
On the Security of the XOR Sandwiching Paradigm for Multiple Keyed
Block Ciphers
Ruth Ng Ii-Yung
1
, Khoongming Khoo
2
and Raphael C.-W. Phan
3
1
The College, University of Chicago, 5801 S. Ellis Avenue, Chicago IL 60637, U.S.A.
∗
2
DSO National Laboratories, 20 Science Park Drive, S118230, Singapore City, Singapore
3
Faculty of Engineering, Multimedia University, Persiaran Multimedia, 63100 Cyberjaya, Selangor, Malaysia
Keywords:
Data-encryption Standard, Block Ciphers, Meet-in-the-Middle, Related-key.
Abstract:
While block cipher design is relatively mature, advances in computational power mean that the keylength
of block ciphers, upon which the security relies entirely, becomes less resistant to cryptanalysis over time.
Therefore, the security for a block cipher with a particular keylength typically is seen to last for at most some
decades. One common approach to strengthen a block cipher’s security is based on increasing its keylength.
In the literature, two strategies have emerged: multiple keyed multiple encryption and multiple keyed XOR
sandwiching. Known attacks on these such as Meet-in-the-Middle(Merkle and Hellman, 1981; van Oorschot
and Wiener, 1991; Lucks, 1998) and Related-Key (J. Kelsey and Wagner, 1996; Choi et al., 1996; Vaudenay,
2011; Phan, 2004) attacks, show that Triple Encryption is significantly weaker than a brute-force attack would
suggest, especially for block ciphers with small keys, such as the Data Encryption Standard (DES). This paper
provides a comprehensive analysis on the security of the XOR sandwiching paradigm against known attacks
for the case of multiple keyed triple encryption, without loss of generality, using DES as the underlying block
cipher. In particular, we focus on DES-XEXEXEX variants, based on 2-Key and 3-Key Triple-DES, which
involve performing the XOR for key-whitening before and after each encryption with an additional 64-bit
key. One of the conclusions to be drawn from this work is the increased strength obtained from the XOR
sandwiching paradigm while requiring little in terms of additional computational resources.
1 INTRODUCTION
Work on the Data Encryption Standard (DES) in the
areas of Meet-in-the-MiddleAttacks and Related-Key
Attacks have revealed 2-Key and 3-Key Triple DES
to be much weaker than a na¨ıve attack would suggest.
We therefore hope to strengthen such encryption by
increasing key-length.
Perhaps the most obvious response would be
to increase these Triple Encryption DES variants
to Quadruple Encryption DES variants. However,
a quick calculation by a traditional Meet-in-the-
Middle attack will reveal that both Triple-DES and
Quadruple-DES can be attacked with a time complex-
ity of 2
113
, an ominous sign suggesting that the ex-
tra computational time of the added DES encryption
is both needlessly cumbersome and insufficient to in-
crease security.
∗
A part of this research was done while the author was
at DSO National Laboratories
1.1 Our Contribution
What we propose is to use an XOR-sandwiching
paradigm to include an additional 64-bit key into a
multiple encryption scheme. Specifically, we pro-
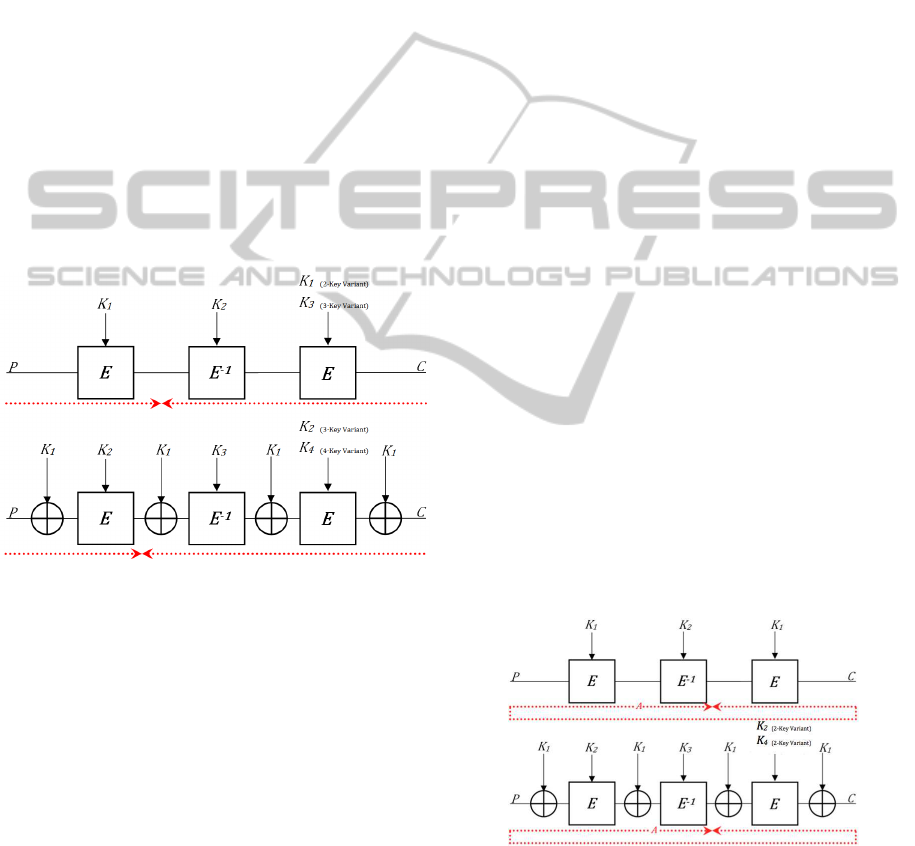
pose an XEXEXEX model (Figure 1) as an extension
to both 2-Key-Triple-Encryption and 3-Key-Triple-
Encryption, by XORing an additional 64-bit key in
between each encryption call. These are also easy
to implement in existing triple-encryption systems.
As in DES-EXE and DES-X, the use of the XOR
function for key-whitening strengthens the encryption
scheme with negligible computational overhead.
We present recent attacks to justify the choice of
such an encryption scheme. As far as we know, major
Figure 1: DES-XEXEXEX variants proposed.
305
Ng Ii-Yung R., Khoo K. and C.-W. Phan R..
On the Security of the XOR Sandwiching Paradigm for Multiple Keyed Block Ciphers.
DOI: 10.5220/0004505903050312
In Proceedings of the 10th International Conference on Security and Cryptography (SECRYPT-2013), pages 305-312
ISBN: 978-989-8565-73-0
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)
steps in breaking Triple-Encryption include the basic
Meet-in-the-Middle (MITM) attack and its optimiza-
tion (Lucks, 1998), MITM variants that targets 2-key
triple-DES (Merkle and Hellman, 1981; van Oorschot
and Wiener, 1991). In addition, we study Related-
Key (RK) MITM attacks that exploits key differ-
ences (J. Kelsey and Wagner, 1996; Choi et al., 1996)
and RK-MITM attacks that exploits key-permutation
(Phan, 2004; Vaudenay, 2011). In this research, we
argue that our XEXEXEX encryption variant signif-
icantly strengthens Triple-Encryption against known
attacks, through the example of DES.
2 MEET-IN-THE-MIDDLE
ATTACK
The traditional MITM attack is described diagram-
matically (Figure 2) below, comparing the original
Triple-Encryption with the one which we propose.
Figure 2: Traditional MITM attack on Triple-DES and
DES-XEXEXEX variants.
For 3-Key Triple-DES, we obtain (P,C), a known
Plaintext-Ciphertext (PT-CT) pair, and consider the
possible K
1
separately from possible (K
2
, K
3
), seek-
ing E
K
1
(P) = E
K
2
(E
−1
K
3
(C)). Note that we accept val-
ues of (K
1
, K
2
, K
3
) satisfying the above equation if the
encryption is true for ⌈log
2
64
2
168
⌉ = 3 PT-CT pairs.
Notice that this attack requires a time complexity in
the order of 2
113
encryptions and a memory complex-
ity of (64+ 56)2
56
≈ 2
63
bits.
A very similar search for E
K
2
(P ⊕ K
1
) ⊕ K
1
=
E
K
3
(E
−1
K
4
(C⊕ K
1
) ⊕ K
1
) can be carried out for our 4-
Key DES-XEXEXEX model. However, to remove
significant memory complexity we consider this at-
tack individually for each value of K
1
since that is
constant in the encryption scheme. We accept val-
ues of (K
1
, K
2
, K
3
, K
4
) if the results are consistent over
⌈log
2
64
2
212
⌉ = 4 PT-CT pairs. This attack will have
a time complexity in the order of 2
177
and a memory
complexity of approximately 2
63
.
As for 2-Key Triple DES, through a similar logic
as suggested above, we consider each value of K
1
sep-
arately. We expect that ⌈log
2
64
2
112
⌉ = 2 known PT-
CT pairs will confirm the correct value of K
1
and K
2
with a time complexity of 2
113
and a negligible mem-
ory requirement. The logical extension will mean that
for our 3-Key DES-XEXEXEX model we consider
each (K
1
, K
2
) individually, and accept values that are
consistent over ⌈log
2
64
2
176
⌉ = 3 PT-CT values. We
arrive at a time complexity of 2
177
and a negligible
memory complexity.
The addition of an additional key in the proposed
XEXEXEX model has thus increases the time com-
plexity of a basic MITM attack by 2
64
, an identical
increase to what we would expect from a na¨ıve attack.
2.1 Merkle-Hellman MITM Attack
The Merkle-Hellman MITM attack (Merkle and Hell-
man, 1981) is a chosen-plaintext alternative to this.
The common application of this attack is in the case of
2-Key Triple Encryption (Figure 3). In 2-Key Triple-
DES, we decrypt some 64-bit value A based on all 2
56
possible values of K
1
. For each A, we make a chosen
plaintext encryption query to obtain the correspond-
ing ciphertext and decrypt each A via the guessed K
1
as before. We then store these values and exhaustively
search all K
2
such that E
−1
K
1
(Enc(E
−1
K
1
(A))) = E
−1
K
2
(A)
(where Enc is the chosen plaintext encryption query).
We accept a value of (K
1
, K
2
) when ⌈log
2
64
2
112
⌉ = 2
PT-CT pairs are consistent with those keys. This at-
tack has a time complexity of 3(2
56
) ≈ 2
57.6
Encryp-
tions (neglecting that of obtaining the ciphertexts of
2
56
chosen-PT) and a memory complexity of 2
63
.
Figure 3: Merkle-Hellman MITM attacks on 2-Key Triple-
DES and both DES-XEXEXEX variants.
As for our 3-Key variant of the above attack,
we consider combinations of (K
1
, K
3
) separately
from K
2
, as represented diagrammatically above
(Figure 3). Specifically, the equality we search
for is E
−1
K
2
(Enc(E
−1
K
2
(A ⊕ K1) ⊕ K1) ⊕ K1) ⊕ K1 =
SECRYPT2013-InternationalConferenceonSecurityandCryptography
306

E
−1
K
3
(A). We accept a value of (K
1
, K
2
, K
3
) when
⌈log
2
64
2
176
⌉ = 3 PT-CT pairs are consistent with
those keys. This has a time complexity of 2
121.6
and
a memory complexity of 2
63
. This also requires the
entire codebook of PT-CT pairs.
For the original 3-Key Triple-DES and 4-Key
DES-XEXEXEX algorithm, this gives us no advan-
tage over the original MITM attack. Note that while
the attack, with the entire codebook of PT-CT pairs,
we can consider possible K
2
separately from the re-
maining keys, this gives negligible time advantage.
Therefore, similar to the original MITM attack,
our variant of 2-Key Triple DES has succeeded in in-
creasing the complexity of a chosen plaintext MITM
attack by a factor of 2
64
.
2.2 Van Oorshot - Wiener MITM
Attack
Van Oorshot and Wiener’s proposal to extend Merkle-
Hellman’s chosen plaintext attack to a known-
plaintext attack is applicable to the case of 2-Key
Triple DES, where the Merkle-Hellman attack gives
us a significant reduction in complexity on the orig-
inal MITM attack (van Oorschot and Wiener, 1991).
We choose 2
32
values of P. For each P, we calcu-
late all 2
56
possible values of E
−1
K
1
(P) and check these
against the 2
32
PT-CT pairs. For the matches we find,
we compute B = E
−1
K
1
(C) and store (K
1
, B) using at
most 2
56
memory entries. On each of these, we con-
duct an exhaustive search of K
2
and test resultant can-
didate (K
1
, K
2
) pairs with additional PT-CT pairs. We
repeat this process for different values of P until the
correct key is found. With 2
32
known PT-CT pairs,
this attack has time complexity of 2
89
encryptions and
a memory complexity of (64+ 56)2
56
≈ 2
63
.
Similarly, we apply this to the Merkle-Hellman
attack on our 3-key DES-XEXEXEX variant as de-
scribed in Section 2.1. Starting with 2
32
PT-CT pairs,
we accept a value of (K
1
, K
2
, K
3
) when ⌈log
2
64
2
176
⌉ =
3 PT-CT pairs are consistent with those keys. This at-
tack expects a time-complexity of 2
153
and memory-
complexity of 2
63
.
Therefore, in the case of 2-Key Triple DES and its
variant, we have shown that the time complexity in-
crease in the implementation of the XEXEXEX vari-
ant is 2
63
, similar to the attacks discussed above.
2.3 Lucks MITM Attack
As for 3-Key Triple DES, Lucks proposes an opti-
mization which reduces the time complexity with in-
creased memory (Lucks, 1998). He presents a variety
of attacks, however, we select the attack with com-
parable requirements to other attacks we present and
which considers DES as an ideal cipher, for fair com-
parison. His most efficient attack involves a set 2
32
PT-CT pairs (p
1
, c
1
), . . . (p
2
32
, c
2
32
) and a second set
S ⊂ { 0, 1}
64
and |S| = 2
33
. Due to the complexity of
his attack, we paraphrase his attack below:
1. For a ∈ S, we define the set M
a
= {(i, K
1
) ∈
{1, . . . 2
32
} × {0, 1}
56
| E
K
1
(p
i
) = a}, which re-
quires time-complexity of 2
32
× 2
56
= 2
88
.
2. For b ∈ {0, 1}
64
, i ∈ {1, . . . 2
32
}, we define N
b,i
=
{K
3
∈ {0, 1}
k
| E
K
3
(b) = c
i
}. It can be computed
with complexity 2
32
× 2
56
= 2
88
, by computing
b = E
−1
K3
(c
i
) for all 2
32
c
i
and for all 2
56
K
3
, and
placing K
3
into the corresponding set N
b,i
.
3. For K
2
∈ { 0, 1}
56
, a ∈ Sm, search for N
b,i
such that
E
−1
K
2
(a) = b. Then, for (K
2
, a, b) where (i, K
1
) ∈
M
a
, K
3
∈ N
b,i
, enter (K
1
, K
2
, K
3
) into a hash table.
4. When some (K
1
, K
2
, K
3
) has entered the hash ta-
ble twice, we test the set of keys with 1 other val-
ues of (p
i
, c
i
). Notice that this is sufficient since
we accept the keys when ⌈log
2
64
2
168
⌉ = 3 PT-CT
pairs are consistent with them.
We refer the reader to (Lucks, 1998) for detailed
calculations to derive the requirements of the attack.
2
33
values of a ∈ S, 2
32
PT-CT pairs, 2
88
encryptions
and 2
88
(56) ≈ 2
93.8
memory-complexityare required.
We then attempt to apply this to our 4-Key DES-
XEXEXEX variant. We considered two possible
methods of adapting the attack. The first is to sim-
ply repeat the attack by guessing values of K
1
, and re-
peating this for all values of K
1
. This would mean that
the time complexity would simply be 2
90
· 2
64
= 2
154
single encryptions and memory complexity, reusable
for each K
1
, will be 2
93.8
bits. Note, though, that as
⌈log
2
64
2
176
⌉ = 4, “tripletest” will now need to test the
candidate keys on two additional PT-CT pairs.
The second method involved, for an arbitrary
(P,C) pair, define a = E
K
2
(p⊕ K
1
) and b = E
−1
K
4
(c⊕
K
1
). We then calculate M
a,K
1
and N
b,i,K
1
, sets iden-
tical to that which we studied before, but restricted
to each K
1
. The rest of the attack proceeds by con-
sidering each value of K
1
individually then searching
for values to “tripletest” (searching for E
−1
K
3
(a⊕K
1
) =
b⊕ K
1
). However, this would come at the cost of 2
64
times more memory and would wind down to a com-
parable time complexity because each K
1
would still
be considered as an individual case. Therefore, with
the first method preferable, we can once again report
an additional 2
64
increase in time complexity of an at-
tack with the addition of the 64-bit K
1
key.
Note that the Lucks’ attack is inefficient when the
OntheSecurityoftheXORSandwichingParadigmforMultipleKeyedBlockCiphers
307
first and third DES encryption make use of the same
key since much recalculation would be done. To this
end, the Merkle-Hellman or Van Oorshot-Wiener at-
tack is much more efficient. Therefore, we did not
consider an application of Lucks’ attack on 2-Key
Triple-DES and our 3-Key variant of it as part of our
study.
3 RELATED-KEY ATTACKS
We also consider their security under Related-Key at-
tacks, something which is posited to be not as purely
theoretical as it seems in recent years (Phan, 2004).
3.1 Kelsey-Wagner-Schneier
Related-Key Attack
We begin with the original Kelsey-Wagner-Schneier
Related-Key Attack (J. Kelsey and Wagner, 1996).
This attack on Triple-DES involves a known PT-CT
pair, (P,C) encrypted on unknown keys (K
1
, K
2
, K
3
)
and the resultant ciphertext being decrypted under
keys (K
1
⊕ ∆, K
2
, K
3
), where ∆ is known, to arrive at
P
′
. Then, a exhaustive search can be done for K
1
since
E
K
1
(P) = E
K
1
⊕∆
(P
′
). From here, a MITM attack can
be performed on the remaining two keys, similar to
that which is performed on double-DES. Notice that
this will require approximately 3(2
56
) ≈ 2
57.6
encryp-
tions and 2
63
memory complexity. Note that since
⌈log
2
64
2
168
⌉ = 3, we would also need to test resultant
pairs against 2 other known PT-CT values.
A similar attack can be arranged for 4-Key DES-
XEXEXEX, given related keys (K
1
, K
2
, K
3
, K
4
) and
(K
1
⊕ ∆, K
2
, K
3
, K
4
). A known PT-CT pair is en-
crypted on the former and the resultant ciphertext
decrypted on the latter. This allows us to do a ex-
haustive search on combinations of (K
1
, K
2
), and con-
duct a MITM attack to find possible (K
3
, K
4
) for
each candidate (K
1
, K
2
). Notice that we will ac-
cept a combination of keys if it is consistent over
⌈log
2
64
2
232
⌉ = 4 PT-CT pairs. We expect a time com-
plexity of 2
121
encryptions and a memory complexity
of 2
56
(56 + 64) = 63. This attack is not applicable
to 2-Key Triple-DES and our 3-Key DES-XEXEXEX
variant.
3.2 Choi et al. Related-key Attack
Given that a chosen-plaintext attack is considered un-
feasible at present (van Oorschot and Wiener, 1991),
a chosen-CT attack is even less useful. In this re-
gard, most studies look to the known PT-CT attack
presented by Choi et al (Choi et al., 1996) as diagram-
matically represented below (Figure 4).
With 2
32
known PT-CT pairs encrypted under
the keys and another 2
32
known PT-CT pairs en-
crypted under the Related-Keys, we search for col-
lisions as indicated by the arrows. For 2-Key Triple
DES, we search for (P,C), (P
′
,C
′
) and K
1
such that
E
K
1
(P) = E
K
1
⊕∆
(P
′
) and E
−1
K
1
(C) = E
−1
K
1
⊕∆
(C
′
) are
both satisfied. For 3-Key Triple DES, we search for
(P,C), (P
′
,C
′
) and K
1
such that E
K
1
(P) = E
K
1
⊕∆
(P
′
)
and C = C
′
. We expect to exist by the Birthday Para-
dox. With these candidates, we do a MITM search
for the remaining keys. We will accept the keys when
they are consistent across ⌈log
2
64
2
168
⌉ = 3 PT-CT
pairs for Three-Key Triple-DES and ⌈log
2
64
2
112
⌉ = 2
PT-CT pairs for Two-Key Triple-DES.
Figure 4: RK attacks on 2-Key Triple DES and 3-Key Triple
DES.
This has an expected time complexity of 2
89
en-
cryptions and a memory complexity of 2
39
for 2-
Key Triple-DES. For 3-Key Triple-DES, this is a
time complexity of 2
57.6
single encryptions and 2
60
of memory complexity (Choi et al., 1996).
Extending this to our XEXEXEX variants, we
make use of the key-relation (K
1
, K
2
, K
3
, K
4
) and
(K
1
, K
2
⊕ ∆, K
3
, K
4
) or (K
1
, K
2
, K
3
) and (K
1
, K
2
⊕
∆, K
3
). As before, there is the solution of simply re-
peating the entire attack for all guesses of K
1
, modi-
fying the collision search to include the relevant XOR
functions. This will leave us with identical memory
complexity for both attacks and a time complexity of
2
153
encryptions for 3-Key DES-XEXEXEX and 2
121
for 4-Key DES-XEXEXEX. Notice, however, that we
would only accept a set of keys after ⌈log
2
64
2
212
⌉ = 4
PT-CT pairs are consistent with the results. However,
we present an alternative here, which might occur as
SECRYPT2013-InternationalConferenceonSecurityandCryptography
308

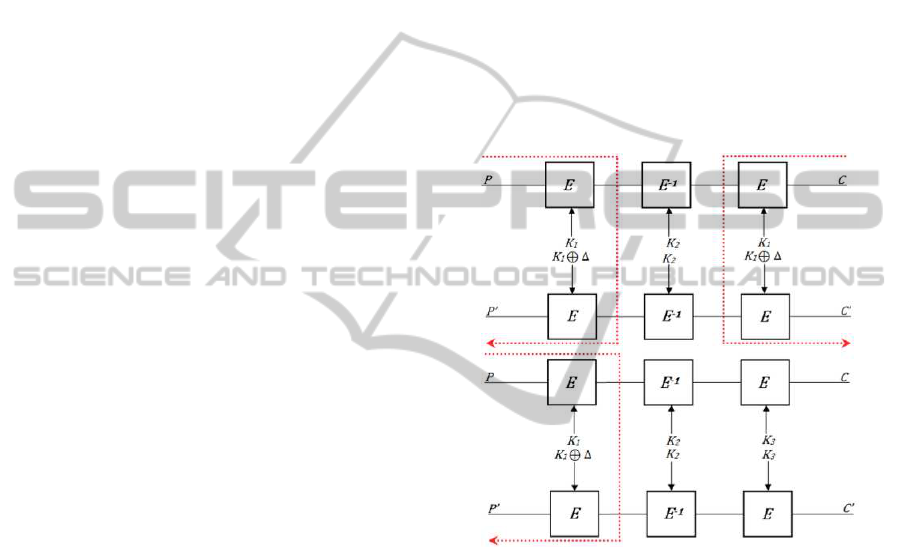
Figure 5: Alternate RK attacks on DES-XEXEXEX vari-
ants.
a logical extension to a reader (Figure 5).
For both DES-XEXEXEX variants, we search
among 2
32
known PT-CT pairs encrypted under keys
(K
1
, K
2
, K
3
) or (K
1
, K
2
, K
3
, K
4
) and their Related-
Keys, (K
1
, K
2
⊕ ∆, K
3
) and (K
1
, K
2
⊕ ∆, K
3
, K
4
). We
instead guess all (K
1
, K
2
) and search for a (P,C) pair
such that E
K
2
(P⊕K
1
) = E
K
2
⊕∆
(P
′
⊕K
1
) and E
−1
K
2
(C⊕
K
1
) = E
−1
K
2
⊕∆
(C
′
⊕ K
1
), in the case of 3-Key DES-
XEXEXEX, and that E
K
2
(P⊕ K
1
) = E
K
2
⊕∆
(P
′
⊕ K
1
)
and C = C
′
, in the case of 4-Key DES-XEXEXEX.
We then do a exhaustive search for the remaining
keys. However, this wastefully computes and stores
all encryptions of all possibilities of K
1
, in memory,
without performing better than the first method.
3.3 Vaudenay RK Attack
The RK attack proposed by Vaudenay (Vaudenay,
2011) on Three-Key Triple-DES notes that if we
were to encrypt a plaintext, P, according to keys
(K
1
, K
2
, K
3
) then decrypt the ciphertext according to
Related-Keys φ(K
1
, K
2
, K
3
) = (K
2
, K
1
, K
3
) to give a
second ciphertext, C. This allows us to yield the fol-
lowing relation: (E
K
1
◦ E
−1
K
2
)
2
(P) = C. From this, we
streamline a list of plaintexts, x, which yield “fixed
points” where (E
−1
K
2
(E
K
1
(x)) = x under keysK
1
, K
2
.
With candidate K
1
, K
2
proposed, and the respective x,
we can then do a exhaustive search for K
3
.
Vaudenay presents an attack based on known PT-
CT pairs and another based on Broadcast Known
Plaintexts (BKP). However, since we are more inter-
ested in comparing Triple-DES to our variants, and
not so much on comparing the results of various at-
tacks, we will study the BKP variant and acknowledge
that our results can be trivially adapted to the known
Plaintext variant of Vaudenay’s attack.
We refer the reader to Vaudenay’s report (Vau-
denay, 2011) for the exact procedure of Vaudenay’s
rather complex attack and calculations of complexity.
For 3-Key Triple-DES, he propose n = 3, (number
of pairs of Related-Keys), meaning we will encrypt
known PT-CT pairs under K, φ(K), K ⊕ ∆
1
, φ(K ⊕
∆
1
), K ⊕ ∆
2
, φ(K ⊕ ∆
2
) with known ∆
1
, ∆
2
. Thus,
we require 2
67
BKP and R
n
, the expected number of
wrong keys that are considered in the second part of
the attack, is approximately 2
−1.72
, yielding an ex-
pected time complexity of 2
57
· 3 ≈ 2
58.6
and an ex-
pected memory complexity of approximately 2
63
.
As for Two-Key Triple-DES, we instead consider
Encryption of some plaintext P by keys (K
1
, K
2
) and
decryption of the ciphertext by Related-Keys (K
2
, K
1
)
to giveC. This yields the equation (E
K
1
◦ E
−1
K
2
)
3
(P) =
C. Fixed points of the same form as above are sieved
out. However,wrong key-guessesare easily discarded
by a consistency check, meaning n = 1. This requires
2
65
BKP and yields a time complexity of 2
57.6
single
encryptions and a memory complexity of 2
63
.
The purpose of finding fixed points in this attack
is to be able to consider the behaviour of a subset of
the keys. In this case, it is that of K
3
, by requiring
that the plaintext which enters the encryption scheme
be identical to the ciphertext before it is encrypted by
K
3
. In the case of 2-Key Triple DES, the same thing
is achieved for the last K
1
. This is done by exploiting
the second DES function in the encryption scheme be-
ing a decryption and the specific key relation. Notice,
however, that in an XEXEXEX variant, if we hold the
guessed K
1
constant, whether we perform iterations
of encryptions, decryptions or some combination of
the two, the identical XOR function performed after
the triple-encryption and the start of the second triple
encryption will cancel out. However, the XOR func-
tions between the encryptions are not affected. This
means that the resultant function will not be repeating
in the way that we were able to achieve in Vaudenay’s
attack since the encryptions can no longer take on a
consistent pattern.
However, consider instead 2
32
(P,C⊕ K
1
) values,
for some guessed K
1
. We can then attack 3-Key
DES-XEXEXE by guessing all possible K
1
. Simi-
larly, by guessing K
1
, we can compute 2
32
(P ⊕ K
1
)
values for each K
1
and attack 4-Key DES-EXEXEX.
To this end, notice that now we can perform the
same combination, of an encryption and decryption,
on P to arrive at C, with Related Keys (K
1
, K
2
, K
3
)
and (K
1
, K
3
, K
2
) for the 3-Key Variant as well as
for (K
1
, K
2
, K
3
, K
4
) and (K
1
, K
3
, K
2
, K
4
) for the 4-Key
OntheSecurityoftheXORSandwichingParadigmforMultipleKeyedBlockCiphers
309

variant. Define a function, x ⊕ K
1
= f(x), then, we
can arrive at equations similar to those above where
( f ◦ E
K
2
◦ f ◦E
−1
K
3
)
3
(P) = C for the 3-Key Variant and
( f ◦ E
K
2
◦ f ◦ E
−1
K
3
)
2
(P) = C for the 4-Key Variant.
Notice then that we need to change the value of n
(number of pairs of K, φ(K) we consider) since key-
length has been increased, in 4-Key DES-EXEXEX.
We therefore have the following calculations (adapted
from (Vaudenay, 2011), Section 3.1, pg 5-6):
First, we calculate the expected f n
∗
, the number
of lists with an odd number of fixed points. Let n = 6,
E(n
∗
) = 1+ (n− 1)
1− e
−
3
2
2
≈ 2.94 (1)
Then, we have that there are 2
2(56)+(64)
possible
combinations of keys but an equation to satisfy on
(2.94)(64) bits. This gives us the respective value
of R
n
(expected number of wrong keys in R given n
Related-Key pairs) as:
R
n
≈ 2
2(56)+(64)−(2.94)(64)
= 2
−12.16
(2)
Notice that the value of n does not impact the
choice to repeat the entire attack 2 times (i.e. N
n
is
unrelated to n so long as a > 0). Therefore, with an
identical success rate, we require 6(2
64+1
) ≈ 2
68
BKP.
The only difference in the time complexity which
sees a 2
64
increase in the calculations to arrive at a
fixed point, since each K
1
must be guessed separately.
Note that the XOR functions to derive each set of
(P,C⊕K
1
) or (P⊕ K
1
,C) values are assumed to be of
negligible complexity. This has a time complexity of
2(2· 2
56+64
+ 2
56
· 2
−12.16
) + 2
56
≈ 2
122
encryptions.
Memory can be reused for each guess of K
1
, there-
fore, we have that the memory complexity is 2
63
.
For the Three-Key DES-XEXEXE, we can adopt
the same method of finding fixed points, however, as
in the original attack on Two-Key Triple-DES, take
n = 1. This has time complexity of 4(2
56+64
) = 2
122
encryptions and a memory complexity of 2
63
.
Notice that in both these cases, the time complex-
ities are comparable to that of the attack we con-
sidered on DES-XEXEXEX. This, we realized, is
because Vaudenay’s attacks on DES-EXEXEX and
DES-XEXEXE involve guessing each K
1
in turn, re-
turning to an attack very reminiscent of that of DES-
XEXEXEX. This makes the memory space 2
64
times
less, and reduces the required value of n, other in-
dicators that the attack is identical in nature. There-
fore, we have shown the robustness of our method of
strengthening Triple-DES, in that, even if RK attacks
such as Vaudenay’sattack could be more than trivially
applied, we still achieve a 2
64
complexity increase for
the 64-bits of added keylength.
3.4 Phan RK Attack
Phan’s RK slide-attack can be applied to both the 2-
Key and the 3-Key Triple Encryption effectively, as
discussed in his paper (Phan, 2004). We refer the
reader to his paper for the exact details of each attack.
With 2
32
PT-CT pairs each for the original key
and the Related-Key, we can expect 1 pair with the
desired relation by the Birthday Paradox. The first
set of encryptions (for all possible K
1
on all values
of P) dominates the time complexity, meaning that
2
56
· 2
32
= 2
88
single-DES encryptions are required
for the attack. The memory complexity is also domi-
nated by this step, 2
88
· (56+ 64+ 64) ≈ 2
96
.
In the 3-Key Triple DES, we consider PT-
CT pairs encrypted under the keys (K
1
, K
2
, K
3
)
and (K
2
, K
3
, K
1
). We then search for (P,C), en-
crypted under (K
1
, K
2
, K
3
) and (P
′
,C
′
) encrypted un-
der (K
2
, K
3
, K
1
) such that C
′
= E
K
1
(P) and C =
E
K
1
(P
′
). Once again, we obtain 2
32
PT-CT pairs for
each set of keys and create a list of candidates for K
1
by encrypting each P and decrypting each C accord-
ing to each K
1
. Those satisfying the collision con-
ditions give candidate values for K
1
. This, as he re-
ports, requires 2
88
DES encryptions and a memory
complexity of 2
32
· (64+ 64) = 2
39
.
Notice that an exhaustive search for K
2
, K
3
via a
traditional MITM attack applies once K
1
has been
determined. This can be achieved with 2
39
memory
complexity by portioning the 2
56
candidates for K
1
into sets of 2
32
values, a separate MITM attack is then
performed using an exhaustive key-search for K
2
and
matching against possible ciphertext values given for
each group. The total time complexity of this search
should be2
(56−32)
· (2
56
) = 2
80
, negligible in compar-
ison to the time-complexity of the main attack.
Similar to our analysis in other sections of this pa-
per, to achievea time-complexity lower than 2
64
times
that of the original attack, the attack must segment
the keys into two mutually exclusive groups. No-
tice that should be attempt a slide attack on either
DES-XEXEXEX variant, to isolate one or more en-
cryptions, XOR functions both inside and outside the
shared segment of the encryption scheme encryption
under the pair of Related-Keys must follow, making
them not mutually exclusive. Therefore, our focus
turns to the search for a method for the Phan attack
to achieve this complexity.
For this, we obtain 2 sets of 2
32
PT-CT pairs, en-
crypted under (K
1
, K
2
, K
3
, K
4
), denoted (P
∗
,C
∗
), and
(K
1
, K
3
, K
2
, K
4
), denoted (P
′∗
,C
′∗
). We guess a par-
ticular K
1
and XOR all 2
33
PT-CT pairs by it, to arrive
at (P,C) = (P
∗
⊕ K
1
,C
∗
⊕ K
1
) and (P
′
,C
′
) = (P
′∗
⊕
K
1
,C
′∗
⊕ K
1
), which is of negligible time-complexity.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
310
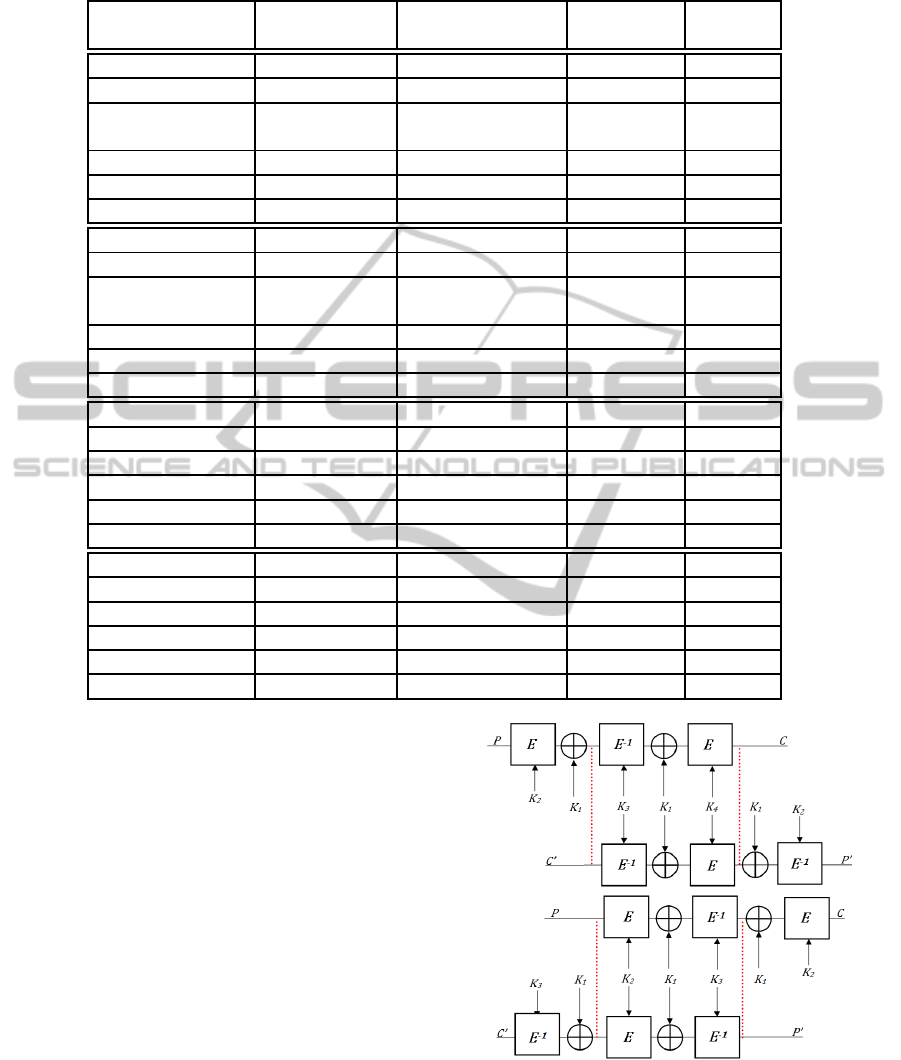
Table 1: Summary of Complexities for MITM and RK Attacks on Triple-Encryptions and DES-XEXEXEX variants.
Encryption Attack PT-CT Pairs Time Memory
Scheme Requirement (Encryptions) (bits)
3K Triple-DES MITM 3 Known 2
113
2
63
3K Triple-DES Lucks 2
32
Known 2
90
2
93.8
3K Triple-DES Kelsey et. al 1 Chosen-Decryption 2
57
2
63
2 Known
3K Triple-DES Choi et. al 2
33
RK-Known 2
57
2
60
3K Triple-DES Vaudenay 2
67
RK-BKP 2
58.6
2
63
3K Triple-DES Phan 2
33
RK-Known 2
88
2
39
4K DES-XEXEXEX MITM 4 Known 2
177
2
63
4K DES-XEXEXEX Lucks 2
32
Known 2
154
2
93.8
4K DES-XEXEXEX Kelsey et. al 1 Chosen-Decryption 2
121
2
63
2 Known
4K DES-XEXEXEX Choi et. al 2
33
RK-Known 2
121
2
60
4K DES-XEXEXEX Vaudenay 2
68
RK-BKP 2
122
2
63
4K DES-XEXEXEX Phan 2
33
RK-Known 2
152
2
63
2K Triple-DES MITM 2 Known 2
113
Negligible
2K Triple-DES Merkle-Hellman 2
56
Chosen 2
57.6
2
63
2K Triple-DES Oorschot-Wiener 2
32
Known 2
89
2
63
2K Triple-DES Choi et. al 2
33
2
33
RK-Known 2
89
2
39
2K Triple-DES Vaudenay 2
33
2
33
RK-Known 2
57.6
2
63
2K Triple-DES Phan 2
33
RK-Known 2
88
2
96
3K DES-XEXEXEX MITM 3 Known 2
177
Negligible
3K DES-XEXEXEX Merkle-Hellman 2
120
Chosen 2
117
2
63
3K DES-XEXEXEX Oorshot-Wiener 2
33
Known 2
153
2
63
3K DES-XEXEXEX Choi et. al 2
33
RK-Known 2
153
2
39
3K DES-XEXEXEX Vaudenay 2
33
RK-Known 2
121
2
63
3K DES-XEXEXEX Phan 2
33
RK-Known 2
152
2
96
Then, the attack can proceed as diagrammatically dis-
played below (Figure 6). This yields an identical
memory complexity and a time complexity of 2
144
encryptions for 4-Key DES-XEXEXEX and 2
152
en-
cryptions for 3-Key DES-XEXEXEX.
4 CONCLUSIONS
The merits of the 3-Key and 4-Key DES-XEXEXEX
variants in strengthening Triple-DES against known
MITM and RK attacks have been extensively shown.
Due to the fact that we employ the XOR function, us-
ing the same key, across the entire encryption scheme,
we have arrived at a cipher which cannot readily be
portioned into segments with independent keys to be
attacked separately. These results are summarized in
Table 1. For a key-extension of 64-bits, we see a
strengthening of the cipher by a complexity of 2
64
. In
addition, the XOR function involves negligible com-
putation, thereby not affecting the implementation of
Figure 6: Phan attacks on 4-Key DES-EXEXEX and 3-Key
DES-XEXEXE.
the cipher. 3-Key or 4-Key Quadruple-DES is an ex-
ample of an intuitive solution that does not satisfy
these conditions.
Our contribution is useful to employing multiple-
OntheSecurityoftheXORSandwichingParadigmforMultipleKeyedBlockCiphers
311

encryption structures with insufficient security af-
forded by its key-length. Beyond DES, similar results
will be obtained in application to any block cipher,
meaning, for a cipher with block-size n, we achieve a
2
n
increase in security for a n-bit key-length increase.
Recent literature, such as (Phan, 2004) and (Kil-
ian and Rogaway, 1996) support moving away from
XOR to addition modulo 64. This is because the in-
verse function of XOR is itself, whereas addition is
not symmetrical, invalidating some attacks. However,
Phan presents an attack that is applicable to DES-+
and not DES-X (Phan, 2004). Our brief study into
DES - +E+E+E+ models for Triple-Encryption re-
vealed similar results to DES-XEXEXEX with the
exception of the Vaudenay attack. Future work can
study addition in relation to this in more detail.
Also, we considered a general t + 1-key DES-
(XE)
t
X encryption scheme and we believe that sim-
ilar attacks can be applied to show that a 2
64
increase
in security is achieved. However, more research can
be done on this to study the significance of this in-
crease as t increases, as well as other schemes involv-
ing less or more than t + 1 keys.
REFERENCES
Choi, J., Kim, J., Sung, J., Lee, S., and J.Lim (1996).
Related-key and meet-in-the-middle attacks on triple-
des and des-exe. In Proceedings of the 2005 interna-
tional conference on Computational Science and Its
Applications - Volume Part II. Springer-Verlag.
J. Kelsey, B. S. and Wagner, D. (1996). Key-schedule cryp-
toanalysis of idea, g-des, gost, safer, and triple-des. In
Proceedings of the 16th Annual International Cryptol-
ogy Conference on Advances in Cryptology. Springer-
Verlag.
Kilian, J. and Rogaway, P. (1996). How to protect des
against exhaustive key search. In Proceedings of the
16th Annual International Cryptology Conference on
Advances in Cryptology. Springer-Verlag.
Lucks, S. (1998). Attacking triple encryption. In Proceed-
ings of the 5th International Workshop on Fast Soft-
ware Encryption. Springer-Verlag.
Merkle, R. and Hellman, M. (1981). On the security of
multiple encryption.
Phan, R. (2004). Related-key and meet-in-the-middle at-
tacks on triple-des and des-exe. In In Topics in Cryp-
tology - The Cryptographer’s Track at RSA Confer-
ence (CT-RSA ’04). Springer.
van Oorschot, C. and Wiener, M. (1991). Related-key at-
tack against triple encryption based on fixed points.
In Proceedings of the workshop on the theory and ap-
plication of cryptographic techniques on Advances in
cryptology. Springer-Verlag New York, Inc.
Vaudenay, S. (2011). Related-key attack against triple
encryption based on fixed points. In SECRYPT.
SCITEPRESS.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
312
