
Social Network Modelling for Counter Extremism
Comparing Criminality in Two Activist Networks
Rosemary Penny
1
, Robert Bowles
2
and Noémie Bouhana
1
1
Department of Security and Crime Science, University College London, Gower Street, London, U.K.
2
Department of Mathematics, University College London, Gower Street, London, U.K.
Keywords: Social Networks, Agent-based Modelling, Criminology.
Abstract: This paper examines the phenomenon of extreme protest activities in the environmental and animal rights
movements, and how their propagation can be simulated through the construction of agent-based models. It
uses criminological theory to examine what factors cause a propensity for violent action to spread across
social networks, and uses this as the basis for constructing agent-based models of the activist networks. The
differences in the results emerging from the models enable inferences to be made regarding which elements
in their construction may cause the differences. Modifying the models to explore how these differences in
construction affect the outputs from the models enables us to further understand which real-world factors
may contribute to differences in the spread of criminality through the social networks of activists.
1 INTRODUCTION
Social network modelling has undergone a
transformation in recent decades. In the 1980s and
1990s political scientists began to realise the benefits
of using graph theory to describe social systems
(Wasserman and Faust, 1994); (Diani, 2003). These
basic models have since grown in sophistication,
with social scientists increasingly looking to the
physical sciences for inspiration. Advances in
computational power have also had an impact, and
social scientists are now turning to computer
simulation as a viable method for answering
questions in their field, especially those involving
systems of interacting actors with heterogeneous
characteristics, such as might be found in a social
network (Townsley and Johnson, 2008). Simulation
has a number of advantages for the social scientist: it
is cheap, it is fast, it is easy to control the
environment, and it allows for an unlimited number
of repetitions (ibid).
This paper takes the field of social network
modelling further, by combining the techniques of
models rooted in disciplines such as kinetic theory
with the social theories of criminology. Drawing on
both social and physical science theory, this paper
reports on the construction of models describing the
spread of criminality through two networks of
activists. The differences in the construction of the
models are explored to see how they affect the
outputs from the models. Using the models in this
way enables them to be used as a tool that can
suggest explanations for the differences in the ways
the two groups protest.
2 BACKGROUND
2.1 Network Modelling
Network modelling has been well used in fields such
as fluid mechanics and statistical physics (Aletti et
al., 2007); (Benczik et al., 2009), though the
techniques used have only recently been applied to
social systems. Several theoretical models have been
developed which seek to describe social situations,
such as opinion formation and voting models (Wu
and Huberman, 2004); (Lanchier, 2010) which use
techniques originating in fields such as discrete
kinetic theory.
Broadly speaking there are two ways in which
one can model a network: equation-based modelling
(EBM) or agent-based modelling (ABM) (Parunak
et al., 1998). The key difference between these two
methods is in whether one seeks to model the
observables or the individuals in the system, with
EBMs examining the relationships between the
observables and ABMs considering the attributes of
382
Penny R., Bowles R. and Bouhana N..
Social Network Modelling for Counter Extremism - Comparing Criminality in Two Activist Networks.
DOI: 10.5220/0004586403820388
In Proceedings of the 3rd International Conference on Simulation and Modeling Methodologies, Technologies and Applications (SIMULTECH-2013),
pages 382-388
ISBN: 978-989-8565-69-3
Copyright
c
2013 SCITEPRESS (Science and Technology Publications, Lda.)

and interactions between individuals. ABMs have
some advantages over EBMs: they can be easier to
construct and understand, they have an extra level of
validation available (as they can be tested at either
the system or individual level), and they make it
easy to conduct “what if” experiments (ibid). As this
paper examines attributes of individuals and
interactions between them, the models developed in
this paper are all ABMs.
The aim of this paper is to see whether these
models can be constructed to describe real social
networks, in such a way that they can be used to
answer questions that would be difficult to answer
using conventional social science methods. The
networks on which this paper is based are networks
of political activists; the intention is to determine
whether differences in the levels of criminality
among protesters for two different causes can be
generated by models constructed to describe their
social networks, and if so which aspects of the
models have caused those differences. This will
provide insight into what factors lead to differences
in the levels of criminality among groups of people.
2.2 Activism and Criminality
The two types of activists analysed in this research
are environmentalists and animal rights activists, for
the reason that despite many similarities in their
origin they display different characteristics in the
ways they protest. Research conducted in the mid-
1990s into the protest activities of environmentalists
found that environmental protesters tended towards
demonstrative or confrontational actions, with those
wishing to go further opting for minor attacks on
property (Seel et al., 2000: 41). Animal rights
activists in the period had a much greater tendency
towards violence (ibid). More recent research
conducted in the USA supports this, showing both
that the number of attacks by animal rights activists
exceeded those of environmentalists, and that the
attacks conducted by animal rights activists were
more likely to target people (Carson et al., 2012).
There are many factors which influence whether
people engage in criminal activity. Recent advances
in criminology have articulated the interplay
between individual propensity (morality and self-
control) and situational characteristics (moral
context and criminogenic factors) to explain the
occurrence of crime (Situational Action Theory; see
Wikstrom et al., 2012). These interactional models
have been used successfully to make sense of
fragmented findings on the emergence of the
propensity for political violence (Bouhana and
Wikstrom, 2011). The present study builds upon
these advances in the criminology of political
violence, by examining two of the factors in the
developmental process through which an individual
acquires a criminal propensity. Since the propensity
for committing crime is far harder to measure than
crime itself, it is a subject which lends itself well to
simulation. The factors examined in this study are
the cognitive characteristics that make an individual
susceptible to moral change (which we shall refer to
as their “moral volatility”), and social contact with
individuals with higher levels of criminal propensity
(which we shall call “social exposure”). For brevity,
we shall refer to an individual’s propensity to
engage in criminal action as their “level of
criminality”.
Through the construction of separate models
describing the social networks of environmental and
animal rights activists based on empirical data, any
differences in the number of people with high
criminal propensity in the models should provide
insight into the reasons why these two groups of
activists have developed different propensities for
violent action, and thus go some way towards
explaining the differences in their violent protest
behaviour.
3 METHODOLOGY
3.1 Construction of the Models
The models in this paper contain no assumptions
regarding the level of influence individual activists
(the agents) have over each other, or the amount of
interaction required for an agent’s attributes to
change. The social network can thus be represented
by an undirected unweighted graph with N nodes
representing the activists, and links representing
acquaintance. This graph can be described using an
NxN transition matrix A, where
0
1
for agents i and j
not adjacent
(1)
for agents i and j
adjacent
Each agent i ∈{0, … , N-1} has two associated
attributes: their level of criminality C, and their
moral volatility M. All variables are functions of
time t, where time is a discrete variable with one
time-step for these models taken to represent one
month. ΔM is defined by:
∆
,
,
,1
(2)
SocialNetworkModellingforCounterExtremism-ComparingCriminalityinTwoActivistNetworks
383

with ΔC similarly defined. We then define the social
exposure to criminality of agent i at time t, S(i, t), as:
,
,
,
(3)
Note that zero exposure indicates that the agent’s
associates are (on average) of the same level of
criminality as the agent themselves, and that this
definition allows for negative values.
3.2 Initial State of the Network Models
The first step is to decide on the initial state of the
models: specifically the shape of the networks, and
the initial distributions of moral volatility and
criminality levels among the agents.
3.2.1 Shape of the Networks
As interest in network modelling in the social
sciences has increased various studies have been
done into the shapes of graphs that most accurately
describe social systems. Barabási and Albert (1999)
proposed that most real networks are such that the
probability that a node is connected to k other nodes
follows a power-law distribution, with P(k) ~ k
-γ
,
where γ is between 2 and 3. This is known as a
scale-free network (Gómez-Gardeňes and Moreno,
2006). The network models in this paper are created
using an algorithm devised by Batagelj and Brandes
that generates random scale free networks (2005: 4).
3.2.2 Distributions of Moral Volatility
and Criminality Levels
For the purposes of these simple models we assume
a normal distribution of moral volatility across
activists at the start of the simulations; this
assumption is supported by data from Wikström’s
PADS+ cohort study of criminal behaviour among
adolescents (2009: 258). To facilitate calculations,
M(i, t) shall be a bounded function taking values
between 0 and 30, and with a mean of 15. We shall
set the initial moral volatility level for agent i to be a
random variable with M(i, 0) ~ N(15, 7.5).
For the criminality levels we must determine
whether a relationship exists between this variable
and moral volatility. To establish this the researcher
carried out a survey of animal rights and
environmental protesters, testing their morality
levels using a method devised by Wikström in his
work on crime amongst adolescents (2009), and
testing their propensities for criminal activity using a
scale devised by Moskalenko and McCauley in their
work on activism and radicalism (2009). For the
animal rights activists there was a statistically
significant positive correlation between these two
variables, but no such correlation existed for the
environmentalists. To facilitate comparison the two
models should start with the same mean criminality
level, and so for the animal rights model we define
C(i, 0)~N(M(i, 0), 7.5), and for the environmentalist
model we define C(i, 0)~N(15, 7.5).
There was no evidence to suggest a relationship
between either variable and the number of links an
activist has to other activists. The distributions of
these attributes are thus independent of node degree.
3.3 Defining the Rules of the Model
The next step is to define the rules for how C, M,
and S change with respect to t. Changes to any of the
three variables may affect the others, and thus there
are six hypotheses regarding the relationships
between the variables that must be tested to establish
whether they hold, to what extent, and whether
differences exist between the two groups of activists.
The hypothesis testing was carried out using data
collected from the aforementioned survey and
interviews with activists for both causes; the results
are summarised in the following sections.
3.3.1 Moral Volatility
Two hypotheses relate to how moral volatility may
change after social exposure or a change in
criminality level:
H1: Moral volatility increases after social
exposure to criminality:∆,∝,.
H2: Moral volatility increases after personal
increase in criminality:∆,∝∆,.
Data from the survey suggested that M(i, t)
should increase a small amount after both a change
in criminality level and social exposure. However
M(i, t) should also reduce gradually with respect to t,
as evidence suggests that moral reasoning changes
with age (Decety et al, 2012). We therefore define:
∆,
min
∆
,1
,0.5
0.1
min
∆
,1
,0.5
0.05
0.1
0.05
for ΔC(i, t-
1)>0,
S(i, t)>0
(4)
for ΔC(i, t-
1)>0,
S(i, t)≤0
for ΔC(i, t-
1)≤0,
S(i, t)>0
for ΔC(i, t-
1)≤0,
S(i, t)<0
where the term min
∆
,1
,0.5
explains the
SIMULTECH2013-3rdInternationalConferenceonSimulationandModelingMethodologies,Technologiesand
Applications
384

small increase in susceptibility to moral change that
comes after an increase in personal criminality, the
adding of the constant describes the small effect of
social exposure, and the subtracting of the constant
describes the effect of age. M(i, t) will also be
bounded by 0 and 30 for all t.
3.3.2 Criminality Level
Another two hypotheses relate to how an individual's
criminality level may change based on changes in
the other two variables:
H3: An increase in moral volatility leads to an
increase in criminality:∆,∝∆,.
H4: Level of criminality becomes greater after
social exposure to criminality:∆,∝,.
Data from the interviews suggests that a change
in criminality level does follow social exposure and
can increase rapidly. However criminality level does
not appear to change as a result of a change in moral
susceptibility. We define:
∆
,
,1
nodedegree
0
for S(i, t-1)>0
(5)
otherwise
In addition, as all activists engaged in their protest
activities willingly we can say that an activist's
moral susceptibility limits their criminality. Thus
C(i, t) will have an upper bound, set at 1.5xM(i, t)
for all t.
3.3.3 Social Exposure to Criminality
The final two hypotheses relate to how social
exposure to criminality may change:
H5: Social exposure to criminality increases after
personal increase in criminality:∆,∝∆,.
H6: Social exposure to criminality increases as
moral volatility increases:∆,∝∆,
The way a social network changes over time is
complicated. Three key issues need to be
determined: why people join campaign groups in the
first place, how their social circles change once they
are in them, and what happens when they leave.
On the first issue, evidence from the interviewees
presented a mixed picture: some had migrated from
other campaigns, while others had initiated contact
with a group when they developed an interest in the
cause. The joining of groups will be represented in
the models by a proportion of nodes (estimated at
1%) forming a new link with another node at each
time step. The question is how to determine which
other node they form the link with.
Data from the survey carried out by the
researcher suggests the most radical people in the
animal rights movement were radical beforehand,
while those who were not remained peaceful once in
the movement. There is no equivalent correlation for
environmentalists, from which we can conclude that
the extreme environmentalists draw their ranks both
from those new to illegal protest activity and from
experienced radicals. A possible explanation for this
which stems both from the literature and from
interviews is that the animal rights movement
comprises disparate sub-groups, with the radical
groups attracting more radicals to the cause (Jasper
and Nelkin, 1992). The environmental groups
however join forces during big campaigns, allowing
the groups to mingle.
To recreate this effect, the nodes representing
animal rights activists will create ties with other
nodes of the same criminality level (to simulate the
distinct sub-groups), while the nodes representing
environmentalists will create ties with other nodes of
the same moral volatility (to simulate homophily,
the phenomenon of being drawn to those similar to
oneself, which is a common feature of social
networks (Lanchier, 2010); (Gargiulo and Huet,
2010).
On the second issue of how activists’ social
circles change after they start campaigning, data
from the interviews showed that, with the exception
of the most extreme activists, they did not
deliberately sever ties with non-activist friends. The
most extreme case is incorporated into the model
through the severing of ties with activists with a
significantly different criminality level. Otherwise,
the models will incorporate natural changes in social
networks through the random creation of links with
friends of friends and the random breaking of links
with friends, at a rate which keeps the average
number of links per agent relatively static.
The final issue is over how activists leave the
network. It is reasonable to suppose that at any time
a small number of activists may leave the cause for
unknown external reasons. This figure is estimated
at 1% per time-step for both groups.
3.4 Threats to Model Validity
There are several threats to the validity of simulation
as method. One question is over construct validity:
that is whether the model really describes the system
it represents (Townsley and Johnson, 2008). A
model is in its very essence a simplification of the
real world and will never completely describe the
system it represents. The question thus becomes
SocialNetworkModellingforCounterExtremism-ComparingCriminalityinTwoActivistNetworks
385
whether the right simplifications have been made: if
variables omitted from the model influence the
observables, the model might not be valid. This can
be mitigated by testing the outputs of the simulations
against real world data. Other threats to the validity
of the model are best countered through multiple
repetitions of the simulation to check consistency
(ibid).
3.5 Coding the Model
The models were coded using C due to its speed and
simplicity, enabling the simulation to be run many
times with a relatively large number of nodes
without requiring any more computer power than
that available on a home laptop. The limitations on
the computing power available restricted the number
of nodes in the models to 1000. The models were
run 100 times each, with t running from 0 to 180.
The simulations thus covered a 15 year period,
allowing the model outputs to be compared with
empirical data collected by the Association of the
British Pharmaceutical Industry and the activist
groups themselves dating back to the early 2000s
(The Economist, 2011); (Bite Back, 2012).
4 FINDINGS
Following the simulations the outputs were
compared to assess whether the models produced
consistent results. The outputs of interest were the
average criminality levels of the agents over time,
and the number of criminally-minded agents in the
networks (defined to be the number of agents with a
criminality level greater than 22). Both models were
found to produce consistent results over multiple
runs for both output variables of interest. The
outputs from the models for the two groups of
activists could therefore be compared.
To validate the models, the output for the
average criminality levels of the agents was
compared with data collected on the number and
types of attacks, as discussed in Section 3.5. There
are problems with this method of validation, as the
number and severity of attacks will not be directly
correlated with criminality levels, and the empirical
data itself is not entirely reliable. However,
comparison of the model outputs with the data does
show that the models outputs display a credible
extent and rate of change in criminality levels.
In order to determine whether the outputs from
the two models are statistically different, the outputs
from the 100 simulations were averaged to
determine an overall average criminality level and
an overall number of criminally-minded agents for
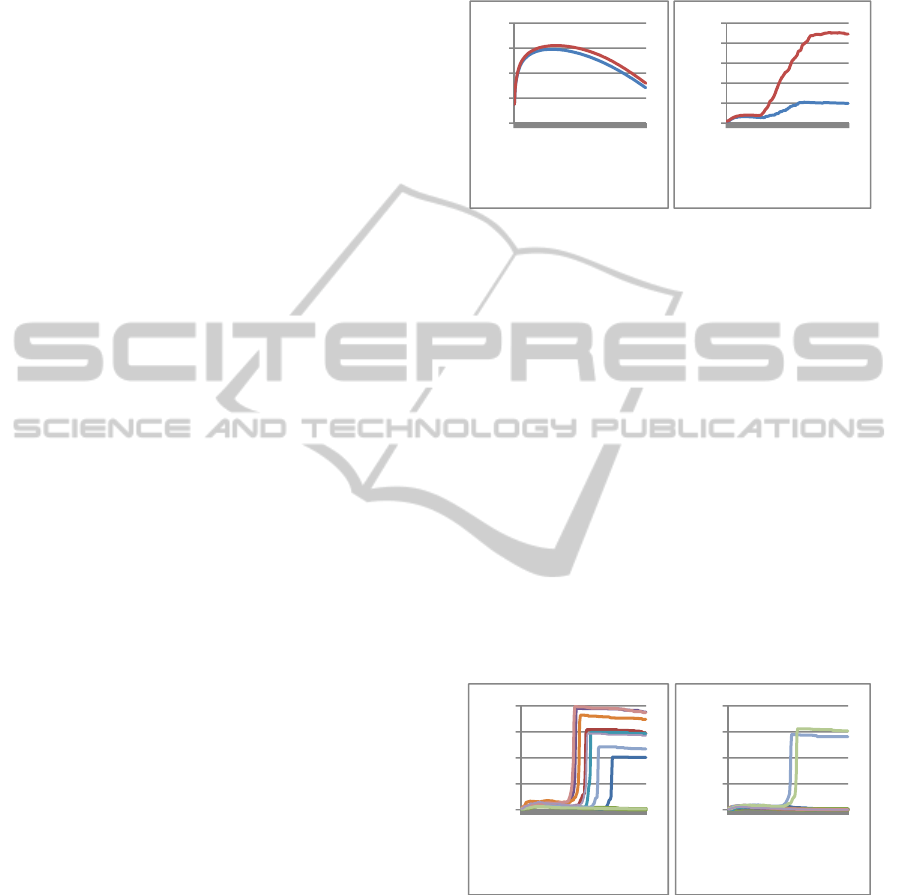
each model. These are displayed in Figure 1.
Figure 1: Comparison of the environmentalist (blue) and
animal rights (red) models averaged over 100 simulations
for average criminality level (left) and number of
criminally-minded agents (right).
There is a small but visible difference in the average
criminality levels of the two models, with the animal
rights model producing a consistently higher
criminality level. An independent samples t test
confirms that the difference is statistically
significant (with the exception of time t=0), with p
values of less than 0.01.
The difference between the animal rights and
environmental models is much more obvious from
the diagram showing the difference in the number of
criminally-minded agents averaged over 100
simulations, but the variance for this statistic is very
large. These data can be better analysed by plotting
some examples of the outputs from individual
simulations; these are displayed in Figure 2.
Figure 2: Comparison of the number of criminally-minded
agents for 10 simulations for animal rights (left) and
environmental (right) activists.
From Figure 2 it can be seen that while there is
significant variation across the different runs they
follow a similar pattern, with a sharp increase in the
number of criminally-minded agents followed by a
gentle decline. The timing of the sharp increase, and
indeed whether it occurs at all, varies considerably,
but it is evident that the increase is more likely to
occur in the animal rights model than the
12
14
16
18
20
1
31
61
91
121
151
Time(months)
0
50
100
150
200
250
1
31
61
91
121
151
Time(months)
0
100
200
300
400
1
31
61
91
121
151
Time(months)
0
100
200
300
400
1
31
61
91
121
151
Time(months)
SIMULTECH2013-3rdInternationalConferenceonSimulationandModelingMethodologies,Technologiesand
Applications
386

environmental model.
4.1 Explaining the Differences
There are two differences in the construction of the
two network models: one difference in the
initialisation of the networks, and one difference in
the way exposure changes with time. By re-running
the simulations and switching the two routines we
can learn which of these factors created the
differences in output, or if both factors contributed.
After running 100 simulations of each of the
model variants it becomes apparent that it is the
initialisation of the network that causes the
differences in both average criminality level and the
numbers of criminally-minded agents in the
networks. Therefore it is the correlation between
criminality level and moral volatility that causes the
increased propensity for criminal activity among
animal rights campaigners when compared with
environmentalists.
An interpretation of these simulated results could
be that where a campaign attracts people whose
criminality levels are already closely aligned to their
susceptibility to moral change – such as pre-existing
activists – then a propensity for violence flourishes
among the protesters. This would ultimately lead to
a higher likelihood of criminal behaviour taking
place during protests attended by these individuals.
5 FURTHER WORK
The models are naively constructed, with many
assumptions made, and this limits their faithfulness
to reality. This becomes evident when the
simulations are run for longer and the distribution of
criminality levels across the agents is analysed.
Figure 3 shows scatterplots illustrating the
criminality levels of all 1,000 agents at time t=0 and
t=500 for one typical run of the model.
From Figure 3 it can be seen that at time t=500
the criminality levels cluster around zero and a
higher value, resulting in a bimodal distribution.
Further, examination of the network at time t=500
reveals that all links between agents are gone,
leaving every agent isolated. While a plausible
explanation for this could be argued – for instance
that after 500 months (over 40 years) people are
unlikely to have the same friends, and will either
have lost their propensity for violence altogether or
it will be deeply entrenched – a more likely
explanation is that this is due to a lack of
sophistication in the model.
Figure 3: Criminality levels for all agents for one typical
run of the model at time t=0 and t=500.
There are a number of ways the models could be
improved to make them more faithful to reality. One
failing is the lack of new blood introduced into the
networks. The graphs showing how average
criminality levels change with time demonstrate that
the models reach a steady state after a few years,
with a gentle tailing off of criminality levels which
is almost certainly due to the changes in moral
reasoning that come with age. It would be more
realistic to introduce a number of new agents with
each time step that are initialised in the same way as
the rest of the network at time t=0, and to entirely
remove the old agents that have cut their ties. This
amendment would be further improved with
empirical data providing realistic figures as to how
many people join and leave the movements each
year.
Other improvements could be made to the
models with sufficient data about the social circles
of the activists. The main assumptions made in the
construction of the models concern the making and
breaking of friendships. It was outside the scope of
the research to date to collect detailed data about the
way peoples’ social circles change over time; a
longitudinal study tracking the social links within a
specific group of activists would need to be done to
make this aspect of the models more realistic.
A further change given such data could be to use
a directed weighted graph for the network models
instead of an undirected unweighted graph. A
directed weighted graph would have the capacity to
model the strengths of social ties and how much
each individual influences or is influenced by those
around them. This could easily be incorporated into
the models by changing the values in the transition
matrix so that it holds values other than just 0 and 1.
Finally, these models take into account only two
factors that contribute to the development of a
propensity for criminal action. For greater realism
additional variables should be incorporated, for
example the activists’ capacity for self-control, and
factors contributing to their susceptibility to being
0
5
10
15
20
25
0 500 1000
AtStart
0
5
10
15
20
25
0 500 1000
AtTimet=500
SocialNetworkModellingforCounterExtremism-ComparingCriminalityinTwoActivistNetworks
387

exposed to criminality, such as place of residence.
With sufficient improvement to these models
they could be used to make more reliable judgments
regarding which factors influence the levels of
criminality in a social network, and the size of the
effect those factors have. The simple versions
described in this paper are an important first step.
6 CONCLUSIONS
This paper has demonstrated that combining social
theories such as those found in criminology with
network modelling techniques rooted in the physical
sciences produces a powerful tool that could be of
great use in fields such as research into extremism.
The models used here are simplistic and are thus
limited in their ability to provide insight into real
world phenomena, but they form an important first
step. Further empirical data about the social
networks of activists and their levels of criminality
would allow greater complexity to be incorporated
into these basic models to make them truer to life.
This increased construct validity would give the
models the power to answer with much greater
certainty questions such as what critical factors
affect the spread of criminality through a social
network. These models could then become of
practical use to policy makers, both in the field of
crime prevention and in other fields where
conditions can spread through social interaction.
REFERENCES
Aletti, G., Naldi, G., Toscani, G. , 2007. First-Order
Continuous Models of Opinion Formation. In Journal
of Applied Mathematics, 67 (3), 837-853.
Barabási, A.-L., Albert, R., 1999. Emergence of Scaling in
Random Networks. In Science, 509-512.
Batagelj, V., Brandes, U., 2005. Efficient generation of
large random networks. In Physical Review E, 71
(036113).
Benczik, I. J., Benczik, S. Z., Schmittmann, B., Zia, R. K.,
2009. Opinion dynamics on an adaptive random
network. In Physical Review E, 79 (046104).
Bite Back, 2012. Diary of Actions. Retrieved July 20,
2012, from Bite Back:
http://www.directaction.info/news.htm
Bouhana, N., Wikström, P.-O., 2011. Al Qa’ida-influenced
Radicalisation: A Rapid Eviden ce Assessment Guided
by Situational Action Theory. Occasional Paper 97,
Research, Development and Statistics, Office for
Security and Counter-Terrorism. Home Office.
London.
Carson, J. V., LaFree, G., Dugan, L., 2012. Terrorist and
Non-Terrorist Criminal Attacks by Radical
Environmental and Animal Rights Groups in the
United States, 1970-2007. In Terrorism and Political
Violence, 24 (2), 295-319.
Decety, J., Michalska, K. J., Kinzler, K. D., 2012. The
Contribution of Emotion and Cognition to Moral
Sensitivity: A Neurodevelopmental Study. In Cerebral
Cortex, 22 (1), 209-220.
Diani, M., 2003. 'Leaders' or 'brokers'? Positions and
influence in social movement networks. In M. Diani,
& D. McAdam, Social movements and networks (pp.
105-122). Oxford University Press. Oxford.
Gargiulo, F., Huet, S., 2010. Opinion dynamics in a group-
based society. In EPL, 91 (58004).
Gómez-Gardeňes, J., Moreno, Y., 2006. From Scale-free
to Erdos-Rényi Networks. In Physical Review E, 73
(056124).
Jasper, J. M., Nelkin, D., 1992. The Animal Rights
Crusade: The Growth of a Moral Protest. The Free
Press, Macmillan. New York.
Lanchier, N., 2010. Opinion dynamics with confidence
threshold: an alternative to the Axelrod model. In
ALEA, 7, 1-18.
Moskalenko, S., McCauley, C., 2009. Measuring Political
Mobilization: The Distinction Between Activism and
Radicalism. In Terrorism and Political Violence, 21
(2), 239-260.
Parunak, H. V., Savit, R., Riolo, R. L., 1998. Agent-Based
Modeling vs. Equation-Based Modeling: A Case
Study and Users' Guide. In Proceedings of Multi-agent
systems and Agent-based Simulation (MABS '98),
LNAI 1534 .
Seel, B., Paterson, M., Doherty, B., 2000. Direct action in
British environmentalism. Routledge. London.
The Economist, 2011. Britain: A beastly business;
Animal-rights protests. In The Economist , 401 (8756),
42.
Townsley, M., Johnson, S., 2008. The need for systematic
replication and tests of validity in simulation. In L.
Liu, & J. Eck, Artificial crime analysis systems: using
computer simulations and geographic information
systems (pp. 1-18). Information Science Reference.
Hershey.
Wasserman, S., Faust, K., 1994. Social Network Analysis:
Methods and Applications. Cambridge University
Press. Cambridge.
Wikström, P.-O., 2009. Crime propensity, Criminogenic
Exposure and Crime Involvement in Early to Mid
Adolescence. In Monatsschrift fur Kriminologie und
Strafrechtsreform, 92, 523-566.
Wikström, P.-O., Oberwittler, D., Treiber, K., Hardie, B.,
2012. Breaking Rules: The Social and Situational
Dynamics of Young People’s Urban Crime. Oxford
University Press. Oxford.
Wu, F., Huberman, B. A., 2004. Social Structure and
Opinion Formation.
SIMULTECH2013-3rdInternationalConferenceonSimulationandModelingMethodologies,Technologiesand
Applications
388
