
Developed and Taught Course Modules to Enhance Cloud
Computing Education
Huiming Yu, Nakia Powell, Dexter Stembridge and Jonathan Rann
Department of Computer Science, North Carolina A&T State University, Greensboro, NC, U.S.A.
Keywords: Cloud Computing, Course Module, Hands-on Project, Education Tool.
Abstract: Cloud computing (CC) is emerging as a promising solution to businesses and individual users. In order to
effectively teach knowledge of CC we have developed three course modules, one education tool, and one
real world project. These modules have been successfully taught in COMP 621 Web Security course in
Spring 2011, Spring 2012 and Spring 2013 in the Department of Computer Science at XXXX. Our
experience exhibits that teaching these modules helped students not only understand the need of CC, but
also gained significant knowledge of CC and security architecture. Through a laboratory exercise and a real
world project students gained hands-on experience. Students’ survey and feedback reflected that these
modules and the laboratory exercise are very valuable in their educational experience. These modules and
hands-on laboratory exercise could be used in software engineering, networking, Web security and other
first year graduate level courses.
1 INTRODUCTION
Cloud computing provides flexible information
technology infrastructures and configurable software
services, reduces costs, enables business innovation
and many others benefits. The service that cloud
computing provides has become a commodity; when
companies like Amazon, Intel, Google develop new
applications, they sculpt cloud computing into the
product they will produce. Several cloud computing
systems have been developed by the industry, such
as Amazon Elastic, Amazon EC2, Google Apps, etc.
(Amazon Web Services, Google 2010). As a result
expectations for Information Technology (IT)
workforce have been increased by rapidly expanding
cloud computing applications. It becomes an urgent
task to teach knowledge of cloud computing to
computer science students, so that they can meet the
industry’s expectation for the next generation IT
professionals.
Most Computer Science, Information
Management System, and Software Engineering
curriculums do not adequately prepare students for
such expectations. Based on demand three cloud
computing course modules have been developed and
taught, and the hands-on laboratory exercise has
been designed and used in the Department of
Computer Science at XXXX. In this paper, we
present these new course modules titled
“Introduction to Cloud Computing”, “Introduction to
Cloud Computing Services”, “Security Architecture
for Trustworthy Cloud Computing”, one education
tool, one hands-on laboratory exercise and one real
world application project, and discuss our teaching
experience. In section 2 the learning objectives and
outcomes will be discussed. The details of these
modules will be presented in section 3. A hands-on
laboratory exercise will be specified in section 4. In
section 5 a real world application project will be
given. In section 6 teaching and evaluation results
will be presented. The conclusion and future work
will be discussed in section 7.
2 LEARNING OBJECTIVE AND
OUTCOMES
Cloud computing is expanding rapidly. As a result it
increases the expectations for IT professionals. In
order to prepare students for IT workforce and for
them to effectively learn knowledge of cloud
computing we have developed three course modules.
The learning objective of these modules is to
enhance the computer science curriculum by
providing information and technology that are
related to cloud computing and cloud computing
security. Instructors can teach these modules in
167
Yu H., Powell N., Stembridge D. and Rann J..
Developed and Taught Course Modules to Enhance Cloud Computing Education.
DOI: 10.5220/0004842101670175
In Proceedings of the 6th International Conference on Computer Supported Education (CSEDU-2014), pages 167-175
ISBN: 978-989-758-021-5
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

computer science senior classes or first year of
graduate courses.
After attending the lecture of these modules,
conducting a laboratory exercise and completing the
assigned project students should be able to 1)
understand the need for cloud computing, 2) gain
significant knowledge of cloud computing
architectures, characteristics and benefits, service
models, deployment models, enabling technologies,
data storage and operating system, and 3) apply
learned knowledge to real world applications.
3 THE COURSE MODULES
Three courses modules have been developed that are
“The Introduction to Cloud Computing”,
“Introduction to Cloud Computing Services”, and
“Security Architecture for Trustworthy Cloud
Computing”. We used three hours to teach the
module 1, three hours for module 2 and two hours
for module 3.
3.1 Module 1: Introduction to Cloud
Computing
In this module, basic concepts, characteristic,
benefits, enable technologies, service models and
several cloud computing architectures are
introduced.
In the basic concepts section we first answer the
question why we need cloud computing. Cloud
computing has the promise to provide all of
businesses, or single user needs such as storage,
computations, and applications in the mass, and the
end user decides what they would like to have. With
the increased demand for defining and molding
cloud computing into something that is not that
easily defined causes companies like Google,
Salesforce, IBM to become very aggressive in terms
of producing the product fast in order to be the
inimitable leader. This causes a need for other
companies like Twitter, Facebook to evolve and
adapt in order to keep up with and hopefully exceed
the pack of competing companies.
Secondly we briefly give the definition of
clouding computing by introducing several
definitions. One concept from Simon Wardley’s
“Cloud computing-Why it matters” presented at
OSCON 09 was “Cloud Computing is a generic term
used to describe the disruptive transformation in IT
towards a service based economy driven by a set of
economic, cultural and technological conditions”
(Wardley, 2009). We use a graphic image to display
the concept of cloud computing. Cloud computing
can be defined as a paradigm in which a system
utilizes the virtualized resources of networks of
computers to handle a systems workload. A
hypervisor must be a part of the system (Choi,
2009).
We present several existing systems to help
students understand the architecture of cloud
computing. First we introduce the architecture in a
basic and simple way. A cloud computing
environment consists of clients, the datacenter and
the distributed servers (Velte et al., 2009). We use
Amazon Elastic Computer Cloud (EC2) as an
example because Amazon EC2 is a web service that
provides resizable computing capacity in the cloud.
It allows the user to obtain and configure capacity
with minimal friction. It provides a user with
complete control of their computing resources and
lets them run on Amazon’s proven computing
environment. Amazon EC2 changes the economics
of computing by allowing the user to pay only for
capacity that they actually use (Amazon Web
Services).
We discuss five main characteristics of cloud
computing in this module. These characteristics are
On-demand self-service, broad network access,
resource pooling, rapid elasticity, and measured
service. On-demand self-service implies a consumer
can unilaterally provision computing capabilities.
Broad network access has capabilities that are
available over the network and accessed through
standard mechanisms that promote use by
heterogeneous thin or thick client platforms.
Resource pooling gives the provider’s computing
resources which are pooled to serve multiple
consumers using a multi-tenant model, with
different physical and virtual resources dynamically
assigned and reassigned according to consumer
demand. Rapid elasticity can be quickly and
elastically provisioned, in some cases automatically.
To the consumer, the capabilities available for
provisioning often appear to be unlimited and can be
purchased in any quantity at any time. Measured
service demonstrates cloud systems automatically
control and optimize resource use by leveraging a
metering capability at some level of abstraction
appropriate to the type of service. Resource usage
can be monitored, controlled, and reported providing
transparency for both the provider and consumer of
the utilized service (Mell et al., 2009).
We also discuss three service models that are
Software as a Service (SaaS), Platform as a Service
(PaaS), and Infrastructure as a Service (IaaS) in this
CSEDU2014-6thInternationalConferenceonComputerSupportedEducation
168

module (Choi, 2009). SaaS gives users the
capability to use the cloud provider applications
running on a cloud infrastructure. PaaS gives users
everything that they need to develop, test, and
deploy applications to the cloud. IaaS is delivery of
the computing infrastructure as a fully outsourced
service, versus an in-house, capital investment-
sourced model (Mell et al., 2009).
We introduce three key enabling technologies
that are virtualization, hypervisor and Web services
in this module. Over the last several years,
virtualized technologies have become a standard in
the world of computers. These technologies,
including the virtual machine, are software
implementations of computer systems which
partition hardware into high-level abstractions. This
allows for resource sharing within the cloud along
with more affordable, flexible and scalable hardware
services (Wang et al., 2008).
Virtualization can be looked at as the abstraction
of computer resources from the actual computer
which can successfully allow databases, middleware,
and operating systems to practically run anywhere.
Cloud computing paradigm allows workloads to be
deployed and scaled-out quickly through the rapid
provisioning of virtual machines or physical
machines. Service virtualization combines and slices
business services deployed independent of the
operating systems, programming language or
hosting location. An intermediary cloud gateway sits
between the producer and the consumer and
aggregates the Web Service Description Languages.
When software is run on a virtual machine, the
bits representing the programs instructions run
through a layer of software that simulates a
dedicated server infrastructure. This layer of
software is known as the hypervisor. Hypervisors
allow servers to run a single instance of software
that serves multiple clients at a time, without
needing to rewrite the software. They also allow
operating systems and applications to install a
consistent hardware profile (Yu et al., 2012). Web
services today are frequently just Application
Programming Interfaces (API) or web APIs that can
be accessed over a network, and executed on a
remote system hosting the requested services.
3.2 Module 2: Introduction to Cloud
Computing Services
In this module we discuss data storage as a service,
software as a service, and cloud computing
operating system.
Commonly known as Storage as a Service
(StaaS) cloud computing presents a solution for any
user’s need with its robust infrastructure that far
exceeds the needs of any user with an internet
connection. StaaS allows users to store data at
remote disks and access them anytime from any
place (Wang et al., 2008). User’s data is stored on
remote storage systems that are maintained by a
third party. The data is then accessible through the
Internet.
Cloud storage as of today comes in many
different architectural designs. A cloud based
storage system connects the user to their stored
information through a web application that allows
the user to create, store, and file all the information
chosen (Wang et al., 2008). This design shows
where the user works on the application layer
uploading files to the cloud, the software service
then distributes the uploaded information to three
separate storage locations for disaster recovery. The
application, which is the web portal or interface to
the cloud storage, allows users to subscribe to the
web cloud storage. Copies of the files that the user
submits are then transferred over the Internet to
cloud storage servers.
We use Amazon S3 (Simple Storage Service) as
an example to explain how StaaS works. Amazon S3
is a platform that allows for cloud storage to users
on any scale from one gigabyte to thousands of
exabytes. With low cost, scalability and reliability
Amazon S3 can meet any software developers’
needs [Amazon Simple Storage Service].
A cloud computing operating system (OS)
provides an interface for developing and deploying
massively scalable distributed applications on behalf
of a large number of users and exploiting the
seemingly infinite CPU, storage, and bandwidth.
Traditional Operating Systems are used to manage
hardware components within the computer. The
cloud OS relies on distributed processes that manage
the cloud resources. A cloud OS is similar as a
traditional OS that is a collection of scheduler,
virtual memory allocator, file system code, interrupt
handlers, etc. to regulate the access by software to
CPU, memory, disk, and other hardware peripherals.
A cloud OS provides an additional set of
functionalities to give administrative access to
resources in the cloud. A cloud OS also provides a
set of network-based interfaces that applications can
use them to query the management system and
control cloud resources (Pianese et al. 2010).
The Architecture of the cloud operating system
consists of two separate spaces that are the User
Space and Kernel Space (Pianese et al. 2010). The
cloud’s kernel space is used to regulate physical
DevelopedandTaughtCourseModulestoEnhanceCloudComputingEducation
169

allocation, access control, accounting and
measurement of resources within the cloud’s space.
The cloud’s user’s space contains processes that are
directly used by users.
Virtual Machine (VM) Management is the
process that controls the allocation and de-allocation
of virtual machines. Through the authentication
kernel access rights are granted to the VM
Management Kernal. This kernal is responsible for
mapping an object name with its network address
and port number. Catching all signals from the cloud
OS, objects in the cloud user space are called and
handled through this process.
Distributing processes is a key to provide
abstraction and flexibility to computing resources
from its physical nodes; this can be done with the
use of Virtual Machines. Support for multiple OS’s
on the same hardware presents isolation to a certain
extent between processes running on different VMs.
Dynamic allocation on the cloud is done at two
locations, the cloud process level migrates single
processes between nodes while the VM level uses
check pointing which can restore a VM state on a
different node. Access control is controlled by a
factotum server running on every machine,
dedicated to authenticate the users resulting in a
single sign on facility. The cloud user space contains
libraries of API’s that can be manipulated and
changed to scale the application to satisfy different
specifications just by updating a minor amount of
embedded cloud library parameters (Pianese et al.,
2010).
The cloud user space helps developers in two
ways. One is eliminating the need for a developer to
implement his or her own custom libraries, but
instead use the cloud library API’s and customize
them. Secondly updating cloud library parameters
for different specifications results in reusability of
application components.
Software services known as SaaS (Software as a
Service) identifies the use of computing power on a
huge scale such as the cloud where companies can
access applications and large amounts of virtual
computing software without buying it. A service
request is sent to the actual cloud service provider
through a high level design. The web services
architecture has three roles: a cloud provider, an
application execution requestor, and a
broker/mapper. The provider creates the web service
and makes it available to clients who want to use it.
An application requestor is a client application that
consumes the web service. The mapper provides a
way for the provider and the requestor of a web
service to interact. The provider, requestor, and
broker interact with each other through the
operations of publish, find, and bind. A provider
informs the broker about the existence of the web
service by using the broker's publish interface to
make the service accessible to clients. The
information published describes the service and
specifies where the service is located. The requestor
consults the broker to locate a published web service
(Lu, 2010).
3.3 Module 3: Security Architecture
for Trustworthy Cloud Computing
Many security technologies have been proposed and
developed to enhance cloud computing security. In
this module we use Cisco Secure Data Center
Framework as an example to discuss security issues.
Cisco Secure Data Center Framework is one of them
that provides multiple security layers and applied
different existing security technologies to enhance
cloud computing security [Bakshi].
Cisco has developed the Cisco Secure Data
Center Framework with many security and trust
considerations. The first consideration is general
security issues. In this framework traditional security
issues of information assurance such as data access
control, encryption, and incident detection are
integrated. The second consideration is access
control that means an enterprise has capability to
directly manage how and where data and
applications are deployed and used. The third
consideration is compliance and service-level
management (SLA). It includes contracting and
enforcement of service level agreements between
different parties, legal issues, regulation and industry
requirements, etc. The framework consists of Threat
Profile, Cloud Data Center Visibility, Cloud Data
Center Protection, Cloud Data Center Building
Blocks, Cloud Data Center Control, Cloud Data
Center Compliance and SLA. The Threat Profile
contains threat models such as Service Disruption,
Intrusion and Takeover, Data Leakage, Data
Disclosure, Data Modification, Identity Theft and
Fraud, etc. The Cloud Data Center Visibility
provides various functions such as intrusion
detection, anomaly detection, packet capture,
network data collection and monitoring as well as
event analysis and correlation. The Cloud Data
Center Protection is very straightforward and
provides different protection techniques and
mechanisms such as stateful firewall access control,
intrusion prevention, content filtering, and enforces
endpoint and baseline security. Cloud Data Center
Control deals many issues with how data being
CSEDU2014-6thInternationalConferenceonComputerSupportedEducation
170
control. Because data are centralized in Cloud
Computing it increase the possibility of insider
threats, therefore a compartmentalization strategy is
important. The data encryption policy must be in
place for customers and providers. For an
administrator, who accesses and controls virtualized
operating system, must be strong authenticated. The
Cloud Data Center Compliance and SLA deal with
how the data being handled is controlled. So certain
requirements are set in place by the consumer and
provider in order to reach an agreement to make sure
requirements for both are met. The service level
agreement is in place to enforce these requirements
and to make sure that the consumer and provider
remain compliant [Bakshi].
4 A HANDS-ON LABORATORY
EXERCISE
A key issue for students learning cloud computing
knowledge and apply it to real world applications is
to get hands-on experience. We have developed a
deployment education tool and a one hour laboratory
hands-on exercise to help students learn related
knowledge and use cloud computing platforms.
4.1 Using Microsoft Windows Azure
Platform
There exist many cloud providers. All of which have
platforms associated with the deployment of
applications to their cloud environment. Each
provider implements its cloud service in order to
cater to the needs of clients.
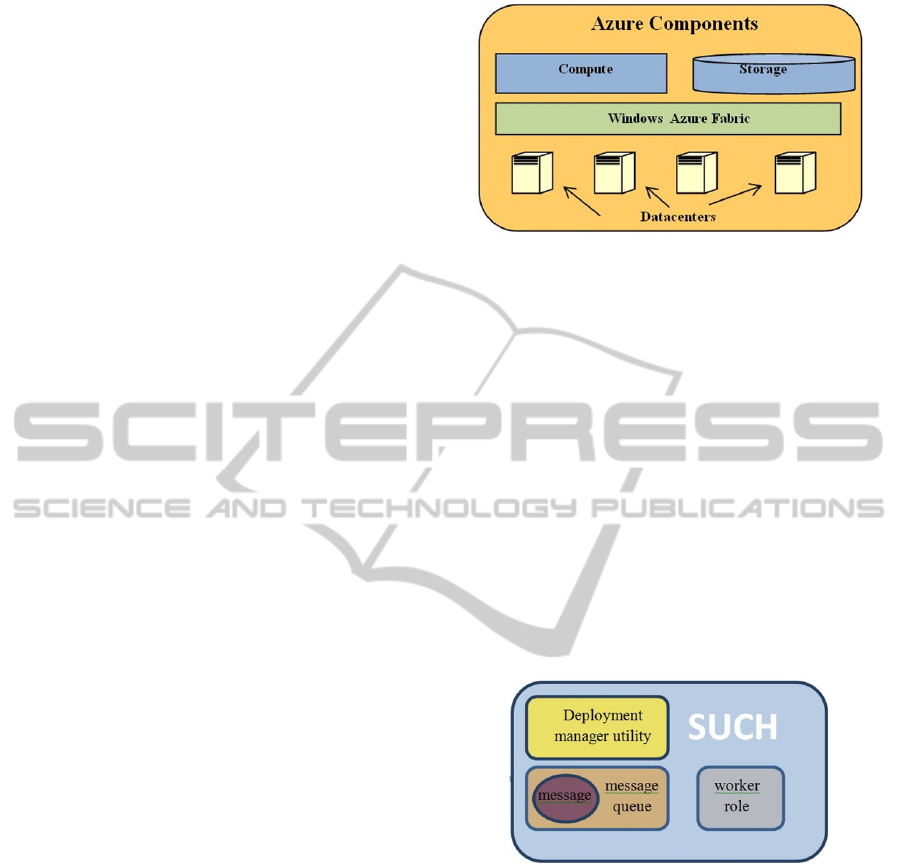
We selected Microsoft Windows Azure as our
cloud platform. This platform provides and
maintains control of an integrated development and
hosting environment to allow software developers to
easily create, manage, scale, and host applications
through Microsoft datacenters. Applications are
executed using Azures compute services, while
storage is handled by the storage services; both of
which are built on top of a component known as the
Windows Azure fabric, which ties all services
together and monitors applications to maintain
desired states (Chappelle, 2008). These services are
the main components of Windows Azure, shown in
Figure 1. Specifically, a few of the responsibilities
of the Azure fabric is to create new VM’s and assign
them to processor cores, run instances of an
application, and detect when a instance has failed.
Figure 1: Windows Azure components.
4.2 Designing and Implementing an
Education Tool
We designed and implemented an education tool
named Scientific Utility for Cloud Harnessing
(SUCH) (Yu et al. 2012). This tool provides
functions to successfully deploy scientific
applications to the Windows Azure cloud platform
in a less complex manner than other methods, thus
helping students to get hands-on experience of using
cloud services. SUCH consists of three main
components that are the deployment manager utility,
the message queue, and the worker role. These
components are shown in Figure 2. All of these
components work together to upload, execute, and
manage deployments within Windows Azure.
Figure 2: SUCH components.
The deployment manager utility allows students
to upload files as well as manage services and
applications utilizing the cloud. When the
deployment manager is executed, it initiates cloud
components, uploads files, and creates, starts, stops,
and deletes deployments. To execute it, users must
navigate to the Azure Application executable file
located in Azure Deployment Manager folder in
SUCH. The Message Queue utility builds messages,
and stores them on the message queue for the worker
role. It is composed of three programs:
RunScienceCodeMessage.cs, a bucket class used to
create message objects for the message queue,
PopulateMessage.cs, which creates message object
DevelopedandTaughtCourseModulestoEnhanceCloudComputingEducation
171

instances, initiates the message queue in Azure,
serializes messages and populates the message
queue, and ClearMessageQueue, which clears the
message queue of messages.
The Worker Role,
located in the Application Worker Role folder, first
uses an infinite loop to check the queue for
instructions. If a message is located, the worker role
takes it from the queue and executes message
instructions with the assistance of Azure
components.
SUCH provides a simple means of utilizing the
vast resources within the cloud, thus students can
avoid many unnecessary complications. It is user-
friendly; students can join the laboratory lecture,
read a few pages of instructions, complete set up and
configuration steps, then they can execute their
applications in the cloud.
4.3 Developing a Hans-on Laboratory
Exercise
We developed a one hour hands-on laboratory
exercise to help students understand how Microsoft
Windows Azure works, how to develop and deploy
an application to a cloud system. We wrote a
document titled “User Manual for Using Microsoft
Windows Azure and SUCH”. It describes all details
of ten steps to guide students using Microsoft
Windows Azure and SUCH.
First students must sign up for an account and
downloading the Windows Azure SDK. Then
students should download the SUCH zip file
containing Clear Message Queue, Populate Message
Queue, Application Worker Role, and Azure
Deployment Manager. Students need to create an IIS
management certificate and upload it to Azure via
the management portal. They must fill in storage
credentials into the values in the setting property of
the SUCH worker role. Students need to generate a
package file via the publish function in the SUCH
worker role. Once the file is generated, they
navigate to the Publish folder in the Application
Worker Role folder, copy the configuration and
service package files, and move them into the Debug
folder of the Deployment Manager Utility Folder.
Once those steps are completed, students must fill in
account name, account key, etc. for the
configuration files in the populate message queue,
clear message queue, and deployment manager
utilities. The file intended to be executed in the
Azure should then be uploaded to Azure storage.
Finally, users simply run the
AzureDeploymentManager.exe, which will progress
through a sequence of steps which enable successful
application deployment. As SUCH executes,
students can navigate to the online Azure
management portal to view the creation, starting,
stopping, and deletion of deployments. Figure 3
shows the Azure management portal as a
deployment is in its Starting phase.
Figure 3: Output files created from executed applications
within Azure.
In order to deploy to Azure, all executable
applications must be uploaded to blob storage using
CloudBerry Explorer for Azure Blob Storage. Using
CloudBerry Explorer, a student would navigate to
the Release folder location in the bin section of each
folder that the executable file is located in. Next the
student would execute SUCH and wait until the
deployment has fully started. Once the deployment
is ready, the student would fill the Populate Message
Queue configuration file with information specifying
the name of the executable files to be executed in
Azure, location of each of the executable files in
Azure storage, and the expected output file. After
SUCH successfully runs, studnets should check their
storage container to see if a new output file was
created and uploaded to the cloud storage.
4.4 Getting Hands-on Experience
After students attend the lectures of the new course
modules they are required to attend the one hour
hands-on laboratory exercise. In the laboratory, we
briefly introduce the functions of Microsoft
Windows Azure and how to use the Scientific Utility
for Cloud Harnessing. Then we guide students to go
through installation and create a configuration file.
We have developed several small application
examples to let students to deploy them and to run
these examples in Microsoft Windows Azure
according to the steps that are described in 4.3. One
application example is that prints a message to a text
output file and fills an array with random numbers,
then sorts the array in ascending and descending
order, and displays the results in the output file. The
results are shown in Figure 4. The output text file
CSEDU2014-6thInternationalConferenceonComputerSupportedEducation
172
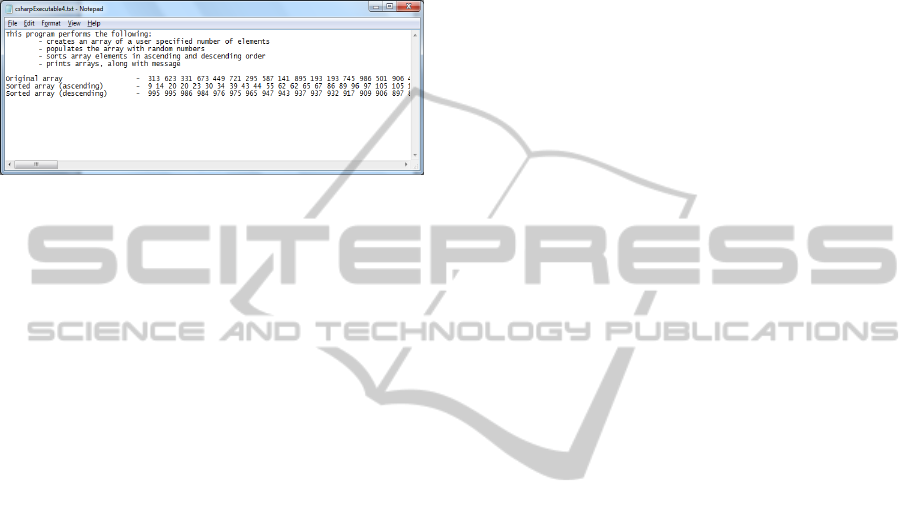
first displays a message explaining the functions of
the program such as ‘creates an array of a user
specified number of elements’. The next line
displays an array of 50 elements, containing random
numbers between 0 and 1000. The line after that
displays the sorted array in ascending order, and the
last line displays the sorted array in ascending order.
Figure 4: The output file.
Because COMP 621 Web Security is a graduate
class most students (about 80%) can follow the
instruction to deploy and run the sample program
successfully. Some students need Teaching
Assistants help.
5 A REAL WORLD
APPLICATION PROJECT
Another key issue for students learning cloud
computing knowledge and applying it to real world
is to let them develop an application and run it in an
existing cloud computing platform. Using this
method students learn how to solve a real world
problem and how to use a cloud computing system,
and reduce the gap between classroom and the real
world.
We assigned a real world application project to
students. Two or three student formed a team. We
provided detailed information about Microsoft
Windows Azure, such as Azure account
management, Azure services, configuration and
package files, etc. to students. The project consisted
of four major phases. In phase I each team
developed a real world application program and
executed it on a local computer. The program could
be a hotel reservation system, a car dealer system, a
student information management system, etc. In
phase II students used SUCH to deploy the
developed application to the Microsoft Windows
Azure. In phase III students executed the application
in the Microsoft Windows Azure and putted output
information into a data file. In phase V students
checked their storage container (via Cloudberry) to
see if a new data file was created and uploaded to
storage in the cloud. Each team must hand in a
project report that included how the program was
developed, how they deployed the program to the
cloud, and the executed result. We also required
every team to demonstrate their project in the class
and exchange experience with other students within
ten minutes.
6 RESULTS
We have successfully taught three course modules in
COMP 621 Web Security class in the Department of
Computer Science at XXXX in Spring 2011, Spring
2012, Spring 2013 and received excellent results.
Eighteen students took this course in Spring
2011, twenty-six in Spring 2012 and sixteen in
Spring 2013. The students were very excited about
learning the new emerging technology of cloud
computing. To evaluate the students’ reactions and
get feedback for teaching these modules we
conducted a pre and post surveys at each semester.
These surveys were in addition to the university
course evaluation. The survey consists of two
groups. The first group contains eight questions that
reflected knowledge level of students. These
questions are 1) basic knowledge of cloud
computing, 2) knowledge of characteristics, service
models and enable technologies, 3) knowledge of
architectures, 4) knowledge of data storage services,
5) knowledge of operating systems, 6) knowledge of
application software services, 7) knowledge of
threats, and 8) knowledge of security mechanisms.
Students’ ratings could be very low, low, medium,
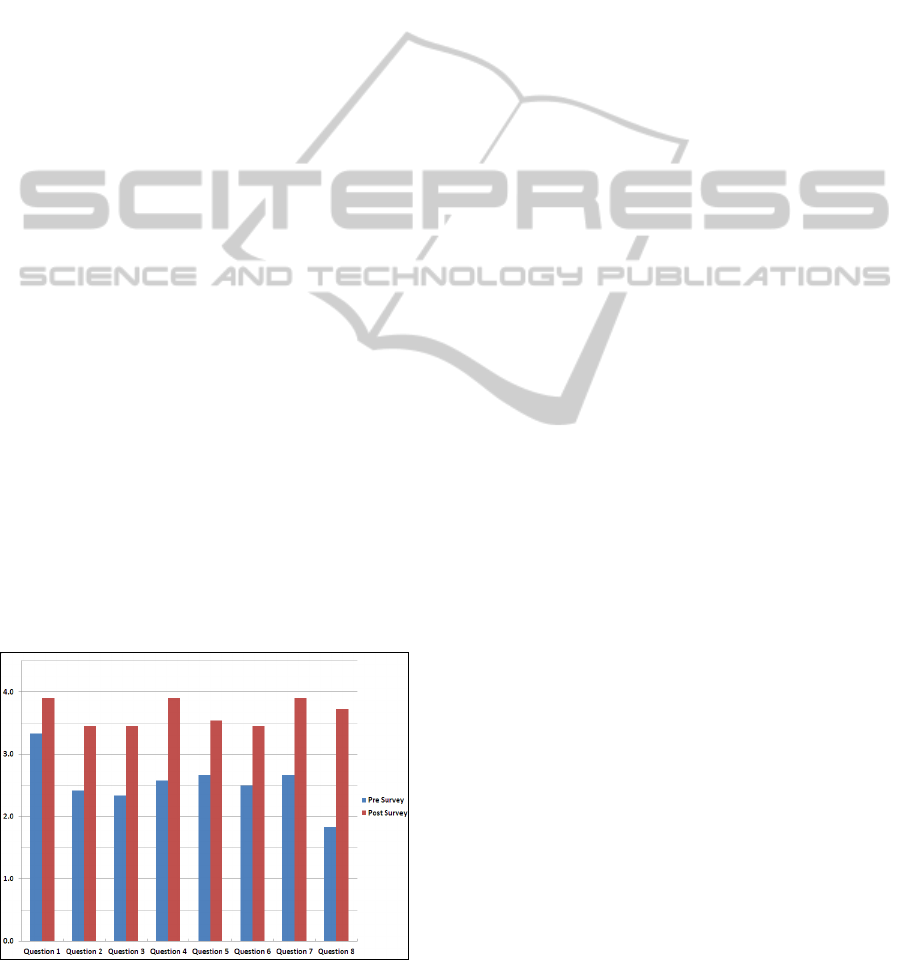
high, and excellent. The Spring 2013 survey results
are displayed in Figure 5. Blue color represents pre-
survey and red color represents post survey. For the
pre-survey majority of the students gave a very low
rating for their knowledge of characteristics, service
models, enable technologies, architectures,
deployment models, application software services
and security mechanisms of cloud computing. The
results varied more for students’ knowledge on data
storage services, operating systems and threats of
cloud computing, while majority of students seemed
to have basic knowledge of cloud computing. No
students rated their knowledge as High for any
questions in the pre-survey. The post survey results
show that students learned cloud computing and
improved their knowledge levels. They had big
improvement in their knowledge of characteristics,
service models, enable technologies, architectures,
data storage services, operating systems, threats, and
security mechanisms of cloud computing. The
DevelopedandTaughtCourseModulestoEnhanceCloudComputingEducation
173
second group are general questions that are 9) these
modules help you gain knowledge of cloud
computing and security related issues, and 10) you
are more knowledge about cloud computing, threats
and security mechanisms. Students could select
Strongly Agree, Agree, Neither Agree or Disagree,
Disagree, or Strongly Disagree. 100% students
selected agree or strongly agree for all questions in
the second group. Students felt these modules
stimulated their interest to learn more about cloud
computing. Most students enjoyed the hands-on
laboratory exercise.
7 CONCLUSIONS
This paper presents three new cloud computing
course modules titled “Introduction to Cloud
Computing”, “Introduction to Cloud Computing
Services” and “Security Architecture for
Trustworthy Cloud Computing”, an education tool, a
hands-on laboratory exercise and a real world
application project assignment. These modules cover
the basic concepts, architecture, characteristics and
benefits, service models of cloud computing. These
modules also discuss virtualization, hypervisor, Web
services of enabling technologies, deployment
models and cloud computing operating systems.
Microsoft Windows Azure was selected as the cloud
platform for the hands-on laboratory exercise. An
education tool, Utility for Cloud Harnessing was
developed to provide functions to deploy
applications to the Windows Azure cloud platform
in a simple manner, was used. A hands-on
laboratory exercise has been developed to guide
students to deploy and run an application in the
Azure cloud platform step by step. Finally a real
world application project was assigned to students.
Figure 5: Spring 2013 Surveys.
We have successfully taught these modules in
COMP 621 Web Security course in Spring 2011,
Spring 2012 and spring 2013. Students’ survey and
feedback reflected these modules are very valuable.
They felt the module stimulated their interest to
learn more about cloud computing. Our experience
exhibits that combining lectures and hands-on
laboratory exercise together can successfully
integrate education and real world application into
cloud computing education. The lectures bring new
technology to students; let them learn the knowledge
and applications of cloud computing. The hands-on
laboratory exercise demonstrates how to deploy and
run an application in an existing cloud platform,
helps students understand functions of a real world
cloud computing system and learn how deploying
and running an application on the cloud platform,
and lets students gain important insights into how
applying learned knowledge into a real world.
Assigning a real world application as a project helps
students understand the difference running an
application on a local computer and on a cloud
computing system, increases their capability to solve
complicated problems and breaks barriers between
education and real world applications. Our
experience also proves that teaching cloud
computing modules is beneficial to students through
both theory and hands-on experience, helps them
learn advanced technology and apply learned
knowledge to real world applications.
In order to satisfy the high demand of cloud
computing professionals we are developing a course
titled “Cloud Computing and Security”. We will
offer this course in Fall 2014.
ACKNOWLEDGEMENTS
This work was partially supported by National
Science Foundation under the award number CNS-
0909980, DUE-0830686 and DUE-1129136.
REFERENCES
Amazon Web Services, DOI=http://aws.amazon.com/ec2/
Google 2010 Google Apps, DOI=http://
code.google.com/apis.
Wardley, S., 2009. Cloud Computing-Why it Matters.
O’Reilly Open Source Convention.
Choi, P., 2009. How to Develop an Effective Security
Strategy to Play in the Public Cloud. Cloud Computing
Journal.
Velte, T., Velte, A. and Elsenpeter, R., 2009. Cloud
CSEDU2014-6thInternationalConferenceonComputerSupportedEducation
174

Computing A Practical Approach. McGraw-Hill.
Mell, P. and Grance, T., 2009. The NIST Definition of
Cloud Computing. Version 15, October 7, 2009.
Chappelle, D., 2008. Introducing the Azure Services
Platform. Microsoft Corporation.
Wang, L., Tao, J. and Kunze, M., 2008. Scientific Cloud
Computing: Early Definition and Experience. In
Proceedings of 10
th
IEEE International Conference on
High Performance Computing and Communications.
Wu, J., Ping, L., Ge, X., Wang, Y. and Fu, J., 2010.
Cloud Storage as the Infrastructure of Cloud
Computing. In Proceedings of IEEE Int. Conf. on
Intelligent Computing and Cognitive Informatics.
Amazon, Amazon Simple Storage Service,
DOI=http://aws.amazon.com/s3/faqs/#What_can_I_do
_with_Amazon_S3.
Pianese, F., Bosch, P., Duminuco, A., Janssens, N.
Stathopoulos, T. and Steiner, M., 2010. Toward a
Cloud Operating System. In Proceedings of IEEE
Network Operations and Management Symposium.
Lu, X., 2010. An Approach to Service and Cloud
Computing Oriented Web GIS Application. In
Proceedings of IEEE International Conference on
Internet Technology and Applications.
Bakshi, K. Cisco Cloud Computing - Data Center
Strategy, Architecture, and Solutions.
DOI=http://www.cisco.com/web/strategy/docs/gov/Ci
scoCloudComputing_WP.pdf .
Yu, H., Rann, J. and Zhan, J., 2012. SUCH: A Cloud
Computing Management Tool. In Proceedings of the
5th IFIP International Conference on New
Technologies, Mobility & Security.
DevelopedandTaughtCourseModulestoEnhanceCloudComputingEducation
175
