
Secure Second Price Auctions with a Rational Auctioneer
Boaz Catane and Amir Herzberg
Department of Computer Science, Bar Ilan University, Ramat Gan, 52900, Israel
Keywords:
Auctions, Cryptographic Auction Schemes, Cryptographic Protocols, Vickrey Auctions.
Abstract:
We present novel security requirements for second price auctions and a simple, efficient and practical pro-
tocol that provably maintains these requirements. Novel requirements are needed because commonly used
requirements, such as the indistinguishability-based secrecy requirement of encryption schemes presented by
(Goldwasser and Micali, 1982), do not fit properly in the second price auctions context. Additionally, the pre-
sented protocol uses a trustworthy supervisor that checks if the auctioneer deviated from the protocol and fines
him accordingly. By making sure the expected utility of the auctioneer when deviating from the protocol is
lower than his expected utility when abiding by the protocol we ascertain that a rational auctioneer will abide
by the protocol. This allows the supervisor to optimize by performing (computationally-intensive) inspections
of the auctioneer with only low probability.
1 INTRODUCTION
Various types of auctions are used worldwide (En-
glish, Dutch, sealed bid, etc.), each with its own
advantages and disadvantages. Special interest has
been given to second
1
price sealed bid auctions (also
known as Vickrey auctions (Vickrey, 1961)), because
of their efficiency and simplicity: each bidder sends
only a single sealed bid, and the winning bidder
(sender of the maximal bid) pays the amount of the
second (or k
th
) highest bid. The optimal strategy for
players is to bid their true valuation of the goods,
hence these auctions are executed efficiently and se-
curely (assuming rational bidders).
In sealed bid auctions, the auctioneer advertises
the auction details, receives sealed bids and declares
the winner and the price she
2
has to pay for the goods
(the clearing price). Many works on such auctions fo-
cus on the actions taken by the bidders and regard the
auctioneer as part of the auction mechanism, assum-
ing he abides by the protocol. Because in such sealed
bid auctions only the auctioneer sees the bids and de-
clares the auction’s outcome, a ‘real world’ auction-
eer may misbehave, e.g. output false results or insert
a fictitious bid just below the highest honest bid to de-
ceitfully raise the clearing price. Hence, a mechanism
1
For simplicity, we focus on second price auctions, but
our results apply also to k
th
price auctions.
2
For clarity, we use ”she”, ”her”, etc. to refer to the
bidders, and ”he”, ”his”, etc. for other entities.
that carries out an auction correctly even in the face
of a misbehaving auctioneer is required.
We present a simple and efficient protocol ensur-
ing that a rational auctioneer will not misbehave, i.e.,
his expected utility from outputting the wrong out-
come or dishonestly affecting the outcome will be
lower than his expected utility when outputting the
auction’s true outcome. The protocol is based on a
trusted supervisor, that (randomly) inspects the out-
come reported by the auctioneer; we show that infre-
quent random inspections are sufficient to ensure that
a rational auctioneer will operate correctly. This is
significant since the supervisor - in our protocol and
other protocols - is an external entity trusted by both
bidders and auctioneer, which implies significant pro-
cessing costs.
1.1 Auctions: Entities and Interests
So far, there were only few real-world applications of
secure auction protocols, in spite of the many works
and protocols published. One reason for this may be
that existing proposals are rather complex, conceptu-
ally and computationally. Our goal is to design a sim-
ple and practical protocol for secure auctions.
A secure auction protocol would protect the in-
terests of all parties: bidders, auctioneer and owner.
Since these interests may be conflicting, we assume
the parties agree on an additional trusted party, whom
we refer to as the supervisor. The roles and interests
158
Catane B. and Herzberg A..
Secure Second Price Auctions with a Rational Auctioneer.
DOI: 10.5220/0004526101580169
In Proceedings of the 10th International Conference on Security and Cryptography (SECRYPT-2013), pages 158-169
ISBN: 978-989-8565-73-0
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

of the parties are as follows:
Owner. The entity owning goods to be auctioned.
The owner wants to receive a maximal price for
the goods, and in particular to receive the value of
the second-highest bid (minus the fee paid to the
auctioneer, if it exists).
Bidders. Parties that are interested in buying the auc-
tioned goods. They send sealed bids to the auc-
tioneer in order to win the auction. The winning
bidder is a bidder that bid the highest bid. The
winner pays no more than her bid and receives the
goods. Bidder interests include confidentiality of
the submitted bids (from other bidders and from
the auctioneer, at least while the auction takes
place), and integrity of the auction’s result (i.e.
that the correct (highest bidding) bidder wins and
that she is charged the correct amount offered in
the second-highest bid).
Auctioneer. Manages the auction by receiving bids
and outputting the winning bidder and the clear-
ing price. The auctioneer (usually) is a proxy for
the owner of the goods. Note that the auctioneer
may also be interested in purchasing the goods,
and may participate in the auction as a bidder by
inserting his own bids.
Supervisor. An entity trusted by the bidders and
owner which is used to ensure that the auction-
eer operates correctly and does not try to cheat.
The auctioneer also trusts the supervisor to oper-
ate adequately, e.g. to follow the protocol and al-
low the auction to end correctly. In practice, in
order for all parties to trust the supervisor he may
be implemented using tamper-resistant hardware
running attested-software, or using a set of mul-
tiple machines operated by different entities for
redundancy; both cases imply significant compu-
tational and communication costs. To decrease his
(amortized) work, the supervisor only checks the
auctioneer randomly; we show that this suffices
(for a rational auctioneer).
1.2 Contribution
This paper’s contributions are:
1. Presentation of novel security requirements ap-
propriate for second price auction schemes. These
requirements include validity, rational correct-
ness, secrecy and non-malleability. The com-
monly used encryption related security require-
ments, such as the indistinguishability-based se-
crecy (Goldwasser and Micali, 1982), do not
fit properly in the auctions context since an ad-
versary may legitimately learn some information
about bids (see Section 1.4).
2. Presentation of a simple and practical auction
scheme that provably maintains the aforemen-
tioned requirements. This is achieved using a
trusted supervisor that randomlyvalidatesthe auc-
tioneer’s behavior, which enables the protocol to
be very efficient.
1.3 Goals and Protocol Overview
Our protocol’s goals are threefold: Firstly, keep bids
secret from other bidders and from auctioneer until
the end of the bidding phase. If bids are not secret
then a correct clearing price cannot be guaranteed.
A malicious bidder might insert a bid that is only
slightly lower than the highest honest bid, resulting in
a fictitiously high clearing price. This goal is achieved
by using cryptographic tools such as encryption.
Secondly, minimize the trust in the auctioneer. In
sealed bid auctions the auctioneer declares the auc-
tion’s outcome after he alone receives all bids, which
are kept secret from all other entities. Such an entity
can easily manipulate the auction’s results by adding
or removing bids or by declaring false outcome. Min-
imizing the trust in the auctioneer is needed if bidders
are to participate in such an auction. This is attained
in the presented protocol by modeling the auctioneer
as a rational adversary and having a supervisor fine
him in case a false outcome is detected. The fine
is high enough such that the auctioneer’s expected
utility when abiding by the protocol is higher than
when cheating. Thus, a rational auctioneer will not
cheat. The supervisor, as opposed to the auctioneer,
is trusted either because he has less motivation to de-
viate from the protocol (since the bidders do not send
him money at any stage of the protocol) or because his
computation is done using secure and costly means
(e.g. secure hardware or secure multiparty computa-
tion).
Thirdly, have a practical and efficient protocol.
This goal, which is of utmost importance in our
scheme because of the use of costly means to imple-
ment a trusted supervisor, is achieved by using the
supervisor occasionally, i.e. only with some (small)
probability.
Figure 1 shows the high level overview of the pre-
sented protocol. In it, the auctioneer publishes the
auction details (e.g. item to be auctioned, deadline for
bid commitment submission, etc.), and bidders send
timed-commitments of their bids to the auctioneer.
The commitments are timed such that the auctioneer
is able to reveal the value of the bids but not before
the end of the bidding phase. The auctioneer pub-
SecureSecondPriceAuctionswithaRationalAuctioneer
159

Figure 1: Overview of the presented protocol: Auctioneer
publishes auction details. Bidders send timed-commitments
of bids to Auctioneer, and Auctioneer publishes them. After
the bidding phase Auctioneer sends the computed auction’s
outcome to Supervisor. After Supervisor signs on the out-
come Auctioneer sends clearing price to the winning bidder.
lishes the received commitments on a bulletin board
(e.g. the auctioneer’s website). After the end of the
bidding phase the auctioneer computes the auction’s
outcome (i.e. winning bidder and clearing price). The
supervisor (possibly) verifies auction’s outcome. If he
detects that the auctioneer tried to cheat he fines the
auctioneer. Otherwise, the supervisor signs the out-
come and sends his signature to the auctioneer. The
auctioneer then sends the supervisor-signed outcome
to the winning bidder.
Loosely speaking, the protocol ensures it will not
be beneficial for the auctioneer to cheat, i.e. devi-
ate from the protocol. Auctioneer’s cheating may
include influencing the auction’s outcome in a vari-
ety of ways: First, he can ignore bid commitments.
Second, the auctioneer can declare arbitrary false re-
sults (wrong winning bidder or wrong clearing price).
Third, the auctioneer can use knowledge about re-
ceived bids to add or remove specific bids. This may
influence the auction’s outcome in different ways:
1. After opening the commitments and seeing all
bids the auctioneer might insert a bid that is only
slightly lower than the highest honest bid. This
will make the winning bidder pay a fictitiously
high clearing price.
2. The auctioneer might insert in advance many dif-
ferent bids. After seeing the honest bids he might
remove bids that he inserted and that are higher
than the highest honest bid but leave the rest,
again making the winning bidder pay a fictitiously
high clearing price.
The protocol ensures that deviation from the protocol
would not be the auctioneer’s rational move.
Notice that some actions taken by the auctioneer
to influence the auction’s outcome are legitimate, and
do not result in a fine; in our formal modeling of utili-
ties these actions are legitimate and do not harm other
parties, although arguably in a practical deployment
some of these actions may be deemed inappropriate.
Firstly, the auctioneer may insert (himself or by a col-
laborating bidder) a commitment for a bid, and in case
his bid is the highest bid he wins the auction. This ef-
fectivelyintroducesa minimal price for the goods (i.e.
inserting such a bid ensures that the goods will not be
sold for a price lower than the auctioneer’s bid). This
is a legitimate strategy and we do not try to prevent
it. Secondly, in case of a tie (e.g. a few bidders bid
the highest bid) the auctioneer may choose a winner
arbitrarily. Such actions are not considered a fraud
since no bidder is harmed: The winning bidder pays
an amount equal to her bid (i.e. the second highest
bid) and receives the goods which she values as equal
to the paid price. Likewise, other bidders do not pay
or receiveanything and so no damage is inflicted upon
them. In reality, there may be some objection to this
modeling, e.g., since bidders may have preferred to
bid elsewhere, but this is not captured by the usual
modeling of utilities and will require further research.
1.4 Related Work
Auctions are a well studied subject; a few of the many
good references in this area include (Engelbrecht-
Wiggans, 1980; Milgrom and Weber, 1982; Klem-
perer, 2004). Special interest is given to second price
auctions (also known as Vickrey auctions) (Vickrey,
1961), in which the bidders’ optimal strategy is to bid
their true value of the auctioned goods.
Much work on the use of cryptography for con-
ducting secure auctions has focused on the goal of
complete privacy, where no one (including the auc-
tioneer) learns information about the bids even after
the auction has ended (e.g. (Harkavy et al., 1998;
Naor et al., 1999)); unfortunately, these solutions
have high computational requirements. Our proto-
col is much more efficient and hence more practi-
cal, although allowing the auctioneer and supervisor
to learn the values of the bids (but only after the end
of the bidding phase).
Some protocols achieve complete privacy by
bidder-resolved multi-party computation (Brandt,
2006). However, in many cases privacy is achieved
by using third parties, either through numerous auc-
tioneers or by asymmetric models in which in addi-
tion to the auctioneer the entity of a supervisor (or
SECRYPT2013-InternationalConferenceonSecurityandCryptography
160

auction issuer) is assumed (Naor et al., 1999; Lip-
maa et al., 2003). Parkes et al. (Parkes et al., 2008)
settle for verifiable correctness and trustworthiness in
combination with complete secrecy to all parties ex-
cept the auctioneer. However, their scheme demands
considerable time for preparation and verification of
auctions.
In contrast to the aforementioned work, we define
and require novel security requirements to capture the
notions of correctness, secrecy, and non-malleability
in the auctions context. Past works did not formally
define these requirements or even require all of them,
e.g. non-malleability, although using malleable en-
cryption for preserving bid secrecy can be disastrous,
as shown by Dolev et al. (Dolev et al., 1991). In addi-
tion, close observation reveals that the indistinguisha-
bility based secrecy definition (Goldwasser and Mi-
cali, 1982) commonly used for encryption schemes is
not fit for use in auctions, since an attacker may distin-
guish between encrypted messages and win the cryp-
tographic experiment by using legitimately learned
information about encrypted bids (i.e. the identity
of the winning bidder or the clearing price). Thus,
we settle for complete secrecy for all bidders (but
not the auctioneer or supervisor) and non-malleability
of bids, and analytically prove correctness. This is
achieved by using a supervisor and assuming the auc-
tioneer will deviate from the protocol if and only if it
maximizes his utility function.
In the following protocol we use timed commit-
ments. The general notion of timed cryptography
(e.g. an encrypted message that can only be decrypted
after a predetermined amount of time has passed)
was first introduced by (Rivest et al., 1996). Timed-
commitments, a commitment scheme in which there
is an optional forced opening phase enabling the re-
ceiver to recover (with effort) the committed value
without the help of the sender, were later presented
by (Boneh and Naor, 2000). Although their scheme
is sound, it has considerable computational overhead.
We note that our scheme can be adapted to use their
cryptographic primitive, but for efficiency reasons we
implement timed-commitments using a Time Lapse
Cryptography (TLC) Service that is similar to the one
presented in (Rabin and Thorpe, 2006). This TLC
service provides a commitment scheme which, in ad-
dition to the general hiding and binding properties of
commitments, ensures that the committed value can
be revealed at an exact time in the future even without
the help of the committing party.
A privacy and efficiency comparison of various
protocols is presented in Table 1. For each protocol
we count the (average) number of modular exponen-
tiations computed by each entity.
1.5 Current and Full Paper Versions
Some parts of this paper were omitted in the current
version due to lack of space and will appear only in
the full version
3
. The omitted parts include:
• Full proofs showing that the presented scheme
maintains all security requirement. In this version
only proof sketches are presented.
• Discussion about adversarial bidders. The current
version discusses only an adversarial auctioneer.
• Discussion regarding future research.
2 PRELIMINARIES
2.1 Model
In the supervised auction model there are n bidders
participating in an online sealed bid second price auc-
tion with an untrusted auctioneer. Each bidder ψ has
a private valuation v
ψ
for the goods being auctioned,
and each sends her bid b
ψ
to the auctioneer. Note that
in a second price auction bidding one’s true valuation
is the optimal strategy (i.e. b
ψ
= v
ψ
). The auction-
eer should output (ψ
win
, p) where ψ
win
is the winning
bidder (i.e. a bidder that bid the highest bid) and p
is the amount she has to pay (i.e. the clearing price,
which is equal to the second highest bid). If it maxi-
mizes his utility function, the auctioneer might output
different values than the true values of (ψ
win
, p). In
order to prevent him from deviating from the proto-
col and outputting false results a trusted third party, a
supervisor, checks the auction’s outcome, settles dis-
putes, and fines the auctioneer (if needed).
2.2 Time Lapse Cryptography Service
In the presented protocol we use timed-commitments
for hiding the bid values until the end of the bidding
phase. Implementation of timed-commitments can
be done using cryptographic methods, as presented
by (Boneh and Naor, 2000). For efficiency reasons,
our protocol uses a Time Lapse Cryptography (TLC)
Service resembling the one presented by Rabin and
Thorpe (Rabin and Thorpe, 2006). The TLC service
provides a cryptographic timed-commitment protocol
that enables the use of commitments with the classi-
cal hiding and binding properties. In addition, it pre-
vents bidders from refusing to open committed bids
3
The full version will be available at http://
eprint.iacr.org/
SecureSecondPriceAuctionswithaRationalAuctioneer
161
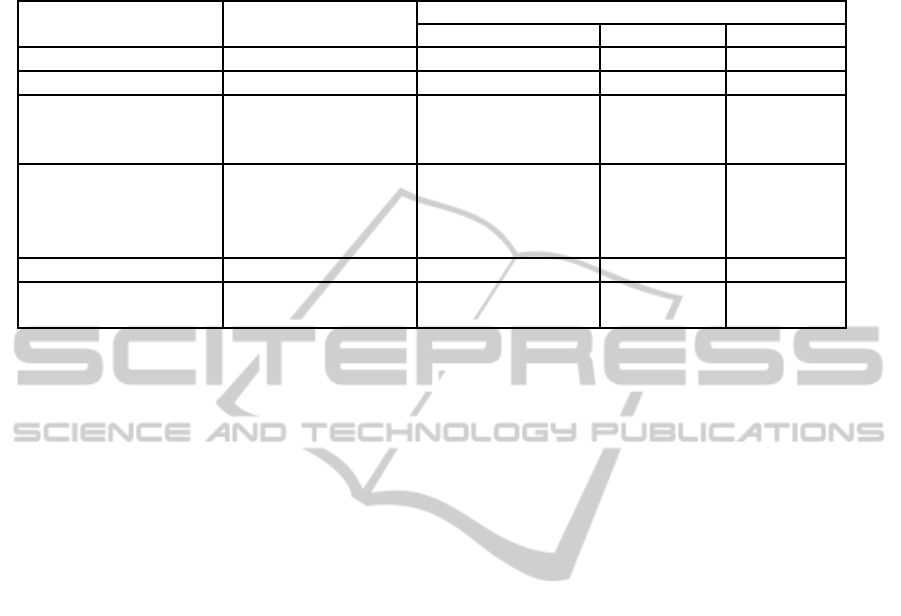
Table 1: Comparison of various secure auction schemes. Legend: n - Number of bidders; α - Probability that a third party
verifies auctioneer’s output; l - Maximum number of bits needed to represent a single bid; k - A constant used in (Parkes et al.,
2008).
Protocol Bids Privacy Kept No. of Modular Exponentiations
Single Bidder Auctioneer Third Party
Boneh and Naor, 2000 None 1 0 N/A
Our protocol From other bidders 2 2n+ 1 2+α(n−1)
Parkes et al., 2008 From other bidders n+ 5 kn + 3
(typically
k > 5400)
n
Lipmaa et al., 2003 From bidders and
Auctioneer. Third
party learns bid
statistics
O(l) O(2
l
) O(l)
Naor et al., 1999 From all entities O(l) O(nl) O(nl)
Juels and Szydlo, 2003 From all entities 2 (+ O(l) modular
multiplications)
O(nl) O(nl)
and also prevents the auctioneer from dropping re-
ceived commitments after he published them, claim-
ing not to have been able to open the committed bids.
The supervisor, acting as the TLC service provider,
publishes a public key of a non-malleable encryption
scheme before the auction begins, and sends the cor-
responding private key only when no new bids can be
sent (i.e. after the bid submission deadline).
Whenevertimed commitments are used in the pro-
tocol it is to say that a bidder encrypts her bid using
the supervisor-generated public encryption key. This
encrypted bid is to be opened later by the auctioneer
after receiving the corresponding decryption key.
2.3 Notation
If A is a probabilistic polynomial time (p.p.t) algo-
rithm that runs on input x, then A(x) denotes the ran-
dom variable corresponding to the output of A on in-
put x and uniformly random coins. In addition, we de-
note computational indistinguishability (Goldwasser
and Micali, 1984) of ensembles A and B by A
c
≈ B.
We will need to discuss vectors of values. A vec-
tor is denoted in bold font, as in x. We denote by |x|
the number of components in x, and by x.i the i-th
component, so that x = (x.1, ..., x.|x|). We extend set
membership notation to vectors, writing e.g. x ∈ x to
mean that x is in the set {x.i : 1 ≤ i ≤ |x|}. We also
extend the notation for algorithms with variables as
input to accept also vectors as input with the under-
standing that operations are performed component-
wise. Thus if A is an algorithm then x ← A(y) is
shorthand for the following: for 1 ≤ i ≤ |y| do x.i ←
A(y.i).
We will consider relations of arity d where d will
be polynomial in the security parameter k. Rather
than writing R(x
1
, . . . , x
d
) we write R(x, x) meaning
that the first argument is special and the rest are
bunched into a vector x with |x| = d − 1.
Regarding the auctioneer’s utility we use the fol-
lowing notations:
U denotes the auctioneer’s utility when abiding by
the protocol. This utility comprises the salary he
receives for functioning as an auctioneer plus any
rightfully won auction gains (in case he bid and
won the auction).
U
+
σ
denotes, for a given cheating (i.e. deviating from
the protocol) strategy σ, the auctioneer’s utility
when playing σ and not being caught.
U
−
σ
denotes, for a given cheating strategy σ, the auc-
tioneer’s utility when playing σ and being caught.
α denotes the probability that the auctioneer’s cheat-
ing will be caught (i.e. the probability that the
supervisor will check the auction’s outcome).
Note that the auctioneer’s expected utility when not
abiding by the protocol and playing some cheating
strategy σ is
(1− α)U
+
σ
+ αU
−
σ
(1)
Hence, abiding by the protocol would maximize his
expected utility iff for every cheating strategy σ the
following holds:
U ≥ (1 − α)U
+
σ
+ αU
−
σ
(2)
That is, a rational auctioneer would not cheat if his ex-
pected utility when abiding by the protocol is greater
than his expected utility when deviating from it.
2.4 Syntax of Auction Schemes
An auction scheme AUC = (KG, Bidder, De-
code, Auctioneer, Supervisor, Winner) consists of six
polynomial-time algorithms:
SECRYPT2013-InternationalConferenceonSecurityandCryptography
162

• The probabilistic key generation algorithm KG
takes as input an entity ψ ∈ {1, . . . , n} ∪ {A, S}
and a sting 1
k
, where k ∈ N is the security param-
eter, and returns a (Public key, Private key) pair.
• The probabilistic bidding algorithm Bidder takes
the following as input: As local input, Bidder re-
ceives a (Public key, Private key) pair and a nu-
meric bid value bid. Bidder also receives pub-
lic information (that may consist of the auction-
eer’s public key, details about the planned auction,
etc.). Additional information (such as the supervi-
sor’s public key) is received off-band. Bidder then
outputs a vector message that consists of mes-
sage.encoded
bid and message.id such that mes-
sage.encoded bid encodes bid while message.id
contains additional information (bidder’s identi-
fication information, commitment to pay for the
item in case the bidder won the auction, etc.).
Generating message.encoded
bid may require bid
and a secret key. In addition, the encoding string
may hide the numeric value of bid (i.e. may be the
output of an encryption process). The encoding is
reversible, namely bid can be retrieved from mes-
sage.encoded
bid by the Decode algorithm (see
below).
• The deterministic decoding algorithm Decode
takes as input a key Dec and a string en-
coded
bid and outputs the numeric value bid that
was used by Bidder to generate encoded
bid,
or ⊥ if no such bid exists. Formally, Decode
outputs bid such that for any auction
details,
bidder’s public and secret keys (pk, sk), nu-
meric bid value bid, auctioneer’s public key
A.pk, and supervisor’s public key S.pk and key
pair (Enc, Dec), if (message.encoded
bid, mes-
sage.id) ← Bidder(auction details, S.pk, A.pk,
pk, sk, Enc, bid) then bid ← Decode(Dec, mes-
sage.encoded
bid), otherwise ⊥ ← Decode(Dec,
message.encoded
bid).
We note that the Decode algorithm is mainly for
defining and proving the security requirements
(see Sections 2.5 and 4), and does not necessar-
ily need to be implemented in a real auction.
• The probabilistic auctioneering algorithm Auc-
tioneer takes as local input a (Public key, Private
key) pair. Furthermore, Auctioneer receives pub-
lic keys (such as the bidders’ or supervisor’s), and
may receive additional public or private informa-
tion (e.g. encoded bids) and a stage stg ∈ {‘init’,
‘receive’,‘outcome’}. If stg = ‘init’ the algorithm
outputs details about a planned auction. If stg =
‘receive’ the algorithm outputs state information
to be used later. If stg = ‘outcome’ the algorithm
outputs an auction’s outcome (i.e. the winning
bidder and the clearing price).
• The probabilistic auction supervising algorithm
Supervisor takes as input a (Public key, Private
key) pair, public information (that may consist
of the auctioneer’s public keys), additional in-
put from the auctioneer (such as auction details
or outcome), a probability α, and a stage stg ∈
{‘sign’, ‘generate’, ‘verify’}. If stg = ‘sign’ the
algorithm outputs a signature on the auction de-
tails input. If stg = ‘generate’ the algorithm out-
puts a (Public key, Private key) pair of a non-
malleable CPA-secure encryption scheme. If stg
= ‘verify’ it outputs either the string ‘Verified out-
come’ or a proof that the auctioneer cheated and
an amount fine the auctioneer needs to pay.
• The deterministic winner finding algorithm Win-
ner takes as input bids, a vector of bidders’ bids
and messages, a vector containing outputs of
the Bidder algorithm (namely, a vector of (en-
coded
bid, id) pairs) such that bidder i’s bid is
bids.i, and her encoded bid and identity informa-
tion is messages.i.encoded
bid and messages.i.id,
respectively. The algorithm outputs the winning
bidder ψ
winner
according to the auction rules (i.e.
ψ
winner
is the bidder that bid the highest bid. In
case more than one bidder bid the highest bid the
algorithm outputs the bidder whose encoded bid
has lexicographic precedence).
2.5 Requirements
An auction scheme is required to be secure, as defined
below.
Definition 1. An auction scheme is secure iff it is
valid, correct for a rational auctioneer, preserves se-
crecy, and non-malleable (as detailed below).
2.5.1 Validity
An auction scheme is said to be valid if, when the
supervisor checks the auction’s outcome, in case the
auctioneer deviated from the protocol he will be
caught with overwhelming probability. Formally, for
any auction scheme AUC = (KG, Bidder, Decode,
Auctioneer, Supervisor, Winner), adversary Adv and
k ∈ N we associate Experiment 1. In it, Adv has four
stages: init, details, encode and cheat. In the init stage
Adv is given a unary string 1
k
and outputs n ∈ N, the
number of participating bidders. In the details stage,
after a public and private key pair was issued to each
entity (the bidders, the auctioneer and the supervisor),
SecureSecondPriceAuctionswithaRationalAuctioneer
163

Adv receivesthe secret keys of all bidders
4
along with
all public keys. He then outputs an auction details
string that defines the auction. Possible details may be
the item to be auctioned, maximum allowed bid, etc.
Later, in the encode stage, Adv is invoked on behalf
of the bidders and is given the public key Enc gener-
ated by the supervisor. He outputs a vector messages
as the output of all bidders which is comprised of n
(bid encodings, identification string) pairs. Adv is in-
voked again, this time as the auctioneer, in the cheat
stage. He is given the key Dec and outputs the en-
coded bid of the winning bidder winning
encoded bid
and a clearing price p as the auction’s outcome. The
Supervisor is then given his private and public keys
along with the auction details, all encoded bids, the
declared outcome (winning
encoded bid, p), and 1 as
the probability to validate this auction, and outputs a
verification string. If Adv deviated from the proto-
col (i.e. winning
encoded bid is not the encoded bid
of the winning bidder or p is not the second highest
bid) while verification = ‘Verified outcome’ then the
experiment outputs 1, Otherwise it outputs 0. Note
that in addition to the above, in the details and encode
stages Adv outputs state information to be used later.
The advantage of adversary Adv in breaking the
validity of AUC is denoted by
Advantage
Validity
AUC , Adv
(k) =
Pr[Exp
Validity
AUC , Adv
(k) = 1] (3)
Definition 2. An auction scheme AUC is valid if for
any polynomial-time adversary Adv and k ∈ N the
function Advantage
Validity
AUC , Adv
(k) is negligible.
2.5.2 Rational Correctness
An auction scheme is correct for a rational auction-
eer if a rational auctioneer will not deviate from the
protocol, i.e. his expected utility when deviating from
the protocol is not greater than when abiding by it.
Formally, for every auctioneer’s strategy σ Equation
2 should hold (See Section 2.3).
2.5.3 Secrecy
An auction scheme preserves secrecy if no colluding
set of bidders is able to learn any nonessential infor-
mation about other bids even after the auction is over.
Consider two adversarially-chosen bidders (ψ
0
and
4
Although it may be sufficient to give Adv the secret
keys of colluding bidders only, we simplify this experiment,
as well as Experiments 2 and 3, by giving him the secret
keys of all bidders, as done in other works (e.g. (Bellare
et al., 2003)).
ψ
1
) who are assigned two adversarially-chosen bids
(bid
0
and bid
1
). A colluding group of (other) bidders
should not be able to tell which of ψ
0
and ψ
1
bade
either of the two bids with probability significantly
better than guessing.
Experiment 1: Exp
Validity
AUC , Adv
(k).
1: n ← Adv(‘init’, 1
k
)
2: for each ψ ∈ {1, . . . , n} ∪ {A, S} do
(ψ.pk, ψ.sk) ← KG(ψ, 1
k
)
3: (auction
details, St
1
) ← Adv(‘details’, S.pk,
A.pk, A.sk, 1.pk, 1.sk, . . . , n.pk, n.sk)
4: (Enc, Dec) ← AUC .Supervisor(‘generate’,
auction
details, S.pk, S.sk, A.pk, 1
k
)
5: (messages, St
2
) ← Adv(‘encode’, St
1
, Enc)
⊲ |messages| = n
6: (winning
encoded bid, p) ←Adv(‘cheat’, St
2
,
Dec)
7: verification ← AUC .Supervisor(‘verify’,
auction
details, S.pk, S.sk,
messages.1.encoded
bid, ...,
messages.n.encoded bid, Dec,
winning
encoded bid, p, 1)
8: for each i ∈ {1, . . . , n} do
9: bids.i ← AUC .Decode(Dec,
messages.i.encoded
bid)
10: ψ
winner
← AUC .Winner(bids, messages)
11: if
winning
encoded bid 6=
messages.ψ
winner
.encoded bid ∨ p 6=
second
highest(bids)
∧ verification = ‘Ver-
ified outcome’ then return 1
12: else return 0
Formally, for any auction scheme AUC = (KG,
Bidder, Decode, Auctioneer, Supervisor, Winner), ad-
versary Adv, k ∈ N and bit b we associate Experiment
2. In it, Adv has five stages: init, details, choose, en-
code and guess. In the init stage Adv outputs n, the
number of participating bidders, s.t. n > 1. In the de-
tails stage, after each entity (the bidders, the auction-
eer and the supervisor) received a public and private
key pair, Adv receives the secret keys of all bidders
and all public keys. He then outputs state information
St
1
and an auction
details string that defines the auc-
tion. Possible details may be the item to be auctioned,
maximum allowed bid, and so on. Later, in the choose
stage, Adv is given the public key Enc generated by
the supervisor and outputs state information St
2
along
with two special bidders ψ
0
, ψ
1
∈ {1, . . . , n} and two
bids bid
0
, bid
1
for these bidders. For each special bid-
der ψ
i
the following takes place: the Bidder algorithm
is invoked with bidder ψ
i
’s keys and bid bid
b⊕i
. Ad-
ditionally, the Auctioneer algorithm receives Bidder’s
output and saves state information in state. Later, for
SECRYPT2013-InternationalConferenceonSecurityandCryptography
164

Experiment 2: Exp
Secrecy-b
AUC , Adv
(k).
1: n ← Adv(‘init’, 1
k
) ⊲ n > 1
2: for each ψ ∈ {1, . . . , n} ∪ {A, S} do
(ψ.pk, ψ.sk) ← KG(ψ, 1
k
)
3: (auction
details, St
1
) ← Adv(‘details’, S.pk,
A.pk, 1.pk, 1.sk, . . ., n. pk, n.sk)
4: (Enc, Dec) ← AUC .Supervisor(‘generate’,
auction
details, S.pk, S.sk, A.pk, 1
k
)
5: (bid
0
, bid
1
, ψ
0
, ψ
1
, St
2
) ← Adv(‘choose’,
St
1
, Enc) ⊲ |bid
0
| = |bid
1
|, ψ
0
, ψ
1
∈
{1, . . . , n}, ψ
0
< ψ
1
6: state ← ⊥
7: for each i ∈ {0, 1} do
8: messages.ψ
i
←
AUC .Bidder(auction details, S.pk, A.pk,
ψ
i
.pk, ψ
i
.sk, Enc, bid
b⊕i
)
9: state ← AUC .Auctioneer(‘receive’,
auction
details, S.pk, A.pk, A.sk, 1.pk, . . .,
n.pk, messages.ψ
i
, state)
10: for each i ∈ {1, . . . , n} \ {ψ
0
, ψ
1
} do
11: (messages.i, St
2
) ← Adv(‘encode’,
St
2
, messages.ψ
0
.encoded
bid,
messages.ψ
1
.encoded bid, i)
12: state ← AUC .Auctioneer(‘receive’,
auction
details, S.pk, A.pk, A.sk, 1.pk, . . .,
n.pk, messages.ψ
i
, state)
13: (ψ
winner
, p) ← AUC .Auctioneer(‘outcome’,
state, Dec)
14: if ψ
winner
∈ {ψ
0
, ψ
1
} then b
′
← Adv(‘guess’,
St
2
)
15: else b
′
← Adv(‘guess’, St
2
, ψ
winner
, p)
16: if b
′
= b then return 1
17: else return 0
each non-special bidder i Adv is invoked in stage en-
code. Adv receives St
2
, i, and the encoded bids of the
two special bidders and outputs a vector message for
that bidder. The Auctioneer algorithm then receives
the vector message and outputs state. After all mes-
sages were received by Auctioneer he is invoked in
stage outcome with state and Dec as input and out-
puts the auction’s outcome, namely the winning bid-
der ψ
winnder
and the clearing price p. In the guess
stage, if the winning bidder is one of the two special
bidders then Adv receives state information St
2
only.
Otherwise, if the winning bidder is non-special then
Adv additionally receives the winning bidder’s name
and the clearing price. In either case Adv then out-
puts his guess, a bit b
′
. If b
′
= b then the experiment’s
output is 1, otherwise it returns 0.
The advantage of adversary Adv in breaking the
secrecy of AUC is denoted by
Advantage
Secrecy-b
AUC , Adv
(k) =
Pr[Exp
Secrecy-b
AUC , Adv
(k) = 1] − Pr[Exp
Secrecy-b
AUC , Adv
(k) = 0]
(4)
Definition 3. An auction scheme AUC preserves se-
crecy if for any polynomial-time adversary Adv, k ∈ N
and bit b the function Advantage
Secrecy-b
AUC , Adv
(k) is negli-
gible.
2.5.4 Non-malleability
Informally, non-malleability requires that an attacker,
after receiving an encoding of some bid, cannot mod-
ify it into an encoding of a different bid whose “mean-
ingfully related” to the original bid. This requirement
ensures that a set of colluding bidders and the auction-
eer cannot insert bids whose values depend on bids
of honest bidders. Following the work of Pass et al.
(Pass et al., 2006), we present this non-malleability
requirement using an indistinguishability based ex-
periment.
Formally, for any auction scheme AUC = (KG,
Bidder, Decode, Auctioneer, Supervisor, Winner), ad-
versary Adv and k, l ∈ N we associate Experiment 3.
In it, Adv has four stages: init, details, choose and
guess. In the init stage Adv outputs the number of
bidders that will participate in the auction. A public
and secret key pair is then generated and given to each
entity. In the details stage Adv receives the supervi-
sor’s public key along with the public and secret keys
of the auctioneer and all bidders (to capture the possi-
bility of an adversary colluding with both the auction-
eer and bidders). He then outputs the auction details
of his choice and state information St
1
. The supervi-
sor is then invoked and is given the auction details,
his public and private keys and the auctioneer’s pub-
lic key, and outputs a newly generated key pair (Enc,
Dec). Afterwards, in the choose stage, Adv is given
Enc and St
1
and is required to output a bidder ψ, two
bids bid
0
and bid
1
and state information St
2
. The Bid-
der algorithm is then invoked with auction
details, the
supervisor’s and auctioneer’s public keys, bidder ψ’s
public and private keys, Enc and bid
b
as input and
outputs a (encoded
bid, id) pair. In the guess stage
Adv receives St
2
along with bidder ψ’s encoded bid
and outputs a vector of length l containing encoded
strings. The experiment outputs a corresponding vec-
tor containing, for each encoding c
i
, the symbol ⊥ if
c
i
is identical to the challenge encoded
bid, or a de-
coding of c
i
(using the Decode algorithm) otherwise.
Adv is successful if the vector returned by the exper-
iment is computationally distinguishable when b = 0
compared to when b = 1.
SecureSecondPriceAuctionswithaRationalAuctioneer
165

Experiment 3: Exp
Non-Mal-b
AUC , Adv
(k, l).
1: n ← Adv(‘init’, 1
k
)
2: for each ψ ∈ {1, . . . , n} ∪ {A, S} do
(ψ.pk, ψ.sk) ← KG(ψ, 1
k
)
3: (auction
details, St
1
) ← Adv(‘details’, S.pk,
A.pk, A.sk, 1. pk, 1.sk, . . . , n.pk, n.sk)
4: (Enc, Dec) ← AUC .Supervisor(‘generate’,
auction
details, S.pk, S.sk, A.pk, 1
k
)
5: (ψ, bid
0
, bid
1
, St
2
) ← Adv(‘choose’, Enc, St
1
)
⊲ |bid
0
| = |bid
1
|
6: (encoded
bid, id) ←
AUC .Bidder(auction
details, S.pk, A.pk,
ψ.pk, ψ.sk, Enc, bid
b
)
7: (c
1
, ..., c
l
) ← Adv(‘guess’, St
2
, encoded
bid)
8: return (d
1
, ..., d
l
) where d
i
=
(
⊥ if c
i
= encoded
bid
AUC .Decode(c
i
) otherwise
Definition 4. Let AUC be an auction scheme and
let the random variable Exp
Non-Mal-b
AUC , Adv
(k, l) where b ∈
{0, 1}, Adv is an adversary algorithm and k, l ∈ N
denote the result of Experiment 3. AUC is non-
malleable if for any p.p.t algorithm Adv and for any
polynomial p(k), the following two ensembles are
computationally indistinguishable:
n
Exp
Non-Mal-0
AUC , Adv
(k, p(k))
o
k∈N
c
≈
n
Exp
Non-Mal-1
AUC , Adv
(k, p(k))
o
k∈N
(5)
3 THE PROTOCOL
3.1 Assumptions
In the presented protocol we assume the following:
• All entities have signature key pairs. Public keys
are known to all.
• All entities have synchronized clocks.
• The auctioneer has a certified bulletin board (such
as a website) to post public information.
• Communication delays for all messages are at
most ∆.
In addition to the above, the protocol uses an
encryption scheme that is non-malleable with re-
spect to chosen-plaintext attacks. We use the
indistinguishability-based definition of such non-
malleability, as presented by Pass et al. (Pass et al.,
2006). Informally, a non-malleable encryption
scheme with respect to chosen-plaintext attack en-
sures that an attacker, after choosing two plaintexts
and receiving an encryption of one of them, cannot
modify this encryption into an encryption of a dif-
ferent message that is “meaningfully related” to the
original one. Such an encryption scheme is needed to
maintain both the auction scheme’s secrecy and non-
malleability requirements.
3.2 The Protocol
Below are details of the presented protocol, as de-
picted in Figure 2.
1. The auctioneer sends auction details to the super-
visor and asks him to participate in the auction.
The auctioneer may pay the supervisor for his ser-
vices. Auction details include: details of the auc-
tioned goods; maximum allowed bid b
maxAl
; le-
gal commitment by the auctioneer to pay a fine
of value fine in case the supervisor presents proof
that the auctioneer deviated from the protocol; bid
commitment submission deadline t
sd
; maximum
number of bidders n
max
; auction ending time t
end
(see Section 3.2.1 for detailed computation of the
auction ending time).
2. If the supervisor accepts the auction details he ar-
Figure 2: Outline of the protocol. Auctioneer asks Super-
visor to participate in the auction and publishes auction de-
tails. Bidders send timed-commitments of bids to Auction-
eer. Supervisor helps Auctioneer open bids and compute
auction’s outcome, and then Supervisor (possibly verifies
and) signs on the outcome. Auctioneer sends clearing price
to winning bidder.
SECRYPT2013-InternationalConferenceonSecurityandCryptography
166

bitrarily sets α such that
α ≥
b
maxAl
fine+ b
maxAl
(6)
and sends the auctioneer a public key of a CPA-
secure non-malleable encryption scheme, along
with the supervisor’s signature on the key and the
auction details.
3. The auctioneer publishes the signed auction de-
tails and public key.
4. Each bidder i sends the auctioneer an encryption
of her bid. The bidder also sends a legal com-
mitment to pay for the goods (a price not higher
than her committed bid) in case the auctioneer
presents, no later than the auction ending time
t
end
, a supervisor-signed statement saying that this
bidder won the auction and needs to pay such and
such as clearing price. The message is signed by
the bidder’s private signing key.
5. After receiving each message the auctioneer ver-
ifies both that the bidder’s signature is valid and
that an identical encryption was not published ear-
lier on the bulletin board (otherwise the auction-
eer ignores the message). He then publishes the
encrypted bid on the bulletin board.
In case a bidder detects that her encrypted bid was
not published she will resend it to the supervi-
sor, who in turn, after verifying the bidder’s signa-
ture and that such an encrypted bid was not pub-
lished already, will forward it to the auctioneer. If
the auctioneer ignores encrypted bids forwarded
to him by the supervisor then the supervisor will
stop participating in the auction.
6. After time t
sd
+ 3∆, the supervisor saves all pub-
lished bid commitments (to be used later in case
he would verify the auction’s outcome), and sends
the secret decryption key to the auctioneer
5
.
7. The auctioneer decrypts all bids and computes
(i
′
, p
′
) where i
′
is the bidder with the highest bid
and p
′
is the amount she has to pay (i.e. the second
highest bid). He sends (i
′
, p
′
) to the supervisor.
In case of a tie the auctioneer chooses a winner
arbitrarily out of the set of highest bidders (e.g.
he chooses the highest bidder with lexicographi-
cal precedence.).
8. With probability α, the supervisor validates the
auction’s outcome: He decrypts all encrypted bids
he previously saved and verifies that the winning
bidder and clearing price are indeed (i
′
, p
′
). If the
5
According to Section 3.2.1 and Footnote 6, the last mo-
ment in which the supervisor might receive legitimate en-
crypted bids is t
sd
+ 3∆.
supervisor detects that the auctioneer cheated he
will fine him. In case the supervisor did not de-
tect cheating (either the auctioneer did not deviate
from the protocol or the supervisor did not verify
the auction’s outcome) he sends the auctioneer his
signature on (i
′
, p
′
).
9. The auctioneer sends the supervisor-signed values
(i
′
, p
′
) to the winning bidder.
3.2.1 Auction Ending Time
Note that the auctioneer can compute in advance an
upper bound for the auction’s ending time t
end
. The
ending time for the auction is no later than the time to
send a bid to the auctioneer in the worst case
6
, which
is t
sd
+ 4∆, plus time to decrypt n
max
encryptions and
compute the auction’s outcome twice (in case the su-
pervisor verifies the auctioneer’s computed outcome),
plus time to send 3 more messages (the auctioneer
sends outcome to the supervisor, supervisor replies
with signature, auctioneer sends outcome to winning
bidder). This computed bound is t
end
.
4 SECURITY ANALYSIS
Theorem 1. The presented scheme is secure.
Proof. Security of the scheme follows from Lemmas
1, 2, 3 and 4 asserting that the scheme is valid, correct
for a rational auctioneer, preserves secrecy, and non-
malleable, respectively.
Below are proof sketches for the aforementioned
lemmas. Full proofs will be presented in the full pa-
per
7
.
4.1 Validity
Lemma 1. The presented scheme is valid.
Proof sketch. We prove that the probability that the
auctioneer will not be caught by the supervisor when
deviating from the protocol if the supervisor validates
the auction’s outcome is negligible. This is done by
dividing the protocol into three phases, analyzing de-
viation at each phase separately, and proving that the
auctioneer cannot deviate in any phase without being
caught with overwhelming probability.
6
e.g. a bidder sends a bid at the last moment possible,
the auctioneer does not publish it, and the bidder resends it
to the auctioneer via the supervisor. So the last message is
received by the auctioneer at time t
sd
+ 4∆.
7
For the full paper version see footnote 3.
SecureSecondPriceAuctionswithaRationalAuctioneer
167

The protocol can be divided into the following
phases:
1. The preliminary phase: up until the auctioneer
publishes the auction details.
2. The submission phase: from the end of the pre-
liminary phase until the auctioneer stops receiving
new submissions (time t
sd
+ 4∆).
3. The outcome revelation phase: from time t
sd
+ 4∆
until the end of the auction (t
end
).
In the preliminary phase, publishing a supervisor-
signed false auction details will require forging of the
supervisor’s signature. In the submission phase the
auctioneer cannot ignore commitments since they will
be resent to the supervisor. He cannot learn informa-
tion about submitted bids and submit commitments
according to them because of the hiding property of
commitments. He cannot ignore bids after decrypting
them because the supervisor independently calculates
the auction’s outcome and will notice if the outcome
was changed because of bid ignoring. In the outcome
revelation phase the auctioneer can’t send the super-
visor wrong information since everything is already
published on the bulletin board. He cannot send a
bidder false outcome because the outcome needs to
be signed by the supervisor.
4.2 Rational Correctness
Lemma 2. The presented scheme is correct for a ra-
tional auctioneer.
Proof sketch. Equation 6 is used to show that the
auctioneer’s expected utility when cheating is non-
positive. Therefore, for any non-negativeutility U for
abiding by the protocol a rational auctioneer will not
cheat.
4.3 Secrecy
Lemma 3. The presented scheme preserves secrecy.
Proof Sketch. Secrecy of bids in the face of colluding
bidders is shown by reduction: If an adversary Adv
exists that has a non-negligible advantage in the se-
crecy experiment (Experiment 2) then an adversary
Adv’ can be constructed that has a non-negligible ad-
vantage in the non-malleability experiment of the un-
derlying CPA-secure encryption scheme: Adv’ uses
Adv to have a non-negligible advantage in the non-
malleability experiment defined by Bellare and Sahai
(Bellare and Sahai, 1999). This definition is strictly
weaker than the definition of Pass et al. (Pass et al.,
2006) which we use, and therefore Adv’ breaks the
non-malleability of the encryption used by the auc-
tion scheme.
4.4 Non-malleability
Lemma 4. The presented scheme is non-malleable.
Proof Sketch. The proof is fairly straightforward: if
an adversary Adv exists that can break the non-
malleability of the presented auction scheme then
an adversary Adv’ can be constructed that breaks
the non-malleability of the underlying encryption
scheme.
5 CONCLUSIONS
In this paper we presented novel security definitions
for the validity, rational correctness, secrecy, and non-
malleability of second price auction schemes. In ad-
dition, a simple and efficient scheme is presented in
which the security requirements hold. This is done
using a trusted supervisor which randomly validates
the auction’s outcome.
One may wonder,in case such a trusted supervisor
exists, why not let this trusted entity run the auction
instead of the auctioneer. One answer is that an entity
that validates the outcome but which does not receive
payments from the bidders (such as the supervisor)
has less incentive to cheat, as opposed to the auction-
eer. More importantly, in case there is a need for a
highly trusted supervisor, the supervisor program may
be run using secure means such as special hardware
or secure multiparty computation. Employing such
costly means for the supervisor may introduce sub-
stantial overhead. To ensure the protocol’s efficient
and practicality, such a costly supervisor may choose
to participate only in auctions where α is low enough,
guaranteeing both that the auction is secure and that
the supervisor has a low amount of expected compu-
tation. Notice, however, that requiring α to be small
may induce a high fine, since according to Equation 6
the lower bound of fine is:
fine ≥
(1− α)b
maxAl
α
(7)
Still, we believe there is enough freedom in tuning the
supervisor’s workload to ensure the scheme is practi-
cal.
ACKNOWLEDGEMENTS
We thank Alon Rosen, Yehuda Lindell, and Benny
SECRYPT2013-InternationalConferenceonSecurityandCryptography
168

Pinkas for their comments. Additionally, we thank the
following organizationsfor financially supporting this
research: The Israeli Ministry of Science and Tech-
nology, and the RSA division of EMC corporation.
REFERENCES
Bellare, M., Micciancio, D., and Warinschi, B. (2003).
Foundations of group signatures: Formal definitions,
simplified requirements, and a construction based on
general assumptions. In EUROCRYPT, pages 614–
629.
Bellare, M. and Sahai, A. (1999). Non-malleable
encryption: Equivalence between two notions,
and an indistinguishability-based characterization.
In Advances in cryptology-CRYPTO99, pages 78–
78. Springer. http://cseweb.ucsd.edu/∼mihir/papers/
nm.pdf.
Boneh, D. and Naor, M. (2000). Timed commitments. In
CRYPTO, pages 236–254.
Brandt, F. (2006). How to obtain full privacy in auc-
tions. International Journal of Information Security,
5(4):201–216.
Dolev, D., Dwork, C., and Naor, M. (1991). Non-malleable
cryptography. In Proceedings of the twenty-third an-
nual ACM symposium on Theory of computing, pages
542–552. ACM.
Engelbrecht-Wiggans, R. (1980). Auctions and bidding
models: A survey. Management Science, pages 119–
142.
Goldwasser, S. and Micali, S. (1982). Probabilistic en-
cryption & how to play mental poker keeping secret
all partial information. In Proceedings of the four-
teenth annual ACM symposium on Theory of comput-
ing, pages 365–377. ACM New York, NY, USA.
Goldwasser, S. and Micali, S. (1984). Probabilistic en-
cryption. Journal of computer and system sciences,
28(2):270–299.
Harkavy, M., Tygar, J., and Kikuchi, H. (1998). Elec-
tronic auctions with private bids. In Proceedings of
the 3rd USENIX Workshop on Electronic Commerce,
volume 31.
Klemperer, P. (2004). Auctions: theory and practice.
Lipmaa, H., Asokan, N., and Niemi, V. (2003). Secure
vickrey auctions without threshold trust. In Financial
Cryptography, pages 87–101. Springer.
Milgrom, P. and Weber, R. (1982). A theory of auctions
and competitive bidding. Econometrica: Journal of
the Econometric Society, pages 1089–1122.
Naor, M., Pinkas, B., and Sumner, R. (1999). Privacy pre-
serving auctions and mechanism design. In Proceed-
ings of the 1st ACM conference on Electronic com-
merce, pages 129–139. ACM.
Parkes, D., Rabin, M., Shieber, S., and Thorpe, C. (2008).
Practical secrecy-preserving, verifiably correct and
trustworthy auctions. Electronic Commerce Research
and Applications, 7(3):294–312.
Pass, R., Vaikuntanathan, V., et al. (2006). Construction of
a non-malleable encryption scheme from any semanti-
cally secure one. In Advances in Cryptology-CRYPTO
2006, pages 271–289. Springer.
Rabin, M. and Thorpe, C. (2006). Time-lapse cryptography.
Rivest, R., Shamir, A., and Wagner, D. (1996). Time-lock
puzzles and timed-release crypto.
Vickrey, W. (1961). Counterspeculation, auctions, and
competitive sealed tenders. The Journal of finance,
16(1):8–37.
SecureSecondPriceAuctionswithaRationalAuctioneer
169
