
Meet-in-the-Middle Preimage Attacks Revisited
New Results on MD5 and HAVAL
Yu Sasaki
1
, Wataru Komatsubara
2
, Yasuhide Sakai
2
, Lei Wang
3
, Mitsugu Iwamoto
2
,
Kazuo Sakiyama
2
and Kazuo Ohta
2
1
NTT Secure Platform Laboratories, Tokyo, Japan
2
The University of Electro-Communications, Tokyo, Japan
3
Nanyang Technological University, Nanyang, Singapore
Keywords:
MD5, HAVAL, Hash Function, Preimage Attack, Meet-in-the-Middle, Local-collision, Initial Structure.
Abstract:
In this paper, we revisit previous meet-in-the-middle preimage attacks on hash functions. We firstly present
a technical improvement for the existing local-collision and initial-structure techniques. With applying some
equivalent transformation, we can significantly reduce the memory requirement from the original proposals.
We then revisit the previous preimage attacks on MD5 and HAVAL with recent techniques. Consequently, we
can improve the memory complexity of the previous preimage attack on full MD5 from 2
45
to 2
13
and on full
4-pass HAVAL from 2
64
to 2
32
. Moreover, we extend the preimage attack on 5-pass HAVAL from 151 steps
to 158 steps, and present the first preimage attack with a single block message for 3-pass HAVAL.
1 INTRODUCTION
Cryptographic hash functions are one of the most
fundamental primitives for cryptography, which com-
press an input message of arbitrary length into a fixed-
size hash value. For a hash function H , the preim-
age resistance is one of the most important security
notions, which means that for a given hash value y,
finding x such that H (x) = y must be computation-
ally hard. When the hash value size is N bits, H
must resist any preimage attack with a complexity less
than 2
N
computations. In fact, in the SHA-3 com-
petition conducted by NIST (NIST, 2007), submitted
algorithms were required to provide the preimage re-
sistance up to 2
N
computations.
Most of hash functions in practice adopt the
narrow-pipe Merkle-Damg
˚
ard domain extension al-
gorithm. In this scheme, an N-bit initial value IV(=
H
0
) is defined and the input message M is divided
into several message blocks M = M
0
∥M
1
∥···∥M
ℓ−1
.
The hash value of M is computed by iteratively up-
dating IV with a fixed-input size compression func-
tion H
i+1
= CF(H
i
,M
i
) for 0 ≤ i ≤ ℓ − 1. It is widely
known that preimages for the compression function
CF, which are also called pseudo-preimages, can be
converted to preimages for the hash function H with a
multi-block message (Menezes et al., 1997, Fact9.99).
Based on this property, many researches have been
conducted in order to find preimages on the compres-
sion function with a complexity less than 2
N
. Leurent
presented the first successful preimage attack on MD4
(Leurent, 2008). Then, Aoki and Sasaki presented the
framework of the meet-in-the-middle preimage attack
on the compression function (Aoki and Sasaki, 2009).
The basic idea is separating the compression func-
tion into two independent subfunctions called forward
chunk and backward chunk so that a part of input
message bits for the forward chunk labeled as M
F
(resp. M
B
for the backward chunk) never impacts to
the computation of the backward chunk (resp. for-
ward chunk), respectively. In this paper, M
F
and M
B
are called free bits. One of the core ideas in (Aoki and
Sasaki, 2009) is the splice-and-cut technique, which
regards the first and last steps of the compression
function as consecutive steps. The technique signif-
icantly enlarges the choices of how to separate the
compression function into two independent chunks.
However, as a side-effect, the attack only generates
pseudo-preimages and thus using the conversion al-
gorithm becomes necessary, which means that gener-
ated preimages are always longer than 1 block.
Many other techniques have been studied for the
meet-in-the-middle preimage attack. In this paper, we
focus on the local-collision (Sasaki and Aoki, 2008)
and initial-structure (Sasaki and Aoki, 2009) tech-
niques which make the attack possible even if the
111
Sasaki Y., Komatsubara W., Sakai Y., Wang L., Iwamoto M., Sakiyama K. and Ohta K..
Meet-in-the-Middle Preimage Attacks Revisited - New Results on MD5 and HAVAL.
DOI: 10.5220/0004521101110122
In Proceedings of the 10th International Conference on Security and Cryptography (SECRYPT-2013), pages 111-122
ISBN: 978-989-8565-73-0
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)
beginning of two chunks contain free bits for both
chunks. As a side-effect, the memory requirement be-
comes large. In fact, the previous preimage attack on
MD5 and 4-pass HAVAL requires a memory to store
about 2
45
words and 2
64
words, respectively, which is
infeasible or very hard to implement. Note that the
original definition of the initial-structure is very con-
ceptual, and a part of the initial-structure was later
formalized as biclique in (Bogdanov et al., 2011).
However, the biclique only can deal with determinis-
tic events, and thus cannot be applied to the previous
attacks on MD5 and HAVAL which utilize probabilis-
tic events for their initial-structure or local-collision
techniques. We believe that investigating improve-
ment of the local-collision and initial-structure tech-
niques are useful.
MD5 is a 128-bit hash function designed by Rivest
in 1992 (Rivest, 1992), and HAVAL is a variable-
output-size hash function designed by Zheng el al. in
1992 (Zheng et al., 1993). In this paper, we focus on
the 256-bit output for HAVAL, which makes the com-
putation structure be a narrow-pipe Merkle-Damg
˚
ard.
The previous results on MD5 and HAVAL are sum-
marized in Table 1. The previous preimage attacks
on full MD5 and full 4-pass HAVAL require a large
amount of memory. The previous preimage attack on
5-pass HAVAL does not reach the full (160) steps. All
of the previous attacks on MD5 and HAVAL cannot
generate preimages which fit within 1-block.
Motivation for Short Preimages
To apply preimage attacks for protocols, the size of
preimages may be a critical issue. For example, let us
consider the following authentication protocol;
1. A (secret) key string denoted by M, say
1024 bits, is generated and given to a user.
2. The user stores M in his own device such as
a smart card.
3. The user registers the hash value of the key
string denoted by H (M) to the database.
The database stores H (M) rather than M
in order to protect the original key string
even if the data in the database is leaked.
4. Every time he accesses to the system, the
user inputs the key string M via his device
and the system computes its hash value and
compares it with the stored H (M).
If the preimage resistance of H is broken, an at-
tacker can recover the key string
1
from the stored
digest. In such a protocol, usually the (maximum)
1
The recovered string may be different from the original
key string M but has the same effect for this protocol.
length of the key string M is defined by the system.
This indicates that if the length of generated preim-
ages by the attacker is very long, they do not give
any impact. In other words, evaluating the minimum
length of preimages is an important work. In fact, the
preimage attack on full MD5 only generates preim-
ages of more than 2
32
message blocks, which seem
hard to give impact to protocols in practice.
Our Contributions
In this paper, we present several improvements for
the meet-in-the-middle preimage attacks on MD5 and
HAVAL. The results are summarized in Table 1. We
improve the memory requirement for full MD5 from
2
45
to 2
13
and for full 4-pass HAVAL from 2
64
to 2
32
.
We then extend the number of attacked steps for 5-
pass HAVAL from 151 to 158 steps, and present the
first preimage attack with a single block message for
3-pass HAVAL.
Regarding MD5 and 4-pass HAVAL, we present
a technical improvement, which significantly re-
duces the memory requirement of the previous local-
collision and initial-structure techniques. We explain
our idea based on the previous application to HAVAL.
See its illustration in Figure 1. Let m
j
and m
j+8
be
Q
j
B
m
j
F
Q
j+9
F
m
j+8
B
m
j
F
m
j+8
B
Q
j
Q
j+9
Q
j
Q
j+9
m
j+8
m
j
Figure 1: Memoryless local-collision technique. The super-
scripts ‘B’ and ‘F’ represent the free bits for the backward
chunk and forward chunk, respectively. The size of free bits
is 2n for the previous work while only n for ours.
message words used in steps j and j +8, respectively.
Then, the chaining variable after step j + 8 labeled as
Q
j+9
is represented by Q
j+9
= Q
j
+ m
j
+ m
j+8
. The
attack uses m
j
and m
j+8
as free bits for the forward
chunk and backward chunk, respectively. To make
the two chunks independent, Q
j+9
(resp. Q
j
) must be
computed independently of m
j+8
(resp. m
j
). How-
ever, Q
j+9
is dependent of both of m
j
and m
j+8
. To
SECRYPT2013-InternationalConferenceonSecurityandCryptography
112
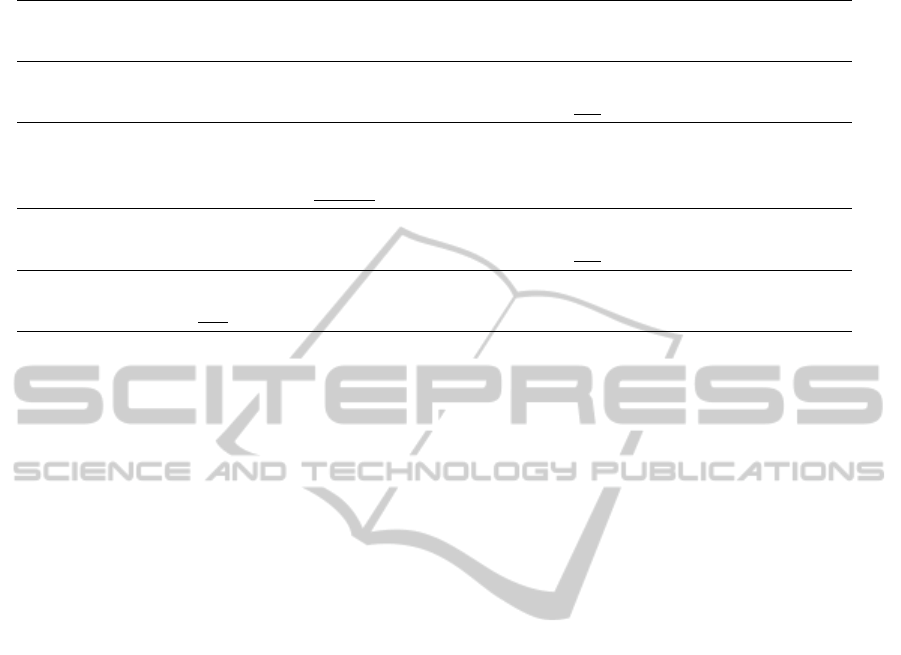
Table 1: Summary of preimage attacks on MD5 and HAVAL. Our improved points are emphasized.
Target #Steps Minimum length Complexity Memory Reference
of preimages (words)
MD5 64 (full) 2
33
blocks 2
123.4
2
45
(Sasaki and Aoki, 2009)
64 (full) 2
33
blocks 2
123.4
2
2
2
13
Ours
3-pass HAVAL 96 (Full) 2 blocks 2
230
2
64
(Aumasson et al., 2009)
96 (Full) 2 blocks 2
225
2
64
(Sasaki and Aoki, 2008)
96 (Full) 1 block 2
244
2
15
Ours
4-pass HAVAL 128 (Full) 2 blocks 2
241
2
64
(Sasaki and Aoki, 2008)
128 (Full) 2 blocks 2
242
2
2
2
32
Ours
5-pass HAVAL 151 2 blocks 2
241
2
64
(Sasaki and Aoki, 2008)
158 2 blocks 2
254
2
9
Ours
solve the problem, the previous work also regards the
Q
j
and Q
j+9
as free bits for the backward and for-
ward chunks, respectively, and later check the consis-
tency of the equation Q
j+9
= Q
j
+ m
j
+ m
j+8
prob-
abilistically. In details, the forward chunk and back-
ward chunk are computed depending on 2n free bits
of (m
j
,Q
j+9
) and (m
j+8
,Q
j
), respectively, where n
represents the word size. The approach requires a
memory to store 2
2n
values to perform the meet-in-
the-middle attack with 2n free bits. In this paper, as
shown in Figure 1, we observe that the order of the ad-
dition with m
j
and m
j+8
can be exchanged as long as
the local collision is formed properly. We fix the value
of Q
j
+ m
j+8
and Q
j+9
− m
j
denoted by the bold line
in the bottom of Figure 1 to some value x, say x = 0.
Then, Q
j+9
can be computed solely dependent on m
j
by x + m
j
and Q
j
can be computed solely dependent
on m
j+8
by x − m
j+8
. Due to this effort, the forward
chunk and the backward chunk can be computed de-
pending on only n free bits of m
j
and m
j+8
respec-
tively, with always satisfying the relation of these 4
variables. This reduces the memory requirement to
the square root of the previous work, i.e., from 2
2n
to
2
n
, while the time complexity keeps the same as the
previous work.
Regarding 5-pass and 3-pass HAVAL, we eval-
uate their structures in details with the recent tech-
niques. Specifically, we analyze the initial-structure
and partial computation during the matching part in
a bit-wise level rather than a word-wise level which
was done by the previous work. We search for new
choices of free bits taking into account these techni-
cal advancements, and find better ones.
The rest of the paper is organized as follows. In
Section 2, we describe MD5 and HAVAL. In Section
3, we present the low-memory local-collision tech-
nique and apply it to 4-pass HAVAL. In Section 4, we
present our attack on MD5. In Section 5, we present
our attacks on 5-pass and 3-pass HAVAL. Finally, we
conclude this paper in Section 6.
2 SPECIFICATIONS
2.1 Specification of MD5
MD5 (Rivest, 1992) is a 128-bit hash function that
adopts the narrow-pipe Merkle-Damg
˚
ard domain ex-
tension. First, an input message M is padded to be
a multiple of 512 bits, and then divided into 512-
bit message blocks M
0
∥M
1
∥···∥M
ℓ−1
. H
0
is set to
the initial value IV defined in the specification, and
H
i+1
← md5(H
i
,M
i
) is computed for i = 0,1,...,ℓ −
1, where md5: {0,1}
128
×{0,1}
512
→ {0,1}
128
is the
compression function of MD5. Finally, H
n
is output
as a hash value of M.
The compression function takes H
i
and M
i
as in-
put, and outputs H
i+1
. M
i
is divided into 32-bit mes-
sage words m
0
∥m
1
∥···∥m
15
, and a 128-bit value p
0
is
set to H
i
. Then, p
j+1
← R
j
(p
j
,m
π( j)
) is computed for
j = 0, 1, . . . , 63, where R
j
is the step function for step
j explained later. Finally, p
64
+ H
i
is output as H
i+1
.
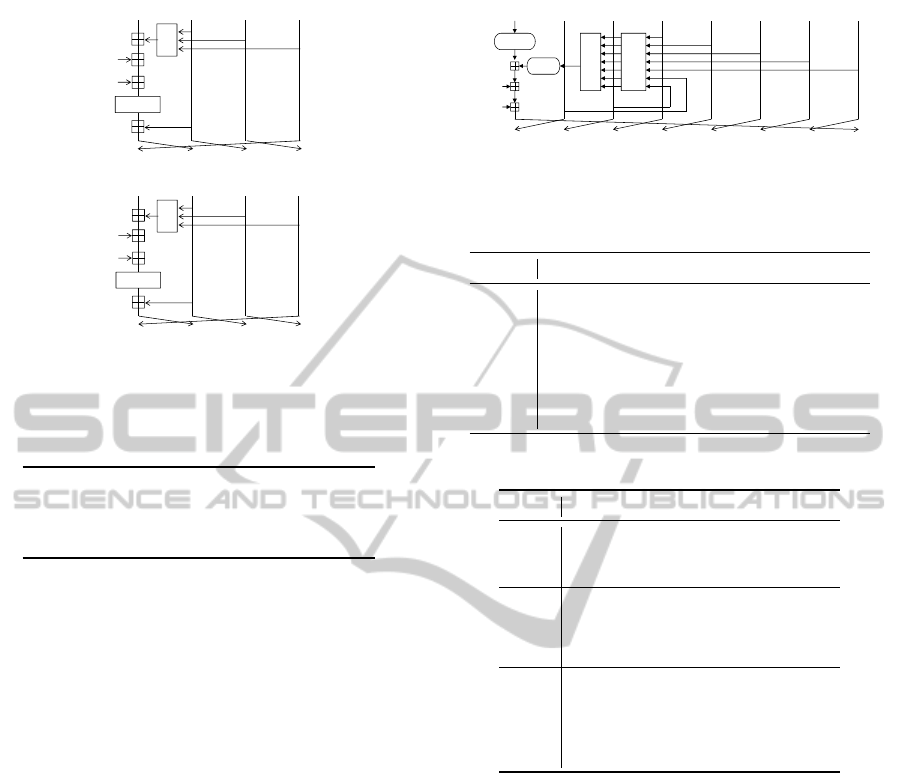
The step function is shown in Figure 2. Let Q
j
be a
32-bit value satisfying p
j
= (Q
j−3
∥Q
j
∥Q
j−1
∥Q
j−2
).
The step function R
j
(p
j
,m
π( j)
) first computes
Q
j+1
← Q
j
+ (Q
j−3
+ Φ
j
(Q
j
,Q
j−1
,Q
j−2
) + m
π( j)
+
k
j
) ≪ s
j
, and then output p
j+1
as p
j+1
←
(Q
j−2
,Q
j+1
,Q
j
,Q
j−1
). Here, Φ
j
,k
j
, and ≪ s
j
are
the bitwise Boolean function, constant value, and
left rotation defined in the specification, respectively.
π( j) is an MD5 message expansion. Refer to (Rivest,
1992) for details. In Table 2, we give the specification
of π( j), which is important for our paper.
Meet-in-the-MiddlePreimageAttacksRevisited-NewResultsonMD5andHAVAL
113
Q
jͲϯ
Q
j
Q
jͲϭ
Q
jͲϮ
Φ
j
m
π
(j)
k
j
<<<
s
j
Q
jͲϮ
Q
j+1
Q
j
Q
jͲϭ
Q
j-3
Q
j
Q
j-1
Q
j-2
Φ
j
m
π
(j)
k
j
<<<
s
j
Q
j-2
Q
j+1
Q
j
Q
j-1
Figure 2: MD5 step function for step j.
Table 2: Message expansion of MD5. The number in the
i-th row (0 ≤ i ≤ 3) and the j-th column (0 ≤ j ≤ 15) rep-
resents the message-word index for step 16 · i + j.
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
1 6 11 0 5 10 15 4 9 14 3 8 13 2 7 12
5 8 11 14 1 4 7 10 13 0 3 6 9 12 15 2
0 7 14 5 12 3 10 1 8 15 6 13 4 11 2 9
2.2 Specification of HAVAL
HAVAL adopts the narrow-pipe Merkle-Damg
˚
ard
structure, which uses a 256-bit chaining variable and
a 1024-bit message block to compute a compres-
sion function. The number of steps in the compres-
sion function is chosen from either 96, 128, or 160,
where the corresponding algorithms are called 3-pass
HAVAL, 4-pass HAVAL, and 5-pass HAVAL, respec-
tively. Due to the similarity to MD5, we omit the de-
scription of the domain extension.
Let haval : {0, 1}
256
× {0,1}
1024
→ {0,1}
256
be
the compression function of HAVAL. First, M
i
is di-
vided into 32-bit message words m
0
∥m
1
∥···∥m
31
and
a 256-bit value p
0
is set to H
i
. Then, p
j
is iteratively
updated with the step function p
j+1
← R
j
(p
j
,m
π( j)
)
for j = 0, 1, . . . , r, where r = 32x − 1 for x-pass
HAVAL. Finally, p
r+1
+ H
i
is output as H
i+1
.
R
j
is the step function for Step j, which is de-
picted in Figure. 3. Q
j
is a 32-bit value satisfying
p
j
= (Q
j−7
∥Q
j−6
∥···∥Q
j
). R
j
for x-pass HAVAL is
defined as follows:
T
j
= f
j
◦ ϕ
x, j
(Q
j−6
,Q
j−5
,··· , Q
j
),
Q
j+1
= (Q
j−7
≫ 11) + (T
j
≫ 7) + m
π( j)
+ k
x, j
,
R
j
(p
j
,m
π( j)
) = (Q
j−6
∥Q
j−5
∥...∥Q
j
∥Q
j+1
),
where f
j
is a bitwise Boolean function defined in
Table 3, ϕ
x, j
is a word-wise permutation defined in
Table 4, π
j
is a message expansion function defined
Q
j-7
Q
j-6
Q
j-5
Q
j-4
Q
j-3
Q
j-2
Q
j-1
Q
j
Q
j-6
Q
j-5
Q
j-4
Q
j-3
Q
j-2
Q
j-1
Q
j
Q
j+1
>>>11
>>>7
f
j
φ
x,j
m
π(j)
k
x, j
Figure 3: HAVAL step function for step j
Table 3: Boolean functions of HAVAL. x
a
x
b
represents bit-
wise AND operation.
j f
j
(x
6
,x
5
,.. .,x
0
)
0–31 x
1
x
4
⊕ x
2
x
5
⊕ x
3
x
6
⊕ x
0
x
1
⊕ x
0
32–63 x
1
x
2
x
3
⊕ x
2
x
4
x
5
⊕ x
1
x
2
⊕ x
1
x
4
⊕ x
2
x
6
⊕
x
3
x
5
⊕ x
4
x
5
⊕ x
0
x
2
⊕ x
0
64–95 x
1
x
2
x
3
⊕ x
1
x
4
⊕ x
2
x
5
⊕ x
3
x
6
⊕ x
0
x
3
⊕ x
0
96–127 x
1
x
2
x
3
⊕ x
2
x
4
x
5
⊕ x
3
x
4
x
6
⊕ x
1
x
4
⊕ x
2
x
6
⊕
x
3
x
4
⊕ x
3
x
5
⊕ x
3
x
6
⊕ x
4
x
5
⊕ x
4
x
6
⊕ x
0
x
4
⊕ x
0
128–159 x
1
x
4
⊕ x
2
x
5
⊕ x
3
x
6
⊕ x
0
x
1
x
2
x
3
⊕ x
0
x
5
⊕ x
0
Table 4: Wordwise rotations of HAVAL.
Input x
6
x
5
x
4
x
3
x
2
x
1
x
0
ϕ
3,1
x
1
x
0
x
3
x
5
x
6
x
2
x
4
ϕ
3,2
x
4
x
2
x
1
x
0
x
5
x
3
x
6
ϕ
3,3
x
6
x
1
x
2
x
3
x
4
x
5
x
0
ϕ
4,1
x
2
x
6
x
1
x
4
x
5
x
3
x
0
ϕ
4,2
x
3
x
5
x
2
x
0
x
1
x
6
x
4
ϕ
4,3
x
1
x
4
x
3
x
6
x
0
x
2
x
5
ϕ
4,4
x
6
x
4
x
0
x
5
x
2
x
1
x
3
ϕ
5,1
x
3
x
4
x
1
x
0
x
5
x
2
x
6
ϕ
5,2
x
6
x
2
x
1
x
0
x
3
x
4
x
5
ϕ
5,3
x
2
x
6
x
0
x
4
x
3
x
1
x
5
ϕ
5,4
x
1
x
5
x
3
x
2
x
0
x
4
x
6
ϕ
5,5
x
2
x
5
x
0
x
6
x
4
x
3
x
1
in Table 5, ≫ s is an s-bit right rotation, and k
x, j
is a
constant defined in the specification.
3 MEMORY EFFICIENT LOCAL-
COLLISION TECHNIQUE
In this section, we explain that the local-collision
technique (Sasaki and Aoki, 2008) can be performed
with lower amount of memory with keeping the same
time complexity, and then apply this improvement to
the previous preimage attack on 4-pass HAVAL.
3.1 Previous Attack on 4-pass HAVAL
The previous attack separates the 128-step compres-
sion function into two independent chunks as shown
in Table 6. All bits of the message words m
24
and
m
5
are chosen as the free bits for the forward chunk
SECRYPT2013-InternationalConferenceonSecurityandCryptography
114
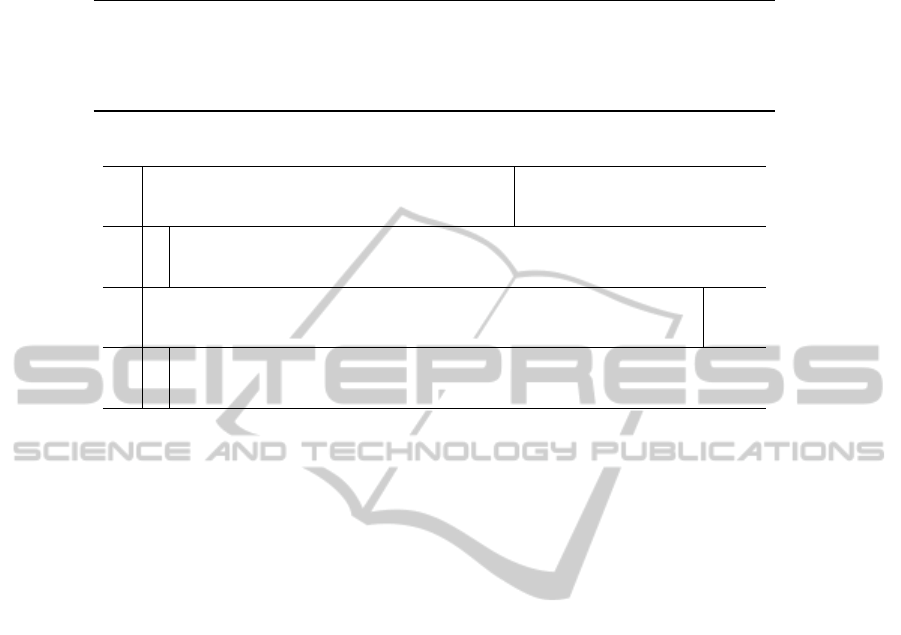
Table 5: Message expansion of HAVAL. The number in the i-th row (0 ≤ i ≤ 4) and the j-th column (0 ≤ j ≤ 31) represents
the message-word index for step 32 · i + j.
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
5 14 26 18 11 28 7 16 0 23 20 22 1 10 4 8 30 3 21 9 17 24 29 6 19 12 15 13 2 25 31 27
19 9 4 20 28 17 8 22 29 14 25 12 24 30 16 26 31 15 7 3 1 0 18 27 13 6 21 10 23 11 5 2
24 4 0 14 2 7 28 23 26 6 30 20 18 25 19 3 22 11 31 21 8 27 12 9 1 29 5 15 17 10 16 13
27 3 21 26 17 11 20 29 19 0 12 7 13 8 31 10 5 9 14 30 18 6 28 24 2 23 16 22 4 1 25 15
Table 6: Message word distribution for 4-pass HAVAL.
Step 0 1 2 3 4 5 6 7 ··· 20 21 22 23 24 25 26 27 28 29 30 31
index 0 1 2 3 4 5⃝ 6 7 ·· · 20 21 22 23 24⃝ 25 26 27 28 29 30 31
backward chunk ← local-collision
Step 32 33 34 · ·· 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63
index 5⃝ 14 26 · ·· 30 3 21 9 17 24⃝ 29 6 19 12 15 13 2 25 31 27
→ forward chunk
Step 64 65 66 67 68 69 70 71 72 73 74 75 76 77 ··· 90 91 92 93 94 95
index 19 9 4 20 28 17 8 22 29 14 25 12 24⃝ 30 ··· 21 10 23 11 5⃝ 2
forward chunk skip
Step 96 97 98 · ·· 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127
index 24⃝ 4 0 ··· 22 11 31 21 8 27 12 9 1 29 5⃝ 15 17 10 16 13
backward chunk
and the backward chunk, respectively, which means
that m
24
never appears during the backward chunk
and m
5
never appears during the forward chunk. In
Table 6, m
24
and m
5
are stressed by circles. Note
that each message word appears exactly once in ev-
ery 32 steps. Besides two chunks, Table 6 contains
two other steps called “local-collision” and “skip”.
For the local-collision part, as we will explain the
mechanism later, the attack can be performed as if the
message-word positions of m
24
in step 24 and m
5
in
step 32 were swapped. This enables the attacker to
avoid the dependency between two chunks caused by
these message words. For the skip part, the attacker
cannot continue the independent computations (from
neither direction) due to the use of the free bits for
the opposite chunk. However, even if they cannot be
computed, the match of the results from two chunks
can be partially confirmed. We refer to the original
paper (Sasaki and Aoki, 2008) for the details. Briefly
speaking, the forward chunk fully computes the 256-
bit value p
94
and the backward chunk fully computes
the 256-bit value p
97
. Because the step function of
HAVAL updates only 32 bits of the internal state in
each step, the forward chunk still contains 224-bit in-
formation of p
95
, 192-bit information of p
96
, and 160-
bit information of p
97
. Hence, the attacker can match
the 160-bit information of p
97
from both chunks.
The local collision part lies between step 24 and
step 32, where the input to step 24 is p
24
=
(Q
17
∥Q
18
∥···∥Q
24
) and m
24
, and step 32 outputs
p
33
= (Q
26
∥Q
27
∥···∥Q
33
) by using m
5
. The main
idea of this technique is to fix the value of seven 32-bit
variables Q
18
∥···∥Q
24
so that the value of Q
25
, which
is the updated value in step 24, does not give any influ-
ence in the subsequent seven steps. This is achieved
by using the absorption property of f
j
, which makes
T
25
to T
32
constant irrespective of the value of Q
25
.
Then, Q
33
, which is the updated value in step 33, be-
comes solely dependent of the value of Q
25
, and is
expressed as follows:
Q
33
= Q
25
≫ 11 + T
33
+ k
33
+ m
5
= (Q
17
≫ 11 + c
24
+ m
24
) ≫ 11 + c
33
+ m
5
,
(1)
where c
j
is the constant value denoted by T
j
+k
j
. Be-
cause the equation includes the free bits for the both
chunks, the independent computation cannot be per-
formed. To solve this problem, the previous work
firstly ignored the relationship in Eq. 1 (32-bit con-
straint), and regard all bits of m
24
and Q
33
as the free
bits for the forward chunk, and all bits of m
5
and Q
17
as the free bits for the backward chunk. Because each
chunk has 64 free bits, the attack can be faster than the
brute force attack by a factor of 2
64
at this stage, while
the memory requirement is about 2
64
words to store
the results of at least one chunk. After the match of
two independent computations are found, the attacker
checks if Eq. 1 is satisfied or not. The probability that
Eq. 1 is satisfied is 2
−32
. In the end, the previous work
finds pseudo-preimages faster than the brute force at-
tack by a factor of 2
32
, which is 2
256−32
= 2
224
. Fi-
nally, the pseudo-preimage attack is converted to a
preimage attack with the complexity of 2
241
.
3.2 Idea of Our Improvement
We show that the local-collision technique can be
performed only with a memory requirement of 2
32
Meet-in-the-MiddlePreimageAttacksRevisited-NewResultsonMD5andHAVAL
115

words. The sketch of the idea is already given in Fig-
ure 1. For simplicity, let us omit the cyclic shift in
Eq. 1 and c
24
= c
33
= 0. Then, the equation becomes
Q
33
= Q
17
+ m
24
+ m
5
.
Due to the property of the local-collision, the value of
Q
17
+ m
24
only impacts to Q
33
but never impacts to
other variables. Therefore, the order of the addition
can be swapped. Then, we write the equation as
Q
33
− m
24
= Q
17
+ m
5
.
Suppose that Q
33
− m
24
= x and Q
17
+ m
5
= x for
some x. Here, we fix the value of x to any value, say
x = 0. Then, for any value of m
5
, which is the free
bits for the backward chunk, we can compute the cor-
responding Q
17
by x − m
5
. Similarly, for any value
of m
24
, we can compute the corresponding Q
33
by
x + m
24
. In the end, each chunk only contains 32 free
bits with the relationship among Q
17
,m
24
,Q
33
,m
5
al-
ways satisfied. This achieves the meet-in-the-middle
attack faster than the brute force attack by a factor of
2
32
only with a memory requirement of 2
32
words.
Our approach has the same efficiency as the previous
work but has a lower memory requirement.
3.3 Application to 4-pass HAVAL
We then extend our idea for the exact form of Eq. 1.
Due to the cyclic shift, exchanging the positions of
m
24
and m
5
is not straight-forward. For simplicity, we
label Q
24
≫ 11 + c
24
as Q
′
24
and Q
33
− c
33
by Q
′
33
.
Then, Eq. 1 becomes as follows:
Q
′
33
= (Q
′
24
+ m
24
) ≫ 11 + m
5
.
If the following relation
(Q
′
24
+ m
24
) ≫ 11 = (Q
′
24
≫ 11) + (m
24
≫ 11)
(2)
is satisfied, then we can derive
Q
′
33
− (m
24
≫ 11) = (Q
′
24
≫ 11) + m
5
.
Suppose that Q
′
33
− (m
24
≫ 11) = (Q
′
24
≫ 11) +
m
5
= x for some x. Then, whenever we choose m
24
,
Q
′
33
(and thus Q
33
as well) can be computed indepen-
dently of m
5
by x + (m
24
≫ 11). The same is applied
for (Q
′
24
,m
5
).
Unfortunately, Eq. 2 is not always satisfied.
Hence, we experimentally verify the success proba-
bility of this equation. The strategy is counting up
how many times Eq. 2 is satisfied for all possibilities
of (Q
′
24
,m
24
). However, this is infeasible due to the
too large space (2
64
values). Therefore, we execute
a small experiment with reducing the word-size to 16
bits. The exact code for the experiment written by the
C language is given in Appendix. From the experi-
ment, we obtain that the success probability of Eq. 2
is about 2
−2
. Intuitively, Eq. 2 is satisfied when
Table 7: Message word distribution for full MD5.
Step 0 1 2 3 4 5 6 7 8 9 10 11 12 13 1415
index 0 1 2 3 4 5 6⃝ 7 8 9 10 11 12 13 14⃝15
backward chunk initial
Step 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
index 1 6⃝ 11 0 5 10 15 4 9 14⃝ 3 8 13 2 7 12
structure forward chunk
Step 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47
index 5 8 11 14⃝ 1 4 7 10 13 0 3 6⃝ 9 12 15 2
forward chunk skip
Step 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63
index 0 7 14⃝ 5 12 3 10 1 8 15 6⃝ 13 4 11 2 9
skip backward chunk
1. a carry does not occur from bit position 11 to 12.
2. a carry does not occur from bit position 31.
Due to the two conditions, the success probability is
about 2
−2
.
In the end, we perform the meet-in-the-middle
part by assuming that Eq. 2 is always satisfied. We
then later check the consistency of Eq. 2 only for the
matched pairs, which is satisfied with 2
−2
. Hence,
our attack achieves the memory requirement of 2
32
words, but loses the advantage of the time complex-
ity by a factor of 2
2
. Thus the time complexity of the
pseudo-preimage attack is 2
256−(32−2)=2
226
, and this
is converted to a preimage attack with the time com-
plexity of 2
(256+226)/2+1
= 2
242
.
4 IMPROVED ATTACK ON MD5
With the similar technique used for 4-pass HAVAL,
we can reduce the memory requirement for the preim-
age attack on full MD5.
4.1 Previous Attack on MD5
The previous attack separates the 64-step compres-
sion function into two independent chunks as shown
in Table 7. m
14
and m
6
are chosen as the free bits
for the forward chunk and the backward chunk, re-
spectively. 4 steps between steps 14 and 17 are called
“initial structure”, where its role is the same as the
local-collision technique, namely, the attack can be
performed as if the message-word positions of m
14
in
step 14 and m
6
in step 17 were swapped.
One of the most significant techniques of their at-
tack is the construction of the initial-structure. They
analyzed the step function in details and separated
those 4 steps so that the forward computation with
m
14
and the backward computation with m
6
are inde-
pendent each other. The construction is very compli-
cated and thus we refer to the original paper (Sasaki
SECRYPT2013-InternationalConferenceonSecurityandCryptography
116

Q
Q
Q
Φ
m
k
<<<
Q
Q
18
Q
Q
Q
Q
Q
Q
Φ
m
k
<<<
Q
Q
18
Q
Q
Q
m Q
m
!"!########
!$
0-20,
29-31
0-4,
17-20,
29-31
Figure 4: Construction of the initial-structure for step 17.
and Aoki, 2009) for the details. Here, we only ex-
plain the related part, which is the last step of the
initial-structure, i.e., step 17. The left-hand side in
Figure 4 shows the computation in step 17 by the pre-
vious work. Before step 17, the free bits of m
14
in
step 14 propagates to Q
15
,Q
16
,Q
17
, while in step 17,
the free bits of m
6
in step 17 will propagate to Q
14
. In
Figure 4, the forward computation depending of m
14
is drawn by black bold lines and the backward com-
putation depending of m
6
is drawn by grey bold lines.
Because the equation
Q
18
= (Q
14
+ Φ
17
+ m
6
+ k
17
) ≪ 9 + Q
17
(3)
depends on the both chunks, Q
18
and Q
14
cannot be
computed independently. To solve this problem, the
previous work regards two variables (20 bits in Q
14
and 24 bits in m
6
) as free bits for the backward chunk
and two variables (32 bits in Q
18
and 12 bits in m
14
) as
free bits for the forward chunk. After the match of the
meet-in-the-middle part, the consistency of the 32-bit
relation in Eq. 3 is checked with a probability of 2
−32
.
Note that the free bits of m
6
are bit positions 0–20 and
29–31, while bit positions 5–16 of Q
14
must be fixed
to some value in order to construct the initial-structure
properly.
In the end, the improved factor for the time com-
plexity is about 2
44
due to the meet-in-the-middle part
but it loses the advantage by a factor of 2
32
with the
consistency check. According to (Sasaki and Aoki,
2009), the complexity of the pseudo-preimage attack
is 2
116.86
, and this is converted to a preimage attack
with a complexity of 2
123.4
. The memory requirement
is about 2
44
for the meet-in-the-middle part. If all the
details are taken into account, the memory require-
ment is 2
45
as claimed in (Sasaki and Aoki, 2009).
4.2 Our Improvement
With exchanging the order of additions in step 17, we
can avoid the probabilistic consistency check, which
enables us to perform the attack only with one free
variable and thus the memory requirement is signif-
icantly reduced. The details are given in the right-
hand side of Figure 4. We fix the value of Q
14
+m
6
to
0xFFFFFFFF in advance. Then, for any value of the
free bits for the backward chunk m
6
, we can compute
Q
14
by 0xFFFFFFFF −m
6
= 0xFFFFFFFF +1+m
6
=
m
6
, where m
6
is the bit complement of m
6
. There-
fore, for a given m
6
, we can derive the corresponding
Q
14
bit-by-bit, without the carry effect. In the for-
ward chunk, for any value of the free bits of m
14
and
the corresponding Q
15
,Q
16
,Q
17
, we can compute Q
18
by (0xFFFFFFFF + Φ
17
+ k
17
) ≪ 9 + Q
17
.
We also need to ensure that free bits of m
6
do not
break the fixed bits of Q
14
. We simply reduce the
number of free bits of m
6
: use only bit positions 0-4,
17-20, and 29-31, in total 12 bits. The other bits are
fixed. Then, the free bits of m
6
never impact to the
fixed bits of Q
14
, and the free bits of Q
14
can be set to
any value by choosing the corresponding bits of m
6
.
For the entire attack, we compute the forward
chunk with 12 free bits in m
14
and compute the back-
ward chunk with 12 free bits in m
6
. The memory
requirement is now reduced to about 2
12
message
words. With all the details, the memory requirement
becomes 2
13
message words with the same reason
as the previous work. The other part of the attack
is exactly the same as the previous work. Thus the
time complexity does not change, which is 2
116.86
for
pseudo-preimages and 2
123.4
for preimages.
5 NEW ATTACKS ON 3-PASS
HAVAL AND 5-PASS HAVAL
In this section, we extend the previous preimage at-
tack on 5-pass HAVAL from 151 steps to 158 steps,
and present the first 1-block preimage attack on 3-
pass HAVAL. We evaluate the step function in details
with the recent techniques. Specifically, we analyze
the initial-structure and the matching part in a bit-wise
level, and search for new choices of free bits.
5.1 158-step Attack on 5-pass HAVAL
The chunk separation is shown in Table 8. We choose
m
25
as free bits for the forward chunk and m
5
for
the backward chunk. Steps 25 to 32 are forming the
initial-structure and steps 94 to 109 are the matching
part with some partial computation.
5.1.1 Construction of the Initial-structure
We locate the initial-structure between steps 25 and
32. Namely, we need to guarantee that p
33
is inde-
Meet-in-the-MiddlePreimageAttacksRevisited-NewResultsonMD5andHAVAL
117
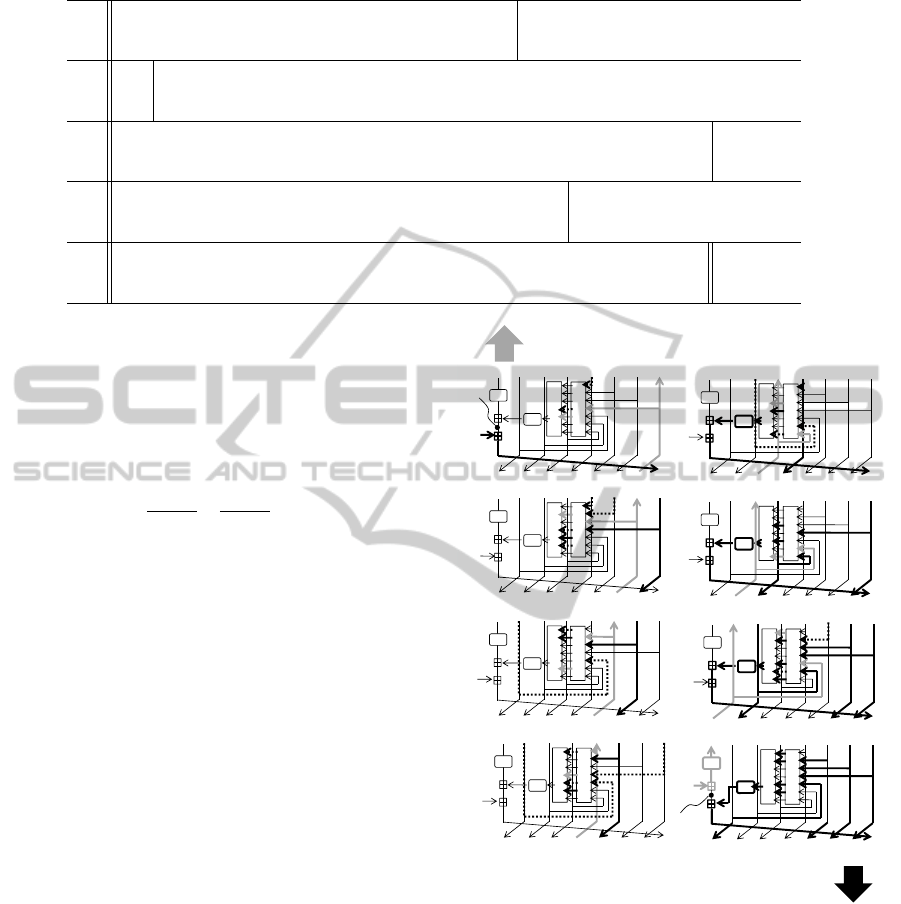
Table 8: Message word distribution for 5-pass HAVAL reduced to 158 steps.
Step 0 1 2 3 4 5 6 7 8 9 ··· 23 24 25 26 27 28 29 30 31
index 0 1 2 3 4 5⃝ 6 7 8 9 ··· 23 24 25⃝ 26 27 28 29 30 31
backward chunk initial-structure
Step 32 33 34 35 36 37 38 39 40 41 42 43 44 45 ··· 59 60 61 62 63
index 5⃝ 14 26 18 11 28 7 16 0 23 20 22 1 10 ··· 13 2 25⃝ 31 27
forward chunk
Step 64 65 66 67 68 69 70 71 72 73 74 75 76 77 · ·· 91 92 93 94 95
index 19 9 4 20 28 17 8 22 29 14 25⃝ 12 24 30 ··· 10 23 11 5⃝ 2
forward chunk skip
Step 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 ··· 124 125 126 127
index 24 4 0 14 2 7 28 23 26 6 30 20 18 25⃝ 19 ·· · 1 29 5⃝ 15
skip backward chunk
Step 128 · ·· 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159
index 27 ··· 31 10 5⃝ 9 14 30 18 6 28 24 2 23 16 22 4 1 25⃝ 15
backward chunk excluded
pendent of the free bits m
π(32)
and p
25
is indepen-
dent of the free bits m
π(25)
. Firstly, we set bit po-
sitions 31–25 of m
π(25)
and bit positions 31–22 and
5–0 of m
π(32)
as free bits. The free bits of m
π(25)
im-
pacts to bit positions 31–25 of Q
26
and the free bits
of m
π(32)
impacts to bit positions 16–1 of Q
25
. Note
that Q
25
is computed by (x − m
π(32)
) ≪ 11. We can
avoid the carry by setting x = 0xFFFFFFFF so that
x −m
π(32)
= x+1+m
π(32)
= m
π(32)
. Secondly, we fix
other chaining variables so that the change of the free
bits does not propagate through the f
j
function. How
chaining variables are fixed is shown in Table 9 and
Fig. 5. In the following, we explain the details of the
computation step by step.
In Table 9, 0, 1, C, C
i
, X , x, and Y denote
0x00000000, 0xFFFFFFFF, (− f
25
≪ 4) − (k
5,25
≪
11), a fixed value, free bits for the forward chunk, a
value dependent on X, and free bits for the backward
chunk, respectively. In Fig. 5, numbers written in a
small bold font denote the value of each variable. The
notation a
b
represents that the one-bit value a con-
tinues for b bits. For example, X
7
0
25
means that bit
positions 24–0 are set to 0 and 31–25 are set to free
bits for the forward chunk. We also use notations
For
and
Back
to denote free bits for the forward and back-
ward chunks, respectively, Black and gray bold lines
represent data lines depending on the free bits for the
forward and backward chunks, respectively. Dotted
lines represent data lines that are fixed to absorb the
impact of the free bits via f
j
. Narrow lines repre-
sent data lines that are always fixed irrespective of the
value of the free bits.
Now we explain how to construct the initial-
structure step by step. In step 26, the f
j
function is
Q
24
Q
25
⊕Q
21
Q
22
⊕Q
26
Q
23
⊕Q
20
Q
24
⊕Q
20
. To make
the output independent of the free bits in Q
25
, we fix
the corresponding bits of Q
24
to 0. Similarly, to make
the output independent of Q
26
, we fix Q
23
to 0. There-
fore, the output of f
26
is always constant even if Q
25
m
25
For
k
5,25
f
25
φ
Q
19
Q
20
Q
21
Q
26
Q
24
Q
23
Q
22
Q
21
Q
22
Q
23
Q
28
Q
27
Q
24
Q
27
Q
32
Q
31
Q
30
Q
29
Q
28
Q
23
Q
24
Q
30
Q
29
Q
28
Q
27
Q
24
Q
31
Q
30
Q
29
Q
28
Q
27
Q
20
Q
21
Q
22
Q
27
Q
24
Q
23
Q
27
Q
28
Q
33
Q
32
Q
31
Q
30
Q
29
Q
22
Q
23
Q
24
Q
29
Q
28
Q
27
Q
22
Q
23
Q
24
Q
29
Q
28
Q
27
m
26
k
5,26
f
26
m
27
k
5,27
f
27
m
28
k
5,28
f
28
m
29
k
5,29
f
29
φ
m
30
k
5,30
f
30
m
31
k
5,31
f
31
m
5
Back
k
5,32
f
32
Ϭ
ϭϱ
z
ϭϲ
Ϭ
y
ϳ
Ϭ
Ϯϱ
y
ϳ
Ϭ
Ϯϱ
y
ϳ
Ϭ
Ϯϱ
y
ϳ
Ϭ
Ϯϱ
y
ϳ
Ϭ
Ϯϱ
y
ϳ
Ϭ
Ϯϱ
y
ϳ
Ϭ
Ϯϱ
y
ϳ
Ϭ
Ϯϱ
y
ϳ
Ϭ
Ϯϱ
dž
dždždž
dždž
dž dždž dž
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
ϭ
ϯϮ
ϭ
ϯϮ
φ
φ
φ
φ
φ
φ
y
ϳ
Ϭ
Ϯϱ
Ϭ
ϯϮ
Q
18
Q
19
Q
20
Q
24
Q
23
Q
22
Q
21
Q
25
Q
25
Q
25
Q
25
Q
25
Q
25
Q
25
Q
25
Q
25
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Q
26
Q
26
Q
26
Q
26
Q
26
Q
26
Q
26
Q
26
ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
Ϭ
ϯϮ
ϭ
ϯϮ
ϭ
ϯϮ
ϭ
ϯϮ
Ϭ
ϯϮ
z
ϭϬ
Ϭ
ϭϲ
z
ϲ
Ϭ
ϭϱ
z
ϭϲ
Ϭ
Ϭ
ϭϱ
z
ϭϲ
Ϭ
Ϭ
ϭϱ
z
ϭϲ
Ϭ
Ϭ
ϭϱ
z
ϭϲ
Ϭ
Ϭ
ϭϱ
z
ϭϲ
Ϭ
Ϭ
ϭϱ
z
ϭϲ
Ϭ
Ϭ
ϭϱ
z
ϭϲ
Ϭ
Ϭ
ϭϱ
z
ϭϲ
Ϭ
Figure 5: Initial-structure for 5-Pass HAVAL.
and Q
26
change.
Similarly, in steps 27 and 28, Q
25
and Q
26
are ab-
sorbed by fixing the other chaining variables as shown
in Table 9. Note that free bits for the forward chunk
denoted by X can give impact to p
33
. Therefore, in
steps 29, 30, and 31, we do not set conditions to ab-
sorb the impact from X, and we only consider absorb-
ing the impact from Q
25
.
Finally, p
33
is computed independently of m
π(32)
and p
25
is computed independently of m
π(25)
.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
118

Table 9: Fixed values in the initial-structure for 5-pass HAVAL reduced to 158 steps
step Conditions m
π( j)
Q
j−7
Q
j−6
Q
j−5
Q
j−4
Q
j−3
Q
j−2
Q
j−1
Q
j
j to absorb Q
25
to absorb Q
26
25 Q
22
= 0 m
25
⃝ C C
1
C
2
0 0 0 0 0
7
Y
25
26 Q
24
= 0 Q
23
= 0 m
26
C
1
C
2
0 0 0 0 0
7
Y
25
X
7
0
25
27 Q
24−0
21
= Q
24−0
26
Q
25
= 0 m
27
C
2
0 0 0 0 0
7
Y
25
X
7
0
25
0
28 Q
28
= 0 Q
22
= Q
27
m
28
0 0 0 0 0
7
Y
25
X
7
0
25
0 0
29 Q
24
= 0 m
29
0 0 0 0
7
Y
25
X
7
0
25
0 0 1
30 Q
26
= 0 m
30
0 0 0
7
Y
25
X
7
0
25
0 0 1 x
31 Q
29
= 1 m
31
0 0
7
Y
25
X
7
0
25
0 0 1 x x
32 m
5
⃝ 0
7
Y
25
X
7
0
25
0 0 1 x x x
33 X
7
0
25
0 0 1 x x x x
5.1.2 Computations for the Skipped Part
Next we explain how to partially compute steps 94–
96 and 109–104. The details are shown in Fig 6 and
Fig 7. In step 94 for example, the equation of Q
95
is
as follows: Q
95
= ((Q
87
≫ 11) + ( f
94
(ϕ
94
(Q
88
,Q
89
,
...,Q
94
)) ≫ 7) + k
5,94
) + m
5
. Bit positions 21–6 of
m
5
are fixed values, so we can compute bit positions
21–6 of Q
95
. First, we compute the sum of Q
87
≫ 11,
k
5,94
and the output of f
94
. Then, we compute the ad-
dition with m
5
to obtain the value of Q
21−6
95
, where the
superscript represents the computable bit positions.
Because bit positions 5–0 of m
5
are unknown, there
are two possible carry patterns from bit position 5 to
6. We consider both carry patterns and proceed the
attack for both of them. The carry information should
be stored so that we can later check the correctness of
the carry assumption. We use variables C
For
a
and C
Back
a
which store the assumed value for the carry. Note that
each carry assumption costs only one bit of memory
but the computational complexity increases.
In step 95 for example, the equation of
Q
96
is as follows: Q
96
= (Q
88
≫ 11) +
( f
95
(ϕ
95
(Q
89
,Q
90
,...,Q
95
)) ≫ 7) + m
π(95)
+ k
5,95
.
Q
95
, whose 16 bits are fixed, is used in the f
j
function, thus we can compute 16 bits of Q
96
. Let the
value after the right cyclic shift by 7 bits be v, and
then, we uniquely obtain v
31,14−0
. Here, we do not
use v
31
, because holding this value will not contribute
to the matching part. Finally we compute the addition
of Q
88
≫ 11, v
14−0
, m
π(95)
, and K
5,95
, and then we
uniquely obtain the value of Q
14−0
96
.
Similarly, we partially compute the step function
in steps 96, 109, 108, 107, 106, 105, and 104, to ob-
tain bit positions 31 and 7–0 of Q
97
from both chunks.
Finally, the match at bit positions 31 and 7–0 of Q
97
,
in total 9 bits, can be performed.
5.1.3 Attack Procedure
1. Set chaining variables and message words but the
free bits in order to satisfy the initial structure and
several constraints for the padding string.
2. For bit positions 31–25 of m
25
, in total 7 free bits,
compute the forward chunk with guessing two un-
known carry bits for the skipped part. Store 9 bits
(bit positions 31 and 0–7) of Q
97
for each guess.
We obtain 2
7
· 2
2
= 2
9
candidates.
3. For bit positions 31–22 and 5–0 of m
5
, in total 16
free bits, do as follows.
(a) Compute the backward chunk with guessing
five unknown carry bits for the skipped part to
obtain 9 bits (bit positions 31 and 0–7) of Q
97
.
We obtain 2
16
· 2
5
= 2
21
candidates.
(b) Check whether or not the 9 bits of Q
97
match.
(c) If 9 bits match, check whether the other bits of
p
97
match and all of the carry assumptions are
correct.
(d) If correct, the corresponding (p
0
,M) is a
pseudo-preimage. Otherwise, repeat this pro-
cedure with choosing other values for randomly
fixed message words in phase 1.
5.1.4 Complexity Evaluation
Let the complexity of 1 step be
1
158
compression func-
tion computations. Roughly speaking, the computa-
tion for the forward chunk requires 2
9
·
68
158
compres-
sion function computations and the memory require-
ment is about 2
9
state values. The computation for
the backward chunk requires 2
21
·
81
158
compression
function computations. Hence, the time complexity
is about 2
20
compression function computations.
The complexity can be improved by considering
the attack details. For example, the unknown carry
Meet-in-the-MiddlePreimageAttacksRevisited-NewResultsonMD5andHAVAL
119
m
2
k
5,95
m
24
k
5,96
f
96
φ
Q
95
Q
96
Q
89
Q
94
Q
93
Q
92
Q
91
Q
90
Q
95
Q
96
Q
97
Q
94
Q
93
Q
92
Q
91
Q
90
Q
87
Q
88
Q
89
Q
94
Q
93
Q
92
Q
91
Q
90
m
5
Back
k
5,94
f
94
φ
Q
95
Q
88
Q
89
Q
94
Q
93
Q
92
Q
91
Q
90
f
95
φ
Figure 6: Partial-computation for the
matching part in the forward chunk.
m
18
k
5,108
f
108
m
25
For
k
5,109
f
109
φ
φ
m
30
k
5,106
f
106
φ
m
6
k
5,105
f
105
φ
m
20
k
5,107
f
107
φ
m
26
k
5,104
f
104
φ
Q
97
Q
98
Q
99
Q
104
Q
103
Q
102
Q
101
Q
100
Q
105
Q
98
Q
99
Q
104
Q
103
Q
102
Q
101
Q
100
Q
105
Q
106
Q
107
Q
104
Q
103
Q
102
Q
101
Q
100
Q
105
Q
106
Q
99
Q
104
Q
103
Q
102
Q
101
Q
100
Q
105
Q
106
Q
107
Q
104
Q
103
Q
102
Q
101
Q
108
Q
105
Q
106
Q
107
Q
104
Q
103
Q
102
Q
109
Q
108
Q
105
Q
106
Q
107
Q
104
Q
103
Q
110
Q
109
Q
108
Q
105
Q
106
Q
107
Q
104
Q
103
Q
102
Q
101
Q
100
Figure 7: Partial-computation for the matching part in the backward chunk.
bits occur in the very last of the computation for
each chunk. Hence, the complexity of the forward
chunk can be 2
7
·
66
158
+ 2
7
· 2 ·
1
158
+ 2
7
· 2
2
1
158
rather
than 2
9
·
68
158
. By considering such an optimization,the
sum of the complexity for the forward and backward
chunks becomes 2
14
·
1169
158
< 2
17
. This means that we
can obtain 2
7+16−9
= 2
14
pairs where 9 bits match
with a complexity of 2
17
. Therefore, by repeating
the above procedure 2
233
times, we expect to obtain a
pseudo-preimage. Finally, the complexity of finding a
pseudo-preimage of 5-pass HAVAL is 2
17+233
= 2
250
,
and this is converted to a preimage with a complexity
of 2
254
. In the attack procedure, the dominant mem-
ory complexity is for the forward chunk, which re-
quires about 2
9
internal state values.
5.2 1-block Attack on 3-pass HAVAL
The overall strategy is the same as the 1-block preim-
age attack on MD4 (Aoki and Sasaki, 2009). To gen-
erate 1-block preimages, we must fix p
0
to the orig-
inal HAVAL’s IV . To achieve this, we use two free
variables in the backward chunk, i.e., we cancel the
impact of changing one free variable by changing the
other variable so that p
0
can be a fixed value. Our
chunk separation is shown in Table 10, where two
message words (m
19
,m
27
) are the free bits for the
backward chunk and m
28
is the free bits for the for-
ward chunk.
To cancel the impact of changing m
27
with m
19
during the backward computation, we need to guar-
antee that m
19
and m
27
form a local-collision in steps
19-27. Therefore we fix chaining variables so that the
change of a chaining variable directly affected by m
19
and m
27
does not propagate through the Boolean func-
tions. How chaining variables are fixed is shown in
Table 11, where ∗ denotes a flexible value which de-
pends on m
19
and m
27
. The Boolean function f
j
for
steps 19 to 27 has the absorption property. For ex-
ample for j = 20, the Boolean function is Q
18
Q
17
⊕
Q
14
Q
20
⊕ Q
15
Q
19
⊕ Q
16
Q
18
⊕ Q
16
. Q
20
is a flexible
value, so Q
14
is fixed to 0 to make the output of f
20
in-
dependent of Q
20
. Similarly, in other steps, the impact
of Q
20
is absorbed by fixing other chaining variables.
In this attack, similarly to the attack on 5-pass
HAVAL, we consider the unknown carry effect when
we compute the skipped part for steps 56 to 68. The
strategy for the partial computation is basically the
same as the one for 5-pass HAVAL, because rotation
numbers are identical in all steps. Due to the page
limitation, we omit the details. The attack procedure
is as follows.
Attack Procedure
1. Fix the chaining variables and message words for
steps 19 to 27 to form a local collision as shown
in Table 11. Then, fix m
29
,m
30
, and m
31
to satisfy
the padding string for a 1-block message.
2. Randomly determine the message words m
i
,
where i ∈ {8, 9, . . . ,18,27}, and compute the step
function from step 19 to 8. After this step, p
8
is
computed.
3. Set p
0
to IV . With a given p
0
and p
8
, compute the
message words m
i
(i ∈ {0,1,...,7}) that connect
these values. This is done by inverting the step
function with respect to m
i
.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
120

Table 10: Message word distribution for 3-pass HAVAL.
Step 0 1 2 3 ··· 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
index 0 1 2 3 ··· 16 17 18 19⃝ 20 21 22 23 24 25 26 27⃝ 28⃝ 29 30 31
fixed local collision forward
Step 32 33 34 35 36 37 38 ··· 52 53 54 55 56 57 58 59 60 61 62 63
index 5 14 26 18 11 28⃝ 7 ··· 17 24 29 6 19⃝ 12 15 13 2 25 31 27⃝
forward chunk skip
Step 64 65 66 67 68 69 70 71 ··· 84 85 86 87 88 89 90 91 92 93 94 95
index 19⃝ 9 4 20 28⃝ 17 8 22 ··· 1 0 18 27⃝ 13 6 21 10 23 11 5 2
skip backward chunk fixed
Table 11: Fixed values for the local-collision in 3-pass HAVAL.
step j Condition to set off Q
20
m
π( j)
Q
j−7
Q
j−6
Q
j−5
Q
j−4
Q
j−3
Q
j−2
Q
j−1
Q
j
19 m
19
⃝ C
0
C
1
0 C
2
0 C
3
C
4
0
20 Q
14
= 0 m
20
C
1
0 C
2
0 C
3
C
4
0 ∗
21 Q
16
= 0 m
21
0 C
2
0 C
3
C
4
0 ∗ 0
22 Q
18
= Q
19
= 0 m
22
C
2
0 C
3
C
4
0 ∗ 0 1
23 Q
21
= 0 m
23
0 C
3
C
4
0 ∗ 0 1 C
5
24 Q
22
= 1 m
24
C
3
C
4
0 ∗ 0 1 C
5
0
25 Q
24
= 0 m
25
C
4
0 ∗ 0 1 C
5
0 C
6
26 Q
26
= 0 m
26
0 ∗ 0 1 C
5
0 C
6
0
27 m
27
⃝ ∗ 0 1 C
5
0 C
6
0 C
7
28 m
28
0 1 C
5
0 C
6
0 C
7
C
8
4. Compute the backward chunk until step 88. Note
that phase 1 to phase 4 are independent of the free
bits for both chunks.
5. For all possible values of bit positions 31–20 of
m
19
in total 12 free bits, do as follows.
(a) Compute m
27
accordingly so that the impact of
m
19
is canceled.
(b) Compute the backward chunk with guessing 3
unknown carry bits. As a result, we store 2
12
·
2
3
= 2
15
candidates of bit positions 31–25 and
5–0, in total 13 bits of Q
59
.
6. For all possible values of bit positions 31–23 and
5–0 of m
28
in total 15 free bits,
(a) Compute the forward chunk with guessing 1
unknown carry bit. As a result, we obtain
2
15
· 2
1
= 2
16
candidates of bit positions 31–25
and 5–0, in total 13 bits of Q
59
.
(b) Check whether both Q
59
computed from the
forward and backward chunks match in the 13
bits.
(c) If 13 bits match, check whether all of the other
internal state bits match and the carry assump-
tions are correct. If correct, the corresponding
M is a preimage.
(d) If a preimage is not found, repeat this procedure
with choosing other values for randomly fixed
message words.
The complexity of this attack is as follows. Steps 1
to 4 are independent of the free bits for both chunks.
The complexity is negligible compared to the other
steps. Step 5 requires the complexity of 2
12
· 2
3
·
23
96
,
and provides 2
15
items in the table. Step 6a requires
the complexity of 2
15
· 2 ·
31
96
, and provides 2
16
can-
didates. After step 6b 2
18
(= 2
15
· 2
16
· 2
−13
) pairs
will remain. In step 6c, for the remaining 2
18
candi-
dates, we compute a few steps, and check the correct-
ness of the carry assumption for 4 bits. This requires
about 2
18
·
8
96
steps, which is less than 2
15
. After that,
2
14
(= 2
18
· 2
−4
) pairs will remain.
If all the complicated details are considered, the
sum of the above complexity becomes 2
14
·
119
96
, which
is less than 2
15
. This means that we can obtain
2
14
pairs where 13 bits match with a complexity of
2
15
. Therefore, by repeating the above procedure 2
229
times, we expect to obtain a preimage. Finally, the
complexity of finding a 1-block preimage of 3-pass
HAVAL is 2
244
.
In the attack procedure, the dominant memory
complexity is for Step 5, which requires 2
15
candi-
dates to be stored. Therefore the memory complexity
of our attack is about 2
15
states.
6 CONCLUSIONS
In this paper, we showed that the memory require-
ment for the previous local-collision technique can
be significantly reduced. We then applied our ob-
servation to the previous preimage attacks on MD5
Meet-in-the-MiddlePreimageAttacksRevisited-NewResultsonMD5andHAVAL
121

and HAVAL. Consequently, we improved the mem-
ory complexity of the previous preimage attack on full
MD5 from 2
45
to 2
13
and on full 4-pass HAVAL from
2
64
to 2
32
. Moreover, we extended the preimage at-
tack on 5-pass HAVAL from 151 steps to 158 steps,
and presented the first preimage attack with a single
block message for 3-pass HAVAL.
REFERENCES
Aoki, K. and Sasaki, Y. (2009). Preimage attacks on one-
block MD4, 63-step MD5 and more. In Avanzi,
R. M., Keliher, L., and Sica, F., editors, Selected Areas
in Cryptography SAC 2008, volume 5381 of Lecture
Notes in Computer Science, pages 103–119, Berlin,
Heidelberg, New York. Springer-Verlag.
Aumasson, J.-P., Meier, W., and Mendel, F. (2009). Preim-
age attacks on 3-pass HAVAL and step-reduced MD5.
In Avanzi, R. M., Keliher, L., and Sica, F., editors, Se-
lected Areas in Cryptography SAC 2008, volume 5381
of Lecture Notes in Computer Science, pages 120–
135, Berlin, Heidelberg, New York. Springer-Verlag.
Bogdanov, A., Khovratovich, D., and Rechberger, C.
(2011). Biclique cryptanalysis of the full AES. In
Lee, D. H. and Wang, X., editors, Advances in Cryp-
tology — ASIACRYPT 2011, volume 7073 of Lecture
Notes in Computer Science, pages 344–371, Berlin,
Heidelberg, New York. Springer-Verlag.
Leurent, G. (2008). MD4 is not one-way. In Nyberg, K.,
editor, Fast Software Encryption (FSE 2008), volume
5086 of Lecture Notes in Computer Science, pages
412–428, Berlin, Heidelberg, New York. Springer-
Verlag.
Menezes, A. J., van Oorschot, P. C., and Vanstone, S. A.
(1997). Handbook of applied cryptography. CRC
Press.
NIST (2007). Federal Register /Vol. 72, No. 212/Fri-
day, November 2, 2007/Notices. http://csrc.nist.gov/
groups/ST/hash/documents/FR Notice Nov07.pdf.
Rivest, R. L. (1992). Request for Comments 1321:
The MD5 Message Digest Algorithm. The Inter-
net Engineering Task Force. http://www.ietf.org/rfc/
rfc1321.txt.
Sasaki, Y. and Aoki, K. (2008). Preimage attacks on 3,
4, and 5-pass HAVAL. In Pieprzyk, J. P., editor,
Advances in Cryptology - ASIACRYPT 2008, volume
5350 of Lecture Notes in Computer Science, pages
253–271, Berlin, Heidelberg, New York. Springer-
Verlag.
Sasaki, Y. and Aoki, K. (2009). Finding preimages in
full MD5 faster than exhaustive search. In Joux,
A., editor, Advances in Cryptology — EUROCRYPT
2009, volume 5479 of Lecture Notes in Computer Sci-
ence, pages 134–152, Berlin, Heidelberg, New York.
Springer-Verlag.
Zheng, Y., Pieprzyk, J., and Seberry, J. (1993). HAVAL
— one-way hashing algorithm with variable length
of output. In Seberry, J. and Zheng, Y., editors, Ad-
vances in Cryptology — AUSCRYPT’92, volume 718
of Lecture Notes in Computer Science, pages 83–104.
Springer-Verlag, Berlin, Heidelberg, New York.
APPENDIX
The below is the code for the experiment. It returns
the following result (in a hexadecimal form).
#Success: 42084000
From this result, we obtain the success probability of
0x42084000/0xFFFFFFFF ≈ 2
−2
.
#include <stdio.h>
#include <math.h>
#include <stdlib.h>
typedef unsigned int UINT32;
UINT32 Q24,m24,temp1,temp2,count=0;
UINT32 rrotate(UINT32 x, int i);
int main(){
for(Q24=0;Q24<=0xFFFF;Q24++){
for(m24=0;m24<=0xFFFF;m24++){
temp1=rrotate(((Q24+m24)&0xFFFF),11);
temp2=((rrotate(Q24,11)+
rrotate(m24,11))&0xFFFF);
if(temp1==temp2){
count++;
}
}
}
printf("#Success: %08x\n",count);
return(0);
}
UINT32 rrotate(UINT32 x, int i){
return (x<<(16-i)|x>>i)&0xFFFF;
}
SECRYPT2013-InternationalConferenceonSecurityandCryptography
122
