
Improving Block Cipher Design by Rearranging Internal Operations
Liran Lerman, Jorge Nakahara Jr. and Nikita Veshchikov
Universit´e Libre de Bruxelles (ULB), Dept. d’Informatique, Brussels, Belgium
Keywords:
Block Cipher Design, Security And Performance Analysis, Rearranging Internal Operations.
Abstract:
This paper discusses the impact of a simple strategy in block cipher design: rearranging the internal cipher
components. We report on a test case in which we observed a significant upgrade on a cipher’s security.
We applied this approach in practice and report on an updated design of the IDEA block cipher, in which
we swapped all exclusive-or operations for multiplications. The consequences of these modifications are far
reaching: there are no more weak multiplicative subkeys (because multiplications are not keyed anymore)
and overall diffusion improves sharply in the encryption framework. The unkeyed multiplication is novel in
itself since it did not exist in IDEA as a primitive operation and it alone guarantees stronger diffusion than the
exclusive-or operation. Moreover, our analysis so far indicate that the new cipher resists better than IDEA and
AES against old and new attacks such as the recent biclique technique and the combined Biryukov-Demirci
meet-in-the-middle attack. Experiments on an 8-bit microcontroller indicate the new design has about the
same performance as IDEA. A theoretical analysis also suggests the new design is more resistant to power
analysis than IDEA.
1 INTRODUCTION
The main motivation for this research came from a
simple question: how the order of internal cipher
components affects its security? Our investigations
shed some light on (undocumented) design decisions
that are not always provided with every announce-
ment of new cryptographic primitives.
Previous work includes reordering the S-boxes in
the DES cipher (Matsui, 1995). The conclusions were
that some S-box orderings, in fact, would consider-
ably weaken the security against differential and lin-
ear cryptanalysis. This means that the order of S-
boxes could serve as a potential trapdoor. Therefore,
not only the cipher components are relevant for secu-
rity, but also the order in which they are applied.
As a concrete instantiation, we analysed what hap-
pens in the International Data Encryption Algorithm
(IDEA) (Lai et al., 1991) block cipher if the exclusive-
or and modular multiplication were swapped. This
modified design might be of independent theoretical
interest.
In (Borisov et al., 2002), Borisov et al. described
a modified IDEA cipher in which some ⊕ opera-
tions were swapped with ⊞. This modified cipher
was called IDEA-X. The objective was to have an ap-
propriate target for their multiplicative-differential at-
tack, since this attack did not affect IDEA. In (Naka-
haraJr, 2009), Nakahara studied different reorderings
of the four round transformations in AES, but no se-
curity threat was detected compared to the original
ordering in the AES. IDEA was released before the
NIST competition for the Advanced Encryption Stan-
dard (AES) (FIPS197, 2001). Even nowadays, there
are still novel analyses (Biham et al., 1417; Wei et al.,
2012) against IDEA. IDEA provided a formidableand
challenging testing ground for all kinds of cryptan-
alytic techniques, already at a time when DES was
the prevailing benchmark. Nowadays, AES is the de
facto world standard. The recent biclique technique
effectively reach the full round versions of the AES,
IDEA and PRESENT ciphers (Bogdanov et al., 2011;
Khovratovich et al., 2012; Abed et al., 2012) with
(time) complexity less than exhaustive key search in
the single-key model. Also, Biham et al. (Biham
et al., 1417) independently attacked the full IDEA us-
ing the Biryukov-Demirci relation and a meet-in-the-
middle approach. Several other attacks also exploited
weaknesses in the key schedule such as (Biryukov
et al., 2002; Borst et al., 1997; Daemen et al., 1993;
Hawkes, 1998) to attack the encryption framework.
This paper is organizedas follows: Sect. 2 lists the
main contributions of this research; in Sect. 3 we con-
cretely instantiate our strategy of rearranging internal
cipher components. We apply this approach to the
IDEA block cipher; Sect. 4 motivates and describes a
27
Lerman L., Nakahara Jr J. and Veshchikov N..
Improving Block Cipher Design by Rearranging Internal Operations.
DOI: 10.5220/0004498200270038
In Proceedings of the 10th International Conference on Security and Cryptography (SECRYPT-2013), pages 27-38
ISBN: 978-989-8565-73-0
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

new key schedule; Sect. 5 provides security analyses;
Sect. 6 concludes the work.
2 CONTRIBUTIONS
The contributions of this work are manifold:
• the focus of this paper is to assess the conse-
quences of a simple design strategy: how the rear-
rangement of internal cipher components affects
its security (and performance). As an example,
we analysed what happens in the IDEA block ci-
pher if we swap all the exclusive-or (denoted ⊕)
and multiplication (denoted ⊙) operations. We
call the new design IDEA
∗
. This simple modi-
fication has not been reported before, which may
be of independent interest. In IDEA
∗
, subkeys are
no longer a mandatory input to the multiplication
operations, meaning that both inputs are variable.
IDEA
∗
also uses the unkeyed division operation,
denoted ⊡, so that a ⊡ b = a⊙b
−1
= a/b, where
a,b ∈ GF(2
16
+ 1). Therefore, if a table of multi-
plicative inverses is provided, a division costs one
multiplication plus a table look-up. Note that un-
like exclusive-or, a⊡b 6= b⊡ a, so the order of the
operands matters in ⊡. In the rest of this paper,
we discuss the many implications of swapping ⊕
by ⊙ in IDEA.
• IDEA
∗
employs the same three algebraic opera-
tions of IDEA which means application environ-
ments that already use IDEA can adopt IDEA
∗
without major changes in infrastructure. Conse-
quently, IDEA
∗
fits in the same legacy environ-
ments as used by IDEA, such as PGP/GPG, digital
rights management, video scrambling for pay-TV,
internet audio/video distribution, government and
corporate IT infrastructure protection.
• The unkeyed multiplication is a new primitive op-
eration and has a considerable impact: there are
no more weak multiplicative subkeys in IDEA
∗
regardless of the key schedule algorithm. More-
over,wordwise diffusionis stronger with multipli-
cation because of a wrap-around effect in compar-
ison to the bitwise diffusion in exclusive-or. This
fact is corroborated in Lai’s Low-High algorithm
(Lai, 1992) for multiplication in GF(2
16
+ 1).
Note that swapping ⊕with ⊞ would not eliminate
weak subkeys, as subkeys would still be a manda-
tory input to ⊙. This modified version was called
IDEA-X by Borisov et al. (Borisov et al., 2002).
They showed multiplicative differential attacks on
IDEA-X, which do not affect IDEA. Likewise,
swapping ⊞ for ⊙ would not work either, because
subkeys would still be input to ⊙ in the the first
half-rounds.
• We suggest an updated key schedule for IDEA
∗
with full key diffusion after the third generated
subkey, which makes each round equally strong,
since the subkeys quickly depend on all bits of the
user key. This design was borrowed from (Naka-
hara.Jr et al., 2003b) and effectively counters
meet-in-the-middle (MITM), related-key, slide
and advanced slide (among other) attacks. This
means that the encryption framework cannot be
purposefully weakened due to particular bit pat-
terns in the key. Comparatively, in IDEA, differ-
ent rounds do not have the same strength because
subkey bits do not overlap, and the total key en-
tropy per round can be much lower than 96 bits.
In IDEA
∗
, individual key bits cannot be flipped in-
dependently without affecting several subkeys at
once, thus hindering divide-and-conquer attacks
that try to exploit independent subkey bits such as
the biclique technique.
• Swapping ⊕ for ⊙ makes differential power anal-
ysis theoretically more difficult against IDEA
∗
than IDEA as the former operation is more side-
channel resistant than the latter. Additionally,
IDEA
∗
’s key schedule counters simple power
analysis due to its elaborated structure that do
not allow the internal instructions of a physical
implementation to be straightforwardly analysed
through power traces, for instance.
• Our analyses indicate that IDEA
∗
better resists
previous attacks than IDEA, including the recent
biclique technique (Sect. 5.4) and the meet-in-
the-middle Biryukov-Demirci (Sect. 5.2). In or-
der to have a fair security comparison, we sug-
gest the number of rounds in IDEA
∗
to be 6.5
instead of 8.5 as originally in IDEA, since the
number of modular multiplications becomes ap-
proximately the same. IDEA
∗
uses six multipli-
cations/divisions per round while IDEA uses four
multiplciations per round. This means that 6.5-
round IDEA
∗
(with 36 ⊙’s) shall provide the same
strenght as 8.5-round IDEA (34 ⊙’s).
3 THE IDEA
∗
BLOCK CIPHER
The International Data Encryption Algorithm (IDEA)
is a block cipher designed by Lai and Massey (Lai
et al., 1991) based on a previous design called PES
(Lai and Massey, 1990). IDEA operates on a 64-
bit state, uses a 128-bit key and iterates 8.5 rounds
(Fig. 1). A main feature of IDEA is the combina-
SECRYPT2013-InternationalConferenceonSecurityandCryptography
28

tion of three group operations on 16-bit words: ad-
dition in ZZ
2
16
(⊞), exclusive-or (xor) (⊕) and mul-
tiplication (⊙) in GF(2
16
+ 1) with 0 ≡ 2
16
. Mixing
incompatible group operations, in the sense that they
satisfy neither associativity nor distributivity rules, is
responsible for the confusion property (Lai, 1992) in
accordance with Shannon’s seminal work (Shannon,
1949). This is not a unique feature of IDEA. Ci-
phers such as RC5 (Menezes et al., 1997) and HIGHT
(Hong et al., 2006) use only Addition-Rotation-Xor
operations, which led to the terminology of ARX de-
signs. In this setting, IDEA could be called an AMX
(Addition-Mult-Xor) cipher. IDEA’s design follows
the Lai-Massey scheme and is not a Feistel nor a
Substitution Permutation Network (SPN) scheme and
therefore adds diversity to the portfolio of block ci-
pher frameworks.
IDEA
∗
preserves the wordwise structure and the
same group operations in IDEA as well as the de-
sign philosophy of repeating a strong round structure
a small number of times, instead of iterating a weak
round function a large number of times. IDEA
∗
also
adopted the design feature of never repeating the same
group operation two or more times during the encryp-
tion/decryption frameworks (Lai, 1992) and there is
full (text) diffusion after a single round. Note that
complete diffusion in IDEA and IDEA
∗
is achieved
in a single round.
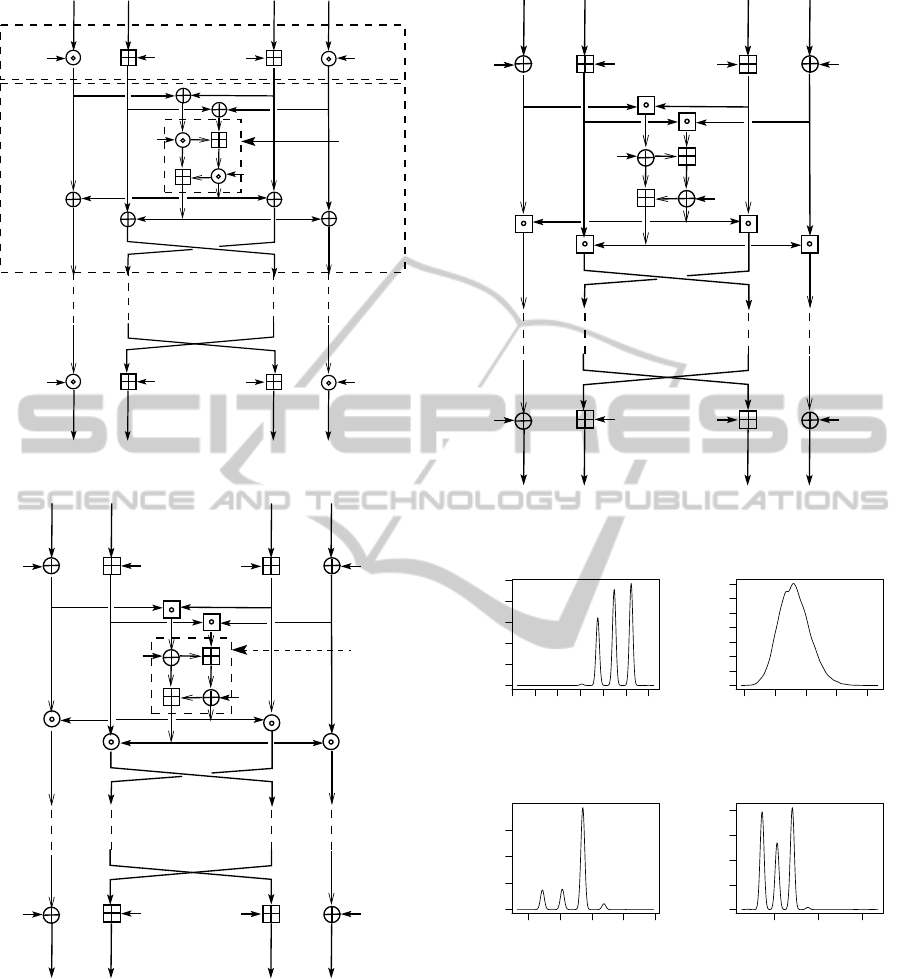
The original MA-box (with Multiplication and
Addition) in IDEA becomes an AX-box in IDEA
∗
(with Addition and Xor). One full encryption round
in IDEA
∗
consists of two half rounds: key-whitening
(KW) and AX (Fig. 2). The KW half-round simply
adds or xors the j-th subkey of the i-th round Z
(i)
j
,
1 ≤ i ≤ 6, 1 ≤ j ≤ 9, to each 16-bit word of the in-
put. A text block (a,b, c,d) becomes (A,B,C,D) =
(a ⊕Z
(i)
1
, b ⊞ Z
(i)
2
, c ⊞ Z
(i)
3
, d ⊕Z
(i)
4
). Decryption is
done by just applying the additive inverse or the xor
of the subkeys in the correct order.
The AX half-round contains an AX-box and an
almost involutory structure (see Fig. 2 for encryption
and Fig. 3 for decryption.). In more detail, the input
to the AX-box is (A ⊡ C, B ⊡ D). Let (E,F) denote
the AX-box output. Then, F = (((A⊙C
−1
) ⊕Z
(i)
5
) ⊞
(B ⊙D
−1
)) ⊕Z
(i)
6
, and E = ((A ⊙C
−1
) ⊕Z
(i)
5
) ⊞ F.
The output of the AX half-round for encryption be-
comes (A ⊙F, C ⊙F, B ⊙E, D ⊙E). For decryp-
tion, the AX-box input becomes (A ⊙F ⊡ (C ⊙F),
B ⊙ E ⊡ (D ⊙E)) = (A ⊙F ⊙C
−1
⊙F
−1
, B ⊙E ⊙
D
−1
⊙E
−1
) = (A ⊙C
−1
, B ⊙D
−1
), which is neces-
sary to recreate the same AX-box input as for encryp-
tion: (E, F). Decryption proceeds as (A ⊙F ⊡ F,
B ⊙ E ⊡ E, C ⊙ F ⊡ F, D ⊙ E ⊡ E) = (A,B,C,D).
Therefore, the AX half-round is almost its own in-
verse, except that ⊙’s are exchanged for ⊡. A nov-
elty in IDEA
∗
is the use of unkeyed ⊙ i.e. with both
operands variable. In IDEA, one operand in every
⊙ is always a fixed (unknown) subkey, which may
weaken the multiplication depending on the subkey
value (Daemen et al., 1993; Biryukov et al., 2002).
The last half round contains just a key whitening with
subkeys (Z
(7)
1
, Z
(7)
2
, Z
(7)
3
, Z
(7)
4
). Notice that ⊙ has
much better diffusion power than ⊕ (which is just bit-
wise). This fact is corroborated by Lai’s Low-High al-
gorithm (Lai, 1992) for multiplication in GF(2
16
+1):
let a,b ∈ZZ
2
16
+1
, R = ab mod 2
16
and Q = ab div 2
16
.
Then
a⊙b =
R−Q, if R ≥ Q
R−Q+ 2
16
+ 1, if R < Q
where R denotes the remainder (”Low” part) and Q
denotes the quotient (”High” part) when ab is divided
by 2
16
. It essentially means that the result of ⊙ de-
pends on all 32 bits of the extended multiplication.
Efficient hardware implementations of IDEA
∗
in
terms of speed and area can be performed by using
modulo 2
n
+ 1 arithmetic for addition and multiplica-
tion operations like in IDEA (Zimmernmann, 1999).
4 KEY SCHEDULE OF IDEA
∗
IDEA
∗
iterates 6.5 rounds and uses six subkeys per
round for a total of 40 subkeys. The key sched-
ule of IDEA
∗
is borrowed from the MESH-64 cipher
(Nakahara.Jr et al., 2003b). Let c
i
denote 16-bit con-
stants defined as follows: c
0
= 1 and c
i
= 3 · c
i−1
,
for i ≥ 1 with multiplication in GF(2)[x]/p(x), where
p(x) = x
16
+ x
5
+ x
3
+ x
2
+ 1 is a primitive polyno-
mial. The constant ”3” is represented by the polyno-
mial x + 1 in GF(2)[x]/p(x). Let a 128-bit key K be
partitioned into eight 16-bit words K
j
, −7 ≤ j ≤ 0.
The elements K
j
⊕c
j+7
form the eight initial values
in the following formula, for 1 ≤i ≤ 40:
K
i
= ((((((K
i−8
⊞ K
i−7
) ⊕K
i−6
) ⊞ K
i−3
) ⊕
K
i−2
) ⊞ K
i−1
) ≪ 7) ⊕c
i+7
. (1)
The j-th subkey of the i-th round, Z
(i)
j
, for 1≤ j ≤
6 and 1 ≤ i ≤ 7, is just the element K
6(i−1)+ j
. For
instance, Z
(1)
1
= K
1
and Z
(2)
1
= K
6
.
Low-weight differences in the key schedule (1)
quickly become unpredictable because of fast key
avalanche due to the primitive polynomial q(x) =
x
8
+ x
7
+ x
6
+ x
5
+ x
2
+ x + 1 and the inter-leaving
of ⊞, fixed bit rotation (≪ 7) and ⊕, all of which
are efficient and lightweight operations. Following
ImprovingBlockCipherDesignbyRearrangingInternalOperations
29

equation (1), we find out that Z
(1)
3
is the first subkey
that depends on all eight words of K. All following
subkeys also fully depend on K. Thus, complete key
diffusion is achieved even faster that text diffusion in
the encryption framework. Moreover, subkey bits in
IDEA
∗
overlap and depend nonlinearly on each other
due to (1), unlike the simple bit permutation mapping
subkeys to a user key in IDEA.
Concerning differentials in the key schedule, we
have analysed wordwise (xor and subtraction) differ-
ences in the key with difference value 8000
x
, because
it affects only the most significant bit in a word, and
thus propagates across ⊞ and ⊕ with certainty. But,
this difference do not survive for long in (1), soon be-
coming heavier Hamming-weight differences. Thus,
the combined ≪, ⊕ and ⊞ provide fast key diffu-
sion at low cost and destroy algebraic invariants and
difference patterns in subkeys, thwarting related-key
attacks (Kelsey et al., 1996; Biham et al., 2008) on
IDEA
∗
. These operations, plus the constants c
i
, make
the key schedule nonlinear and prevent patterns in the
key schedule to propagate or to cancel difference pat-
terns in the encryption framework, further countering
MITM (Demirci et al., 2003; Biham et al., 1417; Ayaz
and Selcuk, 2007), slide and advanced slide attacks
(Biryukov and Wagner, 1999).
The existence of weak keys in IDEA demon-
strated: (i) how a strong encryption framework can
be compromised by a comparatively weak key sched-
ule. Although the number of weak keys in differential
and linear settings represents a small fraction of the
key space (Daemen et al., 1993) it is still more than in
any other block cipher, and even larger than the num-
ber of weak and semi-weak keys in DES (Menezes
et al., 1997) combined; (ii) IDEA is not suitable as a
building block in compression function constructions
since the key can be chosen or manipulated by an op-
ponent in hash functions (Nakahara.Jr et al., 2003a;
Wei et al., 2012). Actually, (Nakahara.Jr et al., 2003a)
demonstrated that weak keys are a persistent problem
even if the number of rounds were doubled. To further
counter biclique attacks (Khovratovich et al., 2012),
simple modifications to the IDEA key schedule as
suggested in (Daemen et al., 1993) are not enough.
For decryption, (1) could be run backwards if the
last eight subkeys were stored instead of the original
user key K.
5 SECURITY ANALYSIS
The design of IDEA
∗
avoids subkeys as inputs in all
multiplication operations. Thus, there are no weak
keys anymore. This fact concerns differential, linear
(Daemen et al., 1993), differential-linear (Hawkes,
1998; Borst et al., 1997) and boomerang (among
other) attacks (Biryukov et al., 2002), since distin-
guishers based on weak keys do not apply to IDEA
∗
.
In the context of multiplicative differentials, (Borisov
et al., 2002) described attacks on IDEA-X, a variant
of IDEA in which ⊞ were substituted by ⊕. The
weak subkeys are the ones combined via ⊕. How-
ever, IDEA
∗
has both modular additions and unkeyed
multiplications, which effectively counter multiplica-
tive differentials.
There are well-known relations connecting ⊙ and
⊞, such as (i) X
∗
= −X = 2
16
+ 1−X = 1 −X mod
2
16
that implies X ⊞ X
∗
= 1 ⇔ X ⊙(X
∗
)
−1
= 0; and
(ii) X ⊙(X
∗
)
−1
= 1 ⇔ X −X
∗
= 0. But, these rela-
tions are not enough for achieving a comprehensive
attack using multiplicative differentials. In (Raddum,
2003), Raddum improved on the attack in (Borisov
et al., 2002) using wordwise difference δ = f f fd
x
.
We analysed IDEA
∗
under this xor difference and
the 1-round iterative characteristic (δ, δ, δ, δ) →
(δ, δ, δ, δ). The following was computed for Z ∈
{Z
(i)
2
,Z
(i)
3
}: δ
⊞Z
→ δ for Z = 0 with certainty, and for
Z ∈ {0002
x
,8002
x
, f f fe
x
} with probability 2
−1
(for
other subkeys the probability is zero); (δ, δ)
⊡
→ 0
with probability 2
−15.41
and (δ, 0)
⊙
→ δ with proba-
bility 2
−15.71
. While for IDEA-X, the 1-round char-
acteristic holds with probability 2
−4
, for IDEA
∗
it is
2
−2(15.41)−4(15.71)
= 2
−93.69
, without accounting for
the penalty due to addition with Z (for some of which
the probability drops to zero). Using subtraction dif-
ference instead of xor difference, both (δ,δ
−1
)
⊡
→ 0
and (δ, δ)
⊙
→ 0 hold with probability 2
−16.26
, where
δ
−1
= 4000
x
; δ
⊕Z
→ δ with variable probability, for in-
stance, 1 if Z = 0, 2
−1
if Z = 2, 2
−2
if Z = 8, but for
some subkey values such as 1, 3, 5, 6 and 7, the proba-
bility is zero. So, in the best cases, (δ, δ, δ, δ) →(δ, δ,
δ, δ) would hold with probability 2
−6(16.26)
= 2
−97.56
,
without accounting for the penalty due to the xor with
Z (for some of which the probability drops to zero).
Mod-n attacks are countered in IDEA
∗
just like in
IDEA: the combination of the three group operations
is enough to destroy invariant relations modulo Fer-
mat primes. The attacks in (Kelsey et al., 1999) apply
to ciphers employing addition and bitwise rotation.
5.1 Linear Cryptanalysis
For a linear analysis, without any weak-key assump-
tion, we start studying a single unkeyed multiplica-
tion. We exhaustively computed linear approxima-
tions to ⊙ (similar results hold for ⊡) for arbitrary,
SECRYPT2013-InternationalConferenceonSecurityandCryptography
30

nonzero bit-masks with low Hamming weight. The
most relevant results are concerned with bit-masks
that affect only the least significant bit (LSB) of a 16-
bit word, while the remaining bits are inactive. These
approximations are optimal for ⊕ and ⊞ since they
avoid carry bits. Consequently, this approach allows
us to take care of approximations covering all three
group operations simultaneously. Let (Γ
1
,Γ
2
)
⊙
→ Γ
3
denote a linear approximation to X ⊙Y = W, that is,
(X · Γ
1
) ⊙(Y ·Γ
2
) = W ·Γ
3
. We computed exhaus-
tively all linear approximations involving the LSBs
of both the input and output of ⊙ and the ones with
nonzero biases are (0,0)
⊙
→ 0 with bias 2
−1
, (1,1)
⊙
→
1 with bias 2
−13.4731
. We used bias as the magnitude
of the difference between the probability of the linear
relation from 1/2: |p −1/2|, following Matsui, and
the bias range is [0,1/2]. If one uses the notion corre-
lation instead, c = |2p −1| = 2*bias, then the range
becomes [0,1]. Table 1 exhaustively lists non-trivial
linear relations with non-zero bias for one full round.
In IDEA, these relations hold with bias 2
−1
under
several weak-key assumptions. Note that (0, 0)
⊙
→ 1,
(0,1)
⊙
→0, (1, 0)
⊙
→0, (1,0)
⊙
→1, (1,1)
⊙
→0 have bias
0. These bias figures corroborate our design decisions
in IDEA
∗
, since not all combinations of bit-masks af-
fecting the LSB of the inputs and the output to ⊙ hold
with nonzero bias.
Concatenating 1-round linear relations from Ta-
ble 1 into 2-round relations leads to bias below 2
−32
,
which makes a linear attack infeasible (Matsui, 1994)
since the codebook size is only 2
64
. But, it is possi-
ble to extend it through a KW half-round without de-
creasing the bias since this half-round contains only
⊞ and ⊕. Therefore, the best trade-off consists of
1.5-round relations such as (0,0, 0,γ) → (0, 0,γ,0) or
(0,γ,0,0) → (0,0, 0,γ) with two KW and one AX
half-round and bias 2
−25.94
. A key-recovery attack
on top of such a 1.5-round relation would recover
subkeys both from an AX half-round before and an-
other AX half-round after the linear relation, for a to-
tal of 2.5 rounds. From Sect. 4, there are no savings
due to non-overlapping bits between (Z
(i)
5
,Z
(i)
6
) and
(Z
(i+2)
5
,Z
(i+2)
6
) two rounds apart. Using the Piling-
up Lemma (Matsui, 1994) leads to a data complexity
of 8(2
−25.94
)
2
= 2
54.88
known plaintexts (and mem-
ory) and a time complexity of 2
54.88
(2
16
)
4
= 2
118.88
1-
round computations. This means 2
118.88
/2.5 ≈2
117.55
2.5-round computations. Note that not all user key
bits were recovered in this case. These results com-
pare favourably with those for IDEA (Daemen et al.,
1993) (for which there are linear relations covering
the full cipher) and MESH-64 (Nakahara.Jr et al.,
2003b) (for which there are linear relations covering
four rounds).
LINEAR HULLS. Consider the 1-round linear re-
lation (0,0,0,γ) → (0,0,γ, 0) from Table 1 but with
γ = 2 i.e. exploiting the second LSB as mask. Tak-
ing into account the linear approximations (2,2)
⊙
→ 2
with bias 2
−13.496
; (3,2)
⊞
→ 2, (2,3)
⊞
→ 3, (3,3)
⊞
→ 2,
(2,2)
⊞
→ 3 and (2, 2)
⊞
→ 2 all with bias 2
−2
, one can
track three separate trails across 1-round IDEA
∗
: one
trail uses (2, 3)
⊞
→ 2 twice, another uses (2, 2)
⊞
→ 3
and (2,3)
⊞
→ 2 and the last one uses (2,3)
⊞
→ 3 and
(3,3)
⊞
→ 2 inside the AX-box. All trails have bias
2
3−2−2−13.49−13.49
= 2
−27.98
. The combined bias of
both linear trails is
√
3 ·2
−27.98
= 2
−27.19
which is
lower than that of the 1-round relation for γ = 1.
In summary, the trails are few and there is an extra
penalty due to the carry bits. For more than one round,
unless the number of trails increases well above the
drop in the combined bias due to the approximations
of ⊞’s inside the AX-box, the overall bias (using
K. Nyberg’s rule (Nyberg, 1995)) will remain lower
than for one-round relations. This means that a poten-
tial linear hull effect will not be enough to counter a
significant bias drop in the long run due to the penalty
paid by carry bits. Even more true since IDEA
∗
has
only 6.5 rounds. The same reasoning applies to the
other relations in Table 1. Concerning the results in
Sect. 5.1, we conclude that 3-round IDEA
∗
is secure
against linear cryptanalysis, including linear hulls.
5.2 Biryukov-Demirci Attack
The application of ⊙ and ⊡ in place of ⊕ in IDEA
∗
implies that there is no more high-probability linear
relation involving the LSB’s of the two middle 16-bit
words in a text block, not even across a single round.
This is an essential weakness exploited in many at-
tacks on IDEA (Junod, 2005; Biham et al., 1417;
Khovratovich et al., 2012; Sun and Lai, 2009).
The Biryukov-Demirci (BD) relation exploits the
fact that the two middle 16-bit words in IDEA only
uses ⊕ and ⊞ to mix intermediate data across the
cipher state. Consequently, the LSB of the corre-
sponding plaintext and ciphertext words are related,
since there is no carry bits in the LSB position. Let
the input to a round be (X
1
,X
2
,X
3
,X
4
), its output be
(Y
1
,Y
2
,Y
3
,Y
4
) and the i-th MA-box output be (s
i
,t
i
).
Then, in IDEA both LSB(X
2
⊕Z
(i)
2
⊕s
i
) = LSB(Y
3
)
and LSB(X
3
⊕Z
(i)
3
⊕t
i
) = LSB(Y
2
) hold with certainty.
Comparatively, in IDEA
∗
, there are ⊙’s across all four
16-bit words in every round, instead of ⊕, and the
BD relation involving (X
2
, Y
3
) and (X
3
, Y
2
) become
(X
2
⊞ Z
(i)
2
) ⊙s
i
= Y
3
and (X
3
⊞ Z
(i)
3
) ⊙t
i
= Y
2
. Note
ImprovingBlockCipherDesignbyRearrangingInternalOperations
31

that LSB((X
2
⊞ Z
(i)
2
) ⊙ s
i
) does not equal LSB(Y
3
)
anymore, since the ⊙ operation has a wrap-around ef-
fect (Lai’s Low-High algorithm (Lai, 1992)) and con-
sequently the LSB of the multiplication does not de-
pend only on the LSBs of its two inputs: LSB((X
2
⊞
Z
(i)
2
) ⊙s
i
) 6= LSB(X
2
⊞ Z
(i)
2
)⊕ LSB(s
i
). Overall, ⊙
has much stronger diffusion than ⊕ (Sect. 3). If
we assume a linear approximation of ⊙ of the form
(1,1)
⊙
→ 1 as in Sect. 5.1, then the approximation
LSB((X
2
⊞ Z
(i)
2
) ⊙ s
i
) = LSB(X
2
⊞ Z
(i)
2
)⊕ LSB(s
i
)
would holds with bias 2
−13.4731
. After two rounds the
bias becomes 2
−25.9462
and after three rounds the bias
becomes 2
−38.4193
, which is too low since the code-
book size is only 2
64
.
5.3 Differential Analysis
For differential analysis, we employed both xor dif-
ferences (∆X = X ⊕X
∗
) and subtraction differences
(∆X = X −X
∗
) involving 16-bit words across a single
⊙, such as X ⊙Y = W. Let ∆
⊕
W = (X ⊙Y) ⊕(X ⊕
δ
1
) ⊙(Y ⊕δ
2
) denote the output difference of an un-
keyed ⊙ for δ
i
∈{8000
x
,0000
x
}, i ∈{1,2}. Note that
∆
−
W = (X ⊙Y)−(X −δ
1
)⊙(Y −δ
2
) behavesexactly
like ∆
⊕
W because X ⊕Y = 8000
x
⇔ X = Y ⊕8000
x
⇔X = Y ⊞ 8000
x
⇔X −Y = 8000
x
. Thus, we denote
∆
⊕
W and ∆
−
W simply as ∆W. Note that for mul-
tiplicative difference, X ⊙(X
∗
)
−1
= 1 ⇔ X −X
∗
=
0 ⇔ X ⊕X
∗
= 0 that is, zero xor-difference implies
⊙ difference equal to one. For xor difference 8000
x
there is no equivalent difference value for ⊙. Thus,
the results in Table 2 do not apply for multiplicative
differentials.
For (∆
1
, ∆
2
) = (0000
x
, 8000
x
) or (8000
x
, 0000
x
)
the probability that ∆W = 8000
x
is 2
−15
. For (∆
1
, ∆
2
)
= (8000
x
, 8000
x
), the probability that ∆W = 8000
x
is
2
−14.98
, and the probability that ∆W = 0000
x
is 2
−15
.
These data also hold for the case X ⊙Y
−1
= W. Thus,
we can construct Table 2. Note that the minimum
number of active ⊙’s is three, and there are no condi-
tions on subkey values for the difference propagation
compared to IDEA. Moreover, these 1-round char-
acteristics hold with much smaller probability than
for IDEA under weak-key conditions (Daemen et al.,
1993). This fact is a consequence of the cipher design,
which placed ⊙’s in order to mix the AX-box outputs
to each 16-bit word in a block at the end of each round
(guaranteeing full diffusion in a single round).
Concatenating 1-round characteristics from Ta-
ble 2 across two rounds results in probability less
than or equal to 2
−120
. Recall that the codebook is
only 2
64
. But, these characteristics can be extended
across one KW half-round, since the difference 8000
x
propagates for free across ⊞ and ⊕. Thus, the best
trade-off consists of 1.5-round characteristics such
as (0,0, δ,0) → (δ,0,0,0) or (0,δ, 0,δ) → (0,0, δ,δ)
with probability 2
−45
. A key-recovery attack on top
of such 1.5-round characteristics would recover sub-
keys both from an AX half-round before and another
AX half-round after the characteristic, for a total of
2.5 rounds. As shown in Sect. 4, there is no over-
lapping between bits of (Z
(i)
5
,Z
(i)
6
) and (Z
(i+2)
5
,Z
(i+2)
6
)
two rounds apart. This implies a data complexity pro-
portional to 2
45
chosen plaintexts (and memory) and
a time complexity of 2
45
(2
16
)
4
= 2
109
1-round com-
putations. This means 2
109
/2.5 ≈ 2
107.67
2.5-round
computations.
For truncated differentials, using either xor or sub-
traction differences, we adopt the approach in (Borst
et al., 1997). For instance, for a single unkeyed
⊙ such that X ⊙Y = W, for arbitrary ∆X 6= 0 and
∆Y = 0 the equality ∆W = ∆X happens with proba-
bility 2
−15
. For ∆X 6= 0 and ∆Y = ∆X, ∆W = 0 with
probability around 2
−16
for arbitrary,nonzero ∆X val-
ues. Let A, B,C,D,E, F, G,H, I ∈ ZZ
2
16
−{0}. A 1-
round truncated differential for IDEA
∗
can have the
form (A,0,B, 0)
2
−16
→ (C,0,C, 0)
2
−16
∗2
−15
∗2
−15
→ (C, C,
0, 0), where the first part (A,0,B,0)
2
−16
→ (C, 0, C, 0)
means that A and B differences cause the same dif-
ference C after crossing the first KW half-round with
probability 2
−16
. For the AX half-round there are two
critical points: (i) the input difference to the leftmost
⊡ has input differences C and C. The resulting dif-
ference is the leftmost input to the AX-box, which we
expect to be zero, that is, the transition (C,C) → 0
across a ⊡. This happens with a 2
−16
chance. The
rightmost AX-box input has zero difference. Thus,
the input difference to the AX-box is (0,0) and al-
ways gives (0,0) output difference; (ii) the double C
differences when combined with the zero differences
from the AX-box are preserved with a 2
−15
chance
each. So, for a single round the truncated differen-
tial (A,0, B,0) → (C,C,0,0) holds with probability
around 2
−62
. The corresponding probability of this
differential for a random permutation is 2
−32
, due
to the zero output difference words. Therefore, this
differential is not useful for distinguishing 1-round
IDEA
∗
from a random permutation.
If we let the double C differences turn into arbi-
trary differences D and E for instance, then the prob-
ability increases to 2
−32
, resulting in the 1-round trun-
cated differential (A,0,B,0) → (D,E,0, 0). Across
the next half-round, D and E will lead to differ-
ences, say, F and G and the block difference becomes
(F,G,0,0). This means the input difference to the
following AX-box becomes (H,I). Then, with prob-
SECRYPT2013-InternationalConferenceonSecurityandCryptography
32

ability 2
−32
the AX-box output difference is (G,F).
When this difference is combined with (F,G,0,0) we
obtain a difference (F ⊙F,F ⊙0,G ⊙G, G ⊙0). If
we wish F ⊙F and G⊙G to lead to zero difference,
then it will cost 2
−16
each and the final probability for
the 2-round differential (A,0, B,0) → (D,E,0, 0) →
(0,J, 0,K) reaches 2
−64−16−16
= 2
−96
, where J is the
difference coming out of F ⊙0, and K from G ⊙0.
If we do not set conditions on F ⊙0 nor on G ⊙0,
then one will have an output difference of the form
(L,J,M,K) with nonzero J, K, L, M. On the one
hand the probability increases to 2
−64
, but on the
other hand: (i) crossing the next round would de-
crease the probability further, and (ii) it would hinder
attacks since there are no bit patterns or other filter-
ing conditions on J, K, L and M. Overall, these 1-
and 2-round truncated differentials are much shorter
than the ones obtained for IDEA and MESH ciphers.
Moreover, for a boomerang distinguisher (Biryukov
et al., 2002), suppose we use such truncated differ-
entials, say, with two rounds in the encryption direc-
tion and one round for the decryption direction, that
is, four truncated differentials. This leads to a prob-
ability of (2
−96
)
2
·(2
−64
)
2
= 2
−320
, which is too low
for a codebook of only 2
64
texts. Suppose the full
codebook is used. Then, 2
64
texts can provide up to
2
64
·(2
64
−1)/2≈2
127
text pairs. Even using 1-round
truncated differentials in each direction, the probabil-
ity is already (2
−64
)
2
·(2
−64
)
2
= 2
−256
.
DIFFERENTIAL-LINEAR ATTACKS. For a
differential-linear attack (Biham et al., 2005), com-
bining 1-round characteristics from Table 2 with
the highest probability 2
−45
and 1-round relations
from Table 1 with the highest bias 2
−25.94
, we
arrive at differential-linear distinguishers with prob-
ability 1/2 + 2pq
2
, where p is the characteristic
probability and q is linear bias. For the concate-
nation of a single 1-round characteristic such as
(0,0, δ,0) → (δ,0,0,0) and a 1-round relation,
such as (0,0, 0,γ) → (0,0, γ,0) this probability is
1/2 + 2 · 2
−45
· (2
−25.94
)
2
= 1/2 + 2
−95.88
which
makes the attack infeasible since the codebook
size of IDEA
∗
is only 2
64
. Combining the 1-round
truncated differential (A,0, B,0) → (C,C,0,0)
with 1-round linear relations in Table 1 such as
(0,0, 0,γ) → (0, 0,γ,0) leads to a combined probabil-
ity of 1/2+ 2·2
−62
·2
−51.88
= 1/2+ 2
−112.88
, which
is again too low for an attack on 2-round IDEA
∗
.
IMPOSSIBLE DIFFERENTIALS. Impossible-
differential distinguishers in IDEA, such as (a, 0,
a, 0)
2.5 rounds
6→ (b, b, 0, 0) (Biham et al., 1999) with
a and b nonzero 16-bit differences, do not apply
to IDEA
∗
because differences across ⊙ and ⊡
behave differently than across ⊕. One can have both
(a,b)
⊙
→ 0 and (a, b)
⊙
→ c for nonzero a, b and c with
nonzero probability. We verified exhaustively that
this probability is close to 2
−16
independent of the
particular values of a, b and c. So far, even for a
single round, (a,0, a,0) → (b,b,0,0) still holds with
nonzero probability (either starting before or after a
half-round). We have thus far not yet found alter-
native impossible differentials for (reduced-round)
IDEA
∗
versions.
SQUARE ATTACKS. Concerning square attacks,
we follow the terminology of (Daemen et al., 1997).
A key-recovery attack on 2-round IDEA
∗
is the fol-
lowing: consider key-dependent λ-sets containing 2
16
plaintexts of the form (z
1
⊕i,c, i−z
3
,c) where c is an
arbitrary 16-bit constant (which makes the 2nd and
4th words passive, denoted P), i assumes all pos-
sible 16-bit value exactly once (which makes it an
active word, denoted A), and z
1
,z
3
are guesses for
Z
(1)
1
and Z
(1)
3
, respectively. We choose the two A
words, due to the i’s, such that they contain the values
{0,1,2,. ..,65535} in the same order. The objective
of this particular λ-set is to bypass the first round of
IDEA
∗
and to propagate the λ-set pattern (A, P,A,P).
When z
1
and z
3
correctly match Z
(1)
1
and Z
(1)
3
, the in-
put to the first AX-box will be two P (passive, 16-bit)
words. When z
1
,z
3
are wrong, the input to the first
AX-box will not be (P,P) because the inputs to the
leftmost ⊡ will not be (i,i).
This construction implies that for the correct z
1
,z
3
,
the output of the leftmost ⊡ we will be i ⊡ i
−1
= 1
for all i ∈ ZZ
2
16
. In other words, both inputs to the
AX-box will be constants or passive words. The in-
put λ-set to the second round will be (A, A,P,P) and
the input to the second AX-box will be (A, A) since
they are the ⊡ combination of an active A word and a
passive P word. Unfortunately, the output of this AX-
box will be (?,?), where ’?’ denotes a garbled word,
with no pattern that allows to distinguish it from a
random 32-bit variable (due to the combination of A
and P words inside the AX-box). Nonetheless, if we
denote the second round output by (x,y,u,v) for any
λ-set, and if the values z
1
,z
3
were guessed correctly,
then u⊡ v = u⊙v
−1
and x⊡ y = x⊙y
−1
, over the λ-
set, should both be A (active) words. Otherwise, the
z
1
,z
3
values were wrong. This key-recovery attack
on 2-round IDEA
∗
costs 2
32
·2
16
= 2
48
chosen plain-
texts, 2
16
memory and effort 2
32
/2 = 2
31
half-round
computations in the worst case, which is equivalent to
2
31
/4 = 2
29
2-round computations.
In (Knudsen and Rijmen, 2008), Kudsen and
Rijmen presented a new attack setting in which the
key is known by the adversary, for instance, in the
context of a hash function. They studied so called
known-key distinguishers based on λ-sets. It is an
ImprovingBlockCipherDesignbyRearrangingInternalOperations
33

inside-out approach in which a single A word inside
a target cipher is left free to propagate both in the
encryption and decryption directions. This approach
allows distinguishers up to 7-round AES (such that
at least one balanced word survive in the state).
For IDEA, known-key distinguishers can reach at
most 2.5 rounds, such as (?,?, A,?)
KW
← (B, ?,A,?)
AX
←
(A,P,P,P)
KW
→ (A, P,P,P)
AX
→ (B,A, ?,?)
KW
→ (?, A,?,?),
where KW and AX denote half-rounds. Simi-
larly, for IDEA
∗
, 2.5-round known-key distin-
guishers exist such as (?,?,A,?)
KW
← (?,?, A,?)
AX
←
(A,P,P,P)
KW
→ (A,P,P,P)
AX
→ (?,A,?,?)
KW
→ (?,A, ?,?)
and (A,?,?,?)
KW
← (A,?,?,?)
AX
← (P,A,P,P)
KW
→
(P,A,P,P)
AX
→ (A, A,?,A)
KW
→ (A,A,?, A). These
distinguishers indicate that 2.5-round IDEA* may
not be an ideal primitive in compression functions
constructions in hash functions.
5.4 Biclique Attacks
For the reasons listed below, we argue that the design
of IDEA
∗
imposes enough countermeasures against
biclique attacks (Khovratovich et al., 2012), which
heavily relies on MITM attacks (Demirci et al., 2003)
and poor diffusion in the key schedule.
• the Biryukov-Demirci relation discussed in
Sect. 5.2 does no hold for IDEA
∗
.
• Sect. 4 detailed full key diffusion in the key sched-
ule after (and including) Z
(1)
3
. As a consequence,
key bits overlap in every subkey, meaning there
are no neutral key bits and thus, related-key dif-
ferentials (with nonzero difference only in the
key and holding with probability 1) needed in bi-
cliques cannot be constructed based on indepen-
dent subkey bits.
• Sect. 3 detailed full text diffusion in a single
round. Moreover,there is improved wordwise dif-
fusion provided by ⊙’s replacing ⊕’s across every
block in the AX half-rounds. Therefore, the effort
for the MITM and biclique constructions becomes
equivalent to that of an exhaustive key search, be-
cause there is no shortcut that allows to partition
the subkeys into independent sets as required in
(Khovratovich et al., 2012).
5.5 Side-channel and Performance
Analysis
For the sake of practical usability, cryptographic
primitives should be carefully designed and imple-
mented in such a way that the internally processed
information remains secure.
From a practical point of view, side-channel anal-
ysis (SCA) represents a serious threat for the secu-
rity of cryptographic systems in addition to conven-
tional cryptanalysis. SCA allows an adversary to re-
cover cryptographic keys by analysing critical pieces
of information unintentionally leaked through physi-
cal means. Power analysis (Kocher et al., 1999) is one
of the strongest kinds of SCA. Its underlying assump-
tion says that the instantaneous power consumption
of an integrated circuit relates to the executed instruc-
tions and processed data. Two widely investigated
families of power attacks are the simple and differ-
ential power analysis: SPA and DPA (Kocher et al.,
1999). Briefly, the former focuses on instruction-
related key aspects present in a few power traces,
whilst the latter focuses on data-related key aspects
present in a typically higher amount of power traces.
For a comprehensive explanation we refer to (Man-
gard et al., 2007).
Power analysis has already been performed on
IDEA (e.g. (Lemke et al., 2004; Oswald and Preneel,
2002)). Oswald and Preneel (Oswald and Preneel,
2002) assessed the theoretical vulnerability of IDEA
to power analysis. As the key schedule of IDEA is rel-
atively simple due to the straightforward cyclic shift-
ing of the key, it turns out that SPA represents a threat.
IDEA
∗
counters SPA theoretically by using a more
elaborate key schedule, as shown in Sec. 4. Lemke
et al. (Lemke et al., 2004) and Pan et al. (Pan et al.,
2008) realized DPA on each one of the boolean and
arithmetic operations (⊙,⊞,⊕) used in IDEA. They
showed that ⊕ is more DPA-resistant than ⊞, which
is in turn more DPA-resistant than ⊙. Nonlinear func-
tions are less robust against DPA than linear functions
(Pan et al., 2008; Guilley et al., 2004; Benoˆıt and
Peyrin, 2010; Prouff, 2005).
The swapping of ⊙ and ⊕ operations in IDEA
∗
makes it theoretically more DPA-resistant than IDEA.
While in IDEA the keys are input to ⊙ and ⊞, in
IDEA
∗
the keys are input to ⊕ and ⊞. Moreover,
implementing DPA against an unknown implementa-
tion of IDEA
∗
is expected to be more time consum-
ing than performing the same attack on e.g. AES,
DES, SERPENT, PRESENT or mCrypton, because
the number of key hypotheses is 2
16
for IDEA
∗
and
respectively 2
8
, 2
6
, 2
4
, 2
4
, 2
4
for the others. Aim-
ing especifically at countering DPA on IDEA, Neiβe
and Pulkus (Neiße and Pulkus, 2004) proposed algo-
rithms to protect the cipher’s arithmetic and boolean
operations by switching masks among the operations.
IDEA
∗
may also benefit from this countermeasure. It
should be noted however that depending on the de-
SECRYPT2013-InternationalConferenceonSecurityandCryptography
34

signer’s resources and constraints DPA may still re-
main an issue for IDEA
∗
as software countermea-
sures for boolean operations can be costly. Never-
theless other countermeasures can be applied such as
randomizing the order of the operations in each exe-
cution, adding noise by executing other instructions
in parallel to the encryption/decryption and adding
random delays between operations (Mangard et al.,
2007).
Concerning efficiency, empirical experiments on
IDEA, IDEA
∗
and AES encryption were performed
on an 8-bit microcontroller ATmega328P. The same
level of optimization was used for all algorithms.
These analyses showed that 6.5-round IDEA
∗
is 6%
slower than an 8.5-round IDEA (same for AES)
thanks to a precomputation of all multiplicative in-
verses (Fig. 4). Also, our AES implementation is
4% faster than IDEA
∗
. It should be emphasized that
increasing the number of rounds in IDEA does not
protects it against side-channel attacks (Nakahara.Jr
et al., 2003a). Indeed, power analyses are performed
on the first (or the last) round independent of the total
number of rounds.
6 CONCLUSIONS
This paper analysed a simple design decision: what
is the impact on a cipher’s security due to a rear-
rangement of the internal cipher components? We
observed significant and relevant consequences when
we swapped the exclusive-or and multiplication oper-
ations in the IDEA cipher.
We called the updated design IDEA
∗
. Our anal-
yses indicate IDEA
∗
effectively counters all previ-
ously reported attacks on IDEA, including theoretical
power analysis. IDEA
∗
has improved overall diffu-
sion through the use of unkeyed multiplication, a new
key schedule and uses 6.5 rounds (compared with 8.5
rounds in IDEA). In summary, the new design coun-
ters not only differential (Borst et al., 1997) and lin-
ear analysis (Daemen et al., 1993; Biham et al., 2007)
but also impossible differentials (Biham et al., 1999),
truncated differentials (Knudsen and Rijmen, 1997),
boomerang (Wagner, 1999; Biryukov et al., 2002),
square (Demirci, 2003; Nakahara.Jr et al., 2002; Bi-
ham et al., 2007), differential-linear (Hawkes, 1998;
Borst et al., 1997), meet-in-the-middle(Demirci et al.,
2003; Ayaz and Selcuk, 2007), multiplicative dif-
ferentials (Borisov et al., 2002), Biryukov-Demirci
(Junod, 2005; Biham et al., 1417; Sun and Lai, 2009),
higher-order differential (Biham et al., 2005), related-
key (Biham et al., 2008) and mod-n attacks (Kelsey
et al., 1999). We have also taken into account recent
developments such as biclique analysis (Abed et al.,
2012; Khovratovich et al., 2012) that reach the full
versions of IDEA, AES and PRESENT. Finally, we
focused also on algorithmic countermeasures against
power analysis in order to compare IDEA to IDEA
∗
.
We showed that IDEA
∗
is theoretically more resis-
tant against power analysis than IDEA. As such, our
contributions also improved our understanding of the
IDEA cipher in view of old and new atttacks.
In summary: simple changes in a cipher can have
significant impacts in it security (and performance).
These changes and design decisions are often undoc-
umented, even in new designs, which may lead to sus-
picion of trapdoors. Only a thoroughanalysis can give
some evidence of the strength of new designs against
modern attacks.
As a topic for future work, we suggest to study
different permutation of cipher components in other
high-profile cryptographic primitives, such as hash
functions and stream ciphers. Potential targets in-
clude the MESH ciphers (Nakahara.Jr et al., 2003b),
which have an Add-Mult-Xor (AMX) design similar
to that of IDEA. The point is that in these ciphers,
there is a clear asymmetry between the internal op-
erations: addition and xor are lightweight operations
(a few CPU cycles) with poor diffusion, while mod-
ular multiplication is heavyweight (several CPU cy-
cles) with better diffusion.
ACKNOWLEDGEMENTS
The authors would like to thank INNOVIRIS, the
Brussels Institute for Research and Innovation, under
the ICT Impulse program CRYPTASC, for sponsor-
ing this work.
REFERENCES
Abed, F., Forler, C., List, E., Lucks, S., and Wenzel,
J. (2012). Biclique cryptanalysis of the PRESENT
and LED lightweight ciphers. IACR ePrint Archive
2012/591.
Ayaz, E. and Selcuk, A. (2007). Improved DST cryptanal-
ysis of IDEA. In Selected Areas in Cryptology (SAC),
LNCS 4356, pages 1–14. Springer.
Benoˆıt, O. and Peyrin, T. (2010). Side-channel analysis of
six SHA-3 candidates. In CHES, LNCS, pages 140–
157. Springer.
Biham, E., Biryukov, A., and Shamir, A. (1999).
Miss in the middle attacks on IDEA, Khufu
and Khafre. In Fast Software Encryption
(FSE), LNCS 1636, pages 124–138. Springer.
ImprovingBlockCipherDesignbyRearrangingInternalOperations
35

Biham, E., Dunkelman, O., and Keller, N. (2005). New
combined attacks on block ciphers. In Fast Soft-
ware Encryption (FSE), LNCS 3557, pages 126–144.
Springer.
Biham, E., Dunkelman, O., and Keller, N. (2007). A new
attack on 6-round IDEA. In Fast Software Encryption
(FSE), LNCS 4593, pages 211–224. Springer.
Biham, E., Dunkelman, O., and Keller, N. (2008). A unified
approach to related-key attacks. In Fast Software En-
cryption (FSE), LNCS 5086, pages 73–96. Springer.
Biham, E., Dunkelman, O., Keller, N., and Shamir, A.
(2011/417). New data-efficient attacks on reduced-
round IDEA. IACR ePrint 2011/417.
Biryukov, A., Nakahara.Jr, J., Preneel, B., and Vande-
walle, J. (2002). New weak-key classes of IDEA. In
Information and Communications Security (ICICS),
LNCS 2513, pages 315–326. Springer.
Biryukov, A. and Wagner, D. (1999). Slide attacks. In Fast
Software Encryption (FSE), LNCS 1636, pages 245–
259. Springer.
Bogdanov, A., Khovratovich, D., and Rechberger, C.
(2011). Biclique cryptanalysis of the full AES. IACR
ePrint archive 2011/449.
Bogdavov, A. and Rechberger, C. (2010). A 3-subset meet-
in-the-middle attack: cryptanalysis of the lightweight
block cipher KTANTAN. IACR ePrint archive
2010/532.
Borisov, N., Chew, M., Johnson, R., and Wagner, D. (2002).
Multiplicative differentials. In Fast Software Encryp-
tion (FSE), LNCS 2365, pages 17–33. Springer.
Borst, J., Knudsen, L., and Rijmen, V. (1997). Two at-
tacks on reduced IDEA (extended abstract). In EU-
ROCRYPT, LNCS 1233, pages 1–13. Springer.
Daemen, J., Govaerts, R., and Vandewalle, J. (1993). Weak
keys for IDEA. In CRYPTO, LNCS 773, pages 224–
231. Springer.
Daemen, J., Knudsen, L., and Rijmen, V. (1997). The block
cipher SQUARE. In Fast Software Encryption (FSE),
LNCS 1267, pages 149–165. Springer.
Demirci, H. (2003). Square-like attacks on reduced rounds
of IDEA. In Selected Areas in Cryptography (SAC),
LNCS 2595, pages 147–159. Springer.
Demirci, H., Selcuk, A., and T¨ure, E. (2003). A new meet-
in-the-middle attack on the IDEA block cipher. In
Selected Areas in Cryptography (SAC), LNCS 3006,
pages 117–129. Springer.
FIPS197 (2001). Advanced encryption standard (AES).
FIPS PUB 197 Federal Information Processing Stan-
dard Publication 197, U.S. Department of Commerce.
Guilley, S., Hoogvorst, P., and Pacalet, R. (2004). Dif-
ferential power analysis model and some results. In
Quisquater, J.-J., Paradinas, P., Deswarte, Y., and
Kalam, A., editors, CARDIS, pages 127–142. Kluwer.
Hawkes, P. (1998). Differential-linear weak key classes of
IDEA. In EUROCRYPT,LNCS 1403, pages 112–126.
Springer.
Hong, D., Sung, J., Hong, S., Lim, J., Lee, S., Koo, B., Lee,
C., Chang, D., Lee, J., Jeong, K., Kim, H., Kim, J.,
and Chee, S. (2006). HIGHT: A new block cipher suit-
able for low-resource device. In Goubin, L. and Mat-
sui, M., editors, Cryptographic Hardware and Embed-
ded Systems, LNCS 4249, pages 46–59. Springer.
Isobe, T. (2011). A single-key attack on the full GOST
block cipher. In Fast Software Encryption (FSE),
LNCS 6733, pages 290–305. Springer.
Joye, M. and Quisquater, J.-J., editors (2004). Crypto-
graphic Hardware and Embedded Systems - CHES
2004, LNCS 3156. Springer.
Junod, P. (2005). New attacks against reduced-round ver-
sions of IDEA. In Fast Software Encryption (FSE),
LNCS 3557, pages 384–397. Springer.
Kelsey, J., Schneier, B., and Wagner, D. (1996). Key-
schedule cryptanalysis of IDEA, G-DES, GOST,
SAFER and triple-DES. In CRYPTO, LNCS 1109,
pages 237–251. Springer.
Kelsey, J., Schneier, B., and Wagner, D. (1999). Mod
n cryptanalysis, with applications against RC5P and
M6. In Fast Software Encryption (FSE), LNCS 1636,
pages 139–155. Springer.
Khovratovich, D., Leurent, G., and Rechberger, C. (2012).
Narrow-bicliques: cryptanalysis of full IDEA. In EU-
ROCRYPT, LNCS 7237, pages 392–410. Springer.
Knudsen, L. and Rijmen, V. (1997). Truncated differentials
of IDEA. Technical report, ESAT-COSIC Tech report
97-1.
Knudsen, L. and Rijmen, V. (2008). Known-key dis-
tinguishers for some block ciphers. In Asiacrypt,
LNCS 4833, pages 315–324. Springer.
Kocher, P., Jaffe, J., and Jun, B. (1999). Differential
power analysis. In CRYPTO, LNCS, pages 388–397.
Springer.
Lai, X. (1992). On the Design and Security of Block Ci-
phers. PhD thesis, ETH no. 9752, Swiss Federal In-
stitute of Technology, Zurich.
Lai, X. and Massey, J. (1990). A proposal for a new block
encryption standard. In EUROCRYPT, LNCS 473,
pages 389–404. Springer.
Lai, X., Massey, J., and Murphy, S. (1991). Markov ci-
phers and differential cryptanalysis. In EUROCRYPT,
LNCS 547, pages 17–38. Springer.
Lemke, K., Schramm, K., and Paar, C. (2004). Dpa on n-bit
sized boolean and arithmetic operations and its appli-
cation to IDEA, RC6, and the HMAC-construction. In
(Joye and Quisquater, 2004), pages 205–219.
Mangard, S., Oswald, E., and Popp, T. (2007). Power Anal-
ysis Attacks: Revealing the Secrets of Smart Cards
(Advances in Information Security). Springer.
Matsui, M. (1994). Linear cryptanalysis method for DES
cipher. In EUROCRYPT, LNCS 765, pages 386–397.
Springer.
Matsui, M. (1995). On correlation between the order of
s-boxes and the strength of DES. In EUROCRYPT,
LNCS 950, pages 366–375. Springer.
Menezes, A., vanOorschot, P., and Vanstone, S. (1997).
Handbook of Applied Cryptography. CRC Press.
NakaharaJr, J. (2009). On the order of round components in
the AES. International Journal of Network Security
(IJNS), 9:44–50.
Nakahara.Jr, J., Preneel, B., and Vandewalle, J. (2002).
Square attacks on reduced-round PES and IDEA
SECRYPT2013-InternationalConferenceonSecurityandCryptography
36

block ciphers. 23rd Symposium on Information The-
ory in the Benelux.
Nakahara.Jr, J., Preneel, B., and Vandewalle, J. (2003a). A
note on weak-keys of PES, IDEA and some extended
variants. In Information Security Conference (ISC),
LNCS 2851, pages 269–279. Springer.
Nakahara.Jr, J., Rijmen, V., Preneel, B., and Vandewalle,
J. (2003b). The MESH block ciphers. In Informa-
tion Security Applications (WISA), LNCS 2908, pages
458–473. Springer.
Neiße, O. and Pulkus, J. (2004). Switching blindings with a
view towards IDEA. In (Joye and Quisquater, 2004),
pages 230–239.
Nyberg, K. (1995). Linear approximation of block ci-
phers. In EUROCRYPT, LNCS 950, pages 439–444.
Springer.
Oswald, E. and Preneel, B. (2002). A theoretical evalua-
tion of some NESSIE candidates regarding their sus-
ceptibility towards power analysis attacks. Technical
report, Katholieke Universiteit Leuven.
Pan, J., denHartog, J., and deVink, E. (2008). An operation-
based metric for CPA resistance. In Jajodia, S., Sama-
rati, P., and Cimato, S., editors, SEC, volume 278 of
IFIP, pages 429–443. Springer.
Prouff, E. (2005). DPA attacks and s-boxes. In Fast
Software Encryption (FSE), LNCS, pages 424–441.
Springer.
Raddum, H. (2003). Cryptanalysis of IDEA-X/2. In Fast
Software Encryption (FSE), LNCS 2887, pages 1–8.
Springer.
Shannon, C. (1949). Communication theory of secrecy sys-
tems. Bell System Technical Journal, 28(4):656–715.
Sun, X. and Lai, X. (2009). The key-dependent attack on
block ciphers. In ASIACRYPT, LNCS 5912, pages 19–
36. Springer.
Vergos, H., Vassalos, E., and Bakalis, D. (2011). Modulo
2
n
+ 1 arithmetic units with embedded diminished-to-
normal conversion. In Digital System Design (DSD),
14th Euromicro Conference, pages 468–475.
Wagner, D. (1999). The boomerang attack. In Fast Soft-
ware Encryption (FSE), LNCS 1636, pages 156–170.
Springer.
Wei, L., Peyrin, T., Sokolowski, P., Ling, S., Pieprzyk,
J., and Wang, H. (2012). On the (in)security of
IDEA in various hashing modes. IACR ePrint archive
2012/264.
Zimmernmann, R. (1999). Efficient VLSI implementation
of modulo 2
n
+1 addition and multiplication. In Com-
puter Arithmetic, 14th IEEE Symposium, pages 158–
167.
APPENDIX
Table 1: 1-round linear relations in IDEA
∗
with γ = 1.
1-round linear relation bias # active ⊙’s
(0,0, 0,γ) → (0,0,γ,0) 2
−25.94
2
(0,0, γ,0) → (γ,0,γ,γ) 2
−63.35
5
(0,0, γ,γ) → (γ,0,0, γ) 2
−38.41
3
(0,γ,0,0) → (0,0,0,γ) 2
−25.94
2
(0,γ,0,γ) → (0, 0,γ,γ) 2
−25.94
2
(0,γ,γ,0) → (γ,0,γ, 0) 2
−38.41
3
(0,γ,γ,γ) → (γ,0, 0,0) 2
−38.41
3
(γ,0,0,0) → (0,γ,γ,γ) 2
−63.35
5
(γ,0,0,γ) → (0, γ,0,γ) 2
−38.41
3
(γ,0,γ,0) → (γ,γ, 0,0) 2
−25.94
2
(γ,0,γ,γ) → (γ,γ,γ,0) 2
−50.88
4
(γ,γ,0,0) → (0,γ, γ,0) 2
−38.41
3
(γ,γ,0,γ) → (0, γ,0,0) 2
−38.41
3
(γ,γ,γ, 0) → (γ,γ,0,γ) 2
−50.88
4
(γ,γ,γ, γ) → (γ,γ, γ,γ) 2
−50.88
4
Table 2: 1-round characteristics in IDEA
∗
using ⊕ or −
differences and δ = 8000
x
.
1-round characteristic probability # active ⊙’s
(0,0, 0,δ) → (δ,δ,δ, 0) 2
−75
5
(0,0, δ, 0) → (δ,0, 0,0) 2
−45
3
(0,0, δ, δ) → (0,δ, δ,0) 2
−75
5
(0,δ,0, 0) → (δ,δ, 0,δ) 2
−75
5
(0,δ,0, δ) → (0,0,δ,δ) 2
−45
3
(0,δ,δ, 0) → (0,δ, 0,δ) 2
−75
5
(0,δ,δ, δ) → (δ,0, δ, δ) 2
−90
6
(δ,0,0, 0) → (0,δ, 0,0) 2
−45
3
(δ,0,0, δ) → (δ,0, δ,0) 2
−75
5
(δ,0,δ, 0) → (δ,δ, 0,0) 2
−45
3
(δ,0,δ, δ) → (0, 0,δ,0) 2
−90
6
(δ,δ,0, 0) → (δ,0, 0,δ) 2
−75
5
(δ,δ,0, δ) → (0,δ, δ, δ) 2
−90
6
(δ,δ,δ,0) → (0,0, 0,δ) 2
−90
6
(δ,δ,δ,δ) → (δ,δ,δ,δ) 2
−90
6
ImprovingBlockCipherDesignbyRearrangingInternalOperations
37
!
"
!
#
!
$
!
%
&"' &"' &"' &"'
!
"
!
#
!
$
!
%
&(' &(' &(' &('
!
)
&"'
!
&"'
*
+, -./
Figure 1: Computational graph of the IDEA cipher.
Z
1
Z
2
Z
3
Z
4
(1) (1) (1) (1)
Z
1
Z
2
Z
3
Z
4
(7) (7) (7) (7)
Z
6
(1)
(1)
5
Z
AX−box
Figure 2: Computational graph of IDEA
∗
for encryption.
Z
1
Z
2
Z
3
Z
4
Z
1
Z
2
Z
3
Z
4
(1) (1) (1) (1)
(7) (7) (7) (7)
Z
6
5
Z
(6)
(6)
Figure 3: Computational graph of IDEA
∗
for decryption.
220000 230000 240000 250000
0.000 0.010 0.020
IDEA
bit/second
probability density
14000 18000 22000
0.000 0.003 0.006
IDEA*
bit/second
probability density
220000 230000 240000
0.00 0.02
IDEA* with a LUT for the inverse
bit/second
probability density
235000 245000
0.000 0.010 0.020
AES
bit/second
probability density
Figure 4: Probability density of the throughput (bit/second)
of encryptions on an 8-bit microcontroller ATmega328P
of four implementations (20,000 measurements): IDEA,
IDEA
∗
, IDEA
∗
with a lookup table for the inverse and AES.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
38
