
Software Systems Versus Intellectual Property Rights
A Moral and Ethical Challenge for Higher Education in Developing Nations
Guy Toko
Applied Information system, University of Johannesburg, Johannesburg, South Africa
Keywords: Computer Systems, Software Systems, Intellectual Property Rights, Higher Education Institutions, Software
Piracy.
Abstract: Higher Education (HE) institutions in most countries represent one of the most important users of computer
systems. HE institutions need access to fast and reliable computing devices, not only to teach, but also for
their day-to-day operations. These systems are not just hardware, but also software systems which are
protected by national and international laws. HE institutions may be able to control their employees and
their software needs, but it is far more difficult to control students. Their software needs to enforce the
respect of intellectual property rights. Students need numerous software packages in order to successfully
comply with the academic requirements, whether deliberate or not, some students rely on illegally acquired
software systems for their academic projects. This type of behaviours has moral, ethical, legal and societal
replications. HE institutions are seen as law-abiding entities, highly respected by their respective
communities, applauded by industries, recommended by their governments, and yet their students may be
jeopardising that status whether deliberately or by pure ignorance. This study aims at investigating why
students engage in using illegal software systems, and why it is difficult to enforce the rule of law when it
comes to software licences within HE institutions.
1 INTRODUCTION
This section will introduce the importance of higher
education worldwide, the role it plays in developing
people and communities, and the challenges HE
faces in order to stay competitive and up to date with
the latest telecommunication tools. We will also
explore the importance of computing systems in HE,
the role of software systems, the important duty of
protecting intellectual property, and most
importantly we will investigate the challenges that
most Information Communication Technology (ICT)
students faced in staying within the framework of
laws, while fulfilling their academic obligations.
HE institutions all over the world have acquired
high levels of respect and accountability from their
respective governments and other national
institutions for their role in creating new knowledge
and research in all aspects affecting their respective
nations (Rensburg, 2013a). However, learning
centres are negatively affected by continuous
government budget cuts, lack of external financial
assistance and the impact of austerity measures
taken to address the respective country’s fiscal
issues, especially from the ministries of education,
or other external donors (Rensburg, 2013b). Some
institutions need to enrol as much as possible the
highest of number of students, in order to obtain
government grants and to ensure a higher financial
return. Potential students usually choose a particular
stream based on the employment opportunities after
graduation, and in the past decade (,) the field of
ICT has become the most sought-after field by
school leavers who wish to ensure a better future.
In order to produce the best ICT students, the
institution needs to be well-equipped with the latest
and state-of-the-art ICT tools in addition to having
the best academic staff to groom the potential ICT
graduates and future industry experts. This means
that the best computer laboratories, latest software
systems and permanent maintenance personnel need
to be in place in order to monitor all student
activities.
This study was initially conducted as part of a
master’s degree research study aiming at exploring
the viability and adoption of open source software
systems as an alternative in higher education in
developing nations. This paper investigates the
250
Toko G..
Software Systems Versus Intellectual Property Rights - A Moral and Ethical Challenge for Higher Education in Developing Nations.
DOI: 10.5220/0004838202500259
In Proceedings of the 6th International Conference on Computer Supported Education (CSEDU-2014), pages 250-259
ISBN: 978-989-758-020-8
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

driving force behind the use of pirated software
systems in HE institutions in developing nations.
2 UNDERSTANDING
COMPUTER SYSTEMS
A computer system is an electronic device
comprising thousands of electronic chips and
microchips. Electronic microchips are now also
widely incorporated into systems ranging from
heavy industrial machineries to miniature handheld
computer systems. Generally speaking, a computer
system consists of two major components, namely:
hardware and software (Meyers, 2003a). The former
is regarded as the physical component of the
computer system, receiving and executing
instructions embedded within the latter (Cashman et
al, 2011). Software systems on the other hand,
comprise digital algorithms which are sets of
instructions that control the hardware components of
the computer system (Meyers, 2003b).
Programmers, developers or coders write the
coded algorithms and these instructions are
translated into a form that only electronically
enabled machines can read and execute (Parker &
Van Alstyne, 2005). This initial authoring is known
as the source code which represents the actual
human intelligence instructions. The source code can
be accessed, modified, enhanced and innovated by
trained persons (Hershey, 2008). The source code
can be accessed by the general public. However, this
will depend on the licence agreement and its release
terms and conditions (Parloff, 2007a). After the
compilation, that is the process of transforming
human readable code into machine readable code,
another authoring is generated, known as the object
code. This is a form of authoring that is readable and
executable by the machine only (Reijswoud & Mulo,
2004; Toko & Mnkandla, 2011a).
To some degree, the source code is regarded as
the actual software system, and users have access to
it through purchasing a licensing agreement with its
vendor or developers. Regardless of what the licence
and agreement stipulates, the users cannot modify it
(Parloff, 2007b). Both sets of authoring (source code
and object code) constitute the software system the
end-user purchases or downloads free of charge
from the Internet for whatever purpose (Stallings,
2003).
The vendors, developers and programmers have
the freedom to release their product under any
licencing agreement of their choice, to define the
conditions under which their software systems will
be used, the manner in which users will access it and
how much users will pay to use it. These factors are
protected by Intellectual Property Law (IPR) and
usually constitute patent rights (Lau, 2003) thereby
preventing other developers, programmers or
vendors from copying it. The right to use the
software systems is therefore limited in access to the
executable component (West & Dedrick, 2005). This
means that although the end-users may purchase the
software, it does not provide them with the right to
modify, compile, innovate or redistribute it (Weber,
2002). This form of release condition is known as
‘proprietary’ had stringent terms and conditions
agreement (Steinmueller, 2001), an example will be
any Microsoft product . Other vendors may choose
to release their software systems without any form
of restriction, and all together (source code and
object code) provide technically knowledgeable
users with the chance of owning, innovating and
redistributing the given software systems to meet a
particular need (Hill, 2007). Technically this is often
referred to as an ‘open source’ and example will be
‘Linux’ product. It is sometimes free of any initial
cost and/or further licensing fees, and mostly
distributed over the Internet (Parloff, 2007c).
Software systems are therefore essential in the
smooth running of a computing system without
which a computer system will only be a piece of
hardware with no utility.
3 INTELLECTUAL PROPERTY
RIGHT
An intellectual property right is a law that protects
any outcome of intellectual effort; it can be enforced
locally or internationally in a court of law; it can be
granted to a person, group, company or entity, and
enables them an exclusive right to exploit for their
own benefit any positive benefit without having to
keep a watchful eye on competitors who may simply
copy their invention, creation or innovation
(Karakaya and Uluturk, 2010). The use of such laws
limits any form of imitation or duplication by
conferring monopoly power to the holder. In most
cases, it may comprise full or sectional rights, and
can include, but is not limited to copyright, patents,
trademarks, geography indication, related rights,
author rights, moral rights or trade secrets (WIPO,
2004). The reasoning behind these initiatives is to
motivate people to generate new ideas, and to
protect them and their creations and subsequently
SoftwareSystemsVersusIntellectualPropertyRights-AMoralandEthicalChallengeforHigherEducationinDeveloping
Nations
251

motivate others to compete on an equal footing. For
example, a copyright gives the exclusive right to
reproduce, distribute, perform, display, or license a
particular work of the inventor if required, and thus
constitutes a licensed derivative of his work (Olsson,
1993). Generally speaking, the enforcement and
protection of intellectual property rights at
international level has always been a complex issue,
and depends on each country and most importantly
on the type of political climate in each nation which
may have an impact on the extent to which these
laws are enforced.
Software systems are known as the creation of
the human mind, and in most cases they are
developed by individuals or companies with
important patent rights. The majority of software
systems these days are proprietary and represent a
foreign product in most developing nations where
they are most of the time formally protected by local
laws, whereby the use and reproduction need to be
authorised by the licensor (Idris, 2003).
4 SOFTWARE LICENSING
Regardless of how a person acquires a proprietary
software system and some open source systems, for
example from the internet or via CD, DVD or USB,
during the installation process there will be a stream
of different screens to go through before the actual
software system is loaded onto the machine, and one
of these screens will deal with the terms and
conditions. These will stipulate the conditions under
which the product that is about to be installed can be
used. It is assumed that if the user cannot comply
with these conditions, the software shall not be
installed. Ironically, even when the software system
which is about to be installed has been acquired
illegally, the same screen must be validated to move
to the next screen, and this brings up the question of
morality as the end-user is the only one to judge
whether or not to continue with the process when
realising that the product may have been illegally
acquired (Hinduja and Sameer, 2003).
Software licensing is seen as a legal instrument
governing the use and distribution of a software
system, although today much of the distribution of
software systems is made over the Internet which
offers greater control. However, many, due to lack
of Internet connectivity in most developing nations,
are still distributed using hard material hence, the
high rate of illegal redistribution of software systems
in many homes, businesses and HE institutions
(Depken II et al, 2004).
The terms and conditions of these software systems
do not only restrict illegal copying, but also restrict
loading the product onto various computers without
the authorization from the vendor. The question is
thus how can one make sure that a software licence
that was legally awarded to a single computer is
indeed installed on a single computer only? It is at
this point that the issue of morality and ethics arises,
and there are many who believe that many illegally
installed software systems are originally acquired
legally, and become illegal only when used beyond
the restricted number of computing devices (Higgins
et al., 2005). Software licensing in general contains
various provisions which enable legal and structural
liability between both parties (the licensee and
licensor). Thus, even when the software has been
acquired legally, the buyer does not have the right to
modify, enhance, or innovate the source code of the
product. And whether one is dealing with open
source or proprietary software systems, there are
always conditions that the end-users have to respect,
and monetary values are not the only access
conditions (Husted, 2000).
5 CAUSES OF SOFTWARE
SYSTEM PIRACY IN HE
INSTITUTION
According to Musa Karakaya and Bulent Uluturk
(2010), the “lack of information, poor administration
and control of software installed on campus
computer systems, poor moral standards, absence of
academic ethics, poor commitment from academic
staff about the respect of intellectual property, high
price of proprietary software systems, and low level
of understanding of country laws are the driving
forces behind the high rate of piracy” in HE
institutions. This neatly points to the fact that behind
the software piracy phenomenon in various HE
institutions across the many developing nations
students are under immense pressure to complete
academic projects using advanced and the latest
software systems, very often, mostly at their own
pace and with little supervision. Moreover, the price
of such software systems is often beyond their reach,
and outdated systems are discarded without further
explanation. Indeed, many students are so poor they
require financial help to fund their studies
(Rensburg, 2013c). Moreover, many ICT streams do
not offer legal subjects or modules to help students
understand the repercussions of their actions or the
legal implications of using pirated software. In many
CSEDU2014-6thInternationalConferenceonComputerSupportedEducation
252

cases academic staff at the universities are not
equipped enough to easily trace project development
with non-legal material; and most importantly
various HE institutions do not have a clear policy
regarding software piracy pertaining to students use
even though they may have an acceptable policy for
their staff.
6 ICT STUDENT AND USE OF
ILLEGAL SOFTWARE
SYSTEMS
In South Africa, the National Qualifications
Framework (NQF) is used to standardize university
degrees and national diplomas, all of which are
three-year qualifications with regard to Application
Software Development, IT Management, ICT
Management or Systems Support as major subjects.
Every student registered for an NQF 4 is expected to
submit a complete application that has been
developed as part of their final project upon which
the final evaluation is based (Faculty of
Management Regulations, undergraduate and
postgraduate, University of Johannesburg, 2012).
For many, this moment remains the most memorable
academic event with the presentation of their final
application to the general public and ICT industry
experts, the latter forming part of the jury.
Students facing this learning experience have to
come up with a topic, an idea or a problem and
develop a software application system to address or
solve it. Thus a system needs to be generated by the
compiler, or written or developed by someone else.
Generally the project must be a student’s original
solution; they need to select the software system
platform they wish to use and most importantly
finance it which many can’t afford. As a result,
many, even in reputable universities, resort to using
an illegal software system in order to complete their
qualification. One of the aspects that stood out at the
2010 student exhibition was that most application
systems had been developed using proprietary
software products. It is important to note that the
students were not bound to a particular computer
system platform or expected to select a particular
platform. Rather they were free to make use of
whatever application system (e.g. compiler) or
platform they found suitable. This was the case not
only for their “front end” GUI, but also for their
“back end” (database systems) or operating systems,
thus meeting the objectives of South Africa’s
national plan for higher education which is: “To
produce graduates with the skills and competencies
required to participate in the modern world in the
21
st
century” (Damoense, 2005a). When examining
the final projects of the students, the part that first
appears is the user interface front end. Nearly all the
students chose applications related to Microsoft
Visual Studio such as Visual Basic Dot Net
(VB.NET), ASP.NET or C#, all of which are PS and
Microsoft products. For the back end most decided
on an SQL server, and again a PS, these being solid,
reliable and robust.
7 OVERVIEW OF THE COST OF
SOFTWARE SYSTEMS
The cost of the software licensing fees in the
developing world is reasonable compared to other
imported ICT materials (Gush et al, 2004). Mostly
evaluated in foreign currency (US dollars), it is
estimated that licensing fees cost the Australian
government around $430 million annually (Scott,
2004). The Republic of South Africa spends 65% of
its annual ICT budget on licensing-related costs
(NACI, 2004). Worldwide licensing amounted to
$35 billion in 1998 and $171 billion in 2000 (Evans,
2004).
For a developing country software licence fees
can become a major hurdle for ICT and overall
national development (Bruggink, 2003) with most of
the vendors (software companies) operating from
abroad or using subsidiary local entities to reach
their end-users and provide technical support
services (when necessary). As a direct result, large
amounts of foreign currencies leave the country’s
shores annually (Ghost, 2003a). In South Africa the
situation is similar to the rest of the developing
world with the estimated software licence cost
totalling around $2,620 per GDP/capita (Ghost,
2003b). This untenable situation has resulted in a
high volume of pirated software being used in many
South African homes, schools, HE institutions and
small businesses (Toko & Mnkandla, 2011b). It is
estimated that over 38% of the total software used in
South Africa is pirated (Ghost, 2003c).
8 EXAMPLE OF SYSTEMS COST
IN HE INSTITUTIONS
In 2007 the University of Johannesburg (UJ)
developed a separate business entity to control and
manage its computer laboratories with the aim of
SoftwareSystemsVersusIntellectualPropertyRights-AMoralandEthicalChallengeforHigherEducationinDeveloping
Nations
253

making them more effective and efficient. The
university is spread across four campuses around the
city of Johannesburg, namely Soweto, Doornfontein
and two campuses in Auckland Park: Bunting Road
and Kingsway, each with its own computer
laboratories. It is estimated that the software
licensing fee for the Soweto campus alone is
approximately $56 980, for Kingsway
approximately $ 152 72, for Bunting Road
approximately $248 98 and for Doornfontein
approximately $82 55. This amounts to a total
budget of approximately $1 065 54 or
$152 220 US for the year 2008. At this stage these
figures relate only to licensing fees for software such
as Ghost and DEEP FREEZE, and do not include
operating systems and other office automation
systems. Software-related licence fees regarding
staff are not included. If one had to expand this to
office automation software such as MS Office, OS,
antivirus, antispyware and Internet connectivity
software, the cost of licensing would run into tens of
millions of rand annually.
9 THE IMPORTANCE OF
SOFTWARE SYSTEMS IN HE
INSTITUTIONS
H.E institutions develop their internal infrastructures
to meet their technological needs and to keep pace
with their competitors, world trends, labour
constraints, internal goals and the modern world
(Damoense, 2005). According to Adams (2003,
p18): “With few exceptions, universities have been
unable to develop and implement programs, such as
advanced research in networking, computer science,
community applications, and programs that promote
technology-savvy intellectual capital. Economic
factors ranging from the lack of capacity to pay for
costly infrastructure to sustaining computer
networks introduced through donor funding weighed
on universities as their budgets continued to get
slashed.”-
ICT research and development have for years
been an integral part of H.E institutions worldwide,
and most importantly, these institutions have
participated in many successful advanced ICT
projects that have had a huge positive impact on the
ICT industry and society in general (Câmara &
Fonseca, 2005). The science and technology
innovation that the world is currently experiencing is
mainly driven by academic researchers upon whom
industry researchers rely, not only to get
accreditation for their personal research findings but
also to validate them, and obtain technical support
and acknowledgement (Fresquez & Frias, 2006).
Academics thus play an important role in creating
awareness of intellectual property rights. Developing
a community of law-abiding developers is thus seen
as crucial for any respectable nation (Wooi, 2004).
A particular example is the role scholars and
academics have played in developing the UNIX
operating system, one of the most reliable, stable,
secure and free pieces of OS that has led to further
software development around the world (Parloff,
2007d). The ICT academic world is also regarded as
the human resource development ground for the ICT
industry, helping to make H.E institutions a breeding
ground for ICT industry professionals. Furthermore,
the level of education or qualification is the most
fundamental and reliable evaluation instrument used
to determine the suitability of any candidate entering
the sector (Damoense, 2005c). The qualification of
the potential entrant is evaluated against university
standards and monitored by the Department of
Higher Education.
Up to now we have explored, explained and
elaborated on various aspects pertaining to the role
of software licensing, and motivations that drive the
ever increasing number of pirated software systems
in many H.E institutions - mostly in developing
nations. Very often these H.E institutions from
developing nations compete with first-world
institutions, these ICT products are priced with set
and standard consumers in mind. Thus, as a result of
internal financial problems of many developing
countries, illegal products are often used in some
H.E institutions even though such actions are seen as
immoral, unethical and unacceptable in all cultures.
Nevertheless some H.E institutions are not only the
repositories of knowledge, but some are indirectly
promoting “white collar” criminal activities when
“forcing” students to keep up to date with the latest
technology which they can only afford by obtaining
pirated software if they wish to succeed in their
academic studies.
10 METHODOLOGY
The research study was conducted over a period of
two years as part of a larger research project known
as ‘The role of open source software in higher
education institutions’ which is available online
under the university of Johannesburg website. This
type of research is generally classified as research
project; it enables the researcher to develop solid
CSEDU2014-6thInternationalConferenceonComputerSupportedEducation
254
research literacy at a time when reliable academic
data is non-existent in many developing nations. The
method employed was exploratory followed by
explanatory built-up research. For this particular
research project, a quasi-experimental research
design was used due to its nature and the aim of the
project. The most important motivation for these
choices was the ability to use a survey questionnaire
over the Internet which could easily be distributed to
people in the most remote locations in South Africa.
The project was primarily conducted in the Republic
of South Africa, although the outcome can be easily
replicated in other developing nations around the
globe.
A questionnaire was sent to various H.E
institutions around the country and uploaded onto
the Internet. The main sources of data were students,
academics and ICT professionals operating in
various H.E institutions around the country. The
Internet thus enabled respondents to access the
questionnaire wherever they were. Participants were
randomly selected without targeting a specific
group. The researcher drew the sample population
from all corners and sectors of H.E institutions in the
country, i.e. from people with both ICT and
academic backgrounds. The stratified sampling
method was used to obtain data for analysis. This
selected approach is based on probability sampling
which enables each participant within the target
population an equal chance of being selected. The
primary target was to reach at least 200 respondents
from all sectors, namely ICT students, academics,
professionals. Each question was designed to
address a specific outcome which could help
understand the problem at hand, and we received
nearly 600 responses. The aim of the research
project was to examine how students understood
intellectual property rights in terms of software
licensing issues.
11 FINDINGS
The survey questionnaire was completed online.
Although the research questions addressed many
software-related issues such as open source software
systems versus proprietary systems, this paper will
only deal with the question related to the
understanding of intellectual property rights of
software systems within H.E systems.
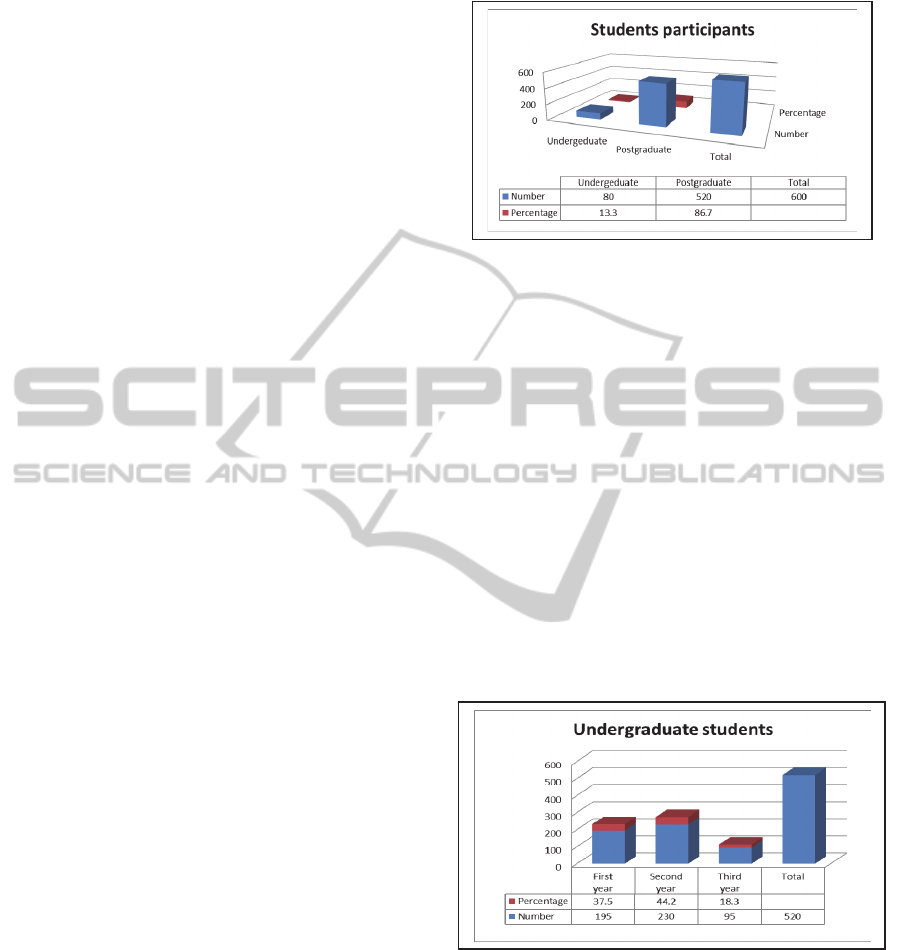
Question 1
Figure 1: Student level of study.
Question: Please indicate if you are an
undergraduate or postgraduate student.
Analysis: This question was primarily aimed at
getting to know the students, to know whether they
were undergraduates or postgraduates. It was
assumed that postgraduate students are better
equipped to understand the implications of using
illegal systems, and those undergraduates still
required more time to be informed about the dangers
of using unlicensed products. We noted a large
number of undergraduate students as compared to
postgraduates who participated in this study. This
was expected, because in most cases, as student
progress academically, and graduate, they look for
jobs and put any future studies on hold.
Question 2
Figure 2: Sub-level within undergraduate student.
Question: If you are an undergraduate student,
please indicate you current progress.
Analysis: This question is aimed at narrowing the
focus to a particular sub-group. It was expected that
undergraduate students would form the biggest
group because as they progress through their
academic studies, many students drop out of the
system, thus resulting in a smaller pool of
SoftwareSystemsVersusIntellectualPropertyRights-AMoralandEthicalChallengeforHigherEducationinDeveloping
Nations
255
postgraduate students. Moreover, it is assumed that
first-time students are the most ignorant when it
comes to various aspects relating to software
licensing and intellectual property. In addition, in
many institutions, third-year students are required to
submit a final year project where they have to
develop their own software systems. It was assumed
that this final project would put pressure on students
so much so that they would tend to use pirated
software given the high standards required of them.
However, the results showed that second-year
students were the most common users of pirated
software, followed by first-year students, and then
by third-year students. This pattern may be
explained by the fact that many students drop out
during the course of their academic studies. The
reasons for dropping out are many, including a lack
of financial means to pay for further studies.
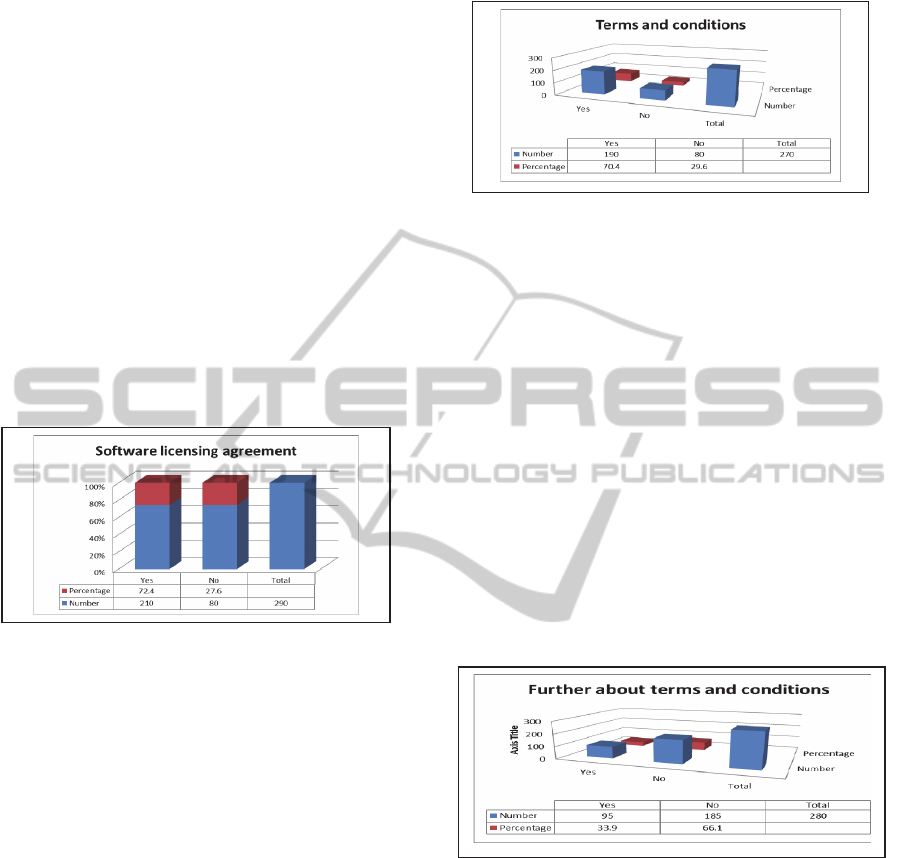
Question 3
Figure 3: Software license agreement.
Question: Does the institution where you are
enrolled provide you with software?
Analysis: This question was aimed at determining
whether or not certain institutions that were aware of
the availability of software systems for their students
made these available free of charge. Providing
software systems to students doing ICT-related
courses sometimes falls under the umbrella of
“corporate responsibility”. By engaging in such
actions, organizations help alleviate the financial
burden on students who, as a result, do not have to
resort to using illegal software systems for their
academic projects. In response to this question, it
was found that nearly 200 students said that they
received software systems from their respective
institutions. This might be due to the fact that the
problem is so common that the only way to cope
with the demand of software systems is for the H.E
institutions to provide the software themselves in
order to limit software piracy.
Question 4
Figure 4: Software terms and conditions.
Question: Are you aware of the terms and conditions
of using software systems?
Analysis: This question was primarily intended to
assess whether or not students actually read the
terms and conditions of the software system installed
on their computer system. Very often the lack of
understanding or ignorance may lead to non-
compliance with the country’s rules and regulations.
Before any law can be enforced, it is important to
assess whether the law is well explained and
understood. The answers to this question suggest
that the majority do read the system’s terms and
conditions. This can be explained by the fact that
many are forced to read these terms and conditions
in order to proceed with the installation. In fact the
end-user needs to validate the condition window
before proceeding further.
Figure 5: Terms and conditions understanding.
Question 5
Question: Do you understand the terms and
conditions of your software system?
Analysis: This question was meant to examine
whether after reading the terms and conditions,
which the majority claimed to have read, they
actually understood what they had read. Moreover,
since most software systems need a positive
validation of the terms and conditions in order for
the user to be able to move to the next step of the
installation, does this contribute in any way to the
lack of understanding of the legal conditions? In the
CSEDU2014-6thInternationalConferenceonComputerSupportedEducation
256
previous question, most indicated that they did
indeed read the terms and conditions, and thus the
question needs to be asked whether they actually
understand what they have read. The answers to this
question indicate that the majority do not understand
the meaning and importance of such texts. This
result supports the previous assumption that many
merely scroll through the terms and conditions in
order to be able to install the system.
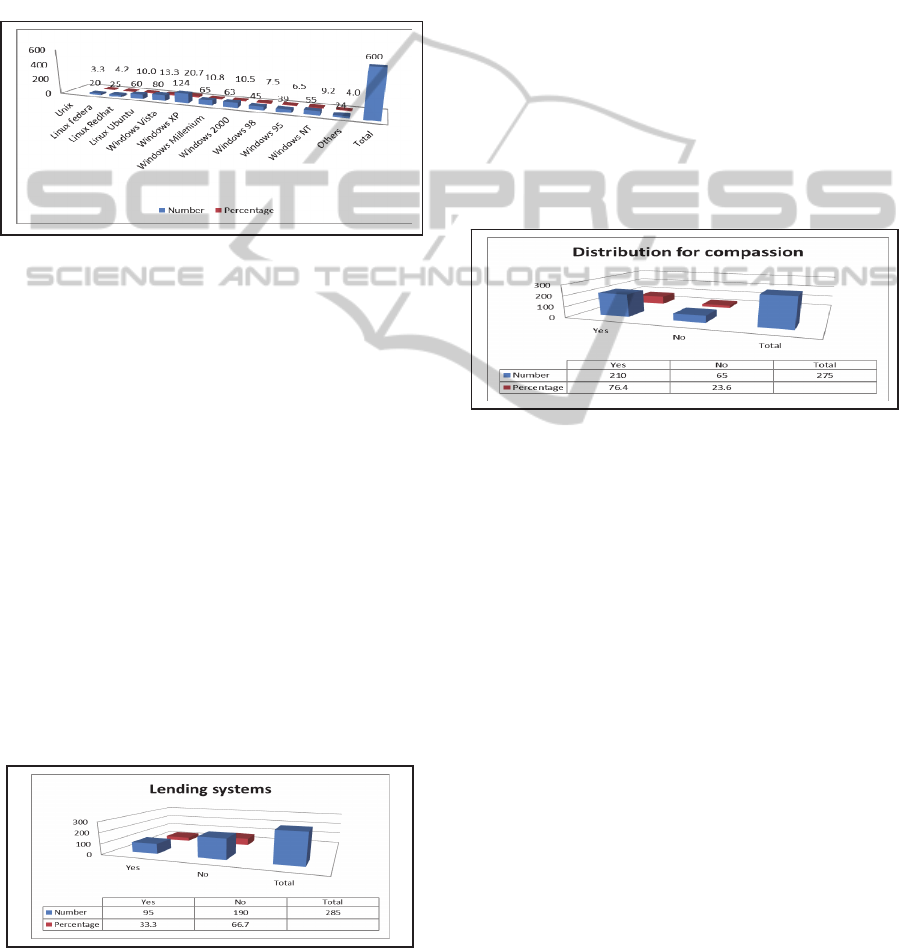
Question 6
Figure 6: Types of operating system on private PCs.
Question: What types of operating systems are
installed on your private computer?
Analysis: This question seeks to ascertain the
number and types of operating systems installed on
students’ computer systems in order to understand
whether there is a match with their institutions’
systems as far as the operating system only is
concerned. Knowing the types of operating system
installed on students’ computers will help to
understand what sort of software needs they may
have. This question thus indicates that XP is by far
the most commonly used operating system which is
a proprietary system and therefore requires
licensing. Moreover, because of the type of
platforms they are running, there will be some
specific types of applications that can be supported;
hence there should be a better understanding of the
intellectual property rights.
Question 7
Figure 7: Lending software systems.
Question 7: Have you ever asked a friend, lecturer or
ICT department to make you a copy of software (or
installed it on your private computer system) you
urgently needed for a school project and because
you could not afford to legally acquire a copy of
your own?
Analysis: This question brings up the fundamental
issue of software piracy among students, especially
from previously disadvantaged students. The cost of
most software systems are beyond the reach of such
students and this ultimately results in many of them
using illegal systems. It is to be expected that when
facing the issue of obtaining software that is out of
reach as a result of financial constraints, students
will ask help from their friends in order to complete
a project. More than half of the participants admitted
asking for a software copy from friends.
Question 8
Figure 8: Software system distribution for compassion.
Question: During a class project you managed to
legally obtain a copy of the software system needed
for the project; you then realise that many of your
classmates can’t afford to access it, can you share
the software system with them, install it on their
system, or simply make duplicate copies so that they
have their own copy?
Analysis: The answers to this question show that in
many instances end-users of intellectual property are
not aware of the crime they are committing by
illegally making copies of the software systems they
legally purchased. Moreover, in many communities,
sharing with the less fortunate is embedded in their
culture, and depriving others from what one
abundantly has is seen as immoral. This view also
impacts on the sharing of software systems, and
many software system vendors will limit the usage
of their product to a certain number of computers,
end-users, or put a limit on the time during which it
can be used. The answers to this question indicate
that the majority of students are willing to make
copies of software systems in order to help fellow
students. The question thus arises whether they
SoftwareSystemsVersusIntellectualPropertyRights-AMoralandEthicalChallengeforHigherEducationinDeveloping
Nations
257
actually are aware that by doing this, they are
engaging in an illegal activity. This indicates how
very often legally acquired software systems become
illegal as people make copies not knowing that their
legal software system was meant to be used on one
computer system only.
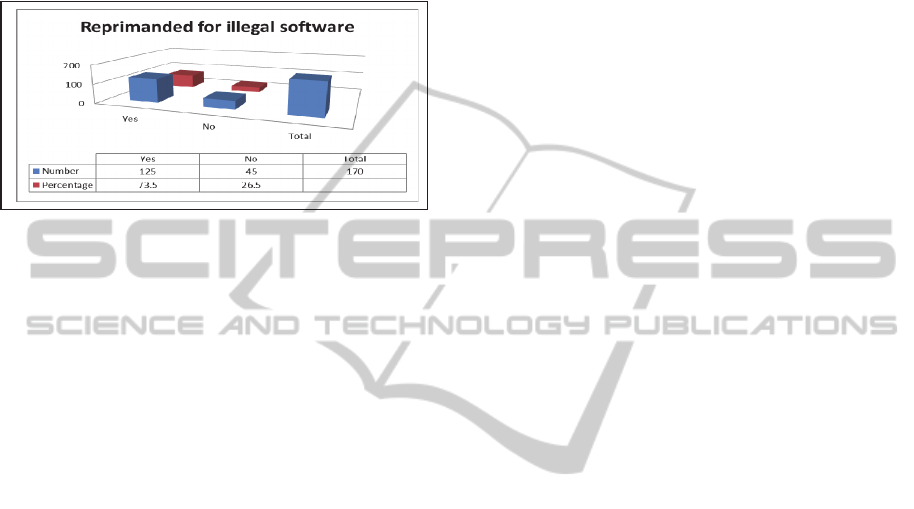
Question 9
Figure 9: Reprimanded for using illegal software.
Question: Have you ever been reprimanded for using
an illegal software system on your campus computer
system?
Analysis: Many H.E institutions are well aware of
the software licensing issue, and more specifically of
the use of pirated software on their computer
systems or on students’ final year projects, which are
used for evaluation. In many cases, there have been
reprimands and students have been asked not to
repeat this offence. This is an important step towards
understanding the importance of intellectual
property rights in H.E. It was found that more than
half admitted to having been reprimanded after
illegally making copies of a software system. This
can be seen as a way of enforcing the rule of law to
some degree; it also indicates the extent to which the
problem seems to have escalated.
12 CONCLUSION
The literature shows the extent to which H.E
institutions are facing the impact of software
licensing costs, how this affects their operational
needs, and how more financial assistance is needed
to help alleviate this non-academic burden. Most
countries in developing nations are capitalist
economies, practicing a free market economy, which
simply means that whenever someone invents, re-
invents, innovates or discovers something new after
investing substantial financial amounts into the
project, they expect a return on investment. Thus,
before anyone can gain access to the product,
permission will have to be granted for the use of the
product, otherwise the use of the product is deemed
unlawful and such infringements of the law will
result into legal action. H.E institutions are seen as a
mirror of society, are usually well respected, are
known to have a high moral standing, and therefore
should not be involved in any way in unlawful
practices. This applies to both their staff and their
students. Nonetheless, some of these unlawful
activities are carried out without the knowledge or
consent of the institution. Moreover, some of the
students engaging with such activities are not well
informed regarding the repercussions of their actions
(see Questions 3, 4 and 5). They seem to be ignorant
of the fact that making a copy of a software system
without prior approval of the owner constitutes a
crime. This paper has shown that many students are
using illegally obtained proprietary software systems
on their private computers (see Figure 6), and yet
they ignore the conditions under which such
software may be used. Figure 7 and Figure 9
indicate that the majority of students who
participated in this research have at least been
reprimanded for making illegal copies of software
systems. It is important to note that the phenomenon
of software piracy may have serious repercussions
and can tarnish the image of any institution found
supporting the illegal use of intellectual material
such as software systems. Ideally, legal software
systems should be distributed to all registered
students free of charge, but budget issues may limit
this ambition. Moreover, the high cost of Internet
connectivity in most developing nations compels
developers and vendors to distribute their products
via CDs and DVDs, which are more likely to be
copied. The theft of intellectual property is not
acceptable in any nation, no matter how poor, yet it
is understandable why end-users like disadvantaged
students are tempted to obtain pirate copies.
Software piracy can take many forms, and it should
be noted that many students are not even aware that
they are acting illegally, for instance when obtaining
copies from friends. The only thing that may stop or
prevent them from engaging in such illegal activities
would be their moral and ethical values.
REFERENCES
Adams (2003). ‘Newest version of industry leading motion
software gives engineer … ‘ VPD campus license
systems. Highbeam research.
Bruggink, M. (2003). 'Open source in Africa: Towards
Informed decision-Making'. International Institute for
Communication and Development (IICD).
CSEDU2014-6thInternationalConferenceonComputerSupportedEducation
258

Câmara, G. & Fonseca, G. (2005). 'Structural constraints
in open source software development and their public
policy implications', Brazilian national institute for
research Sao jose dos campos/ the pennsylvania state
university, state college, USA
Cashman & all. (2001). 'Discovery computers 2011'.
Shelly Cashman series.
Damoense, M. (2005). 'Online learning: implications for
effective learning for higher education is SA'. The
Monash University SA.
Depken II, Craig. A Ve Lee C. Simmons (2004) 'Social
construct and the propensity for software piracy,
applied economics'
Evans, D. (2004). 'Politics and programming: government
preferences for promoting open source software'.
Fresquez F & Frias, B. (2006). 'Ariko Fujii. Gail S. Furey.
Available from http://www.pipl.com/directory/
name/Fresquez/L. (Accessed 05/09/2009).
Ghost, R. (2003). ‘Licensing fees and GDP per capita: the
case for open source in developing countries’. Peer
reviwed journal on the internet
Gush, k. & Cambridge, G. & Smith, R. (2004). 'The digital
doorway-Minimally invasive education in Africa'.
CSIR
Hershey, P. A. (2008). 'Encyclopaedia of decision making
and decision support technology'
Higgins, George E. Abby, Wilson , Brian Fell (2005) 'An
application of deterrence thery to software piracy'
journal of criminal justice and popular culture.
Hill, Charles (2007) 'Digital piracy: causes, consequences,
and stractegic responses' Asia Pacific Journal of
Management.
Hinduja & Sameer (2003) 'Trends and patterns among
online software piracy. Ethics and information
technology'
Husted, Bryan (2000) 'The impact of national culture on
software piracy, journal of business ethics'
Idris, K (2003) 'intellectual property, power tool for
economic growth' WIPO
Karakaya, M & Uluturk, B. (2010) 'Individual and Social
reasons behind software piracy: an analysis of
previous studies'
Lau, Eric Kin (2003) ' An empirical study of software
piracy. Business ethics: a European review'
Meyers, M. (2003). 'Introduction to PC hardware and
troubleshooting'. MCGraw Hill
National Advisory Council on Innovation ‘NACI’ (2004).
Free/libre & open source software and open standards
in SA.
Olsson, H. (1993) 'Introduction to intellectual property
law' WIPO/CNR/S/93/1
Parker, G. & Van Alstyne, M. (2005). 'Innovation through
optimal licensing in free markets and free software'.
Tulane University. Bolton University.
Parloff, R. (2007). 'Microsoft takes on the world.
Tortune'. available from http://money.cnn.com/
magazines/fortune/fortunes_archive/2007/05/28/10003
3867/index3.htm (Accessed 28/07/2007).
Reijswoud, V. & Mulo (2004). 'Free and open source
software for development myth or reality? case study
of a university in Uganda. Uganda Martyrs
University, Kampala', Uganda. Available from
Http://www.umu.ac.za.ug. (Accessed 25/09/2009).
Rensburg Ihron 2013 'Universities between a rock and a
hard place' Sunday time, Professor Ihron Rensburg is
Principal and Vice-Chancellor of the University of
Johannesburg
Scott, B. (2004). 'Open source and the IT trade deficit.
Open source law'. Available from http://
www.opensourcelaw.biz. (Accessed 25/08/2007).
Stallings, W. (2003c). 'Computer organization and
architecture: designing for performance'. Upper
sadder river. NJ. Prentice Hall.
Steinmueller, E. (2001). 'ICTs and the possibilities for
leapfrogging by developing countries international
labor organisation'. Geneva
Toko, G & Mnkandla, E 2011, 'Open source system:
migration and adoption for education purposes in
developing nation', second international conference
on computer science education: innovation and
technology, 2251-2195, page 1-8
Weber, S. (2002). 'Open source software in developing
economies'. University of California. Berkeley.
West, J. & Dedrick, J. (2005). 'The effect of computerise
movements upon organisational adoption of open
source'. College of business San Jose state university.
WIPO, (2004) 'WIPO Intellectual property handbook:
policy, law and use'
Wooi, T. (2004). 'International Development Research
Centre (IDRC)'. Available from www.idrc.ca/en/ev-83
806-201-1-DO_TOPIC.html. (Accessed 05/11/2009).
SoftwareSystemsVersusIntellectualPropertyRights-AMoralandEthicalChallengeforHigherEducationinDeveloping
Nations
259
