011, Development and evaluation
of arterial incident detection models using fusion of
simulated probe vehicle and loop detector data.
Information Fusion, 12, 2011, 20–27.
Hawas, Y. E. , 2007. A fuzzy-based system for incident
detection in urban street networks. Transportation
Research Part C, 15, 2007, 69–95.
INFORM, 2001, FuzzyTech 5.5: User’s Manual.
GmbH/Inform Software Corporation, Germany.
Khan, S. I., Ritchie, S. G. 1998. Statistical and neural
classifiers to detect traffic operational problems on
urban arterials. Transportation Research C, Vol 6,
1998, pp. 291–314.
Liu, Y., Lei, Y., Yi, Q., Jianquan, W., Huimin, W., 2007,
Traffic incident detection algorithm for urban
expressways based on probe vehicle data. Journal of
Transportation Systems Engineering & Information
Technology, Vol. 8(4), 2007, 36-41.
Parkany, E. 2005. A complete review of incident detection
algorithms & their deployment: what works and what
doesn’t. The New England Transportation
Consortium. NETCR37.
Sermons, M. W., Koppelman, F. S., 1996. Use of Vehicle
Positioning Data for Arterial Incident Detection.
Transportation Research Part C, 4(2), 1996, 87-96.
Yuan, F., Cheu. R. L. 2003. Incident detection using
support vector machines. Transportation Research C,
Vol 11, 2003, pp. 309–328.
Zhang, K., Taylor, M. A. P., 2006. Effective arterial road
incident detection: a Bayesian network based
algorithm. Transportation Research Part C, 14, 2006,
403–417.
ICAART2013-InternationalConferenceonAgentsandArtificialIntelligence
472
