
Implementation of Data Security Requirements in a Web-based
Application for Interactive Medical Documentation
Anja Perlich, Andrey Sapegin and Christoph Meinel
Hasso Plattner Institute, University of Potsdam
Prof.-Dr.-Helmert-Str. 2-3, 14440 Potsdam, Germany
Keywords:
Medical Documentation, Information Security, Mental Health Care, Client-Server Application, Patient Data.
Abstract:
Keeping data confidential is a deeply rooted requirement in medical documentation. However, there are in-
creasing calls for patient transparency in medical record documentation. With Tele-Board MED, an interactive
system for joint documentation of doctor and patient is developed. This web-based application designed for
digital whiteboards will be tested in treatment sessions with psychotherapy patients and therapists. In order to
ensure the security of patient data, security measures were implemented and they are illustrated in this paper.
We followed the major information security objectives: confidentiality, integrity, availability and accountabil-
ity. Next to technical aspects, such as data encryption, access restriction through firewall and password, and
measures for remote maintenance, we address issues at organizational and infrastructural levels as well (e.g.,
patients’ access to notes). With this paper we want to increase the awareness of information security, and pro-
mote a security conception from the beginning of health software research projects. The measures described
in this paper can serve as an example for other health software applications dealing with sensitive patient data,
from early user testing phases on.
1 INTRODUCTION
Keeping data confidential is a deeply rooted require-
ment in medical documentation. Nowadays, when pa-
tient records are increasingly kept in electronic form,
the number of data access paths rise. An analysis
of security breaches by industry in the United States
shows that in the health care sector, breaches of data
security have become common. Over a three-year pe-
riod, 115 breaches were reported (Curtin and Ayres,
2008).
Increasing calls for patient transparency in medi-
cal documentation and trends of sharing patient data
between medical institutions impose new challenges
of data security (van der Linden et al., 2009).
A recent literature review about security and pri-
vacy in electronic health records (EHR) shows that
more work needs to be done in terms of adopting to
security and privacy standards and directives. Even
though the sharing of medical data between stake-
holders is an integral part of the concept of EHR,
some 25% of the selected articles had no indication
on data encryption (Fern
´
andez-Alem
´
an et al., 2013).
We want to tackle the challenge of data security
from the beginning along with our research on the
proof-of-concept of an interactive medical documen-
tation system — Tele-Board MED. Its fundamental
idea is to let the patient co-document treatment ses-
sions together with the doctor. We investigate if dig-
ital whiteboards are a suitable medium for this pur-
pose. Giving the patient the right to actively con-
tribute to and manipulate the documentation system
also raises additional questions on data security.
Therefore, we have analyzed and implemented se-
curity measures to provide a secure environment for
both patients and doctors using our system and to
ensure the compliance with existing patient data pri-
vacy laws. In particular, this paper describes the secu-
rity measures of the interactive documentation system
Tele-Board MED by taking into account legal obliga-
tions as well as typical information technology secu-
rity objectives.
With this paper we want to increase awareness
of information security among health informatics re-
searchers, and promote a security conception from
the beginning of research projects. The measures de-
scribed in this paper were motivated from the setting
of an application server located in the network of an
ambulant psychotherapeutic clinic. Nonetheless, the
exemplary implementations of security guidelines can
352
Perlich A., Sapegin A. and Meinel C..
Implementation of Data Security Requirements in a Web-based Application for Interactive Medical Documentation.
DOI: 10.5220/0005204503520359
In Proceedings of the International Conference on Health Informatics (HEALTHINF-2015), pages 352-359
ISBN: 978-989-758-068-0
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

serve as a general example for health software appli-
cations dealing with sensitive patient data.
This paper is organized as follows. Section 2 pro-
vides details on the Tele-Board MED system and its
setup in the clinic network. In section 3 we ana-
lyze security criteria for this setup. Based on this,
we provide details on the implementation of the se-
curity policies in section 4; while section 5 describes
security measures for connected systems. Finally, the
paper closes with future work and conclusions in sec-
tions 6 and 7.
2 TELE-BOARD MED
During a treatment session at the doctor’s office the
patient usually does not get to see the notes which are
taken. Often they can only get a glimpse at illegible
handwriting or at the back of a computer screen.
In the scope of the research project Tele-Board
MED, we investigate how medical documentation can
be turned from a necessity taken care of by the doc-
tor, into a task that supports the patient’s recovery.
More specifically we try out whether digital white-
boards can be a suitable medium for joint documen-
tation for both patient and doctor, and we investigate
if this leads to higher personal engagement by the pa-
tient.
2.1 Therapist-patient Documentation in
Behavior Psychotherapy
The domain of application and testing is behavior psy-
chotherapy, since here the patient’s verbal contribu-
tion is higher compared to, e.g., cancer treatment.
Moreover, the treatment outcome very much depends
on the patient’s personal engagement and the patient-
therapist relationship (Lambert, 2013).
Tele-Board MED is being developed as an adjunct
to the traditional face-to-face therapy to allow a joint
documentation of the session’s therapeutic content.
Figure 1 shows a user scenario with a digital white-
board to display and operate the documentation panel
via touch gestures. Additionally, tablet computers are
used as input devices.
The system is being tested at a major German out-
patient clinic for psychotherapy with about 200 ther-
apists.
2.2 General Setup and Software
Components
Tele-Board MED is a web-based application acces-
sible from common web browsers. It is designed
Figure 1: A doctor-patient scenario: Using Tele-Board
MED in a therapy session.
to enable interactions with digital whiteboard panels,
e.g., drawing with digital pens, erasing pen strokes,
and writing, posting, arranging and clustering sticky
notes. Nonetheless, it can be used on a normal screen
with mouse and keyboard input as well.
With Tele-Board MED we build upon Tele-Board,
a whiteboard system designed to support remote col-
laboration in distributed design thinking teams (Gu-
mienny et al., 2011). In Tele-Board, there are four
main software components: the web portal, the white-
board client, the sticky note pad application and the
server component. The web portal is a web appli-
cation which serves as the user’s entry point to the
system. It provides a platform to manage the white-
board panels. The actual work on a panel happens
in the whiteboard client, a Java application launched
from the web portal via Java Web Start. The sticky
note pad app allows sending digital sticky notes from
mobile devices, e.g., tablets, to the whiteboard. The
server component contains the database (MySQL
1
),
a web server (Apache HTTPD
2
), and a collaboration
server for the synchronization of the whiteboard panel
elements (Openfire
3
).
The system architecture with the different devices
linked to the software components is shown in figure
2. The whiteboard client can be operated on digital
whiteboards as well as on a laptop. Sticky notes can
also be created and sent to the whiteboard via the web
portal and the sticky pad app.
1
http://www.mysql.com
2
http://httpd.apache.org
3
http://www.igniterealtime.org/projects/openfire
ImplementationofDataSecurityRequirementsinaWeb-basedApplicationforInteractiveMedicalDocumentation
353

Figure 2: Software system architecture, adapted from (Gu-
mienny et al., 2013).
In order to allow collaboration over distances,
Tele-Board is accessible via the World Wide Web. For
the pilot application in psychotherapy sessions how-
ever, we do not make use of the remote collabora-
tion feature. That is, patient and therapist are in one
room and they are the only persons documenting on
the whiteboard panel.
2.3 Integrating the Tele-board MED
Server in the Clinic Network
Protecting the patient data is the clinic’s topmost pri-
ority. This is why it was no option to locate the server
in a remote location, such as the research institution.
Though this setup would have had the advantage of
performing the technical maintenance locally.
In any case, in order to test Tele-Board MED with
patients, the server holding the data had to be located
in the clinic’s premises and not be publicly available
through the internet. Therefore, we have set up a
dedicated Tele-Board MED server and connected it
to the clinic network. Our setup includes the physi-
cal server (running Ubuntu GNU/Linux 12.04 Server)
and the Tele-Board MED server component, includ-
ing the database (cf. subsection 2.2). Additionally
there is a NAS
4
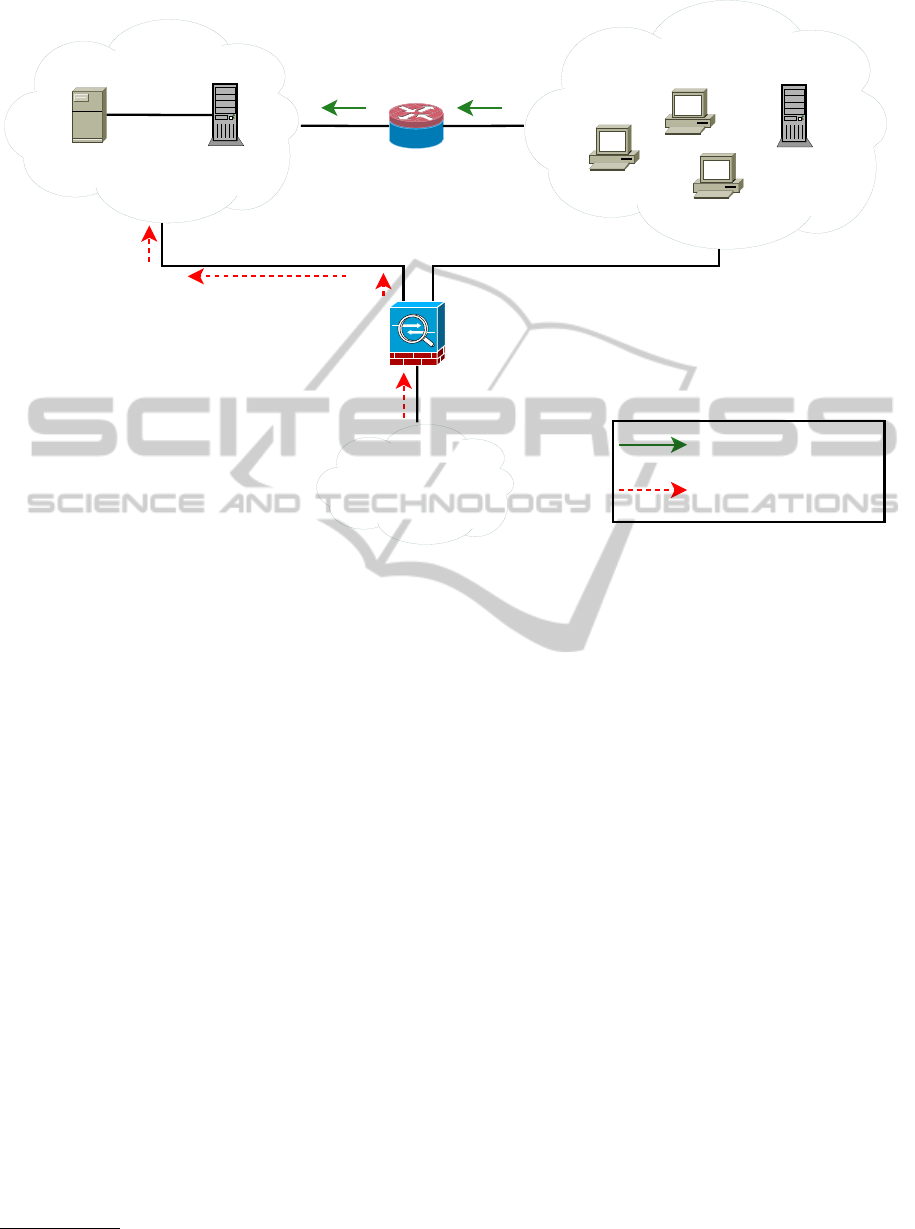
for data backups. Figure 3 shows the
integration of our setup into the network.
The Tele-Board MED components are located in
a dedicated subnet, where all connections can be con-
trolled. In order for therapists to log into the Tele-
Board MED application they need to be connected
to the clinic network. However, for security reasons,
connections initiated by the Tele-Board MED server
into the internal network are blocked using a router
with a firewall.
Thus, our setup is separated from the main net-
work, but allows connections from the therapists’
computers as well as remote maintenance for admin-
istrators (cf. section 5). In the following sections
4
Network-attached storage
the security measures of this setup are discussed in
greater detail.
3 DATA SECURITY CRITERIA
The need for the protection of private patient data has
its roots in the medical profession itself. The pro-
fessional code of secrecy states that everybody who
works in health services has to keep strictly confi-
dential all information obtained concerning the pa-
tient. Data privacy shall guarantee that everybody can
decide which data is gathered about him or her, for
which purpose, and to whom it is transferred (Leiner
et al., 2009).
Since patient cases are documented with Tele-
Board MED, the protection against information secu-
rity breach is crucially important. In the results of
a feedback study about Tele-Board MED with ther-
apists, we found one skeptical group of therapists,
mainly concerned about data security issues (von
Thienen et al., 2015). The dialogue with the cooper-
ating clinic’s directors also disclosed general worries
concerning data security.
Therefore, in our project we strictly adhere to the
legal obligations and ensure that our setup meets the
general information security objectives, as described
in the following subsections.
In this context, it is worthwhile mentioning the
standardization of security measures according to the
ISO 27000 series. The ISO 27001 standard in par-
ticular is the specification for an information security
management system and its integration into business
processes. The standard implies not only the presence
of properly configured security tools, but also care-
ful planning and implementation of security policies
within different departments of a company. (Pelnekar,
2011). Yet, this goes beyond the mandatory require-
ments and is out of proportion to our research project.
3.1 Legal Obligations
In countries of the European Union, the statutory reg-
ulations are geared to the data protection directive
(European Parliament and the Council of the Euro-
pean Union, 1995). Every documentation system
especially in the sensitive healthcare domain has to
comply with the demands on confidentiality and data
security.
In Germany, the legal foundation is the Federal
Data Protection Act
5
. Based on this law, the German
5
German: Bundesdatenschutzgesetz, BDSG, 1990
HEALTHINF2015-InternationalConferenceonHealthInformatics
354
Internet
Tele-Board MED
server
NAS for
data backup
Clinic firewall / VPN
Router with
firewall
Clinic network
Tele-Board MED network
Connection for
remote maintenance
Connection from clients
Figure 3: Connection of the Tele-Board MED server to the clinic network.
Medical Association
6
issued recommendations about
data privacy and data processing in a doctor’s office.
Specifically the technical appendix (German Medical
Association, 2008) provides an overview of the secu-
rity measures to be set up in medical practices.
3.2 Information Security Objectives
General security objectives and measures with regard
to web-based health care applications are described
by (Roehrig and Knorr, 2000). In addition to the so-
called CIA requirements for communication security
(confidentiality, integrity, availability), they also em-
phasize accountability as the fourth major security ob-
jective of computerized health care applications.
• Confidentiality. To keep data confidential means
to protect it from unauthorized disclosure. In
healthcare, confidentiality is considered the most
important information security objective since
medical data is highly sensitive.
• Integrity. Integrity means making sure that data
is not tampered with and that it is what it is sup-
posed to be. Compromised data integrity in health
care can, for instance, lead to medical malprac-
tice.
6
German: Bundes
¨
arztekammer
• Availability. A system is called available when
the required data and services are delivered within
an acceptable period of time. A computerized
system taking too long to respond, e.g., due to
overload or collapse, can delay the therapy and
at worst be life-threatening for a patient.
• Accountability. If the accountability of a system
is guaranteed, every participant of a communica-
tion can be sure that the partner (e.g., person or
machine) is the one purported to be. In healthcare
it is important to know who performed which ser-
vice at which time in order to hold users responsi-
ble for their actions.
4 REALIZATION OF SECURITY
MEASURES
The starting point for the implementation of security
measures was the technical appendix of the recom-
mendations (German Medical Association, 2008) (cf.
section 3.1). We have implemented these recommen-
dations in our setup and provide an overview in table
1. It shows the relevant excerpts of the recommenda-
tions together with short descriptions of the practical
application.
At this point we want to briefly comment on
ImplementationofDataSecurityRequirementsinaWeb-basedApplicationforInteractiveMedicalDocumentation
355

how the therapists’ perception of data security risk
changed. In a feedback study carried out in 2013
concerns about data security were particularly pro-
nounced (von Thienen et al., 2015). After a follow-
up presentation to the therapists on the system devel-
opment progress and the implemented security mea-
sures, they were asked to fill in a feedback question-
naire. The results show that none of the therapists had
concerns about data security. We can conclude that
the awareness about and actions taken for higher data
security led to a more confident feeling about using
Tele-Board MED in treatment sessions.
We now describe the implemented measures in
more detail according to the information security ob-
jectives listed in section 3.2.
4.1 Confidentiality Measures
Technical confidentiality measures have been imple-
mented at application as well as at hardware-near lev-
els.
To ensure security of the data transferred to and
from users, the web portal only allows SSL
7
con-
nections, which are encrypted. The login to the
web portal and the sticky pad application requires
user name and password, and is implemented us-
ing the form-based authentication mechanism by the
CakePHP framework
8
. Access control lists (ACLs)
are used to regulate more specific access to parts of
the web portal.
In order to prevent physical access to the data, the
server’s hard disk’s data partition is encrypted
9
(cf.
table 1, #9).
To separate patient records from each other, the
web portal provides a treatment session mode with
restricted view (cf. table 1, #1). When a session is
running for a certain patient, the files of other patients
are hidden in the web portal. Every action is logged,
such as starting and stopping a treatment session, or
operating the whiteboard panel content.
In addition to technical measures, we also im-
plemented organizational confidentiality measures,
namely the non-disclosure agreement signed by the
researchers (cf. table 1, #4), the instructions on re-
quirements of password characteristics (cf. table 1,
#7), and the limitation of the application’s user ac-
counts to therapists. Therefore, the patient does con-
tribute to the documentation, but only if the therapist
is present. However, there are export features so that
patients can receive a copy of their data (cf. table 1,
7
Secure Sockets Layer
8
http://www.cakephp.org
9
We used the Advanced Encryption Standard (AES)
with a 256-bit key, and RIPEMD-160 hash algorithm.
#2). Accounts are given out to therapists at the clinic
only after personal introduction.
4.2 Integrity Measures
The integrity of the patient data could be harmed
by unauthorized manipulation through the web por-
tal and whiteboard client, or at database level. Each
transaction in the Tele-Board MED application is
logged in the database. Furthermore, a former white-
board panel state can easily be recovered with the help
of the history function. Deleted elements are only
marked as deleted but are never completely erased.
In order to prevent data manipulation at database
level the server itself and the database are password-
protected.
4.3 Availability Measures
The server’s configuration was chosen according to
the maximal expected capacity utilization. To pre-
vent the server from being attacked, and services and
data from being unavailable, we set up a firewall (cf.
table 1, #8). The only ports which are open for re-
quests from outside of the server are the ones for the
protocols SSH
10
(for remote maintenance), HTTPS
11
(for access to web portal), and XMPP
12
with SSL (for
the synchronization of panel elements in whiteboard
client sessions). The database port is only open for
requests from inside of the server.
In case of a data loss on the server, the backup can
be used to reconstitute the data availability (cf. table
1, #11). Backups of the database and other personal
data, e.g., images, are done on a daily basis in an au-
tomated way using a backup script. Every time the
complete data is packed in an archive and encrypted
using the asymmetric encryption method RSA
13
.
Another measure for redundancy in data storage
on the server is RAID 1
14
. In case of disk failure,
the server could continue operating in degraded mode
using the mirrored hard disk until the failed one is
replaced.
Finally, the server has a dual power supply and is
connected to a Uninterruptible Power Supply (UPS)
unit to resist short-term power interruptions.
10
Secure Shell
11
Hypertext Transfer Protocol Secure
12
Extensible Messaging and Presence Protocol
13
named after the inventors Rivest, Shamir and Adleman
14
redundant array of independent disks – mirroring
HEALTHINF2015-InternationalConferenceonHealthInformatics
356
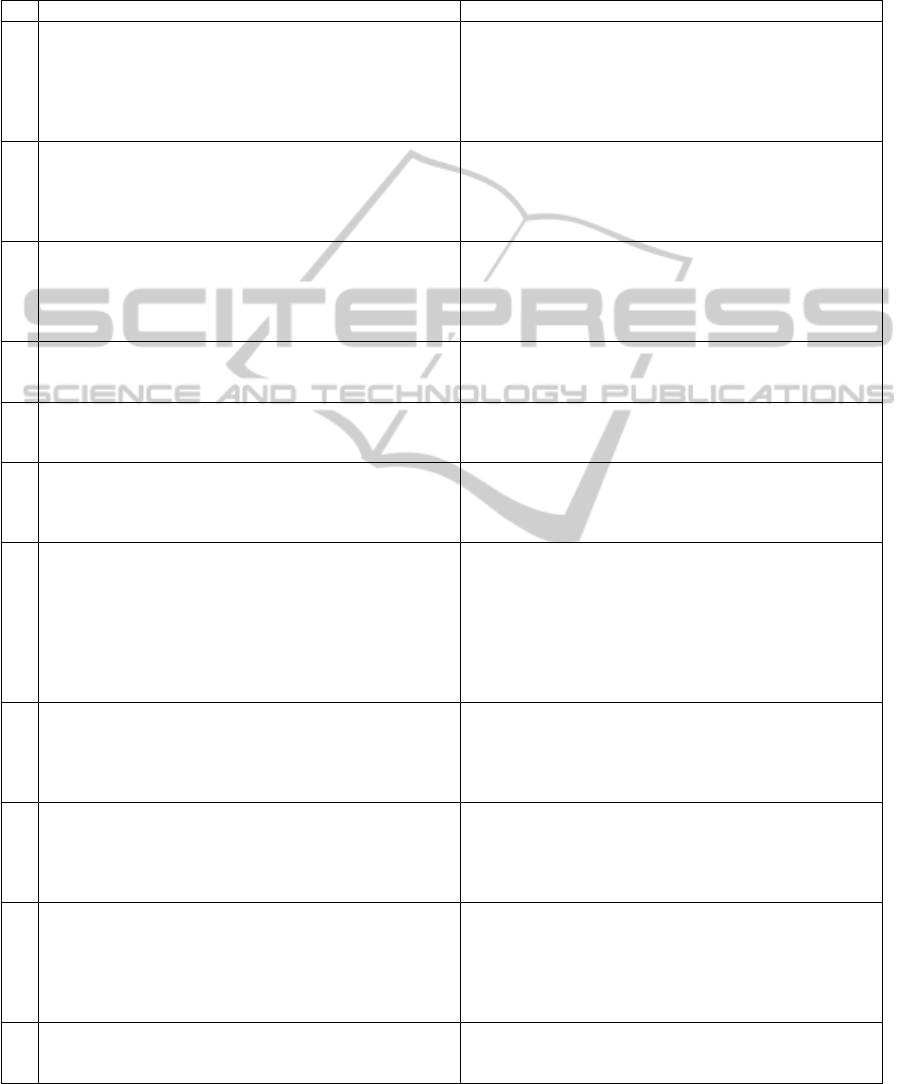
Table 1: Translated excerpt from the recommendations (German Medical Association, 2008) and corresponding security
measures in Tele-Board MED.
# Recommendation excerpt Realization
1
“Patient files should in no case be placed in a way that
patients can view files of other patients.” (section 4.2)
A treatment session mode was implemented.
Switching to this mode requires an additional
authentication. When a doctor starts a session for a
patient in the web portal, the other patient files are
hidden, and only documents are shown which belong
to the current patient.
2
“In no case should the patients by themselves have the
possibility to operate the doctor’s computer.
Nonetheless, printouts or a digital copy of the doctor’s
notes transferred via secure electronic communication
should be provided.” (s. 5.1)
Patients do not get login credentials, and can only
access the data in the presence of the doctor. The
doctor has the possibility to export data (e.g., as a
picture or into common office formats) and hand over
printouts (or digital copies) to a patient.
3
“As far as there is no authorization or justification, a
transmission of personal data is only allowed if there is
an explicit or implicit patient consent. This consent
must refer to the concrete transmission process.” (s.
5.2)
The patient is informed in a written form about the
project Tele-Board MED and signs a patient consent
for explicitly described purposes of data handling.
4
“In a contractual relationship the contractor and
authorized co-workers have to commit their
confidentiality in a written consent.” (s. 6)
The researchers involved in the Tele-Board MED
project sign the privacy policy of the cooperating clinic.
5
“All (remote) maintenance activities as well as the
name of the performing person have to be
documented.” (s. 6)
Log files are created automatically on the server. A log
file contains the timestamps, types and authors of every
access.
6
“In remote maintenance, the data transfer between the
doctor’s computer and the technician’s computer has to
be encrypted and should only be done via a secured
connection.” (technical appendix, s. 10)
The remote maintenance is done via a
password-protected VPN connection and the SSH
protocol which allows encrypted connection only.
7
“A password should be longer than seven characters,
should not be listed in dictionaries and should not
consist of names or personal data (e.g., date of birth).
Furthermore it should contain special characters (e.g.,
$, #, ?, *, &) and/or numerical digits. If special
characters or numerical digits are used, common
variations, such as adding them at the beginning or
end, should be avoided.” (technical appendix, s. 2.1)
The Tele-Board MED web portal is only accessible via
HTTPS, and the access is password-protected. The
users are instructed to change the default password as
soon as possible and to choose a password according to
the requirements.
8
“For individual computers, the installation of a
so-called personal firewall [...] provides a basic
protection; Unix-like systems (e.g., Linux or Mac OS
X) should be run with their own firewall mechanisms.”
(technical appendix, s. 3.1.3)
The server’s firewall was configured so that only those
ports are opened which are absolutely necessary.
9
“The storage media used in the doctor’s practice
holding patient data, e.g., notebooks and PDAs, must
be completely encrypted, in order to avoid abuse of
sensitive data in the case of a theft.” (technical
appendix, s. 5)
The Tele-Board MED server’s hard disk was encrypted.
In case of a theft the data on the server cannot be read
without the possession of the encryption key, which is
stored on a data carrier in a physically safe place.
10
“The doctor’s notes have to be retained for a period of
ten years after the treatment’s completion.” (s. 4.3)
The duration of the research cooperation is limited.
The responsibility for the long-term storage resides
with the psychotherapy clinic. There are several
possibilities of downloading data from the Tele-Board
MED server, e.g., as a database dump, or as a Word or
image file export.
11
“In order to ensure the protection of patient data, daily
backups should be created on suitable external media.”
(s. 6)
The Tele-Board MED server creates encrypted
database backups daily and stores them on the
network-attached storage.
ImplementationofDataSecurityRequirementsinaWeb-basedApplicationforInteractiveMedicalDocumentation
357

4.4 Accountability Measures
Accountability measures concern the communication
at operating system and application level.
In order to guarantee that the machine the client
is communicating with is the Tele-Board MED server
and no other machine, an X.509 certificate is used.
The certificate not only makes it possible to verify the
server’s identity, but also to establish an encrypted
communication channel between the server and the
client via HTTPS. This certificate was issued by a
certificate authority (CA) being part of a public key
infrastructure (PKI). The CA is the affiliated univer-
sity which is in turn trusted by the German National
Research and Education Network
15
.
The whiteboard client code is signed with a code
signing certificate, which makes it possible to verify
that the source code originates from the declared de-
velopers. A combination of the code’s verified origin
and its encrypted transmission give evidence of the
code’s authenticity.
The crucial factor for accountability at client side
is a conscious handling of login data. If the user cre-
dentials fall into the wrong hands, anybody can pre-
tend to be a certain user. An accountability breach of
unauthorized web portal access using someone else’s
user name and password, can be detected based on
database entries. The IP address, the web browser and
operating system version of the accessing computer
together with timestamps of start and end of the con-
nection are saved. Access to the server is also logged
at operating system level (cf. table 1, #5).
5 SECURING THE PERIMETER
The mentioned measures are related to securing the
Tele-Board MED server itself. But the security of the
data stored on the server also depends on the secu-
rity of the clients. For example, if the doctor’s com-
puter is compromised, one could connect through it to
the Tele-Board MED server and access the data. An-
other example would be a physical access to the server
hardware. In spite of the hard disk encryption, an at-
tacker could steal the server and influence its avail-
ability. Finally, the computers used by the researchers
for server maintenance could also be an entry point
for the attacker.
In order to protect the data stored on the server
against unauthorized access we also ensured the se-
curity of the network perimeter:
15
German: Deutsches Forschungsnetz (DFN)
• Network Security and Physical Access. Since
the Tele-Board MED server is located in the clinic
building and connected to the clinic network, the
security of the network and prevention of phys-
ical access to the hardware was delegated to the
clinic’s information technology department.
• Security of Remote Maintenance Connection.
To ensure that the data cannot be leaked during
the remote maintenance procedure, we secured
the connection to the server. Via an encrypted
VPN
16
connection we connect to the server over
SSH with public-key authorization. The remote
maintenance is only allowed from a dedicated lap-
top
17
and the VPN connection can only be estab-
lished from a specific range of IP addresses (from
inside the research institute’s network). Besides
that, all researchers involved in the project have
signed the clinic’s privacy policy.
6 FUTURE WORK
The steps offered for securing patient data ensure only
a minimal level of data security. However, this basic
implementation complies with the legal regulations of
the Federal Data Protection Act and provides an ad-
equate environment for short-term testing of medical
information systems such as Tele-Board MED.
For a long-term operation a higher security level is
recommended. The following measures can be used
to enhance the security:
• Database integrity checks can be realized via
checksums. Periodically, checksums from the
database tables containing patient data are calcu-
lated (using a cryptographic hash function) and
stored on an external medium. To check the in-
tegrity, a checksum of the current database state
is recalculated, and compared to the latest stored
one. If they match, there is a high probability that
no change has occurred.
• Password brute-force protection tools such as
Fail2ban
18
, allow to automatically block users,
who try to guess the password for the web appli-
cation repeatedly.
• Continuous monitoring allows ensuring the
availability of all critical services. Tools such
as Nagios periodically check running services for
their status and availability (Josephsen, 2007).
16
Virtual Private Network
17
The laptop also has a configured firewall and is used
only for the maintenance of Tele-Board MED.
18
http://www.fail2ban.org
HEALTHINF2015-InternationalConferenceonHealthInformatics
358

The Tele-Board MED server’s availability could
be checked by a request from inside the clinic
network. Incidents of e.g., hard disk failure, can
then be reported automatically by using an inter-
nal mail server.
• Automated security scans performed with a spe-
cial software, e.g., Nessus,
19
allow to check the
infrastructure for vulnerabilities on a regular ba-
sis. These checks provide feedback for the person
responsible for security updates of the involved
systems.
The mentioned measures and tools allow an auto-
mated prevention and detection of security threats,
and therefore improve the protection and simplify the
management of security events for the monitored sys-
tem. However, the presence of such tools still does
not guarantee that a system is fully secure.
7 CONCLUSION
In this paper we illustrated the realization of security
measures in our system Tele-Board MED in order to
create conditions which shall enable user tests involv-
ing patients in a psychotherapy clinic.
The described security issues concern technical,
infrastructural, personal as well as organizational lev-
els. In order to cover these aspects as comprehen-
sively as possible we took into account several refer-
ences such as legal obligations and general informa-
tion security objectives.
The more comprehensive the security measure
catalogue gets, the higher the security level is. Yet,
an absolute guarantee can never be reached.
The focus in research projects on new applications
or concepts of human computer interaction, is often
on functional features and their usage. Nevertheless,
if such projects involve sensitive data, an integrated
security concept is recommended from the beginning.
Even if it is about early user tests, sensitive personal
data is worthwhile protecting.
We hope that the measures described in this pa-
per can serve as an example for other health software
research projects dealing with sensitive patient data.
ACKNOWLEDGEMENTS
The work of this project was funded by the HPI-
Stanford Design Thinking Research Program.
19
http://www.nessus.org
REFERENCES
Curtin, C. M. and Ayres, L. T. (2008). Using Science to
Combat Data Loss: Analyzing Breaches by Type and
Industry. I/S: A Journal of Law and Policy for the
Information Society, 4:566–598.
European Parliament and the Council of the European
Union (1995). Directive 95/46/EC of the european
parliament and of the council of 24 october 1995 on
the protection of individuals with regard to the pro-
cessing of personal data and on the free movement of
such data. Official Journal of the European Union,
L281:0031–0050.
Fern
´
andez-Alem
´
an, J. L., Se
˜
nor, I. C., Lozoya, P.
´
A. O., and
Toval, A. (2013). Security and privacy in electronic
health records: A systematic literature review. Journal
of Biomedical Informatics, 46(3):541–562.
German Medical Association (2008). Empfehlungen zur
¨
arztlichen Schweigepflicht, Datenschutz und Daten-
verarbeitung in der Arztpraxis - Technische An-
lage. http://www.bundesaerztekammer.de/downloads/
Schweigepflicht Tech Anlage 2008.pdf.
Gumienny, R., Gericke, L., Quasthoff, M., Willems, C., and
Meinel, C. (2011). Tele-Board: Enabling efficient col-
laboration in digital design spaces. Proceedings of the
International Conference on Computer Supported Co-
operative Work in Design (CSCWD), pages 47–54.
Gumienny, R., Gericke, L., Wenzel, M., and Meinel, C.
(2013). Supporting creative collaboration in globally
distributed companies. CSCW ’13, pages 995–1007.
ACM.
Josephsen, D. (2007). Building a Monitoring Infrastructure
with Nagios. Prentice Hall PTR, Upper Saddle River,
NJ, USA.
Lambert, M. J. (2013). Bergin and Garfield’s Handbook of
Psychotherapy and Behavior Change. John Wiley &
Sons.
Leiner, F., Gaus, W., Haux, R., Knaup-Gregori, P., and
Pfeiffer, K.-P. (2009). Medizinische Dokumenta-
tion: Grundlagen einer qualit
¨
atsgesicherten integri-
erten Krankenversorgung ; Lehrbuch und Leitfaden.
Schattauer.
Pelnekar, C. (2011). Planning for and Implementing ISO
27001. ISACA Journal, 4:28–35.
Roehrig, S. and Knorr, K. (2000). Towards a Secure Web
Based Health Care Application. Proceedings of the
European Conference on Information Systems (ECIS),
pages 1323–1330.
van der Linden, H., Kalra, D., Hasman, A., and Talmon,
J. (2009). Inter-organizational future proof EHR sys-
tems. A review of the security and privacy related is-
sues. International journal of medical informatics,
78(3):141–60.
von Thienen, J. P. A., Perlich, A., and Meinel, C.
(2015). Design Thinking Research. Building Innova-
tors, chapter Tele-Board MED: Supporting Twenty-
First Century Medicine for Mutual Benefit. Springer.
ImplementationofDataSecurityRequirementsinaWeb-basedApplicationforInteractiveMedicalDocumentation
359
