
Signaling Attacks in Mobile Telephony
Mihajlo Pavloski and Erol Gelenbe
Department of Electrical & Electronic Engineering, Intelligent Systems and Networks Group,
Imperial College, London SW7 2AZ, U.K.
Keywords:
Signaling Attacks, UMTS, Mitigation, Denial of Service.
Abstract:
Mobile telephony based on UMTS uses finite-state control schemes for wireless channels and for signaling
across the network. These schemes are used systematically in various phases of the communication and are
vulnerable to attacks that can bring down the network through unjustified bandwidth allocation and excessive
signaling across the control plane. In this paper we identify those system parameters which are critical to the
success of such attacks, and propose changes that can limit the effect of the attack. The approach is based
on establishing a mathematical model of a UMTS system that is undergoing attacks, and on showing how
parameters can be optimally modified to minimise the effect of the attack as experienced by the mobile device
and the network.
1 INTRODUCTION
Smartphone and tablet use has increased rapidly in the
last few years, allowing users to access the Internet at
any time and place (Marck, 2013). The popularity
of smartphone applications has also rapidly increased
and in order to improve user experience and provide
real-time services, application developers tend to pro-
vide always-on connectivity in their applications by
including background traffic and “keep-alive” mes-
saging. All of this would have functioned perfectly
well if mobile phones had PC-like Internet connectiv-
ity.
However in mobile networks such as Universal
Mobile Telecommunications System (UMTS), con-
nections are dynamically created and teared-down to
optimise the use of resources. The creation of each
connection requires exchanging of additional signal-
ing messages to setup and reserve network resources.
Malicious or poorly developed smartphone apps gen-
erate traffic which triggers frequent connections and
produces excessive signaling in the control plane of
the network.
In order to avoid developer’s mistakes, the Global
System for Mobile Communications Association
(GSMA) has issued a guideline for network-friendly
application development (GSMA, 2012). But mali-
cious apps may be intentionally developed to attack
the network stability and interrupt it’s services. This
type of attack can lead to network overload and rep-
resents a Denial of Service (DoS) attack known as a
Signaling Attack (Abdelrahman and Gelenbe, 2014).
Indeed, it is reported that most of todays networks
are vulnerable to signaling attacks that can lead to
documented network failures (Wireless, 2012). While
from a network perspective such an attack via many
mobile devices using the network, would congest the
wireless bandwidth and the signaling servers in the
backbone, it would also have a negative effect for the
user. An infected device would successively trigger
unwanted communication with the network and drain
the battery of the device, and perhaps also create un-
desirable billing for services that are being accessed
within the UMTS network and outside via web sites.
2 AIMS OF THIS RESEARCH
This paper proposes a probabilistic approach towards
optimising network’s parameters in order to lower the
impact of signaling attacks. We are interested to see
how the network (referred also as system) reacts to
a signaling attack. Then we investigate whether it
can maintain its stability under an attack by changing
some specific state transition time constants, such as
it’s inactivity timers, or by adding delay in responding
to bandwidth request messages.
For this purpose we first propose a mathematical
model of a an individual mobile’s states in the UMTS
system, that includes the effects of a signaling attack.
We introduce an attack cost function that incorporates
206
Pavloski M. and Gelenbe E..
Signaling Attacks in Mobile Telephony.
DOI: 10.5220/0005019802060212
In Proceedings of the 11th International Conference on Security and Cryptography (SECRYPT-2014), pages 206-212
ISBN: 978-989-758-045-1
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

the probability of presence of the mobile’s states in
the attack and normal states. This model is then used
for optimisation. The results obtained suggest that se-
lecting correct values for the parameters can improve
the overall system performance even when attacks oc-
cur.
The paper is organised as follows. Section 2.1
briefly reviews the related work in the field, while
Section 3 discusses the Radio Resource Control
(RRC) mechanism in UMTS. In Section 4 we de-
scribe our model and its parameters, and in Section 5
we introduce the cost function to be optimised. Sec-
tion 6 presents and discusses the results that are ob-
tained, while Section 7 presents some conclusions and
suggests further research directions.
2.1 Related Work
Security in general (Gelenbe and Wu, 2012) has come
to the forefront of much of the research in informa-
tion technology in recent years, and cybersecurity in
particular (Gelenbe et al., 2013b) is viewed as an in-
tegral part of security in general. Indeed it is impossi-
ble today to address physical security (Gelenbe et al.,
1997; Cao and Gelenbe, 1998) without including the
impact of cybersecurity. In particular UMTS based
mobile network infrastructures which are universally
available constitute an essential component of today’s
secure infrastructures.
The security of wireless networks has been of
great interest in recent years (Yu et al., 2014), lead-
ing to many research projects in Europe and else-
where (Gelenbe et al., 2013a). In particular, signal-
ing DoS attacks and their mitigation (Gelenbe and
Loukas, 2007) has been a popular research topic in
wireless and mobile communications. Publications
in the field range from analytical algorithms, simu-
lations using real world data to complex systems for
inspecting attacks on mobile networks.The authors in
(Kambourakis et al., 2011) present an extensive sur-
vey of possible attacks in mobile networks.
A large Markov chain model is used in (Abdelrah-
man and Gelenbe, 2014) for the mathematical eval-
uation of signaling attacks parameters, with the ob-
jective of identifying the system parameters which
should be avoided, namely those that, from an at-
tacker’s perspective, produce the largest amount of
damage through load in the network. The work in
(Wang et al., 2004) regards the detection of traditional
flooding-based DoS attacks as a change-point prob-
lem and applies the non-parametric CUSUM test for
detection. Similarly, in (Lee et al., 2007) a CUSUM
test in the early detection algorithm of low-rate, low-
volume signaling attacks is suggested and simulations
driven by real traces are used to demonstrate the im-
pact of a signaling attack. Good points of the ap-
proach are the simplicity, dynamism and small detec-
tion time of the method, although the emulation of 3G
signaling on WLAN is doubtful and some unrealistic
assumptions are made.
The work in (Wu et al., 2010) proposes a random-
ization of the Radio Resource Management (RRM)
and Mobility Management (MM) procedures to hide
the parameters which are important to attackers. The
analysis of signaling traffic in real-world UMTS net-
work is presented in (Choi et al., 2014). The paper
shows a comparison of signaling traffic by different
type of mobile applications and its influence on the
RRC part of the network. It also explores some ap-
plication and network layer solutions for controlling
application signaling traffic. The authors in (Gupta
et al., 2013) inspect the influence of high signaling
volumes in LTE networks on the energy consumption
in mobile phones. Other modeling approaches of DoS
attacks in 3G cellular networks are reviewed in (Ric-
ciato et al., 2010).
3 UMTS RADIO RESOURCE
CONTROL
The management of communication resources in
UMTS is regulated by the Radio Resource Control
(RRC). In general, there are two RRC connectivity
modes: Idle and Connected. In Idle mode there aren’t
any radio resources used between the User Equip-
ment (UE) and the Radio Network Controller (RNC).
The few tasks a UE performs in Idle mode are related
to neighbor cell monitoring, cell re-selection, paging
and broadcast data reception. In this state, the UE
consumes the least amount of energy. RRC’s Con-
nected mode is further divided in four states:
• CELL
DCH - a state where a dedicated connec-
tion exists in UL and DL direction. Radio re-
sources are dedicated exclusivelyto the UE allow-
ing it to send and receive data at higher speeds;
• CELL
FACH - there aren’t any dedicated con-
nections but data can be transferred via common
channels. This state is suitable for transfer of
small amount or bursty data. This state preserves
the use of radio resources in the cell;
• CELL
PCH - similarly to Idle state the UE moni-
tors only the paging and broadcast channels. The
difference is that the logical RRC connection still
exists;
• URA
PCH - a state similar to CELL PCH where
every cell change does not trigger a cell update
SignalingAttacksinMobileTelephony
207
procedure in order to decrease the signaling activ-
ity.
In UMTS the concept of connection is separated
from the concept of Radio Bearer (RB). When an
idle UE wants to make a data call it needs to es-
tablish a connection and obtain communication re-
sources. The UE first initiates establishment of a
RRC connection and then the network creates one or
more RBs depending on the requested and available
resources. There can be only one RRC connection per
data call or per UE but many RBs within one connec-
tion. The RB defines the properties of the connection
depending on the requested QoS parameters. For in-
stance, to transfer low volume data the UE will obtain
a common physical channel (CELL FACH state) and
a dedicated physical channel (CELL
DCH state) for
a higher volume, delay-restricted data. The network
then revokes allocated resources after an inactivity
timeout t
L
in CELL
FACH state or t
H
in CELL DCH
state (3GPP, 2002; Korhonen, 2003).
The RRC mechanism, as described, is vulnera-
ble to attacks triggering an excessive number of tran-
sitions between states. A single user request for
connection/resources triggers multiple signaling mes-
sages that are transferred in the access and core part
of the network. If requests are repeated regularly by
many malicious UEs, the network will overload.
In particular, we can distinguish between two dif-
ferent types of signaling attacks:
• FACH attacks. A FACH attack occurs when
the attacker makes a low bandwidth request in
repetitive intervals. This attack triggers signaling
messages by transitioning between CELL
PCH
and CELL
FACH states or between Idle and
CELL
FACH states.
• DCH attacks. The attacker performs a DCH at-
tack with repetitive high bandwidth requests. This
type of attack generates signaling traffic by al-
ternating between CELL DCH and CELL FACH,
CELL PCH or Idle states.
The most common signaling attacks are CELL
PCH
state triggered FACH attacks and CELL FACH state
triggered DCH attacks. Excessive signaling has neg-
ative influence also on the user experience because of
high power consumption in the UE.
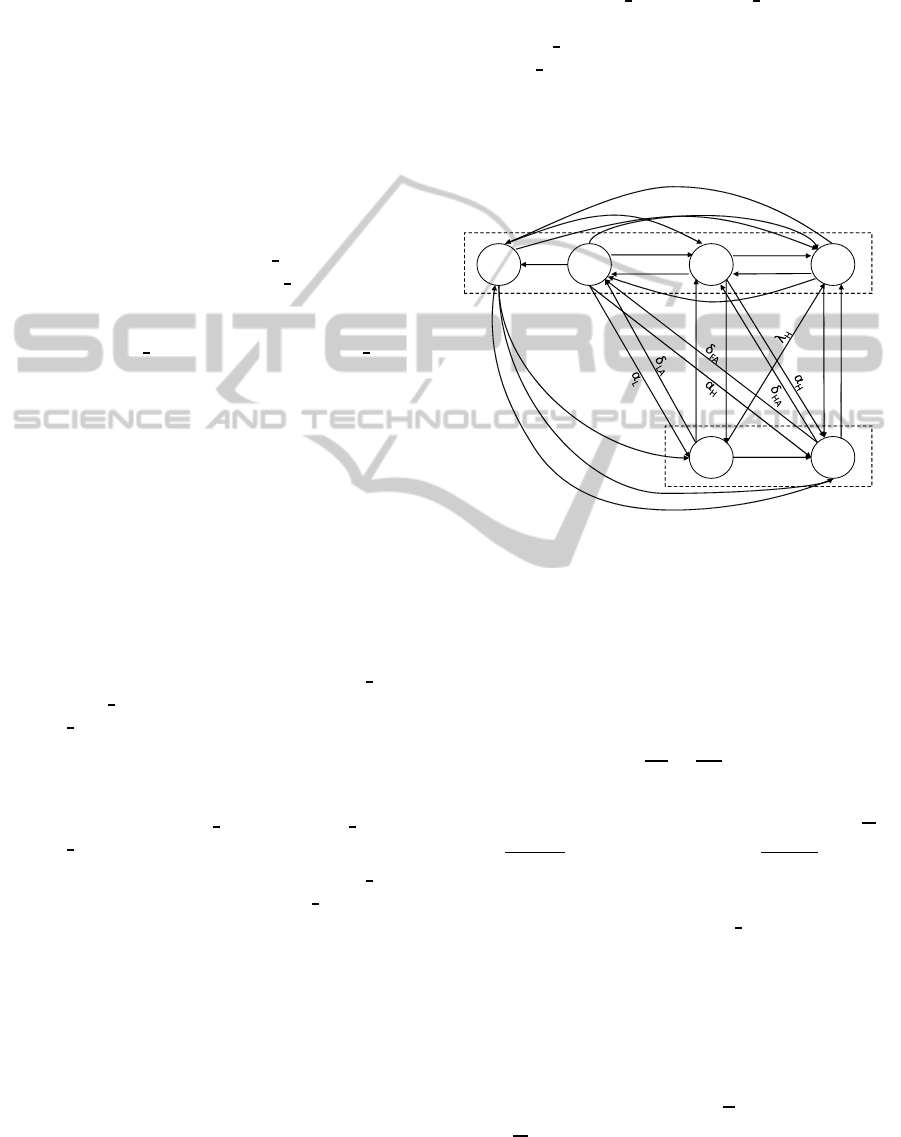
4 SYSTEM MODEL
The model used in this research is based on con-
ventional stochastic modeling techniques (Gelenbe,
1979) and focuses on a single user’s RRC part of the
UMTS system. It is described by the state diagram on
Figure 1. The figure depicts a model derived from
the conventional UMTS model with added ’attack’
states in the system. The idle state is represented by
D - Dormant. CELL
PCH and URA PCH are repre-
sented by a single P state. L (the low state) repre-
sents CELL
FACH and H (the high state) represents
the CELL
DCH state. The corresponding states when
attacks occur, or the attack states, are denoted with
subscripts L
A
and H
A
for allocated FACH and DCH
channels because of an attack.
ʄ
,
ɷ
,
ɲ
,
W > ,
>
,
ʄ
,
ɲ
,
ʄ
>
нʄ
,
ɲ
>
нɲ
,
ʄ
>
ʄ
>
ʄ
>
ɷ
>
ɲ
>
ɲ
>
ʄ
,
ɷ
s
ɷ
W
ɷ
s
ɷ
&
ŶŽƌŵĂůƐƚĂƚĞƐ
ĂƚƚĂĐŬƐƚĂƚĞƐ
Figure 1: RRC model of UMTS under signaling attack.
At any given time and state, the system may re-
ceive one of the following four requests triggered by
the UE: normal FACH, normal DCH, attack FACH
and attack DCH request which trigger the promotion
transitions in the system. Namely, λ
i
denoting the rate
of normal and α
i
the rate of attack requests for state i,
where i ∈ {L, H}. We define the attack ratio parame-
ter k as
k =
α
L
λ
L
=
α
H
λ
H
, (1)
which gives the impact of the attack. State demo-
tion rates from normal states are denoted by δ
P
=
1
t
P
,
δ
L
=
1
t
FACH
+t
L
and δ
H
= δ
F
= δ
V
=
1
t
DCH
+t
H
, where
t
FACH
and t
DCH
represent the average duration of data
transmission in the respective states while t
P
is the
inactivity timeout period in CELL
PCH state. Tran-
sitions denoted by δ
F
and δ
V
represent the fast dor-
mancy mechanisms which were introduced in later
versions of UMTS standards.
During a signaling attack, the attacker usually
does not transmit any data because the purpose of
the attack is solely to trigger the signaling transi-
tions. Therefore, the demotion rates from the at-
tack states are selected as δ
LA
=
1
t
L
and δ
HA
= δ
FA
=
δ
VA
=
1
t
H
. Two specific cases are included when low-
bandwidth (FACH) requests are served in dedicated
SECRYPT2014-InternationalConferenceonSecurityandCryptography
208

channel states, represented by the transitions from H
to H
A
and vice-versa.
5 SYSTEM OPTIMISATION
The following section describes a probabilistic ap-
proach towards minimizing the impact of signaling at-
tacks on the system. Denoting the probability of state
i with P
i
we can describe the system model with the
following linear equations:
P
D
(λ
L
+ λ
H
+ α
L
+ α
H
) =
= P
P
δ
P
+ P
H
δ
V
+ P
HA
δ
VA
,
P
P
(λ
L
+ λ
H
+ α
L
+ α
H
+ δ
P
) =
= P
L
δ
L
+ P
H
δ
F
+ P
LA
δ
LA
+ P
HA
δ
FA
,
P
L
(λ
H
+ α
L
+ α
H
+ δ
L
) =
= (P
D
+ P
P
+ P
LA
)λ
L
+ P
H
δ
H
+ P
HA
δ
HA
,
P
H
(δ
V
+ δ
H
+ α
L
+ α
H
+ δ
F
) =
= (P
D
+ P
P
+ P
L
+ P
LA
)λ
H
+ P
HA
(λ
H
+ λ
L
),
P
LA
(λ
L
+ λ
H
+ α
H
+ δ
LA
) =
= (P
D
+ P
P
+ P
L
)α
L
,
P
HA
(λ
L
+ λ
H
+ δ
HA
+ δ
FA
+ δ
VA
) =
= (P
D
+ P
P
+ P
L
+ P
LA
)α
H
+ P
H
(α
L
+ α
H
).
(2)
The probabilities of each state can be found by
solving this system of equations with the normaliza-
tion condition
∑
i
P
i
= 1.
The goal of our optimisation will then be to min-
imise the time spent in the attack states, i.e. to min-
imise P
LA
and P
HA
and maximise the time spent in
normal states, and is reflected by the cost function C:
C =
P
LA
+ P
HA
P
L
+ P
H
(3)
which needs to be minimised.
To minimise C the influence of the following two
parameters is inspected:
• inactivity timers t
L
and t
H
;
• call setup delay in promotion transitions to FACH
and DCH, denoted with t
xL
and t
xH
respectively.
Changing the inactivity timers is fairly straight-
forward, while inserting delay in call setup should be
looked at from the system’s perspective.
Denote by θ
i
= λ
i
+ α
i
the total rate of requests
for state i seen by the system, where i ∈ {L, H}. The
average interval between requests is t
θ
i
=
1
θ
i
. We
insert a setup delay at transitions to state i and get
t
′
θ
i
= t
θ
i
+ t
xi
, where t
′
θ
i
is the new interval between
requests. Solving for the new arrival rates we get:
λ
′
i
=
λ
i
1+t
xi
λ
i
(k+ 1)
α
′
i
=
kα
i
k+ t
xi
α
i
(k+ 1)
(4)
which represent the “delayed” normal and attack rates
at state i.
The partial derivative of C(t
i
, t
xi
) with respect to
the inspected parameters does not lead to a closed
form solution. To find the numerical solution for the
problem we make the following assumptions:
• the arrival rates of normal requests are set to λ
L
=
λ
H
= 0.2 [req/sec], as a typical value in real-world
networks (Inc., 2013);
• the average duration of data transmission in
FACH and DCH states is t
FACH
= t
DCH
= 1.28sec
which is calculated as the time to transmit an aver-
age 320 KB web page in DCH channel at 2 Mbps
(Ramachandran, 2010) or 512 B (upper limit of
FACH data size) of background data at 3.2 kbps
in FACH channel;
• the inactivity timers are set to t
P
= 20min, t
L
=
4sec and t
H
= 6sec as usually used values by mo-
bile operators;
• the attack ratio is set to k = 1. Note that k is only
a measure of attack strength, and as so it does not
influence the form of C, only its amplitude.
We also assume that the fast dormancy mechanism
is not implemented (δ
F
= δ
V
= δ
FA
= δ
VA
= 0) and
we inspect the system under both FACH and DCH
attacks. The next section presents and discusses the
obtained results.
6 RESULTS AND DISCUSSION
First, we investigate the influence of inactivity timers
in FACH and DCH states on the security of the sys-
tem. Three scenarios are inspected for both FACH
and DCH types of attacks: t
L
and t
H
are changed to-
gether; the timer in DCH is fixed to 6s and we change
the timer in FACH; the timer in FACH is fixed to 4s
and we change the timer in DCH only. Then we insert
delay t
xL
and t
xH
in setup rates and inspect three simi-
lar scenarios: inserting delay in both FACH and DCH
requests; inserting delay only in FACH requests; and
inserting delay only in DCH requests.
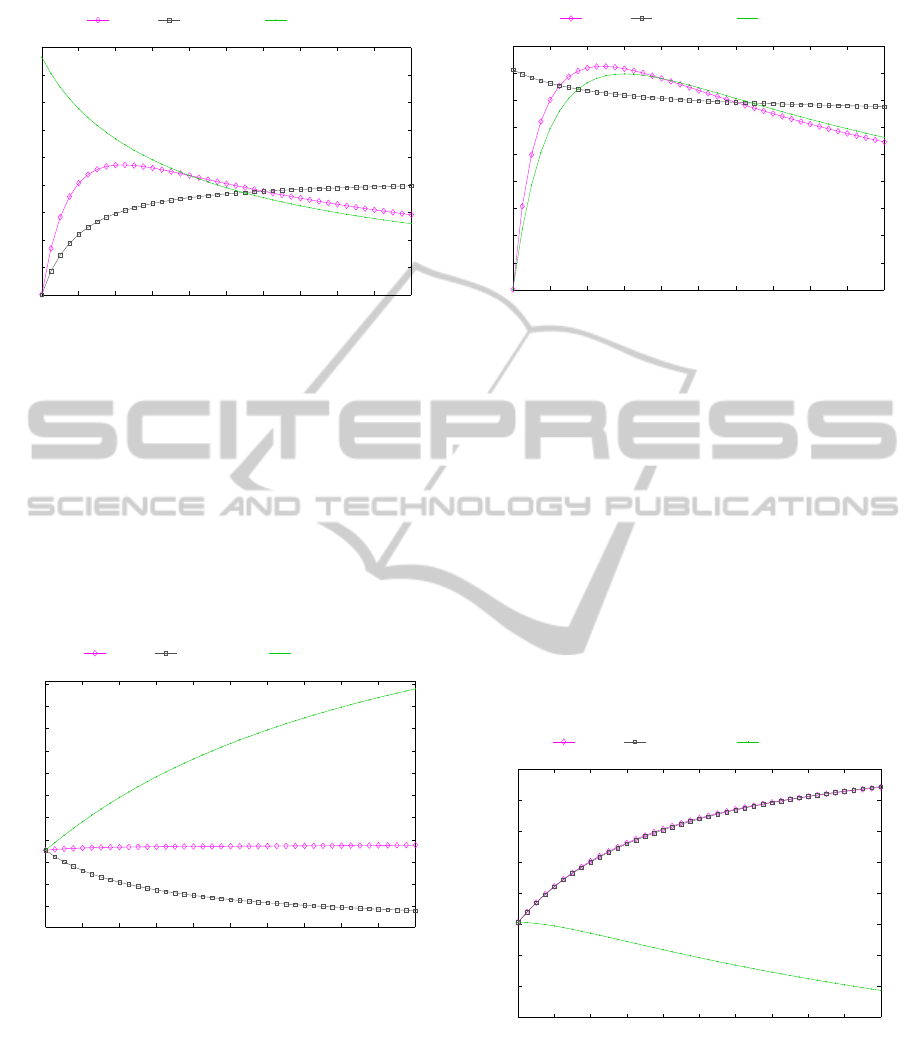
Figure 2 depicts the three scenarios of inactivity
timers in a system under FACH attack. For fixed
t
L
= 4sec the cost function decreases with the increase
of t
H
. This simply shows that the longer the system
stays in H state the lower the probability of attack
on FACH state. For fixed t
H
= 6sec the cost func-
tion increases with the increase of t
L
meaning that the
SignalingAttacksinMobileTelephony
209
0 1 2 3 4 5 6 7 8 9 10
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
0.4
0.45
Inactivity timer at state i [s]
C
i=L,H
i=L, t
H
=6s i=H, t
L
=4s
Figure 2: C as a function of inactivity timeout period at state
i for FACH attacks.
quicker the system returns to normal state, the lower
probability of attack. The cost function for changing
both t
L
and t
H
together rises to a certain point after
which it starts to decline. Of course, the cost function
has a minimum at t
L
= t
H
= 0 but selecting low values
for the timeout periods would mean larger number of
transitions (attacks) although the time spent in attack-
ing states is minimised. Therefore a better choice is
selecting higher values for the two timers.
0 1 2 3 4 5 6 7 8 9 10
0.05
0.1
0.15
0.2
0.25
0.3
0.35
0.4
0.45
0.5
0.55
Setup delay at state i [s]
C
i=L,H
i=L, t
xH
=0s i=H, t
xL
=0s
Figure 3: C as a function of setup delay at state i for FACH
attacks.
Figure 3 shows the influence of inserting delay in
state promotion transitions in system under FACH at-
tack. Setting t
xH
= 0 and increasing t
xL
is a good
choice for lowering the attack. In contrast to that, in-
creasing the delay of DCH requests while an attack
is ongoing on FACH state sharply increases the prob-
ability of attack states. Increasing the delay in both
FACH and DCH requests at the same time does not
introduce any improvements.
In case of DCH attacks, Figure 4 suggests that in-
0 1 2 3 4 5 6 7 8 9 10
0
0.02
0.04
0.06
0.08
0.1
0.12
0.14
0.16
0.18
Inactivity timer at state i [s]
C
i=L,H
i=L, t
H
=6s i=H, t
L
=4s
Figure 4: C as a function of inactivity timeout period at state
i for DCH attacks.
creasing the inactivity timeout in FACH state t
L
intro-
duces small improvements, analogous to the case of
increasing the DCH timer for FACH attack. Chang-
ing both timers at the same time is similar to the case
of changing t
L
and t
H
timers together under FACH
attack (Figure 2) - the cost function has a minimum
value for t
H
= 0 but selecting higher values for t
H
is a
safer choice. Although we would expect constant in-
crease in C with the increase of t
H
when t
L
is fixed to
4s, C drops after a certain point. This is due to normal
FACH requests being served in high bandwidth chan-
nels, thus the transition H
A
to H being more probable
than H to H
A
.
0 1 2 3 4 5 6 7 8 9 10
0.08
0.1
0.12
0.14
0.16
0.18
0.2
0.22
0.24
Setup delay at state i [s]
C
i=L,H
i=L, t
xH
=0s i=H, t
xL
=0s
Figure 5: C as a function of setup delay at state i for DCH
attacks.
Finally, Figure 5 depicts the case of inserting de-
lay in promotion transitions in a system under DCH
attack. Analog to the case of FACH attack, insert-
ing delay in DCH requests in this case lowers the cost
function. Inserting delay in FACH requests increases
the probability of attack states, same as inserting de-
SECRYPT2014-InternationalConferenceonSecurityandCryptography
210

lay at FACH and DCH requests at the same time. The
increase in C at this case is a result of lowering the
probability of L state which is in the denominator of
function C.
In general, the cost function for changing the inac-
tivity timer of FACH state under FACH attack or the
inactivity timer of DCH state under DCH attack has a
minimum at t
L
= 0 and t
H
= 0 respectively. This re-
sult is correct by means of lowering the probability of
attack state. Anyway, selecting small timers in both
cases means larger number of transitions, i.e. larger
number of attacks. In case of FACH attack, setting
the inactivity timer of DCH state to higher values is
a good choice. Similarly, selecting higher values for
the inactivity timer in FACH state slightly improves
the security of the system under DCH attack. Adding
delay in setup transitions for FACH state in a system
under FACH attack, or setup transitions for DCH state
in a system under DCH attack provides good results
by lowering the probability of attack states. The other
cases of adding delay in setup transitions have nega-
tive influence.
7 CONCLUSION
The increasing use of smartphone applications has
created new security issues for mobile cellular net-
works. In order to provide better user experience and
real-time services, mobile applications are usually de-
veloped assuming they have an “always on” connec-
tivity to the Internet. However mobile networks such
as UMTS are originally designed for voice calls and
browsing type of data traffic, and do not provide a
continuous access to the network. Connections are
created and teared down dynamically by demand.
This “creation and tear down” characteristic, which is
also meant to save bandwidthcapacity for the network
as a whole, introduces some interesting liabilities that
can be easily exploited for signaling attacks.
In this paper we have analysed the influence of pa-
rameters such as the inactivity timeouts and call setup
delay on the impact of signaling attacks in UMTS
networks. We proposed a model of UMTS Radio
Resource Control mechanism under attack and de-
fined a cost function based on the probability of at-
tack states in the model. Results show that in system
under FACH/DCH attack it is a good choice to extend
the duration of inactivity timers and to add delay in
requests for the corresponding states.
Future work may include optimising the system in
terms of transitions’ probability, analysis in a simu-
lation environment as well as obtaining new mecha-
nisms for mitigation of attacks. It would also be of
interest to evaluate how such signaling attacks may
actually affect a realistic security setting, for instance
when spectators at a sports or cultural venue have
to be evacuated rapidly with the help of instructions
distributed through smartphones because of an emer-
gency (Filippoupolitis and Gelenbe, 2009; Dimakis
et al., 2010; G¨orbil and Gelenbe, 2013) and a signal-
ing attack is simultaneously launched by malicious in-
dividuals who wish to further disrupt the emergency
situation.
REFERENCES
3GPP (June 2002). Utran functions, examples on signaling
procedures (release 1999). TR 25.931 v3.7.0.
Abdelrahman, O. H. and Gelenbe, E. (2014). Signalling
storms in 3G mobile networks. In IEEE International
Conference on Communications (ICC’14), Communi-
cation and Information Systems Security Symposium,
Sydney, Australia. Accepted for publication.
Cao, Y. and Gelenbe, E. (1998). Autonomous search for
mines. European Journal of Operational Research,
108(2):319–333.
Choi, Y., Yoon, C.-h., Kim, Y.-s., Heo, S., and Silvester, J.
(2014). The impact of application signaling traffic on
public land mobile networks. Communications Mag-
azine, IEEE, 52(1):166–172.
Dimakis, N., Filippoupolitis, A., and Gelenbe, E. (2010).
Distributed building evacuation simulator for smart
emergency management. Comput. J., 53(9):1384–
1400.
Filippoupolitis, A. and Gelenbe, E. (2009). A distributed
decision support system for building evacuation. In
Human System Interactions, 2009. HSI’09. 2nd Con-
ference on, pages 323–330.
Gelenbe, E. (1979). Probabilistic models of computer sys-
tems. Acta Inf., 12:285–303.
Gelenbe, E., Gorbil, G., Tzovaras, D., Liebergeld, S., Gar-
cia, D., Baltatu, M., and Lyberopoulos, G. (2013a).
Security for smart mobile networks: The NEMESYS
approach. In Proceedings of the 2013 IEEE Global
High Tech Congress on Electronics (GHTCE’13).
Gelenbe, E., G¨orbil, G., Tzovaras, D., Liebergeld, S., Gar-
cia, D., Baltatu, M., and Lyberopoulos, G. L. (2013b).
Nemesys: Enhanced network security for seamless
service provisioning in the smart mobile ecosystem.
In Gelenbe, E. and Lent, R., editors, ISCIS, volume
264 of Lecture Notes in Electrical Engineering, pages
369–378. Springer.
Gelenbe, E. and Loukas, G. (2007). A self-aware approach
to denial of service defence. Computer Networks,
51(5):1299–1314.
Gelenbe, E., Schmajuk, N., Staddon, J., and Reif, J. (1997).
Autonomous search by robots and animals: A survey.
Robotics and Autonomous Systems, 22(1):23–34.
Gelenbe, E. and Wu, F.-J. (2012). Large scale simulation for
SignalingAttacksinMobileTelephony
211

human evacuation and rescue. Computers & Mathe-
matics with Applications, 64(12):3869–3880.
G¨orbil, G. and Gelenbe, E. (2013). Disruption tolerant com-
munications for large scale emergency evacuation. In
PerCom Workshops, pages 540–546. IEEE.
GSMA, S. A. P. (Apr 2012). Smart apps for smarter phones.
Gupta, M., Jha, S., Koc, A., and Vannithamby, R. (2013).
Energy impact of emerging mobile internet applica-
tions on lte networks: issues and solutions. Commu-
nications Magazine, IEEE, 51(2):90–97.
Inc., S. (2013). Charting the signaling storms.
Kambourakis, G., Kolias, C., Gritzalis, S., and Park, J. H.
(2011). Dos attacks exploiting signaling in umts and
ims. Comput. Commun., 34(3):226–235.
Korhonen, J. (2003). Introduction to 3g mobile communi-
cations.
Lee, P., Bu, T., and Woo, T. (2007). On the detection of sig-
naling dos attacks on 3g wireless networks. In INFO-
COM 2007. 26th IEEE International Conference on
Computer Communications. IEEE, pages 1289–1297.
Marck, P. (2013). Iab - focus on mobile.
Ramachandran, S. (2010). Web metrics: Size and number
of resources.
Ricciato, F., Coluccia, A., and DAlconzo, A. (2010). A
review of dos attack models for 3g cellular networks
from a system-design perspective. Computer Commu-
nications, 33(5):551 – 558.
Wang, H., Zhang, D., and Shin, K. (2004). Change-point
monitoring for the detection of dos attacks. Depend-
able and Secure Computing, IEEE Transactions on,
1(4):193–208.
Wireless, R. (2012). Docomo demands google’s help with
signalling storm.
Wu, Z., Zhou, X., and Yang, F. (2010). Defending against
dos attacks on 3g cellular networks via randomization
method. In Educational and Information Technology
(ICEIT), 2010 International Conference on, volume 1,
pages V1–504–V1–508.
Yu, C.-M., Ni, G.-K., Chen, I.-Y., Gelenbe, E., and Kuo,
S.-Y. (2014). Top-k query result completeness verifi-
cation in tiered sensor networks. IEEE Transactions
on Information Forensics and Security, 9(1):109–124.
SECRYPT2014-InternationalConferenceonSecurityandCryptography
212
