
Design and Configuration of Context-aware VoIP Telephony Systems
Slawomir Nasiadka
Gdansk University of Technology, Narutowicza 11/12, Gdansk, Poland
Keywords:
Context, Context-aware, VoIP, Telephony, Design, Configuration.
Abstract:
Voice over IP is a widely used concept with regard to a realization technology of different types of telephony
systems, including those that are used in enterprises. Such systems consist of a call processing component and
a set of desk endpoints that are pervasive from a user perspective. Those endpoints are usually not mobile,
but in result can deliver a much greater set of functions needed in an everyday office work (e.g. secretary
and attendant features). Those functions also make VoIP telephony systems well suited for using a context
information to adapt to the situations of their users. The paper presents an approach to designing such systems
from a context-aware point of view and organizing a configuration of their objects. A sample deployment has
been prepared and evaluated.
1 INTRODUCTION
A context (Krawczyk and Nasiadka, 2011) with re-
gard to a communication between people can be used
in different ways (Schilit et al., 2007). However, they
mostly regard cell phones and extension of their ca-
pabilities to interpret context data. Apart from those
devices there is also a group of telephony systems
(TS) used within enterprises and smaller companies.
They consist of distributed or centralized call process-
ing system and a set of desk endpoints (or softphones)
that are pervasive from a user perspective. Those end-
points can deliver a much greater set of functions that
are needed in an everyday office work (e.g. secretary
and attendant features) than cellular phones. Such
TS systems are often VoIP (Johnston, 2009) based
solutions. As enterprises are global and hire great
number of people located worldwide, those systems
can become very large and complex. Nevertheless,
they are supposed to offer their users a context-aware
functionality. Delivering it can be challenging from
a design and configuration point of view. The aim
of this article is to propose a new approach to design-
ing enterprise telephonysystems and configuring tele-
phony objects (e.g. endpoint devices) using informa-
tion about their context. There has been prepared a
sample deployment of a VoIP TS enhanced with the
environment based on the system for dynamic ser-
vice integration described in (Dziubich et al., 2012).
Thanks to the presented approach the design process
regarding context-awareness can be systemized and
TS can dynamically adapt to changes in its and its
users environment.
The reminder of the article is constructed as fol-
lows. Section 2 describes state of the art regarding
context-aware behavior of telephony devices. In sec-
tion 3 there is presented a model of a VoIP telephony
system (VoIP TS). Section 4 describes how a context
is used in VoIP TS across its layers. In Section 5 there
is introduced a new approach to designing and con-
figuring context-aware VoIP TS. This approach has
been used to prepare a sample deployment which is
described in Section 6. This section also briefly de-
scribes experimental results regarding introduction of
that approach. Section 7 summarizes the paper.
2 RELATED WORK
The vast majority of publications regarding context-
aware telephony refer to mobile interruptions. They
address the problem of cell phones ringing at inap-
propriate moments (such as in a theater). In the pa-
per (Schmidt et al., 2000) authors propose a mech-
anism that addresses this issue. Each mobile phone
user can choose a state which expresses if he is will-
ing to receive calls. Callers can then check what
is the status of the person to whom the call is to
be made and decide whether to make a call. An-
other approach is presented in the publication (Raento
et al., 2005), where authors describe a framework that
allows to automatically collect information about a
context of a mobile phone user. This context can
42
Nasiadka S..
Design and Configuration of Context-aware VoIP Telephony Systems.
DOI: 10.5220/0004314100420048
In Proceedings of the 3rd International Conference on Pervasive Embedded Computing and Communication Systems (PECCS-2013), pages 42-48
ISBN: 978-989-8565-43-3
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

then be presented in various forms to the caller who
can decide whether to continue with the call. How-
ever, such an approach means sharing certain pri-
vate information (e.g. location) about people. The
paper (Khalil and Connelly, 2006) draws attention
to this aspect and describes what are people prefer-
ences regarding providing information about their sit-
uation. Described publications touch different aspects
of VoIP telephony systems (including design, tools
and frameworks), however they mostly regard mobile
phones which greatly differ from enterprise VoIP sys-
tems. Another approach has been described in (Chi-
han et al., 2012), where authors concentrate on creat-
ing a framework for developing context-aware com-
munication systems. That work focuses on communi-
cation services, but lacks the analysis of how a design
and configuration of particular objects existing in a
telephony system should be organized with regard to
context-awareness.
Some commercial systems (like Cisco Unified
Communications Manager) already use context data.
For instance, Cisco softphonesmay be used by mobile
users in different locations where the same distributed
VoIP TS is deployed. Because of using VoIP technol-
ogy the current location can be easily recognized (e.g.
by the IP address) by the TS and during a registra-
tion of an endpoint and it can be assigned a different
set of configuration entries than in its home location.
That set of entries can influence mainly on its dial-
ing capabilities (e.g. allowing dialing only internal
calls) and on a codec it uses to encode a voice stream.
A context can also be used during assigning different
call routing rules. E.g. depending on a current time,
an endpoint may have different dialling restrictions.
During work hours it can be allowed to dial any type
of numbers, but after work hours only internal and
emergency calls are allowed. However, commercial
products make use of only limited context data and
only in some particular configuration aspects.
3 VoIP TELEPHONY SYSTEM
MODEL
Telephony systems can be described using a layered
model which is shown in Figure 1.
The lowest layer (endpoints layer) represents
physical devices that are used by users to make calls
(phones, softphones). That layer also includes gate-
ways to Public Switched Telephone Network (PSTN)
and other devices or software that are used as termina-
tion points of media streams (such as media resources
- like transcoders, conference bridges, and so on).
Those devices register to a TS through a register (reg-
Figure 1: A telephony system layered model.
istry layer), which includes information about values
of parameters describing endpoints. Those parame-
ters may represent a location of a device, its codec or
video capabilities and so on. They are used in the pro-
cess of call routing and establishment. That process is
actually the most important one in every TS and is lo-
cated in a separate layer - call routing layer. Based on
the information from the registry the call routing pro-
cess, routes and establishes calls between endpoints
based on the input from a caller. The top layer - ap-
plication layer - represents applications that utilize the
call routing and establishment process, such as Au-
tomatic Call Distribution (ACD) or Auto Attendand
(AA). Within each of the presented layers there have
to be configuration, security and safety mechanisms
available.
A VoIP Telephony System (VoIP TS) is a tele-
phony system that uses the Internet Protocol (IP) as
a transport protocol for voice and signalization pack-
ets. On the one hand it simplifies the management
of the infrastruture, but on the other hand it causes
difficulties in guaranteeing proper QoS characteristics
- mainly regarding latency, jitter and queue manage-
ment (Verma, 2011). That is why across all the lay-
ers of the ISO/OSI model (Tanenbaum, 2010) there
have to be introduced advanced QoS mechanisms
(like LLQ - Low Latency Queuing). Another feature
that is available to users in VoIP TS systems is a mo-
bility of endpoints. Wherever a particular endpoint is
connected to the IP network, if only it can communi-
cate with its VoIP TS, it can register and function with
the same settings as in the home location. That gives
users a consistent experience and allows administra-
tors to easily manage a whole telephony infrastruc-
ture. Moreover, those endpoints also provide addi-
tional functionalities like access to web applications.
As it can be observed the usage of the IP protocol
mostly incluences on the endpoints and registry lay-
ers. Often the QoS mechanisms are controlled by the
call routing layer.
Deploying a VoIP TS is a complex process which
most important parts are a design and a configuration
of particular TS mechanisms and objects across all
DesignandConfigurationofContext-awareVoIPTelephonySystems
43

the layers of the TS layered model (see Figure 1).
Those parts are organized according to the user re-
quirements which may regard a context-awareness.
Because those requirements may be formulated late
by the users during the deployment (e.g. based on
the experience of using a partly deployed TS system)
an agile-based approach is necessary. To introduce a
new approach to designing and configuring a context-
aware VoIP TS there will be analyzed a sample VoIP
TS deployment. Its initial set of requirements is sum-
marized in Table 1.
Table 1: Initial set of requirements for the sample VoIP TS
deployment.
Id Requirement
1 200 users in different locations (geograph-
ically distributed)
2 a redundancy (2 sites)
3 a local PSTN access and a toll bypass
functionality
4 Direct Dial-In (DDI) numbers for users
5 calling to international numbers should be
available only for a particular group of
users
6 a Voice Mail account for each user
7 an ability to move users between loca-
tions and an automatic adjutsing of config-
uration parameters of their endpoints (e.g.
codecs)
8 after work hours all incoming calls should
be routed directly to cell phones or voice
mail when no answer
9 an administration should only be allowed
for users with appropriate skills
10 a line description, a presentation and a
phone language should change after a user
logs into a workstation
Some of the requirements regard functionalities
that don’tdepend on context(like number of usersand
telephony numbers that they use). However, some of
them are context-aware (with ids 7 - 10). How a con-
text can be utilized in TS VoIP systems is described
in the next section.
4 CONTEXT IN VoIP TS
With regard to context-awaresystems there can be de-
fined two types of input data (Krawczyk and Nasi-
adka, 2011). In case of a context-aware VoIP TS the
first one is related to the user input which is a tele-
phony number that the user enters to reach a called
party (called DNIS number). The second one is the
data that create context which can influence on differ-
ent aspects of the TS behavior that are spread among
layers from the model presented in Figure 1.
4.1 Endpoints
Endpoints can perform sensing, processing and act-
ing functions. This is possible because in a VoIP TS
they need to perform complex operations during each
call (e.g. a TCP/IP connection establishment, encod-
ing voice). Hence, they are equiped with a processor
and memory which can also be utilized to perform
additional operations, that are not directly related to
the telephony. Those operations can be context-aware
(e.g. switching a device to an idle mode after a par-
ticular amount of inactivity time). Thanks to this, the
usage of a VoIP enterprise telephony makes the space
where it is deployed intelligent (Intelligent Space -
IS). That is further used in such concepts as intelli-
gent buildings, where telephony endpoints are used
as interfaces for users to non-telephony systems (like
controlling an air condition or a room automation).
4.2 Registry
A registry that contains all the information about end-
points also needs to allow to enhance them with con-
text data. Moreover, it should be possible to change a
configuration of entries based on the current context.
That is crucial e.g. for mobile users, who can con-
nect an endpoint to the infrastructure anywhere they
are. Depending on a location and other context data
the informationcontained in the registry should be ap-
propriately changed, so that e.g. a codec negotiation
and call routing mechanisms can behave correctly.
4.3 Call Routing
Because of the use of the IP protocol for transporting
media packets, different quality issues in a VoIP TS
may arrise. Hence, depending on the situation in the
network layer (which may also be included in a con-
text) and information contained in the registry, the call
routing mechanism has to establish connections dif-
ferently to maximise a quality of calls (e.g. in case of
a total Wide Area Network bandwidth saturation the
VoIP TS system should use external PSTN circuits to
establish long distance calls). Other type of context
PECCS2013-InternationalConferenceonPervasiveandEmbeddedComputingandCommunicationSystems
44

data that can be used during execution of processes
from this layer is the current time.
4.4 Applications
A behavior of additional call handling applications
(e.g. Interactive Voice Response, Voice Mail, Auto
Attendant) may be different depending on an ANI
number, a time, data, a profile of a caller and so on.
A management and administration of the system and
a login and logout functionality for users also creates
context that can be used by applications.
Because endpoints provide an access to function-
alities and information anytime and anywhere, they
can be treated as pervasive devices. As a result, the
layered model presented in Figure 1 can be divided
into a pervasive part, which consists of the endpoints
layer and a ubiquitous part, which consists of the reg-
istry, the call routing and the applications layer. That
reflects the nature of enterprise telephony systems,
where endpoints are distributed among users (they are
physically close to them and each user has his own
endpoint) and the rest of the system is logically cen-
tralized but accessible anywhere users need.
From the set of requirements presented in Table 1,
last four of them regard context-awareness. To deliver
a system which meets those requirements it is nec-
essary do go through the process of its deployment
which mainly includes design and configuration.
5 DESIGN AND
CONFIGURATION APPROACH
FOR CONTEXT-AWARE VoIP TS
A deployment of a context-awareVoIP TS can be sys-
temized with the usage of the layered model presented
in Figure 1. A resulting approach is organized accord-
ing to the Agile method. Firstly, the requirements
for a new VoIP TS deployment have to be assigned
to the particular layers of the TS model. Next, each
of the requirements needs to have assigned a priority
expressing its importance from the user perspective.
Based on the analysis, for each requirement there can
be assessed a time that is needed to prepare a nec-
essary configuration. The conducted analysis should
include a necessary design of a part of the VoIP TS
(which will satisfy the requirements) as well as inter-
ferences with the already deployed parts of the sys-
tem. The design that regards context-aware require-
ments should include defining a situation (particular
context) to which appearance in the space the VoIP
TS will react, and also which configuration changes
in the TS will take place. Based on the priorities, as-
sessments and time constraints the deployment pro-
cess can be divided into separate iterations. After
each iteration is completed, there is delivered a use-
ful from the user perspective functionality that can be
tested and accepted. That also allows users to intro-
duce new or correct previously specified requirements
along with the progress of the deployment, which is a
common situation during VoIP TS deployments. The
organization of the sample deployment which resulted
from implementing described approach is presented
in Table 2 (context-aware requirements are marked
with ’(c)’).
Comparing to the initial set of requirements (see
Table 1) a one additional requirement has been for-
mulated by users. After they used a partly deployed
system (delivered in the first iteration) users decided
that when someone logs out from a workstation, an
office phone should switch to a stand-by (idle) mode
and should require an authorization for making calls.
That requirement (with id 11(c)) appeared during the
second iteration and its realization has been planned
for the third iteration. Within each iteration after the
design is completed, a necessary configuration needs
to be prepared.
VoIP TS systems may need to behave differently
depending on their (and their objects) context. Hence,
a particular object (apart from the initial configuration
needed to satisfy context-unaware requirements) may
need to be reconfigureddepending on context data de-
livered by sensors (i.e. endpoints - see Section 4 or
other sources). Nowadays, such context-aware recon-
figuration can be based on a limited set of parameters
(most often a time and a location). However, VoIP
TS systems can be deployed in different environments
and the definition of a context can change between
deployments. That is why a VoIP TS should have a
capability of defining a context and based on it - re-
configuring its particular objects. Context data can be
sent by sensors using a SIP protocol (Pan et al., 2003)
(in a form of additional headers) which is widely used
in the telephony signalization.
Regarding an aspect of context-awareness, VoIP
TS systems can be modelled using the CAA model in-
troduced in (Krawczyk and Nasiadka, 2011). As such
their architecture can be extended with components
needed to execute CAA applications. Those compo-
nents are responsible for context analysis, commu-
nication with sensors, knowlegde base management
and changing configuration. The implementation of
such extension for a particular VoIP TS deployment
has been described in the next section.
DesignandConfigurationofContext-awareVoIPTelephonySystems
45
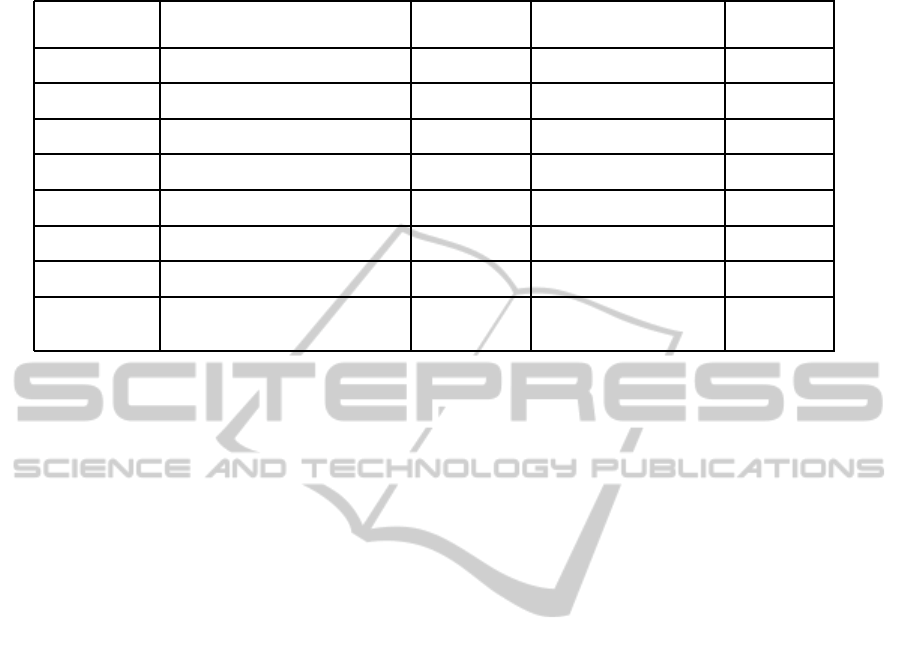
Table 2: An organization of design and configuration tasks in the sample deployment.
Requirement
id
Layer Priority (1 -
highest)
Time assessement in
MD - ManDay
Iteration
number
1, 2 application layer 1 25MD 1
3 call routing layer 1 5MD 1
4, 5 registry layer 1 7MD 1
6, 9(c) application layer 2 11MD 1
7(c) registry layer 1 5MD 2
8(c) call routing layer 2 1MD 2
10(c) registry layer 2 10MD 2
11(c) endpoints layer and registry
layer
2 5MD 3
6 IMPLEMENTATION
To see how the presented approach behaves in a real
life scenario, there was prepared a sample deploy-
ment of a VoIP TS. It was organized according to
Table 2. The deployment was based on the Cisco
Unified Communications Manager (CUCM) 8.5 plat-
form. That platform already has some context-aware
mechanisms built into the registry and the call rout-
ing layers but they are too limited to fulfill all the re-
quirements presented in Table 2 (i.e. requirements
9, 10 and 11 were not satisfied). Hence, those
mechanisms were enhanced by the introduction of an
execution environment for CAA applications (later
called CAAEE) which was based on the system for
dynamic service integration described in (Dziubich
et al., 2012). The resulting structure of the deployed
system is presented in Figure 2.
The CAAEE environment consists of a base ser-
vices environment component, a context analysis
component, an action execution component and a
knowledge base component. The base services en-
vironment component communicates with custom
.NET applications (installed on user workstations)
which deliver context data. The data included a name
of a user that logged in (or logged out) to the work-
station associated with the endpoint (an association
was configured in the CUCM) and a current time.
It was then analyzed in the context analysis compo-
nent. Based on the analysis, a particular configura-
tion change was applied (through the action execu-
tion component of the CAAEE) to the telephony ob-
ject using the AXL (Administration XML) interface.
Based on the context-aware requirements there were
designed the following rules which were further im-
plemented in the CAAEE (each entry is in a form: a
situation - a necessary change in the configuration):
• a user has logged out from the workstation - make
a copy the CSS of the phone along with its parti-
tions and patterns belonging to the partitions, en-
able the Forced Authorization Code setting on the
patterns and set the new CSS on the phone; set the
idle URL on the phone,
• a user has passed a training on the CUCM and
gained a knowledge about the CUCM configura-
tion - change the user profile in the CUCM so that
the user can save configuration changes,
• a user has logged in to the workstation - change
the CSS of the phone to the one that contains par-
titions that don’t force an authorisation, (if exists)
delete the CSS forcing an authorization, unset the
idle URL, set a new line description, a presenta-
tion and a language settings.
The endpoints (Cisco 7965 IPPhones) sent their
IP address directly to the CUCM during registration.
Based on this information an appropriate Device Pool
was chosen. That allowed to adjust configuration
paramters for the endpoint according to its location
which was determined based on the IP address. Addi-
tionally, a current time was also analyzed internally
by the CUCM call routing process for each routed
call. That analysis was performed on a partition level
and enabled changes in the routing so that after work
hours all incoming calls were routed to a voice mail
or cell phones.
The use of CAAEE allowed to satisfy all the re-
quirements that were identified in the Table 2. Some
of them could be satisfied without that additional
PECCS2013-InternationalConferenceonPervasiveandEmbeddedComputingandCommunicationSystems
46

CAA Execution
Environment
(CAAEE)
Telephony system
Call routing layer
Application layer
Registry layer
Endpoints layer
Security, Safety, Quality
Phones (endpoints)
Applications
Context
data
C
o
n
f
i
g
u
r
a
t
i
o
n
ch
a
n
g
e
(
AX
L
)
Configuration
Context
data
Figure 2: The structure of the sample context-aware VoIP TS system.
component - particularly context-unaware require-
ments (with ids 1 - 6) as well as context-aware ones
for which the CUCM built-in mechanisms were suffi-
cient (requirements with ids 7 - 8). It is worth to men-
tion the latter regarded the call routing which is a real-
time task. It can be expected that the use of a context
during execution of those tasks can be limited only to
built-in mechanisms as the additional analysis of con-
text data can make them last unacceptably long. How-
ever, a configuration of those tasks (which doesn’t
have to be completed in a real-time) can successfuly
be enhanced with a context-awareness. Hence, the
CAAEE could be used for changing configuration of
telephony objects across all the layers from the lay-
ered model presented in Figure 1. A particular change
of the configuration needed to satisfy requirements
with ids 9, 10 and 11 took about 3 seconds (measured
from the time the situation appeared in the IS to the
time that the new configuration was sent through the
AXL interface). In case of the CUCM platform it is
also important that after some configuration changes
the endpoint has to be restarted. However, as those
changes are done rarely (login and logout from the
workstation) it wasn’t annoying for users.
7 CONCLUSIONS
The paper presents a new approach to designing (and
more generally deploying) and configuring context-
aware enterprise VoIP telephony systems. Thanks to
this approach a deployment process can be system-
ized and agile-oriented. To prove that the proposed
approach is useful there has been prepared a deploy-
ment based on a commercial VoIP telephony solu-
tion. The implementation showed that a VoIP TS can
be succesfully designed according to the presented
method and that a proposed mechanism of changing
a configuration based on the current context is useful
and feasable for users. For the sample deployment
there was used a currently available system for con-
text analysis and adaptaion action execution. It al-
lowed to dynamically change a configuration of par-
ticular telephony objects so that they behave more
convenient from the end user perspective (they adapt
to the current situation).
It is worth to mention that the proposed organiza-
tion of a design and a configuration processes signif-
icantly differ from those that are used currently. This
is because interactions between objects cannot be ex-
plicitly expressed within a configuration. They need
to be taken into account by designing an appropriate
contexts based on which a particular configuration is
chosen. That is why it may be more difficult to deploy
a VoIP system and test it before running in production.
A requirement for new supporting tools arises in this
area.
REFERENCES
Chihan, B., Bertin, E., Suprapto, I., Zimmermann, J., and
Crespi, N. (2012). Enhancing existing communication
services with context awareness. Journal of Computer
Networks and Communications.
Dziubich, T., Kaczmarek, P., and Nasiadka, S. (2012). A
ubiquitous system using semantic knowledge in dy-
namic service integration. In PECCS’12, 2nd Interna-
tional Conference on Pervasive Embedded Computing
and Communication Systems. SciTePress.
Johnston, A. B. (2009). SIP: Understanding the Session
Initiation Protocol. Artech House, 3rd edition.
Khalil, A. and Connelly, K. (2006). Context-aware tele-
phony: Privacy preferences and sharing patterns. In
CSCW’06, 20th anniversary conference on Computer
supported cooperative work.
Krawczyk, H. and Nasiadka, S. (2011). A new model for
context-aware applications analysis and design. In
UBICOMM’11, The Fifth International Conference
on Mobile Ubiquitous Computing, Systems, Services
and Technologies.
Pan, J., Tan, C. P., and Lee, W. T. (2003). Context-
aware service protocol. an extensible and configurable
framework for user context awareness services in per-
vasive computing systems. In WCNC’03, Wireless
Communications and Networking.
Raento, M., Oulasvirta, A., Petit, R., and Toivonen, H.
(2005). Contextphone: A prototyping platform for
DesignandConfigurationofContext-awareVoIPTelephonySystems
47

context-aware mobile applications. Pervasive Com-
puting.
Schilit, B. N., Hilbert, D. M., and Trevor, J. (2007).
Context-aware telecommunication services. Telecom-
munication Systems and Technologies.
Schmidt, A., Takaluoma, A., and Mntyjrvi, J. (2000).
Context-aware telephony over wap. Personal and
Ubiquitous Computing.
Tanenbaum, A. S. (2010). Computer Networks. Prentice
Hall PTR, 5th edition.
Verma, P. K. (2011). Voice Over IP Networks: Quality of
Service, Pricing and Security. Springer.
PECCS2013-InternationalConferenceonPervasiveandEmbeddedComputingandCommunicationSystems
48
