
Hybrid-intelligent Mobile Indoor Location using Wi-Fi Signals
Location Method using Data Mining Algorithms and Type-2 Fuzzy Logic Systems
Manuel Casta
˜
n
´
on-Puga, Abby Salazar-Corrales, Carelia Gaxiola-Pacheco, Guillermo Licea,
Miguel Flores-Parra and Eduardo Ahumada-Tello
Autonomous University of Baja California, Tijuana, Mexico
Keywords:
Location, Wi-Fi, Situational Awareness, Fuzzy Logic, Data Mining, Smartphone.
Abstract:
Technology with situational awareness needs a lot of information of the environment to execute the correct
task at the correct moment. Location of the user is typical information to achieve the goal. This work proposes
a mobile application that enables the indoor location of smartphones using the potential infrastructure given by
Wireless Local Area Networks. This infrastructure goes beyond GPS (Global Position System) where signal is
weak or is not available for indoors. This application uses an alternative and unconventional method to indoor
location using Wi- Fi RSSI fingerprinting as well as an estimation based on Type-2 fuzzy inference systems
provided by the developed framework JT2FIS. Wi-Fi Fingerprinting creates a radio map of a given area based
on the RSSI data from several access points (APs) and generates a set of RSSI data for a given zone location.
Consequently Data Mining is required for clustering the obtained set of data and generating the structure of
a Type-2 Mamdani or Takagi-Sugeno Fuzzy Inference System; thus new RSSI values are introduced to the
Type-2 Fuzzy Inference System to obtain an estimation of the user zone location.
1 INTRODUCTION
The growing technology and advanced algorithms can
generate a lot of useful information to be used to im-
prove other tasks. Also with recent advances in tech-
nology exists the possibility of connecting different
devices using wireless networks to transparently in-
teract with the environment and seamlessly with peo-
ple. The challenge of this idea is to find ways to know
the particular context or situation in time and space
to make a decision based on it without the aware-
ness of the user. Devices require algorithms with the
ability to understand the context information so that
a given system can adapt to it and behave in a cer-
tain way. The behavior of a person frequently de-
pends on the context. Human nature enables us to
be aware of a lot of variables at a time that influence
a person to behavior in a certain way. Context aware-
ness could be a more suitable technological for the
needs of the moment. In order to understand the con-
text, it is necessary to have in mind different factors
which vary depending on the activity to be performed
such as current weather or temperature, atmospheric
pressure, lighting from one place, position of an ob-
ject, the place where a person is, among others. Some
other variables are more complex to detect such as the
mood of a person or the identity of other persons near
the target person. On other hand, there are variables
that are useful to determine more of these variables,
an example is the location of persons or objects; this
can help to detect the number of persons in a room or
if certain users are near. The proposed mobile appli-
cation estimates the indoor location of the user using a
hybrid-intelligent method that makes use of Wi-Fi Re-
ceived Strength Signal Indicators (RSSIs). The data
mining and fuzzy logic methods were implemented
using the developed JT2FIS framework.
1.1 Situational Awareness
In the past, objects that could understand their envi-
ronment, communicate and properly respond without
the need of direct intervention of man looked distant
due to the complexity involved. However, nowadays
this is more possible mainly by two factors: because
in the last years the technological advancement has
been increasing, and also because of the great increase
of devices connected to different networks, such as
Internet (Sanchez et al., 2014). The context is any
information that can be used to characterize the situa-
tion of an entity. An entity is a person, place, or object
that is considered relevant to the interaction between
609
Castañón-Puga M., Salazar-Corrales A., Gaxiola-Pacheco C., Licea G., Flores-Parra M. and Ahumada-Tello E..
Hybrid-Intelligent Mobile Indoor Location Using Wi-Fi Signals - Location Method Using Data Mining Algorithms and Type-2 Fuzzy Logic Systems.
DOI: 10.5220/0005369806090615
In Proceedings of the 17th International Conference on Enterprise Information Systems (ICEIS-2015), pages 609-615
ISBN: 978-989-758-096-3
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

a user and an application, including the user and ap-
plications themselves (Dey, 2001). Devices with the
capability of understanding the context are an impor-
tant key for the non-human intervention in technology
tasks. The context or situational awareness parameter
of this work is based on the location of the entity.
1.2 Technologies
Actual location techniques commonly use GPS, Blue-
tooth, or Radio Frequency Identification (RFID) tech-
nologies, among others (Chai et al., 2011). Despite
that, a disadvantage of GPS is that the satellite signals
are blocked by obstacles such as walls, in addition,
variations in weather or the presence of buildings re-
sults in approximations with errors of meters, so it is
not possible to use this system as a method for indoor
location (Navarro et al., 2011)(Hwang and Donghui,
2012). On the other hand, Bluetooth technology has
limited coverage; this communication is focused on
very short distances to achieve the location. Finally
RF is an expensive solution since it involves the in-
stallation of different sensors in the area where you
will estimate the location, so it is not an economically
viable method (Navarro et al., 2011). Consequently
acceptable alternative techniques are required to fit
with established infrastructures and satisfy the func-
tionality of indoor location with ease of use and an
affordable cost, as the use of technologies based on
Wi-Fi (Chai et al., 2011).
1.3 Location Methods
Triangulation and Trilateration: These methods map
RSSI as a function of distance that requires a steep
linear characterization curve in order to be properly
implemented. Functions describing these curves are
then used with live RSSI values as input to generate
an (x,y) location prediction (Chai et al., 2011). The
disadvantages of these methods are: to carry out the
synchronization of these values and that it needs a
model to determine the distance according to RSSI
values. This work is an alternative solution for local-
ization using a radio map of a given area based on
Wi-Fi RSSI data from three (or more) Access Points.
Some advantages are that this method works on in-
door environments with acceptable coverage, a min-
imum or null modification of the area infrastructure
is required, and is a less expensive option than others
(Navarro et al., 2011). The method proposed is based
on a FIS (Fuzzy Inference System) using a cluster-
ing method (Chiu, 1994), that is a fast, one-pass al-
gorithm for estimating the number of clusters and the
cluster centers in a set of data.
2 DATA MINING
The number of generated data is increasing alongside
the increase of technology, networks, and sensors. In
recent years, the use of new information technologies
has come to help handling large amount of data. One
evolution of these technologies is the data mining ex-
traction that allows representing knowledge of data
store implicitly in big databases. Data mining con-
tributes to understand data and identify patterns, re-
lationships, and dependencies that affect the final re-
sults. It creates predictive models that allow undis-
covered relationships through the data mining pro-
cess which are expressed as possible business rules
(Crows, 1999). Data mining is a multidisciplinary
field that combines techniques from machine learn-
ing, pattern recognition, statistics, database, and vi-
sualization, to direct it to the extraction and inter-
pretation of a huge database. The data mining fo-
cuses on filling the need to discover, predict, and fore-
cast the possible actions with some confidence factor
for each prediction (Han and Kamber, 1998). More-
over, it helps to make tactical and strategic decisions,
provided the decision power users, is able to mea-
sure actions and results in the best way, generates de-
scriptive models to explore and understand the data,
and identify patterns, relationships, and dependencies
that affect the final results. Creates predictive models
that allow undiscovered relationships through the data
mining process which are expressed as business rules
possible (Crows, 1999). Clustering of numerical data
forms is a type of data mining. The aim of clustering
methods is to identify natural grouping of data from
a large data set, such that a concise representation of
the systems behaviour is produced (Ren et al., 2006).
Once the clusters of a data set are identified the sys-
tem behaviour can be translated to the rules of a FIS.
Each cluster is translated as one rule of the FIS. Gen-
erally more rules describe in more detail the system
behavior so a better approximation on the evaluation
can be achieved or a better accuracy is gained (Ying
et al., 1998). It is important to consider the computa-
tional cost and the robustness of the system to define
the minimal resources needed to have an acceptable
system evaluation. Some cluster features, as size and
number, are controlled by the specific parameters in-
volved in different clustering techniques.
2.1 Fuzzy C-Means
Fuzzy C-Means clustering algorithm (FCM) (Bozkir
and Sezer, 2013)(Bezdek et al., 1984) makes use of a
membership function and centroid computation pro-
cedure iteratively to find the best centroid. The FCM
ICEIS2015-17thInternationalConferenceonEnterpriseInformationSystems
610
is one of the popular clustering algorithms. The ef-
fectiveness of the clustering method relies on the dis-
tance measure. FCM is the result of combining the
c-means approach with the handling of fuzzy data.
The result of this combination is adequate because it
considers the uncertainty presented in the data, avoid-
ing incorrect results, and creating crisp partitions in a
correct way (Bozkir and Sezer, 2013). Additionally
the FCM is used to acquire the adequate levels of the
set clustering parameters (Yin et al., 2013). In this
work the clustering algorithm FCM is used to obtain
the fuzzy rules of a Mamdani inference system that is
used to estimate the location of a device (smartphone
with Wi-Fi) as described in section 3.
2.2 Subtractive Method
Subtractive clustering operates by finding the optimal
data point to define a cluster center based on the den-
sity of surrounding data points. It reduces the com-
putational complexities and gives better distribution
of cluster centers in comparison with other clustering
algorithms (Ren et al., 2006). This method considers
each point as a potential center and, based on math-
ematical approximations, calculates the best choice
of center. Each cluster center can be considered as
a fuzzy rule of the system, and the cluster identi-
fied represents the antecedent of this rule. The mea-
sure of potential for a data is estimated based on the
distance of this data point from all other data points
(Vaidehi et al., 2008). The identification of a Takagi-
Sugeno (TSK) FLS using clustering involves forma-
tion of clusters in the data space and translation of
these clusters into TSK rules such that the model ob-
tained is close to the system to be identified.
3 TYPE-2 FUZZY LOGIC
The concept of a Type-2 fuzzy set was introduced by
Zadeh (Zadeh, 1965) as an extension of the concept
of usually Type-1 fuzzy sets. A Type-2 fuzzy set is
characterized by a membership function whose mem-
bership value for each element of the universe is a
membership function within the range [0, 1], unlike
the Type-1 fuzzy sets where the value of membership
is a numeric value in the range [0, 1]. The creation
of a fuzzy set depends on two aspects: the identifica-
tion of a universe of appropriate values and specify-
ing a membership function properly. The choice of
membership function is a subjective process, mean-
ing that different people can reach different conclu-
sions on the same concept. This subjectivity derives
from individual differences in the perception and ex-
pression of abstract concepts and it has little to do
with randomness. Therefore, subjectivity and ran-
domness of a fuzzy set are the main difference be-
tween the study of fuzzy sets and probability theory
(Jang et al., 1997). A Type-2 Fuzzy Logic System
(FLS) can be used when it is not possible to deter-
mine exact membership grades or its uncertainty in
the rules (Cai et al., 2007). In Type-1 fuzzy sets, once
the membership function is defined for a concept, this
is based on the subjective opinion of one or more in-
dividuals and shows no more than one value for each
element of the universe. In doing so, it loses some
of the ambiguity of the discussed concepts, especially
where people may have a slightly different opinion,
but they are considered valid. The Type-2 fuzzy sets
allow handling linguistic and numerical uncertainties.
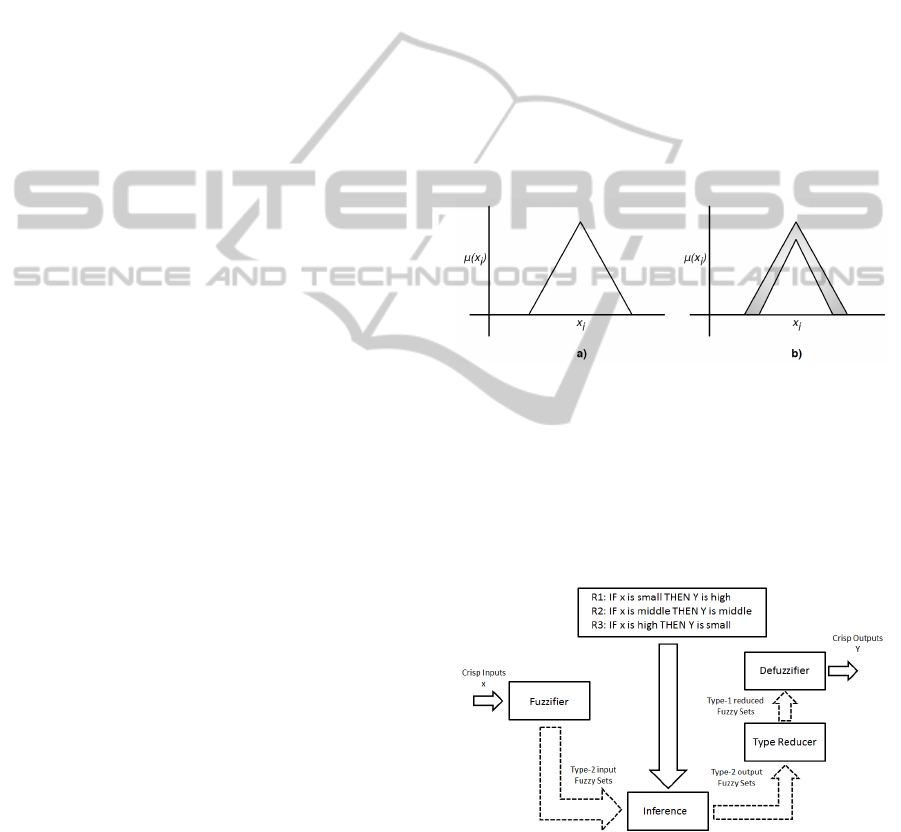
Figure 1 depicts two graphics of fuzzy sets: a) with
Type-1 fuzzy logic, and b) with Type-2 fuzzy logic.
Figure 1: Difference between type-1 and type-2 fuzzy logic
membership functions.
The FLS process is divided in four parts: fuzzifier,
rule base, fuzzy inference engine, and output proces-
sor. In type-2 a type reducer is needed in the output
processor to derive a type-1 set from the type-2 set
(Cai et al., 2007). Figure 2 shows a diagram with a
more detailed example of a FIS structure.
Figure 2: Fuzzy Inference System diagram.
3.1 Mamdani and Takagi-Sugeno FLSs
Mamdani and Takagi-Sugeno FLSs are popular and
are formed by IF-THEN rules with the same an-
tecedent structures. The difference between them is
in the consequent structures. The consequent of a
Hybrid-IntelligentMobileIndoorLocationUsingWi-FiSignals-LocationMethodUsingDataMiningAlgorithmsand
Type-2FuzzyLogicSystems
611

Mamdani rule is a fuzzy set while in TSK is a func-
tion, so TSK uses fewer fuzzy rules to represent a
real system than Mamdani (Cai et al., 2007). TSK
FLS was proposed in an effort to develop a system-
atic approach to generating fuzzy rules from a given
input-output data set. This model consists of rules
with fuzzy antecedents and mathematical function in
the consequent part. The antecedents divide the input
space into a set of fuzzy regions, while consequences
describe behaviour of system in those regions (Ren
et al., 2006).
4 JT2FIS FRAMEWORK
JT2FIS is a class library developed for Java. The
main purpose is to deploy a library for building in-
terval Type-2 fuzzy inference systems with an object-
oriented programming language. A fuzzy inference
system (FIS) is based on logical rules that can work
with numeric values or fuzzy inputs; these rules and
individual results are evaluated together to form a
fuzzy output, then, a numerical value must be passed
through a process of defuzzification if necessary. Be-
cause it is developed in native Java it is possible to in-
tegrate its methods with Android capabilities and the
smartphone resources.
4.1 JT2FIS Clustering
JT2FISClustering is a class library developed for
Java. The main purpose is to deploy a library to
build interval Type-2 fuzzy inference systems with
an object-oriented programming language from data
mining process. A clustering method is a data min-
ing classic technique used to discover fuzzy sets and
rules to congure the FIS from real data. The library
implements a Fuzzy C-Means or Subtractive Cluster-
ing algorithm for data mining.
5 CASE OF STUDY
There is an interest on detecting the location of peo-
ple in indoor spaces, such as shopping malls and mu-
seums, in order to generate statistics about the inter-
ests of the visitors in order to guide the new ideas and
improvements of the place to cover those estimated
interests. Another advantage of knowing the location
of a person is to show them relevant or interesting in-
formation related to that place and the profile of the
user. Therefore, this case of study proposes the loca-
tion of children inside an interactive museum with an
android mobile device using wireless signals from 3
different Access Points (APs) in the area. The case
of study was developed in an interactive museum ori-
ented for kids. This museum has three active floors
with different rooms on each one. The collected data
was taken in one room on the first floor with approxi-
mately twenty interactive modules about science. For
experimental purposes the test was divided in two
phases, the first with three not so close areas (darker
grey). The second collection of data was in four zones
(lighter grey) with few meters of distance (1 meter as
the minimum distance) as the representation shown
in Figure 3. Moreover, 3 APs are strategically posi-
tioned for getting enough coverage of the zones to do
the triangulation and estimation of the location of the
kids.
Figure 3: Case of study: zones and Access Points stablished
in the museum room.
The objective is to have enough RSSIs values from
the selected APs that describe each desired zone; then
a clustering method is applied in order to generate the
Mamdani or TKS Type-2 FISs to determine the lo-
cation. An important detail is that the location out-
side and between the selected zones is possible be-
cause when the membership of two outputs is approx-
imately equal and greater than the other output zones,
means the child or device is between the two of them.
For example, the case of the output of approximately
50% in zone 1, the output of zone 2 of about 50%, and
a low membership of zone 3, results in a position in
the showroom, meanwhile a 50% in zone 2 and zone
3, could be a zone between them that is the corridor
or the hall. And so, a collection and training of data
in every area from the place of study is not needed.
5.1 Collecting Location Data
The proposed mobile application uses the JT2FIS
class library to implement a fuzzy inference system
(FIS) and Fuzzy C-Means or Subtractive clustering
methods to do the estimation of the location process.
Wireless signals change because of different factors,
ICEIS2015-17thInternationalConferenceonEnterpriseInformationSystems
612

then the environment conditions when the values for
generating a specific FIS were taken, should be as
similar as possible to the time when the location was
done, or should do a new FIS for best results. The ap-
plication detects the wireless signals from at least the
three selected APs in the area to have enough sam-
ples of each different zone from each AP. There are
required at least three different APs to be able to do a
correct triangulation on the space. No stablished con-
nection in any moment is required with the APs, it is
only needed a scan of the RSSIs of the selected APs.
The collected data was taken in different zones using
a function to do a Wi-Fi scan with an Android device
searching RSSIs of three selected APs. The collec-
tion of every set of data from each zone was based on
a defined limited time. Some factors, such as the total
area of the zone, determine how many data you will
need to have a good coverage of valid points for that
zone. More quantity and diversity of data can help
to have less uncertainty to generate and have a better
evaluation of the FIS. Table 1 shows samples of data.
In this example, three different inputs obtained for the
collected data correspond to each of the three AP sig-
nals. At the same time, three different outputs were
generated (in-line during collection) with a value of
one in the corresponding zone the input data was col-
lected. These were saved as .cvs files.
Table 1: Sample of collected data for each zone and the
generated outputs.
Zone Input1 Input2 Input3 Output1 Output2 Output3
1 -78 -74 -54 1 0 0
1 -80 -72 -45 1 0 0
1 -72 -66 -58 1 0 0
2 -76 -60 -58 0 1 0
2 -74 -59 -59 0 1 0
2 -65 -56 -56 0 1 0
3 -65 -66 -64 0 0 1
3 -66 -67 -60 0 0 1
3 -68 -65 -67 0 0 1
... ... ... ... ... ... ...
5.2 Mining the Collected Data
Once the inputs and outputs in location are obtained,
the next step is to use the JT2FIS class library specific
methods inside the Android application to do the data
mining in-line. The first thing to do is the clustering,
which consists in detecting the different sets or groups
of data in all the collected data. As explained before,
each cluster found is a fuzzy rule that describes the
location system. Generally more fuzzy rules give us
a more descriptive behavior; also an increase on the
number of inputs and outputs increases the number of
rules and the complexity of the system too. Specif-
ically in location where zones are closer, a more de-
tailed description of the data is needed, thus increas-
ing the number of clusters may help. This can be con-
trolled by the FCM parameter number of clusters or
with the influence radio of each center of clusters in
Subtractive clustering method.
5.3 Results of Three Not so Close Zones
The first tests were executed in zones with more dis-
tance between them (2 meters approximately) as the
darker zones seen in Figure 3. Table 2 shows a com-
parison of results using Fuzzy C-Means clustering
method and Mamdani FLS. Increasing the number of
clusters will increase the regression coefficient that
indicates the similarity grade of the evaluation data
with the target real data. Also increasing the number
of clusters increases the time of generation and evalu-
ation of the FLS. Taking an acceptable regression co-
efficient of 0.85, the less rules cost was with a cluster
number of 4 with an acceptable coefficient of 0.8677.
This evaluation was generated by 1680 data per input
in total of the different 3 zones.
Table 2: Comparison table Mamdani 3 inputs 3 outputs.
Clusters Gen. time (secs) Eval. time (secs) Regression coeff.
3 5.09 0.03-0.1 0.7041
4 3.94 0.07-0.121 0.8677
7 20.41 0.07-0.12 0.8881
10 37.27 0.094-0.18 0.8913
15 56.86 0.14-0.21 0.8918
30 97.45 0.26-0.34 0.9005
70 161.66 0.61-0.97 0.9061
On the other hand, Table 3 shows Takagi-Sugeno
data with the same values used with FCM with Mam-
dani. In this case the modified parameter was the in-
fluence radius or granularity grade from 0.9 to 0.1. A
low radius tends to generate more clusters; the num-
ber of clusters is the number of rules obtained. A
low radius implies clusters with closer data. High ra-
dio implies clusters with dispersed data or low den-
sity, so generally will obtain a fewer number of clus-
ters. Also, the approximation to the clusters process is
slower in subtractive method than FCM, but even with
the same number of found clusters a better regression
coefficient is obtained with subtractive and TSK than
FCM and Mamdani. Meanwhile, the elapsing time of
evaluation decreases on TSK because the operations
of the consequent parts are mathematical equations
rather than Mamdanis fuzzy sets operations.
5.4 Results of Four Closer Zones
Another test was developed in four zones with less
Hybrid-IntelligentMobileIndoorLocationUsingWi-FiSignals-LocationMethodUsingDataMiningAlgorithmsand
Type-2FuzzyLogicSystems
613

Table 3: Comparison table Takagi-Sugeno 3 inputs 3 out-
puts.
Radius Clusters Gen. time (secs) Eval. time (milli secs) Regression coeff.
0.9 4 217.96 3.1 - 3.8 0.7361
0.7 4 217.91 3.1 - 5.2 0.9143
0.5 4 220.90 3.3 - 5.5 0.9245
0.4 4 224.36 4.2 - 5.1 0.9307
0.3 4 235.08 3.1 - 4.0 0.9345
0.2 8 222.05 7.0 - 10.0 0.9528
0.1 19 242.30 12.4 - 17.8 0.9741
distance between them, as shown in the lighter grey
zones in Figure 3. This set of data is about 1344 data
for each input and for each zone or output. Is difficult
to identify the grade of membership of the points be-
cause of the low distance between each zone (about
1 meter approximately). As shown in Table 4, even
with 150 clusters in FCM, the regression coefficient
is very low and the evaluation time cost is more than
2 seconds in that case.
Table 4: Comparison table Mamdani 3 inputs 4 outputs.
Clusters Gen. time (secs) Eval. time (secs) Regression coeff.
4 10.6563 0.0035 - 0.0041 0.3296
5 15.7962 0.069 - 0.145 0.3680
10 30.7855 0.15 - 0.23 0.3969
30 70.7959 0.39 - 0.56 0.4573
... ... ... ...
100 155.2 1.42 - 1.5 0.4264
150 165.8371 2.0 - 2.32 0.4776
Table 5 shows information of the generation and
evaluation of the set of data using subtractive clus-
tering method and TSK FLS. To achieve the desired
regression coefficient, a lower influence radius was
needed (0.1), however was not able to be successfully
executed in the test device. The regression coefficient
with a 0.1 radius was obtained with Matlab tools, and
the number of rules obtained was 153. Again the eval-
uation time is slower in Mamdani rather than TSK
FLS, but subtractive is slower than FCM.
Table 5: Comparison table Takagi-Sugeno 3 inputs 4 out-
puts.
Radius Clusters Gen. time (secs) Eval. time (milli secs) Regression coeff.
0.9 4 154.4764 0.0560 - 0.17 0.5237
0.7 4 155.6307 0.0390 - 0.022 0.5219
0.5 4 158.0025 0.0088 - 0.0037 0.5173
0.4 6 154.6215 0.0052 - 0.007 0.5343
0.3 12 161.7910 0.01100 - 0.016 0.5874
0.2 31 198.2 0.021 - 0.048 0.7475
0.1 - - - 0.9875
5.5 Information of Devices
The device to sense the RSSIs from each AP and
where the tests were executed is a Samsung Galaxy
Tab 4 7.0, 1.4Hz Quad Core Processor, 4KmAh
Battery. The three routers or APs used were a
Belkin Wireless G Router 2.4 GHz-802.11g model
no. F5D7230-40, an AirPort Extreme by Apple model
no. A1034 and a D-Link Wireless Router 2.4 GHz-
802.11g model DI-524.
6 CONCLUSIONS
This paper introduced a location on indoor areas
method using Wi-Fi signal networks, Type-2 fuzzy
inference system approach with a clustering method,
and how this can help to make applications that help
users in real time depending on the context. On
this approach, data was collected by one mobile de-
vice that sensed Wi-Fi signals from real indoor ar-
eas. Then, we built a Java Type-2 fuzzy inference
system using C-Means and Subtractive clustering al-
gorithm. The obtained fuzzy system can be Mam-
dani or TSK type which is later used to evaluate fu-
ture signals on mobile devices in order to decide the
current localization area. FCM is quicker than sub-
tractive but it is recommended only when having an
idea of the patterns in the collected data, otherwise is
complicated to estimate an acceptable number of clus-
ters to have an acceptable FLS structure. Other types
of pre-processing techniques can be implemented to
solve this problem. Subtractive is slower to identify
the centers but gives better results once possible opti-
mal centers are found. An expert is not necessary to
estimate the number of clusters; in less iterations it is
possible to find optimal centers. For evaluation, TSK
is better than Mamdani because it is desired to esti-
mate the location of the device in real time, and eval-
uation in Mamdani implies more processing becom-
ing slower. As future work, we are planning to use
a neuro-fuzzy system in order to improve precision
on how to produce the fuzzy inference system from
data. Also a found limitation of this proposed method
is the distance between the zones to locate. It is not
implementable in mobile devices when the distance
between zones is approximately about less than 1.5
meters. There are details to test using Wi-Fi devices
about variety of the signals depending on the number
of persons in the places, or position of objects, and
temperature, also the impact of adding one more in-
put (AP) to the system. This information is unknown
in this work; actually there are considerations to im-
prove about lost signals of APs during location, so a
strategy to solve this problem is still in construction.
Finally for an evaluation of the method, a regression
between target and outputs values gives a better idea
of the behavior of the FLSs depending on the param-
eter of the clustering methods, but a final and correct
ICEIS2015-17thInternationalConferenceonEnterpriseInformationSystems
614

evaluation of the system with a confusion matrix will
achieve this goal. Also to generate the FISs and eval-
uate them in this work the same values were used, so
it is needed to implement a thorough method that uses
a percentage of random data used in the generation of
the FISs and a percentage of real tested data. These
two samples of data will be a better set of data to test
during evaluation with a confusion matrix.
ACKNOWLEDGEMENTS
This work was supported in part by the Internal Fund
for Research Projects (Grant No. 300.6.C.135.17) of
the Autonomous University of Baja California, Mx-
ico.
REFERENCES
Bezdek, J. C., Ehrlich, R., and Full, W. (1984). Fcm: The
fuzzy c-means clustering algorithm. Computers and
Geosciences, 10(2-3):191–203.
Bozkir, S. and Sezer, E. (2013). Fuat - a fuzzy clustering
analysis tool. In Expert Systems with Applications,
FUZZYSS11: 2nd International Fuzzy Systems Sym-
posium, vol. 40.
Cai, A., Quek, C., and L., M. D. (2007). Type-2 ga-tsk
fuzzy neural network. In Evolutionary Computation.
CEC 2007 IEEE Congress.
Chai, W., Zhou, J., Chen, C., Nies, H., and Loeld, O.
(2011). Continuous indoor localization and naviga-
tion based on low-cost ins/wi-fi integration. In Inter-
national Conference of Positioning and Indoor Navi-
gation.
Chiu, S. (1994). Fuzzy model identication based on cluster
estimation. In Journal of Intelligent and Fuzzy Sys-
tems, vol. 2.
Crows, T. (1999). Introduction to Data Mining and Knowl-
edge Discovery. Two Crows Corporation.
Dey, A. (2001). Understanding and using context. Personal
and Ubiquitous Computing, 5(1).
Han, J. and Kamber, M. (1998). DataMining: Concepts and
Techiques. Morgan Kaufmann, 2nd edition.
Hwang, S. and Donghui, Y. (2012). Gps localization im-
provement of smart- phones using built-in sensors.
nternational Journal of Smart Home, 6.
Jang, J., Sun, C., and Mizutani, E. (1997). Neuro-Fuzzy
and Soft Computing: A Computational Approach to
Learning and Machine Intelligence. MATLAB Cur-
riculum Series. Prentice Hall.
Navarro, E., Peuker, B., and Quan, M. (2011). Wi-Fi Local-
ization Using RSSI Fingerprinting. PhD thesis, Com-
puter Engineering Department.
Ren, Q., Baron, L., and Balanzisnki, M. (2006). Type-2
takagi-sugeno-kang fuzzy logic modeling using sub-
tractive clustering. In Fuzzy Information Processing
Society. NAFIPS 2006. Annual meeting of the North
American.
Sanchez, L., noz, L. M., Galache, J., Sotres, P., Santana, J.,
and Gutierrez, V. (2014). Smartsantander: Iot exper-
imentation over a smart city testbed. Computer Net-
works.
Vaidehi, V., Monica, S., Saafer, S. S., Deepika, M., and
Saangeetha, S. (2008). A prediction system based on
fuzzy logic. In Proceedings of the World Comgress on
Engeineering and Computer Science, WCECS 2008.
Yin, X. F., Khoo, L. P., and Chong, Y. T. (2013). A fuzzy c-
means based hybrid evolutionary approach to the clus-
tering of supply chain. Computers and Industrial En-
gineering, 66(4):768–780.
Ying, H., Ding, Y., Li, S., and Shao, S. (1998). Typi-
cal takagi-sugeno and mamdani fuzzy systems as uni-
versal approximators: Necessary conditions and com-
parison. In Fuzzy Systems Proceedings, 1998. IEEE
World Congress on Computational Intelligence. The
1998 IEEE International Conference Vol 1.
Zadeh, L. (1965). Fuzzy sets. Information and Control,
8(3):338–353.
Hybrid-IntelligentMobileIndoorLocationUsingWi-FiSignals-LocationMethodUsingDataMiningAlgorithmsand
Type-2FuzzyLogicSystems
615
