
Controlled Proxy Re-signing - Conditional Proxy Re-Signatures
S. Sree Vivek and Guhan Balasubramanian
Samsung Research Institute, Bangalore, India
Keywords:
Delegation, Proxy Re-Signature, Conditional Proxy Re-Signature, Provable Security, Random Oracle Model.
Abstract:
Delegation of authentication is one of the vital security management strategies to manage device authentication
in an enormous network. Major issue while delegating authentication using traditional proxy cryptography is
that the delegator loses control over the messages which are authenticated by the delegatee and in proxy re-
cryptography controlling the proxy from resigning unintended signatures of the delegatee is not possible. To
address this concern, we propose a useful delegation scheme called as conditional proxy re-signature. In
this paper, we propose a security model for unidirectional conditional proxy re-signature, present a concrete
scheme and prove the security of the scheme in the random oracle model.
1 INTRODUCTION
Proxy Re-Cryptography was introduced by Blaze et.
al. (Blaze et al., 1998) and has been an emerging
field of interest in the research community. This
was mainly motivated by its widespread applications
and also the challenges faced in the construction of
practical schemes. Proxy Re-Signature and Proxy
Re-Encryption schemes are the essential primitives
for secure delegation. Proxy Re-Encryption allows a
semi-trusted proxy to convert a ciphertext on a mes-
sage such that it can be decrypted by another receiver
instead of the intended receiver defined during the
original encryption process. Many such schemes have
been designed and are being used for various applica-
tions like distributed storage, digital rights manage-
ment and sharing in cloud storage.
Proxy Re-Signatures: Proxy Re-Signature scheme
involves a semi-trusted proxy between two parties A
and B, where the proxy has the capability and infor-
mation (Re-Signature Key) to convert the signature on
a message, say m, signed by one user A, to the signa-
ture of the other user B on the same message m (A is
the delegatee, B is the delegator). This kind of signa-
ture comes handy in situations wherein B the delega-
tor is not available to sign on a given message m. Then
using a signature of the delegatee A on the message
m, the semi-trusted proxy can generate a signature
on behalf of B on the same message m with the help
of a rekey (interchangeably used as re-signature key
or re-sign key), without involving delegator B in the
signing process. More details on proxy re-signature
schemes can be seen in (Chow and Phan, 2008; Lib-
ert and Vergnaud, 2008; Shao et al., 2010).
Conventionally, the delegator must have a strong
control over the delegation and signing process since
the signature is eventually going to be verified with
his/her public key. In proxy re-signatures, the semi-
trusted proxy has unconditional power to translate any
signature of the delegatee to that of the delegator. This
is undesirable as there is no control over the kind
of messages the proxy can translate. We try to re-
solve this issue by introducing conditions to proxy
re-signatures which hinder the proxy from convert-
ing signatures without the consent of the delegatee.
A condition parameter will be an inherent part of all
the algorithms in the proxy re-signature scheme.
There must be a certain hold over the degree of
freedom given to the proxy to translate signatures.
Thus in conditional proxy re-signatures, the proxy can
only translate signatures based on a certain condition.
The proxy will be given the re-signature key with re-
spect to certain conditions during the rekey genera-
tion process. Therefore, the proxy will only be able
to translate those signatures for which the condition
matches with that present in the re-signature key. In
this case, the proxy is constrained to abide by the con-
ditions on messages that were signed by the delegatee
before translating the signatures to that of the delega-
tor. This feature brings in a win-win situation for both
the delegatee and the delegator due to the following
reasons:
• The delegator can assure that the proxy does not
translate signatures of unwanted messages to that
186
Sree Vivek S. and Balasubramanian G..
Controlled Proxy Re-signing - Conditional Proxy Re-Signatures.
DOI: 10.5220/0005510601860193
In Proceedings of the 12th International Conference on Security and Cryptography (SECRYPT-2015), pages 186-193
ISBN: 978-989-758-117-5
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

of the delegator’s signature.
• The delegatee can control what kind of signatures
generated by him can be translated by the proxy,
thereby avoiding a conflict of issues with the del-
egator.
The delegatee cannot freely sign on messages of
his/her own since it could be translated by the proxy.
The proxy can translate any signatures of the delega-
tee to that of the delegator at will, without the con-
sent of the delegatee. In this case the delegator will
not have any means to deny signatures which were
not signed by him since the translated signatures by
the proxy will verify with the delegators public key.
There will be no means to prove the fact that the sig-
nature was translated with the consent of a delegatee.
This issue can pose a real threat in applications like
temporary certificate generation for public key infras-
tructure and signature delegations in organizations.
These issues can be very effectively tackled by us-
ing conditions along with proxy re-signatures. Some
applications of proxy re-signatures with this new fea-
ture are e-passports, issuing certificates in PKI, in hi-
erarchical organizations, cloud infrastructure, to list a
few.
Related Work: Proxy signatures were introduced by
Mambo et. al. (Mambo et al., 1996). Proxy signature
uses warrant which defines the condition or the type
of messages on which the delegatee can sign on be-
half of the delegator. Ivan et al. (Ivan and Dodis,
2003) gave a new look to delegate signing rights.
This scheme was not proxy based in a true sense, be-
cause the secret key was split between the delegator
and delegatee. The most recent proxy signature (with
anonymity of delegatee) was given by Pointcheval et.
al. in (Fuchsbauer and Pointcheval, 2008).
Proxy re-signatures as mentioned before, was first
introduced by Blaze et. al. (Blaze et al., 1998).
Later the notion was formalized by Ateniese and Ho-
henberger (Ateniese and Hohenberger, 2005), who
gave the security model and proposed the first proxy
re-signature scheme (both unidirectional and bidirec-
tional) which are the most efficient schemes till date.
Shao et. al. (Shao et al., 2007) proposed identity
based systems in the standard model. The primitive
was further formalized by Chow et. al. (Chow and
Phan, 2008) and a concrete scheme secure in the stan-
dard model was proposed. Libert et. al. (Libert and
Vergnaud, 2008) addressed the problem of multi-use,
where the signatures can be translated more than once
if the rekey is available. They were also responsible
for introducing the chosen key model where the chal-
lenger has no knowledge about the corrupted private
keys. An update on the implementation front was also
showed in (Wang and Yang, 2009), which explained
how the proxies can be setup in order to avoid a dis-
tributed denial of service attack.
In the literature, conditional delegation started
with (Watanabe and Numao, 2002), an application for
P2P data sharing. The concept of inducing conditions
in proxy re-cryptography was formalized in the con-
text of CCA-secure conditional proxy re-encryption
in papers by Weng et. al. (Weng et al., 2009a) (proven
insecure by (Zhang and Chen, 2009)) (Weng et al.,
2009b) and (Chu et al., 2009). The most efficient
one being proposed by Selvi et. al. (S. Sree Vivek
and Rangan, 2011). Fang et. al. proposed an anony-
mous proxy re-encryption scheme secure in the stan-
dard model in (Fang et al., 2009) and an interactive
version of it in (Fang et al., 2011). The first identity
based conditional proxy re-encryption was introduced
by Shao et. al. (Shao et al., 2011). Recently Fang et.
al. proposed the hierarchical version of conditional
proxy re-encryption scheme (Fang et al., 2012).
Our Contribution: In this paper, we introduce con-
ditions in the context of proxy re-signatures which
has natural applications. Then we propose a security
model for chosen message and condition attack to sat-
isfy the property in unidirectional proxy re-signatures
with a private proxy. The security model for the uni-
directional proxy re-signature scheme is based on the
unidirectional security notion against static corrup-
tion, proposed by Shao et. al. in (Shao et al., 2010).
We give a concrete scheme using bilinear maps and
prove its security with the help of random oracles in
the proposed security model. The hardness of break-
ing the scheme is related to the hardness of the com-
putational Diffie-Hellman problem.
2 APPLICATION IN AD-HOC
VEHICULAR NETWORKS
Vehicular ad-hoc networks are being theorized as the
foundation of connected cars and bring in a whole
new dimension to the internet of things. With an
increase in road traffic and freight movement, and
the digitization of the transportation industry with e-
license, electronic vehicle registration plates, smart
toll booths, traffic management based on GPS, etc.
there is an immense and desperate requirement for
secure systems. With a spread of technology across
transportation industry, authentication becomes a ma-
jor concern. The vehicular public key infrastructure
(VPKI) deployed in this environment consists of a
country root certificate authority (CA), a regional CA
and road side units (RSU). The ad-hoc environment
of vehicles which consists of an on-board unit (OBU)
and a trusted platform module (TPM). The OBU is
ControlledProxyRe-signing-ConditionalProxyRe-Signatures
187
in charge of communicating with the infrastructure
where as the TPM is responsible for all the secure
storage and computation. This will hold the iden-
tity information of the vehicle which will be certi-
fied by the CA. Hence to identify the cars authorized
in a region, any vehicle inside a region should hold
a valid certificate signed by the regional CA. They
are termed as pseudonym certificates as defined by
Fuentes et. al. (Jos Mara de Fuentes, 2011) and Raya
et al. (Maxim Raya, 2005).
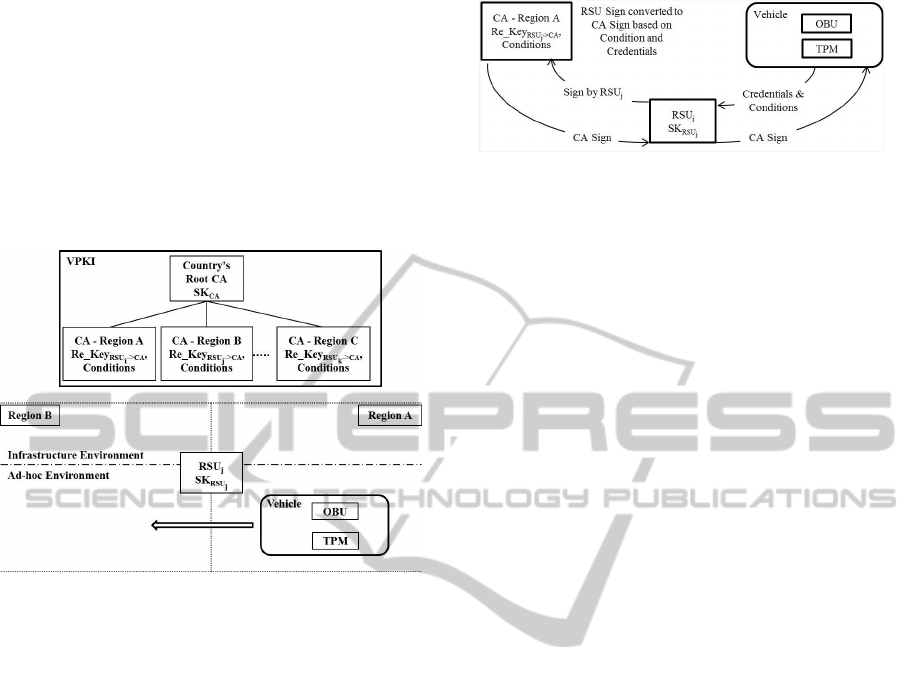
Figure 1: Vehicular Public Key Infrastructure.
Figure 1 shows the block diagram of VPKI. The
country’s root CA has a secret key SK
CA
. Since there
may be many regions in a country, each region will
have a regional CA. This is purely for distribution of
job and convenience. Each regional CA will have few
RSUs associated with them. RSUs have their own
secret keys. For example RSU
j
, comes under region
B has a secret key SK
RSU
j
. The regional CA will
have a conditional re-sign key, which converts root
RSU’s signature into root CA’s signature if the condi-
tion holds good. When a vehicle enters region B from
Region A, it is required to pass through RSU
j
. RSU
j
checks the vehicle and signs on the vehicle’s creden-
tials and the condition to cross the border, to grant en-
try. Since there are multiple RSUs for a single region,
the signature of RSU
j
should be converted to that of
the root CA’s signature. Hence the authenticity to the
entry of all vehicles in a given area can be verified
using the root CA’s public key. The proxy holds the
conditions for which the signature can be converted.
The delegator (root CA) can impose what kind of ve-
hicles can pass through the specific RSU. Hence the
proxy can convert signatures only if it satisfy certain
conditions. These re-signature keys with embedded
conditions can be defined on the fly as and when new
policies may be introduced.
Figure 2 shows how the vehicle provides the cre-
Figure 2: Authentication Granted Using CPRS.
dentials and conditions to the RSU, and the RSU signs
it and sends to the regional CA, who converts it into
the sign of root CA and sends it back to the RSU to
verify and proceed further. This can be of practical
use when we do not want to allow entry for vehicles
which are not insured or those for which the taxes are
not paid in a specific region. Tourist vehicles can be
authenticated based on conditions in a foreign region
using this mechanism. Yet another scenario could be
using the scheme to permit VIP cars into another re-
gion without any hassle. This application hence can
be used as a viable substitute for access control lists
and hence having limited effect on storage in the in-
frastructure and distribute the load on the root CA.
3 DEFINITIONS
In this section, we provide the definitions which are
used for constructing and proving our scheme.
3.1 Conditional Proxy Re-Signature
Scheme
The PKI-based scheme is defined by a set of six al-
gorithms described below: (Setup, KeyGen, ReKey,
Sign, ReSign, Verify).
• Setup(k) - This algorithm takes as input the secu-
rity parameter k and generate the system parame-
ters params, which is required for the user to gen-
erate his/her keys.
• KeyGen(k, params) - This algorithm takes the se-
curity parameter k and the system parameters
params as input and generates the public, secret
key pair for a user who invokes the algorithm.
This algorithm is executed by each user and the
generated public keys are certified by a Certifica-
tion Authorities (CA).
• ReKey(sk
Delegator
,sk
Delegatee
, C) - This algorithm is
an interactive protocol which is carried out in a
secure channel between the delegator, delegatee
and the proxy. Assuming the system to have a
private proxy (re-signature key is kept secret with
SECRYPT2015-InternationalConferenceonSecurityandCryptography
188

the proxy), this algorithm takes as input the secret
keys of the users between whom the re-signature
key must be generated, and the condition for sig-
nature translation. The output of this algorithm
is a re-signature key rk
Delegatee→Delegator
which is
kept secret with the proxy. The re-signature key
is structured in such a way that the proxy cannot
gain any advantage regarding the secret keys of
the delegator and delegatee.
• Sign(m, C, sk) - This algorithm takes as input the
message m, condition C and the secret key sk of
the user who is signing the message. It outputs
the signature of the user on m for the condition C.
• ReSign(m, C, σ, pk
Delegator
, pk
Delegatee
) - This al-
gorithm takes as input, the message m, the con-
dition C and the public keys of the delegator and
the delegatee. It first verifies whether the message
and the condition verifies the signature with re-
spect to the public key of the delegator. If false,
then it returns invalid signature. Otherwise, it uses
the re-signature key generated by the ReKey al-
gorithm and then translates the signature σ into a
re-signature
ˆ
σ which can be verified by the public
key of the delegatee.
• Verify(m,C,σ,pk) - This algorithm takes as in-
put, the message, the condition, the signature/re-
signature on the message and the public key of the
user which the signature/re-signature is to be veri-
fied with. It returns true if the signature is success-
fully verified with respect to the message, condi-
tion and public key and returns false otherwise.
3.2 Security Model for Conditional
Proxy Re-Signatures
In general, the security of a signature scheme is es-
tablished using the notion of existential unforgeabil-
ity against adaptive chosen message attack, where the
adversary will be able to come up with forgeries on
messages for which he had not queried the signature.
We use the same security notion (but with a stronger
unforgeability notion where existing message signa-
ture pairs cannot be forged) and come up with a new
security model to incorporate conditions (chosen con-
dition attack). There are two existing standard secu-
rity models for proxy re-signatures - static corruption
and dynamic corruption based on which we define the
security models for conditional proxy re-signatures.
The security model is defined as a game between an
adversary and a challenger, where the challenger is
required to prove the security of the scheme. The
challenger simulates the system, to give the adversary
a ”view” of the system. The adversary is allowed to
query the various oracles of the system (which require
the computation with secret information) provided by
the challenger and train itself to obtain enough infor-
mation and perform a valid forgery for a chosen con-
dition and message.
The stronger security model would be Dynamic
Corruption which is based on the fact that the role
of the adversary is dynamic and any user of the sys-
tem can turn adversarial at any point during the game.
The aim of this model is to explicitly protect the
scheme against External (outside the system) and In-
ternal (within the system) adversaries.
We adopt a more applicable model - static corrup-
tion model - for proving the security of our scheme,
which was originally introduced in the security mod-
els for proxy re-encryption schemes (Ateniese et al.,
2006) where the corrupted and uncorrupted users are
decided before the beginning of the security game. In
this model, the challenger who is proving the secu-
rity of the scheme, initially trains the adversary who
queries a set of oracles which define the behaviour of
the system (oracles for conditional proxy re-signature
schemes defined below). It is also to be noted that the
security model for unidirectional proxy re-signature
schemes with private proxy given in (Shao et al.,
2010) is an improved version over that of (Ateniese
and Hohenberger, 2005).
According to (Shao et al., 2010) the re-signature
key generation queries, a delegation chain is con-
structed. For example, if the re-sign key for A to B
and B to C is generated, then all the signatures of A
can be indirectly converted to that of C by the proxy.
The use of conditions may restrict this type of insecu-
rities in the delegation chain.
In the static corruption model, since the challenger
can differentiate between the corrupted and uncor-
rupted users beforehand, it simulates the appropriate
oracles for the corresponding users. The oracles of
the CPRS system are discussed in detail below.
1. Corrupted Key Generation Oracle: For a cor-
rupted user, the challenger generates and outputs
the private key and the corresponding public key.
2. Uncorrupted Key Generation Oracle: For an un-
corrupted user, the challenger generates the pri-
vate key and outputs only the public key.
3. ReKey Oracle: For the input of the public keys of
the delegator and the delegatee, the condition, the
challenger outputs the corresponding re-signature
key between the users for the corresponding con-
dition.
4. Uncorrupted Signature Oracle: Given the input
of the uncorrupted user’s public key, the message
and the corresponding condition to sign on, the
ControlledProxyRe-signing-ConditionalProxyRe-Signatures
189

challenger outputs the corresponding signature.
5. Re-Signature Oracle: Given the signature on the
message, the condition and the public key of the
user to whom the signature is to be translated as
input, the challenger outputs the corresponding
re-signature on the same message and condition
for the given user.
Note: The adversary controls the actions of the cor-
rupted users. At the end of the training phase, the
adversary will not have any advantage with respect
to the information of the uncorrupted users. The ad-
versary can query the above mentioned oracles con-
sidering its limited computation power. Undesirable
delegation chains between corrupted and uncorrupted
parties can be avoided by the use of conditions.
In the forgery phase, we could conclude that the
scheme is secure if the adversary with the access to all
these oracles, is able to come up with a valid forgery
on the signature or the re-signature with respect to a
condition and a message for an uncorrupted user with
respect to some conditions as discussed below:
Let ( ¯m,
¯
C) represent the message, condition that were
already queried to the sign/re-sign oracle with respect
to an uncorrupted user
¯
pk. Let (m
∗
, C
∗
) represent the
message, condition pair for which the forgery is gen-
erated for an uncorrupted user pk
∗
. Forgery σ
∗
is
valid if it satisfies the following constraints:
• Verify (pk
∗
, m
∗
, C
∗
) = True.
• if σ∗ 6= σ, where σ is an output of O
Sign
(m
∗
, C
∗
) or
O
ReSign
(m
∗
, C
∗
,
¯
pk, pk
∗
). Or there is a delegation
chain with C
∗
from
¯
pk to pk
∗
.
• if
(m
∗
, C
∗
) 6= ( ¯m,
¯
C)
or
m
∗
6= ¯m
or
C
∗
6=
¯
C
.
• The adversary has not made a ReKey query chain
to delegate the signing rights from a corrupted to
pk
∗
on the condition C
∗
.
We define the advantage of the forger as the proba-
bility that he/she wins in the above game. The result-
ing conditional proxy re-signature scheme is strongly
unforgeable against chosen message and condition at-
tack if the above mentioned forgery can be performed
only with a negligible probability. Motivation for this
kind of a security model based on (Shao et al., 2010)
is that the forger should not be able to derive any un-
due advantage as a consequence of the introduction
of the condition. As one may notice, the introduction
of condition reduces the number of constraints on the
forgery as when compared to a traditional proxy re-
signature.
Bilinear Pairing: Let G be an additive cyclic group
generated by P, with prime order p, and G
1
be a mul-
tiplicative cyclic group of the same order p. A bilinear
pairing is a map ˆe : G × G → G
1
with the following
properties.
• Bilinearity: For all P, Q, R ∈ G,
– ˆe(P + Q, R) = ˆe(P, R)ˆe(Q, R)
– ˆe(P, Q + R) = ˆe(P, Q) ˆe(P, R)
– ˆe(aP, bQ) = ˆe(P, Q)
ab
• Non-Degeneracy: There exist P, Q ∈ G such that
ˆe(P, Q) 6= I
G
1
, where I
G
1
is the identity in G
1
.
• Computability: There exists an efficient algorithm
to compute ˆe(P, Q) for all P, Q ∈ G.
Computational Diffie-Hellman Problem: Let G be
a group of prime order p and g be the generator of
G. The CDH problem can be defined as follows: An
algorithm A is said to have an advantage ε in solving
the CDH problem if
Pr[A(P, aP, bP) = abP] ≥ ε
where the probability is calculated over the random
choices of a, b ∈ Z
∗
p
, g ∈ G
∗
and the random bits used
by algorithm A.
4 SCHEME
In this section we define a concrete PKI-based con-
ditional proxy re-signature scheme which is based on
pairing. The security is asymptotically based on a se-
curity parameter k.
Setup(k) and KeyGen(k)
• Let G and G
1
be cyclic groups of prime order p
defined to satisfy the billinear map ˆe : G ×G → G
1
• P is chosen as the generator of G.
• Choose four cryptographic hash functions defined
as follows:
H
1
: {0, 1}
∗
→ G
H
2
: {0, 1}
∗
× G × G → G
H
3
: {0, 1}
∗
× {0, 1}
∗
× G → G
H
4
: {0, 1}
∗
× {0, 1}
∗
× G × G → G
• Each user generates his/ her private and public key
pair using the public parameters defined above.
After generating the key pair, he/ she gets the pub-
lic key certified from the certification authority.
The keys are generated as follows:
– Choose x ∈
R
Z
p
and set sk = x as the user’s pri-
vate key.
– Compute the public key pk = xP ∈ G.
– With respect to our scheme, we assume that the
delegatee’s (X) secret key is x and the delega-
tor’s (Y ) secret key is y.
SECRYPT2015-InternationalConferenceonSecurityandCryptography
190

Note: In certain cases, where the condition can be
directly obtained from the message to be signed, we
may assume a heuristic black box K(m) = C that
when given the input message m, returns the condi-
tion(s) C, that corresponds to the message. This may
not be applicable for applications where the condition
depends on the situation (example: urgency). The in-
troduction of this black box will not provide the forger
any undue advantage for giving a forgery.
ReKey(x, y, C)
The re-signature key rk
x→y
(C) is generated for the
condition C using an interactive protocol which indi-
rectly accepts the secret keys of the delegatee X and
the delegator Y without revealing it to the proxy.
• The proxy selects elements R ∈
R
G and r
2
∈
R
Z
q
,
and sends R and r
2
P to the delegator Y .
• Y then computes yH
1
(C) + yH
2
(C, r
2
P) ∈ G
where y is the secret key and C is the condition for
which the delegator chooses to delegate its sign-
ing rights.
• Y sends yH
1
(C) + yH
2
(C, r
2
P) + R ∈ G and the
condition C to the delegatee X.
• X computes xH
1
(C) and sends yH
1
(C) +
yH
2
(C, r
2
P) + R − xH
1
(C) ∈ G to the proxy.
• The proxy removes R and assigns the re-signature
keys from X to Y for the condition C as
rk
1
= (y − x)H
1
(C) + yH
2
(C, r
2
P) ∈ G
rk
2
= r
2
P ∈ G.
The rekey rk
x→y
(C) = hrk
1
, rk
2
i. Note that role of R
in the rekey generation process is to prevent X and
Y from misusing the intermediate information and r
2
is known to the proxy and is used in the resign algo-
rithm.
Remark: We use an interactive rekey algorithm in or-
der to facilitate the proxy to re-use the randomness in
the resign algorithm. This reduces the space and com-
putation time required to carry out the re-signature
process and moreover offers more secure construc-
tion. Since it is a one-time computation, it does not
affect the performance of the scheme.
Sign(m, C, x)
Given the message m, condition C and the secret
key x of the signer as input, the algorithm performs
the following steps:
• Choose a random r
1
∈ Z
p
and compute r
1
P ∈ G
• Compute σ
1
= xH
1
(C) + r
1
H
3
(m, C, r
1
P)
• Compute σ
2
= r
1
P
Hence, the output signature σ for message m and con-
dition C for the user X is hσ
1
, σ
2
i.
Remark: Notice that the signature algorithm is based
on the short signature scheme proposed by Boneh et.
al. (BLS signature scheme (Boneh et al., 2001)).
ReSign(σ, xP, m, C, rk
x→y
(C))
Given the message m, condition C, public key xP
for the corresponding signature σ and the re-signature
key rk
x→y
(C) as input, the re-signature algorithm per-
forms the following steps:
• The algorithm Veri f y(σ, xP, m, C) is invoked in
order to check the validity of the signature to be
translated with respect to the delegatee’s public
key xP. If this test does not hold, the translation
will be meaningless. Hence, the resign algorithm
can continue only if the test holds.
• Compute and store re-randomization component
as r
2
H
4
(m, C, r
2
P, r
1
P) ∈ G where r
2
is from the
ReKey algorithm. The hash function includes the
randomness introduced in the sign and rekey al-
gorithm to maintain the integrity of the resultant
resignature.
• The translated signature is computed as
ˆ
σ
1
= {σ
1
} + {rk
1
} + }Re-Randomization
component}.
= {xH
1
(C) + r
1
H
3
(m, C, r
1
P)} + {yH
1
(C)−
xH
1
(C) + yH
2
(C, r
2
P)}+
{r
2
H
4
(m, C, r
2
P, r
1
P)}
= yH
1
(C) + r
1
H
3
(m, C, r
1
P) + yH
2
(C, r
2
P)+
r
2
H
4
(m, C, r
2
P, r
1
P).
• Assign
ˆ
σ
2
= σ
2
= r
1
P.
• Assign
ˆ
σ
3
= rk
2
= r
2
P.
Hence, the output re-signature
ˆ
σ for message m and
condition C for the user Y is h
ˆ
σ
1
,
ˆ
σ
2
,
ˆ
σ
3
i.
Verify(σ,xP,m,C)
This algorithm takes the signature σ / re-signature
ˆ
σ of the user X on the message m for the condition C
as input and returns true if the signature is valid.
The algorithm performs the following to check the va-
lidity of a signature:
ˆe(σ
1
, P)
?
= ˆe(H
1
(C), xP). ˆe(H
3
(m, C, r
1
P), σ
2
)
where signature is of the form:
hσ
1
, σ
2
i = hxH
1
(C) + r
1
H
3
(m, C, r
1
P), r
1
Pi
The algorithm performs the following to check the va-
lidity of a re-signature:
e(
ˆ
σ
1
, P)
?
=e(H
1
(C), xP).e (H
3
(m, C, r
1
P),
ˆ
σ
2
).
e(H
2
(C, r
2
P), xP).e (H
4
(m, C, r
2
P, r
1
P),
ˆ
σ
3
)
where the re-signature is of the form:
h
ˆ
σ
1
,
ˆ
σ
2
,
ˆ
σ
3
i = hxH
1
(C) + r
1
H
3
(m, C, r
1
P) +
xH
2
(C, r
2
P) + r
2
H
4
(m, C, r
2
P, r
1
P), r
1
P, r
2
Pi
If the above test fails, then the signature is invalid.
ControlledProxyRe-signing-ConditionalProxyRe-Signatures
191

Correctness of Signature Verification:
ˆe(σ
1
, P) = ˆe(xH
1
(C) + r
1
H
3
(m, C, r
1
P), P)
= ˆe(xH
1
(C), P). ˆe(r
1
H
3
(m, C, r
1
P), P)
= ˆe(H
1
(C), xP). ˆe(H
3
(m, C, r
1
P), r
1
P)
= ˆe(H
1
(C), xP). ˆe(H
3
(m, C, r
1
P), σ
2
)
Correctness of Re-Signature Verification:
ˆe(
ˆ
σ
1
, P)= ˆe(xH
1
(C) + r
1
H
3
(m, C, r
1
P) + xH
2
(C, r
2
P)
+r
2
H
4
(m, C, r
2
P, r
1
P), P)
= ˆe(xH
1
(C), P). ˆe(r
1
H
3
(m, C, r
1
P), P).
ˆe(xH
2
(C, r
2
P), P). ˆe(r
2
H
4
(m, C, r
2
P, r
1
P), P)
= ˆe(H
1
(C), xP). ˆe(H
3
(m, C, r
1
P), r
1
P).
ˆe(H
2
(C, r
2
P), xP). ˆe(H
4
(m, C, r
2
P, r
1
P), r
2
P)
= ˆe(H
1
(C), xP). ˆe(H
3
(m, C, r
1
P),
ˆ
σ
2
).
ˆe(H
2
(C, r
2
P), xP). ˆe(H
4
(m, C, r
2
P, r
1
P),
ˆ
σ
3
)
Efficiency Analysis: The signature has two group ele-
ments and the re-signature only increases the size by
an extra group element, due to the extra randomiza-
tion component introduced by the resign algorithm.
While commenting on the computational complex-
ity, the sign algorithm requires three scalar multipli-
cations and one group addition in G. The resign al-
gorithm requires one scalar multiplication and three
group additions in G. The verify algorithm for a sig-
nature requires three pairing operations and one group
multiplication in G
1
while the verify algorithm for a
re-signature requires five pairing operations and three
group multiplications in G
1
.
Proof of Security
Theorem 1: We show that if there is an adversar-
ial algorithm that is capable of forging the CPRS
scheme, then it is possible to construct another al-
gorithm which breaks the CDH problem with a non-
negligible advantage.
Proof Sketch: The challenger gets an instance of the
CDH problem say hP, aP, bPi as input. The goal of the
challenger is to find abP with a non-negligible prob-
ability. The challenger sets up the system and in the
training phase, the forger is allowed to query (poly-
nomial in number) Corrupted KeyGen Oracle, Uncor-
rupted KeyGen Oracle , all the hash oracles, Uncor-
rupted User’s Sign oracle, Rekeygen oracle and Re-
Sign oracle in order to be trained by the challenger to
perform the forgery. We explain the oracles which are
required to show the proof sketch here.
Uncorrupted KeyGen Oracle: The challenger takes a
random x
i
∈ G and outputs (a +x
i
)P as the public key
(where aP is an input of the hard problem instance).
The challenger does not know the private key a.
H
1
Oracle: For condition C
∗
, which is fixed by the
challenger, the challenger embeds the hard problem.
• Choose t
1i
∈
R
Z
p
and compute t
1i
bP ∈ G.
H
2
Oracle: Given the condition C and the random
group element r
2i
P ∈ G, the challenger chooses ran-
dom t
2i
∈
R
Z
p
and returns t
2i
P ∈ G. The challenger
stores the tuple hC, r
2i
P, t
2i
i in the list L
2
for future
use.
H
3
Oracle: Given a message m, a condition C and
a random group element in r
3i
P ∈ G the challenger
chooses t
3i
∈
R
Z
p
and returns t
3i
P ∈ G. The chal-
lenger stores the tuple hm, C, r
3i
P, t
3i
i in the list L
3
for
future use.
H
4
Oracle: Given a message m, condition C, and two
random group elements r
41i
P, r
42i
P, the challenger
chooses t
4i
∈
R
Z
p
and returns t
4i
P ∈ G. The chal-
lenger stores the tuple hm, C, r
41i
P, r
42i
P, t
4i
i in the list
L
3
for future use.
Explanation about the Uncorrupted User Sign oracle,
Rekeygen oracle and ReSign oracle will be available
in the full version of the paper and is omitted here due
to page restriction. In the forgery phase, the forger
comes up with a valid signature or re-signature on the
message m
∗
and condition C
∗
. It is also assumed that
H
1
(C
∗
) was queried during the training phase. Other-
wise the game is aborted.
Forgery on Signature
is of the form hσ
∗
1
, σ
∗
2
i = h(a +
x
∗
)H
1
(C
∗
) + r
∗
1
H
3
(m
∗
, C
∗
, r
∗
1
P), r
∗
1
Pi.
Challenger checks in list L
3
for the input m
∗
, C
∗
, σ
∗
2
and if present, obtains the value of t
∗
3
. And hence σ
∗
1
= (a + x
∗
)t
1i
bP + r
∗
1
t
∗
3
P. The challenger now finds the
solution to the hard problem by computing
σ
∗
1
−x
∗
t
∗
1
bP −t
∗
3
σ
∗
2
=
= abt
∗
1
P + x
∗
t
∗
1
bP + r
1
t
∗
3
P − x
∗
t
∗
1
bP −t
∗
3
r
1
P
= abt
∗
1
P
Now abP is obtained by multiplying the inverse of t
∗
1
to the above output.
Forgery on Re-Signature
is of the form h
ˆ
σ
∗
1
, σ
∗
2
,
ˆ
σ
∗
3
i =
h(a + x
∗
)H
1
(C
∗
) + r
∗
1
H
3
(m
∗
, C
∗
, r
∗
1
P) + (a + x
∗
)
H
2
(C
∗
, r
∗
2
P) + r
∗
2
H
4
(m
∗
, C
∗
, r
∗
2
P, r
∗
1
P), r
∗
1
P, r
∗
2
Pi
The challenger checks the list L
3
to obtain value of t
∗
3
,
checks the list L
2
to obtain the value of t
∗
2
and checks
the list L
4
to obtain the value of t
∗
4
. The challenger
computes the following to obtain the solution to the
CDH problem:
ˆ
σ
∗
1
−x
∗
t
∗
1
bP −t
∗
3
σ
∗
2
− x
∗
t
∗
2
P −t
∗
2
aP −t
∗
5
σ
∗
3
= abt
∗
1
P + x
∗
t
∗
1
bP + r
1
t
∗
3
P +t
∗
2
aP + x
∗
t
∗
2
P+
r
∗
2
t
∗
5
P − x
∗
t
∗
1
bP −t
∗
3
r
1
P − x
∗
t
∗
2
P −t
∗
2
aP −t
∗
5
r
∗
2
P
= abt
∗
1
P
Now abP is obtained by multiplying the inverse of t
∗
1
to the above output.
SECRYPT2015-InternationalConferenceonSecurityandCryptography
192

5 CONCLUSIONS
In this paper, we have proposed a new primitive
called conditional proxy re-signature. We have de-
fined a suitable security model for conditional proxy
re-signatures. We have presented a concrete condi-
tional proxy re-signature scheme which is unidirec-
tional and single-use, and proved the security in the
random oracle model. The security of the proposed
scheme is related to the hardness of the CDH prob-
lem.
We let the design of a multi-use CPRS scheme,
where the signature can be translated more than one
time with a nominal increase in complexity and sig-
nature size for each translation as an interesting open
problem. Providing CPRS schemes in the identity
based setting and certificateless settings would also
be challenging and would have practical relevance in
cloud based systems. A standard model security proof
would further solidify the practical applicability of
such a scheme.
REFERENCES
Ateniese, G., Fu, K., Green, M., and Hohenberger, S.
(2006). Improved proxy re-encryption schemes with
applications to secure distributed storage. ACM Trans.
Inf. Syst. Secur., 9(1):1–30.
Ateniese, G. and Hohenberger, S. (2005). Proxy re-
signatures: new definitions, algorithms, and applica-
tions. In ACM Conference on Computer and Commu-
nications Security, pages 310–319.
Blaze, M., Bleumer, G., and Strauss, M. (1998). Divertible
protocols and atomic proxy cryptography. In EURO-
CRYPT, pages 127–144.
Boneh, D., Lynn, B., and Shacham, H. (2001). Short sig-
natures from the weil pairing. In ASIACRYPT, pages
514–532.
Chow, S. S. M. and Phan, R. C.-W. (2008). Proxy re-
signatures in the standard model. In ISC, pages 260–
276.
Chu, C.-K., Weng, J., Chow, S. S. M., Zhou, J., and
Deng, R. H. (2009). Conditional proxy broadcast re-
encryption. In ACISP, pages 327–342.
Fang, L., Susilo, W., Ge, C., and Wang, J. (2011). In-
teractive conditional proxy re-encryption with fine
grain policy. Journal of Systems and Software,
84(12):2293–2302.
Fang, L., Susilo, W., Ge, C., and Wang, J. (2012). Hier-
archical conditional proxy re-encryption. Computer
Standards and Interfaces, vol - 34(no - 4):380 – 389.
Fang, L., Susilo, W., and Wang, J. (2009). Anonymous con-
ditional proxy re-encryption without random oracle.
In ProvSec, pages 47–60.
Fuchsbauer, G. and Pointcheval, D. (2008). Anonymous
proxy signatures. In SCN, pages 201–217.
Ivan, A.-A. and Dodis, Y. (2003). Proxy cryptography re-
visited. In NDSS.
Jos Mara de Fuentes, Ana Isabel Gonzlez-Tablas, A. R.
(2011). Overview of security issues in vehicular ad-
hoc networks. In Handbook of Research on Mobility
and Computing, pages 894–911. Hershey: IGI Global.
Libert, B. and Vergnaud, D. (2008). Multi-use unidirec-
tional proxy re-signatures. In ACM CCS, pages 511–
520.
Mambo, M., Usuda, K., and Okamoto, E. (1996). Proxy sig-
natures for delegating signing operation. In Proceed-
ings of the 3rd ACM, CCS ’96, pages 48–57. ACM.
Maxim Raya, J. H. (2005). The security of vehicular ad hoc
networks. In Proceedings of the 3rd ACM Workshop
on Security of ad hoc and Sensor Networks, SASN -
2005, pages 11–21. ACM.
S. Sree Vivek, S. Sharmila Deva Selvi, V. R. and Ran-
gan, C. P. (2011). Conditional proxy re-encryption
– a more efficient construction. In CNSA, CCIS 196,
pages 502–512.
Shao, J., Cao, Z., Wang, L., and Liang, X. (2007). Proxy
re-signature schemes without random oracles. In IN-
DOCRYPT, pages 197–209.
Shao, J., Feng, M., Zhu, B., Cao, Z., and Liu, P. (2010). The
security model of unidirectional proxy re-signature
with private re-signature key. In ACISP, pages 216–
232.
Shao, J., Wei, G., Ling, Y., and Xie, M. (2011). Identity-
based conditional proxy re-encryption. In IEEE Con-
ference on Communications - ICC, pages 1–5.
Wang, X. a. and Yang, X. (2009). On ddos attack against
proxy in proxy re-encryption and proxy re-signature.
In Proceedings of the 2009 Ninth IEEE International
Conference on Computer and Information Technology
- Volume 02, CIT ’09, pages 213–218. IEEE Computer
Society.
Watanabe, Y. and Numao, M. (2002). Conditional cryp-
tographic delegation for p2p data sharing. In Pro-
ceedings of the 5th International Conference on Infor-
mation Security, ISC ’02, pages 309–321. Springer-
Verlag.
Weng, J., Deng, R. H., Ding, X., Chu, C.-K., and Lai,
J. (2009a). Conditional proxy re-encryption secure
against chosen-ciphertext attack. In ASIACCS, pages
322–332.
Weng, J., Yang, Y., Tang, Q., Deng, R. H., and Bao, F.
(2009b). Efficient conditional proxy re-encryption
with chosen-ciphertext security. In ISC, pages 151–
166.
Zhang, X. and Chen, M.-R. (2009). On the security of a
conditional proxy re-encryption. IEICE Transactions,
92-A(10):2644–2647.
ControlledProxyRe-signing-ConditionalProxyRe-Signatures
193
