
Analyzing Risks in Business Process Models using a Deviational
Technique
Hanane Lhannaoui, Mohammed Issam Kabbaj and Zohra Bakkoury
AMIPS Research Group, Ecole Mohammadia d’Ingénieurs,
MOHAMMED V University, Agdal, Rabat, Morocco
Keywords: Business Process Management, HAZOP, Deviational Analysis, Risk Analysis.
Abstract: In a business environment, many processes are performing ineffectively due to different risks. Several
methods and techniques for the identification and management of risks in business processes have been
proposed. Some of them originate from other domains and have been adapted to the business environment
such as deviational approaches. Nevertheless, there are few examples for potential applications of those
methods in business process redesign. This paper addresses this gap through proposing an approach that
adapts HAZOP (HA-Zard OP-erability), a systematic deviational technique, to business process
environment. We discuss how this method can contribute to the improvement of business process models.
1 INTRODUCTION
In the last few years, organizations have become
more aware of the importance of managing risks.
They are increasingly implementing procedures that
aim to control and manage business risks. This leads
to an extra effort and costs that may sometimes
distract people from doing what they should focus
on: the business.
Therefore, creating and preserving value in
business cannot be assured without bringing the risk
management practices closer to business process
management (BPM) domain. This need had given
birth to the Risk aware business process. In fact, the
Risk-aware business process system is a system that
allows the reasoning about management of risks in
BPM from the design to the post execution of
business process. This integration has many
advantages including the ability to:
analyze risks and incorporate risk mitigation
strategies in a business process model during
design time (Goluch et al., 2008),
monitor the emergence of risks and apply
risk mitigation actions during run time
(Conforti et al., 2011),
Identify risks from logs and other post-
execution artifacts (Jans et al., 2011).
This paper addresses the topic of risk-aware
business process management. It describes an
approach for analyzing risks in business process
during the design time by studying the deviational
behavior of the process. Since risk-aware business
process environment has many similarities with the
safety domain. The method described in this paper is
inspired from this domain. Concretely, it uses
HAZOP a deviational technique from the safety
domain. That would potentially improve the risk
analysis process. Thus, the results of risk analysis
(HAZOP output) can be used to propose a redesign
for the studied process. This is done by
incorporating risk controls into the design since the
analysis is considered earlier in process lifecycle.
This paper is structured as follows: Section 2 covers
related work while Section 3 summarizes some
preliminaries needed for the understanding of the
concepts introduced in the paper. Section 4 describes
EPC-Based HAZOP Analysis which is an adaptation
of HAZOP a traditional method for deviational
analysis. Section 5 discusses how our method can be
used to motivate business process improvement.
Finally, Section 6 concludes the paper.
2 RELATED WORK
The use of risk management techniques in design is
a concept that had been initially adapted in safety
critical systems. Many of those tools and methods,
for example FMEA (Failure Mode and Effects
189
Lhannaoui H., Kabbaj M. and Bakkoury Z..
Analyzing Risks in Business Process Models using a Deviational Technique.
DOI: 10.5220/0005109801890194
In Proceedings of the 9th International Conference on Software Engineering and Applications (ICSOFT-EA-2014), pages 189-194
ISBN: 978-989-758-036-9
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

Analysis), FTA (Fault Tree Analysis) and HAZOP
(Hazardous Operability Analysis), have been used in
various domains such as the military, power plant,
aircraft and space industry. The objective is to
design reliable and safe systems.
In software engineering for example, HAZOP
studies have also been successfully performed on
several kinds of models such as object-oriented
models (Lano et al., 2002), data flow models and
CORE models (McDermid, 1995). HAZOP has
proved that it is useful for software hazard analysis,
and safety-certification authorities recommend its
use during software development. Subsequently,
many adaptations have been proposed such as UML-
BASED HAZOP analysis (Martin-Guillerez et al.,
2010).
The application of risk management techniques
in business environment is a concept that has been
introduced in the past ten years. Most approaches
that have been proposed in the area of risk-aware
business process management tried to address the
issue of risk in business processes at design time
(Suriadi et al., 2012) including design time risk-
analysis.
Suriadi et al. enumerated, in (Suriadi et al.,
2012) risk-Aware BPM approaches that integrate
risk analysis partially or comprehensively. However,
the research efforts in this area are distributed across
various types of risk analysis, including risk
probability analysis, risk impact analysis, risk
identification/discovery analysis, and risk mitigation
analysis (Fenz and Neubauer, 2009), (Mock and
Corvo, ). They lack the technical precision to afford
a convincing design-time risk analysis approach
(Suriadi et al., 2012). In addition, even if the risk
analysis is carried in the design-time, its output is
not exploited to improve the reliability of the
process. In fact, these approaches do not propose
mechanisms that attach risk analysis to the design
quality.
In this paper, we propose an approach of
analyzing risks that can facilitate a design change in
an earlier phase process lifecycle. This objective has
been proposed formerly in (lhannaoui et al., 2013).
Nevertheless, the present paper introduces more
comprehensive version of the risk analysis method.
It also details the concepts related to the risk analysis
output.
3 PRELIMINARIES
In this section, we describe basic concepts that are
used in this paper.
3.1 Event-Driven Process Chain
EPCs (Event-driven Process Chain) are a graphical
business process description language introduced by
Keller, Nuttgens and Scheer in 1992 (Govermatori,
2006). It was developed at the Institute for
Information Systems of the University of Saarland,
Germany, in collaboration with SAP AG. The EPC
is a core part of the ARIS-framework and combines
different views towards the description of
enterprises and information systems in the control
view on the conceptual level (ISO/DIS 31000,
2006).
EPCs describe processes on the level of their
business logic. The name represents the control flow
structure of the process as a chain of events and
functions. Actually, the EPC describes processes by
the use of alternating functions and events as time-
referring state changes. Events and functions are
linked by the control flow as directional edges
(Govermatori, 2006).
An event-driven process chain consists of the
following elements:
Functions: The basic building blocks.
Functions are active elements used to
describe the tasks or activities of a business
process that needs to be executed.
Events: Passive elements used to describe
under which circumstances a process (or a
function) works or which state a process (or
a function) results in (like pre- / post-
conditions).
Logical connectors: They can be used to
connect activities and events. This is the way
how the flow of control is specified. There
are three types of connectors: AND, XOR
(exclusive or) and OR.
The extended EPC includes the elements
described below:
The Organization Unit or Role is responsible
for performing an activity or function.
The Information Objects portray input data
serving as the basis for a function, or output
data produced by a function.
The deliverables represent results (services
or products) functions produce or input
functions require.
In this paper, we will use EPC as a modeling
language for describing business process.
ICSOFT-EA2014-9thInternationalConferenceonSoftwareEngineeringandApplications
190
3.2 HAZOP
The HAZard and Operability (HAZOP) study was
initially developed by the company ICI in 1974 for
chemical developing facilities but has later been
extended to other types of systems and also to
complex operations and to software systems
(Ministry of Defense, 2000). It is typically
conducted by a team consisting of four to eight
persons with a detailed knowledge of the analyzed
system. HAZOP is performed using a set of
guidewords and attributes. It is based on a theory
that assumes risk events are caused by deviations
from design or operating intentions.
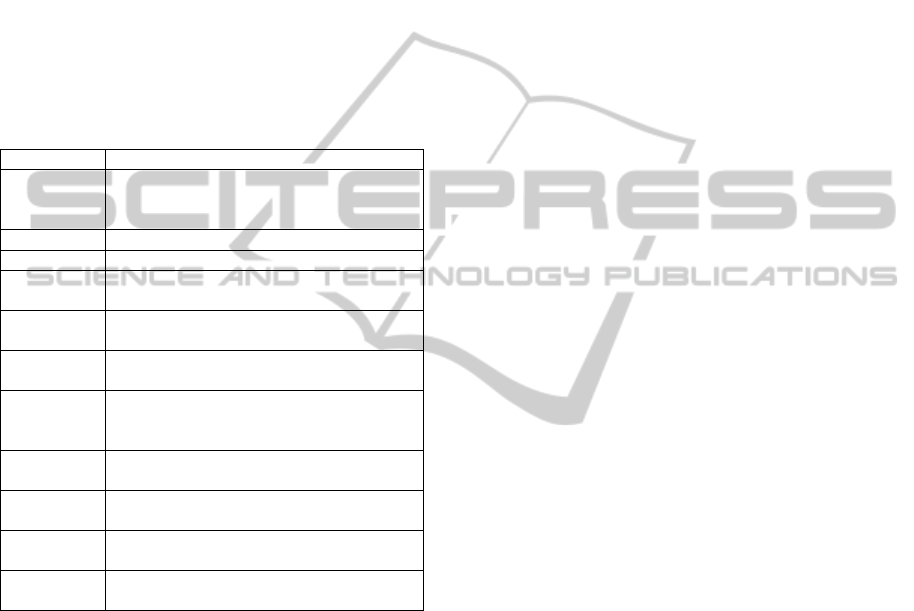
Table 1: HAZOP Guidewords.
Guidewords Interpretation
No This is a complete negation of the design
intention. No part of the intention is
achieved and nothing else happens.
More This is a quantitative increase.
Less This is a quantitative increase.
As well as All the design intention is achieved
together with additions.
Part of Only some of the design intention is
achieved.
Reverse The logical opposite of the intention is
achieved.
Other than Complete substitution, where no part of the
original intention is achieved but
something quite different happens.
Early Something happens earlier than expected
relative to clock time.
Late Something happens later than expected
relative to clock time.
Before Something happens before it is expected,
relating to order or sequence.
After Something happens after it is expected,
relating to order or sequence.
The purpose of a HAZOP study is to identify
what potentially hazardous variations from the
design intent could occur in components and in the
interactions between components of a system
(Ministry of Defense, 2000). Consequently, this will
permit us to avoid continuing development of
designs with potential hazards (Ministry of Defense,
2000). The technique uses “guidewords” to promote
creative thinking about the ways in which hazardous
situations might occur. A guideword is used to
express a particular kind of deviation (Table 1).
In this paper, we use HAZOP technique for risk
analysis since it is:
A qualitative method. In fact, our approach is
based on the study of risk behavior rather
than its appreciation;
An inductive risk assessment tool, meaning
that it is a “bottom-up” risk identification
approach where we start from a particular
fault to the general effect of the fault;
Risk-focused. Actually, it concentrates on
how the design will cope with abnormal
conditions rather on how it will perform
under normal conditions;
Design-oriented because apart from being
used for identifying hazards, it proposes
recommendations with low-level details on
the design.
4 EPC-BASED HAZOP
In this section, we present our method to analyze
risks based on an EPC model representing a business
process description. The risk analysis is then
performed on this description using an adaptation of
the HAZOP method. For this, we consider that we
have an EPC business process model. The design
should be done as early as possible in the
development process to allow early identification of
major risks and to program consequent adaptation of
the design to incorporate risk controls.
4.1 Hazop Method Adaptation
This section aims to propose an adaptation of
HAZOP for EPC-extended models. Actually, a
business process model fragment can be considered
as a HAZOP entity and its EPC elements as HAZOP
attributes. Therefore, once the EPC model is
completed, the EPC-based HAZOP method is
applied by selecting model’s elements and applying
the corresponding guidewords to them.
Since “Function”, is the only active element in
the EPC models, we will only consider guidewords
interpretation for this element.
For this, we simulate the function in an EPC
model to a system in the safety domain. Its
parameters are simulated to the other EPC elements:
passive elements (events) and annotations. Therefore,
we divide those parameters to three groups: the Role,
the input parameters and the output parameters
(Table 2).
Taking this into account, we then propose new
definitions of hazard related to guidewords
deviations which will suit for applying in the
business environment. We call, consequently, EPC-
based HAZOP the re-interpretation of HAZOP
guidewords previously presented in Table 1 in the
context of EPC modeling. Table 4 represents then the
AnalyzingRisksinBusinessProcessModelsusingaDeviationalTechnique
191
proposed definitions of the possible deviations that
can be detected for the described guidewords and the
related parameters.
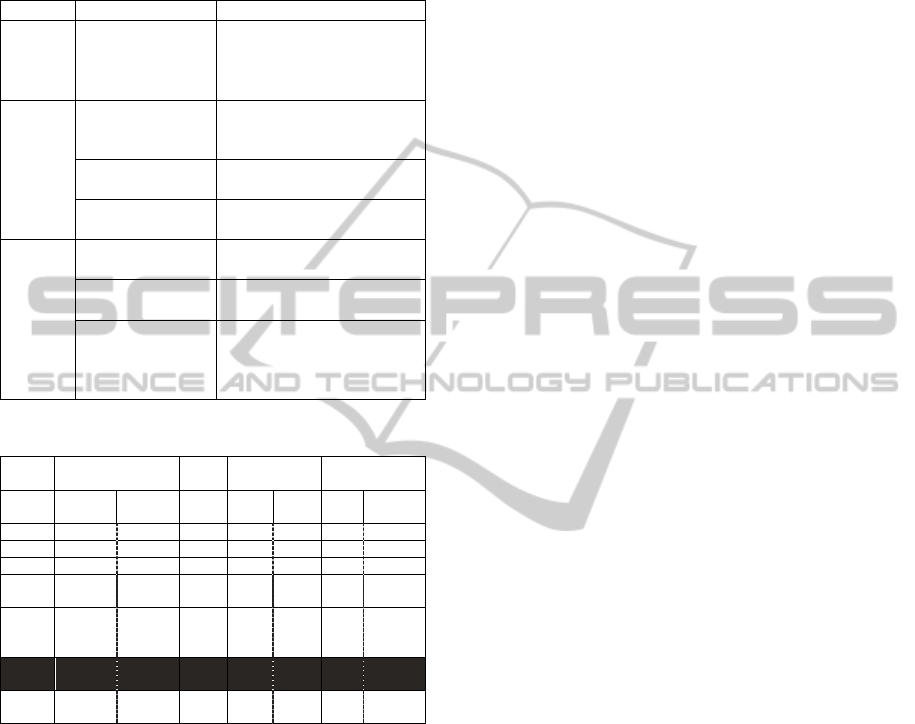
Table 2: Groups of parameters.
Group Parameters Description
Role The
Organization
Unit or Role
The Organization Unit or
Role is responsible for
performing an activity or
function.
Input Event
(precondition)
Circumstances under
which a function or a
process works.
The Information
Objects
Input data serving as the
basis for a function.
The deliverables Input services or products
that functions require.
Output Event
(postcondition)
The state that a process or
a function results in.
The Information
Objects
Output data produced by a
function.
The deliverables The deliverables represent
results (services or
products) functions
produce.
Table 3: Correlation of guidewords and parameters.
GW Event Role Deliverables
Information
objects
Precon
dition
Postco
ndition
Inp
ut
Out
put
Inp
ut
Output
No + + + + + + +
Less + + + +
More + + + +
Part
of
+ + + + + +
As
well
as
+ + + +
Reve
rse
Other
than
+ + + + +
Once deviations have been identified, possible
consequences and causes are analyzed. We note that
some deviations can be caused by the deviation of
other categories of elements, such as events, the
organization role or unit, the deliverables and the
information objects. In those cases, the overall
deviation is associated to the function itself.
Consequently, Table 3 represents the mapping
between guidewords and the other process elements.
The final outcome of EPC-Based HAZOP
analysis consists of a list of recommendations and a
list of hazards, together with the possible deviations
leading to them. This list of hazards can be converted
to a list of risks. HAZOP inherently assumes that risk
events are caused by deviations from design or
operating intentions. In the next section, we propose
a new version of the HAZOP output in order to take
into account all the variables that are related to
business process risks.
4.2 EPC-based HAZOP Analysis Table
In this section, we will introduce EPC-based HAZOP
table, an adapted version of HAZOP table (the output
of HAZOP) that meets the purpose of our work. In
the literature, Kletz defines, in (Suriadi et al., 2012),
5 principal columns in HAZOP table: guideword,
deviation, possible causes, consequences action and
severity, which represents a preliminary risk
estimation of the impact of the deviation’s
consequences. and action required. Other columns
can be added to the HAZOP table such as safeguards,
comments, responsible for
In this paper, we use the term “recommendation”
that relates to the new security requirement or the
actions required to deal with the related deviation.
The recommendation represents changes that should
be applied to control risks.
We also introduce the severity and frequency
which represent respectively, the deviation impact
and the occurrence probability of the harm due to it.
Those two columns represent the risk valuation.
For the consequences column, generally two
levels are represented in the HAZOP table: The use
case effect which represents the consequences of the
deviation on the HAZOP element (the attribute) and
the system effect which associates the deviation to
the whole process and gives its effect in the real
world.
To sum up, we propose a deviation analysis table
with the following columns (c.f. Table 5):
Attribute: the EPC element on which the
deviation is applied.
GW: the applied guideword.
Description: the deviation resulting from the
combination of the attribute and the
guideword.
Composite: if the deviation is resulted for an
external reason or from the deviation of
other parameters.
Possible Causes: possible causes of the
deviation that can be resulted from the
deviation of any of the parameters
predefined.
Use Case Effect: effect at the use case level.
System Effect: possible effect in the real
world.
Severity: rating of effect of the worst case
scenario.
ICSOFT-EA2014-9thInternationalConferenceonSoftwareEngineeringandApplications
192
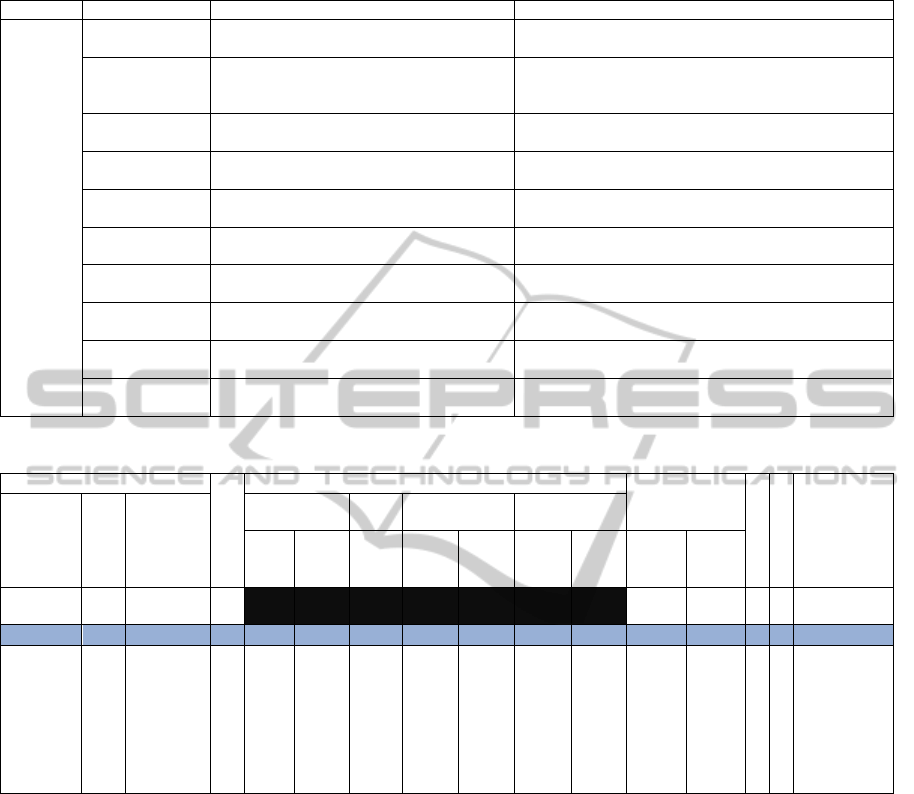
Table 4: List of deviations.
Element Guideword Interpretation Related parameters
Function
Not
The function is not executed and the output
is not generated
Event (Postcondition) , Output (deliverable,
Information objects)
More
The function has been executed several
times or produced more than intended
output
Event (Postcondition) , Output (deliverable,
Information objects)
Less
The function has produced less than the
intended output
Event (Postcondition) , Output (deliverable,
Information objects)
As well As
The function has generated the intended
output but with additional result
Event (Postcondition) , Output (deliverable,
Information objects
Part of
Only part of the intended activity occurs or
a part of the output has been generated
Event (Postcondition) , Output (deliverable,
Information objects
Other than
A complete substitution of the activity has
been performed
Event(Precondition), Input (Deliverable, Information
objects)
Early
The function happened earlier than what is
intended
Event (Precondition)
Late
The function happened later than what is
intended
Event(Precondition)
After
The action succeeds something that it
should precede
Event(Precondition)
Before
The action precedes something that it
should succeeds
Event(Precondition)
Table 5: EPC-based HAZOP Output.
Deviation
Composite
(O/N)
Possible Causes
Consequences
Severity
Frequency
Recommen
dation
Attribute
G
W
Descripti
on
Event Role Deliverables
Information
objects
Prec
ondi
tion
Post-
cond
ition
Input
Outp
ut
Input
Outp
ut
Use
case
effect
Syste
m
effect
Function
1
N
Function
2
No
The
function
is not
executed
and the
output is
not
generated
O
Input
data
is not
avail
able
Frequency: represents the occurrence
probability of the deviation’s consequences.
Recommendation: the actions required to
deal with the related deviation.
5 DEVIATIONAL ANALYSIS FOR
BUSINESS PROCESS
IMPROVEMENT
The purpose of this paper is to present an approach
that allows identifying which potentially hazardous
variations from the design intent could occur in the
different elements of the business process model.
This will help business process designers to optimize
their work in order to incorporate risk controls in an
early phase of the business process lifecycle: the
design phase. In fact, taking risks into account in an
early phase may reduce future costs of process
changes and needs for process adaptations will
decrease as those costs normally increase since
reliability is improved. Furthermore, reducing risks
in an early phase of business process lifecycle will
decrease the number of failures during execution.
Consequently, business losses are minimized.
Therefore, it is becoming inconceivable in a
competitive context, as the current one, to rely only
on detective and curative treatment approaches while
dealing with risks during process execution when we
can reduce risks from the design phase.
In fact, (lhannaoui et al., 2013) showed through a
motivation example how risk analysis can be used to
change a business process model for the purpose of
reducing process risks. EPC-based HAZOP is the
AnalyzingRisksinBusinessProcessModelsusingaDeviationalTechnique
193

only approach that links the risk analysis to the
process model itself. Actually, it proposes a
systematic approach for identifying and analyzing
risks but also suggests hints regarding possible risk
reduction means to prevent the occurrence of
deviations or to provide protection against their
unwanted effect. Once the analysis is conducted,
there will be a way of preventing the occurrence of
deviations. This is done by guaranteeing that
recommendations are incorporated in the initial
design in order to get an improved model.
Accordingly, we believe that EPC-based HAZOP
presented in this paper, sketching out how new
guidewords, attributes can be an input to business
process improvement by providing to the
organization’s management the required tools to deal
with risks in an early phase of the business process
lifecycle. Such as, changes produced from the EPC-
based HAZOP output will be used as input to re-
design the process model(s) for future executions.
6 CONCLUSION
In order to improve business process, appropriate
analysis methods are needed. For this, we propose
new aspects that should be taken into account while
changing a process design. Effectively, carrying out
an appropriate risk analysis in an early phase of the
process lifecycle can lead to a review of the business
process model.
This paper presents an adaptation of HAZOP
method that is applied in the business process
environment. In fact EPC-based HAZOP simulates
an EPC model to HAZOP entities for whose
elements guide words may be applied. Later, we
proposed a unified output for EPC-based HAZOP
that aims to facilitate the translation of
recommendations to design.
Finally, we plan to extend our approach by
proposing mechanisms that permit to incorporate the
recommendation in EPC-based HAZOP table in
business process models in order to improve their
reliability.
REFERENCES
Conforti, R., Fortino, G., Rosa, M. L., ter Hofstede, A.,
2011. History-aware real-time risk detection in
business processes. In OTM 2011 Conferences.
Fenz, S., Neubauer, T., 2009. How to determine threat
probabilities using ontologies and bayesian networks.
In Proceedings of the 5th Annual Workshop on Cyber
Security and Information Intelligence Research: Cyber
Security and Information Intelligence Challenges and
Strategies, CSIIRW ’09, pages 69:1–69:3, New York,
NY, USA. ACM.
Goluch, G., Tjoa, S., Jakoubi, S., Quirchmayr, G., 2008.
Deriving resource requirements applying risk-aware
business process modeling and simulation. In ECIS,
AISeL.
Governatori, G., Milosevic, Z., Sadiq, S., 2006.
Compliance checking between business processes and
business contracts. In: Proceedings of the 10th IEEE
Conference on Enterprise Distributed Object
Computing.
ISO/DIS 31000, 2009. Risk management — Principles and
guidelines on implementation. International
Organization for Standardization.
Jans, M., Depaire, B., Vanhoof, K., 2011. Does process
mining add to internal auditing? An experience report.
In Halpin, T. A., Nurcan, S., Krogstie, J., Soffer,
P.,Proper, E., Schmidt, R., and Bider, I., editors,
BMMDS/EMMSAD, volume 81 of LNBIP, pages 31–
45, Springer.
Lano, K., Clark, D., Androutsopoulos, K., 2002. Safety
and security analysis of object-oriented models. In S.
Anderson et al., editors, Computer Safety, Reliability
and Security: SAFECOMP, volume 2434 of Lecture
Notes in Computer Science (LNCS). Springer-Verlag,
2002.
Lhannaoui, H., Kabbaj, M.I., Bakkoury, Z., 2013.
Towards an approach to improve business process
models using risk management techniques. Intelligent
Systems: Theories and Applications (SITA), 8th
International Conference on 8-9 May 2013.
Martin-Guillerez, D., Guiochet, J., Powell, D. Zanon, C.,
2010. A uml-based method for risk analysis of human–
robot interactions. In 2nd International Workshop on
Software Engineering for Resilient Systems, pp. 32–
41.
McDermid, J., Nicholson, M., Pumfrey, D., Fenelon, P.,
1995. Experience with the application of HAZOP to
computer-based systems. In Computer Assurance.
COMPASS ’95. IEEE.
Ministry of Defence, 2000. HAZOP studies on systems
containing programmable electronics. Defence
Standard 00-58, Parts 1 and 2, Issue 2, May 2000.
Mock, R., Corvo, M., 2005. Risk analysis of information
systems by event process chains. International journal
of critical infrastructures, 1(2-3):247– 257.
Suriadi, S., Weiß, B., Winkelmann, A., ter Hofstede, A.,
Adams, M., Conforti, R., Fidge, C., La Rosa, M.,
Ouyang, C., Rosemann, M., Pika, A., Wynn, M., 2000.
Current Research in Risk-Aware Business Process
Management - Overview, Comparison, and Gap
Analysis, BPM Center Report BPM-12-13,
BPMcenter.org.
ICSOFT-EA2014-9thInternationalConferenceonSoftwareEngineeringandApplications
194
