
A Secure Anonymous Proxy Multi-signature Scheme
Vishal Saraswat and Rajeev Anand Sahu
C.R.Rao Advanced Institute of Mathematics Statistics and Computer Science
Hyderabad, India
Keywords:
Identity-based Cryptography, Bilinear Map, CDHP, Provable Security, Digital Signature, Signing Rights
Delegation, Proxy Multi-signature, Anonymity, Accountability.
Abstract:
A proxy signature scheme enables a signer to delegate its signing rights to any other user, called the proxy
signer, to produce a signature on its behalf. In a proxy multi-signature scheme, the proxy signer can produce
one single signature on behalf of multiple original signers. We propose an efficient and provably secure
threshold-anonymous identity-based proxy multi-signature (IBPMS) scheme which provides anonymity to the
proxy signer while also providing a threshold mechanism to the original signers to expose the identity of the
proxy signer in case of misuse. The proposed scheme is proved secure against adaptive chosen-message and
adaptive chosen-ID attacks under the computational Diffie-Hellman assumption. We compare our scheme with
the recently proposed anonymous proxy multi-signature scheme and other ID-based proxy multi-signature
schemes, and show that our scheme requires significantly less operation time in the practical implementation
and thus it is more efficient in computation than the existing schemes.
1 INTRODUCTION
Digital signature is a cryptographic primitive to guar-
antee data integrity, entity authentication and signer’s
non-repudiation. A proxy signature scheme enables
a signer, O, also called the designator or delegator,
to delegate its signing rights (without transferring the
private key) to another user P , called the proxy signer,
to produce, on the delegator’s behalf, signatures that
can be verified by a verifier V under the delegator O’s
public key. For example, the director of a company
may authorize the deputy director to sign certain mes-
sages on his behalf during a certain period of his ab-
sence.
Proxy multi-signature is a proxy signature prim-
itive which enables a group of original signers
O
1
,...,O
n
to transfer their signing rights to a proxy
signer P who can produce one single signature which
convinces the verifier V of the concurrence of all the
original signers. Threshold anonymous proxy multi-
signature provides anonymity to the proxy signer
while also providing a (t,n)-threshold mechanism to
the original signers to expose the identity of the proxy
signer in case of misuse. The proxy identification al-
gorithm in the standard proxy signature protocol is
replaced by a proxy exposure protocol where any t (or
more) out of n original signers can come together to
expose the identity of the proxy signer. Note that the
threshold anonymous proxy multi-signature is differ-
ent from threshold proxy signatures in the sense that
while in threshold proxy signatures, any t (or more)
out of n proxy signers must come together to pro-
duce a valid signature, in threshold anonymous proxy
multi-signature any t (or more) out of n original sign-
ers must come together to revoke the anonymity of the
proxy signer.
Consider the following example in a secure multi-
party computation setting, multiple parties O
1
,...,O
n
start a process P after authenticating themselves.
Once the process P is started, the parties do not need
to stay connected while the process P may remain ac-
tive and need access to additional resources that re-
quire further authentication. The parties thus delegate
their rights to the process P and the resources allow
access to P as long as the resources can verify that
P was indeed authorised by the original parties. The
resources do not need to know the ‘identity’ of the
process at all and P may remain anonymous to them.
In fact, most of the times the resources do not even
need to know whether it is actually the set of origi-
nal parties who were authenticated or their proxy P .
But in case of a malicious process, the original parties
should be able to expose the process and restrict any
further activities by it on their behalf.
55
Saraswat V. and Sahu R..
A Secure Anonymous Proxy Multi-signature Scheme.
DOI: 10.5220/0005021200550066
In Proceedings of the 11th International Conference on Security and Cryptography (SECRYPT-2014), pages 55-66
ISBN: 978-989-758-045-1
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

1.1 Related Work
The notion of proxy signature has been around since
1989 (Gasser et al., 1989) but it took almost seven
years for the first construction (Mambo et al., 1996)
of a proxy signature scheme to be proposed. Since
then many variants of the proxy signature have been
proposed and many extensions of the basic proxy sig-
nature primitive have been studied. The formal se-
curity model of proxy signatures was first formalized
in (Boldyreva et al., 2003) and further strengthened
and extended to the identity-based setting in (Schuldt
et al., 2008). A formal security model for anonymous
proxy signatures was introduced relatively recently
in (Fuchsbauer and Pointcheval, 2008) by unifying
the notions of proxy signatures and group signatures.
The notion of proxy-anonymous proxy signatures
was introduced in (Shum and Wei, 2002). Their
scheme was based on the proxy signature scheme
of (Lee et al., 2001) which was shown insecure
in (Sun and Hsieh, 2003). The anonymization tech-
nique itself was shown to cause insecurity – (Lee and
Lee, 2005) showed that the original signer can gener-
ate valid proxy signatures, thus violating the property
of the strong unforgeability.
Many proxy signature schemes have since been
proposed with the aim of providing anonymity of
the proxy signers — (Yu et al., 2009; Toluee et al.,
2012) provide proxy-anonymity by having a large
“ring” of proxy-signers; (Wu et al., 2008; Fuchs-
bauer and Pointcheval, 2008) require a large “group”
of proxy signers with one or more group managers
to revoke the anonymity of a malicious proxy-signer;
and (Lee et al., 2005; Du and Wang, 2013) require
a trusted third-party or trusted authority or trusted
dealer to provide the required functionality. In the
ring-based and group-based settings, the proxy signa-
ture schemes require that the number of proxy sign-
ers authorized by the original signer is large enough
to provide sufficient anonymity to the proxy signer.
The cost (time, space, etc.) of providing anonymity
is rather large and the anonymity is not even absolute
but only 1-out-of-n where n is the size of group or
ring. The trusted third-party setting has its fair share
of well-known issues including the requirement of an
absolutely trustworthy authority/ dealer who is always
available.
The recently proposed scheme of (Du and Wang,
2013) is most notable in its attempt but it comes with
several flaws. First and foremost, their implementa-
tion of the anonymization technique is not correct and
because of that the signature verification cannot be
done. In particular their proxy key generation is not
consistent — they are adding a group element with
scalar elements (integers). Thus their scheme is not
consistent and is in fact incorrect. Second, it is not
even a proxy multi-signature scheme but is just a con-
catenation of n proxy signature schemes, where n is
the number of original signers, since each original
signer in the scheme issues a warrant with a differ-
ent pseudonym: Q
pseu
i
= R
O
+ R
P
i
+ Q
P
. Third, each
original signer O
i
can reveal the identity of the proxy
signer P and even try to (partially) “demonstrate” by
using the signature of the proxy. Fourth, during the
proxy multi-signature verification PMSVeri, it is re-
quired that the verifier “checks whether or not the
proxy signer P is authorized by the n original sign-
ers O
1
,...,O
n
in the warrant w”. Nevertheless, if the
verifier can already check the authority of the proxy
signer P then P never remains anonymous! Fifth,
the dealer D of the secret sharing scheme used by the
original signers also knows the identity of P and can
also compute R
P
i
from the R
O
(which he computes
himself) and publicly available values Q
P
and Q
pseu
.
Finally, the scheme of (Du and Wang, 2013) is based
on the proxy multi-signature scheme of (Cao and Cao,
2009) which can be shown to be insecure (Xiong
et al., 2011) when n = 1.
1.2 Our Contribution
To the best of our knowledge, almost all available
proxy-anonymous signature schemes are either too
costly or inefficient to be practical or have not been
proved secure. We propose an efficient and provably
secure threshold-anonymous ID-based proxy multi-
signature scheme which provides anonymity to the
proxy signer while also providing a threshold mech-
anism to the original signers to expose the identity
of the proxy signer in case of misuse. The proposed
scheme is proved secure against adaptive chosen-
message and adaptive chosen-ID attacks under the
computational Diffie-Hellman (CDH) assumption.
In this paper, we build our scheme on the tech-
nique of pseudonym and secret sharing as suggested
by (Du and Wang, 2013) to provide the required func-
tionality – the identity of the proxy signer is hidden
but in case of misuse of the delegated rights, t or more
of the n original signers can come together to reveal
the proxy signer’s identity.
In our scheme we modify the structure of the war-
rant slightly. As in usual proxy signature schemes,
the warrant in our scheme includes the nature of mes-
sage to be delegated, period of delegation, identity in-
formation of original signers, etc. But unlike usual
proxy signature schemes, it does not include the iden-
tity information of the proxy signer. Instead, the war-
rant includes the proxy signer’s pseudonym, which
SECRYPT2014-InternationalConferenceonSecurityandCryptography
56

is a proxy signature verification key that cannot be
linked to the identity of the proxy signer easily — t
or more original signers must come together to reveal
the proxy signer’s identity.
Compared with the scheme of (Du and Wang,
2013), our scheme allows the proxy signer to act as
the dealer of the secret sharing scheme and uses a
verifiable secret sharing scheme (Pedersen, 1991) to
restrict the proxy from acting as a malicious dealer.
Our scheme requires only 2n broadcasts compared to
3n + 1 of Du’s scheme to construct the pseudonym
of the proxy and thus our scheme requires 33% less
broadcasts to provide anonymity. Also we use a
much more efficient and provably secure proxy multi-
signature scheme of (Sahu and Padhye, 2012) as our
basic scheme so that the overall proxy signature has
less operation time and thus more efficient (14%-23%
more) than the existing best schemes in computation.
1.3 Outline of the Paper
The rest of this paper is organized as follows. In
Section 2, we introduce some related mathematical
definitions, problems and assumptions. In Section 3,
we present the formal definition of an anonymous
ID-based proxy multi-signature scheme and a secu-
rity model for it. Our proposed anonymous ID-based
proxy multi-signature scheme is presented in Sec-
tion 4. In Section 5 we analyze the security of our
scheme. Finally, Section 6 includes the efficiency
comparison.
2 PRELIMINARIES
In this section, we introduce some relevant defini-
tions, mathematical problems and assumptions and
briefly discuss the verifiable secret sharing scheme.
2.1 Bilinear Map
Let G
1
be an additive cyclic group with generator P
and G
2
be a multiplicative cyclic group with generator
g. Let the both groups are of the same prime order q.
Then a map e : G
1
×G
1
→ G
2
satisfying the following
properties, is called a cryptographic bilinear map:
1. Bilinearity: For all a, b ∈ Z
∗
q
, e(aP,bP) =
e(P,P)
ab
, or equivalently, for all Q,R,S ∈ G
1
,
e(Q + R,S) = e(Q,S)e(R,S) and e(Q, R + S) =
e(Q,R)e(Q,S).
2. Non-Degeneracy: There exists Q,R ∈ G
1
such
that e(Q,R) 6= 1. Note that since G
1
and G
2
are
groups of prime order, this condition is equivalent
to the condition e(P,P) 6= 1, which again is equiv-
alent to the condition that e(P, P) is a generator of
G
2
.
3. Computability: There exists an efficient algorithm
to compute e(Q,R) ∈ G
2
, for any Q,R ∈ G
1
.
2.2 Discrete log (DL) Assumption
Let G
1
be a cyclic group with generator P.
Definition 1. Given a random element Q ∈ G
1
, the
discrete log problem (DLP) in G
1
is to compute an
integer n ∈ Z
∗
q
such that Q = nP.
Definition 2. The DL assumption on G
1
states that
the probability of any polynomial-time algorithm to
solve the DL problem in G
1
is negligible.
2.3 Computational Diffie-Hellman
(CDH) Assumption
Let G
1
be a cyclic group with generator P.
Definition 3. Let a, b ∈ Z
∗
q
be randomly chosen and
kept secret. Given P,aP, bP ∈ G
1
, the computational
Diffie-Hellman problem (CDHP) is to compute abP ∈
G
1
.
Definition 4. The (t,ε)-CDH assumption holds in
G
1
if there is no algorithm which takes at most t run-
ning time and can solve CDHP with at least a non-
negligible advantage ε.
2.4 Verifiable Secret Sharing
The notion of secret sharing was introduced indepen-
dently by (Shamir, 1979) and (Blakley, 1979) to en-
able a secret to be shared among a group of users so
that the secret can be reconstructed only when a suf-
ficient number of them come together. For integers
n and t such that 1 < t ≤ n, an (t,n)-secret sharing
scheme consists of two phases:
1. in the splitting phase, a dealer shares a secret σ
among n users;
2. in the combining phase, only t or more users in
the group can reconstruct the secret σ.
Verifiable secret sharing (VSS), introduced in (Chor
et al., 1985), enables each user to verify the correct-
ness of their shares to prevent malicious attack per-
formed by the dealers. For the purpose of this pa-
per, we use Pedersen’s non-interactive and informa-
tion theoretic secure VSS (Pedersen, 1991). This
scheme protects the secret to be distributed uncondi-
tionally for any value of t, (1 < t ≤ n), and the cor-
rectness of the shares depends on the assumption that
the dealer cannot find discrete logarithms before the
distribution has been completed.
ASecureAnonymousProxyMulti-signatureScheme
57

3 ANONYMOUS ID-BASED
PROXY MULTI-SIGNATURE
SCHEME AND ITS SECURITY
MODEL
Here we give a formal definition of an anonymous
ID-based proxy multi-signature scheme and a formal
security model for it as presented in (Cao and Cao,
2009; Sahu and Padhye, 2012) built upon the work
of (Boldyreva et al., 2003) and (Schuldt et al., 2008).
3.1 Anonymous ID-based Proxy
Multi-Signature Scheme
In a (t,n)-threshold anonymous ID-based proxy
multi-signature scheme, group of n original signers
are authorized to transfer their signing rights to a sin-
gle proxy signer to sign any document anonymously
on their behalf but in case of misuse of the delegated
rights by the proxy signer, t or more of the original
signers can come together to reveal and demonstrate
the identity of the proxy signer. Public and private
keys of original and proxy signers are generated by a
Private Key Generator (PKG), using their correspond-
ing identities. Let the n original signers O
i
have the
identities ID
O
i
, i = 1,.. .,n, and the proxy signer P
has the identity ID
P
. A (t, n)-threshold anonymous
ID-based proxy multi-signature scheme can be de-
fined consisting the following:
Setup: For a security parameter k, the PKG runs
this algorithm and generates the public parameters
params and a master secret of the system. Further,
the PKG publishes params and keeps the master se-
cret confidential.
Extract: This is a private key generation algorithm.
For a given identity ID, public parameters params
and master secret, PKG runs this algorithm to gen-
erate private key S
ID
of the user with identity ID, and
provides this private key through a secure channel to
the user corresponding to the identity ID.
Proxy multi-generation: This is an interactive pro-
tocol among the original signers and the proxy signer.
In this phase, the group of original signers interact
with the proxy signer to agree on a pseudonym to
anonymize the identity of the proxy signer and a war-
rant w which includes the nature of message to be del-
egated, period of delegation, identity information of
original signers, the pseudonym for the proxy signer
etc. Finally the original signers delegate their sign-
ing rights to the proxy signer and the proxy signer
produces the (secret) proxy signing key. This algo-
rithm takes as input, the identities ID
O
i
,ID
P
and pri-
vate keys S
ID
O
i
,S
ID
P
of all the users and outputs the
pseudonym Q
ID
Q
, the warrant w, the shares ρ
O
i
of the
original signers, the delegation V
O
i
, i = 1,. .., n, and
the proxy signing key S
P
.
Proxy multi-signature: This is a randomized algo-
rithm, the proxy signer runs this algorithm to gener-
ate a proxy multi-signature on an intended message
m. This algorithm takes proxy signing key of the
proxy signer, the warrant w, message m and outputs
the proxy multi-signature σ
P
.
Proxy multi-verification: This is a deterministic
algorithm run by the verifier on receiving a proxy
multi-signature σ
P
on any message m. This algorithm
takes as inputs the proxy multi-signature σ
P
, the mes-
sage m, the warrant w, the identities ID
O
i
of all the
original signers, Q
ID
Q
and outputs 1 if the signature
σ
P
is a valid proxy multi-signature on behalf of the
group of original signers on m, and outputs 0 other-
wise. We emphasize that the actual identity ID
P
of
the proxy signer is not required but the pseudonym
Q
ID
Q
, as in the warrant, is required for the verifica-
tion.
Reveal & Demonstrate: To reveal and demonstrate
the proxy signer’s identity, t or more original signers
combine their shares ρ
O
i
to recover the shared secret
ρ
O
and proceed to reveal the proxy signer’s identity
from the pseudonym.
3.2 Security Model for Anonymous
ID-based Proxy Multi-Signature
Schemes
3.2.1 Unforgeability
In this model we consider a case where an adver-
sary A tries to forge the proxy multi-signature work-
ing against a single user, once against an original
signer say O
i
and once against the proxy signer P .
We consider that ID
O
i
(i = 1,...,n) denotes iden-
tities of the original signers and ID
P
denotes iden-
tity of the proxy signer. The adversary A is allowed
to access polynomial number of hash queries, ex-
traction queries, proxy multi-generation queries and
proxy multi-signature queries. The goal of the adver-
sary A is to produce one of the following forgeries:
SECRYPT2014-InternationalConferenceonSecurityandCryptography
58

1. A proxy multi-signature for a message m by user
1 on behalf of the original signers, such that either
the original signers never designated user 1, or the
message m was not submitted in the proxy multi-
signature queries.
2. A proxy multi-signature for a message m by some
user i (i 6= 1) on behalf of the original signers, such
that user i was never designated by the original
signers, and user 1 is one of the original signers.
An ID-based proxy multi-signature scheme is said
to be existential unforgeable against adaptive chosen-
message and adaptive chosen-ID attack if there is
no probabilistic polynomial time adversary A with a
non-negligible advantage against the challenger C in
the following game:
1. Setup: Challenger C runs the Setup algorithm and
provides the public parameters params to the ad-
versary A.
2. Extract query: When the adversary A asks private
key of any user with identity ID
i
, the challenger
runs the Extract algorithm and responds the pri-
vate keys to the adversary.
3. Proxy multi-generation query: When the adver-
sary A requests to interact with the user 1 for
the proxy signing key by proxy multi-generation
query on the warrant w
0
and identities ID
i
of its
choice where the user 1 may be either one of the
original signers or the proxy signer, the challenger
C runs the proxy multi-generation algorithm to re-
spond the proxy signing key to the adversary and
maintains corresponding lists.
4. Proxy multi-signature query: Proceeding adap-
tively when the adversary A requests for a proxy
multi-signature on message m
0
and warrant w
0
of
its choice, C responds by running the proxy multi-
signature algorithm and maintains a query list say
L
pms
for it.
5. Output: After the series of queries, A outputs a
new proxy multi-signature (U
P
,σ
P
,U, w) on mes-
sage m under a warrant w for identities ID
O
i
and
ID
P
. Where A has never requested private keys
for ID
O
i
and ID
P
in extraction queries. A has
never requested a Proxy multi-generation query
including warrant w and identities ID
O
i
. A has
never requested a proxy multi-signature query on
message m with warrant w and identity ID
P
.
The adversary A wins the above game if the
new ID-based proxy multi-signature (U
P
,σ
P
,U, w)
on message m is valid.
Definition 5. An ID-based proxy multi-signature
forger A (t,q
H
,q
E
,q
pmg
,q
pms
,n+1,ε)-breaks the n +
1 users ID-based proxy multi-signature scheme by the
adaptive chosen-message and adaptive chosen-ID at-
tack, if A runs in at most t time; makes at most q
H
hash queries; at most q
E
extraction queries; at most
q
pmg
proxy multi-generation queries; at most q
pms
proxy multi-signature queries; and the success proba-
bility of A is at least ε.
Definition 6. An ID-based proxy multi-signature
scheme is (t,q
H
,q
E
,q
pmg
,q
pms
,n + 1,ε)-
secure against adaptive chosen-message and
adaptive chosen-ID attacks, if no adversary
(t,q
H
,q
E
,q
pmg
,q
pms
,n + 1, ε)-breaks it.
3.2.2 Anonymity and Accountability
Definition 7 (Anonymity). By anonymity we mean
that no one except the original signers should be able
to determine the identity of the proxy signer from the
proxy signatures or the warrant.
Definition 8 (Threshold Anonymity). By (t,n)-
threshold anonymity we mean that even the original
signers O
i
who know the identity of the proxy signer
P should not be able to prove that P is the signer of a
certain proxy multi-signature unless at least t of the n
original signers participate in the proof.
Definition 9 (Accountability). Accountability en-
sures that the proxy signer P does not abuse its
anonymity. Any t (or more) out of n original sign-
ers can come together to prove that P is the signer of
any verifiable designated proxy multi-signature.
Remark: Note that each of the original signers al-
ways know the identity of the proxy signer P since
they delegate their rights to P . Our definitions re-
quire that any group of less than t original signers is
not able to prove to a third party that P is indeed the
proxy signer.
4 PROPOSED SCHEME
In this section, we present our efficient and provably
secure threshold-anonymous identity-based proxy
multi-signature (IBPMS) scheme which provides
anonymity to the proxy signer while also providing a
threshold mechanism to the original signers to expose
the identity of the proxy signer in case of misuse. Our
scheme consists of the following phases: setup, ex-
tract, proxy multi-generation, proxy multi-signature,
proxy multi-verification, reveal & demonstration.
The scheme uses the following signature scheme
which was proved to be secure in (Sahu and Padhye,
2012) (with Setup and Extract as defined below in the
definition of the threshold anonymous proxy multi-
signature):
ASecureAnonymousProxyMulti-signatureScheme
59

Signature: To sign a message m ∈ {0,1}
∗
,
• randomly selects r ∈ Z
∗
q
,
• computes U = rP ∈ G
1
,
• h = H
2
(mkU) and
• V = hS
ID
+ rPub.
The signature on message m is σ = hU,V i.
Verification: To verify a signature σ = hU,V i on
message m for an identity ID, the verifier first com-
putes
• Q
ID
= H
1
(ID), and
• h = H
2
(mkU).
Then accepts the signature if
e(P,V ) = e(Pub, hQ
ID
+U),
and rejects otherwise.
4.1 Our Anonymous IBPMS Scheme
Setup: For a given security parameter 1
k
, let G
1
be
an additive cyclic group of prime order q with gener-
ator P and G
2
be a multiplicative cyclic group of the
same prime order q. Let e : G
1
×G
1
→ G
2
be a crypto-
graphic bilinear map as defined above. Let H
1
and H
2
are two hash functions defined for security purpose as
H
1
: {0,1}
∗
→ G
1
and H
2
: {0,1}
∗
→ Z
∗
q
. The PKG
randomly selects s ∈ Z
∗
q
and sets Pub = sP as public
value. Finally, the PKG publishes system’s public pa-
rameter params = hk,e,q,G
1
,G
2
,H
1
,H
2
,P,Pubi and
keeps the master secret s confidential to itself only.
Extract: Given a user’s identity ID, the PKG com-
putes its
• public key as: Q
ID
= H
1
(ID) and
• private key as: S
ID
= sQ
ID
respectively.
Proxy multi-generation: To delegate the signing
capability to the proxy signer P , the n original sign-
ers do the following jobs to make a signed warrant w.
The warrant includes the nature of message to be del-
egated, period of delegation, identity information of
original signers, the pseudonym for the proxy signer
etc. In successfully completion of the protocol, proxy
signer gets a proxy signing key S
P
.
Delegation generation: (a) Pseudonym generation:
Each original signer with identity ID
O
i
selects
a random number ρ
O
i
∈ Z
∗
q
and sends it to the
proxy signer P in a secure channel. P computes
ρ
O
= ρ
O
1
+ρ
O
2
+··· + ρ
O
n
∈ Z
∗
q
and uses a (t,n)-
threshold verifiable secret sharing scheme (Ped-
ersen, 1991) to split ρ
O
into n shares ρ
s
i
, i =
1,2,...,n. P then sets R
O
= ρ
O
P and sends
R
O
,ρ
s
i
to the corresponding original signer O
i
for i = 1,2, ... ,n through a secure channel. P
also selects a random number ρ
P
∈ Z
∗
q
, computes
R
P
= ρ
P
P and its standard signature s
R
P
. Finally
P sends R
P
,s
R
P
to all the n original signers O
i
for i = 1,2,. .., n through a secure channel. Each
original signer computes Q
ID
Q
= Q
ID
P
+R
P
+R
O
as the proxy signer’s pseudonym, which will be
included in the warrant and will be used as the
signature verification key.
Remark: Note that all the n original signers can
come together with the ρ
O
i
that they sent to P and
compute ρ
O
= ρ
O
1
+ρ
O
2
+·· ·+ρ
O
n
to expose the
identity of the proxy signer in case of misuse. We
are using a threshold secret sharing scheme to pro-
vide a threshold mechanism to the original signers
so that only t ≤ n of the original signers are suf-
ficient to participate to expose the identity of the
proxy signer. Also note that we use a verifiable
secret sharing scheme so that a malicious proxy
signer cannot mislead the original signers with an
incorrect ρ
s
i
to avoid being held responsible for its
proxy-signatures. The original signers can verify
their shares as soon as they receive it and are as-
sured that the ρ
s
i
they receive will correctly con-
struct to ρ
O
corresponding to the R
O
which they
receive. Also, P ’s signature is required for non-
repudiation.
(b) Delegation generation: For i = 1, ... ,n, each
O
i
• selects r
i
∈ Z
∗
q
,
• computes U
i
= r
i
P and
• broadcasts U
i
to the other n−1 original signers.
For i = 1, ... ,n, each O
i
computes
• U =
∑
n
i=1
U
i
,
• h = H
2
(wkU), and
• V
O
i
= hS
ID
O
i
+ r
i
Pub
and sends (w,U
i
,V
O
i
) to the proxy signer P , with
V
O
i
as a delegation value.
Delegation verification: For i = 1, ... ,n, P verifies
the delegation by U =
∑
n
i=1
U
i
and h = H
2
(wkU)
and checking
e(P,V
O
i
) = e(Pub,hQ
ID
O
i
+U
i
).
If the above equality does not hold for some i =
1,...,n, P requests a valid delegation (w,U
i
,V
O
i
)
or terminates the protocol.
SECRYPT2014-InternationalConferenceonSecurityandCryptography
60

Proxy signing key generation: Having accepted del-
egations (w,U
i
,V
O
i
), i = 1,. .., n, P computes
S
ID
Q
= S
ID
P
+ ρ
P
Pub + ρ
O
Pub
and sets the proxy signing key S
P
as
S
P
= V
O
+ hS
ID
Q
,
where V
O
=
∑
n
i=1
V
O
i
and h = H
2
(wkU).
Remark: Note that
S
ID
Q
= S
ID
P
+ ρ
P
Pub + ρ
O
Pub
= sQ
ID
P
+ ρ
P
sP + ρ
O
sP
= s(Q
ID
P
+ ρ
P
P + ρ
O
P)
= s(Q
ID
P
+ R
P
+ R
O
)
= sQ
ID
Q
.
So, (Q
ID
Q
,S
ID
Q
) is a valid public-key / private-key
pair.
Proxy multi-signature: To sign a message m
anonymously on behalf of the group of n original
signers, the proxy signer P computes the following:
• Randomly picks r
P
∈ Z
∗
q
, and
• computes
- U
P
= r
P
P,
- h
P
= H
2
(mkU
P
) and
- V
P
= h
P
S
P
+ r
P
Pub.
The anonymous proxy multi-signature on message m,
by P on behalf of the n original signers is σ
P
=
(w,U
P
,V
P
,U).
Proxy multi-verification: To verify an anonymous
proxy multi-signature σ
P
= (w,U
P
,V
P
,U) for mes-
sage m under a warrant w, the verifier proceeds as fol-
lows:
• Checks whether or not the message m conforms to
the warrant w. If not, stop. Continue otherwise.
• Checks whether or not the pseudonym Q
ID
Q
is au-
thorized by the group of n original signers in the
warrant w. If not, stop. Continue otherwise.
• Computes h
P
= H
2
(mkU
P
), h = H
2
(wkU) and ac-
cepts the proxy signature if and only if the follow-
ing equality holds:
e(P,V
P
) = e(Pub,h
P
(h(
n
∑
i=1
Q
ID
O
i
+Q
ID
Q
)+U)+U
P
).
Remark: Note that the identity of the proxy signer
P or its public key Q
ID
P
is not required for the verifi-
cation.
Reveal & Demonstrate: To reveal the identity of
the proxy signer, any original signer O
i
can reveal R
O
and R
P
and show that
Q
ID
Q
= Q
ID
P
+ R
P
+ R
O
.
That R
P
was indeed sent by P is proved using the
signature s
R
P
. To prove that R
O
is not just a solution
to the equation Q
ID
Q
= Q
ID
P
+ R
P
+ R
O
, t or more
original signers combine their shares to recover the
secret ρ
O
and show that R
O
= ρ
O
P.
5 SECURITY ANALYSIS
In this section, we analyze the correctness, secu-
rity, threshold-anonymity and accountability of our
scheme. First we prove the correctness of the scheme,
then we prove that the underlying IBPMS scheme
is existential unforgeable against adaptive chosen-
message and adaptive chosen-ID attacks and finally
we analyze the threshold-anonymity and accountabil-
ity of the proposed anonymous proxy multi-signature
scheme.
5.1 Correctness
Theorem 10. The presented threshold anonymous
proxy multi-signature scheme is correct.
Proof. This follows since
e(P,V
P
) = e(P,h
P
S
P
+ r
P
Pub)
= e(P,h
P
(V
O
+ hS
ID
Q
) + r
P
Pub)
= e(P,h
P
(
n
∑
i=1
(hS
ID
O
i
+ r
i
Pub) + hS
ID
Q
)
+ r
P
Pub)
= e(Pub,h
P
(
n
∑
i=1
(hQ
ID
O
i
+ r
i
P) + hQ
ID
Q
)
+ r
P
P)
= e(Pub,h
P
(
n
∑
i=1
hQ
ID
O
i
+
n
∑
i=1
r
i
P + hQ
ID
Q
)
+U
P
)
= e(Pub,h
P
(h(
n
∑
i=1
Q
ID
O
i
+ Q
ID
Q
) +U )
+U
P
).
5.2 Security Proof of the IBPMS
Scheme
We now prove that the underlying IBPMS scheme
is existential unforgeable against adaptive chosen-
ASecureAnonymousProxyMulti-signatureScheme
61

message and adaptive chosen-ID attacks.
We facilitate the adversary to adaptively select the
identity on which it wants to forge the signature. Fur-
ther the adversary can obtain the private keys associ-
ated to the identities. The adversary also can access
the proxy multi-generation oracles on warrants w
0
of
its choice, and proxy multi-signature oracles on the
warrant, messages pair (w
0
,m
0
) of its choice, as many
times it wants.
Theorem 11. We consider the random oracle for re-
ply to hash queries. If there exists an adversary
A(t,q
H
1
,q
H
2
,q
E
,q
pmg
,q
pms
,ε)
which breaks the proposed ID-based proxy multi-
signature scheme, then there exists an adversary
B(t
0
,q
0
H
1
,q
0
H
2
,q
0
E
,q
0
pmg
,q
0
pms
,ε
0
)
which solves CDHP in time at most
t
0
≥ t + (q
H
1
+ q
E
+ 2q
pmg
+ 4q
pms
+ 1)C
G
1
with success probability at least
ε
0
≥
ε(1 − 1/q)
M(q
E
+ q
pmg
+ q
pms
+ n + 1)
where C
G
1
denotes the number of scalar multiplica-
tions in group G
1
.
Proof. First of all the challenger runs the setup al-
gorithm and provides the
params = hq, G
1
,G
2
,e,P, sP, bPi
to B. Here, A is a forger algorithm whose goal is to
break the underlying ID-based proxy multi-signature
scheme. The adversary B simulates the challenger
and interacts with A. The goal of B is to solve CDHP
by computing sbP ∈ G
1
.
Key Generation: For security parameter 1
k
, B gen-
erates the system’s public parameter
params = hq, G
1
,G
2
,e,P, Pub,H
1
,H
2
i
and provides Pub = sP to A.
H
1
-queries: To respond to the H
1
hash function
queries, B maintains a list L
H
1
= {hID,h,a,ci}.
When A queries the H
1
hash function on some iden-
tity ID
i
∈ {0,1}
∗
, B responds as follows:
1. If the query ID
i
already appears in the list L
H
1
in some tuple hID
i
,h
i
,a
i
,c
i
i then algorithm B re-
sponds to A with H
1
(ID
i
) = h
i
.
2. Otherwise B picks a random integer a
i
∈ Z
∗
q
and
generates a random coin c
i
∈ {0,1} with probabil-
ity Pr[c
i
= 0] = λ, for some λ ∈ [0,1].
3. If c
i
= 0, B computes h
i
= a
i
(bP) and if c
i
= 1, B
computes h
i
= a
i
P.
4. Algorithm B adds the tuple hID
i
,h
i
,a
i
,c
i
i to the
list L
H
1
and responds to A with h
i
.
H
2
-queries: To respond to the H
2
hash function
queries, B maintains a list L
H
2
= {hw,U, f i}. When
A requests the H
2
query on (w
0
,U
0
) for some warrant
w
0
, B responds as follows:
1. If the query (w
0
,U
0
) already appears on the list
L
H
2
in some tuple hw
0
,U
0
, f i then algorithm B re-
sponds to A with H
2
(w
0
kU
0
) = f .
2. Otherwise B picks a random integer f ∈ Z
∗
q
and
adds the tuple hw
0
,U
0
, f i to the list L
H
2
and re-
sponds to A with H
2
(w
0
kU
0
) as H
2
(w
0
kU
0
) = f .
Extraction queries: If A requests a private key on
identity ID
i
, B responds as follows:
1. B runs the above algorithm for responding to H
1
queries on ID
i
and obtains the corresponding tu-
ple hID
i
,h
i
,a
i
,c
i
i on the list L
H
1
.
2. If c
i
= 0, then B outputs ‘failure’ and terminates.
3. If c
i
= 1, then B responds to A with S
ID
i
=
a
i
Pub ∈ G
1
.
Remark: Note that H
1
(ID
i
) = h
i
= a
i
P so that
e(S
ID
i
,P) = e(a
i
Pub,P)
= e(a
i
P, Pub)
= e(H
1
(ID
i
),Pub)
= e(Q
ID
i
,Pub).
Thus, S is a valid private key corresponding to the
identity ID
i
and the probability of success is (1 − λ),
because we have considered the case for c
i
= 1.
Proxy multi-generation queries: When the adver-
sary A requests to interact with either the proxy signer
or anyone from the original signers, then challenger B
responds as follows:
1. Suppose, A requests to interact with the user ID
O
i
,
who is playing the role of one of the original
signers. For this, A creates a warrant w
0
and re-
quests ID
O
i
to sign the warrant. B queries w
0
to
its signing oracle and upon receiving a response
hU
0
O
i
,V
0
O
i
i, sends hw
0
,U
0
O
i
,V
0
O
i
i to A and adds the
warrant w to the delegation generation list say
L
del
.
2. Suppose, A requests to interact with user ID
P
,
where ID
P
is playing the role of the proxy signer.
For this, A creates a warrant w
0
and computes the
SECRYPT2014-InternationalConferenceonSecurityandCryptography
62

signatures V
0
O
i
= H
2
(w
0
kU
0
)S
ID
O
i
+ x
0
i
Pub. Where
U
0
=
∑
n
i=1
x
0
i
P for randomly selected x
0
i
∈ Z
∗
q
and
S
ID
O
i
is private key of the original signer O
i
which
can be collected by A in the extraction query.
Then A sends (w
0
,V
0
O
i
) (for i = 1,. .., n) to B .
B provides the corresponding proxy signing key
S
0
P
to A and adds the tuple hw
0
,S
P
i to the proxy
multi-generation list say L
pmg
.
In either of the above cases,
1. B runs the above algorithm for responding to H
2
queries on w
0
obtaining the corresponding tuple
hw
0
,U
0
, f i, on L
H
2
list.
2. For H
1
query, if c = 0, then B reports ‘failure’ and
terminates. If c = 1, then, H
1
(ID
O
i
) = a
O
i
P.
Then for V
0
O
i
= f a
O
i
Pub + x
0
i
Pub, one can check
that:
e(Pub, f Q
ID
O
i
+U
0
i
)
= e(Pub, f H
1
(ID
O
i
) +U
0
i
)
= e(Pub, f a
O
i
P + x
0
i
P)
= e(P, f a
O
i
Pub + x
0
i
Pub)
= e(P,V
0
O
i
).
Hence the above provided proxy signing key is valid.
The success probability is (1 − λ), because we have
considered the case for c = 1.
Proxy multi-signature queries: Proceeding adap-
tively when adversary A requests for a proxy multi-
signature on message m
0
of its choice (with satisfying
the warrant w
0
), by the proxy signer P on behalf of
the n original signers O
i
, (i = 1,2, ..,n). B does the
following:
1. runs the above algorithm to respond H
2
-queries on
w
0
, obtaining the tuple hw
0
,U
0
, f i on L
H
2
list.
2. If c = 0 then reports ‘failure’ and terminates. If
c = 1, then by the corresponding H
1
-query h = aP.
Now B randomly selects r
0
P
,r
0
∈ Z
∗
q
and computes
U
0
P
= r
0
P
P and U
0
= r
0
P then having H
2
(w
0
kU
0
) =
f from H
2
query, for the tuple hw
0
,U
0
, f i and
H
2
(m
0
kU
0
P
) = f
P
from H
2
query, for the tuple
hm
0
,U
0
P
, f
P
i, B again computes Q
P
= f (
∑
n
i=1
Q
ID
O
i
+
Q
ID
P
) +U
0
. Finally B computes V
0
P
= [ f
P
{ f (a
O
1
+
··· + a
O
n
+ a
P
) + r
0
} + r
0
P
]Pub for the signature on
message m
0
. One can check that:
e(Pub, f
P
{ f (
n
∑
i=1
Q
ID
O
i
+ Q
ID
P
) +U
0
} +U
0
P
)
= e(Pub, f
P
{ f (H
1
(ID
O
1
) + ·· · + H
1
(ID
O
n
)
+ H
1
(ID
P
)) +U
0
} +U
0
P
)
= e(Pub, f
P
{ f (a
O
1
P + ·· · + a
O
n
P + a
P
P) + r
0
P}
+ r
0
P
P) (for the case when c = 1)
= e(Pub, f
P
{ f (a
O
1
+ ··· + a
O
n
+ a
P
) + r
0
}P
+ r
0
P
P)
= e(P, f
P
{ f (a
O
1
+ ··· + a
O
n
+ a
P
) + r
0
}Pub
+ r
0
P
Pub)
= e(P,[ f
P
{ f (a
O
1
+ ··· + a
O
n
+ a
P
) + r
0
}
+ r
0
P
]Pub)
= e(P,V
0
P
).
Hence, the produced proxy multi-signature
(w
0
,U
0
P
,V
0
P
,U
0
) on message m
0
is valid, which
satisfies
e(P,V
0
P
) = e(Pub,h
P
(h(
n
∑
i=1
Q
ID
O
i
+Q
ID
P
)+U
0
)+U
0
P
).
The success probability is (1 − λ), because we have
considered the case for c = 1.
Hence, the probability that B does not abort dur-
ing the simulation is
(1 − λ)
q
E
+q
pmg
+q
pms
.
Output: If B never reports ‘failure’ in the above
game, A outputs a valid ID-based proxy multi-
signature (w,U
P
,V
P
,U) on message m which satisfies
e(P,V
P
) = e(Pub,h
P
(h(
n
∑
i=1
Q
ID
O
i
+Q
ID
P
)+U)+U
P
).
If A does not query any hash function, that is, if re-
sponses to all the hash function queries are picked
randomly then the probability that verification equal-
ity holds is less than 1/q. Hence, A outputs a new
valid ID-based proxy multi-signature (w,U
P
,V
P
,U)
on message m with the probability
(1 − λ)
q
E
+q
pmg
+q
pms
(1 − 1/q).
Now we compute the success probability of B for
the solution of CDHP using the above forgeries (by
A). We consider both the possible cases, viz. , suc-
cess probability in case when A plays against an orig-
inal signer and when A plays against the proxy signer.
ASecureAnonymousProxyMulti-signatureScheme
63

Case 1. Suppose, A simulates B and requests to in-
teract with any user say ID
O
1
, where the user ID
O
1
is
playing the role of one original signer. For ID
O
1
, A
did not request the private key in Extraction queries,
A did not request a Proxy multi-generation query
including hw,ID
O
1
i and A did not request a Proxy
multi-signature query including hID
O
1
,w, mi. If c = 1,
then H
1
(ID
O
i
) = a
O
i
P for i = 2,.. .,n, and H
1
(ID
P
) =
a
P
P from the H
1
-query. Further B computes V
∗
P
=
V
0
P
− ([ f
P
{ f (a
O
2
+ ··· + a
O
n
+ a
P
) + r
0
} + r
0
P
]Pub),
then proceeds to solve CDHP using the equality:
e(P,V
0
P
) = e(Pub,h
P
(h(
n
∑
i=1
Q
ID
O
i
+ Q
ID
P
) +U
0
)
+U
0
P
)
= e(Pub, f
P
{ f (H
1
(ID
O
1
) + ·· · + H
1
(ID
O
n
)
+ H
1
(ID
P
)) +U
0
} +U
0
P
)
= e(Pub, f
P
{ f (a
O
2
+ ··· + a
O
n
+ a
P
) + r
0
}P
+ r
0
P
P)e(Pub, f
P
{ f H
1
(ID
O
1
)})
= e(P,[ f
P
{ f (a
O
2
+ ··· + a
O
n
+ a
P
) + r
0
}
+ r
0
P
]Pub)e(Pub, f
P
{ f H
1
(ID
O
1
)})
or, by above we can write
e(P,V
∗
P
) = e(Pub, f
P
{ f H
1
(ID
O
1
)})
= e(Pub, f
P
f a
O
1
(bP))
= e(P, f
P
f a
O
1
(bsP))
= e(P,k(bsP))
where k = f
P
f a
O
1
∈ Z
∗
q
.
Comparing the components on both sides, B gets
V
∗
P
= k(bsP)
which implies that k
−1
V
∗
P
= bsP. Thus B can solve
an instance of CDHP.
The probability of success is λ(1 − λ)
n
.
Case 2. When A simulates B and requests to in-
teract with a user ID
P
, where user ID
P
is the proxy
signer. For ID
P
, A did not request the private key,
A did not request a proxy multi-generation query in-
cluding hw,ID
P
i and A did not request a proxy multi-
signature query including hID
P
,w, mi. As the above
case, we can show that B can derive sbP with the
same success probability λ(1 − λ)
n
.
Hence the overall success probability that B
solves the CDHP in the above attack game is:
ε
0
= λ(1 − λ)
q
E
+q
pmg
+q
pms
+n
(1 − 1/q)ε.
Now the maximum possible value of the above prob-
ability occurs for
λ =
1
q
E
+ q
pmg
+ q
pms
+ n + 1
.
Hence the optimal success probability is
ε(1 − 1/q)
M(q
E
+ q
pmg
+ q
pms
+ n + 1)
where
1
M
is the maximum value of
(1 − λ)
q
E
+q
pmg
+q
pms
+n
for
λ =
1
q
E
+ q
pmg
+ q
pms
+ n + 1
.
Therefore
ε ≤
ε
0
M(q
E
+ q
pmg
+ q
pms
+ n + 1)
1 − 1/q
.
Now taking care of running time, one can observe
that the running time of algorithm B is same as A’s
running time plus the time taken to respond to the
hash, extraction, proxy multi-generation and proxy
multi-signature queries, that is,
q
H
1
+ q
H
2
+ q
E
+ q
pmg
+ q
pms
.
Hence, the maximum running time is given by
t + (q
H
1
+ q
E
+ 2q
pmg
+ 4q
pms
+ 1)C
G
1
,
as each H
1
Hash query requires one scalar multiplica-
tion in G
1
, Extraction query also requires one scalar
multiplication in G
1
, proxy multi-generation query re-
quires two scalar multiplications in G
1
, proxy multi-
signature query requires four scalar multiplications
in G
1
and to output CDH solution from A’s forgery,
B requires at most one scalar multiplication in G
1
.
Hence
t
0
≥ t + (q
H
1
+ q
E
+ 2q
pmg
+ 4q
pms
+ 1)C
G
1
.
5.3 Anonymity
Theorem 12. The presented threshold anonymous
proxy multi-signature scheme is anonymous.
Proof. Since ρ
O
i
∈ Z
∗
q
are random, so is ρ
O
and
hence so is R
O
= ρ
O
P. Also, since ρ
P
∈ Z
∗
q
is random,
so is R
P
= ρ
P
P. Since ρ
O
i
, ρ
s
i
, R
O
and R
P
were com-
municated through a secure channel, these are hidden
from any adversary. So, no adversary would be able
to ascertain the identity of the proxy signer from the
computation Q
ID
Q
= Q
ID
P
+ R
P
+ R
O
.
In fact, note that even a collusion of t
0
original
signers (t
0
< t) cannot recover ρ
O
and cannot really
prove that P is indeed the proxy signer. The last state-
ment follows from the security of the threshold veri-
fiable secret sharing (Pedersen, 1991) and to get the
value ρ
O
from R
O
, the adversary has to solve discrete
log problem, which is assumed to be hard.
SECRYPT2014-InternationalConferenceonSecurityandCryptography
64
5.4 Accountability
Theorem 13. The presented threshold anonymous
proxy multi-signature scheme is accountable.
Proof. To reveal the identity of the proxy signer, any
original signer O
i
can reveal R
O
and R
P
and show that
Q
ID
Q
= Q
ID
P
+ R
P
+ R
O
. (1)
That R
P
was indeed sent by P is proved using the
signature s
R
P
.
To prove that R
O
is not just a solution to the equa-
tion (1), t or more original signers combine their
shares to recover the secret ρ
O
and show that R
O
=
ρ
O
P. Since R
P
was randomly chosen by P , given
Q
ID
P
and Q
ID
Q
, R
O
is also random, and hence dis-
honest original signers can produce correct ρ
O
only if
they can solve the discrete log problem in G
1
.
6 EFFICIENCY COMPARISON
Here, we compare the efficiency of our scheme with
the IBPMS schemes of (Cao and Cao, 2009), (Du and
Wang, 2013) and (Shao, 2009), and show that our
scheme is more efficient in the sense of computation
and operation time than these schemes. For the com-
putation of operation time, we refer to (Debiao et al.,
2011) where the operation time for various crypto-
graphic operations have been obtained using MIR-
ACL (MIRACL), a standard cryptographic library,
and the hardware platform is a PIV 3 GHZ proces-
sor with 512 M bytes memory and the Windows XP
operating system. For the pairing-based scheme, to
achieve the 1024-bit RSA level security, Tate pairing
defined over the supersingular elliptic curve E = F
p
:
y
2
= x
3
+x with embedding degree 2 was used, where
q is a 160-bit Solinas prime q = 2
159
+ 2
17
+ 1 and p
a 512-bit prime satisfying p + 1 = 12qr. We note that
the OT for one pairing computation is 20.04ms, for
one scalar multiplication it is 6.38ms, for one map-to-
point hash function it is 3.04ms and for one general
hash function it is < 0.001ms. To evaluate the total
operation time in the efficiency comparison tables, we
use the simple method from (Cao et al., 2010; Debiao
et al., 2011). In each of the three phases: proxy multi-
generation, proxy multi-signature and proxy multi-
verification, we compare the total number of bilin-
ear pairings (P), scalar multiplications (SM), map-to-
point hash functions (H) and the consequent opera-
tion time (OT) while omitting the operation time due
to a general hash function which is negligible com-
pared to the other three operations. Further, across
all the compared schemes, in the computation table
for proxy multi-generation, we take into consideration
the computations of only one of the n original signers
following the methodology of (Cao et al., 2010; De-
biao et al., 2011).
For example, the proxy multi-generation phase of
our scheme takes 2 pairing operations, 7 scalar mul-
tiplications and 1 map-to-point hash function. Hence
the total operation time for this phase can be calcu-
lated as: 2 × 20.04 + 7 × 6.38 + 1 × 3.04 = 87.78ms.
Similarly, we have computed the total OT in other
phases for all the schemes.
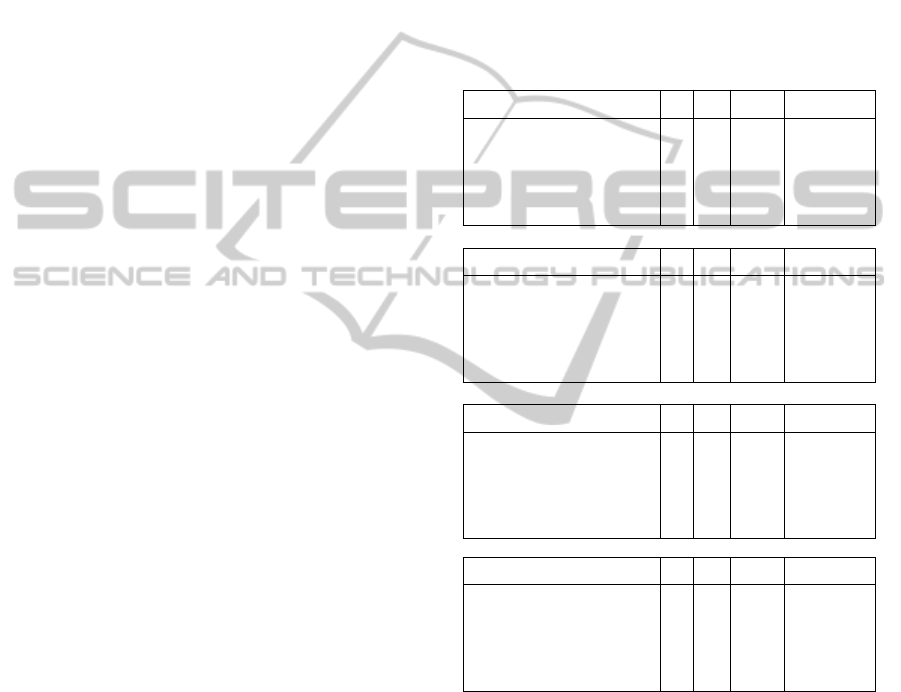
Table 1: Efficiency Comparison
Proxy multi-generation:
Scheme P H SM OT (ms)
(Cao and Cao, 2009) 3 3 3 88.38
(Du and Wang, 2013) 3 4 4
∗
97.80
(Shao, 2009) 3 3 2 82.00
Our scheme 2 1 7
∗
87.78
Proxy multi-signature:
Scheme P H SM OT (ms)
(Cao and Cao, 2009) 0 1 2 15.80
(Du and Wang, 2013) 0 1 2 15.80
(Shao, 2009) 0 1 2 15.80
Our scheme 0 0 3 19.14
Proxy multi-verification:
Scheme P H SM OT (ms)
(Cao and Cao, 2009) 4 3 1 95.66
(Du and Wang, 2013) 4 3 1 95.66
(Shao, 2009) 4 3 0 89.28
Our scheme 2 1 2 55.88
Overall Time:
Scheme P H SM OT (ms)
(Cao and Cao, 2009) 7 7 6 199.84
(Du and Wang, 2013) 7 8 7 209.26
(Shao, 2009) 7 7 4 187.08
Our scheme 4 2 11 162.80
* The scalar multiplications due to pseudonym gen-
eration are not considered.
From the efficiency comparison table (1), it is
clear that our scheme is computationally more ef-
ficient and having less operation time than the
schemes (Cao and Cao, 2009; Du and Wang, 2013;
Shao, 2009).
REFERENCES
Blakley, G. R. (1979). Safeguarding cryptographic keys. In
National Computer Conference, pages 313–317.
ASecureAnonymousProxyMulti-signatureScheme
65

Boldyreva, A., Palacio, A., and Warinschi, B. (2003).
Secure proxy signature schemes for delegation of
signing rights. IACR Cryptology ePrint Archive,
2003:096.
Cao, F. and Cao, Z. (2009). A secure identity-based
proxy multi-signature scheme. Information Sciences,
179(3):292–302.
Cao, X., Kou, W., and Du, X. (2010). A pairing-free
identity-based authenticated key agreement protocol
with minimal message exchanges. Information Sci-
ences, 180(15):2895–2903.
Chor, B., Goldwasser, S., Micali, S., and Awerbuch, B.
(1985). Verifiable secret sharing and achieving simul-
taneity in the presence of faults (extended abstract). In
FOCS, pages 383–395.
Debiao, H., Jianhua, C., and Jin, H. (2011). An id-based
proxy signature schemes without bilinear pairings.
Ann. Telecommun., 66(11-12):657–662.
Du, H. and Wang, J. (2013). An anonymous but accountable
proxy multi-signature scheme. Journal of Software,
8(8):1867–1874.
Fuchsbauer, G. and Pointcheval, D. (2008). Anonymous
proxy signatures. In Security and Cryptography for
Networks, pages 201–217.
Gasser, M., Goldstein, A., Kaufman, C., and Lampson, B.
(1989). The digital distributed system security archi-
tecture. In NCSC’89, pages 305–319.
Lee, B., Kim, H., and Kim, K. (2001). Strong proxy signa-
ture and its applications. In Proc of SCIS, volume 1,
pages 603–608.
Lee, N.-Y. and Lee, M.-F. (2005). The security of a strong
proxy signature scheme with proxy signer privacy
protection. Applied mathematics and computation,
161(3):807–812.
Lee, Y.-H., Hong, S.-M., and Yoon, H. (2005). A se-
cure strong proxy signature scheme with proxy signer
privacy protection. In CCCT’05. (International Con-
ference on Computing, Communications and Control
Technologies).
Mambo, M., Usuda, K., and Okamoto, E. (1996). Proxy
signatures: Delegation of the power to sign messages.
IEICE transactions on fundamentals of electronics,
communications and computer sciences, 79(9):1338–
1354.
MIRACL. Multiprecision integer and ra-
tional arithmetic cryptographic library.
http://certivox.org/display/EXT/MIRACL.
Pedersen, T. P. (1991). Non-interactive and information-
theoretic secure verifiable secret sharing. In Advances
in Cryptology – CRYPTO’91, pages 129–140.
Sahu, R. A. and Padhye, S. (2012). Efficient id-based
proxy multi-signature scheme secure in random ora-
cle. Frontiers of Computer Science, 6(4):421–428.
Schuldt, J. C. N., Matsuura, K., and Paterson, K. G. (2008).
Proxy signatures secure against proxy key exposure.
In Public Key Cryptography, volume 4939 of LNCS,
pages 141–161.
Shamir, A. (1979). How to share a secret. Communications
of the ACM, 22(11):612–613.
Shao, Z. (2009). Improvement of identity-based proxy
multi-signature scheme. Journal of Systems and Soft-
ware, 82(5):794–800.
Shum, K. and Wei, V. K. (2002). A strong proxy signa-
ture scheme with proxy signer privacy protection. In
Enabling Technologies: Infrastructure for Collabora-
tive Enterprises, 2002. WET ICE 2002. Proceedings.
Eleventh IEEE International Workshops on, pages 55–
56. IEEE.
Sun, H.-M. and Hsieh, B.-T. (2003). On the security of
some proxy signature schemes. IACR Cryptology
ePrint Archive, 2003:068.
Toluee, R., Asaar, M. R., and Salmasizadeh, M. (2012). An
anonymous proxy signature scheme without random
oracles. IACR Cryptology ePrint Archive, 2012:313.
Wu, K.-L., Zou, J., Wei, X.-H., and Liu, F.-Y. (2008). Proxy
group signature: A new anonymous proxy signature
scheme. In Machine Learning and Cybernetics, 2008
International Conference on, volume 3, pages 1369–
1373.
Xiong, H., Hu, J., Chen, Z., and Li, F. (2011). On
the security of an identity based multi-proxy signa-
ture scheme. Computers & Electrical Engineering,
37(2):129–135.
Yu, Y., Xu, C., Huang, X., and Mu, Y. (2009). An efficient
anonymous proxy signature scheme with provable se-
curity. Computer Standards & Interfaces, 31(2):348–
353.
SECRYPT2014-InternationalConferenceonSecurityandCryptography
66
