
A Key-revocable Attribute-based Encryption
for Mobile Cloud Environments
Tsukasa Ishiguro, Shinsaku Kiyomoto and Yutaka Miyake
KDDI R&D Laboratories Inc. 2-1-15 Ohara, Fujimino, 356-8502 Saitama, Japan
Keywords:
Attribute-Based Encryption (ABE), Access Control, Cloud Computing, Key Revocation, Mobile Cloud.
Abstract:
In this paper, we propose a new Attribute-Based Encryption (ABE) scheme applicable to mobile cloud environ-
ments. A key issue in mobile cloud environments is how to reduce the computational cost on mobile devices
and delegate the remaining computation to cloud environments. We also consider two additional issues: an
efficient key revocation mechanism for ABE based on a concept of token-controlled public key encryption,
and attribute hiding encryption from a cloud server. To reduce the computational cost on the client side, we
propose an efficient ABE scheme jointly with secure computing on the server side. We analyze the security of
our ABE scheme and evaluate the transaction time of primitive functions implemented on an Android mobile
device and a PC. The transaction time of our encryption algorithm is within 150 msec for 89-bit security and
about 600 msec for 128-bit security on the mobile device. Similarly, the transaction time of the decryption
algorithm is within 50 msec for 89-bit security and 200 msec for 128-bit security.
1 INTRODUCTION
1.1 Background
Commercial social network services (SNS) and doc-
ument management systems have been launched in
cloud environments (Google, 2012; Amazon, 2012),
and outsourcing the services of an enterprise system
has come to be considered a potential application
for cloud computing. NIST defines cloud comput-
ing as (NIST, 2009): “Cloud computing is a model
for enabling convenient, on-demand network access
to a shared pool of configurable computing resources
(e.g., networks, servers, storage, applications, and
services) that can be rapidly provisioned and released
with minimal management effort or service provider
interaction. ” Cloud computing is becoming more
common and widespread, and it provides several ben-
efits for both cloud service providers and their users.
Here, we look at a data storage service, which
is one of the most common services for cloud envi-
ronments, and consider a situation where a company
stores their data by utilizing the storage service. It
can be assumed that company personnel need to ac-
cess the data using their mobile devices. The system
consists of an outsourcing database in a cloud envi-
ronment and mobile devices. This situation is called
a “mobile cloud environment”.
Security risks associated with cloud environments
are of increasing concern(Cloud Security Alliance,
2009; European Network and Information Security
Agency, 2010). If the cloud service is vulnerable or
the cloud provider has a malicious/curious adminis-
trator, the private information of users and corporate
confidential information is at risk of being leaked.
Furthermore, a fine-grained access control mecha-
nism is needed whenever a database on a cloud ser-
vice is shared by users and an access policy is defined
for each role of users. Accordingly, if we consider
this situation, which is one of the most common sit-
uations for a cloud environment, it can be assumed
that data encryption and access control are mandatory
functions.
Attribute-based encryption (ABE) schemes are an
efficient solution to realize both functionalities: en-
cryption and fine-grained access control. Sensitive
user data are encrypted according to an access pol-
icy in ABE schemes, and a user cannot decrypt the
data if the user does not have an access right satis-
fying the access policy for the data. Generally, the
access policy can be described by user’ attributes,
e.g. affiliations and roles. The computational cost of
ABE schemes is still huge in practical terms because
it increases markedly as the number of attributes de-
scribed in the access policy increases. We focus on
the mobile cloud environment and consider accesses
51
Ishiguro T., Kiyomoto S. and Miyake Y..
A Key-revocable Attribute-based Encryption for Mobile Cloud Environments.
DOI: 10.5220/0004505300510061
In Proceedings of the 10th International Conference on Security and Cryptography (SECRYPT-2013), pages 51-61
ISBN: 978-989-8565-73-0
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

from mobile devices. In the mobile cloud environ-
ment, the computational cost on mobile devices be-
comes problematic in practice. Another issue con-
fronting ABE is key revocation. The system needs to
manage the revocation of users since mobile devices
are easily lost or stolen.
1.2 Related Works
Attribute-based encryption (ABE) has been exten-
sively researched as a cryptographic protocol (Sahai
and Waters, 2005; Bethencourt et al., 2007; Hinek
et al., 2008; Lewko et al., 2010). In Ciphertext-Policy
ABE (CP-ABE) systems (Bethencourt et al., 2007), a
user encrypts data with descriptions of an access pol-
icy. The access policy defines authorized users, and
their statements consisting of attributes and logical
relationships such as AND, OR, or M of N (thresh-
old gates); for example, users who have the attributes
“Project manager” and “Administration department”
can access the data, of which the access policy is de-
fined as “Project manager ∧ Administration depart-
ment”. The mechanism can prevent a cloud service
provider or an adversary from accessing the secret
information. Another type of ABE is a Key-Policy
ABE (KP-ABE) (Goyal et al., 2006). In KP-ABE, a
user’s personal key corresponds to a combination of
attributes “Project manager ∧ Administration depart-
ment”.
Generally, ABE schemes require huge computa-
tions such as many pairing computations. Several pa-
pers have been published that deal with the imple-
mentation of pairing computations on different de-
vices (Beuchat et al., 2010; Scott, 2011; Aranha et al.,
2010; Naehrig et al., 2010). As shown in these papers,
one pairing computation can be completed in less than
a few milliseconds on a current PC. However, more
computation time is required on other devices that
have less computational power, such as smartphones.
Furthermore, the computational power of the ABE
mechanism increases appropriately as the number of
attributes increases.
Some papers have proposed schemes to remove
heavy computations from a mobile device (Zhou and
Huang, 2011; Green et al., 2011) and delegate them
to cloud servers at a remote site. In (Zhou and Huang,
2011), Zhou et al. divided the encryption step into
two parts, a mobile device part and a cloud server
part. For the first part, the mobile device encrypts
data in a constant time; the transaction time of the
first encryption function does not depend on the num-
ber of attributes. For the second part, the cloud server
can operate the second encryption function without
plaintext information; no information is revealed to
the cloud server. In the same way, they also divide
the decryption step into two parts. The Zhou et al.
scheme has no key revocation mechanism; thus, this
is an open issue for ABE in mobile cloud environ-
ments. Furthermore, they did not present sufficient
security analyses for their ABE scheme.
Another solution for mobile cloud environments is
outsourcing decryption processes (Green et al., 2011;
Goyal et al., 2006; Waters, 2011) using a proxy server.
A user has a translation key TK along with a secret
key. The user sends the TK to a proxy server, for the
decryption process on the proxy server. An ElGamal-
style ciphertext for the decryption process is used to
avoid revealing any part of a message. The decryption
step is similar to ElGamal decryption, and the compu-
tational cost of decryption imposed on a mobile de-
vice can be reduced by delegating some of the pro-
cesses of decryption to the proxy server, even though
the cost for encryption is still heavy.
From the viewpoint of key management, a revoca-
tion mechanism is also required. However, no key
revocation mechanisms can be found in the litera-
ture for the Zhou et al. scheme(Zhou and Huang,
2011). Some papers have proposed schemes to re-
voke an unauthorized user (Baek et al., 2005; Galindo
and Herranz, 2006; Sadeghi et al., 2010). Token-
controlled public key encryption (TCPKE) is a pub-
lic key encryption scheme in which an entity cannot
decrypt an encrypted message until the entity obtains
additional information called a “token”. Beak et al.
introduced this concept and a concrete algorithm in
(Baek et al., 2005). Galindo et al. formalized a nat-
ural security goal for TCPKEs and proposed an im-
proved TCPKE. Some TCPKE schemes (Galindo and
Herranz, 2006; Sadeghi et al., 2010) exist, but no
schemes directly applicable to mobile cloud environ-
ments have been fully discussed.
1.3 Our Contributions
In this paper, we propose a key-revocable ABE
scheme for a mobile cloud environment, which real-
ize the following functionalities:
•
• User Revocation. Our scheme is based on the
concept of the ABE scheme proposed by Zhou et
al. and achieves efficient key revocation by intro-
ducing a new entity, the Token Service Provider
(TSP). The TSP distributes a “token” to a valid
user when the user requests decryption of a ci-
phertext. However, when the user is unauthorized,
the TSP does not return a valid token, which re-
vokes the user.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
52

• Attribute Hiding. We realize attribute informa-
tion hiding from a cloud server. The user termi-
nal executes a few computations in order to mask
attribute information.
Furthermore, we optimize the ABE scheme and show
that the scheme is applicable to a current mobile cloud
environment. We evaluate transaction time using an
Android mobile device and a PC, and discuss the fea-
sibility of our scheme. Security analyses based on
four security requirements are presented in this paper.
2 PRELIMINARY
In this section, we define some notations used in our
scheme.
Definition 1 (Bilinear Pairing e). Let G
0
and G
1
be
two multiplicative cyclic groups of prime order p. Let
g ∈ G
0
be the generator of G
0
and e be a bilinear
map e : G
0
× G
0
→ G
1
. The bilinear map e has the
following properties:
• Bilinearity: ∀u,v ∈ G
0
,a,b ∈ Z
p
,e(u
a
,v
b
) =
e(u,v)
ab
D
• Non degeneracy: ∀u ∈ G
0
,e(u,u) 6= 1
Definition 2 (Monotone Access Structure). Let
{P
1
,··· ,P
n
} be a set of partiesD A collection A =
2
{P
1
,···,P
n
}
is monotone if ∀B,C : if B ∈ A and B ⊆
C, then C ∈ AD An access structure is a collection
A of non-empty subsets of {P
1
,· · · ,P
n
}, i.e., A ⊆
2
{P
1
,···,P
n
}
\ {φ}. Sets contained in A are called au-
thorized sets and the sets not in A are called unautho-
rized sets.
Definition 3 (Access Tree). Let T be an access tree
representing an access structure. Each non-leaf node
of the tree represents a threshold gate, which defines
a required condition in the child nodes. If a node x is
a non-leaf node of the tree and has num
x
children and
k
x
is its threshold value, then 0 < k
x
≤ num
x
. When
k
x
= 1, it is an OR gate and when k
x
= num
x
, it is an
AND gate. Each leaf node x of the tree is described
by an attribute and a threshold value k
x
= 1. This ac-
cess structure satisfies the conditions for a monotone
access structure.
In this paper, we use functions to describe an
access tree. Child nodes of every node are num-
bered from 1 to num in the access tree. The function
index(x) returns the number of the node x, and att(x)
denotes the attribute associated with the leaf node x in
the tree. The function f(S,W) returns 1 if and only if
a set of attributes S satisfies an access policyW, other-
wise it returns 0. We denote the number of attributes
in a tree T by |T |.
!
"#$
%
(1) Encrypt
Usr
!
"#$
(2) Encrypt
Srv
!
"#$
&',
(
)
(2) GetToken
!
&',
(
)
(4) Decrypt
Srv
!
*$+
(3) GetMaskKey
!
*$+
(5) Decrypt
Usr
,-
.
/ !
Encryption Decryption
User
CSP
TSP
CSP
User
(1) GetCoupon
(
)
(
,-
.
/ 0
,-/ !
0/ !
*$+
%
,-
.
!
!
Figure 1: Outline of Encryption and Decryption Steps.
We assume that the following four prob-
lems(CDH, DDH, BDH, DBDH) are hard in our
scheme:
Definition 4 (Computational Diffie-Hellman Prob-
lem(CDH)(Boneh, 1998)). G denotes a group of a
prime order p. Let choose a,b ∈ Z
p
at random, and
given g,g
a
,g
b
. The CDH is to compute g
ab
.
Definition 5 (Decisional Diffie-Hellman Prob-
lem(DDH)(Boneh, 1998)). G denotes a group of a
prime order p. Let choose a, b, c ∈ Z
p
at random, and
given g
a
,g
b
,g
ab
, and g
c
. The DDH is to determine
whether (g
a
,g
b
,g
ab
) = (g
a
,g
b
,g
c
).
Definition 6 (Bilinear Diffie-Hellman Prob-
lem(BDH)(Boneh and Franklin, 2001; Joux, 2004)).
Given g,g
a
, g
b
, g
c
for some a,b,c ∈ Z
p
, the BDH is
to compute e(g,g)
abc
.
Definition 7 (Decisional Bilinear Diffie-Hellman
Problem(DBDH)(Boneh and Franklin, 2001)). Let
G
0
and G
1
denotes a group of a prime order p. Let
choose a,b,c ∈ Z
p
at random and g
1
∈ G
0
,g
2
∈ G
1
,
and given g
a
i
,g
b
j
,g
c
k
, and e(g
1
,g
2
)
z
, where {i, j,k} ∈
{(1,1,1),(1,1,2),(1,2,2),(2,2,2)}. The DBDH is to
determine whethere(g
1
,g
2
)
abc
= e(g
1
,g
2
)
z
.
3 OUR SCHEME
In this section, we explain our key-revocable ABE
scheme for a mobile cloud environment.
3.1 Definition
Our scheme consists of nine algorithms Setup, Key-
Generation, Encrypt
Usr
, Encrypt
Srv
, Decrypt
Usr
,
Decrypt
Srv
, GetCoupon, GetToken, GetMask Key.
There are four entities in our scheme: User, Trusted
Key Generator (TKG), Cloud Service Provider (CSP),
and Token Service Provider (TSP). The TSP is
adopted to realize a key revocation mechanism. An
overview of the encryption and decryption steps in
our scheme is shown in Figure 1.
AKey-revocableAttribute-basedEncryptionforMobileCloudEnvironments
53

Before the encryption and decryption steps, the
TKG generates a public key and users’ private keys by
running two algorithms, Setup and KeyGeneration,
and the TKG securely distributes the keys to users.
The TKG also sends IDs and related information such
as a terminal-ID to the TSP.
In the encryption step, the user first decides on a
ciphertext policy and runs Encrypt
Usr
to compute a
temporal ciphertext, then the user sends the temporal
ciphertext and the ciphertext policy to the CSP. As the
second encryption step, the CSP runs Encrypt
Srv
to
calculate a complete ABE ciphertext.
In the decryption step, the user runs Get-
MaskKey, and sends a query to the TSP to obtain
a token. The TSP checks whether the user is not
revoked, and returns a token to the user by running
GetToken. Note that the GetCoupon is assumed to
be securely computed on the TSP and the user can-
not compute an invalid ciphertext coupon to use an
altered terminal-ID. Thus, the validity of the terminal-
ID is ensured in our scheme. Next, the user requests
the CSP to run Decrypt
Srv
and the user receives a par-
tial ciphertext from the CSP, provided the user has at-
tributes that satisfy the ciphertext policy. Finally, the
user runs Decrypt
Usr
to obtain a plaintext from the
partial ciphertext.
The nine algorithms are denoted as follows;
• Setup(λ,n) → (PK, MK).
The algorithm receives a security parameter λ and
the number of possible attributes n as an input,
and it outputs two keys: a system public key PK
and a master key MK.
• KeyGeneration(MK,PK,S
u
,b
u
) → (ID
u
, SK
u
,
b
D
u
).
Let S be a group of all possible attributes in the
system. A master key MK, a public key PK, the
attributes S
u
∈ S of the user u, and a terminal-ID
b
u
of the user are input to the algorithm. The al-
gorithm outputs a user’s ID ID
u
, a secret key SK
u
of the user and token data
b
D
u
.
• Encrypt
Usr
(PK,M,W) → CT
Usr
.
The algorithm takes a public key PK, a plaintext
message M, and a decryption policy W as input,
and outputs a temporal ciphertext CT
Usr
.
• Encrypt
Srv
(PK,W,CT
Usr
) → CT.
From input of data, a public key PK, a decryption
policy W and a user-side ciphertext CT
Usr
, the al-
gorithm outputs a complete ABE ciphertext CT.
• GetCoupon(
b
C) →
b
C
b
.
From input a
b
C, the algorithm returns a ciphertext
coupon
b
C
b
.
• GetToken(ID
u
,
b
C
b
)→ T or ⊥.
A user ID ID
u
and a ciphertext coupon
b
C
b
are in-
put to the algorithm, and the algorithm outputs a
token T if the user’s ID ID
u
is not revoked, other-
wise the algorithm outputs ⊥.
• GetMaskKey(SK
u
,T,b
u
) → (
f
SK
u
,t
u
).
The algorithm computes a masked secret key
f
SK
u
and a masked value t
u
from input of a secret key
SK
u
and a token T.
• Decrypt
Srv
(
f
SK
u
,CT) → CT
Srv
.
The algorithm receives a masked secret key
f
SK
u
and a ciphertext CT, and outputs a partial cipher-
text CT
Srv
.
• Decrypt
Usr
(CT
Srv
,t
u
,T) → M.
From input of a masked value t
u
and a partial ci-
phertext CT
Srv
and a token T, the algorithm out-
puts a plaintext M.
3.2 Security Requirements
Our scheme must satisfy the following three require-
ments similar to existing schemes:
• Plaintext Confidentiality. No information about
plaintext is leaked to any adversary including a
malicious operator for a cloud service provider.
Even if all cloud servers collude after correct key
distribution, they are not able to obtain informa-
tion about plaintext.
• Unclonability. The scheme must satisfy unclone-
ability of private keys in order to prevent unautho-
rized use of the private keys. When a malicious
user copies her private key and provides the copy
to another user, the private information of the ma-
licious user is leaked. It implies that private key
cloning by a malicious user is suppressed due to
the violation of the user’s privacy. Thus, a mali-
cious user would not clone the private key.
• Privacy Preserving. A terminal-ID b that is a
unique identifier of a user should be protected,
where a temporal identifier of the user ID
u
is
leaked in a cloud service.
Furthermore, the scheme satisfies an additional re-
quirement as follows:
• Attribute Hiding. Attribute information of a user
cannot be obtained from transaction data at a rea-
sonable cost, even if other users are compromised.
In this section, we formalize the above security
requirements.
3.2.1 Plaintext Confidentiality
We define the security game for Plaintext Confiden-
tiality as follows;
SECRYPT2013-InternationalConferenceonSecurityandCryptography
54

System Setup: The challenger runs the Setup
algorithm and gives the public parameters, PK to the
adversary.
Challenge: The challenger initializes empty tables V
and L, and an empty set D. The adversary submits
two equal length messages M
0
and M
1
. In addition
the adversary gives a value W
∗
enc
. The challenger
flips a random coin c, and encrypts M
c
under W
∗
enc
.
The challenger generates ID
0
and stores the entry
(0,r,r
0
,S
0
,
f
SK
0
,t
0
) in the table V. The resulting
ciphertext CT
∗
and CT
∗
Srv
, ID
0
and
f
SK
0
are given to
the adversary.
Game: The challenger sets an integer j = 0. The
game is repeated with the restrictions that the adver-
sary cannot
• trivially obtain a private key for the challenge
ciphertext. That is, it cannot issue a corrupt
query that would result in a value S
0
that satisfies
f(S
0
,W
∗
enc
) = 1 being added to D.
• issue a trivial decryption queries. That is,
Decrypt
Usr
queries will be answered, except in the
case where the response would be either M
0
or
M
1
, then the challenger responds with the special
message test instead.
Proceeding adaptively, the adversary can repeat-
edly make any of the following queries:
• Create(PK, S
j
): The challenger sets j := j + 1,
and b
j
= j. It runs the KeyGeneration algorithm
to obtain SK
j
,ID
j
, and
c
D
j
, and then it stores a tu-
ple of j, ID
j
, and
c
D
j
in the table L. Next, it runs
the GetMaskKey algorithm to obtain the pair
(SK
j
,
f
SK
j
,t
j
) corresponding to attributes S
j
of a
user j, and stores the entry (j,r, r
j
,S
j
,SK
j
,
f
SK
j
,t
j
)
in the table V. Finally, it returns to the adversary
the value j, the masked secret key
g
SK
j
, and the ID
ID
j
.
• Corrupt(i): If there exists an i-th entry in table V
and i 6= 0, then the challenger obtains the entry
(i,r, r
i
,S
i
,SK
i
,
f
SK
i
,t
i
). If S
i
6= S
0
, then the chal-
lenger sets D := D∪ {S
i
} and returns the entry to
the adversary including the private key SK
i
. If no
such entry exists or S
i
= S
0
, then it returns ⊥.
• GetToken(i,
b
C): Note that
b
C is included in CT. If
i exists in the table L, then the challenger obtains
the entry (i, ID
i
,
b
D
i
) and returns the token T
i
and
ID
i
to the adversary. If no such entry exists, then
it returns ⊥.
• Encrypt(i,PK,W
enc
,M): The challenger runs the
algorithms Encrypt
Usr
and Encrypt
Srv
. The
challenger then returns CT, and CT
Usr
.
• Decrypt
Srv
(
f
SK
i
,CT): The challenger returns
the output CT
Srv
of the decryption algorithm
Decrypt
Srv
on input (
f
SK
i
,CT) to the adversary.
• Decrypt
Usr
(i,CT
Srv
,T
i
): If there exists an i-th en-
try in the table V, then the challenger obtains the
entry (i,r,r
i
,S
i
,SK
i
,
f
SK
i
,t
i
), and it returns to the
adversary the output M of the decryption algo-
rithm Decrypt
Usr
on input (SK, T
i
,t
i
,CT). If no
such entry exists, then it returns ⊥.
Guess: The adversary outputs a guess c
0
of c.
We should consider a security model for ABE that
supports two-stage encryption and decryption on a
client terminal and a cloud server. The general notion
of security against chosen-ciphertextattacks (CCA) is
somewhat too strong and it cannot be directly applied
to the mobile cloud environment. We thus use a re-
laxed security notion called replayable CCA security
(Canetti et al., 2003), which allows modifications to
the ciphertext but does not allow any changes to the
underlying message in a meaningfulway. The scheme
achieves Plaintext confidentiality, where the scheme
satisfies the following definition.
Definition 8 (RCCA-secure(Green et al., 2011)).
The ABE scheme is RCCA-secure (or secure against
replayable chosen-ciphertext attacks) under the
selective-ID model, if all polynomial time adversaries
have at most a negligible advantage in the game de-
fined above.
3.2.2 Uncloneability
The scheme can be achieved Unclonability where the
scheme satisfies the following definition.
Definition 9 (Strong Uncloneability(Hinek et al.,
2008)). A polynomial-time algorithm F exists and it
executes the GetToken oracle, the Decrypt
Srv
oracle,
and the following functions:
F
{GetToken,Decrypt
Srv
}
(PK,
b
C, i,
b
D
i
) =
Decrypt
Usr
(b
i
,Decrypt
Srv
(i,CT),t
i
,GetToken(i,
b
C))
If an extractor algorithm χ can compute a user
identifier ID and the terminal-ID b from a given
f
SK
i
,CT,ID
i
,t
i
,
b
C, and T by O(|B|) computation, it is
said that the ABE scheme satisfies Strong Unclone-
ability. Note that |B| is the domain of terminal-IDs of
all users.
3.2.3 Privacy Preserving
The scheme can achieve Privacy Preserving where
the scheme satisfies the following definition.
AKey-revocableAttribute-basedEncryptionforMobileCloudEnvironments
55

Definition 10 (Privacy Preserving(Hinek et al.,
2008)). Let MK, PK, T, S
u
be a master key, a pub-
lic key, a token, and all attributes of a user u. If
Pr[b
u
|PK,MK,ID
u
,S
u
,T] = Pr[b
u
|ID
u
,S
u
],
then the ABE scheme satisfies Privacy Preserving.
3.2.4 Attribute Hiding
The objective of an adversary A is to guess at-
tribute values embedded in a ciphertext. For the
sake of simplicity, we consider the case where an
access policy of the ciphertext includes an attribute,
without limiting the generality of the security re-
quirement. The scheme can achieve attribute hid-
ing where the scheme satisfies the following defini-
tion. This definition is similar to a security defini-
tion of password-based key-exchange protocols (Bel-
lare et al., 2000). That is, the adversary cannot engage
in off-line searching of the attribute using transaction
data.
Definition 11 (Attribute Hiding). Let q
D
be the num-
ber of decrypt queries. Let the size of S
u
be N. If the
success probability of attribute guessing by an adver-
sary A is bounded by q
D
/N, then the ABE scheme
satisfies attribute hiding.
3.3 Construction
In this section, we explain our scheme in detail.
Setup(λ) → (PK,MK). Let G
0
and G
1
be bilinear
groups of prime order p (where p is a λ bit prime),
e : G
0
× G
0
→ G
1
be a bilinear map, and g be a gen-
erator of G
0
. With randomly chosen a ∈ Z
p
, the sys-
tem public key PK and the system master key MK are
given by, PK = (g,e(g,g)
a
,e,G
0
,G
1
),MK = g
a
KeyGeneration(MK, PK, S
u
,b
u
) → (ID
u
, SK
u
,
b
D
u
)
Let H : {0, 1}
∗
→ G
0
be the collision-resistant hash
function. A random number r ∈ Z
p
and r
j
∈ Z
p
are
assigned to each attribute j ∈ S
u
. The decryption key
for the user-ID ID
u
is given by,
SK
u
= (∀ j ∈ S : D
j
= g
r
· H( j)
r
j
,D
′
j
= g
r
j
)
The TKG computes
b
D
u
= g
(a+r)
b
u
and sends (ID
u
,
b
D
u
)
to the TSP.
Encrypt
Usr
(PK,M,T
Usr
) → CT
Usr
. A polynomial
q
R
∈ Z
p
[X],deg(q
R
) = 1 is randomly chosen, and
s = q
R
(0),s
1
= q
R
(1),s
2
= q
R
(2) are calculated. Let
Y be set of leaf nodes of a T with a “DO” node. The
user calculates CT
Usr
as follows;
CT
Usr
= (s
1
,T
U
,
b
C = g
s
,
e
C = M · e(g,g)
as
;
∀y ∈ Y : C
y
= g
q
y
(0)
,C
′
y
= H(att(y))
q
y
(0)
)
Encrypt
Srv
(PK,T ,CT
Usr
) → CT. Polynomials q
x
∈
Z
p
[X] for all nodes in T without a root node and a
“DO” node are randomly chosen. The polynomials
are chosen in a top-down manner from the start node
θ which is the highest node without a root node and
a “DO” node. For each node x under θ, the degree
d
x
of each polynomial q
x
is assigned a value less than
the threshold value k
x
; for example, d
x
= k
x
− 1. For
the start node θ, a polynomial is selected to satisfy
q
θ
(0) = s
1
. Then, for each node under θ, a polynomial
is selected to satisfy q
x
(0) = q
parent(x)
(index(x)) using
randomly chosen coefficients without constant terms.
Let Y
U
be set of leaf nodes of a T without a “DO”
node. CT
Srv
is calculated as follows:
CT
Srv
= (∀y ∈ Y
U
: C
y
= g
q
y
(0)
,C
′
y
= H(att(y))
q
y
(0)
)
For Y that is the set of all leaf nodes of T , CT is
calculated as follows:
CT = (T
Srv
,
e
C,
b
C;∀y ∈ Y : C
y
= g
q
y
(0)
,C
′
y
= H(att(y))
q
y
(0)
)
GetMaskKey(SK
u
,T,b
u
) → (
f
SK
u
,t
u
,
b
C
b
). t
u
∈ Z
p
is randomly chosen and
f
SK
u
is calculated as follows;
f
SK
u
= (∀ j ∈ S
u
: D
j
= (g
r
· H( j)
r
j
)
t
u
,D
′
j
= (g
r
j
)
t
u
)
GetCoupon(
b
C) →
b
C
b
For an input C, a ciphertext coupon
b
C
b
is computed
thus:
b
C
b
=
b
C
b
GetToken(ID
u
,
b
C
b
) → T or ⊥. The token server
outputs a token T = e(
b
C
b
,
b
D
u
) = e(g
b
u
s
,g
a+r
b
) =
e(g,g)
s(a+r)
where the user-ID ID
u
is not revoked. If
not, the server outputs ⊥. In our scheme, key revoca-
tion revokes ID
u
and removes
b
D
u
from the data stored
in the TSP.
Decrypt
Srv
(
f
SK
u
,CT
′
) → CT
Srv
. CT
′
is described as
follows:
CT
′
= (T ,
e
C = M · e(g,g)
as
,
∀y ∈ Y
U
∪Y
DO
: C
y
= g
q
y
(0)
,C
′
y
= H(att(y))
q
y
(0)
)
Let ρ(ℓ) be (ℓ,parent(ℓ),parent(parent(ℓ)),··· , R) for
all ℓ ∈ T . z
ℓ
is calculated as follows:
z
ℓ
=
∏
x∈ρ(ℓ),x6=R
∆
i,S
(0),where i = index(x),
=
∏
x∈ρ(ℓ),x6=R
∏
j∈S
u
, j6=i
− j
i− j
SECRYPT2013-InternationalConferenceonSecurityandCryptography
56

Finally, A is calculated as:
A =
∏
ℓ∈L,i=att(ℓ)
e(D
i
,C
ℓ
)
e(D
′
i
,C
′
ℓ
)
z
ℓ
= e(g,g)
rst
u
,
and CT
Srv
= (A,
e
C) is sent to the user.
Decrypt
Usr
(CT
Srv
,t
u
,T) → M. M is calculated as
follows:
e
CA
1
t
u
T
=
Me(g,g)
as
· e(g,g)
rs
(e(g,g)
s(a+r)
)
=
Me(g,g)
(a+r)s
e(g,g)
(a+r)s
= M
4 ANALYSIS
In this section, we analyze the security and perfor-
mance of the proposed scheme.
4.1 Security Analysis
In this subsection, we present proofs of scheme secu-
rity with regard to three security requirements: Plain-
text Confidentiality, Strong Uncloneability, and Pri-
vacy Preserving.
4.1.1 Plaintext Confidentiality
An objective of the adversary is to output a correct
value of c from a given ciphertext and related transac-
tion data. From the adversary’s viewpoint, challenge
plaintext M
c
is embedded in
e
C of CT
∗
Srv
. It is hard
to remove t
0
from A
0
of CT
∗
Srv
, if the BDH problem
holds. Thus, the adversary cannot obtain M
c
from
the ciphertext CT
∗
Srv
to execute the Decrypt
Usr
algo-
rithm in the game. The adversary cannot obtain s
and g
a
with feasible computational costs in the game,
and it is difficult for the adversary to compute the
value of e(g,g)
as
. Thus, for the adversary, two cipher-
texts M
0
e(g,g)
as
and M
1
e(g,g)
as
are indistinguish-
able with non-negligible success probability. First,
we prove that our scheme has plaintext confidentiality
where the decisional BDH assumption holds.
Theorem 1. Our scheme has plaintext confidentiality
under the decisional BDH assumption.
Proof 1. (Sketch) Suppose that we have an adver-
sary A with a non-negligible advantage ε in the
selective-ID game against our construction. We build
a challenger B that plays the decisional BDH prob-
lem. First, the challenger takes on the BDH chal-
lenge g,g
α
,g
β
,g
γ
,Y
w
. The challenger outputs w = 0
where Y
w
is guessed as Y
w
= (g,g)
αβ
; otherwise out-
puts w = 1. As the system setup, the challenger runs
the setup algorithm and gives PK to the adversary.
The adversary submits two messages M
0
and M
1
as
a challenge. The challenger flips a random coin c
and make CT
∗
and CT
∗
Srv
including
b
C,
e
C, and A:
b
C = g
βr
′
,
e
C = M
c
· e(g
βr
′
,g
a
), and A = (Y
w
)
rr
′
, where
r
′
is a randomly chosen from Z
p
. The two cipher-
texts CT
∗
and CT
∗
Srv
, ID
0
, and
f
SK
0
are given to the
adversary. The challenger stores the tuple (0, r
′
, M
c
,
CT
∗
, CT
∗
Srv
) in the table E. In the game, the chal-
lenger B runs the adversary A at described in 3.2.
For the KeyGeneration queries, the challenger com-
putes D
j
= g
αr
· H( j)
r
j
and
b
D = (g
αr
· g
a
)
1/b
for a
randomly chosen r and r
j
. If the Decrypt
Srv
(
f
SK
0
,CT)
is received, the challenger obtains the entry of i = 0
and decrypts CT to obtain M. The challenger then
returns CT
Srv
= ((Y
w
)
rr
′
,Me(g,g
αr
)
a
) and the tuple
(0, r
′
, M, CT, CT
Srv
) to the table E. The challenger
returns CT
∗
Srv
stored in the table E to the adversary,
when the adversary sends the Decrypt
Srv
(
f
SK
0
,CT
∗
)
to the challenger. Note that the adversary cannot dis-
tinguish whether A = (Y
w
)
rr
′
or A = e(g,g)
rst
except
in the case where the adversary has obtained t
0
. For
the Decrypt
Usr
(0,CT
Srv
,T
0
), the challenger obtains M
from the table E and returns M, if the entry (0, r
′
,
M, CT, CT
Srv
) exists in the table E; otherwise it re-
turns ⊥. Finally, the adversary outputs c
0
at the guess
stage. The challenger outputs w = 0 where c
0
= c;
otherwise outputs w = 1. The adversary outputs a
correct bit c
0
= c with the non-negligible probabil-
ity ε where Y
w
= (g,g)
αβγ
; otherwise randomly out-
puts the correct bit with the probability 1/2. The
challenger B can play the decisional BDH game with
non-negligible advantage. This result contradicts the
assumption. Thus, the ABE scheme has plaintext con-
fidentiality under the decisional BDH assumption.
Note on Collusion. The data structures of ciphertext
and a private key in our scheme are the same as those
of tk-CP-ABE proposed by Hinek et al. (Hinek et al.,
2008). Our scheme can be viewed as a variant of tk-
CP-ABE. In our scheme, the access policy consists of
two sub-trees T
S
and T
DO
. T
DO
contains only a sin-
gle attribute DO to reduce the computational cost. A
user randomly selects a 1-degree polynomial q
x
and
sets s = q
x
(0),s
1
= q
x
(1),s
2
= q
x
(2). Then, the user
sends {s
1
,T } to CSP. CSP cannot know q
x
without s
and s
2
. The servers get e(g,g)
αs
1
easily since e(g,g)
α
is a public parameter. A decryption server knows
e(g,g)
r
′
st
, e(g,g)
r
′
s
1
, e(g,g)
r
′
s
2
, and e(g,g)
r
′
s
through
AKey-revocableAttribute-basedEncryptionforMobileCloudEnvironments
57

the Decrypt
Srv
function. An encryption server has the
values s
1
and e(g,g)
αs
1
,s
1
, but the values of s
2
and
s are in unknown. The decryption server obtains all
blinded private keys as well as the blinded private key
f
SK
u
′
of user u
′
. Note that
f
SK
u
′
is not a valid pri-
vate key since the
e
D
u
is embedded with a random
parameter t
u
. Since t
u
is the exponent of the gener-
ator g, the derivation of t
u
is equivalent for solving
the DLP problem that is considered to be hard. Thus,
the hardness of DLP on G
0
and G
1
are given, and
cloud servers cannot derivee(g,g)
αs
2
or e(g,g)
αs
even
if they collude.
4.1.2 Uncloneability
If a private key is easily copied from an inner user to
an adversary, the adversary can access the user’s data.
Cloning a private key should be prevented. We prove
our scheme has Strong Uncloneability (Hinek et al.,
2008).
Theorem 2. Our scheme has Strong Uncloneability.
Proof 2. (Sketch) First, an extractor χ computes the
plaintext M using the algorithm F . Since the ex-
tractor χ must access GetToken, it can request T =
GetToken(i,
b
C), and χ computes A = e(g,g)
rst
from
PK, CT, SK
′
. Since M =
e
CA
1
t
i
T
, χ tries to check all the
values of b
i
∈ B until the above equation is satisfied.
Thus, χ computes b
i
within time complexity (|B|) in
the worst case.
4.1.3 Privacy Preserving
Personal information should remain private even if a
key generator is corrupted and colludes with a token
server. We prove that our scheme preserves privacy
(Hinek et al., 2008).
Theorem 3. Our scheme is privacy preserving.
Proof 3. (Sketch) Since PK, MK are chosen indepen-
dently of b
u
,
Pr[b
u
|PK,MK,ID
u
,S
u
,
ˆ
C] = Pr[b
u
|ID
u
,S
u
,
ˆ
C]
holds. Next, recall that
ˆ
D
u
= g
(a+r)
b
u
and the order of
G is q. It follows that
Pr[b
u
|ID
u
,S
u
,
ˆ
D
u
] = Pr[b
u
|ID
u
,S
u
,
(a+ r)
b
u
mod p].
Since a,r,b are independently chosen,
Pr[b
u
|ID
u
,S
u
,
(a+ r)
b
u
mod p] = Pr[b
u
|ID
u
,S
u
]
holds. Thus, our scheme is privacy preserving.
4.1.4 Attribute Hiding
We show that our scheme satisfies Attribute Hiding.
Theorem 4. Our scheme satisfies Attribute Hiding.
Proof 4. (Sketch) Assume for simplicity there is just
one attribute j
a
that is needed to decrypt a ciphertext
CT. The value C
′
y
= H(att(y))
q
y
(0)
is denoted as g
x
.
Thus, it is difficult to distinguish the attribute j
a
using
C
y
andC
′
y
where the decisional Diffie-Hellman (DDH)
problem is hard. We view an adversary A as trying to
guess the attribute using queries defined in 3.2, and
consider a set of remaining candidate attributes in the
game. The size of the set of remaining attributes de-
creases by at most one with each oracle query. The
adversary decreases the candidate attributes to use
the Decrypt query as follows. First, the adversary ob-
tains a pair of CT
Srv
= (A,
e
C) for the challenge ci-
phertext CT to use the Decrypt
Srv
query. Next, the
adversary sets a guessed attribute j
′
a
to
f
SK and sends
a Decrypt
Srv
query to an entity. If the entity outputs
the correct pair of CT
Srv
= (A,
e
C), then j
′
a
= j
a
; oth-
erwise the adversary removes j
′
a
from the candidate
attributes. The success probability of the adversary is
q
D
/N where the number of queries is bounded by q
D
.
In addition to proofs for the security requirements,
we consider the feasibility of the user revocation pro-
cess.
4.1.5 User Revocation
Our proposal scheme realizes a user revocation. A
system administrator can revoke malicious users by
removing user’s entry(i.e. (ID
u
,
b
D
u
)) from the token
server’s database.
b
D
u
is a power of generator g, and
the exponent of
b
D
u
is randomized. Therefore, the user
can not recover the entry because of the discrete log-
arithm problem(DLP). Since a user needs a decryp-
tion token in order to decrypt any ciphertext (using a
private key of the user), the user can not obtain any
ciphertext after the revocation of the user.
4.2 Analysis of Communication Cost
In this section, we analyze communication cost of
our scheme. In the Table 1, we show the parameter
sizes. The parameter h represents the maximum num-
ber of attributes. The symbol |T
h
| denotes the size of
a tree using h attributes (nearly h|Z
p
|). The largest
part of the communication cost is the transaction that
involves sending ciphertextCT
Usr
from the user to the
server. The size of CT
Usr
approaches asymptotically
estimated as O(h
2
|Z
p
|). The communication cost is
proportional to h
2
similar to that of existing schemes.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
58
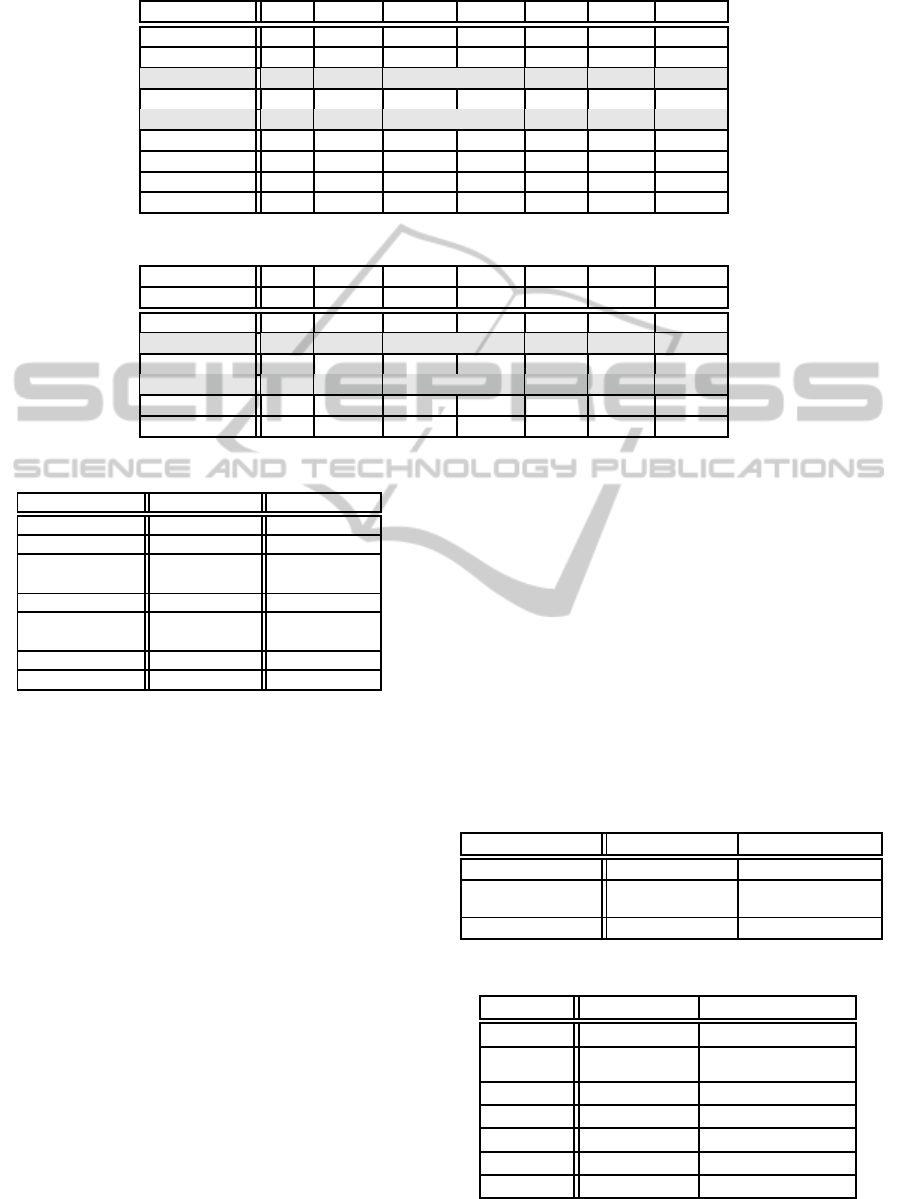
Table 2: Computational cost of our scheme.
Hash Mul G
0
Exp G
0
Mul G
1
Inv G
1
Exp G
1
Pairing
Setup - - 1 - - 1 1
KeyGeneration |S
u
| |S
u
| 2|S
u
| + 2 - - - -
Encrypt
Usr
1 - 4 1 - 1 -
Encrypt
Srv
|T | - 2|T | - - - -
Decrypt
Usr
- - - 2 1 1 -
Decrypt
Srv
- - - 2|T | |T | |T | 2|T | + 1
GetToken - - - - - - 1
GetCoupon - - 1 - - - -
GetMaskKey - - |T | - - - -
Table 3: Computational Cost of Zhou’s scheme.
Setup - - 3 - - 1 1
Hash Mul G
0
Exp G
0
Mul G
1
Inv G
1
Exp G
1
Pairing
KeyGeneration |S
u
| |S
u
| 2|S
u
| + 1 - - - -
Encrypt
Usr
1 - 3 1 - 1 -
Encrypt
Srv
|T | - 2|T | - - - -
Decrypt
Usr
- - - 2 1 1 -
Decrypt
Srv
- - - 2|T | |T | |T | 2|T | + 1
GetMaskKey - - 1 - - - -
Table 1: Sizes of Data.
Data Size Direction
Public key PK |G
0
| + |G
1
| TA → User
Private Key SK |Z
p
| + 2h|G
0
| TA → User
Ciphertext CT
Usr
|Z
p
| + h|T
h
|
+4|G
0
| + |G
1
|
User → Server
Ciphertext CT
Srv
2|G
1
| Server → User
Ciphertext CT
|T
h+1
| + 4|G
0
|
+|G
1
|
Server (local)
Token T |G
1
| TSP → User
Input of Token
ˆ
C |G
0
| User → TSP
4.3 Performance Analysis
Our scheme reduces the computational cost on a mo-
bile device; the computational cost of Encrypt
Usr
,
Decrypt
Usr
is less than that of the existing scheme
(Hinek et al., 2008).
The function GetMaskKey is pre-computed be-
fore computing Decrypt
Usr
and it requires O(1) com-
putation. The computational cost of Decrypt
Usr
is
also O(1). Thus, the computational cost of decryp-
tion on a mobile device is O(1).
The total computational cost of the whole process
is O(|T |). The worst case is that where N attributes,
and in that case, the total computational cost is esti-
mated to be O(N). Here we show the estimation of
the computational cost of each operation in Table 2.
The symbol S
u
is the set of attributes allocated to a
user u.
We show the computationalcost of Zhou’s scheme
in Table 3. The computational costs of functions
KeyGeneration, Encrypt
Usr
, and GetMaskKey in
our scheme are somewhat larger than those in Zhou’s
scheme. GetMaskKey can be pre-computed before
decryption of any data. The increases of other func-
tions are constant time; in the view of an asymptotic
estimation, these increases are negligible. We con-
clude that the increases in computational cost from
adding key revocation are negligibly small in our
scheme.
4.4 Implementation of Primitives
We implemented a Reduced Modified Tate (RMT)
pairing to estimate the cost of our scheme. Our tar-
get devices are a PC and an Android smartphone as
shown in the Table 5.
Table 4: Parameters.
89 bit security 128 bit security
m 193 509
Irreducible Polynomial f(x) = x
193
− x
64
+ 1
f(x) = x
509
− x
318
−x
191
+ x
127
+ 1
Oder of Z
p
p = 3
193
− 3
97
+ 1 p = (3
509
− 3
255
+ 1)/7
Table 5: Target Devices.
PC Mobile Devise(MD)
Model - HTC Sensation XE
CPU
Intel Xeon
W3680 3.33GHz
Qualcomm Snapdragon
MSM8260 1.5GHz
Core Hexa-core Dual-core
Word length 64-bit 32-bit
Memory 16GB 768MB
OS CentOS6.0 Android 2.3.4
Compiler GCC4.4.4 Android NDK r7
AKey-revocableAttribute-basedEncryptionforMobileCloudEnvironments
59
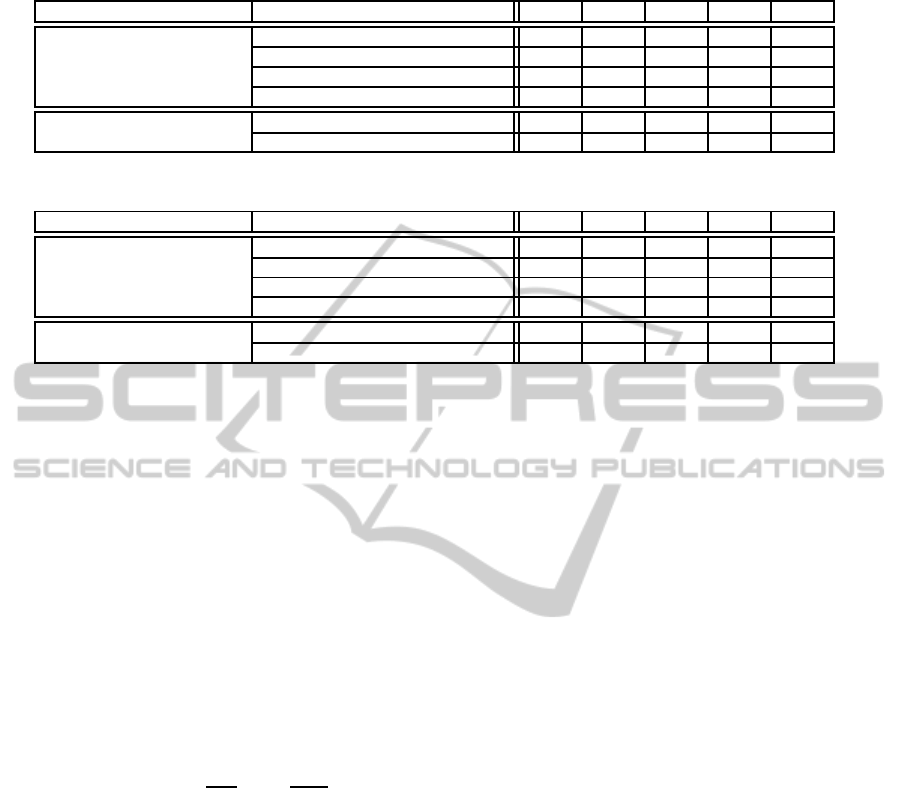
Table 6: Transaction Time in 89-bit security per function (msec).
The number of attributes (AND condition) 1 2 3 4 5
Our scheme Encrypt
Usr
: Android 157.29 133.88 149.25 130.10 130.94
Encrypt
Srv
: PC 7.28 15.30 22.72 29.96 32.02
Decrypt
Usr
: Android 29.18 30.40 32.82 32.16 34.28
Decrypt
Srv
: PC 17.46 24.47 26.64 39.56 46.82
CP-ABE(Bethencourt et al., 2007) Encrypt : Android 95.9 140.2 184.5 228.8 273.1
Decrypt : Android 96.9 169.7 242.5 315.3 388.1
Table 7: Transaction Time in 128-bit security per function (msec).
The number of attributes (AND condition) 1 2 3 4 5
Our scheme Encrypt
Usr
: Android 557.99 556.95 586.17 558.71 557.86
Encrypt
Srv
: PC 51.48 90.14 117.89 148.13 184.87
Decrypt
Usr
: Android 185.28 189.24 193.12 184.27 193.00
Decrypt
Srv
: PC 115.54 174.10 244.51 286.07 322.59
CP-ABE(Bethencourt et al., 2007) Encrypt : Android 1079 1599 2119 2639 3159
Decrypt : Android 743 1302 1861 2420 2979
Our implementation is similar to that of Beuchat
et al. (Beuchat et al., 2010). We adopted a design
for the RMT pairing based on supersingular elliptic
curves defined over a finite field of characteristic three
and select the parameters for two security levels: 89-
bit security and 128-bit security.
We consider the supersingular curves E(F
3
m
) with
embedding degree k = 6 defined as follows;
E(F
3
m
) = {(x,y) ∈ F
3
m
× F
3
m
| y
2
= x
3
− x+ 1} ∪ {∞}.
The order of E(F
3
m
), #E(F
3
m
) is calculated as
#E(F
3
m
) = 3
m
+ 1 + b
′
3
(m+1)/2
, where b
′
is defined
as follows:
b
′
=
1 (mod 12) if m ≡ 1,11
−1 (mod 12) if m ≡ 5,7
The RMT pairing ˆe
r
is defined using η
T
pairing as
follows:
ˆe
r
(P,Q) = η
T
(
− µb
′
3
3m−1
2
P,Q)
3
6m
−1
N
,
where P, Q ∈ E(F
3
m
). The orders of groups G
0
CG
1
are #E(F
3
m
), #F
∗
3
6m
respectively.
The η
T
pairing consists of a main loop and a final
exponentiation. We used a loop unrolling technique
(Beuchat et al., 2010) for the main loop, and the fi-
nal exponentiation calculation was carried out accord-
ing to (Shirase et al., 2008). The computational cost
of a multiplication over F
3
m
is dominant in the η
T
pairing. We implemented a window method (Brauer,
1939) that was the fastest multiplication algorithm for
a characteristic three field, and selected a window size
of w = 4. We selected the parameters for two security
levels as shown in the Table 4.
4.5 Evaluation Result
We implemented our ABE system on the target de-
vices in Table 5. Two functions, Encrypt
Usr
and
Decrypt
Usr
, were implemented on the smartphone
and two other functions, Encrypt
Srv
and Decrypt
Srv
,
were implemented on the PC. Evaluation results of
the transaction time of the four functions for 89-bit
and 128-bit security settings are shown in Table 6
and Table 7, respectively. An access policy that de-
fines an access condition AND of all w attributes
(w = 1,2,3,4,5) was used for the evaluation. The ac-
cess policy is the worst case for the transaction time
where we use w attributes in the system. Constant
transaction time is required to compute two functions
on the smartphone, Encrypt
Usr
and Decrypt
Usr
, and
transaction time of Encrypt
Srv
and Decrypt
Srv
are
proportional to the number of attributes; but are neg-
ligibly small for the PC. We compare our results with
a CP-ABE scheme proposal by Bethencourd et al.
(Bethencourt et al., 2007), which is a conventional
CP-ABE and requires that the smartphone must ex-
ecute all calculations for encryption and decryption.
As evaluation results of primitive functions, the trans-
action times of the encryption and decryption of the
CP-ABE using 5 attributes are estimated to be 271.3
msec and 388.1 msec for 89-bit security and 3159
msec and 2979 msec for 128-bit security respectively.
These results show that our scheme is faster than the
scheme (Bethencourt et al., 2007) where all functions
are implemented on the smartphone, and are applica-
ble to a mobile cloud environment.
5 CONCLUSIONS
In this paper, we proposed a new ABE scheme appli-
cable to mobile cloud computing environments. The
computational cost on a mobile device is O(1), and
cloud services can securely provide most computa-
SECRYPT2013-InternationalConferenceonSecurityandCryptography
60

tions required for the ABE scheme. Furthermore, the
scheme includes a key revocation mechanism for the
private keys and an attribute hiding mechanism. The
transaction time of our encryption algorithm is within
150 msec for 89-bit security and about 600 msec for
128-bit security on the mobile device, respectively.
Similarly, the transaction time of the decryption al-
gorithm is within 50 msec for 89-bit security and 200
msec for 128-bit security. The evaluation of transac-
tion time demonstrated that our scheme is feasible for
mobile cloud services using current smartphones.
REFERENCES
Amazon (2012). Amazon Web Services. http://aws. ama-
zon.com/.
Aranha, D., L´opez, J., and Hankerson, D. (2010). High-
speed parallel software implementation of the η
T
pair-
ing. In Topics in Cryptology - CT-RSA 2010, volume
5985 of Lecture Notes in Computer Science, pages
89–105. Springer.
Baek, J., Safavi-Naini, R., and Susilo, W. (2005). Token-
controlled public key encryption. In Information
Security Practice and Experience, volume 3439 of
Lecture Notes in Computer Science, pages 386–397.
Springer.
Bellare, M., Pointcheval, D., and Rogaway, P. (2000). Au-
thenticated key exchange secure against dictionary at-
tacks. pages 139–155. Springer.
Bethencourt, J., Sahai, A., and Waters, B. (2007).
Ciphertext-policy attribute-based encryption. In Pro-
ceedings of the 2007 IEEE Symposium on Security
and Privacy, Security and Privacy 2007, pages 321–
334. IEEE Computer Society.
Beuchat, J., Gonzalez-Diaz, J., Mitsunari, S., Okamoto,
E., Rodriguez-Henriquez, F., and Teruya, T. (2010).
High-speed software implementation of the optimal
Ate pairing over Barreto-Naehrig curves. In Pairing-
Based Cryptography - Pairing 2010, volume 6487
of Lecture Notes in Computer Science, pages 21–39.
Springer.
Boneh, D. (1998). The decision diffie-hellman problem.
pages 48–63. Springer.
Boneh, D. and Franklin, M. (2001). Identity-based encryp-
tion from the weil pairing. In Advances in Cryptol-
ogy - CRYPTO 2001, volume 2139 of Lecture Notes
in Computer Science, pages 213–229. Springer.
Brauer, A. (1939). On addition chains. In Bull. Amer. Math.
Soc., volume 45, pages 736–739.
Canetti, R., Krawczyk, H., and Nielsen, J. (2003). Relaxing
chosen-ciphertext security. In Advances in Cryptol-
ogy - CRYPTO 2003, volume 2729 of Lecture Notes
in Computer Science, pages 565–582. Springer.
Cloud Security Alliance (2009). Security guidance
for critical areas of focus in cloud computing.
http://tinyurl.com//ycrchqj.
European Network and Information Security
Agency (2010). Cloud computing risk assess-
ment. http://www.enisa. europa.eu/act/rm/files/
deliverables/cloud-computing-risk-assessment/at
down
load/fullReport.
Galindo, D. and Herranz, J. (2006). A generic construc-
tion for token-controlled public key encryption. In
Di Crescenzo, G. and Rubin, A., editors, Financial
Cryptography and Data Security, volume 4107 of
Lecture Notes in Computer Science, pages 177–190.
Springer.
Google (2012). Google App for Buiziness. http://
www.google.com/apps/intl/en/business/index.html.
Goyal, V., Pandey, O., Sahai, A., and Waters, B. (2006).
Attribute-based encryption for fine-grained access con-
trol of encrypted data. In Proceedings of the 13th ACM
conference on Computer and communications security,
CCS ’06, pages 89–98. Algorithms and Computation in
Mathematics.
Green, M., Hohenberger, S., and Waters, B. (2011). Out-
sourcing the decryption of ABE ciphertexts. In Pro-
ceedings of the 20th USENIX conference on Security,
SEC’11, pages 34–34. USENIX Association.
Hinek, M. J., Jiang, S., Safavi-Naini, R., and Shahandashti,
S. F. (2008). Attribute-based encryption with key
cloning protection. Cryptology ePrint Archive, Report
2008/478.
Joux, A. (2004). A one round protocol for tripartite
diffie?hellman. Journal of Cryptology, 17:263–276.
Lewko, A., Okamoto, T., Sahai, A., Takashima, K., and
Waters, B. (2010). Fully secure functional encryp-
tion: Attribute-based encryption and (hierarchical) in-
ner product encryption. In Advances in Cryptology -
EUROCRYPT 2010, volume 6110 of Lecture Notes in
Computer Science, pages 62–91. Springer.
Naehrig, M., Niederhagen, R., and Schwabe, P. (2010). New
software speed records for cryptographic pairings. In
Progress in Cryptology - LATINCRYPT 2010, volume
6212 of Lecture Notes in Computer Science, pages 109–
123. Springer.
NIST (2009). The nist definition of cloud comput-
ing. http://csrc.nist.gov/publications/nistpubs/800-145/
SP800-145.pdf.
Sadeghi, A., Schneider, T., and Winandy, M. (2010). Token-
based cloud computing. In Trust and Trustworthy Com-
puting, volume 6101 of Lecture Notes in Computer Sci-
ence, pages 417–429. Springer.
Sahai, A. and Waters, B. (2005). Fuzzy identity-based en-
cryption. In Advances in Cryptology - EUROCRYPT
2005, volume 3494 of Lecture Notes in Computer Sci-
ence, pages 557–557. Springer.
Scott, M. (2011). On the efficient implementation of pairing-
based protocols. Cryptology ePrint Archive, Report
2011/334.
Shirase, M., Takagi, T., and Okamoto, E. (2008). Some effi-
cient algorithms for the final exponentiation of η
T
pair-
ing. IEICE Transactions, 91-A(1):221–228.
Waters, B. (2011). Ciphertext-policy attribute-based encryp-
tion: An expressive, efficient, and provably secure real-
ization. In Public Key Cryptography - PKC 2011, vol-
ume 6571 of Lecture Notes in Computer Science, pages
53–70. Springer.
Zhou, Z. and Huang, D. (2011). Efficient and secure data stor-
age operations for mobile cloud computing. Cryptology
ePrint Archive, Report 2011/185.
AKey-revocableAttribute-basedEncryptionforMobileCloudEnvironments
61
