
A Proposal for Network Coding with the IEEE 802.15.6 Standard
Xiaomeng Shi and Muriel M´edard
Department of Electrical Engineering and Computer Science,
Massachusetts Institute of Technology, 77 Massachusetts Ave., Cambridge, MA, U.S.A.
Keywords:
Network Coding, IEEE 802.15.6, WBAN, Energy Efficiency.
Abstract:
We examine the Medium Access Control sublayer of the IEEE 802.15.6 Wireless Body Area Network
(WBAN) standard, and propose minor modifications to the standard so that linear random network coding can
be included to help improve energy efficiency and throughput of WBANs compatible with the standard. Both
generation-based and sliding window approaches are possible, and a group-block acknowledgment scheme can
be implemented by modifying block acknowledgment control type frames. Discussions on potential energy
and throughput advantages of network coding are provided.
1 INTRODUCTION
The IEEE 802.15.6 WBAN standard (IEEE, 2012)
was published by the IEEE 802.15 Task Group 6
(TG6) in 2012 to overcome limitations of other Per-
sonal Area Network standards such as IEEE 802.15.4
(Zigbee) and IEEE 802.15.1 (Bluetooth). Since its
initial draft proposal, many studies have been con-
ducted to analyze the performance of medium access
mechanisms of this standard. For example, (Ullah and
Kwak, 2011) presents theoretical throughput and de-
lay limits and bandwidth efficiency results for ideal
channels without transmission errors, while (Tach-
tatzis et al., 2010) analyzes the energy lifetime of pe-
riodic scheduled access modes.
In this article, we propose to incorporate the use
of network coding (NC) into a WBAN arranged in a
star topology. By examining the IEEE 802.15.6 stan-
dard, we propose modifications to frame acknowledg-
ment schemes so that linear NC can be included in the
communication process, thus potentially improve the
energy efficiency and/or throughput of the system.
Although still a relatively young field, NC has
shown great potential in addressing issues such as net-
work throughput, robustness, and security (Fragouli
and Soljanin, 2007). Unlike traditional routing, NC
encourages nodes within a network to mix data be-
fore forwarding. Data flows are viewed as informa-
tion which can be combined algebraically. As long
as enough degrees of freedom, in the form of linearly
independent coded packets or symbols, are received,
the original uncoded data can be recovered.
The concept of NC is introduced in the seminal
paper (Ahlswede et al., 2000). The authors in (Koetter
and M´edard, 2003) provide an algebraic framework
for linear network codes, while (Ho et al., 2006) intro-
duces random linear network codes (RLNC), showing
that RLNC achieves multicast capacity probabilisti-
cally in a distributed manner, exponentially in the fi-
nite field size for coding operations. Several practi-
cal approaches of NC have since been proposed to
bridge theoretical studies to real applications. To take
into account randomly generated coding coefficients,
a generation-based scheme with concurrently trans-
mitted coefficients is considered in (Chou et al., 2003)
to allow NC to co-exist with current network pro-
tocols. Simple XOR codes can be implemented in
two-way relay networks and four-way cross topolo-
gies by inserting an additional NC layer between the
IP and MAC layers of the 802.11 protocol (Katti et al.,
2008). Apart from such generation-based schemes, a
sliding-window approach similar to that used in the
Transmission Control Protocol (TCP) for flow and
congestion control can be introduced for NC, such
that end-to-end packet losses in wireless networks us-
ing TCP can be masked (Sundararajan et al., 2009).
Moreover, the important potential of NC in pro-
viding improved efficiency in lossy networks in a dis-
tributed manner makes it an attractive option for en-
ergy constrained WBANs. The rateless nature of net-
work codes can lower energy consumption by reduc-
ing the amount of medium access control needed, and
by reducing energy used by nodes to wake up peri-
odically to receive timing allocations from the control
145
Shi X. and Médard M..
A Proposal for Network Coding with the IEEE 802.15.6 Standard.
DOI: 10.5220/0005245701450150
In Proceedings of the 4th International Conference on Sensor Networks (SENSORNETS-2015), pages 145-150
ISBN: 978-989-758-086-4
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

base station (Shih et al., 2001). In a star network,
by adapting redundancy based on transmission and
reception energies for data and control packets, sig-
nificant energy reduction may be achieved when NC
is incorporated and as the receiving energy per con-
trol packet increases from equal to much larger than
the transmitting energy per data packet (Shi et al.,
2011). Achievable gains also increase as more nodes
are added to the star network, and when the channels
seen by different nodes become more asymmetric.
In what follows, we provide a summary of the
medium access control (MAC) sublayer specifica-
tions of the 802.15.6 WBAN standard, and describe
how NC can be included with minimal changes to the
MAC layer, with discussions on the potential through-
put and energy benefits of using a coded system.
2 THE MAC SUBLAYER
SPECIFICATION OF THE IEEE
802.15.6 STANDARD
In a WBAN compatible with the IEEE 802.15.6 stan-
dard, there are multiple nodes but one and only one
hub. The hub coordinates medium access among dif-
ferent nodes. Nodes can be arranged into a star-
shaped topology, or into a two-hop extended star
topology, where information are exchanged between
the hub and a node via another relay-capable node.
In a WBAN, a hub may or may not provide time
referenced allocations to all nodes. When it does, the
MAC sublayer uses a slotted time reference model,
with the time axis divided into beacon periods (su-
perframes) of equal lengths, and each beacon period
divided into allocation intervals of equal length. A
frame transmission may span more than one alloca-
tion interval, with start and end times not necessarily
aligned to interval boundaries. A beacon frame may
be broadcasted by the hub at the beginning of or at a
shifted location within each beacon period.
There are three possible access modes within a
WBAN: beacon mode with beacon periods (super-
frames), non-beacon mode with superframes, and
non-beacon mode without superframes. In beacon
mode with beacon periods, a beacon frame is broad-
casted at the beginning of each beacon period to spec-
ify the length of allocation intervals within the super-
frame, the start and stop times of the access phases
present, and the number of inactive superframes to
follow the current active superframe. Four types of
access phases can be present in a beacon frame, cov-
ering contention-based random access, scheduled ac-
cess, and improvised polling/posting.
In beacon and non-beacon modes with super-
frames, scheduled access may be used to obtain up-
link and downlink allocations, and scheduled-polling
may be used to obtain bilink allocations. To obtain
one or more new scheduled allocations, a node sends a
Connection Request frame to the hub, which in return
sends a Connection Assignment frame to the node to
grant access when possible. Existing scheduled allo-
cations can be modified or terminated by the trans-
mission of a new Connection Request frame.
2.1 MAC Frame Format, Frame Types
and Subtypes
A MAC frame consists a header, a variable-length
frame body, and a cyclic redundancy check sequence.
The MACframe body has a maximum possible length
of 255 octets. The MAC header contains the sender
and receiver IDs, as well as a frame control sequence.
The contents of a MAC frame differ among dif-
ferent frame types and subtypes. In the MAC frame
header, a Frame Type field can take on four dif-
ferent values, representing management, data, con-
trol and reserved frames. A management type frame
can be further divided into beacon, security-related,
connection-related, and reserved frame subtypes. In
beacon mode with beacon periods, a beacon frame is
multicasted by the hub at the beginning of every bea-
con period. Its frame payload contains the length of
the current beacon period, and timing allocation in-
formation such as the time duration of each alloca-
tion slot and start and stop times of each access in-
terval. Data type frames are divided into subtypes
depending on user priority levels and data subtypes.
A control type frame is used by a node or a hub to
acknowledge the recipient of a management type or
a data type frame. A node or hub receiving a control
type frame does not generate any further acknowledg-
ments. In each transmitted management type or data
type frame, an Ack Policy field in the MAC header in-
dicates the type of acknowledgment requested by the
current frame.
2.2 Modes of Frame Acknowledgments
The Ack Policy field of the MAC header indicates the
type of acknowledgment requested. Different values
represent four different policies.
No acknowledgment (N-Ack): an N-Ack indicates
that the current frame does not require an acknowl-
edgment from the recipient. A frame with an N-Ack
request can be transmitted by either the hub or a node.
Control type frames have their Ack Policy fields set to
N-Ack.
SENSORNETS2015-4thInternationalConferenceonSensorNetworks
146

Group acknowledgment (G-Ack): G-Acks are ap-
plicable to data frames sent to a hub. A G-Ack is
requested if the frame is of data type, its Ack Policy
field is set to N-Ack, and its frame subtype field is
set to a pre-defined constant. The hub acknowledges
frames with G-Ack requests from multiple nodes to-
gether through the use of a G-Ack multicast, in the
form of a frame subtype called B2 frames. A B2
frame contains a set of node IDs (NIDs) to indicate
nodes from which the hub has received a frame with
G-Ack requests since the last transmitted B2 frame.
A node may retry the frame with the G-Ack request if
it fails to receive the expected B2 frame, or if its NID
does not appear in a received B2 frame. Figure 61 of
(IEEE, 2012) gives an example of G-Acks.
Immediate acknowledgment (I-Ack): a frame with
an I-Ack request can be transmitted by either the hub
or a node. The frame is acknowledged by an I-Ack
immediately upon the frame’s reception. The recip-
ient sends back the I-Ack frame after the end of the
frame reception, after a given interframe spacing, de-
noted by pSIFS (e.g. 75µs). Management type frames
are always transmitted with an I-Ack request. Data
type frames can be transmitted with a request for any
one of the four acknowledgment modes.
Block acknowledgment later (L-Ack) and Block
acknowledgment (B-Ack): a frame with an L-Ack or a
B-Ack request can be transmitted by either the hub or
a node. The transmitted frame must contain a whole
MAC Service Data Unit (MSDU). Frames with L-
Ack requests are not followed by any I-Acks. Instead,
blocks of frames with L-Acks are acknowledged by
a B-Ack frame pSISF after the reception of the last
frame with a B-Ack request. Figure 63 of (IEEE,
2012) illustrates the block transmission scheme estab-
lished through the use of L-Acks and B-Acks. During
block transmission, the source shall send frames in
the order of non-decreasing sequence numbers, with
repetitions if retransmissions take place. Figure 63 of
(IEEE, 2012) provides two instances of retries. All
frames in a block transmission should be of the same
type and subtype. A block transmission may span
more than one allocation interval.
Three fields of a B-Ack frame function together
to provide acknowledgments to a block of data: Old-
est Frame Expected, Next Block Size, and Frame Sta-
tus Bitmap. The Oldest Frame Expected field is not
present if there is only one frame in the current block.
When present, it is set to the sequence number of
the oldest frame that is expected but has not been re-
ceived. If all frames in the block has been received,
the Oldest Frame Field is set to one plus the sequence
number of the frame preceding the B-Ack frame.
Thus, the Oldest Frame Expected field indicates the
next expected frame, assuming all frames are trans-
mitted in order. This is similar to acknowledgments
sent in the Transmission Control Protocol (TCP). The
Next Block Size field is not present if only one new
frame is expected and allowed. When present, it is
set to the maximum number of frames that can be in-
cluded in the next block transmission. The one byte-
long Frame Status Bitmap field indicates the reception
status of each successive frame in the block transmis-
sion, starting from the one immediately next to the
oldest expected frame in sequence number. Succes-
sive frames are frames with successivesequence num-
bers. Hence, acknowledgments are packet specific;
any un-acknowledged packet is retransmitted in the
next block. Moreover, since frames in a block trans-
mission are required to contain whole MSDUs, the re-
cipient may implement a timeout mechanism so that
MSDUs can be released to the upper layers without
the reception of all frames in the block.
Other than I-Ack, B-Ack, and B2 frames, I-
Ack+Poll and B-Ack+Poll control type frames can
also be transmitted by the hub to grant immediate
polled allocations or to announce a future poll or
post request, in addition to frame acknowledgments.
Moreover, a node or a hub shall treat an expected
frame, such as an I-Ack or B-Ack frame, as not ar-
riving after waiting for the physical layer preamble of
the frame for a given amount of time.
3 INCORPORATION OF
NETWORK CODES
A comparison between the acknowledgment modes
offered by the IEEE 802.15.6 standard, and the net-
work coding (NC) scheme in (Shi et al., 2011) shows
that NC can be easily incorporated into the standard.
In this subsection, we explain how this can be carried
out. The quantitative advantages of network coded
transmissions require detailed analysis of actual im-
plementations of the standard. We do not attempt to
characterize the performance of such systems here.
3.1 Generation-based Approach
NC can be carried out at individual nodes using a
generation-based approach (Chou et al., 2003). First,
the block acknowledgment mode with L-Acks/B-
Acks can be used with coded frames transmitted by
a node or the hub. At the transmitter side, the MAC
frame payload of a given number of packets, to be
transmitted in a block, can be coded together. Each
block is thus a generation. With RLNC, coding coeffi-
cients can be attached as part of the payload. With de-
AProposalforNetworkCodingwiththeIEEE802.15.6Standard
147
Hub
Transmits
B2
Beacon
pMIFS
pMIFS
Node 1 uplink
NC
Data
(GB-
Ack)
Nodes
Transmit
NC
Data
(GB-
Ack)
NC
Data
(GB-
Ack)
NC
Data
(GB-
Ack)
Node 1 uplink
NC
Data
(GB-
Ack)
NC
Data
(GB-
Ack)
Node 2 uplink
NC
Data
(GB-
Ack)
NC
Data
(GB-
Ack)
NC
Data
(GB-
Ack)
Node 1 uplink
allocation interval
Burst Mode
Node 1 uplink
allocation interval
Node 2 uplink
allocation interval
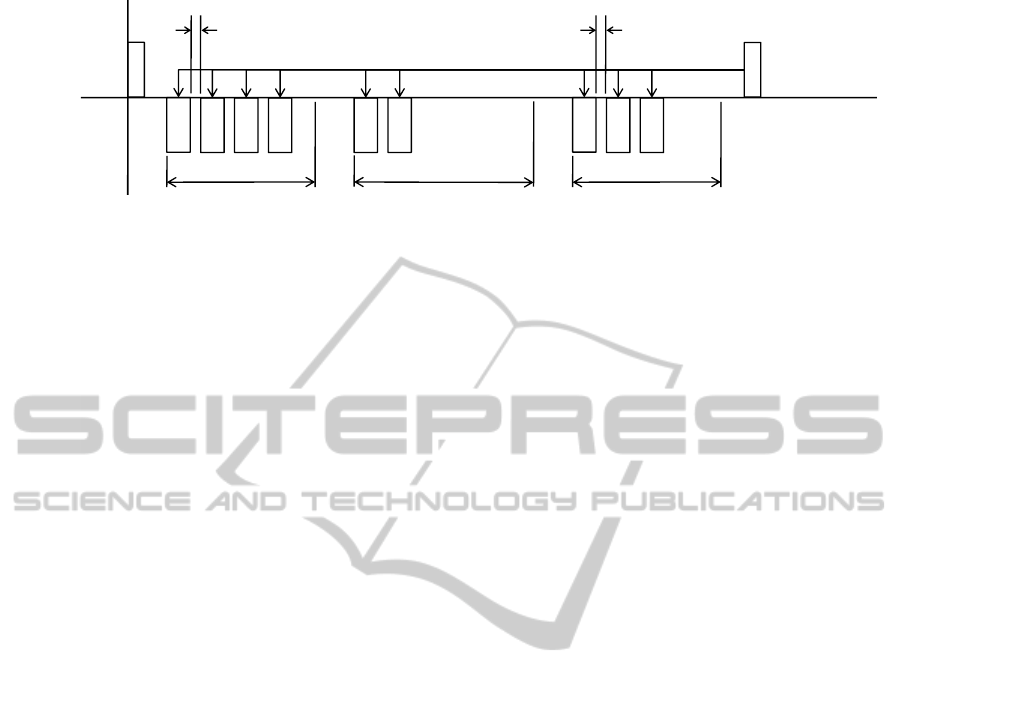
Figure 1: Example of coded data blocks with Group-Block Acknowledgments (GB-Ack).
terministic codes, coding coefficients are pre-defined.
In the MAC frame control header of the transmitted
frame, a reserved bit can indicate whether the current
packet is coded. With coding, redundant packets can
be added to compensate for potential losses. As dis-
cussed in (Shi et al., 2011), a reasonable level of re-
dundancy can be computed heuristically. Packet loss
rates can be estimated and redundancy levels can be
adjusted accordingly. A systematic network code can
be used to minimize coding energy. All coded frames
except the last one carry an L-Ack request to the re-
ceiver, while the last coded frame carries a B-Ack re-
quest to the receiver.
At the receiver side, assuming well-chosen coef-
ficients, each arriving packet is a unique degree of
freedom (DOF), innovative to the receiver with high
probability. Whenever a B-Ack request is received,
the receiver can use the Frame Status Bitmap field to
acknowledge to the transmitter the number of DOFs
received, or the number of DOFs still expected. The
Oldest Frame Expected field can be modified to indi-
cate the generation number. When uncoded, only 9
frames can be acknowledged in each block (indicated
by the Oldest Frame Expected field, plus 8 bits in the
Frame Status Bitmap). With coded data, more than 9
frames can be included in a single block.
Moreover, B-Ack and G-Ack modes can be com-
bined into a Group-Block acknowledgment(GB-Ack)
mode. Figure 1 shows a possible use of GB-Acks
in scheduled access mode, for data blocks uploaded
from two nodes to a hub. At each node, data frames in
a block are coded with random or deterministic coeffi-
cients. In the MAC frame control header of the trans-
mitted frame, a reserved bit can be used to indicate if
the current packet is coded. At the hub, a B2 frame is
broadcasted at a pre-determined allocation slot when
G-Acks are requested by multiple nodes. A B2 frame
contains a set of NIDs, each representing a node to be
group acknowledged. Since there can be a maximum
of 64 nodes within a WBAN, each with a single-octet
NID, but the B2 frame payload can be of 255 octets
long, it is possible to append to the current B2 frame
payload the numbers of DOFs successfully received
from each node for its respective current generation.
For example, a one-octet field can be added to the B2
frame payload for each node from which the hub has
received coded frames in the current block. The first
4 bits can represent the generation number, while the
last 4 bits can represent the number of DOFs received.
There are several possible advantages of using
coded transmissions with B-Acks or GB-Acks. First,
independently coded packets are individual DOFs,
thus acknowledgments do not need to specify which
individual packet has been received successfully. In
addition, with coded payloads, more than 9 frames
can be included in a block transmission.
From a throughput perspective, in cases where
an acknowledgment is lost and retransmission occurs
without the loss of the actual data frame, a retrans-
mitted data frame is wasteful if uncoded. By com-
parison, if the retransmitted frame is coded with a set
of coefficients linearly independent from the previous
frame, the retransmission is innovative, carrying one
more DOF to the hub. In addition, in burst mode block
transmissions, interframe spacing between successive
frames is smaller than the I-Ack case. Thus with less
frequent transmissions, the overall throughput of in-
dividual nodes can be higher. Figure 2 shows an sam-
ple timing diagram of I-Ack, B-Ack (coded or un-
coded) and GB-Ack schemes. Here Guard Intervals
(GT) are centrally added in between allocation inter-
vals instead of distributively included in each alloca-
tion interval. Although we do not provide detailed
computations here, it is not difficult to show that the
number of data frames transmitted in an allocation in-
terval with GB-Acks can be higher than the number of
data frames transmitted in the same allocation interval
with I-Acks or B-Acks, although if the allocation in-
terval is very short, with high probability, the same
number of frames fits into the interval regardless if B-
Acks or GB-Acks is used. It is also not hard to see
that if the number of nodes in the WBAN is large,
using GB-Ack is beneficial in terms of reducing the
total number of acknowledgment frames transmitted
in one superframe.
From an energy perspective, given a fixed num-
SENSORNETS2015-4thInternationalConferenceonSensorNetworks
148

Hub
I
-
pSIFS
I
-
Hub
pMIFS
pSIFS
B
Hub
Transmits
Data
(I-
Ack)
-
Ack
Nodes
Transmit
Data
(I-
Ack)
-
Ack
Hub
Transmits
Nodes
Transmit
NC
Data
(L-
Ack
)
NC
Data
(L-
Ack
)
NC
Data
(B-
Ack
)
B
-Ack
•••
•••
Node 1 uplink
allocation interval
pSIFS
GT
Ack
)
Ack
)
Ack
)
Node 1 uplink
allocation interval
GT
Node 2 uplink
allocation interval
•••
Node 2 uplink
allocation interval
•••
pSIFS
pMIFS
(a) (b)
Hub
Transmits
NC
NC
NC
NC
NC
NC
B2
pSIFS
pMIFS
Node 1 uplink
allocation interval
Burst Mode
NC
Data
(GB-
Ack)
Nodes
Transmit
NC
Data
(GB-
Ack)
NC
Data
(GB-
Ack)
NC
Data
(GB-
Ack)
Node 2 uplink
allocation interval
NC
Data
(GB-
Ack)
NC
Data
(GB-
Ack)
GT
Burst Mode
(c)
Figure 2: Timing examples (a) uncoded transmission with I-Acks; (b) coded data transmission with B-Acks and L-Acks; and
(c) coded data transmission with GB-Acks.
ber of data frames to transmit by a node, block trans-
mission requires the node to be active for a shorter
period of time than when I-Acks are used. Such en-
ergy savings become more significant when switching
between transmission and reception modes take up a
non-negligibleamount of power. Moreover, with cod-
ing, it is always possible to transmit more redundan-
cies when listening to acknowledgment packets costs
more energy. Nonetheless, coding requires additional
energy, and a tradeoff exists between encoding energy
and transmission/reception energy.
From a reliability perspective, coded transmis-
sions allow redundant coded frames to be transmit-
ted a priori to compensate for possible losses. NC
thus provides another reliability mechanism, allowing
less stringent requirements on PHY design. In cases
where channel quality is low and scheduled alloca-
tions for a node is aborted because none of the trans-
mitted frames is receivedsuccessfully at the hub, such
provision for losses may prolong the duration of the
connection between a node to the hub.
3.2 Sliding Window Approach
An alternative to the generation-based NC scheme is
to use a sliding window approach, as proposed by
(Sundararajan et al., 2009) for interfacing NC with
TCP/IP. At the transmitter, data frame payloads are
put into a coding window of a fixed size as they ar-
rive from the upper layer, as long as the coding win-
dow is not full. A frame is removed from the coding
window when it is acknowledged by the receiver. At
the receiver, coding coefficients from received pack-
ets are put into a matrix and passed through Gaus-
sian elimination into a reduced row echelon form.
Frames on the pivot columns are taken as seen, and
are acknowledged in the next available acknowledg-
ment frame. In short, a receiver is said to have seen
a packet p
k
if it can compute a linear combination of
the form p
k
+
∑
l>k
α
l
p
l
, where α
l
are coding coeffi-
cients, and k represents frame sequence number. It
can be shown that if all frames involved in the coding
operations have been seen, all coded packets can be
decoded. Seen packets are thus dropped from the cod-
ing window at the transmitter side. The notion of seen
packets defines an ordering for the DOF conveyed by
coded packets: for every additional DOF received at
the hub, the next data frame in the coding window is
acknowledged and dropped from subsequent coding
operations.
The sliding window approach can be used in a
WBAN similar to the generation-based approach. At
the transmitter, data frame payloads are coded and
sent with redundancies. At the receiver, either B-Acks
or GB-Acks are used. The Oldest Expected Frame
field of a B-Ack frame can be modified to represent
the oldest expected seen frame. Frames which have
been seen are subsequently removed from the coding
AProposalforNetworkCodingwiththeIEEE802.15.6Standard
149

window at the transmitter. For GB-Ack frames, an
Oldest Expected Seen Frame field can be added to in-
dicate frames to be removed from the coding window
of each transmitting node. A systematic code can also
be used, and the transmission scheme can operate in a
rateless fashion if needed.
An advantage of the sliding window approach is to
allow new data to be added to the transmission queue
incrementally as they arrive at the MAC sublayer and
removed as soon as they are seen at the receiver. A
pre-defined generation size is not required, although
the size of the coding window can vary, depending on
the amount of computation and memory available at
sensor nodes. When data rate is not very high, fast re-
moval of data packets from the coding window is ben-
eficial, since fewer coding operations are performed
for subsequent transmission rounds. Another advan-
tage of the sliding window approach is that its retrans-
mission requests are very short, since it only needs
to acknowledge the last seen DOF. A disadvantage
of the sliding window approach is that even though
memory and energy are assumed to be abundant at
the hub, decoding delay is larger. Seen packets may
have to stay in the receiver queue for longer periods
than the generation-based case, before they can be de-
coded. This problem can be mitigated if the transmit-
ter flushes its coding window periodically.
4 CONCLUSIONS
In this article, we provide a brief description of the
medium access control sublayer of the IEEE 802.15.6
WBAN standard, and consider the incorporation of
network coding (NC) in WBANs compatible with the
standard. Both generation-based and sliding window
approaches are possible, and a group-block acknowl-
edgment can be implemented by modifying block ac-
knowledgmentcontrol type frames. With NC, retrans-
mission requests are simpler, and redundant packets
can be transmitted a priori, in expectation of packet
losses. Such redundancies can be seen as a reliabil-
ity mechanism in addition to forward error correc-
tion schemes in the physical layer. Allowing more
coded packets to be sent in each round also allows
the overall transmission process to terminate in fewer
rounds, leading to potential savings in energy use.
Since the standard only provides general rules and
guidelines, actual implementations can differ in terms
of hardware and signal processing algorithm design.
Whether coding helps in terms of energy or through-
put thus depends on how the standard is realized.
ACKNOWLEDGEMENT
This work was supported by the Interconnect Focus
Center (IFC), one of the six research centers funded
under the Focus Center Research Program (FCRP),
a Semiconductor Research Corporation (SRC) pro-
gram, under subcontract # RA306-S 1.
REFERENCES
Ahlswede, R., Cai, N., Li, S., and Yeung, R. (2000). Net-
work information flow. IEEE Trans. on Info. Theory,
46(4):1204–1216.
Chou, P., Wu, Y., and Jain, K. (2003). Practical network
coding. In Proceedings of the Annual Allerton Con-
ference on Communication, Control and Computing,
volume 41, pages 40–49. The University; 1998.
Fragouli, C. and Soljanin, E. (2007). Network coding fun-
damentals. Foundations and Trends
R
in Networking,
2(1):1–133.
Ho, T., M´edard, M., Koetter, R., Karger, D., Effros, M., Shi,
J., and Leong, B. (2006). A random linear network
coding approach to multicast. IEEE Trans. on Info.
Theory, 52(10):4413–4430.
IEEE (2012). IEEE Standard for Local and metropolitan
area networks - Part 15.6: Wireless Body Area Net-
works.
Katti, S., Rahul, H., Hu, W., Katabi, D., M´edard, M., and
Crowcroft, J. (2008). XORs in the air: practical wire-
less network coding. IEEE/ACM Trans. on Network-
ing (TON), 16(3):497–510.
Koetter, R. and M´edard, M. (2003). An algebraic approach
to network coding. IEEE/ACM Trans. on Networking
(TON), 11(5):782–795.
Shi, X., M´edard, M., and Lucani, D. (2011). When both
transmitting and receiving energies matter: an appli-
cation of network coding in WBANs. In NETWORK-
ING 2011 Workshops, pages 119–128. Springer.
Shih, E., Cho, S., Ickes, N., Min, R., Sinha, A., Wang, A.,
and Chandrakasan, A. (2001). Physical layer driven
protocol and algorithm design for energy-efficient
wireless sensor networks. In Proceedings of the 7th
annual international conference on Mobile comput-
ing and networking, pages 272–287. ACM New York,
NY, USA.
Sundararajan, J., Shah, D., M´edard, M., Mitzenmacher, M.,
and Barros, J. (2009). Network coding meets TCP. In
Proceedings of IEEE INFOCOM, pages 280–288.
Tachtatzis, C., Di Franco, F., Tracey, D., Timmons, N.,
and Morrison, J. (2010). An energy analysis of IEEE
802.15.6 scheduled access modes. In GLOBECOM
Workshops, 2010 IEEE, pages 1270–1275. IEEE.
Ullah, S. and Kwak, K. (2011). Throughput and delay limits
of IEEE 802.15.6. In WCNC, 2011 IEEE, pages 174–
178. IEEE.
SENSORNETS2015-4thInternationalConferenceonSensorNetworks
150
