
Implementing Identity-based Key Agreement in Embedded Devices
Giovanni Schmid
1
and Francesco Rossi
2
1
High Performance Computing and Networking Institute (ICAR), Naples, Italy
2
University of Naples Parthenope, Naples, Italy
Keywords:
ID-based Cryptography, Key Agreement, Embedded Device.
Abstract:
In recent years, a substantial work has been devoted to the design of cryptographic protocols with reduced
computational load and power consumption. However, implementations are scarce, especially in case of em-
bedded devices. In this paper, we discuss the implementation over elliptic curves of a two-party key agreement
protocol for the Raspberry PI platform. The protocol requires just one round to derive an (implicit) authen-
ticated session key, and it makes use of identity-based cryptography, which fits very well some application
scenarios, allowing for more efficiency than the certificate-based approach. Our implementation takes advan-
tage of the portability and security features of the Java programming language and, due to a modular design, it
can be easily extended to encompass other identity-based schemes and protocols. We run a set of tests in order
to verify the correctness of our implementation and to measure its performances in term of computing time.
Our results demonstrate that getting secure communications using low cost, resource constrained devices is
viable to the point that it can be used for real world applications.
1 INTRODUCTION
In recent times, we are witnessing an increasing use of
embedded devices, also in relation to services and ap-
plications that require secure communications. Em-
bedded devices have limited computational capabil-
ities and power resources, and these limitations will
be presumably hold also in the future, since the driv-
ing forces in this area of hardware design point to-
wards an increasing miniaturization and more func-
tionalities. On the other hand, security in commu-
nications is obtained due to cryptographic protocols,
which however can result in a not negligible over-
head, enough to jeopardize the operation of embed-
ded devices. A class of especially expensive crypto-
graphic protocols, both in term of memory usage and
computing time, is that for key agreement (Menezes
et al., 2010). Key agreement is at the core of secure
peer-to-peer communications, and its high costs are
because it requires asymmetric cryptography. Once
agreed upon a key, a set of peers can used such key to
secure their communications due to symmetric cryp-
tographic mechanisms. Symmetric mechanisms are
much less expensive than asymmetric ones and they
are feasible even on embedded devices. From the
above, it then follows that efficient, reliable imple-
mentations of key agreement protocols play a cru-
cial role in the realization of secure distributed ap-
plications for embedded devices. The implementa-
tion of a key agreement protocol is a very complex
task. Besides the subtleties concerning the software
coding of reliable cryptographic mechanisms, a cryp-
tographic protocol requires the management of com-
munications through synchronization among parties,
packet assembling and disassembling, data exchange,
and error handling. The present work concerns the
implementation on the Raspberry PI platform (Monk,
2014) of a protocol derived from the two-party key
agreement protocol of (Fiore and Gennaro, 2010) (FG
protocol, for short). The FG protocol uses identity-
based (ID-based) cryptography (Shamir, 1985), thus
avoiding the set-up and management of public key
certificates. ID-based cryptography can be valuable
whenever trust can be enforced centrally through a key
distribution center (KDC), allowing for better mem-
ory efficiency and less communication overhead than
certificate-based approaches. Moreover, the FG pro-
tocol is optimal as number of communication rounds,
requiring just one round to get (implicit) key authenti-
cation. In order to match the constrained resources of
embedded devices such as the Raspberry PI, we have
implemented the FG protocol over elliptic curves. El-
liptic curves are very promising to enforce strong
cryptography on embedded devices, since they allow
117
Schmid G. and Rossi F..
Implementing Identity-based Key Agreement in Embedded Devices.
DOI: 10.5220/0005242901170123
In Proceedings of the 5th International Conference on Pervasive and Embedded Computing and Communication Systems (PECCS-2015), pages
117-123
ISBN: 978-989-758-084-0
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

to scale much better with respect to key sizes (i.e. se-
curity thresholds). Our implementation is in the Java
programming language and, due to a modular design,
it can be easily extended to encompass other identity-
based schemes and protocols. Although Java cannot
achieve the performance of full-compiled languages
(e.g., C, C++), it is well suited for coding distributed
applications and services, because of its portability
and built-in security features (De Caro and Iovino,
2011). The paper is organized as follows. Section
2 discusses related work. Section 3 outlines some
notions and notations that will be used through the
rest of the paper. In Section 4 we describe our ellip-
tic version of the FG protocol. Section 5 describes
our Java implementation for the Raspberry PI device,
discussing design choices and issues. Section 6 sum-
marizes the results of various tests we have done in
order to evaluate performance. Finally, in Section 7
we draw conclusions and sketch out future work.
2 RELATED WORK
A two-party key agreement protocol allows two par-
ties, who each have a long-term key, to agree as peers
upon a common secret key by exchanging messages
with each other (Menezes et al., 2010). Later, the
shared secret key may be used to secure communica-
tion sessions among these parties, due to one or more
of the fast mechanisms offered by symmetric cryptog-
raphy.
Starting from the pioneering work of (Diffie and
Hellman, 1976), many key agreement protocols have
been proposed over the years in the literature. How-
ever, many of these protocols lack a sound secu-
rity analysis, and some of them have been actually
proven insecure. On the other hand, many provably
secure key agreement protocols are far from being op-
timal, and require a significant overhead in local com-
putations and/or communication bandwidth. Com-
prehensive surveys on key agreement can be found
in (Boyd and Mathuria, 2003) and (Menezes et al.,
2010). (Fiore and Gennaro, 2010) introduced a prov-
ably secure, very efficient protocol, which requires
only twice the amount of bandwidth and computa-
tion of the unauthenticated basic Diffie-Hellman pro-
tocol. This protocol is identity-based and outperforms
MQV (Law et al., 2003), the most efficient authen-
ticated two-party Diffie-Hellman based protocol in
the public-key model. The concept of identity-based
(ID-based) cryptography was introduced by (Shamir,
1985). The innovation was the use of identity at-
tributes, instead of digital certificates, for data en-
cryption and signature. This avoids the generation
and management of users’ certificates, reducing sig-
nificantly the complexity and computational cost of
protocols. Pioneered by the work of (Joux, 2000),
various ID-based key agreement protocols ( e.g., (Mc-
Cullagh and Barreto, 2005), (Okamoto et al., 2005),
(Chen et al., 2007)) have been proposed so far. In or-
der to work, however, these protocols require groups
over elliptic curves where special mappings, called bi-
linear pairings (Miller, 2004), are available. Such
groups must be carefully selected for getting ade-
quate performance without a downgrade in security.
Conversely, the FG protocol works over any cyclic
group. This results in the possibility of choosing
much smaller groups than in the case of pairing-
based protocols to get a given threshold of security,
since one can use “regular” elliptic curves, rather
than the ones that admit efficient pairings computa-
tions for high security levels. This paper concerns
an implementation of the FG protocol on the Rasp-
berry PI platform. Although libraries exist that sup-
port identity-based cryptography and bilinear pairing
operations (e.g., the reference benchmark C library
PBC of (Lynn, 2007) and its Java porting jPBC of
(De Caro and Iovino, 2011)), at the time being, to the
best of our knowledge, there are no known implemen-
tations of ID-based key-agreement protocols. Further,
there are few implementations also for other classes of
key-agreement protocols. Actually, only the Charm
library (Akinyele et al., 2011) implements software
components for message serialization, data transmis-
sion, and error handling.
3 PRELIMINARIES
In this section we first describe how ID-based cryp-
tosystems work, and then we give some basic notions
about elliptic curves, showing how to choose them for
our scopes.
3.1 ID-based Cryptosystems
In ID-based cryptography (Shamir, 1985), a trusted
key generation center (KGC) first generates a mas-
ter public/secret key pair, publishing the public key
alongside with any other public parameter which
uniquely identifies the Diffie-Hellmann system to be
used and the set of strings chosen as user identifiers.
In a second phase, the KGC gives to each user hav-
ing identity U a secret key S
U
, which is a function of
the string U and the KGC’s secret key. Using their
own S
U
, users can then perform cryptographic tasks.
These two phases performed by the KGC are named
Setup and Extract, respectively.
PECCS2015-5thInternationalConferenceonPervasiveandEmbeddedComputingandCommunicationSystems
118

A first advantage of ID-based systems is the ver-
satility with which identifiers may be chosen. Since
identities can be arbitrary string, they can be selected
according to the function and attributes of the parties.
For example, a network device might be identified
by its MAC address, its “role” in the network (e.g.,
“router A”), or its physical position (e.g., latitude and
longitude).
A second advantage of identity-based schemes
is that they can significantly simplify authentication
management, bypassing the certification issues. All a
party needs to know in order to communicate with a
given peer is its own secret key, the public informa-
tion of the KGC, and the identifier of the peer.
3.2 Elliptic Curves
An Elliptic curve E(F
q
) over a field of q elements F
q
is the set of solutions (x, y) ∈ F
q
of an equation of the
form:
y
2
+ a
1
xy + a
3
y = x
3
+ a
2
x
2
+ a
4
x + a
6
(1)
together with an additional point at infinity, denoted
as O, which represents the direction of the y-axis.
Equation (1) reduces to a simpler form according to
the field characteristic p, a prime number such that
q = p
d
with d ≥ 1. In the following we will consider
only elliptic curves for which equation (1) reduces to:
y
2
= x
3
+ ax + b . (2)
Such curves are related to fields for which d = 1. In
this case q = p, and the number of points (i.e. the or-
der) of E(F
p
) is given by p + 1 −t, where |t|≤ 2
√
p.
Moreover, for any such t there is an elliptic curve of
equation (2) having exactly order p + 1 −t. Curve of
this type must be defined over fields having a large
prime p characteristic, so that the Diffie-Hellmann
problem over a cyclic group in F
p
can be sufficiently
hard. In our tests (Section 6) we used the three ordi-
nary curves P-160, P-192 and P-224; these are curves
defined in the NIST standard (Brown et al., 2001) hav-
ing orders in bit size of 160, 192 and 224, respec-
tively.
4 THE eFG PROTOCOL
Accordingly to any ID-based cryptosystem, the FG
protocol (Fiore and Gennaro, 2010) requires the iden-
tifiers A, B of the two communicating peers, and all
other information made public by the KGC which
uniquely identifies the system. In case of the elliptic
version eFG of the protocol, this public information
consists of:
• the elliptic curve E to be used;
• the point P ∈ E of prime order l, with gcd(l, p −
1) = l, which generates the cyclic group G ⊂ E
where the Diffie-Hellmann system will be consid-
ered;
• the two hash functions
h : {0, 1}
∗
→ Z
∗
l
, H : G ×G → {0, 1}
n
,
where n is a suitable positive integer;
• the public key P
pub
= sP ∈ G of the KGC, where
s ∈Z
∗
l
is the corresponding secret key, chosen ran-
domly by the KGC.
Moreover, as result of an interaction with the KGC
through a properly protected, out-of-band channel
each user receives its own private key related to its
identity U. In case of the eFG protocol this key is the
output of the Extract algorithm 1, and consists in a
couple (R
U
, s
U
) ∈ G ×Z
∗
l
, which represents the ellip-
tic version of the Schnorr’s signature (Schnorr, 1991)
of the string U under the public key P
pub
.
Algorithm 1: eFG Extract algorithm.
KGC: randomly select r
U
∈ Z
∗
l
;
KGC: compute R
U
= r
U
P;
KGC: compute s
U
= r
U
+ sh(U kR
U
);
KGC: send message {R
U
, s
U
} to U
Protocol’s computations can be subdivided in
three steps. In the first step, each user U asyn-
chronously calculates its ephemeral private-public
key couple (t
U
, T
U
) ∈ Z
∗
l
×G. The second step is a
communication step in which each user U sends to
the other party a packet with its identifier U along-
side with the two points R
U
, T
U
∈ G. Finally, in
the third step each user U computes a couple of
points (Z
U
, Z
0
U
) ∈ G ×G and derives the key as K =
H(Z
U
, Z
0
U
). The computation of (Z
U
, Z
0
U
) requires the
private information of U , together with P
pub
and the
information received by U from its peer due to the
previous communication step. Since each user com-
putes the same couple (Z
U
, Z
0
U
), the computed key K
is actually the same for both users. Note that the pro-
tocol actually does not rely on message authentica-
tion, since each of the two messages exchanged at the
step two is actually not signed by the sender. How-
ever, the way to derive (Z
U
, Z
0
U
) (Alg. 2) assures that
only the two parties with identities A, B can compute
the key K.
It easy to show that protocol eFG is correct, mean-
ing that it actually results in a key agreement between
ImplementingIdentity-basedKeyAgreementinEmbeddedDevices
119
Algorithm 2: eFG protocol.
A: randomly select t
A
∈ Z
∗
l
compute T
A
= t
A
P
B: randomly select t
B
∈ Z
∗
l
compute T
B
= t
B
P
A: send message {A, R
A
, T
A
} to B
B: send message {B, R
B
, T
B
} to A
A: compute Z
A
= (t
A
+ s
A
)(T
B
+ R
B
+ h(B||R
B
)P
pub
)
Z
0
A
= t
A
T
B
K = H(Z
A
, Z
0
A
)
B: compute Z
B
= (t
B
+ s
B
)(T
A
+ R
A
+ h(A||R
A
)P
pub
)
Z
0
B
= t
B
T
A
K = H(Z
B
, Z
0
B
)
users A and B. Indeed:
Z
A
= (t
A
+ s
A
)(T
B
+ R
B
+ h(B||R
B
)P
pub
)
= (t
A
+ r
A
+ sh(A||R
A
))(t
B
P + r
B
P + h(B||R
B
)sP)
= (t
A
+ r
A
+ sh(A||R
A
))((t
B
+ r
B
+ sh(B||R
B
))P)
= (t
A
P + r
A
P + sh(A||R
A
)P)(t
B
+ s
B
)
= (T
A
+ R
A
+ h(A||R
A
)P
pub
)(t
B
+ s
B
)
= Z
B
(3)
and
Z
0
A
= t
A
T
B
= t
A
t
B
P = T
A
t
B
P = Z
0
B
It can be proven that protocol eFG is secure under the
strong Diffie-Hellmann assumption, if the hash func-
tions h and H behaves as random oracles (for these
notions and the security proof (Fiore and Gennaro,
2010)). For each node, the eFG protocol requires 4
point-scalar multiplications, 2 point additions, 2 hash
computations. Moreover, each node has to send and
receive one message, which composes of the sender
identifier and two points in G.
5 eFG IMPLEMENTATION
In this section, we discuss about software design and
development on the Raspberry PI platform, in order
to implement the eFG Protocol discussed in the previ-
ous section. Our design complies with modular pro-
gramming, emphasizing the separation of the func-
tionality offered by a program into independent and
interchangeable modules. This way, software gains in
reliability, security and reusability. Modules can be
separately tested and verified, and they can be used
in other software as well. In our case, some of the
modules developed to implement the eFG protocol
can be reused for other protocols, such as ID-based
group key agreement protocols.
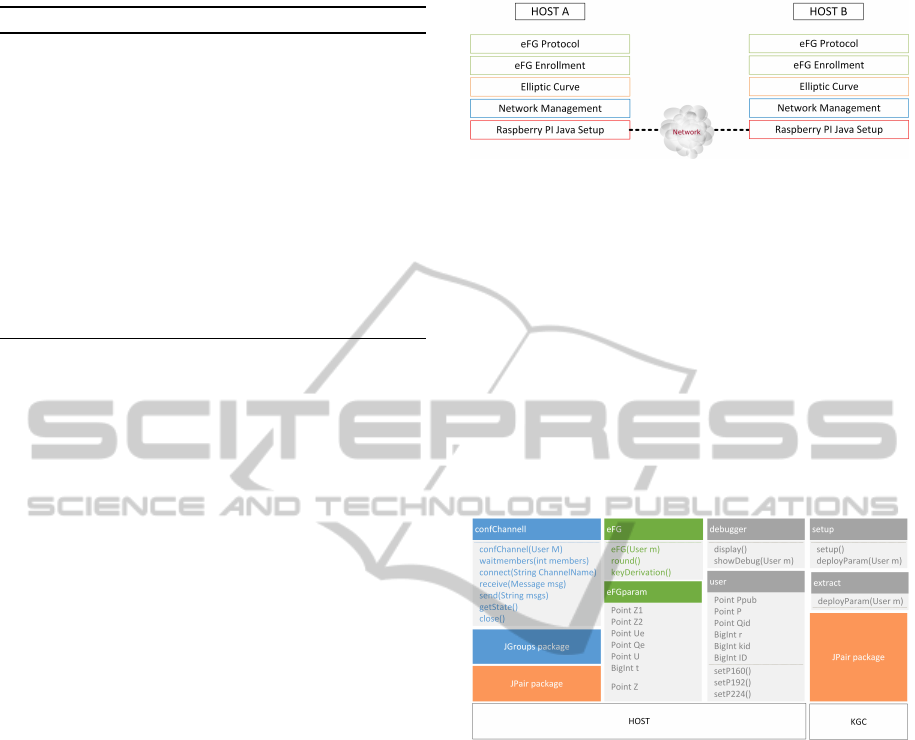
Figure 1: Software modules involved in the key agreement
process performed through eFG protocol.
Our implementation is in the Java programming
language. Java allows for portability and is of
widespread use in mobile platforms. The Raspberry
PI device (Monk, 2014) includes two Java ARM tech-
nologies for speeding up performance, ARM Floating
Point and Jazelle (”ARM”, 2014).
ARM Floating Point technology provides hard-
ware support for floating point operations in half
and single double-precision floating point arithmetic.
Instead, ARM Jazelle technology is a combined
hardware-software solution to increase the perfor-
mance of the Java Virtual Machine (JVM).
Figure 2: The Java classes provided in the eFG protocol
implementation. The three columns on the left are related to
the host device, whilst the lost column on the right concerns
the key generation center.
Figure 2 shows the Java class related to the imple-
mentation of the eFG protocol. The implementation
includes packages JPair (Dong, 2010) and JGroups
(JGroups, 2014), that will be described in the next
sections. Class user stores all public parameters, plus
user’s private and public keys that are generated by
the KGC through Algorithm 1. The confChannel
class is devoted to the configuration of the commu-
nication channel: it includes methods to open/close
the channel and to send/receive data. Class eFG im-
plements the eFG protocol, using class eFGparam for
storing local parameters needed for computations. Fi-
nally, the key generation center (KGC) implementa-
tion includes classes Setup and Extract that are used
for the generation of the public system parameters and
the user public/private key couple, respectively. In the
sequel, we give a brief description for each of the im-
plemented module and its functions.
PECCS2015-5thInternationalConferenceonPervasiveandEmbeddedComputingandCommunicationSystems
120

5.1 Raspberry PI Java Setup
The Raspberry PI Java Setup module relates to Rasp-
berry PI operating system configuration, which in our
case is the Raspian OS (”Raspian”, 2014). In order
to run our application, written in the Java program-
ming language, we have installed Java SE Embed-
ded, release 8. This release introduces a new con-
cept called Compact Profiles, which enables reduced
memory footprint for applications that do not require
the entire Java platform. At the time being, the three
profiles compact1, compact2 and compact3 are sup-
ported, each being a superset of the APIs in the previ-
ous profile. The Compact Profiles feature is very use-
ful for small devices, because it allows for a smaller
size o the Java code. A JRE can be configured with a
compact profile, reducing its footprint for deployment
along with a compact profile application. We devel-
oped our application with NetBeans 8, which supports
compact profiles and allows the deployment of a Java
application directly on an embedded platform such as
the Raspberry PI. Moreover, we installed in Raspian
the P4J library (”Pi4j”, 2014), that allows to control
the GPIO of a Raspberry PI device through Java APIs.
5.2 Network Management
The Network Manager module is devoted to user
synchronization, data transmission, and error han-
dling. We implemented it using the JGroups toolkit
(JGroups, 2014). For any given TCP or UDP commu-
nication channel, JGroups offer services for joining
and leaving, membership detection and notification,
detection and removal of crashed users, and the send-
ing and receiving of unicast and multicast messages.
The most powerful feature of JGroups is its flexible
protocol stack, which allows developers to adapt it for
the best matching of application requirements with
network characteristics. For protocol eFG we have
chosen an UDP asynchronous communication chan-
nel for better performance.
The Message Serialization Manager module is
dedicated to data serialization. Hosts A and B need a
precise order to build packets for delivery. For exam-
ple, referring to first data transaction of protocol eFG,
host A has to make a UDP packet which composes
of the three field A, R
A
, T
A
(Algorithm 2). For allow-
ing recipient B to process the packet correctly, such
fields must be properly identified and must be put in
the right order. This serialization is implemented by
a Java class that splits and merges data using special
characters as separators.
5.3 Elliptic Curve (EC) Module
The EC module implements all mathematical opera-
tions required by elliptic curve cryptography. These
include finite fields and elliptic curve generation, in-
teger arithmetic over elliptic curves and hash func-
tion computation. The API offered by this module
is used by the higher level modules Enrollment and
Protocol, discussed in the next section. The EC mod-
ule is implemented using an extended version of the
JPair library (Dong, 2010) which was completed by
adding the standard NIST curves P-160, P-192, P-224
described in Section 3.2.
5.4 Enrollment Module
Enrollment is the step first required in ID-based cryp-
tosystems. It corresponds to the registration of users
to a specific crypto-service offered by a key genera-
tion center (KGC), and is realized through the Setup
and Extract classes. The Enrollment is executed one-
time and simulates the workaround of a KGC deploy-
ing off-line public parameters on devices through a
secure, out-of-band communication channel.
The scope of the Setup class is the setting of the
KGC crypto-parameters for the intended service. The
operation performed by the Setup class are the follow-
ing:
• Selection of an elliptic curve E(F
p
) and of a point
P ∈ E having as prime order the order of E;
• Choice of a pseudo-random integer s ∈ Z
∗
l
, and
computation of P
pub
= sP. The private/public key
couple of the KGC is (s, P
pub
);
• Instantiation of the two functions:
H : G ×G → Z
∗
l
, h : {0, 1}
∗
→ Z
∗
l
The scope of the Extract class is the generation of the
private keys for users A and B. As we told in Section 4
these private keys are the elliptic version of Schnorr’s
signatures of strings A and B under public P
pub
. This
class corresponds to Algorithm 1 and, given the out-
put returned by class Setup, it does the following:
• Computation of digests H(A), H(B), h(A) and
h(B);
• Choice of the random values r
A
, r
B
→ Z
∗
l
;
• Computation of the points
R
A
= r
A
P and R
B
= r
B
P;
• Computation of the two modulo l integers
s
A
= r
A
+ sh(A||R
A
);
s
B
= r
B
+ sh(B||R
B
);
ImplementingIdentity-basedKeyAgreementinEmbeddedDevices
121
The private keys of users A and B are given by (R
A
, s
A
)
and (R
B
, s
B
), respectively.
Module Protocol implements a Java class for the
eFG protocol. This Java class includes all the methods
required by Algorithm 2 and the eFGparam subclass,
which is used to store local variables.
6 PERFORMANCE
The Raspberry PI (Monk, 2014) is an embedded de-
vice developed in UK by the Raspberry PI foundation.
Its design is based around a Broadcom BCM2835
SoC, which includes an ARM1176JZF-S 700 MHz
processor, 512 Megabytes of RAM and an SD card
for booting and long-term storage. A set of tests were
performed to measure eFG protocol performances.
Each computed value is the average of 1000 execu-
tions, in order to take account of time outliers due
to JVM memory management and HotSpot optimiza-
tions (”Oracle”, 2014). Table 1 shows the elliptic
curves used in tests, along with the order (in bit size)
of the group G considered on the curve, and the corre-
sponding order of a standard group in which the dis-
crete logarithm problem (DLP) has a difficulty com-
parable to that of the DLP in G.
Table 1: The elliptic curves used in tests are the NIST stan-
dards P-160, P-192 and P-224. These are ordinary curves
whose equation differs only for the known term b
i
(Brown
et al., 2001).
Name Equation Order of G DLP Difficulty
P-160 y
2
= x
3
−3x + b
1
160-bit 1024-bit
P-192 y
2
= x
3
−3x + b
2
192-bit 2048-bit
P-224 y
2
= x
3
−3x + b
3
224-bit 4096-bit
Overall, our Java code footprint with all the cryp-
tographic material needed to perform the tests re-
quired just 106 KB of memory versus a the maximum
of 100 MB supported by the Jazelle architecture for
each device. Table 2 reports computing times (ms) of
the Setup and Extract algorithms for each of the ellip-
tic curves of Table 1. In our case, the computing time
of the Extract algorithm encompasses the creation of
the private key for both users A and B.
Table 2: Computation times (ms) for the Setup and Extract
algorithms.
Algorithm P-160 P-192 P-224
Setup 101 102 104
Extract 2407 2497 2499
Table 3 reports the computing times (ms) required
by each user for the execution of the three different
steps in protocol eFG (Section 4). Each value is the
average of the times spent by A and B for each step.
The computing time for the communication step (Step
2) was measured using two different network inter-
face cards, wired LAN (IEEE 802.3u Ethernet) and
WiFi (IEEE 802.11g).
Table 3: Computing time (ms) for each step of the eFG pro-
tocol.
Curve Step 1 Step 2 (wired LAN) Step 2 (WiFi) Step 3
Curve P-160 482 34 90 1956
Curve P-192 584 42 111 2174
Curve P-224 656 48 132 2296
Finally, Table 4 reports the total computing time
(ms) required on average by each of the two commu-
nicating parties to compute the shared key. As for the
previous case, each value is the average of the times
spent by users A and B. Notice that these values are
greater than the totals obtained by summing the val-
ues related to each step, since they include time spent
by parties in synchronization. As before, results are
related to each of the curves given in Table 1 and con-
sider both the cases of communication over a wired
LAN and through WiFi.
Table 4: Total computing time (ms) of the eFG protocol in
case of wired LAN and WiFi communications.
Curve Total ct wired LAN Total ct WiFi
Curve P-160 2002 2060
Curve P-192 2250 2302
Curve P-224 2384 2471
All the above results clearly show that using the
eFG protocol for key agreement using low cost, re-
source constrained embedded devices, such as the
Raspberry PI is viable to the point that it can be used
for real world applications.
7 CONCLUSIONS AND FUTURE
WORK
Implementations of advanced key-agreement proto-
cols are scarce, especially in case of embedded de-
vices. However, the security of networking through
embedded devices can greatly benefit from the im-
plementation of advanced key-agreement protocols.
This paper describes an implementation for embed-
ded devices of a two-party ID-based key agreement
protocol. We considered a variant of a fast, one-round
protocol introduced in (Fiore and Gennaro, 2010),
named eFG protocol. The eFG protocol makes use
of identity-based cryptography and is implemented
on elliptic curves, in order to achieve good perfor-
mances both in computing time and memory alloca-
tion size. These goals were confirmed by experimen-
PECCS2015-5thInternationalConferenceonPervasiveandEmbeddedComputingandCommunicationSystems
122

tal tests, which show that eFG is viable for enabling
secure communications among resource-constrained,
embedded devices such as the Raspberry PIs.
As a next step, we are going to test a porting of our
implementation on wireless sensor network equipped
with low-pan devices (IEEE 802.15.4). More future
work includes the implementation of a related set of
protocols to manage the case of authenticated key
agreement for dynamic groups, plus some new ellip-
tic curves and related bilinear parings. Moreover, we
are working on a real-word scenario testbed in which
such protocols operate to secure a network of Rasp-
berry PI devices deployed for environmental moni-
toring in hostile environments.
REFERENCES
Akinyele, J. A., Green, M. D., and Rubin, A. D.
(2011). Charm: A framework for rapidly prototyp-
ing cryptosystems. Cryptology ePrint Archive, Report
2011/617. http://eprint.iacr.org/.
”ARM” (2014). Arm jazelle. http://www.arm.com/
products/processors/technologies/jazelle.php.
Boyd, C. and Mathuria, A. (2003). Protocols for authenti-
cation and key establishment. Springer.
Brown, M., Hankerson, D., L
´
opez, J., and Menezes, A.
(2001). Software implementation of the NIST elliptic
curves over prime fields. Springer.
Chen, L., Cheng, Z., and Smart, N. P. (2007). Identity-based
key agreement protocols from pairings. International
Journal of Information Security, 6(4):213–241.
De Caro, A. and Iovino, V. (2011). jpbc: Java pairing based
cryptography. In Proceedings of the 16th IEEE Sym-
posium on Computers and Communications, ISCC
2011, pages 850–855, Kerkyra, Corfu, Greece, June
28 - July 1.
De Caro, A. and Iovino, V. (2011). jpbc: Java pairing
based cryptography. In Computers and Communica-
tions (ISCC), 2011 IEEE Symposium on, pages 850–
855. IEEE.
Diffie, W. and Hellman, M. E. (1976). New directions in
cryptography. Information Theory, IEEE Transactions
on, 22(6):644–654.
Dong, C. (2010). Jpair: A quick introduction.
https://personal.cis.strath.ac.uk/changyu.dong/jpair/
intro.html.
Fiore, D. and Gennaro, R. (2010). Identity-based key ex-
change protocols without pairings. In Transactions on
Computational Science X, pages 42–77. Springer.
JGroups (2014). Jgroups toolkit. http://www.jgroups.org/.
Joux, A. (2000). A one round protocol for tripartite diffie–
hellman. In Algorithmic number theory, pages 385–
393. Springer.
Law, L., Menezes, A., Qu, M., Solinas, J., and Vanstone,
S. (2003). An efficient protocol for authenticated
key agreement. Designs, Codes and Cryptography,
28(2):119–134.
Lynn, B. (2007). On the implementation of pairing-based
cryptosystems. PhD thesis, Stanford University.
McCullagh, N. and Barreto, P. S. (2005). A new two-
party identity-based authenticated key agreement. In
Topics in Cryptology–CT-RSA 2005, pages 262–274.
Springer.
Menezes, A. J., Van Oorschot, P. C., and Vanstone, S. A.
(2010). Handbook of applied cryptography. CRC
press.
Miller, V. S. (2004). The weil pairing, and its efficient cal-
culation. Journal of Cryptology, 17(4):235–261.
Monk, S. (2014). Raspberry Pi Cookbook. O’Reilly Media,
Inc., 1st edition.
Okamoto, T., Tso, R., and Okamoto, E. (2005). One-way
and two-party authenticated id-based key agreement
protocols using pairing. In Modeling Decisions for
Artificial Intelligence, pages 122–133. Springer.
”Oracle” (2014). Java se hotspot at a glance.
http://www.oracle.com/technetwork/java/javase/tech/
index-jsp-136373.html.
”Pi4j” (2014). Pi4j project. http://pi4j.com/.
”Raspian” (2014). Raspbian operating system. http://
www.raspbian.org/.
Schnorr, C.-P. (1991). Efficient signature generation by
smart cards. Journal of cryptology, 4(3):161–174.
Shamir, A. (1985). Identity-based cryptosystems and signa-
ture schemes. In Advances in cryptology, pages 47–
53. Springer.
ImplementingIdentity-basedKeyAgreementinEmbeddedDevices
123
