
A Strategy for Dynamic Controller Emulation in Packet-based
Networked Control
S. Falasca
1
, M. Gamba
1
, and A. Bicchi
1,2
1
Interdepartmental Research Center “E. Piaggio”, Via Diotisalvi 2, 56126 Pisa, Italy
2
Istituto Italiano di Tecnologia, Genova, Italy
Keywords:
Networked Control System, Packet-switching Networks, Model-based Control, Time-varying Delays.
Abstract:
The problem of the stabilisation of a nonlinear system via output-feedback dynamic control is addressed, under
the assumption that every communication between the plant and the controller is subject to network-induced
constraints. These constraints include variable transfer intervals; time varying, large communication delays;
non-simultaneous access to the network. A control technique that copes with these constraints is presented
which is based on recent results addressing the problem of static state-feedback. The stability of the resulting
nonlinear networked control system is assessed. Network-in-the-loop experiment results are presented, which
confirm that the proposed method is effective.
1 INTRODUCTION
The past decade has witnessed a dramatic growth in
interest for control over distributed networked archi-
tectures, which have the strong potential to increase
flexibility and scalability of a plant, while inducing
a remarkable reduction of costs for both installation
and maintenance. However, because of the use of
the network and because of the system being dis-
tributed, some problems arise: e.g. bandwidth limi-
tations, time-delays and packet losses, which cannot
be ignored in the control design. The state-of-the-art
is reported and discussed in (Heemels et al., 2010).
An essential aspect of many Networked Con-
trol Systems (NCS), such as those using Ethernet
as a communication layer, is that they organise data
transmission in packets. Such networks carry larger
amount of data with less predictable rates with respect
to circuit-switching communication channels. Pack-
etised transmissions substantially alters the band-
width/performance trade-off of traditional design.
The potentially large size of packet payload can be
exploited to reduce data transmissions without de-
grading the overall NCS performance. (Bemporad,
1998) pioneered the idea of sending feed-forward
control sequences computed in advance on the ba-
sis of a model-based predictive (MBP) scheme to the
aim of compensating for large delays in communica-
tion channels. The technique has been generalised to
address time-varying delays and transfer intervals in
(Polushin et al., 2008).
In (Greco et al., 2012) a control strategy (namely
Packet-Based Control) for stabilising an uncertain
nonlinear NCS affected by varying transmission in-
tervals, varying large delays, and constrained access
to the network is presented. A model of the plant is
used to build a prediction of the control law. Feedback
is provided by measuring the plant state. The state is
measured by distributed sensors. A network proto-
col is in charge of deciding which sensor node can
communicate at each instant. The control sequence
sent by the remote controller is stored in an embed-
ded memory on the plant side, a control command in
the sequence is chosen based on the time stamp con-
tained in the packet.
One major limitation of (Greco et al., 2012) is that
it only applies to static-feedback controllers. The sta-
bilisation of NCSs by means of dynamic controllers
has been considered in (Nesic and Liberzon, 2009)–
where it is addressed under the assumption of small
delays–and in (Polushin et al., 2008)–where the au-
thors solve the problem in the assumption that all
the plant state is sent simultaneously. In this paper
we aim at extending the Packet-Based Control to dy-
namic controllers, hence allowing for large delays and
non-simultaneous transmissions. Indeed, a direct ap-
plication of the aforementioned framework to the use
a dynamic controller would require updating the in-
ternal state of both the system model and the con-
troller by means of a protocol ensuring some nice
29
Falasca S., Gamba M. and Bicchi A..
A Strategy for Dynamic Controller Emulation in Packet-based Networked Control.
DOI: 10.5220/0004427100290038
In Proceedings of the 10th International Conference on Informatics in Control, Automation and Robotics (ICINCO-2013), pages 29-38
ISBN: 978-989-8565-71-6
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

error-decreasing properties.
We depart from the basic idea of updating the in-
ternal state of the dynamic controller in a way consis-
tent with the behavior it would have had if it were
directly connected to the plant. We then devise a
method which produces the same effects as having
a controller on the plant side which sends its inter-
nal state through the network towards the remote con-
troller, the same way the state of the plant is sent. We
consider the effects of our algorithm as virtual send-
ings. The only information we need to consistently
run the controller is the history of the inputs to the
controller. The virtual transmission of the controller
state is hence realised by sending the history of the
outputs of the plant and by using these outputs to feed
the remote controller. The output history can be sent–
again–by exploiting the large payload of packets. If
output sensors are distributed, outputs are partitioned
and the history of each sensor is sent according to a
static protocol similar to Round Robin. The draw-
back of the virtual sendings–especially in the case of
outputs partitioned over many nodes–is that a poten-
tially large delay on the arrival of the virtual packets
is introduced. Such a delay has to be directly taken
into account in the conditions ensuring the stability of
the overall system. We prove the exponential stabil-
ity of the NCS over a prescribed basin of attraction,
provided that some explicit bounds on the Maximum
Allowable Delay (MAD (Heemels et al., 2010)) and
on the Maximum Allowable Transfer Interval (MATI
(Walsh et al., 1999)) are satisfied. We finally apply
our technique to the control of a magnetic levitator
involving an output-feedback dynamic controller. It
will be shown that if the proposed technique is not
used, the network strongly affects the behavior of
the NCS. On the other hand, the presented algorithm
closely mimic the ideal closed-loop behavior; in ac-
cordance with the paradigm adopted i.e. the presence
of the network must be as transparent as possible to
the designer of the stabilising controller.
2 SYSTEM DESCRIPTION
In this section we provide the reader with all the char-
acteristics we assume the controller, the network and
the plant to have. Figure 1 shows the control archi-
tecture. The plant and the controller communicate
via a shared-bus communication network. An output-
feedback dynamic control law for the system is as-
sumed to be available. The plant is equipped with
network-enabled devices for actuation and sensing.
The sensors measure the internal state of the system
and its output. A protocol grants access to the net-
OSn
OSn
SSn
SSn
Plant Model
Dynamic control law
x
u
Controller
Shared Bus Network
Packet FIller
z
Local Dynamic
Dynamic
control law
x
y
z
Plant
y
Actuator Node
u
x
SSn
OSn
Compound Protocol
Figure 1: The proposed control architecture.
work to one node at a time. Output-measuring sensors
send the whole history of readings in tranches. State-
measuring sensors send the current reading each time
they are granted access to the network.
On the controller side, upon reception of output
data, the exact knowledge of the control law is ex-
ploited in order to infer a suitable value for the in-
ternal state of the controller at a given time. The
so computed internal state of the controller, together
with the received information about the internal state
of the plant, is used to initialise a model for the ideal
closed loop composed by a model for the plant dy-
namics and the control law. By means of simulating
the ideal closed loop behavior, a sequence of control
actions is computed, which is intended to be used in
the future. The control actions are then sent to the
plant; they will be received on the actuator side and
used appropriately.
2.1 The Plant and the Controller
We address the stabilisation of a nonlinear
continuous-time system of the form
˙x
p
= f
p
(x
p
,u) (1)
y = g
p
(x
p
), (2)
where x
p
:R
≥0
→R
n
p
is the plant state, y:R
≥0
→R
n
y
is the output, u : R
≥0
→R
n
u
represents the control in-
put, and f
p
: R
n
p
×R
n
u
→R
n
p
and g
p
: R
n
p
→R
n
y
de-
note locally Lipschitz functions. For this system, we
assume that a nominal dynamic feedback controller
of the form
˙x
c
= f
c
(x
c
,y) (3)
u = g
c
(x
c
,x
p
,y) (4)
ICINCO2013-10thInternationalConferenceonInformaticsinControl,AutomationandRobotics
30

is available. Here x
c
: R
≥0
→ R
n
c
is the controller
state, and f
c
: R
n
c
×R
n
y
→ R
n
c
and g
c
: R
n
c
×R
n
p
×
R
n
y
→R
n
u
denote locally Lipschitz functions. Letting
x(t) ,
x
T
p
(t),x
T
c
(t)
T
∈ R
n
p
+n
x
= R
n
and
f(x,u) ,
f
p
(x
p
,u)
f
c
(x
c
,g
p
(x
p
))
g(x) , g
c
(x
c
,x
p
,g
p
(x
p
)),
the closed-loop system (1)-(4) in the absence of net-
work effects simply reads
˙x = f(x,u) (5)
u = g(x). (6)
We assume that the nominal controller (3)-(4)
globally exponentially stabilises the plant (1)-(2) in
the absence of network effects.
Assumption 1 (. Nominal GES) The origin of the
system (1)-(2) in closed-loop with (3)-(4) is glob-
ally exponentially stable (GES), and there exists a
differentiable function V : R
n
→ R
≥0
and constants
α
,α,α,d > 0 such that the following conditions hold
for all x ∈R
n
αkxk
2
≤V(x) ≤ αkxk
2
∂V
∂x
(x) f(x, g(x)) ≤ −αkxk
2
∂V
∂x
(x)
≤ d kxk.
Local Lipschitz constants are assumed to be available
to the designer.
Assumption 2 (. Local Lipschitz) Given some con-
stants R
x
,R
u
> 0, there exist some constants λ
f
,λ
κ
>
0 and all u
1
,u
2
∈B
R
u
, the following inequalities hold
kf(x
1
,u
1
) − f(x
2
,u
2
)k ≤ λ
f
(kx
1
−x
2
k+ ku
1
−u
2
k)
(7)
kg(x
1
) −g(x
2
)k ≤ λ
κ
kx
1
−x
2
k. (8)
The control strategy analysed in this paper aims at
compensating the network-induced effects by relying
on a prediction of the plant behavior. To that aim, we
assume that a model for (1)-(2) is known:
˙
ˆx
p
=
ˆ
f
p
( ˆx
p
, ˆu) (9)
ˆy = ˆg
p
( ˆx
p
). (10)
This model in closed-loop with the nominal controller
(3)-(4) reads
˙
ˆx =
ˆ
f( ˆx, ˆu) (11)
ˆu = ˆg( ˆx), (12)
where ˆx , ( ˆx
T
p
, ˆx
T
c
)
T
: R
≥0
→ R
n
and
ˆ
f( ˆx, ˆu) ,
ˆ
f
p
( ˆx
p
, ˆu)
f
c
( ˆx
c
, ˆg
p
( ˆx
p
))
ˆg( ˆx) , g
c
( ˆx
c
, ˆx
p
ˆg
p
( ˆx
p
)).
The plant-model inaccuracy is assumed to be sector-
bounded.
Assumption 3 (. Sector-bounded Model Inaccuracy)
Given R
x
,R
u
> 0, there exists a constant λ
f
ˆ
f
≥ 0 such
that, for all x ∈ B
R
x
and all u ∈ B
R
u
,
f(x, u) −
ˆ
f(x, u)
≤ λ
f
ˆ
f
(kxk+ kuk). (13)
2.2 The Network
Measurements are taken by distributed sensors and
sent to the controller into packets. Sensors are as-
sumed to be synchronised with each other. We as-
sume that the measurement part of the network is par-
titioned in ℓ nodes and only a unique node at a time
can send its information (i.e. only partial knowledge
of the plant state is available at each time instant).
The controller is seen as a unique node. The over-
all state of the system x(t) ∈ R
n
is thus decomposed
in ℓ + 1 nodes as x(t) = [x
T
p,1
(t) , . . . ,x
T
p,ℓ
(t) , x
T
c
(t)]
T
with x
p,i
(t) ∈R
p
i
and
∑
ℓ
i=1
p
i
= n
p
.
Control sequences are sent as packets. An em-
bedded control device receives, decodes, synchro-
nises these packets and applies control commands to
the plant. We consider that measurements are taken
and sent at instants {τ
m
i
}, and are received by the
remote controller at instants {τ
m
i
+ T
m
i
}. In other
words, {T
m
i
} denotes the sequence of (possibly time-
varying) measurement data delays. Delays cover both
processing time and transmission delays on the mea-
surement chain. Similarly, control commands are sent
over the network at time instants {τ
c
i
}. They reach the
plant at instants {τ
c
i
+ T
c
i
}, where {T
c
i
} denotes the
sequence of delays accounting for both the computa-
tion time and the transmission delay from the remote
controller to the plant.
Assumption 4 (. Network) The communication net-
work satisfies the following properties:
i) (MATI) There exist two constants τ
m
,τ
c
∈ R
≥0
such that τ
m
i+1
−τ
m
i
≤ τ
m
and τ
c
i+1
−τ
c
i
≤ τ
c
, ∀i ∈
N;
ii) (mTI) There exist constants ε
m
,ε
c
∈R
≥0
such that
ε
m
≤ τ
m
i+1
−τ
m
i
andε
c
≤ τ
c
i+1
−τ
c
i
∀i ∈N.
iii) (MAD) There exist two constants T
m
,T
c
∈ R
≥0
such that T
m
i
≤ T
m
and T
c
i
≤ T
c
, ∀i ∈ N;
AStrategyforDynamicControllerEmulationinPacket-basedNetworkedControl
31

Table 1: The sequences {s
i
} and {o
i
} for ℓ
y
= 3.
s
0
o
0
o
1
o
2
s
1
o
3
o
4
o
5
s
2
...
0 1 2 3 4 5 6 7 8 ...
2.3 The Network Protocol
The use of a dynamic controller imposes a careful up-
date of the controller internal model in order to gener-
ate meaningfulcontrol sequences. We propose a strat-
egy that consists in transmitting the measurement his-
tory of each output nodes over a prescribed time hori-
zon, as well as the instantaneous value of the plant’s
state when access is granted to the network. The sys-
tem thus involves two different kinds of sensor nodes:
ℓ
y
output-sending nodes (OSn) and ℓ state-sending
nodes (SSn).
The access to the network is ruled by a protocol
choosing, at each instant τ
m
i
, which node communi-
cates its data. In order to limit the cumulated delays
induced by this approach, we assume that the nodes
are granted access to the network according to the
following rule: after each SSn access, all OSn are re-
quired to send their data according to a prescribed or-
dering (Round Robin). Then access is again granted
to a SSn, and so on. This rule can be formally stated
by extracting from the sequence of access times {τ
m
i
}
two subsequences
τ
m
o
i
and
τ
m
s
i
. More precisely,
we define two sequences {s
i
}, {o
i
} having values in
N. Such sequences have the following meaning: at
time τ
m
s
, s ∈ {s
i
} a SSn is granted access to the net-
work; at time τ
m
o
, o ∈ {o
i
} an OSn has the ability to
send. The policy is such that the two sequences ex-
hibit the following properties
a) {s
i
}∪{o
i
} = N, {s
i
}∩{o
i
} =
/
0;
b) s
i
= (ℓ
y
+ 1)i;
c) o
i
is strictly increasing.
Consider, as an example, ℓ
y
= 3; the sequences {s
i
}
and {o
i
} are shown in table 1.
We keep track of which OSn is granted access to
the network at a given time by means of the defini-
tion of the sequence {ν
i
} having values in [1, ℓ
y
] ⊂ N
defined as
ν
i+1
=
1+ ν
i
ifν
i
< ℓ
y
1 otherwise
(14)
and we consider ν
0
= 1 to express the fact that the
OSn number 1 sends first. The ν
i
−th OSn is thus
granted the access to the network at time τ
m
o
i
.
The SSn are granted access to the network accord-
ing to a protocol ruled by the map involving the error
e
p
(t) ∈ R
n
p
defined as e
p
(t) , ˆx
p
(t) −x
p
(t):
e
p
(τ
m
s
i
+
) = h
p
i,e
p
(τ
m
s
i
)
, ∀i ∈ N. (15)
where h
p
: N ×R
n
p
→ R
n
p
. This protocol is as-
sumed to induce an exponential decrease of the error
e
p
when the inter-sample dynamics are neglected; i.e.
we are interested in UGES protocols. We recall here
a slightly modified version of the definition in (Nesic
and Teel, 2004) as given in (Greco et al., 2012).
Definition 1. A function h : N ×R
n
→ R
n
is said to
be an UGES protocol having parameters a
,a,ρ, c if
there exists a functionW : N ×R
n
→R
≥0
locally Lip-
schitz in its second argument and there exist constants
a
,a > 0;c > a and ρ ∈ [0, 1) such that the following
conditions hold for the auxiliary discrete time system
ξ(i+ 1) = h(i, ξ(i)):
a
kξk ≤W (i,ξ) ≤ a kξk
W (i+ 1, h(i, ξ)) ≤ ρW (i,ξ)
(16)
for all ξ ∈ R
n
and all i ∈ N, and
∂W
∂ξ
(i,ξ)
≤ c (17)
for almost all ξ ∈R
n
and all i ∈ N.
Assumption 5. The protocol (15) is UGES with pa-
rameters a
p
,a
p
,ρ
p
,c
p
.
Remark 1. The UGES class is often used in the net-
work control literature. Although it might seem to
be very conservative, it has to be stressed out that
it is not. Indeed, no limits are being posed on the
rate of convergence of the error. The network pro-
tocol is used as a control-oriented description of the
effects of the sending order (which is not necessarily
pre-defined). UGES network protocols which are of-
ten used in practice are the Round Robin and the so
called Try Once Discard.
3 ALGORITHM DESCRIPTION
The algorithm we propose can be decomposed in dif-
ferent modules. At the plant side of the network,
three kinds of devices are needed, namely the actuator
node, the state-sending node and the output-sending
node. The controller is divided into two modules: the
first one–namely Local Dynamics–is in chargeof con-
verting the output data it receives from the plant into
information about the internal state the controller is
supposed to have; the second one has state-related in-
formation as an input (either received from the net-
work or produced by the Local Dynamics); based on
its input it computes the controls to be sent to the ac-
tuator node.
In this section we describe the behavior of each
module and provide a model for the overall closed-
loop system.
ICINCO2013-10thInternationalConferenceonInformaticsinControl,AutomationandRobotics
32

3.1 The Plant
3.1.1 Actuator Node
Such node is in charge of receiving, decoding and
re-synchronise packets sent by the controller. Each
received packet contains a timestamp and a certain
number of control values which are stored in a local
buffer. Upon choosing which one of the control val-
ues is the most appropriate, it actuates the plant. More
precisely, the actuator node compares the timestamp
of the last packet it received with its internal clock
and moves within the control sequence it received up
to the corresponding starting point.
3.1.2 State-sensor Node
When such a node is granted access to the network
(see section 2.3 for a description of the policy used to
take this decision), it encodes the sensed values into
a network packet, timestamps it and sends it to the
controller.
3.1.3 Output-sensor Node
An output-sensor node continuously monitors the
sensed outputs, storing the readings into a buffer. The
buffer content is timestamped and encoded into pack-
ets sent to the controller when the network is avail-
able. Upon sending, data is discarded. The sending of
tranches of data is consistent with how control data is
sent in (Greco et al., 2012). Figure 2 shows an exam-
ple of the sendings carried out by the output-sensor
nodes.
-
t
y
1
τ
m
o
0
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
y
2
y
3
-
t
y
1
τ
m
o
0
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
y
2
τ
m
o
1
.
.
.
.
.
.
.
.
.
.
y
3
-
t
y
1
τ
m
o
0
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
y
2
τ
m
o
1
.
.
.
.
.
.
.
.
.
.
y
3
τ
m
o
2
.
.
.
.
.
-
t
y
1
τ
m
o
0
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
τ
m
o
3
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
y
2
τ
m
o
1
.
.
.
.
.
.
.
.
.
.
y
3
τ
m
o
2
.
.
.
.
.
-
t
y
1
τ
m
o
0
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
τ
m
o
3
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
y
2
τ
m
o
1
.
.
.
.
.
.
.
.
.
.
τ
m
o
4
.
.
.
.
.
.
.
.
.
.
y
3
τ
m
o
2
.
.
.
.
.
-
t
y
1
τ
m
o
0
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
τ
m
o
3
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
y
2
τ
m
o
1
.
.
.
.
.
.
.
.
.
.
τ
m
o
4
.
.
.
.
.
.
.
.
.
.
y
3
τ
m
o
2
.
.
.
.
.
τ
m
o
5
.
.
.
.
.
Figure 2: Example of OSn sendings for ℓ
y
= 3.
Remark 2. It is tacitly assumed that the effects of
sending discrete-time values instead of continuous
function to the controller and to the actuator node can
be neglected.
3.2 The Controller
3.2.1 Local Dynamics
By exploiting output readings it is possible to mathe-
matically consider the controller as being executed on
the plant side and sending its internal state over the
network. We will define the sequence of time-instants
at which such virtual-sendings happen and the delay
each of these packets incurs into. Finally, we will use
such virtual packets, together with the state packets,
in order to design an overall UGES protocol acting on
the complete system as expressed in (5).
First of all, we need give some definitions.
Definition 2. Given T ∈ R
≥0
, we will say that y
[0,τ]l
is known at time τ + T if there exist j ∈ {o
i
},k ∈ N
such that:
a) τ
m
j
≥ τ, τ
m
j
+ T
m
j
≤ τ+ T;
b) o
k
= j, ν
k
= l.
Moreover, we will say that y
[0,τ]
is known at time
τ+ T if ∀l ∈ [1, ℓ
y
] ⊂ N we have that y
[0,τ]l
is known
at time τ+ T.
This definition reflects the natural notion of the
controller having already received a packet related to
y
l
which was sent no later than time τ.
Definition 3. Given T ∈ R
≥0
, we will say that x
c
(τ) is
known at time τ + T if either τ = 0 or y
[0,τ]
is known
to the controller at time τ + T .
This definition formalises the fact that given σ such
that x
c
(σ) is known at time τ + T , it is possible to
use the solution for the differential equation φ
[σ,τ]
f
c
:
[σ,τ]×[σ,τ]×R
n
c
×R
n
y
[σ,τ]
→R
n
c
in order to compute
x(τ), since
x
c
(τ) = φ
[σ,τ]
f
c
τ,σ,x
c
(σ), y
[σ,τ]
(18)
With the previous definitions in mind we can state the
following.
Proposition 4 (. Virtual Packets) Given i ≥ℓ
y
−1,i∈
N the value x
c
τ
m
o
(
i−(ℓ
y
−1)
)
is known at time
τ
m
o
(
i−(ℓ
y
−1)
)
+ ℓ
y
τ
m
+ T
m
.
This means that we can consider that at time
τ
m
o
(
i−(ℓ
y
−1)
)
a packet containing x
c
τ
m
o
(
i−(ℓ
y
−1)
)
is sent
by the plant; such a virtual packet incurs a delay
which is no longer than ℓ
y
τ
m
+ T
m
.
We will consider those virtual packets in conjunc-
tion with the packets containing x
s
(τ
m
s
i
), which arrive
at the controller at time τ
m
s
i
+ T
m
s
i
. The sequence of
time instants at which such packets are sent is {τ
m
i
}.
As for the delays, we define a new sequence
n
T
f
i
o
.
Definition 5 (. Sequence of State-sending Delays)
The sequence of state-sending delays
n
T
f
i
o
, T
f
i
∈ R
≥0
such that:
T
f
i
=
(
T
m
i
if∃k : i = s
k
min
n
K
τ
m
i
o
otherwise
(19)
AStrategyforDynamicControllerEmulationinPacket-basedNetworkedControl
33

where
K
τ
, {T : x
c
(τ) is known at timeτ+ T}. (20)
By virtue of Proposition 4, the following inequal-
ity holds:
T
f
i
≤ ℓ
y
τ
m
+ T
m
= T
f
. (21)
From now on we will consider the packets con-
taining the state of the system and the virtual packets
containing the state of the controller. The information
they gather will be used in order to design a proto-
col which acts on the error e(t) = (e
T
p
(t), e
T
c
(t))
T
,
ˆx(t) −x(t), where e
c
(t) ∈ R
n
c
: e
c
(t) , ˆx
c
(t) −x
c
(t).
We will show that, provided that an UGES protocol
acting on e
p
is in use (see Assumption 5), the de-
signed protocol is UGES.
Proposition 6 (. Compound Protocol) The function
h : N ×R
n
→ R
n
i,
ξ
T
p
,ξ
T
c
T
7→
h
p
(k, ξ
p
) if∃k : s
k
= i
ξ
p
otherwise
ξ
c
if∃k : s
k
= i
0 ∈ R
n
c
otherwise
(22)
defines an UGES protocol. Here ξ
p
∈R
n
p
,ξ
c
∈ R
n
c
.
3.2.2 Computing the Control Law
When a new measurement is received, the remote
controller uses the new data in order to update an es-
timate of the internal state of the plant. The controller
then computes a prediction of the control signal over
a fixed time horizon
T
p
0
≥ T
c
+ T
f
+ τ
m
+ τ
c
(23)
by numerically running the model (11)-(12). Such
computation generates values for the function ˆu(t)
(cf. equation (12)) which are then coded, marked with
the appropriate timestamp, and put in a single packet
which is sent at the next network access .
3.3 The Overall Model
The loop composed of the system (1)-(2) and the con-
troller node which executes the algorithms described
in Section 3.2 can be modelled by means of the fol-
lowing equations (see also (Greco et al., 2012)).
The NCS model has a state x(t) which models the
internal state of the plant as well as the state of the
controller as it would act if it were connected to the
outputs of the plant. Moreover, N vectors of addi-
tional state variables are used for modelling the esti-
mations of the vector ˆx. N represents the number of
packets, either real or virtual, that can be received by
the controller during the time T
p
0
. It is defined as
N ,
T
p
0
−τ
m
ε
m
+ 1. (24)
By means of the definition of ¯x(t), ˜x(t),e(t) ∈
R
Nn
defined as ¯x(t) ,
x
T
(t), . . . ,x
T
(t)
T
and e(t) ,
e
T
1
(t), . . . ,e
T
N
(t)
T
, e
i
(t) ∈ R
n
, the closed-loop dy-
namics of the NCS can be compactly written as
˙x = F(t, ¯x,e) (25a)
˙e = G(t, ¯x, e) (25b)
e(τ
m+
i
) = H(i,e(τ
m
i
)), (25c)
where
F(t, ¯x, e) = f(x, υ(t,e+ ¯x)) (26a)
G(t, ¯x, e) =
ˆ
f(e
1
+ x, ˆg(e
1
+ x)) − f (x, υ(t, e+ ¯x))
.
.
.
ˆ
f(e
N
+ x, ˆg(e
N
+ x)) − f (x, υ(t, e+ ¯x))
(26b)
H(i,e) =
e
1
+ (h(i,e
N
) −e
1
)η(i, 1)
e
2
+ (h(i,e
1
) −e
2
)η(i, 2)
.
.
.
e
N
+ (h(i,e
N−1
) −e
N
)η(i,N)
, (26c)
where η : N ×{1, . . . , N}→{0, 1}identifies the index
of the relevant state estimate
η(i,r) ,
1 if µ(i) = r
0 otherwise
(27)
and µ : N → {1,...,N} is defined as
µ(i) , ((i−1)modN) + 1 . (28)
The control signal υ in (26a) and (26b) is defined as
υ : R
≥0
×R
Nn
→ R
n
u
,
(t,
ξ
T
1
,... , ξ
T
N
T
) 7→
N
∑
k=1
ˆg(ξ
k
)ζ(t, k) (29)
where ξ
i
∈ R
n
and ζ : R
≥0
×{1, . . . , N} → {0, 1} is
the map
(t, k) 7→
1
if ∃j ∈ N s.t. µ(γ( j)) = k and
t ∈ (τ
c
j
+ T
c
j
,τ
c
j+1
+ T
c
j+1
]
0 otherwise
(30)
and γ : N → N
j 7→ max
n
i ∈ N | τ
m
i
+ T
f
i
< τ
c
j
o
(31)
denotes the index of the latest measurement received
before τ
c
j
.
ICINCO2013-10thInternationalConferenceonInformaticsinControl,AutomationandRobotics
34
4 MAIN RESULT
Theorem 7. Assume that assumptions 1, 4, 5 hold.
Given some R > 0, fix R
x
= R and R
u
= λ
k
R and sup-
pose that assumptions 2 and 3 hold with these con-
stants. Let a
p
,
a
p
,ρ
p
,c
p
α, α,α,d,λ
f
ˆ
f
,λ
f
and λ
k
be
generated by these assumptions. Pick
a
= a
p
ρ
p
,
a = a
p
, ρ = ρ
p
1
ℓ
y
+1
, c = c
p
(32)
and define a
H
,
a,
a
L
,
a ifN = 1
a
N
min
1,
a
a
2
1
ρ
otherwhise
. (33)
Assume that the following conditions on
τ
m
,T
f
,τ
c
,T
c
,ε
m
hold:
τ
m
∈[ε
m
,τ
m
∗
), τ
m
∗
,
1
L
log
Hγ
2
+a
L
L
Hγ
2
+a
L
ρL
N =
l
T
c
+T
f
+τ
c
ε
m
m
+ 1
(34)
where
L ,
c
a
L
(1+ λ
k
)
√
Nλ
f
ˆ
f
+
√
Nλ
f
+
√
N −1+ N −1
λ
f
λ
k
M , (1+ λ
k
)cNλ
f
ˆ
f
γ
2
,
d
α
q
a
a
λ
f
λ
k
. (35)
Then the origin of the NCS (25) is exponentially stable
with radius of attraction
˜
R ,
R
K
(36)
where K ,
√
2
1−γ
1
γ
2
max{(1+ γ
1
)k
2
,(1+ γ
2
)k
1
}, γ
1
,
exp(Lτ
m
)−1
a
l
L(1−ρexp(Lτ
m
))
H, k
1
,
a
H
ρa
L
and k
2
,
q
α
α
.
Conditions expressed in (34) establish a re-
lation between the relevant parameters, namely
ε
m
,T
c
,T
f
,τ
c
and τ
m
. Notice that (21) can be used to
express such a relation in terms of T
m
and ℓ
y
instead
of T
f
. Note that since Theorem 7 guarantees only
local properties, Assumption 1 could be relaxed to lo-
cal exponential stability of the nominal plant, over a
sufficiently large domain.
Remark 3. The presented formulation of the MATI
and the expression for the radius of convergence are
based on (Greco et al., 2012) where examples show-
ing that the MATI constitutes an improvement over the
previously existing state-of-the-art can be found. It is
easily seen that due to the high number of variables
involved in the presented expressions, it is impractical
to actually compute the MATI and the radius of con-
vergence for a real plant. In fact, the same can be said
for most of the similar results which can be found in
literature. In this case the presented theorem can be
seen as an existence result: it assesses that it is pos-
sible to stabilise the system by means of the presented
architecture.
5 NETWORK-IN-THE-LOOP
EXPERIMENTS
In this section, we provide results of the experiments
carried out for the networked control of a magnetic
levitator. The setup uses two computers, one for the
controller and the other for simulating the plant with
sensors and actuators. The computers are connected
through a real Ethernet link. The experimental net-
work setup is such that
1×10
−3
[s] ≤ τ
m
i+1
−τ
m
i
≤ 5×10
−3
[s]
1×10
−3
[s] ≤ τ
c
i+1
−τ
c
i
≤ 5×10
−3
[s]
. (37)
Figure 3 shows the measured round-trip time. Based
on the measurements, we can consider the maximum
delays
1
to be T
m
,T
c
=
maxRTT
2
≈26×10
−3
[s].
The experiments have been carried out by means
of a software for networked control systems based on
the one presented in (Falasca et al., 2010) which al-
lows for network-in-the-loop tests to be carried. For
this purpose a module implementing the local dy-
namic algorithm has been designed.
25
30
35
40
45
50
55
0 5000 10000 15000 20000
RTT [ms]
Time 10
-3
[s]
Figure 3: Round Trip Time.
˙x =
x
2
sin(α)g−
c
m
x
3
x
1
2
−
R
L
x
3
+
2c
L
x
2
x
3
x
2
1
+
1
L
u
y = x
1
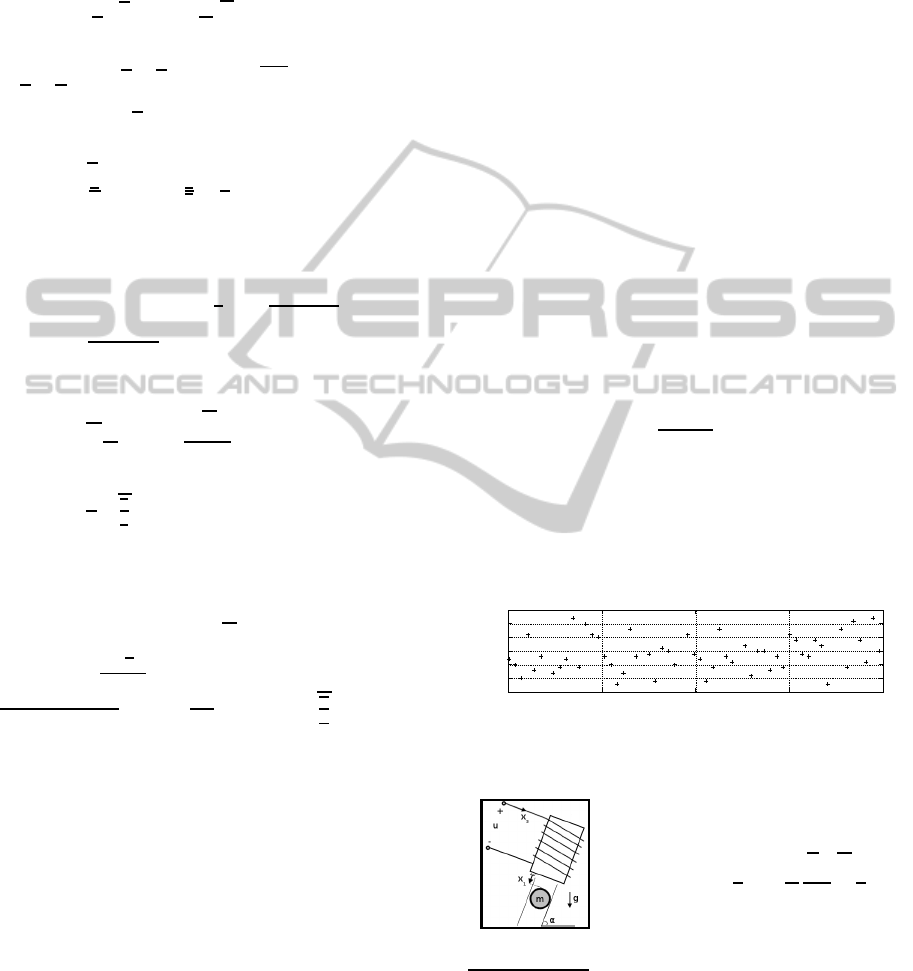
Figure 4: Magnetic levitator and its model
1
The measurements include both the network-induced
delays and some additional delays which have been added
via software in order to simulate the effects of additional
traffic. The program
tc
has been used on both
Linux
hosts
to provide additional sending delays, which have a normal
probability distribution of N (15,5). Hence, the mean value
of the added round trip time is 30ms. Additional delays
account for the larger portion of the overall measured delay.
AStrategyforDynamicControllerEmulationinPacket-basedNetworkedControl
35

The plant parameters (equations are shown in Fig-
ure 4) are α =
π
6
, g = 9.8
h
m
s
2
i
, m = 0.05[Kg], c =
0.5[Hm], L = 1[H] , R = 10[Ω].
Following the philosophy of section 2.1, we as-
sume that a stabilising controller is given for the nom-
inal plant. In our case, the nominal controller is the
result of the straightforward application of numeri-
cal self-tuning routines in Matlab, and has the transfer
function:
C(s) = −
a
2
s
2
+ a
1
s+ a
0
s
2
(s+ b)
(38)
where a
2
= 1418,a
1
= 767, a
0
= 377 and b = 29.
The plant model used in the controlling computer,
is subject to parametric uncertainties. The parame-
ters for the model it uses are very different from the
real ones, i.e. α =
π
2
, g = 9.8
h
m
s
2
i
, m = 1[Kg] , c =
1[Hm], L = 5[H], R = 0.1[Ω]
Figure 5 shows the results of the experiments for
a reference signal x
d
= 0.05[m]. One of the trajec-
tories shows the behavior of the ideal closed-loop;
the second one shows the networked system. Finally,
the behavior of the networked system when the al-
gorithm taking into account local dynamics (cf. sec-
tion 3.2.1) is not used is shown, i.e. the protocol
h : N ×R
n
→ R
n
i,
ξ
T
p
,ξ
T
c
T
7→
h
p
(k, ξ
p
) if∃k : s
k
= i
ξ
p
otherwise
ξ
c
is used. Experiments show that the proposed algo-
rithm manages to produce results resembling the ideal
closed loop behavior. If the proposed algorithm is
not used, the behavior is altered; for instance–for the
given example–the steady state error is not zero.
0.04
0.05
0.06
0.07
0.08
0.09
0.1
0.11
0 5000 10000 15000 20000 25000 30000
Position [m]
Time 10
-3
[s]
Networked
Networked: no local dynamics
Ideal closed loop
0.047
0.05
0.053
5000 10000 15000 20000 25000 30000
Figure 5: Trajectory x
1
p
(t).
The PBC approach has been experimented with
on a real plant, namely a Furuta Pendulum in (Fabbri
et al., 2013). Those experiments assess the real-world
applicability of the approach and give a comparison
on the issues encountered in implementing the PBC
control scheme and the classical local control.
6 PROOFS
We start by giving a proof for Proposition 4.
Proof 1 (. Virtual Packets) Pick i ∈ N,i ≥ ℓ
y
−1 and
assume that x
c
(τ
m
o
i−(ℓ
y
−1)
) is not known at time T =
τ
m
o
i−(ℓ
y
−1)
+ ℓ
y
τ
m
+ T
m
. Then there exists l ∈ [1,ℓ
y
] :
y
0,τ
m
o
i−(ℓ
y
−1)
l
is not known at time T. It follows
that ν
i−(ℓ
y
−1)
6= l and that there exists j < ℓ
y
:
ν
i−(ℓ
y
−1)+ j
= l. Hence y
h
0,ν
i−(ℓ
y
−1)+ j
i
l
is known at
time τ
m
o
i−(ℓ
y
−1)+ j
+ T
m
o
i−(ℓ
y
−1)+ j
. But since τ
m
o
i−(ℓ
y
−1)+ j
+
T
m
o
i−(ℓ
y
−1)+ j
≤ τ
m
o
i−(ℓ
y
−1)+ j
+ T
m
≤ τ
m
o
i−(ℓ
y
−1)
+ jτ
m
+
T
m
≤τ
m
o
i−(ℓ
y
−1)
+ℓ
y
τ
m
+T
m
= T we can conclude that
y
h
0,ν
i−(ℓ
y
−1)+ j
i
l
is known at time T; which is an absurd.
In order to prove Proposition 6 we need to state some
preliminary results.
Lemma 8 (. Sum of Protocols) Given two UGES pro-
tocols h
s
: N ×R
n
s
→ R
n
s
and h
p
: N ×R
n
p
→ R
n
p
with relative constants and functions as contained in
Definition 1, distinguished by the subscript s and p,
let define e ,
s
T
, p
T
T
, with s ∈ R
n
s
, p ∈ R
n
p
. The
protocol:
h(i,e) ,
h
s
(i,s)
h
p
(i, p)
(39)
is UGES with parameters a
= min
a
p
,a
s
,
a =
max{a
s
,a
p
}, ρ = max{ρ
s
,ρ
p
} and c = max{c
s
,c
p
}.
Proof 2. With the parameters defined in the lemma
and the Definition 1 in mind, we define the function
W : N ×R
(n
s
+n
p
)
→ R
≥0
as
W(i, e) =
q
W
s
(i,s)
2
+W
p
(i, p)
2
(40)
Hence
a
2
kek
2
= a
2
ksk
2
+ kpk
2
≤W(i, e)
2
≤
a
2
ksk
2
+ kpk
2
=
a
2
kek
2
W (i+ 1, h(i, e))
2
≤ ρ
2
W
s
(i,s)
2
+W
p
(i, p)
2
.
ICINCO2013-10thInternationalConferenceonInformaticsinControl,AutomationandRobotics
36

Furthermore
∂W
∂e
=
1
W
W
s
∂W
s
∂s
, W
p
∂W
p
∂p
=
1
W
s
W
s
∂W
s
∂s
2
+
W
p
∂W
p
∂p
2
≤
1
W
q
W
2
s
c
2
s
+W
2
p
c
2
p
≤
c
W
q
W
2
s
+W
2
p
= c,
by means of which the theorem is proven.
Lemma 9 (. N-dilation of a Protocol) Let us con-
sider a UGES protocol h : N × R
n
→ R
n
and a
not-decreasing surjective function k : N → N, the
protocol defined as:
h
D
(i, e) =
h(k(i), e) if k(i+ 1) 6= k(i)
e otherwise
(41)
is UGES, provided that ∃
ι : k(i) 6= k(i + ι)∀i. In par-
ticular, if h is UGES with parameters a
,a,ρ, c , h
D
is
UGES with parameters ρα
,α, ρ
1
ι
and c.
Proof 3. Given the function W associated with the
UGES protocol h, we define a function W
D
W
D
(0,e) = W(0, e)
W
D
(i+ 1, e) =
W(k(i+ 1), e) if k(i+ 1) 6= k(i)
ρ
1
ι
W
D
(i,e) otherwise
(42)
The following conditions hold:
ρa
kek ≤W
D
(i,e) ≤ akek.
Furthermore, when k(i+ 1) = k(i)
W
D
(i+ 1, h
D
(i,e)) ≤ ρ
1
ι
W
D
(i,e).
Consider now the case k(i+1) 6= k(i). Take n ≤
ι : k(i) =
k(i−n+ 1) 6= k(i−n). We have:
W
D
(i−n + 1,e) = W (k(i−n + 1), e) (43)
and
W
D
(i, e) = ρ
n−1
ι
W (k(i), e) ≥ ρ
ι−1
ι
W (k(i) , e) . (44)
Therefore:
ρW (k(i), e) ≤ ρ
1
ι
W
D
(i,e). (45)
We can then write W
D
(i+ 1, h
D
(i,e)) =
W (k(i+ 1),h(k(i) , e)) ≤ρW (k(i) , e) ≤ρ
1
ι
W
D
(i,e).
Since ρ < 1, it is apparent from the very definition of
W
D
that
∂W(i, e)
∂e
≤ c ⇒
∂W
D
(i,e)
∂e
≤ c,
which concludes the proof.
We can now give a proof for Proposition 6.
Proof 4. Define
h
Dp
(i,e
p
) =
h
p
(k, e
p
) if ∃k : s
k
= i
e
p
otherwise
(46)
it is easily seen that h
Dp
can be obtained by applying
Lemma 9 to the protocol h
p
(i,e
p
) by defining
k
p
(i+ 1) =
k
p
(i) + 1 if ∃k : s
k
= i
k
p
(i) otherwise
, (47)
k
p
(0) = 0. From the definition of s
i
, it follows that
k
p
(i + ℓ
y
+ 1) 6= k
p
(i)∀i ∈ N. Hence h
Dp
(i,e
p
) is
UGES with parameters a
Dp
= a
p
ρ
p
,
a
Dp
= a
p
, ρ
Dp
=
ρ
1
ℓ
y
+1
p
and c
Dp
= c
p
.
Define now h
c
(i,e
c
) = 0, which is an UGES pro-
tocol having parameters a
c
=
a
c
= c
c
= a
p
and ρ
c
=
ρ
p
2
. If we define
h
Dc
(i,e
c
) =
e
c
if ∃k : s
k
= i
0 otherwise
(48)
it is easily seen that h
Dc
can be obtained by applying
Lemma 9 to the protocol h
c
(i,e
c
) by defining
k
c
(i+ 1) =
k
c
(i) if ∃k : s
k
= i
k
c
(i) + 1 otherwise
, (49)
k
c
(0) = 0. From the definition of o
i
and s
i
, it follows
that k
c
(i+2) 6= k
c
(i)∀i ∈N. Hence h
Dc
(i,e
c
) is UGES
with parameters a
Dc
= a
p
ρ
p
,
a
Dc
= a
p
, ρ
Dc
= ρ
1
2
p
and
c
Dc
= a
p
.
Now, the protocol in Proposition 6 can be ob-
tained by applying Lemma 8 to the protocols h
Dp
and
h
Dc
, hence it is UGES with parameters a
= a
p
ρ
p
,
a = a
p
, ρ = ρ
1
ℓ
y
+1
p
and c = c
p
.
In order to prove Theorem 7, we are now going to
invoke theorem 1 from (Greco et al., 2012). The as-
sumption on the network made there are satisfied by
means of (21) which follows from our Assumption 4
in conjunction with the definition of the sequence of
state-sending times and delays. The assumption re-
garding the protocol being UGES is here satisfied by
means of Proposition 6. The ideal closed-loop system
has the nominal GES property, as stated in Assump-
tion 1. Moreover, Assumptions 2 and 3 are the same
required in (Greco et al., 2012).
Theorem 7 is a rewriting of Theorem 1 in (Greco
et al., 2012) in terms of the quantities involved in the
writing of system (25).
2
The function W
c
(i, e
c
) = a
c
ke
c
k can be used to show
this.
AStrategyforDynamicControllerEmulationinPacket-basedNetworkedControl
37

7 CONCLUSIONS
The networked stabilisation of a nonlinear plant via
an output-feedback dynamic controller has been con-
sidered. An algorithm is proposed which exploits
the packet-based nature of the considered network.
Sufficient condition for the local exponential stabil-
ity of the resulting system are given. The stabilisation
of a magnetic levitator is presented as an example.
Network-in-the loop experiment results show that the
resulting network controlled system closely mimics
the behavior of the ideal closed-loop system. If–on
the contrary–the proposed algorithm is not used, the
network is shown to strongly affect the behavior of
the controlled system.
ACKNOWLEDGEMENTS
The research leading to these results has re-
ceived funding from the European Union Seventh
Framework Programme [FP7/2007-2013] under grant
agreement n257462 HYCON2 Network of excel-
lence”
REFERENCES
Bemporad, A. (1998). Predictive control of teleoperated
constrained systems with unbounded communication
delays. In Proc. IEEE Int. Conf. on Decision and Con-
trol, volume 2, pages 2133–2138, Tampa, FL, USA.
Fabbri, T., Fenucci, D., Falasca, S., Gamba, M., and Bicchi,
A. (2013). Packet-based dynamic control of a furuta
pendulum over ethernet. Proc. IEEE Mediterranean
Conference on Control.
Falasca, S., Belsito, C., Quagli, A., and Bicchi, A. (2010).
A Modular and Layered Cosimulator for Networked
Control Systems. Proc. IEEE Mediterranean Confer-
ence on Control.
Greco, L., Chaillet, A., and Bicchi, A. (2012). Exploiting
packet size in uncertain nonlinear networked control
systems. Automatica, 48:2801–2811.
Heemels, W. P. M. H., Teel, A. R., van de Wouw, N.,
and Neˇsi´c, D. (2010). Networked control systems
with communication constraints: Tradeoffs between
transmission intervals, delays and performance. IEEE
Trans. on Automat. Contr., 55(8):1781–1796.
Nesic, D. and Liberzon, D. (2009). A unified framework for
design and analysis of networked and quantized con-
trol systems. Automatic Control, IEEE Transactions
on, 54(4):732 –747.
Nesic, D. and Teel, A. (2004). Input-output stability proper-
ties of networked control systems. Automatic Control,
IEEE Transactions on, 49(10):1650 – 1667.
Polushin, I. G., Liu, P. X., and Lung, C.-H. (2008). On the
model-based approach to nonlinear networked control
systems. Automatica, 44(9):2409–2414.
Walsh, G. C., Ye, H., and Bushnell, L. (1999). Stability
analysis of networked control systems. In Proc. Amer-
ican Control Conf.
ICINCO2013-10thInternationalConferenceonInformaticsinControl,AutomationandRobotics
38
