
A Novel Anonymous Authenticated Key Agreement Protocol for
Vehicular Ad Hoc Networks
Carsten Büttner
1
and Sorin A. Huss
2
1
Advanced Technology, Adam Opel AG, Rüsselsheim, Germany
2
Integrated Circuits and Systems Lab, Technische Universität Darmstadt, Darmstadt, Germany
Keywords:
Anonymous Authentication, Vehicular Ad-hoc NETworks, Key Agreement, Ring Signatures.
Abstract:
Privacy in Vehicular Ad-hoc NETworks (VANETs) is one of the most important issues to attract users to this
new technology. In this paper we propose a novel protocol that allows vehicles using the same application in a
VANET to agree on an encryption key to exchange confidential data while preserving the privacy. We do this
by combining the Elliptic Curve Integrated Encryption Scheme (ECIES) with ring signatures and we evaluate
the protocol with respect to the privacy of the vehicle. These results clearly demonstrate that the privacy of
vehicles can be preserved while reducing considerably the number of necessary pseudonyms in comparison to
exploiting ECIES only.
1 INTRODUCTION
For safety reasons vehicles in Vehicular Ad-hoc NET-
works (VANETs) use broadcast over ITS-G5 to in-
form other vehicles in the communication range about
their current status, including position, heading and
speed. All safety messages are digitally signed to
prove the integrity of the message and eligibility of
the sender. Since every participant shall receive and
interpret these messages as fast as possible, they are
in general not encrypted. Besides this safety relevant
communication, there are other applications available
where the data exchanged between vehicles is confi-
dential and therefore needs to be encrypted.
Consider a service provider that collects data
about potholes on roads in a certain area. Vehicles
thus record data about potholes and report it to the
service provider, which offers the data to other service
providers or local administrations. However, the data
sent to the service provider contains privacy related
data like the location of the pothole and a coarse time,
when it was detected. If all vehicles would simply
sent their detected data to the service provider, then
this entity may create movement profiles of the vehi-
cles from the reported data. In order to preserve the
privacy of its users and to advertise the privacy con-
siderations, the service provider decides to implement
a privacy preserving mechanism. This mechanism re-
quires that the vehicles exchange their collected data
between each other prior uploading. When using this
mechanism the vehicles report pothole locations de-
tected by other vehicles too. Therefore, the service
provider can no longer determine where a specific ve-
hicle was driving at the given point in time and can no
longer create movement profiles of this vehicle. The
service provider may decide to use the ETSI ITS-G5
network to exchange the data between the vehicles,
because it is free of charge. In addition, the service
provider enforces an encrypted data exchange policy,
so no attacker can record and sell the collected data
next to the service provider. The exchange of the en-
crypted data shall also be privacy preserving.
There are three problems to be considered, when
confidential data is being exchanged between vehi-
cles: (i) How does a vehicle ensure whether the other
vehicle is eligible to receive confidential data? (ii)
How do vehicles exchange the key for encrypting the
communication data? (iii) How can the first two prob-
lems be solved while preserving the privacy of the ve-
hicles?
For safety-related communications in VANETs
each vehicle uses a pseudonym to sign all messages.
To ensure the privacy of the vehicle the pseudonym is
changed on a regular basis, so that two pseudonyms
cannot be linked to the same vehicle. Of course, a
vehicle might simply use an own set of pseudonyms
for each application by encoding the application into
the pseudonym, and exploit well-known key agree-
ment protocols like the Elliptic Curve Integrated En-
cryption Scheme (ECIES) as standardized in (IEEE
259
Büttner C. and A. Huss S..
A Novel Anonymous Authenticated Key Agreement Protocol for Vehicular Ad Hoc Networks.
DOI: 10.5220/0005238902590269
In Proceedings of the 1st International Conference on Information Systems Security and Privacy (ICISSP-2015), pages 259-269
ISBN: 978-989-758-081-9
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

1609.2, 2013) to authenticate against each other and
finally to agree on an encryption key. However, the
vehicle then needs to change its pseudonym for the
application at hand at the same time as the one in-
tended for safety-related communication to prevent
linking of pseudonyms. This introduces a cost over-
head both for additional secure storage for the private
keys and for the data transmission aimed to obtain
new pseudonyms. Therefore, we propose in the se-
quel a novel protocol that solves all three outlined
problems and at the same time reduces the number
of necessary pseudonyms in comparison to exploiting
ECIES only. In order to do so we pick up the concept
of k-anonymity (Sweeney, 2002), combine ring sig-
natures (Rivest et al., 2001) with the ECIES scheme
and evaluate the resulting protocol with respect to the
privacy of the vehicles.
The rest of this paper is organized as follows: In
Section 2 we discuss the term of application-specific
pseudonyms. The state of the art of anonymous au-
thenticated key agreement protocols is reviewed in
Section 3. We then introduce the new anonymous au-
thentication scheme in Section 4. The evaluation of
this protocol is presented in Section 5. Finally, we
conclude the paper in Section 6.
2 APPLICATION-SPECIFIC
PSEUDONYMS
Each vehicle participating in a VANET is equipped
with a set of certificates to sign safety messages.
These certificates are named pseudonyms, since they
do not leak the identity and therefore preserve the pri-
vacy of the vehicle. In this paper we assume that each
application such as the outlined pothole detection ser-
vice issues its own pseudonyms, thus proving that the
owner of the corresponding private key is eligible to
run the application. So, only vehicles equipped with a
valid pseudonym can get access to it. We name such
pseudonyms application-specific pseudonyms.
An unique identifier is assigned to each applica-
tion in order to determine which pseudonym belongs
to which application. In case that this identifier is
also part of the pseudonym, the application can check,
whether the pseudonym is eligible to use the service.
Pseudonyms used in VANETs contain an ITS Appli-
cation ID (ETSI TS 103 097, 2013), which may be
exploited for this purpose.
3 RELATED WORK
The IEEE Standard 1609.2 for Wireless Access in
Vehicular Environments (IEEE 1609.2, 2013) uses
the hybrid encryption scheme ECIES to encrypt mes-
sages between vehicles. In ECIES both parties agree
on a key to encrypt and exchange an AES key. This
AES key is later on used to encrypt the exchanged
data. However, since it is necessary that the vehi-
cles change all their identities each time the safety
pseudonym changes, one set of pseudonyms with the
same size as the one for safety messages would be
necessary for each single application to prevent link-
ing pseudonyms. We reduce the size of the sets nec-
essary for each application by combining ECIES with
ring signatures.
Ring signatures based on RSA and Rabin’s sig-
nature scheme have been introduced in (Rivest et al.,
2001). In order to create a signature, the signer takes
in addition to his own private key the public key of
n other entities to sign the message. To verify the
message, the public key of the signer and the n pub-
lic keys of the other entities are necessary. The veri-
fier of a ring signature cannot distinguish who of the
n +1 entities actually signed the message because the
probability of each signer equals to 1/(n + 1). The
authors of (Lin et al., 2007) propose ring signatures
for anonymous routing in wireless ad-hoc networks,
but they did not evaluate related ring building strate-
gies nor the size of the protocol nor multiple own
pseudonyms. In (Freudiger et al., 2009) the authors
advocate ring signatures in mobile ad-hoc networks
for authentication of neighbor nodes. They did inves-
tigate ring building strategies, but most of their strate-
gies require either a central server or the nodes have
to be a-priori aware of the pseudonyms of all other
nodes. In addition, these authors only considered the
case where each node has just one pseudonym and
elaborated a general formula to calculate the trans-
mission overhead, but they did not evaluate their sug-
gestion.
Secret Handshakes (Balfanz et al., 2003; Castel-
luccia et al., 2004) are used to identify secretly if two
persons belong to the same group. Even if the hand-
shake fails, both parties cannot retrieve the group of
the opposite. Accordingly, a third party is never able
to retrieve the affiliation of a participant to a group.
To reach unlinkability between different handshakes,
a different pseudonym has to be used for each hand-
shake. Otherwise an attacker may eventually link dif-
ferent handshakes to one user. This method is sim-
ilar to the usage of ECIES in VANETs with regu-
lar pseudonym changes. However, we aim to sig-
nificantly reduce the amount of required pseudonyms
ICISSP2015-1stInternationalConferenceonInformationSystemsSecurityandPrivacy
260

compared to this method.
Group Signatures (Chaum and Heyst, 1991) allow
a member of a group to create a signature on behalf of
the group. The verifiers can only prove that the signa-
ture was created by a member of the group but not by
whom. Unfortunately, group signatures are not suit-
able for the envisaged scenario, because each time a
user leaves the group, new credentials have to be dis-
tributed to all group members. This property obstructs
in our case the scalability of the approach because of
the high probability that multiple vehicles leave the
group every day. More over, we cannot assume that
all vehicles are quipped with mobile communication
devices to obtain the required information from the
central entity.
An Anonymous Credential (Camenisch and
Lysyanskaya, 2001) is a set of attributes issued by
a trustworthy entity. An user can prove a subset of
her attributes to a verifier without revealing her iden-
tity, whereas several proofs cannot be linked. Again,
Anonymous Credentials are not suitable in our case,
because they require a regular connection to a cen-
tral entity to get revocation information. As before,
we cannot assume that all vehicles have a connection
to a central entity, because we cannot assume that all
vehicles are equipped with a mobile communication.
In addition proofs of attributes show a high computa-
tional complexity and do not establish an encryption
key.
Matchmaking Protocols (Baldwin and Gramlich,
1985) are intended to authenticate two members of the
same group without revealing their group to others.
However, this scheme does not hide the identity of the
members, it hides only the group they are a member
of. In contrast, we need to hide the identity of the
members and not of the group.
K-anonymity as defined in (Sweeney, 2002) pro-
vides a metric to measure the anonymity of a subject,
where k denotes the number of subjects it is indistin-
guishable from. This metric will be exploited in the
sequel for the envisaged scenario.
4 ANONYMOUS
AUTHENTICATION
In this section we first specify the requirements of the
anonymous authenticated key agreement protocol and
then present it in detail. We also characterize possi-
ble attacks and comment on the protocol parameters
considered so far.
An anonymous authenticated key agreement pro-
tocol allows two parties, who are members of the
same group, to establish a confidential communica-
tion. To achieve this goal, both parties have to agree
on a session key to encrypt the exchanged messages.
The identity of the other party is unknown at the be-
ginning of the protocol and both parties are not will-
ing to expose for privacy reasons their application-
specific identity to anyone. In addition, it shall be
possible to revoke access for single parties and only
members of the same group shall be able to agree on
the session key. The protocol shall fail, if one party is
not a member of the group. Not eligible parties shall
gain as few information as possible about the other
party. We only consider single-hop connections, be-
cause multi-hop connections are difficult to maintain
in VANETs due to frequent topology changes.
4.1 Protocol
The advocated anonymous authenticated key agree-
ment protocol takes the ECIES scheme and combines
it with ring signatures. Such a signature is intended to
sign the transmitted ECIES parameters. By combin-
ing ECIES with ring signatures, the vehicles agree on
a symmetric encryption key as standardized in (IEEE
1609.2, 2013) and bind this key to a specific appli-
cation with the help of a ring signature created with
application-specific pseudonyms. This generic ap-
proach has the advantage that the vehicles can use
the safety identities already known to each other for
ECIES and hide the application-specific identity by
means of ring signatures. So, it is no longer possible
to identify the entity which actually created the sig-
nature. The only information to be derived points to
the set of pseudonyms present in the ring. Therefore,
the application-specific pseudonyms can be reused af-
ter a pseudonym change without any link to safety
pseudonyms. As a consequence, less application-
specific pseudonyms are necessary. We exercise the
ring signature scheme based on elliptic curves as pro-
posed in (Lin et al., 2007). We favor this scheme,
since elliptic curves provide the same security level
with a much shorter signature length compared to
RSA. In addition, we propose a second version of
the protocol, where the pseudonyms of the ring sig-
nature are encrypted together with the signature. We
denote these protocol versions as non-encrypted and
encrypted, respectively.
We introduce the following notation for the de-
scription of the protocol: ServiceAnnouncement de-
notes a service announcement according to (ETSI TS
102 890-2, 2010). V , C and T are defined according
to (IEEE 1609.2, 2013). V is the public key of the
sender, the parameter C is the symmetric AES key K
encrypted by ECIES, while T denotes the authentica-
tion tag of ECIES. The pseudonym of entity X is de-
ANovelAnonymousAuthenticatedKeyAgreementProtocolforVehicularAdHocNetworks
261

noted as Cert
X
. The ring signature consists of n differ-
ent pseudonyms Cert
Xn
, where one is an application-
specific pseudonym of the respective signer and the
others are collected application-specific pseudonyms.
The values x
Xn
are necessary to validate the ring sig-
nature. The actual ring signature is denoted as σ.
When Y is encrypted with the encryption key K, it
is denoted as E
K
(Y ).
The non-encrypted version of the protocol works
as follows:
(1) A → *: ServiceAnnouncement
(2) B → A: V,C,T,
Cert
B1
,...,Cert
Bn
,x
B1
,...,x
Bn
,
E
K
(σ)
(3) A → B: Cert
A1
,...,Cert
An
,x
A1
,...,x
An
,
E
K
(σ)
In Step 1 Alice (A) announces that she offers a ser-
vice that uses the anonymous authenticated key agree-
ment protocol.
Assuming Bob (B) receives the service announce-
ment from Alice and wants to use this service, he first
generates an AES key K as payload for ECIES and
calculates V , C and T according to the ECIES scheme.
Then he selects n − 1 pseudonyms from his collected
pool and one of his own pseudonyms in order to cal-
culate the ring signature σ over V , C and T . Then,
he encrypts σ with the symmetric key K. Finally, he
sends V , C, T , the ring signature, and everything nec-
essary for validation to Alice (Step 2).
After reception Alice decrypts the AES key K ac-
cording to the ECIES scheme and applies it to decrypt
σ before validating the ring signature. When the val-
idation was successful, she selects one of her own
pseudonyms and n − 1 collected pseudonyms. With
this set of pseudonyms she calculates a ring signature
σ over V , C and T , and encrypts it with K. Then she
sends the ring signature and everything necessary to
validate it to Bob (Step 3).
When Bob receives the ring signature from Alice,
he decrypts σ and validates the ring signature. When
the validation was successful, he starts the confiden-
tial communication with Alice.
After the execution of the protocol, Alice and
Bob know that the other party is authorized to use
the service. In addition, both are in possession of
the same encryption key K still without knowing the
application-specific identity of the other party.
The encrypted version of the protocol differs in
Steps 2 and 3. The difference to the non-encrypted
one is, that not only σ is encrypted, but additionally
all necessary data to validate the ring signature. This
version works as follows:
(2
0
) B → A: V,C,T,
E
K
(Cert
B1
,...,Cert
Bn
,
x
B1
,...,x
Bn
,σ)
(3
0
) A → B: E
K
(Cert
A1
,...,Cert
An
,
x
A1
,...,x
An
,σ)
Given that the other party and a potential at-
tacker already know the pseudonym used for safety
messages, the identity applied to execute the ECIES
scheme does not give an attacker any new knowledge.
These safety pseudonyms should change on a regular
basis and not be reused. Therefore, they cannot be
exploited to track anything. The goal of an attacker
is to determine the application-specific pseudonym of
a vehicle, since this shall be reused in different ring
signatures and may therefore be used to link differ-
ent safety identities of the vehicles. This can be done,
when a vehicle exploits the same application-specific
pseudonym twice, but with different pseudonyms for
safety communication in VANETs. Then, an attacker
can link the two safety pseudonyms, because they
are used in combination with the same application-
specific pseudonym.
Consider that Alice applies the safety pseudonym
Cert
S1
and application-specific pseudonym Cert
A1
at the same time. Then, she changes her
safety pseudonym to Cert
S2
, while still using the
application-specific pseudonym Cert
A1
. An at-
tacker now may link Cert
S1
and Cert
S2
because they
were exploited with the same application-specific
pseudonym.
We assume that each vehicle may have multi-
ple valid application-specific pseudonyms at a time.
So, the vehicles can change their application-specific
pseudonym they use for building the ring signature
regularly with their pseudonyms for safety relevant
communication to avoid being tracked by means of
the pseudonyms not being changed.
Multiple pseudonyms confuse an attacker consid-
erably, since each vehicle has multiple identities and
these identities may be used at the same time in ring
signatures of different vehicles. We evaluate the im-
pact of multiple parallel pseudonyms in Section 5.
For the outlined protocol we stick to the same
pseudonym format already existing in VANETs to
sign safety messages, however we bind them to a spe-
cific application. We also use elliptic curve cryptog-
raphy and ECIES, which is already standardized for
safety communication. Therefore, this protocol fits
very well in the VANET environment.
It is possible to exclude a vehicle from suc-
cessfully executing the protocol by revoking its
application-specific pseudonyms. The revocation can
be done in the same way as for safety pseudonyms.
ICISSP2015-1stInternationalConferenceonInformationSystemsSecurityandPrivacy
262
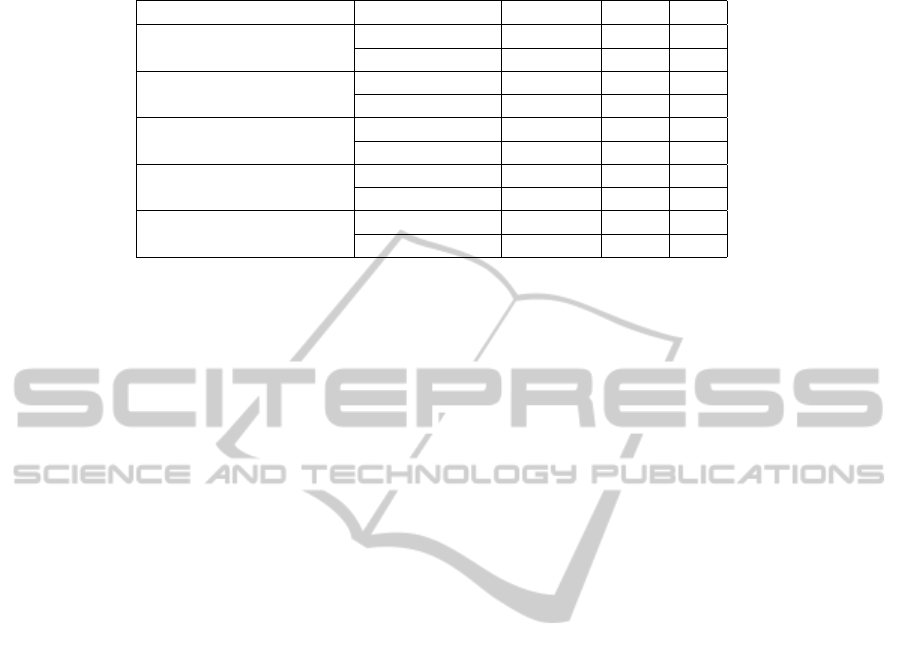
Table 1: Capabilities of different attackers.
Attacker Protocol Ring size Alice Bob
Passive
Non-Encrypted X X X
Encrypted X O O
Active without Non-Encrypted X X X
pseudonyms Encrypted X O O
Active with Non-Encrypted X X X
safety pseudonyms Encrypted X X O
Active with Non-Encrypted X X X
application pseudonyms Encrypted X O X
Active with safety and Non-Encrypted X X X
application pseudonyms Encrypted X X X
4.2 Attacker
4.2.1 Capabilities
We distinguish between passive and active attackers.
A passive attacker can only listen to and record ex-
changed messages, while active attackers can also
replay and send messages under a forged identity.
We consider four types of active attackers that dif-
fer in their access to pseudonyms. The least power-
ful attacker has no access to any valid pseudonyms.
Another attacker has only access to pseudonyms
for safety relevant communication. The third one
has only access to application-specific pseudonyms,
while the most powerful attacker is an insider and has
access to both pseudonym types.
Table 1 compares the encrypted and non-
encrypted version of the protocol regarding the infor-
mation the different attacker types can yield. We con-
sider the size of the ring and the pseudonyms used by
Alice and Bob as critical. When the attacker can get
the respective information, it is denoted as X, other-
wise as O.
Regardless of the used version of the protocol,
all attackers can calculate the current ring size from
the message size. When the non-encrypted version
is used, all attackers can get the pseudonyms used
by Alice and Bob, since they are transmitted in plain
text. Therefore, only the capabilities of the attack-
ers regarding the encrypted version of the protocol are
discussed in the sequel.
The passive attacker cannot get the pseudonyms
of Alice and Bob when the encrypted version is used,
since they are encrypted and the attacker cannot de-
rive the encryption key K just by listening to the ex-
changed messages.
Without access to valid pseudonyms, an active at-
tacker is not able to successfully inject any message,
since all of them are either signed or encrypted. If
the attacker replays the first message, she cannot en-
crypt the second or reply a valid third message, since
she does not know and cannot calculate the encryption
key. If she replays the second message, she is not in
the position to decrypt the pseudonyms used by Bob
in Step 3, since she does not know and cannot calcu-
late the encryption key. Therefore, all active attackers
are not able to get any information by replaying mes-
sages.
An active attacker with access to pseudonyms for
safety relevant communication may generate and send
the first messages. If she sends the first message, she
cannot replay with the third step, because she has no
application-specific pseudonym available in order to
generate a valid ring signature. However, she can de-
crypt the pseudonyms used by Alice in Step 2 by cal-
culating the encryption key K and therefore can get
the pseudonyms used by Alice.
An active attacker, who has only access to
application-specific pseudonyms, cannot generate and
send a valid service announcement, but may answer to
one, since she is able to calculate V , C, T , and a valid
ring signature. Therefore, she decrypts the message
sent by Bob in Step 3 and gets his pseudonyms.
If an active attacker has access to both a
pseudonym for safety relevant communications and
to an application-specific pseudonym, she is now in
the position to send and to answer to all messages of
the protocol and therefore gets the pseudonyms used
by Alice and Bob.
This analysis shows, that only the most power-
ful active attacker is able to unveil the identities used
by Alice and Bob when the encrypted version of the
protocol is being applied. However, lots of sophisti-
cated work will be necessary to implement this type
of attacker in practice, since the private keys of the
pseudonyms are in general stored on a hardware se-
curity module (HSM) inside the vehicle. Of course, if
the HSM fails and an attacker is thus able to extract
the private keys, she can get both the valid safety and
the application-specific pseudonyms and send valid
ANovelAnonymousAuthenticatedKeyAgreementProtocolforVehicularAdHocNetworks
263

1: // Count pseudonym usage
2: Create hashmap hm for pseudonym usage
3: for each colected message m do
4: for each used pseudonym p in m do
5: if hm.contains(p) then
6: hm.put(p, hm.get(p) + 1)
7: else
8: hm.put(p, 1)
9: end if
10: end for
11: end for
12: // Select relevant pseudonyms
13: Create list relevantPseudonyms
14: for each pseudonym p in hm do
15: if p > DaysObserving/PseudonymPoolSize
then
16: relevantPseudonyms.add(p)
17: end if
18: end for
Figure 1: Pseudonym filtering algorithm used by the passive
attacker.
fake messages. However, then the attacker may also
extract only the private keys of the safety pseudonyms
and link them directly or send valid fake safety mes-
sages. In general, it is possible to detect and to revoke
the affected vehicle, which also works with the pro-
posed protocol. However, failed HSMs are a general
problem in VANETs and we will therefore not inves-
tigate it in more detail in this paper.
4.2.2 Behavior
In this section we detail the behavior of the consid-
ered attacker. The attacker is a passive one aiming at
the non-encrypted version of the protocol. This at-
tacker type is sufficient, because even the most pow-
erful attacker aiming at the encrypted version cannot
gain more information. The attacker tries to identify
the application-specific pseudonym of a vehicle from
the ones used in the ring signature. The behavior of
the attacker can be divided into three stages.
In the first stage the attacker records the ex-
changed messages.
After recording, the attacker counts how of-
ten each pseudonym has been applied. Then,
she selects the relevant pseudonyms, which are
used at least DaysObserving/PseudonymPoolSize
times, where DaysObserving denotes the number
of days the attacker recorded the messages and
PseudonymPoolSize the number of own pseudonyms
each vehicle has at the same time, respectively. Thus,
only pseudonyms used regularly are considered. The
filtered ones might be introduced to the communica-
1: do
2: reduced = f alse
3: // Identify unambiguous pseudonyms
4: Create list unambiguousPseudonyms
5: for each collected message m do
6: for each pseudonym p in m do
7: if m.relevantPseudonyms == 1 then
8: unambiguousPseudonyms.add(p)
9: end if
10: end for
11: end for
12: // Reduce ring sizes
13: for each collected message m do
14: for each pseudonym p in m do
15: if p ∈ unambiguousPseudonyms ∧
m.day == unambiguousPseudonyms.get(p).day
then
16: m.delete(p)
17: reduced = true
18: end if
19: end for
20: end for
21: // Handle different ring sizes
22: if di f f erentRingSizes then
23: for each collected message m do
24: for each pseudonym p in m do
25: if p ∈ unambiguousPseudonyms∧
p.ringSize! = m.ringSize then
26: m.delete(p)
27: reduced = true
28: end if
29: end for
30: end for
31: end if
32: while reduced == true
Figure 2: Ring size reduction algorithm used by the passive
attacker.
tion by vehicles driving only once the observed street.
The pseudocode for this stage is shown in Figure 1.
The the third and last stage starts with the iden-
tification of unambiguous pseudonyms and is shown
as pseudocode in Figure 2. An pseudonym is unam-
biguous, if it is the only relevant pseudonym of a ring.
Therefore, this pseudonym must be the identity of the
vehicle.
Afterwards, these unambiguous pseudonyms are
deleted from all rings of the other vehicles on this
day. By ’delete’ we mean that it is now clear that
this pseudonym does not belong to the vehicle and we
therefore do no longer need to consider it in the re-
spective rings.
If each vehicle applies an own ring size, unam-
biguous pseudonyms are also deleted from the ve-
ICISSP2015-1stInternationalConferenceonInformationSystemsSecurityandPrivacy
264

hicles using a different ring size in other days. By
’own ring size’ we mean that not all vehicles use
the same number of pseudonyms to construct their
ring signature. We may delete these pseudonyms, be-
cause we know the ring size of the vehicle owning the
pseudonym is different.
If any pseudonyms were deleted, the attacker tries
to identify new unambiguous pseudonyms, otherwise
the attacker is finished.
Now the attacker has reduced the ring size of the
vehicles by excluding pseudonyms, which cannot be
the identities of the vehicles. We evaluate in Sec-
tion 5.2 by how much the attacker can reduce the ring
size and therefore the k-anonymity in presence of dif-
ferent parameters.
4.3 Considered Parameters
The anonymity of the vehicles is influenced by var-
ious parameters when they use the proposed anony-
mous authentication protocol. We considered the fol-
lowing parameters in the subsequent simulation runs:
Ring Size: The number of pseudonyms present in
the ring signature. Unless explicitly mentioned, we
used the maximum possible ring size of 10 according
to Figure 3.
Fraction of One Time Vehicles: These vehicles
use a set of pseudonyms in their ring that is com-
pletely unknown to the other vehicles. They shall re-
flect, that most vehicles drive the same route each day,
but there are always vehicles that normally do not take
this route in rush-hour, e.g., trucks. Unless explicitly
mentioned, we consider 30% of such one time vehi-
cles.
Standard Deviation of the Starting Times: The
starting times of the vehicles are assumed to be nor-
mally distributed. The standard deviation has an in-
fluence on the potential communication partners. Un-
less explicitly stated we use a standard deviation of 5
minutes.
Ring Building Strategy: When ring signatures
are in place, a vehicle is one of n possible signers.
It is important to apply a good ring building strategy,
because a poor strategy can lead to revealing of most
or even all of the non-signers, so the anonymity of the
signer decreases. In the following we suggest some
appropriate strategies to build a ring. We evaluate
these strategies later on in Section 5.
All: The vehicles collect and save all pseudonyms
they receive from other vehicles. When the vehicles
need to build a new ring, they randomly select the re-
quired number of pseudonyms from their pools.
SameDirection: Vehicles using this strategy col-
lect and save all pseudonyms they receive from other
vehicles driving in the same direction. The basic idea
behind is that vehicles in rush-hour drive every day
at approximately the same time in the same direction.
Therefore, an attacker cannot delete the pseudonyms
of the vehicles driving each day in the opposite direc-
tion from the ring. The same ring building strategy as
for "All" is applied.
SameDirectionLastX: This strategy is similar to
"SameDirection". The only difference is that the ve-
hicles discard pseudonyms they met more than X days
ago. The reason for this is that each day the vehicles
collect pseudonyms of one time vehicles they never
met before and unlikely meet again. If a vehicle uses
such pseudonyms in its ring, an attacker can identify
and remove them to get the identity of the victim ve-
hicle. This can be done because they are less used
than other pseudonyms. When limiting the number of
pseudonyms by the number of previous days, the in-
fluence of these vehicles decreases. Unless explicitly
mentioned, we use this ring building strategy.
SameDirectionLastXDifferentSizes: This strategy
works like "SameDirectionLastX", but each vehicle
applies an own ring size. This strategy is evaluated
later on to assess the influence of different ring sizes
on the anonymity of the vehicles.
Number of Own Pseudonyms: The number of
own pseudonyms a vehicle has at the same time. Each
time a ring is being build, the vehicle randomly selects
one. Unless explicitly stated, we exploit 10 simulta-
neous pseudonyms.
Duration of the Attack: The duration denotes the
number of days the attacker listens to the exchanged
messages. Unless explicitly mentioned, we consider
an attack duration of thirty days.
Number of Previous Days: This parameter de-
notes the number of days a vehicle stores the col-
lected pseudonyms in the strategies SameDirection-
LastX and SameDirectionLastXDifferentSizes.
5 EVALUATION
5.1 Ring Size
The ring size denotes the number of pseudonyms
used in the ring signature. It is obvious that the k-
anonymity of the vehicle increases with the ring size.
Since we want the maximum possible anonymity for
the vehicles, we try to make the ring as large as pos-
sible, but we also have to avoid as far as possible any
fragmentation at the MAC layer (ETSI ES 202 663,
2009).
To determine the maximum feasible message size,
we measured the size of the largest message in the
ANovelAnonymousAuthenticatedKeyAgreementProtocolforVehicularAdHocNetworks
265
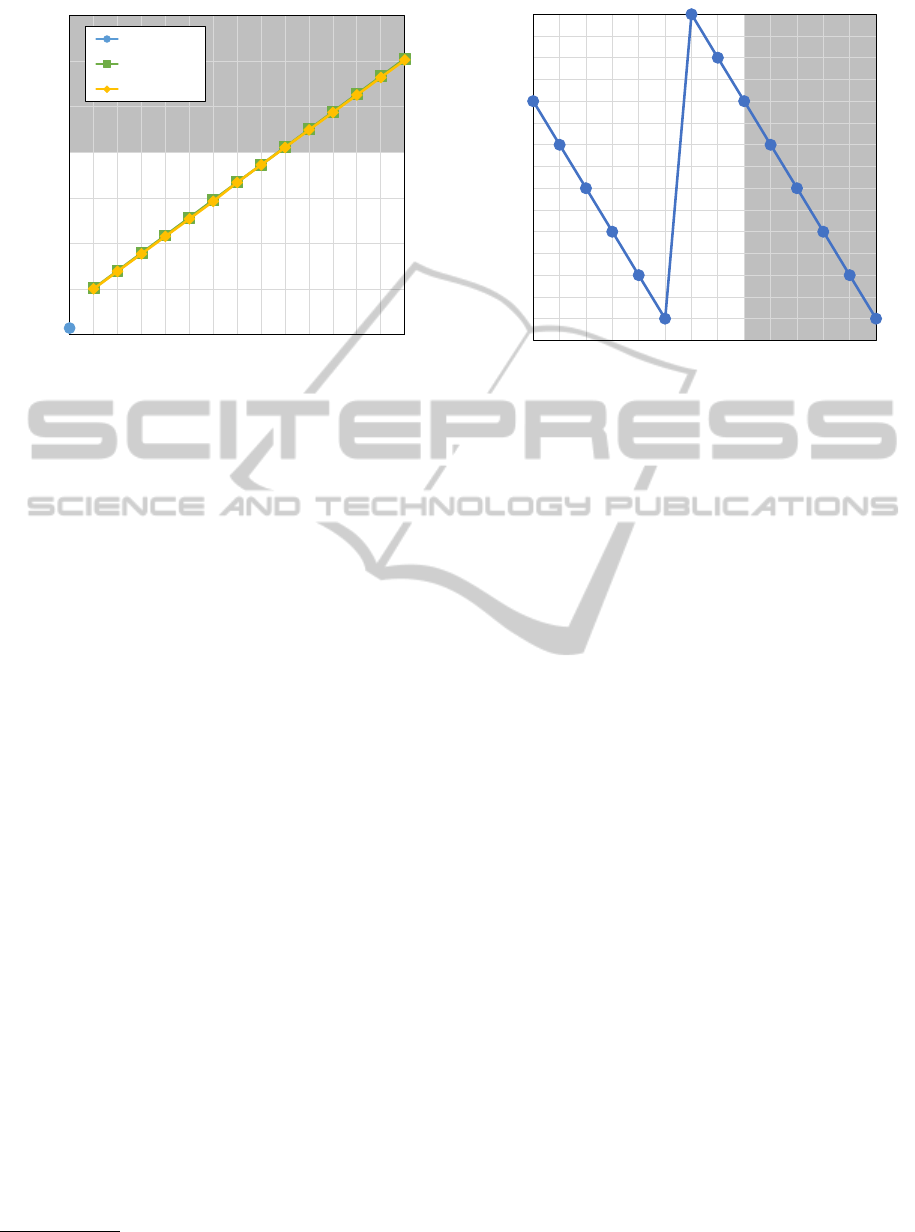
0
500
1000
1500
2000
2500
3000
3500
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
Message size [byte]
Ring size
ECIES
Ring
RingEncrypted
Figure 3: Message size as a function of ring size: Size of
largest message.
protocol. In this implementation we exploited the el-
liptic curve ring signature scheme proposed in (Lin
et al., 2007) with curve P-256 and ECIES as described
in (IEEE 1609.2, 2013). For the pseudonym size we
took 161 bytes, which is the size of a pseudonym cer-
tificate of the Pilot PKI of the Car-2-Car Communica-
tion Consortium
1
. We also took advantage of ellip-
tic curve point compression (Vanstone et al., 2000) to
minimize the size of the messages.
The size of the largest message as a function of
the ring sizes as well as for ECIES without ring sig-
natures is shown in Figure 3. The darker area indi-
cates the Maximum Transmission Unit (MTU), which
is expected to be larger than 2.000 bytes (ETSI TS
102 636-6-1, 2011). ECIES without the ring signa-
tures has the lowest message size at an anonymity of
1. For ring signatures the message size increases lin-
early with the ring size. Due to the fixed size of V
(33 bytes), C (20 bytes) and T (16 bytes) the size of
the message increases with every ring member by the
size of a Cert (161 bytes) and an x (32 bytes), which
are in total 193 bytes. The graph indicates that de-
pending on the MTU ring signatures with 10 or more
members are the ones with the maximum anonymity
in VANETs, when fragmentation at the MAC layer
shall be avoided. Although 10 denotes not that a large
set, we show in the following that this is sufficient for
the protocol and use case presented in order to pre-
serve the privacy of the vehicles while reducing the
number of necessary pseudonyms.
Messages of this size are much larger than safety
messages. However, they are sent at a much lower
frequency. Safety messages are sent up to 10 times a
1
www.car-2-car.org
-15
-14
-13
-12
-11
-10
-9
-8
-7
-6
-5
-4
-3
-2
-1
0
2 3 4 5 6 7 8 9 10 11 12 13 14 15
Message size difference [byte]
Ring size
Figure 4: Message size as a function of ring size: Size dif-
ference of encrypted and plain message.
second, whereas the messages in the proposed proto-
col for the envisaged use case will be sent only a few
times per hour. The messages are also sent on a dif-
ferent channel as the safety messages and do not have
critical time constraints like safety messages. The en-
visaged channel is expected to be also used for Inter-
net browsing, video streaming or software updates.
Figure 4 shows the difference of the largest mes-
sage of the encrypted and non-encrypted version in
bytes. The negative values indicate that the encrypted
version of the protocol has a smaller message size.
When the non-encrypted version is applied only the
signature is encrypted. It has a length of 33 byte
and is therefore encrypted in three AES blocks of 16
bytes, where the last block is padded with 15 bytes
to a multiple of the block size. In the encrypted ver-
sion of the protocol more data is encrypted, whereby
less padding bytes are used and therefore the overall
message size is reduced. The darker area indicates the
ring size when the MTU is in operation.
5.2 Simulation
5.2.1 Setup
For the simulation of the protocol we exploited the
VSimRTI tool set (Schünemann, 2011). As simula-
tion scenario we selected the motorway A60 south of
Rüsselsheim, Germany. At each junction of the mo-
torway one RSU is placed, which is assumed to be
under control of an attacker, who can record all mes-
sages exchanged in the communication range. The
vehicles enter the simulation area at two points: One
in the east, for the vehicles driving westbound, and
ICISSP2015-1stInternationalConferenceonInformationSystemsSecurityandPrivacy
266
one in the west of the map for vehicles driving east-
bound.
Normally the same vehicles drive the same way
every day during rush-hour. Because these are ideal
conditions for an attacker to link pseudonyms used
at different days, we evaluated the privacy proto-
col under this condition. According to the traffic
density categorization in (Forschungsgesellschaft für
Straßen- und Verkehrswesen, 2005) we used a high
density of vehicles in one and a low density in the
other direction. Three classes of vehicles are consid-
ered in the simulation: The fast ones have a maxi-
mum speed of 130 km/h, the regular ones a maximum
speed of 110 km/h, and the slow ones of 80 km/h. The
different vehicle classes are equally distributed. The
vehicles only drive the maximum speed if the traffic
conditions allow it. They also overtake only if there
is space to do so. Ten percent of the vehicles are
equipped with an application software that uses the
proposed anonymous key agreement protocol.
The envisaged simulation duration is 60 minutes.
Since it takes some time until the simulation is ad-
justed, we cut 10 minutes both at the beginning and at
the end of the simulation. Due to the long simulation
duration, we decided to run the simulation without a
specific ring building strategy. Instead, we log which
vehicles establish a session key to map the ring build-
ing strategies afterwards on the vehicles. To evaluate
more than 50 days, we randomly select as much sim-
ulation results as necessary from the pool of all 50
simulation runs and map the recurring vehicles after-
wards into the simulation results.
The elaborated results show that every day each
vehicle executes the protocol at least once in the com-
munication range of each RSU. Thus, an attacker
needs only one RSU under her control to get the rings
of all passing vehicles. The attacker would also not
get any benefit by having control over some of the
vehicles, because it is not possible to get more infor-
mation in this way.
5.2.2 Influence of the Considered Parameters
Ring Size: The k-anonymity of the vehicles, calcu-
lated according to (Sweeney, 2002), increases linearly
with the ring size from 7.0, when a ring size of 10 is
used, up to 10.3 when a ring size of 15 is being used.
Fraction of One Time Vehicles: The k-
anonymity of the vehicle increases from 4.7, when 55
% of the vehicles are one time vehicles, up to 8.6,
when only 11 % of the vehicles in the simulation ap-
pear only once. The reason for this is that there are
more new pseudonyms in the simulations, which are
considered by the vehicles during ring building.
1
2
3
4
5
6
7
8
9
10
1 2 3 4 5 6 7 8 9 10 11 12
k-anonymity
Months
All
SameDirection
SameDirectionLastX
DifferentSizes
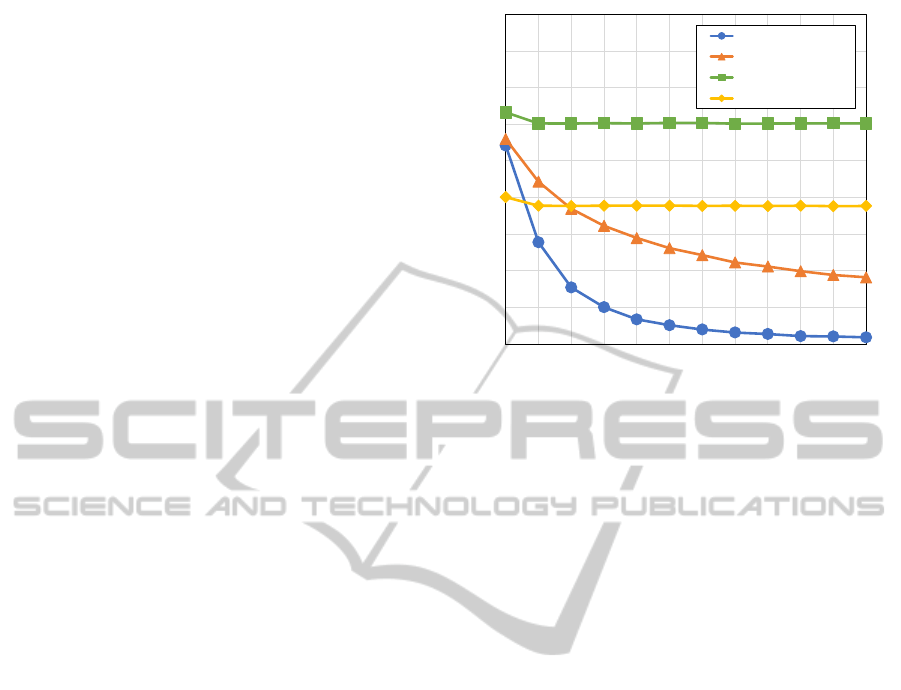
Figure 5: Impact of ring building strategies.
Standard Deviation of the Starting Times: An
increase or decrease of the standard deviation of
the starting times had no notable influence on the
anonymity of the vehicles.
Ring Building Strategy: The influence of the
ring building strategy to the k-anonymity is shown
in Figure 5. The x-axis displays the month in which
the attacker analyzes the messages since the start of
pseudonyms usage. Month 1 is therefore the analysis
of the first month and so on.
The k-anonymity value decreases over time from
6.4 in the first month down to 1.2 in the twelfth month,
when the strategy "All" is in operation. The average
k-anonymity value when using the "SameDirection"
strategy is 6.6 in the first month and steadily decreases
over time down to 2.8 after twelve months. When us-
ing the "SameDirectionLastX" strategy, the vehicles
have a constant k-anonymity of 7.0 from the second
month on. For the strategy "SameDirectionLastXD-
ifferentSizes" the k-anonymity value drops from 7.0
to 4.8 compared to the case when the same sizes are
used after the first month.
These results show, that all vehicles should use the
same ring size to keep the k-anonymity at a high level.
If only pseudonyms received in the last X days are
considered, then the k-anonymity of the vehicles does
not decrease over time.
Number of Previous Days: To get the optimal
number of previous days, we ran simulations with
different day values for the various pseudonym pool
sizes. Based on the outcome of these runs, we se-
lected the most appropriate numbers of days.
Number of own Pseudonyms and Duration of
the Attack: Figure 6 illustrates the k-anonymity
of the vehicles for different numbers of own
ANovelAnonymousAuthenticatedKeyAgreementProtocolforVehicularAdHocNetworks
267
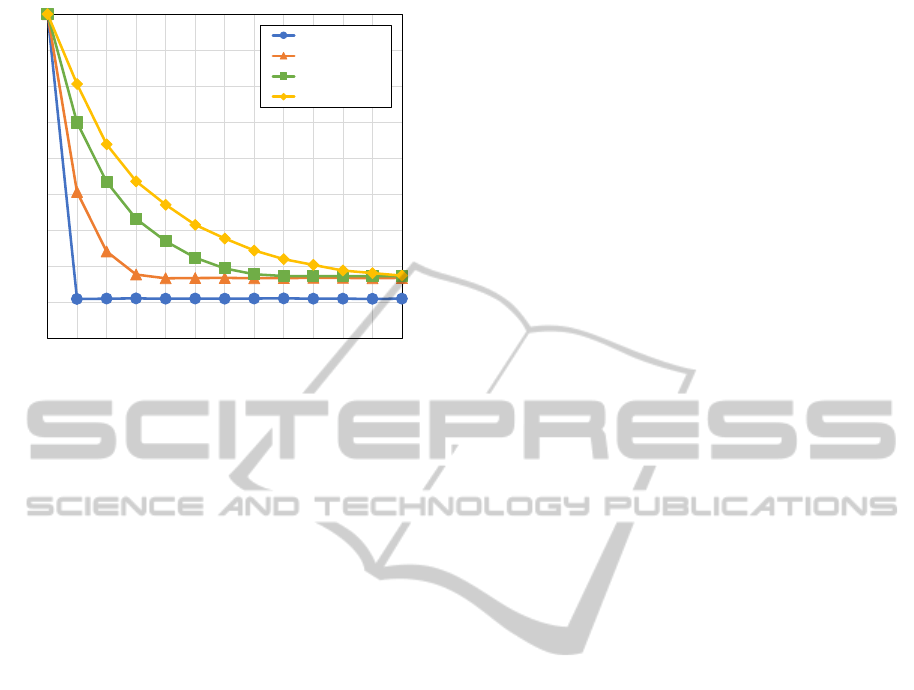
1
2
3
4
5
6
7
8
9
10
1 30 60 90 120 150 180 210 240 270 300 330 360
k-anonymity
Days
1 Pseudonym
5 Pseudonyms
10 Pseudonyms
15 Pseudonyms
Figure 6: Impact of pseudonym pool size.
pseudonyms as a function of the number of days an
attacker records the exchanged messages. It shows
that the k-anonymity value decreases with the num-
ber of days an attacker listens to the exchanged mes-
sages. In addition, the k-anonymity value increases
with the number of own pseudonyms. Depending on
the assumed attack duration, either more pseudonyms
have to be used or the pseudonyms have to be re-
newed more often in order to maintain a certain level
of anonymity.
If an service provider aims to, for example, at a
k-anonymity of at least 5 for its users, the vehicles
could use a new set of 5 pseudonyms every 30 days,
a set of 10 pseudonyms every 60 days or a set of
15 pseudonyms every 90 days. This sums up to 60
pseudonyms per year. If we compare this value to
the safety pseudonyms, where the pseudonym is to
obe changed at least with every trip, we can easily
see that the proposed protocol reduces the number of
necessary pseudonyms considerably.
6 CONCLUSION
In this work we proposed a novel anonymous au-
thenticated key agreement protocol which combines
ECIES with ring signatures and we elaborated recom-
mendations for an appropriate ring size for the com-
munication between vehicles in a VANET.
We showed that the anonymity of the vehicles in-
creases significantly when a good ring building strat-
egy is applied. We also demonstrated that the num-
ber of pseudonyms each vehicle uses at the same time
and the duration of the attack have a clear influence
on the anonymity level of the vehicles. In compari-
son to safety-related communication less pseudonyms
for each vehicle over time are necessary to main-
tain a high level of anonymity, because they can be
reused without the risk of being linked by an attacker.
Therefore, the amount of pseudonyms, which have to
be loaded onto the vehicles, is significantly reduced,
which saves storage space and communication over-
head and thus helps to reduce costs.
The proposed protocol is not restricted to VANET
use cases, but it is especially well-suited for VANETs,
because in such a context it is both expensive and
some times rather difficult to obtain new pseudonyms.
In addition the well-known pseudonyms for safety-
related communication can be reused by binding them
to specific applications.
In the next future we plan to implement the out-
lined protocol into real vehicles and to take measure-
ments to validate the presented simulation results.
REFERENCES
Baldwin, R. and Gramlich, W. (1985). Cryptographic pro-
tocol for trustable match making. In IEEE Symposium
on Security and Privacy.
Balfanz, D., Durfee, G., Shankar, N., Smetters, D., Staddon,
J., and Wong, H.-C. (2003). Secret handshakes from
pairing-based key agreements. In Security and Pri-
vacy, 2003. Proceedings. 2003 Symposium on, pages
180 – 196.
Camenisch, J. and Lysyanskaya, A. (2001). An efficient
system for non-transferable anonymous credentials
with optional anonymity revocation. In Proceedings
of the International Conference on the Theory and Ap-
plication of Cryptographic Techniques: Advances in
Cryptology, EUROCRYPT ’01, pages 93–118, Lon-
don, UK, UK. Springer-Verlag.
Castelluccia, C., Jarecki, S., and Tsudik, G. (2004). Secret
handshakes from ca-oblivious encryption. In Lee, P.,
editor, Advances in Cryptology - ASIACRYPT 2004,
volume 3329 of Lecture Notes in Computer Science,
pages 293–307. Springer Berlin Heidelberg.
Chaum, D. and Heyst, E. (1991). Group signatures. In
Davies, D., editor, Advances in Cryptology — EURO-
CRYPT ’91, volume 547 of Lecture Notes in Computer
Science, pages 257–265. Springer Berlin Heidelberg.
ETSI ES 202 663 (2009). Intelligent Transport Systems
(ITS); European profile standard for the physical and
medium access control layer of Intelligent Transport
Systems operating in the 5 GHz frequency band.
ETSI TS 102 636-6-1 (2011). Intelligent Transport Systems
(ITS); Vehicular Communications; GeoNetworking;
Part 6: Internet Integration; Sub-part 1: Transmission
of IPv6 Packets over GeoNetworking Protocols.
ETSI TS 102 890-2 (2010). Intelligent Transport Systems
(ITS); Facilities Layer Function, Part 2: Services An-
nouncement.
ICISSP2015-1stInternationalConferenceonInformationSystemsSecurityandPrivacy
268

ETSI TS 103 097 (2013). Intelligent Transport Systems
(ITS); Security; Security header and certificate for-
mats.
Forschungsgesellschaft für Straßen- und Verkehrswesen
(2005). Handbuch für die Bemessung von Straßen-
verkehrsanlagen (HBS).
Freudiger, J., Raya, M., and Hubaux, J.-P. (2009). Self-
organized Anonymous Authentication in Mobile Ad
Hoc Networks. In Security and Privacy in Communi-
cation Networks, pages 350–372.
IEEE 1609.2 (2013). Standard for Wireless Access in Ve-
hicular Environments - Security Services for Appli-
cations and Management Messages, IEEE Standard
1609.2.
Lin, X., Lu, R., Zhu, H., Ho, P.-H., Shen, X., and Cao, Z.
(2007). ASRPAKE: An Anonymous Secure Routing
Protocol with Authenticated Key Exchange for Wire-
less Ad Hoc Networks. In IEEE International Con-
ference on Communications, ICC 2007, pages 1247
–1253.
Rivest, R. L., Shamir, A., and Tauman, Y. (2001). How
to leak a secret. In Advances in Cryptology – ASI-
ACRYPT, pages 552–565.
Schünemann, B. (2011). V2X simulation runtime infras-
tructure VSimRTI: An assessment tool to design smart
traffic management systems. Computer Networks,
55:3189–3198.
Sweeney, L. (2002). k-anonymity: A model for protecting
privacy. International Journal of Uncertainty, Fuzzi-
ness and Knowledge-Based Systems, 10(05):557–570.
Vanstone, S. A., Mullin, R. C., and Agnew, G. B. (2000). El-
liptic curve encryption systems. Patent, US 6141420.
ANovelAnonymousAuthenticatedKeyAgreementProtocolforVehicularAdHocNetworks
269
