
Gateway Threshold Password-based Authenticated Key Exchange Secure
against Undetectable On-line Dictionary Attack
Yukou Kobayashi
1
, Naoto Yanai
2
, Kazuki Yoneyama
3,∗
, Takashi Nishide
1
, Goichiro Hanaoka
4
,
Kwangjo Kim
5
and Eiji Okamoto
1
1
University of Tsukuba, Tsukuba, Ibaraki, Japan
2
Osaka University, Osaka, Japan
3
Ibaraki University, Ibaraki, Japan
4
National Institute of Advanced Industrial Science and Technology, Tsukuba, Ibaraki, Japan
5
Korea Advanced Institute of Science and Technology, Daedeok Innopolis, Daejeon, Korea
Keywords:
Password-based Authenticated Key Exchange (PAKE), Threshold Cryptography.
Abstract:
Password-based Authenticated Key Exchange (PAKE) allows a server to authenticate a user and to establish
a session key shared between the server and the user just by having memorable passwords. In PAKE, con-
ventionally the server is assumed to have the authentication functionality and also provide on-line services
simultaneously. However, in the real-life applications, this may not be the case, and the authentication server
may be separate from on-line service providers. In such a case, there is a problem that a malicious service
provider with no authentication functionality may be able to guess the passwords by interacting with other
participants repeatedly. Abdalla et al. put forward a notion of the server password protection security to deal
with this problem. However, their proposed schemes turned out to be vulnerable to Undetectable On-line
Dictionary Attack (UDonDA). To cope with this situation, we propose the Gateway Threshold PAKE prov-
ably secure against this password guessing attack by also taking the corruption of authentication servers into
consideration.
1 INTRODUCTION
1.1 Background
Password-based authenticated key exchange
(PAKE) (Bellare et al., 2000; Boyko et al., 2000; Gol-
dreich et al., 2001; Katz et al., 2001) is a two-party
key exchange allowing users to utilize memorable
passwords as secret information, where each pass-
word is shared between a user and an authentication
server. Conventional authenticated key exchange
protocols based on a public key cryptosystem need
a key whose length is too long to remember. Since
users cannot memorize such complicated information
without devices, the users are unable to respond to
any incident such as an emergency call unless the
users have the devices. On the other hand, users can
rely on PAKE protocols only with a short character
string, and PAKE will also be suitable for cloud
environments where ubiquitous access is important.
∗
This work was done at NTT Secure Platform Laboratories.
There are two cases where conventional PAKE
cannot be deployed. The first case is that there ex-
ists a gateway between a user and an authentication
server as in a global roaming service. The global
roaming is a system where a user can receive the
same services from an overseas provider even if the
user is located outside service areas of the provider
with which the user has made a contract. For ex-
ample, when receiving on-line services via a foreign
access point by using borrowed devices, a user has
only to enter the password registered with the user’s
domestic provider. In the situation where a gateway
called an access point plays a role of an on-line ser-
vice provider,PAKE cannot be deployed in such envi-
ronments because it is assumed that an authentication
server provides services in PAKE.
The second case is that there exists a malicious
authentication server. Actually, European Network
and Information Security Agency (ENISA) (ENISA,
2009) pointed out that malicious providers could be a
high threat with social influence. Even if a provider
39
Kobayashi Y., Yanai N., Yoneyama K., Nishide T., Hanaoka G., Kim K. and Okamoto E..
Gateway Threshold Password-based Authenticated Key Exchange Secure against Undetectable On-line Dictionary Attack.
DOI: 10.5220/0005539300390052
In Proceedings of the 12th International Conference on Security and Cryptography (SECRYPT-2015), pages 39-52
ISBN: 978-989-758-117-5
Copyright
c
2015 SCITEPRESS (Science and Technology Publications, Lda.)

is honest, vulnerabilities on a system can also cause
a problem such as Heartbleed in April 2014. In
fact, the vulnerability of OpenSSL can cause a prob-
lem that the passwords stored in servers are leaked.
ENISA pointed out that an adversary can potentially
obtain the passwords of all users without authentica-
tion (ENISA, 2014). PAKE cannot defend against
such a threat because a single trusted authentication
server stores all the passwords.
Abdalla et al. (Abdalla et al., 2005; Abdalla et
al., 2008) proposed schemes to solve those problems.
Gateway PAKE (GPAKE) is a scheme addressing the
first problem and Gateway Threshold PAKE (GT-
PAKE) is a scheme addressing both problems. How-
ever, their schemes are vulnerable to Undetectable
On-line Dictionary Attack (UDonDA) (Ding et al.,
1995), where an adversary guesses a password in on-
line transaction and its password guessing attack is
not detected by any authentication server. In (Ab-
dalla et al., 2008), it is mentioned that the scheme
can be modified such that the authentication server
can detect on-line dictionary attacks, but the details of
the modification and its security proof are not given.
In their schemes, an authentication server returns a
message without authenticating users, so the adver-
sary can make unlimited attempts to guess a pass-
word. Due to the low entropy of the password, such a
password guessing attack becomes a serious problem.
Therefore, it is necessary to propose a new scheme
that overcomes UDonDA.
1.2 Contribution
We propose new GTPAKE which has resistance
of UDonDA and the corruption of authentication
servers. We prove the security of our GTPAKE
under standard assumptions in the random oracle
model. The proposed scheme has the stronger secu-
rity against a malicious provider compared with ex-
isting schemes, and a global roaming service used
for users regardless of places and devices is expected
as an application. Our scheme is an instantiation of
GTPAKE, and the generalization of GPAKE and GT-
PAKE is left as future work.
A naive extension of GPAKE does not lead to
GTPAKE with the property described in Section 1.1.
The reason is as follows: If one authentication server
holds plain passwords as in GPAKE, the server can
just compare the received password with the corre-
sponding plain password. However, as stored pass-
words should be hidden from authentication servers
in GTPAKE, the authentication servers cannot eas-
ily verify logins of users. To overcome this prob-
lem, we encrypt the stored passwords by a public
key of the authentication servers where the corre-
sponding secret key is shared among the authentica-
tion servers. Furthermore, in the authentication pro-
cess, the servers decrypt the encrypted password par-
tially and authenticate a user simultaneously without
revealing the password itself.
We compare the proposed scheme with other ex-
isting GPAKE and GTPAKE schemes.
2
As shown in
Table 1, the computation and communication costs
of our protocol are not better than those of GT-
PAKE (Abdalla et al., 2005). However, their secu-
rity proof reduces to the non-standard assumptions
such as the Password-based Chosen-basis Decisional
Diffie-Hellman (PCDDH) assumption, which is vul-
nerable to some attacks (Szydlo, 2006). Even if those
flawed assumptions hold, their scheme is vulnerable
to UDonDA, which is out of security model. The se-
curity of our scheme is proven in the random oracle
model if the DDH assumption holds. Our scheme tol-
erates the corruption of some authentication servers
as their scheme. Furthermore, while their scheme is
vulnerable to UDonDA, our scheme is invulnerable to
this attack, although our proof similar to (Wei et al.,
2011) is given in the non-concurrent setting, which
assumes that a new session does not begin until the
previous session is finished.
The organization of the paper is as follows: In
Section 2, we introduce some background to under-
stand this paper. In Section 3, we define the security
model of GTPAKE. In Section 4, we describe the con-
struction of our scheme. In Section 5, we prove the
security of the proposed scheme. Finally we make
final remarks in Section 6.
2 PRELIMINARIES
We show the notation and the security assumption
used in this paper.
Notation. We use the following notations through-
out this paper. We denote by Z
q
a set {0,1,...,q−1}.
x ← A represents that x is chosen uniformly at random
from a set A. Let g be a generator of subgroup G of
order p over Z
q
and a k b be a concatenation of el-
ements a and b, which is able to be divided into the
original elements. We denote by {0,1}
k
a set of all
binary strings of length k. Especially, {0,1}
∗
means a
set of all binary strings of arbitrary length. A function
negl is negligible if and only if for every positive inte-
2
In the comparison here, we focus only on the schemes
with security proofs, and the discussion about the schemes
without security proofs can be found in (Wei et al., 2011).
SECRYPT2015-InternationalConferenceonSecurityandCryptography
40
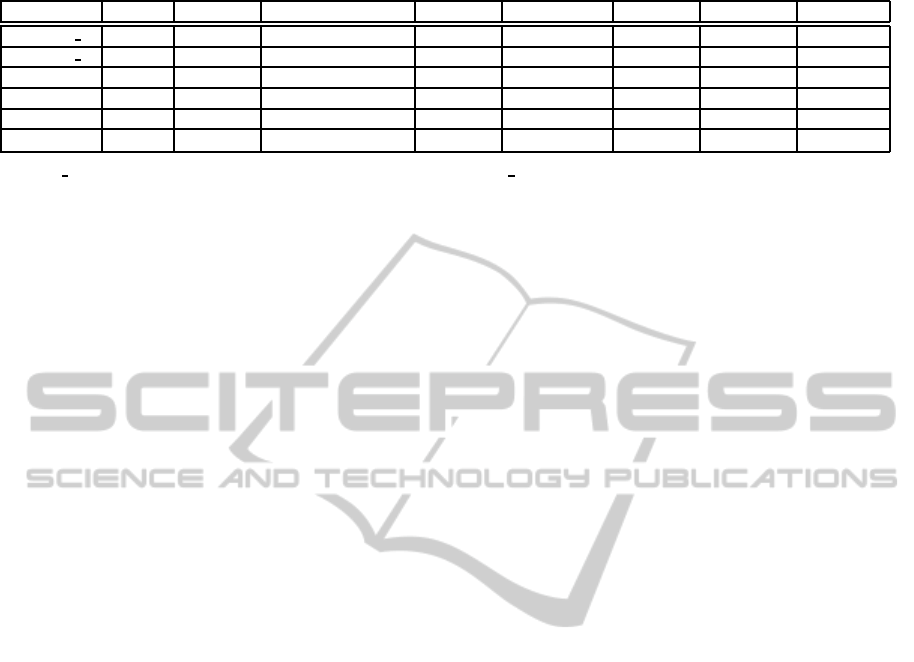
Table 1: Comparison of the existing GPAKE and GTPAKE schemes.
Protocols User Gateway Server Message Assumption Model Threshold UDonDA
ACFP05 a 2e 2e 2e 4 PCDDH ROM NO NO
ACFP05 b 2e 2e (13n+ 18)e 3n+ 4 PCDDH ROM YES NO
WMZ11 3e 2e 2e 6 DDH ROM NO YES
WZM12 5e+ E 2e 5e+ E 6 DDH Standard NO YES
WZM13 3e 2e 2e 9 CDH ROM NO YES
Ours 4e 2e (2n
2
+ 19n+ 11)e 4n+ 11 DDH ROM YES YES
ACFP05 a corresponds to GPAKE in (Abdalla et al., 2005). ACFP05 b corresponds to GTPAKE in (Abdalla et al., 2005).
WMZ11 corresponds to GPAKE in (Wei et al., 2011). WZM12 corresponds to GPAKE in (Wei et al., 2012) and its computa-
tional costs are recalculated by us here. WZM13 corresponds to GPAKE in (Wei et al., 2013). The computational costs for a
user, gateway, and each authentication server are estimated in the User, Gateway, and Server columns, respectively. We use a
modular exponentiation denoted as “e” because a modular exponentiation is the most expensive computation and “E” means
a cost of a public key encryption. For the sake of simplicity, n authentication servers participate in the authentication phase.
In the Message column, the number of communications is shown and we evaluate a broadcast to all authentication servers as
n communication costs. In the Assumption column, a hardness assumption is shown. In the Model column, the random oracle
model or the standard model is shown. In the Threshold column, it is shown whether a protocol tolerates the corruptions
of authentication servers. In the UDonDA column, it is shown whether a protocol can detect malicious login attempts for
guessing the passwords of users.
ger c there exists an integer N such that negl(x) < 1/x
c
for any x > N.
We represent a user as U ∈ U, a gateway as
G ∈ G and the i-th authentication server as S
i
∈ S
for i = 1,..., n where U, G, and S are the set of all
users, gateways, and authentication servers, respec-
tively. Especially, we denote by P any participant in
the set of all participants P (= U ∪ G ∪ S ). We call
one representative of the authentication servers that
communicates with a gateway a combiner C whose
index is contained in the qualified index set L. The
size of L is not less than threshold t.
Security Assumption. The following security as-
sumptions are well-known:
Definition 1. (Computational Diffie-Hellman
(CDH) Assumption.) We define the Computational
Diffie-Hellman (CDH) problem as the problem of
computing g
ab
from given (g,g
a
,g
b
) where g is
a generator chosen at random from group G and
(a,b) ← Z
2
q
. We say the CDH assumption holds in G
if the advantage in solving the CDH problem defined
as Adv
CDH
A
(κ) = Pr[A(g,g
a
,g
b
) = g
ab
] is negligible
for any probabilistic polynomial time algorithm A
with respect to a security parameter κ.
Definition 2. (Decisional Diffie-Hellman (DDH)
Assumption.) We define the Decisional Diffie-
Hellman (DDH) problem as the problem of dis-
tinguishing the distribution of (g,g
a
,g
b
,g
ab
) and
(g,g
a
,g
b
,g
c
) where g is a generator chosen at ran-
dom from group G and (a,b,c) ← Z
3
q
. We say
the DDH assumption holds in G if the advantage in
solving the DDH problem defined as Adv
DDH
A
(κ) =
|Pr[A(g,g
a
,g
b
,g
ab
) = 1] − Pr[A(g,g
a
,g
b
,g
c
) = 1]| is
negligible for any probabilistic polynomial time algo-
rithm A with respect to a security parameter κ.
3 SECURITY MODEL
We describe the system model and security definitions
of GTPAKE, which is a protocol which allows a legit-
imate user to establish a session key with a gateway
with the help of multiple authentication servers. At
the time of authentication, a user cannot directly com-
municate with an authentication server. Although the
communication channel between a user and a gate-
way is insecure and under the control of an adversary,
the channel between a gateway and a combiner is au-
thenticated and the channel between the authentica-
tion servers is secure. When an authentication process
for a user (say, User A) is being processed, another
login attempt from the same user (i.e., User A) is sus-
pended until the preceding authentication process is
finished. We assume a static adversary that corrupts
the set of less than the threshold authentication servers
before the protocol is executed.
3.1 System Model
The proposed scheme consists of the following three
sub-protocols.
• Init. Given the security parameter and the setup
parameters, public parameters params are out-
putted. Although we assume a trusted dealer dis-
tributing some parameters for simplicity, authenti-
cation servers themselves can publish parameters
GatewayThresholdPassword-basedAuthenticatedKeyExchangeSecureagainstUndetectableOn-lineDictionaryAttack
41

by using the technique of the distributed key gen-
eration (Gennaro et al., 2007). If the numbers of
authentication servers are modified, this protocol
phase is executed again.
• Regi. A user registers his password with authenti-
cation servers. If all authentication servers cannot
register the password successfully, then outputs an
error symbol ⊥.
• Auth. The qualified servers the number of which
is not less than the threshold authenticate a user.
If the user and a gateway can establish the same
session key while passing the authentication suc-
cessfully, then outputs a session key sk, otherwise
outputs reject.
3.2 Security Requirements
We describe the security requirements for GTPAKE.
The technical details of reflecting these requirements
are given in Definitions 4 and 6.
Existing Security Requirements. The security re-
quirements for GPAKE are as follows (due to Wei et
al. (Wei et al., 2011)):
• Known-Key Security (KS). The adversary can-
not distinguish a real session key from a random
session key even if the adversary obtains other
session keys.
• Forward Secrecy (FS). The established session
key before the adversary obtains the static keys
of the user including passwords are still indistin-
guishable from a random session key.
• Resistance to Basic Impersonation (BI). The ad-
versary cannot impersonate a legitimate user un-
less the adversary obtains the password of the
user.
• Resistance to Off-line Dictionary Attack
(offDA). The adversary acting as a malicious
gateway cannot guess a password by verifying its
guess in the off-line manner.
• Resistance to Undetectable On-line Dictionary
Attack (UDonDA). The adversary acting as a ma-
licious gateway cannot guess a password by veri-
fying its guess in the on-line manner without be-
ing detected by honest participants.
New Security Requirement. We add a security re-
quirement necessary for the threshold setting. In
GPAKE, an authentication server potentially acts only
as a passive adversary, but in GTPAKE, we need to
take an active adversary corrupting a set of less than
the threshold authentication servers into considera-
tion.
• Resistance to leakage of internal information to
servers (LIS). The adversary cannot distinguish a
real session key from a random session key and
cannot guess a password even if the adversary ob-
tains internal information of some authentication
servers.
3.3 Oracles
We show the necessary oracles to define the stronger
security model than that of GTPAKE (Abdalla et al.,
2005). To distinguish the session between partici-
pants, the i-th instance for participant P is denoted
by P
(i)
. Let U
(i)
, G
( j)
, C
(k)
, and S
(k)
i
be instances of
a user, a gateway, a combiner, and the i-th authentica-
tion server, respectively. The instance of these oracles
defined here reflects the state during the progress of
the protocol.
Existing Oracles (Wei et al., 2011). These oracles
used in existing GPAKE are as follows:
• Execute(U
(i)
,G
( j)
,C
(k)
). This query models pas-
sive attacks. The output of this query consists of
the message exchanged during the honest execu-
tion in the protocol among U
(i)
, G
( j)
, and C
(k)
.
• SendUser(U
(i)
,m). This query models active at-
tacks against a user instance U
(i)
.
3
The output
of this query consists of the message the user in-
stance U
(i)
would generate on receipt of message
m.
• SendGateway(G
( j)
,m). This query models active
attacks against a gateway instance G
( j)
.
3
The out-
put of this query consists of the message the gate-
way instance G
( j)
would generate on receipt of
message m.
• SendServer(C
(k)
,m). This query models active
attacks against a combiner instance C
(k)
.
3
The
output of this query consists of the message the
combiner instance C
(k)
would generate on receipt
of message m.
• SessionKeyReveal(P
(i)
). This query models mis-
uses of session keys which are the intermediate
3
This oracle halts if an adversary asks the oracle in the
invalid order or the counter of incorrect login attempts ex-
ceeds the predetermined limit. The states of the oracle for
an adversary in the same session are preserved. Although
the SendUser and SendServer oracles interacts with an ad-
versary acting as a gateway, the SendGateway oracle inter-
acts with an adversary acting as a user and a combiner.
SECRYPT2015-InternationalConferenceonSecurityandCryptography
42

result calculated from ephemeral keys. If the ses-
sion key for the instance of participant P
(i)
is not
defined, then return ⊥. Otherwise, return the ses-
sion key for P
(i)
.
• StaticKeyReveal(P). This query models leakage
of the static secrets of participant P. If P is a user,
then return the password. If P is a gateway, then
return secret keys for authenticated channels. If
P is an authentication server, then return the en-
crypted passwords for all users, the share of a se-
cret key, and other secret keys for authenticated
and secure channels.
• EphemeralKeyReveal(P
(i)
). This query models
leakage of the ephemeral keys used by instance
P
(i)
. The output of this query consists of the
ephemeral keys of P
(i)
such as chosen random
numbers.
• EstablishParty(U, pw
U
). This query models that
an adversary registers a password pw
U
on behalf
of a userU. The users against whom the adversary
has not ask this query are called honest.
• Test(P
(i)
). This query models the indistinguisha-
bility of the session key of P
(i)
. At the beginning
of an experiment the challenge bit b is chosen. If
the session key for P
(i)
is not defined, then return
⊥. Otherwise, return session key of P
(i)
if b = 1
or a random key of the same size if b = 0. The ad-
versary can ask this query only once at any time
during the experiment.
• TestPassword(U, pw
′
U
). This query models se-
crecy of the password held by an honest user U.
If the guessed password pw
′
U
equals the registered
password pw
U
, then return 1. Otherwise, return 0.
The adversary can ask this query only once at any
time during the experiment.
Added Oracles. We add a new oracle to adapt to
the threshold setting where an adversary can obtain
internal information of authentication servers by cor-
ruption.
• Corrupt(S
i
). This query models intrusion into au-
thentication servers. By asking the query at the
beginning of the protocol, the adversary can take
full control of an authentication server S
i
.
3.4 Security Definitions
We describe the security definitions of GTPAKE. The
definitions here are similar to GPAKE, but the method
of dealing with authentication servers is different.
The Session ID (SID) and Partner ID (PID) are used to
define a partner sharing the session key in PAKE. The
SID is an identifier to determine a session uniquely
and the PID is an instance considered to share a ses-
sion key.
Definition 3. (Partnering (Abdalla et al., 2005).) A
user U
(i)
and a gateway G
( j)
are partnered if the fol-
lowing conditions hold.
1. U
(i)
and G
( j)
are accepted.
2. U
(i)
and G
( j)
have the same SID.
3. The PID ofU
(i)
is G
( j)
and the PID of G
( j)
is U
(i)
.
4. No other instances have the same PID of U
(i)
or
G
( j)
.
For the security of session keys, an adversary can
ask the Test oracle once against a fresh participant.
In the following definition, the adversary is restricted
such that the adversary cannot ask queries that break
the security of the protocol trivially.
Definition 4. (Freshness in Session Key Security.)
A user U
(i)
and a partnered gateway G
( j)
are fresh if
the user is honest and none of the following condi-
tions hold.
1. The adversary asks SessionKeyReveal(U
(i)
) or
SessionKeyReveal(G
( j)
).
2. The adversary asks EphemeralKeyReveal(U
(i)
) or
EphemeralKeyReveal(G
( j)
).
3. The adversary asks SendServer(C
(k)
,m) and ei-
ther queries.
(a) StaticKeyReveal(G).
(b) StaticKeyReveal(C).
4. The adversary asks SendUser(U
(i)
,m) or
SendGateway(G
( j)
,m) and either queries.
(a) StaticKeyReveal(U).
(b) EphemeralKeyReveal(U
(i)
) in any instance i.
(c) Corrupt(S
i
) for not less than t authentication
servers.
In the game to prove the security of session keys,
an adversary is allowed to ask the Execute, SendUser,
SendGateway, SendServer, SessionKeyReveal, Stat-
icKeyReveal, EphemeralKeyReveal, Corrupt, Estab-
lishParty, and Test oracles. The list of participants is
given to an adversary at the beginning of the experi-
ment. In this situation, we define Succ
sks
as the event
that an adversary succeeds in guessing a challenge bit
b in the Test oracle.
Capturing Security Properties of Session Keys.
As described in the condition 1 of Definition 4, KS
is reflected by allowing an adversary to obtain session
keys in the non-target session. As described in the
condition 2, LIS is reflected by allowing an adversary
to obtain internal information of some authentication
GatewayThresholdPassword-basedAuthenticatedKeyExchangeSecureagainstUndetectableOn-lineDictionaryAttack
43

servers and by prohibiting the adversary from obtain-
ing ephemeral keys of users and gateways in the target
session. As described in the condition 3, FS is re-
flected by allowing an adversary to obtain static keys
of the users and by prohibiting the adversary from ob-
taining static keys of partnered gateways and the com-
biner. As described in the condition 4, BI is reflected
by allowing an adversary to ask queries in the non-
target session and by prohibiting the adversary from
obtaining the password of the target user.
Definition 5. (Session Key Security.) In a GTPAKE
protocol L, an advantage of an adversary A for the
session key security is defined as
Adv
sks
L
(A) = |Pr[Succ
sks
] − 1/2|.
The session key security meets the equation
Adv
sks
L
(A) ≤ negl(κ) for any probabilistic polynomial
time adversaries where κ is a security parameter.
For the security of passwords, an adversary can
ask the TestPassword oracle once against a fresh pass-
word.
Definition 6. (Freshness in Password Protection
Security.) A password of a user U is fresh if the user
is honest and an adversary does not ask the following
queries.
1. StaticKeyReveal(U).
2. EphemeralKeyReveal(U
(i)
) in any instance i.
3. Corrupt(S
i
) for not less than t authentication
servers.
In the game to prove the security of pass-
words, an adversary is allowed to ask the SendUser,
SendServer, SessionKeyReveal, StaticKeyReveal,
EphemeralKeyReveal, EstablishParty, Corrupt, and
TestPassword oracles. The list of participants is given
to an adversary at the beginning of the experiment. In
this situation, we define Succ
pps
as the event that an
adversary succeeds in guessing the password pw
U
in
the TestPassword oracle.
Capturing Security Properties of Passwords. As
described in Definition 6, UDonDA is reflected by al-
lowing an adversary to ask the SendUser and Send-
Server oracles until the number of incorrect login at-
tempts does not exceed the predetermined limit. Also
offDA is reflected by allowing an adversary to ob-
tain internal information such as ephemeral or static
keys of the non-target users and a set of less than the
threshold corrupted authentication servers. The cor-
rupted combiner can disturb the communication be-
tween a user and honest authentication servers, but
cannot obtain information about the password of the
user.
Definition 7. ((T ,R )-Password Protection Secu-
rity.) In a GTPAKE protocol L, an advantage of an
adversary A for the (T ,R )-password protection se-
curity is defined as
Adv
pps
L,D
(A) = Pr[Succ
pps
],
where the password is chosen at random from a dic-
tionary D whose size is denoted as |D|. A max ad-
vantage with at most a time T and a resource R is
defined as
Adv
pps
L,D
(T ,R ) = max
A
{Adv
pps
L,D
(A)}.
The (T , R )-password protection security meets
the equation Adv
pps
L,D
(T , R ) ≤ (q
send
+ 1)/|D| +
negl(κ) for any probabilistic polynomial time adver-
saries where q
send
(< |D|) is the number of queries to
the SendUser or SendServer oracles and κ is a secu-
rity parameter.
4 OUR PROPOSED SCHEME
4.1 How to Construct GTPAKE
We describe the problems and give an intuitive ex-
planation of our construction. As described in Sec-
tion 1.2, it is difficult to convert GPAKE of Wei et al.
(which is secure against UDonDA) into GTPAKE in
a naive way. In addition, it seems difficult to make
GTPAKE of Abdalla et al. secure against UDonDA.
In their scheme, it is impossible for an authentica-
tion server to terminate the protocol when an incor-
rect login attempt is made because the message made
by an honest user is indistinguishable from that by
the adversary. In the proposed scheme, it is possible
for authentication servers to compute the result while
keeping a password secret by realizing decryption and
randomization simultaneously. We also use a zero
knowledge proof in communication among authenti-
cation servers to prevent an adversary from showing
incorrect shares.
4.2 Overview of our Scheme
We describe the flow of our proposed scheme. First,
a trusted dealer generates some public system pa-
rameters such as the public key pk of authentication
servers. Second, a user registers the ElGamal encryp-
tion (PW · pk
v
,g
v
) with the hash value PW of his pass-
word pw and a random number v. Third, the user
sends g
r
/PW to authentication servers via a gateway
where r is a random number. After a random num-
ber w is generated while hiding the random number
SECRYPT2015-InternationalConferenceonSecurityandCryptography
44

among authentication servers, a combiner sends g
w
to the user. The user and authentication servers ver-
ify the validity of H(g
rw
) with each other. The user
sends g
x
to the gateway where x is a random number.
The gateway sends g
y
to the user where y is a random
number. Finally, a session key H(g
xy
) is established
between the user and the gateway.
4.3 Construction
We show our proposed scheme based on the system
model defined in Section 3.1. A perspective of the
proposed scheme is shown in Figure 1. First, we de-
scribe the initialization process as below.
Init. Let p be a prime whose bit length is the given
security parameter κ and q be a large prime dividing
p− 1. Let us denote a generator of subgroup G of or-
der q over Z
p
by g. The hash functions H
0
: {0, 1}
∗
→
Z
q
, H
1
: {0,1}
∗
→ G, and H
2
,H
3
: {0,1}
∗
→ {0,1}
κ
are chosen. A trusted dealer computes the param-
eters as follows: The trusted dealer computes an-
other random generator h (6= g) and a public key
pk = g
s
of a secret key s ← Z
q
for the ElGamal en-
cryption. The trusted dealer chooses a
k
← Z
q
for
k = 1,... ,t −1 where t is a given threshold value and
generates a polynomial f(z) = s+a
1
z+···+a
t−1
z
t−1
mod q. The trusted dealer sends a share s
i
= f(i)
mod q to each authentication server S
i
via a secure
channel and publishes g
s
i
mod p among the authen-
tication servers. Finally, the public system param-
eters params = (p,q,G,g,h, pk, H
0
,H
1
,H
2
,H
3
) are
outputted.
Second, we describe the registration process as be-
low.
Regi. A new user chooses a password pw
U
at random
from a dictionary D and computes PW
U
= H
1
(U k
pw
U
) by using his identification U. After generat-
ing the ElGamal encryption Enc(pw
U
) = (PW
U
· pk
v
mod p, g
v
mod p) where v ← Z
q
, the user sends
(U,Enc(pw
U
)) to the authentication servers. This in-
formation is stored in all authentication servers as the
encryption of the password for the user U. If any
problems occur, then an error symbol ⊥ is outputted.
We use the non-interactive zero-knowledge proof
of equality of discrete logarithm as the building block
in a similar manner to Abdalla’s GTPAKE (Abdalla
et al., 2005). We describe the proof system between
a prover and a verifier as follows: The two generators
(g
1
,g
2
) over a group G are given and let EDLog
(g
1
,g
2
)
be the language pairs (x
1
,x
2
) ∈ G
2
where there exists
a random number x ∈ Z
q
such that x
1
= g
x
1
and x
2
=
g
x
2
. The prover chooses y ← Z
q
and computes y
1
= g
y
1
and y
2
= g
y
2
. After computing c = H
0
(q k g
1
k g
2
k x
1
k
x
2
k y
1
k y
2
), the prover computes z = xc + y mod q
and sends (c,z) to the verifier. The verifier checks the
equation c = H
0
(q k g
1
k g
2
k x
1
k x
2
k g
z
1
/x
c
1
k g
z
2
/x
c
2
).
Third, we describe the authentication process
composed of twelve steps as below.
Auth. If a processing request has come in the invalid
order, the request is recorded as an incorrect login at-
tempt and the protocol terminates. When the counter
of incorrect login attempts exceeds the predetermined
limit, a processing request from the gateway to a user
or authentication servers is rejected.
Step 1. A user U computes PW
U
= H
1
(U k pw
U
) by
using his password pw
U
. U chooses r ← Z
q
and com-
putes R
∗
= g
r
/PW
U
. U sends (U,R
∗
) to a gateway G.
Step 2. The gateway G sends (U, G,R
∗
) to a combiner
C.
Step 3. The combiner C publishes (U,G,R
∗
) to
all authentication servers. The authentication server
S
i
generates two polynomials g
i
(z) = b
i,0
+ b
i,1
z +
··· + b
i,t−1
z
t−1
mod q and g
′
i
(z) = b
′
i,0
+ b
′
i,1
z+ ··· +
b
′
i,t−1
z
t−1
mod q where (b
i,k
,b
′
i,k
) ← Z
2
q
for k =
0,...,t − 1. S
i
broadcasts B
i,k
= g
b
i,k
h
b
′
i,k
mod p for
k = 0,...,t − 1 and sends w
i, j
= g
i
( j) mod q,w
′
i, j
=
g
′
i
( j) mod q to S
j
for j = 1, ...,n. S
j
checks the
equation g
w
i, j
h
w
′
i, j
=
∏
t−1
k=0
(B
i,k
)
j
k
for i = 1, ...,n. If
the confirmation does not hold for index i, S
j
pub-
lishes a complaint against S
i
. An authentication server
receiving not less than the threshold t complaints is
marked as disqualified. S
i
receiving a complaint from
S
j
publishes w
i, j
,w
′
i, j
satisfying the confirmation. An
authentication server publishing the complaint with
values satisfying the confirmation is also marked as
disqualified. According to the index set L of not less
than the threshold t non-disqualified authentication
servers, S
i
whose index is included in L computes as
follows: S
i
computes w
i
=
∑
j∈L
w
j,i
and broadcasts
A
i,k
= g
b
i,k
for k = 0,...,t − 1. S
j
checks the equa-
tion g
w
i, j
=
∏
t−1
k=0
(A
i,k
)
j
k
for i ∈ L. If the confirmation
does not hold for index i, S
j
publishes a complaint.
Otherwise S
i
computes W =
∏
i∈L
A
i,0
. Using the
encrypted password Enc(pw
U
) = (E
1
,E
2
) = (PW
U
·
pk
v
,g
v
), S
i
broadcasts F
1,i
= (E
1
· R
∗
)
w
i
, F
2,i
= E
w
i
2
and proofs EDLog
(E
1
·R
∗
,g)
(F
1,i
,
∏
j∈L
∏
t−1
k=0
(A
j,k
)
i
k
),
EDLog
(E
2
,g)
(F
2,i
,
∏
j∈L
∏
t−1
k=0
(A
j,k
)
i
k
). After S
i
checks
the proofs, C sends (U,C,W) to G.
Step 4. The gateway G sends (G,C,W) to U.
Step 5. The user U computes K
1
= W
r
and α =
H
2
(U k G k C k R
∗
k W k K
1
). U chooses (x,d) ← Z
2
q
and computes X = g
x
and a commitmentCom = g
α
h
d
.
U sends (U,X,Com) to G.
Step 6. The gateway G sends (U,Com) to C.
Step 7. The combiner C broadcasts (U,Com) among
S
i
whose index is included in the set L. S
i
com-
GatewayThresholdPassword-basedAuthenticatedKeyExchangeSecureagainstUndetectableOn-lineDictionaryAttack
45

putes F
1
=
∏
i∈L
F
λ
L,0,i
1,i
and F
2
=
∏
i∈L
F
λ
L,0,i
2,i
where
λ
L,i, j
=
∏
{k∈L∧k6= j}
(i− k)/( j − k) is a Lagrange co-
efficient. S
i
broadcasts T
2,i
= F
s
i
2
and a proof
EDLog
(F
2
,g)
(T
2,i
,g
s
i
). After checking the proof, S
i
computes K
1
= F
1
/
∏
i∈L
T
λ
L,0,i
2,i
. S
i
computes α
′
=
H
2
(U k G k C k R
∗
k W k K
1
). C sends (U,α
′
) to G.
Step 8. The gateway G chooses y ← Z
q
and com-
putes Y = g
y
. G computes K
2
= X
y
and an authenti-
cator Auth
′
= H
2
(U k G k C k X k Y k K
2
). G sends
(Y, α
′
,Auth
′
) to U.
Step 9. The user U checks the validity of α
′
by using
α. U computes K
2
= Y
x
and checks the validity of
Auth
′
by using K
2
. If one of the two confirmations is
false, the user increments the counter of incorrect lo-
gin attempts for G, reject is outputted, and the proto-
col is terminated.
4
Otherwise, U computes a session
key sk = H
3
(U k G k C k X k Y k K
2
) and sends (U,d)
to G.
Step 10. The gateway G sends (U,d) to C.
Step 11. The combiner C broadcasts (U,d) among
S
i
whose index is included in the set L. S
i
checks the
validity ofCom by using d and α
′
. If one of the confir-
mations is false, the authentication server increments
the counter of incorrect login attempts forU, reject is
outputted, and the combiner sends (U, failure) to G
where f ailure means that the authentication process
failed. Otherwise, the combiner sends (U,success) to
G where success means that the authentication pro-
cess succeeded.
Step 12. The gateway G computes a session key
sk = H
3
(U k G k C k X k Y k K
2
) and sk is outputted
if success is received. Otherwise (i.e., failure is re-
ceived), the session is rejected.
Remark. We explain the reason why the proposed
scheme uses the commitment scheme in Step 5 al-
though it seems unnecessary. If a user sends α with X
in Step 5 without hiding α, a malicious gateway can
guess the password of a target user with a combina-
tion of the on-line dictionary attack and the off-line
dictionary attack as follows: First, the active adver-
sary chooses the random number
w ← Z
q
and sends
(G,C,g
w
) to the user and obtains α. We note that this
attack in the on-line manner is detected eventually by
honest authentication servers. Second, the passive ad-
versary chooses a password
PW and checks whether
H
2
(U k G k C k R
∗
k g
w
k (R
∗
·PW)
w
) equals the hash
4
An honest user also counts the number of the login failures
if the login attempt failed although a correct password was
used, and will report that the gateway is corrupted if the
counter exceeds the predetermined limit. This is because
the corrupted gateway can cause such login failures.
value
α until the password satisfying this equation
(that is the correct password) is detected.
5 SECURITY ANALYSIS
5.1 Session Key Security
We prove the security of the session key in the pro-
posed scheme under the CDH assumption in the ran-
dom oracle model.
Theorem 1. (Session Key Security.) Let L be our
GTPAKE protocol and A be a probabilistic polyno-
mial time adversary that corrupts at most t −1 authen-
tication servers in advance where (t −1) < n/2. Then
the advantage of A for the session key security in L
is
Adv
sks
L
(A) ≤
q
2
H
0
+ q
2
H
1
+ (q
exe
+ q
send
)
2
2q
+
q
2
H
2
+ q
2
H
3
2
κ+1
+q
exe
· (q
H
2
+ q
H
3
) · Adv
CDH
A
(κ) +
q
H
2
+ q
H
3
q
,
where q
H
0
,q
H
1
,q
H
2
,q
H
3
are the numbers of hash
queries to the oracles H
0
,H
1
,H
2
,H
3
, respectively,
q
exe
is the number of queries to the Execute oracle
and q
send
is the number of queries to the SendUser,
SendGateway, and SendServer oracles.
Proof. We define Succ
sks
in Game n as Succ
sks
n
.
Game 0. This experiment corresponds to a real at-
tack by the adversary in the random oracle model. By
Definition 5, and we have
Adv
sks
L
(A) = |Pr[Succ
sks
0
] − 1/2|.
Game 1. In this experiment, we simulate the hash
functions and the oracle defined in Section 3.3. We
simulate the random oracles H
0
, H
1
, H
2
, and H
3
by
maintaining hash lists Λ
0
, Λ
1
, Λ
2
, and Λ
3
as follows:
• On a hash query H
0
(m), if there already exists
a record (m,r), then we return r; Otherwise, we
choose r ← Z
q
, add the record (m,r) in the hash
list Λ
0
, and return r;
• On a hash query H
1
(m), if there already exists
a record (m,r), then we return r; Otherwise, we
choose r ← G, add the record (m, r) in the hash
list Λ
1
, and return r;
• On a hash query H
2
(m) (resp. H
3
(m)), if there
already exists a record (m,r), then we return r;
Otherwise, we choose r ← {0, 1}
κ
, add the record
(m,r) in the hash list Λ
2
(resp. Λ
3
) and return r;
SECRYPT2015-InternationalConferenceonSecurityandCryptography
46

;DƐŐϰͿ
ǡ ǡ
ൌ
ଵ
צ
՚ Ժ
כ
ൌ
⁄
;DƐŐϱͿ
ǡ ǡ
՚ Ժ
ൌ
௬
ଶ
ൌ
௬
Ԣ ൌ
ଶ
ሺ צ צ צ צ צ
ଶ
ሻ
ଵ
ൌ
ൌ
ଶ
ሺ צ צ צ
כ
צ צ
ଵ
ሻ
ሺǡ ሻ ՚ Ժ
ଶ
ൌ
௫
ൌ
ఈ
݄
ௗ
hƐĞƌܷ 'ĂƚĞǁĂLJܩ ^ĞƌǀĞƌܵ
ďƌŽĂĚĐĂƐƚƐ
ǡ
ൌ
ǡೖ
ĨŽƌ ൌ Ͳǡ ڮ ǡ െ ͳ
ĂŶĚƐĞŶĚƐ
ǡ
ൌ
ǡ
ǡଵ
ڮ
ǡ௧ିଵ
௧ିଵ
ĐŚĞĐŬƐƚŚĞǀĂůŝĚŝƚLJŽĨ
ǡ
ďLJƵƐŝŶŐ
ǡ
ĐŽŵƉƵƚĞƐĂƐŚĂƌĞ
ൌ
∑
ǡ
ŽĨ ൌ
∑
ĂŶĚďƌŽĂĚĐĂƐƚƐ
ଵǡ
ൌ ሺ
ଵ
·
כ
ሻ
௪
ǡ
ଶǡ
ൌ
ଶ
௪
ĐŽŵƉƵƚĞƐ ൌ
∏
ǡ
ŝŶƚŚĞƋƵĂůŝĨŝĞĚƐĞƚ#
ĐŽŵƉƵƚĞƐ
ଵ
ൌ
∏
ଵǡ
ఒ
ಽǡబǡ
ǡ
ଶ
ൌ
∏
ଶǡ
ఒ
ಽǡబǡ
ďƌŽĂĚĐĂƐƚƐ$
ଶǡ
ൌ
ଶ
௦
ĂŶĚĂƉƌŽŽĨ
ĐŽŵƉƵƚĞƐ
ଵ
ൌ
ଵ
∏
$
ଶǡ
ఒ
ಽǡబǡ
⁄
ĂŶĚ′ ൌ
ଶ
ሺ צ צ צ
כ
צ צ
ଵ
ሻ
′ ൌ
ǫ
ଶ
ൌ
௫
Ԣ ൌ
ǫ
ଶ
ሺ צ צ צ צ צ
ଶ
ሻ
& ൌ
ଷ
ሺ צ צ צ צ צ
ଶ
ሻ
ĐŚĞĐŬƐƚŚĞǀĂůŝĚŝƚLJŽĨ ďLJƵƐŝŶŐ
;DƐŐϭͿ
ǡ
כ
;DƐŐϮͿ
ǡ ǡ
כ
;DƐŐϯͿ
ǡ ǡ
;DƐŐϲͿ
ǡ
;DƐŐϴͿ
ǡ ′ǡ ′
;DƐŐϳͿ
ǡ ′
;DƐŐϵͿ
ǡ
;DƐŐϭϬͿ
ǡ
;DƐŐϭϭͿ
ǡ
&''
Ȁ
()*+
&
ൌ
ଷ
ሺ
צ
צ
צ
צ
צ
ଶ
ሻ
Figure 1: Overview of the proposed scheme.
For the simulation in the later games, we also pre-
pare the hash functions H
′
2
and H
′
3
by maintaining
hash lists Λ
′
2
and Λ
′
3
.
The Execute, SendUser, SendGateway, Send-
Server, SessionKeyReveal, StaticKeyReveal,
EphemeralKeyReveal, EstablishParty, Corrupt,
and Test oracles can be simulated as below.
• On a query SendUser(U
(i)
,∗), we proceed as fol-
lows:
If a query StaticKeyReveal(U) or Ephemer-
alKeyReveal(U
(i)
) in any instance i or a query
Corrupt(S
i
) for not less than t authentication
servers has been asked by the adversary or G is a
member of invalid gateways for which the counter
of incorrect login attempts exceeds the predeter-
mined limit or a processing request has come in
the invalid order, we increment the counter of in-
correct login attempts, then do nothing.
1. On a query SendUser(U
(i)
,start), we proceed
as follows: PW
U
= H
1
(U k pw
U
); r ← Z
q
; R
∗
=
g
r
/PW
U
; then return (U,R
∗
);
2. On a query SendUser(U
(i)
,(G,C,W)), we pro-
ceed as follows: K
1
= W
r
; α = H
2
(U k G k
C k R
∗
k W k K
1
); (x,d) ← Z
2
q
; X = g
x
; Com =
g
α
h
d
; then return (U,X,Com);
3. On a query SendUser(U
(i)
,(Y,α
′
,Auth
′
)), we
proceed as follows: We check the validity of
α
′
; K
2
= Y
x
; We check the validity of Auth
′
;
If one of the two confirmations is false, we in-
crement the counter of incorrect login attempts
for G and return abort; Otherwise, sk = H
3
(U k
G k C k X k Y k K
2
); then return (U,d);
• On a query SendServer(C
(k)
,∗), we proceed as
follows:
If a query StaticKeyReveal(G) or StaticKeyRe-
veal(C) has been asked by the adversary or U is
a member of invalid users for which the counter
of incorrect login attempts exceeds the predeter-
mined limit or a processing request has come in
the invalid order, we increment the counter of in-
correct login attempts, then do nothing. In the fol-
lowing queries, an adversary does the process on
behalf of the corrupted authentication server S
j
.
1. On a query SendServer(C
(k)
,(U,G,R
∗
)), we
proceed as follows: The uncorrupted authenti-
cation server S
i
broadcasts B
i,k
= g
b
i,k
h
b
′
i,k
and
sends w
i, j
= g
i
( j),w
′
i, j
= g
′
i
( j) secretly to the
authentication server S
j
corrupted by an adver-
sary; S
i
checks the validity of w
j,i
,w
′
j,i
by us-
ing B
j,k
; S
i
computes a share w
i
=
∑
j∈L
w
j,i
and broadcasts A
i,k
= g
b
i,k
; S
i
checks the valid-
ity of A
j,k
by using w
j,i
; S
i
broadcasts F
1,i
=
(E
1
· R
∗
)
w
i
, F
2,i
= E
w
i
2
and proofs; S
i
checks the
proofs and computes W =
∏
j∈L
A
i,0
; then re-
turn (U,C,W);
2. On a query SendServer(C
(k)
,(U,Com)), we
proceed as follows: The uncorrupted authen-
tication server S
i
computes F
1
=
∏
i∈L
F
λ
L,0,i
1,i
and F
2
=
∏
i∈L
F
λ
L,0,i
2,i
; S
i
broadcasts T
2,i
= F
s
i
2
and a proof; S
i
checks the proof and computes
K
1
= F
1
/
∏
i∈L
T
λ
L,0,i
2,i
; S
i
computes α
′
= H
2
(U k
G k C k R
∗
k W k K
1
); then return (U,α
′
);
3. On a query SendServer(C
(k)
,(U,d)), we pro-
ceed as follows: The uncorrupted authentica-
GatewayThresholdPassword-basedAuthenticatedKeyExchangeSecureagainstUndetectableOn-lineDictionaryAttack
47

tion server S
i
checks the validity of Com; If
one of the confirmations is false, we incre-
ment the counter of incorrect login attempts for
U and return (U, failure); Otherwise, return
(U,success);
• On a query SendGateway(G
( j)
,∗), we proceed as
follows:
If a query StaticKeyReveal(U) or Ephemer-
alKeyReveal(U
(i)
) in any instance i or a query
Corrupt(S
i
) for not less than t authentication
servers has been asked by the adversary or a pro-
cessing request has come in the invalid order, then
do nothing.
1. On a query SendGateway(G
( j)
,(U,R
∗
)), then
return (U,G,R
∗
);
2. On a query SendGateway(G
( j)
,(U,C,W)),
then return (G,C,W);
3. On a query SendGateway(G
( j)
,(U,X,Com)),
then return (U,Com);
4. On a query SendGateway(G
( j)
,(U,α
′
)), y ←
Z
q
; Y = g
y
; K
2
= X
y
; Auth
′
= H
2
(U k G k C k
X k Y k K
2
); then return (Y, α
′
,Auth
′
);
5. On a query SendGateway(G
( j)
,(U,d)), then
return (U,d);
6. On a query SendGateway(G
( j)
,(U,success/
failure)), If success is received, sk = H
3
(U k
G k C k X k Y k K
2
); If failure is received, then
do nothing;
• On a query Execute(U
(i)
,G
( j)
,C
(k)
), we proceed
as follows:
(U,R
∗
) ← SendUser(U
(i)
,start);(U,G,R
∗
) ←
SendGateway(G
( j)
,(U,R
∗
));(U,C,W) ←
SendServer(C
(k)
,(U,G,R));(G,C,W) ←
SendGateway(G
( j)
,(U,C,W));(U,X,Com) ←
SendUser(U
(i)
,(G,C,W));(U,Com) ←
SendGateway(G
( j)
,(U,X,Com));(U,α
′
) ←
SendServer(C
(k)
,(U,Com));(Y,α
′
,Auth
′
) ←
SendGateway(G
( j)
,(U,α
′
));(U,d) ←
SendUser(U
(i)
,(Y,α
′
,Auth
′
));(U,d) ←
SendGateway(G
( j)
,(U,d));(U,success/ failure)
← SendServer(C
(k)
,(U,d));SendGateway
(G
( j)
,(U,success/ failure)); then return
(U,G,C,R
∗
,W, X,Y, α,α
′
,
Auth, Auth
′
,Com,d,success/ failure);
• On a query SessionKeyReveal(P
(i)
), we proceed
as follows:
If the session key sk is defined for the user or the
gateway instance P
(i)
then return sk, else return ⊥;
• On a query StaticKeyReveal(P), we proceed as
follows:
If P is a user U, then return the registered pass-
word pw
U
; If P is a gateway G, then return
a secret key for authenticated channels between
the gateway and authentication servers; If P is
an authentication server S
i
, then return the en-
crypted password Enc(pw) = (PW · pk
v
,g
v
) for
all users, the share s
i
of the secret key for P,
the published parameter g
s
i
for all authentication
servers, and other secret keys for authenticated
channels between the authentication server and a
gateway and secure channels among authentica-
tion servers; else return ⊥;
• On a query EphemeralKeyReveal(P
(i)
), we pro-
ceed as follows:
If there are already the ephemeral keys generated
by the instance P
(i)
, then return the ephemeral
keys, else return ⊥;
• On a query Corrupt(S
i
), we proceed as follows:
We return all the information obtained by the
authentication server S
i
such as static keys,
ephemeral keys, and all the intermediate values of
the computation in S
i
.
• On a query EstablishParty(U, pw
U
), we proceed
as follows:
If there is already a user U, then do nothing, else
establish a new user U with the password pw
U
;
• On a query Test(U
(i)
), we proceed as follows:
sk ← SessionKeyReveal(P
(i)
); if sk = ⊥, then re-
turn ⊥; else b ← {0, 1}; if b = 1 then sk
′
= sk else
sk
′
← {0,1}
κ
; then return sk
′
;
This experiment is perfectly indistinguishable from
the previous experiment, and we have
Pr[Succ
sks
1
] = Pr[Succ
sks
0
].
Game 2. We halt this experiment when the collision
on the outputs of the hash oracles and the transcripts
occurs. We set the number of queries to the hash ora-
cle H
i
as q
H
i
for i = 0,1,2,3, that to the Execute oracle
as q
exe
and that to the SendUser, SendGateway, and
SendServer oracles as q
send
. By the birthday paradox,
and we have
|Pr[Succ
sks
2
] − Pr[Succ
sks
1
]|
≤
q
2
H
0
+ q
2
H
1
+ (q
exe
+ q
send
)
2
2q
+
q
2
H
2
+ q
2
H
3
2
κ+1
.
Game 3. We change the simulation of queries
to the Execute oracle or queries sent by the ora-
cle instances to SendUser and SendGateway oracles
on the selected session. When a query SendGate-
way(G
( j)
,(U,α
′
)) or SendUser(U
(i)
,(Y,α
′
,Auth
′
)) or
SendGateway(G
( j)
,(U,success/ failure)) is asked,
we compute the authenticators Auth (and Auth
′
) and
SECRYPT2015-InternationalConferenceonSecurityandCryptography
48

the session key sk as H
′
2
(U k G k C k X k Y) and
H
′
3
(U k G k C k X k Y) by using the private hash or-
acles H
′
2
and H
′
3
, respectively. The difference be-
tween this experiment and the previous one is in-
distinguishable unless the adversary asks the query
(U k G k C k X k Y k K
2
) to the hash function H
2
or
H
3
. The difference of the following probabilities is
negligible as long as the CDH assumption holds, and
we have
|Pr[Succ
sks
3
] − Pr[Succ
sks
2
]|
≤ q
exe
· (q
H
2
+ q
H
3
) · Adv
CDH
A
(κ).
To evaluate the probability of this event, we con-
struct an algorithm to solve the CDH problem. The
algorithm obtains the CDH tuple (U,V) and chooses
the session (U
(i)
,C
(k)
). We set X = U
u
1
g
u
2
for a query
SendUser(U
(i)
,(G,C,W)) andY = V
u
3
g
u
4
for a query
SendGateway(G
( j)
,(U,α
′
)) where (u
1
,u
2
,u
3
,u
4
) ←
Z
4
q
. All other queries are handled in the same way
as in Game 2. The simulator picks a selected session
as test one with the probability 1/q
exe
. Although the
simulator cannot obtain ephemeral keys of a user and
a gateway by Definition 4, the simulator can simulate
queries to all oracles without log
g
X and log
g
Y.
If the adversary asks the query (U k G k
C k X k Y k K
2
) to the hash function H
2
or
H
3
in the session (U
(i)
,G
( j)
), we can compute
K
2
= CDH(U
u
1
g
u
2
,V
u
3
g
u
4
) = CDH(U
u
1
,V
u
3
) ·
CDH(U
u
1
,g
u
4
) · CDH(g
u
2
,V
u
3
) · CDH(g
u
2
,g
u
4
) =
CDH(U,V)
u
1
u
3
· U
u
1
u
4
· V
u
2
u
3
· g
u
2
u
4
from hash lists
Λ
2
and Λ
3
where CDH is a function to return g
ab
from (g
a
,g
b
) in terms of the generator g in the same
way as (Bresson et al., 2004). In this way, we can
extract the value CDH(U,V) from the given tuple
(U,V). As a result, the only way to distinguish a
session key from a random key is to ask the query
(U k G k C k X k Y k K
2
) to the hash function H
2
or
H
3
. With the probability that the adversary succeeds
in guessing the challenge bit b at random, we have
Pr[Succ
sks
3
] =
1
2
+
q
H
2
+ q
H
3
2
κ
.
5.2 Password Protection Security
We prove the security of the password in the proposed
scheme under the DDH assumption in the random or-
acle model.
Theorem 2. ((T ,R )-Password Protection Secu-
rity.) Let L be our GTPAKE protocol and A be a
probabilistic polynomial time adversary that corrupts
at most t − 1 authentication servers in advance where
(t − 1) < n/2. Then the advantage of A for the pass-
word protection security in L with at most time T and
resource R is
Adv
pps
L
(A) ≤
q
2
H
0
+ q
2
H
1
+ (q
exe
+ q
send
)
2
2q
+
q
2
H
2
+ q
2
H
3
2
κ+1
+(q
exe
+ 1) · Adv
DDH
A
(κ) +
q
sends
+ q
sendu
+ 1
|D|
,
where q
H
0
,q
H
1
,q
H
2
,q
H
3
are the numbers of hash
queries to the oracles H
0
,H
1
,H
2
,H
3
, respectively, q
exe
is the number of queries to the Execute oracle, q
send
is the number of queries to the SendUser, SendGate-
way, and SendServer oracles, q
sends
and q
sendu
are the
numbers of queries to the SendServer and SendUser
oracle, respectively, and |D| is the size of the dictio-
nary D.
Proof. We define Succ
pps
in Game n as Succ
pps
n
.
Game 0. This experiment corresponds to a real at-
tack by the adversary in the random oracle model. By
Definition 7, and we have
Adv
pps
L,D
(A) = Pr[Succ
pps
0
].
Game 1. As in the proof of Section 5.1, we can sim-
ulate the hash functions H
i
for i = 0,1,2,3, the Ex-
ecute, SendUser, SendGateway, SendServer, Ses-
sionKeyReveal, StaticKeyReveal, EphemeralKeyRe-
veal, EstablishParty, and Corrupt oracles. We simu-
late the TestPassword oracle as below.
• On a query TestPassword(U, pw
′
U
), we proceed as
follows: pw
U
← StaticKeyReveal(U); If pw
′
U
=
pw
U
, then return 1, else return 0;
This experiment is perfectly indistinguishable
from the previous experiment, and we have
Pr[Succ
pps
1
] = Pr[Succ
pps
0
].
Game 2. We halt this experiment when the collision
on the outputs of the hash oracles and the transcripts
occurs. By the birthday paradox, and we have
|Pr[Succ
pps
2
] − Pr[Succ
pps
1
]|
≤
q
2
H
0
+ q
2
H
1
+ (q
exe
+ q
send
)
2
2q
+
q
2
H
2
+ q
2
H
3
2
κ+1
.
Game 3. We change the simulation of the queries to
the SendServer oracle for all sessions and the Cor-
rupt oracle for authentication servers. When a query
SendServer(C
(k)
,(U,Com)) or Corrupt(S
i
) is asked,
we replace the secret part needed to decrypt the stored
ElGamal encryption of the password with a random
element for honest users. The difference between this
experiment and the previous one is the stored pass-
words which are not generated by EstablishParty. The
GatewayThresholdPassword-basedAuthenticatedKeyExchangeSecureagainstUndetectableOn-lineDictionaryAttack
49

difference of the following probabilities is negligible
as long as the DDH assumption holds, and we have
|Pr[Succ
pps
3
] − Pr[Succ
pps
2
]| ≤ Adv
DDH
A
(κ).
Suppose a successful distinguisher between
Games 2 and 3, and we construct an algorithm to
solve the DDH problem to prove the above.
The simulator needs to change the process done
by uncorrupted authentication servers to be consistent
with the intended values. We assume w.l.o.g. that S
n
is in the set of uncorrupted authentication servers par-
ticipating in the authentication process. The simulator
controls the other uncorrupted authentication servers
as usual.
First, we deal with the simulation about the public
key in the setup phase Init. In this proposed model,
the trusted dealer computes a secret key s, the public
key pk = g
s
, and the corresponding share g
s
i
. Given
g
s
without s, the simulator needs to publish g
s
n
as a
trusted dealer such that g
s
is the ElGamal public key.
Using the DDH triple (U,V,Z), the corresponding
share for S
n
is set as g
s
n
= U
λ
S,n,0
·
∏
j∈(L\{n})
(g
s
j
)
λ
S,n, j
where λ
S,i, j
=
∏
{k|S
k
∈S∧k6= j}
(i − k)/( j − k) is a La-
grange coefficient. Due to the honest majority setting,
the simulator can compute all the share s
i
of secret key
s.
To simplify the system, we assume that the trusted
dealer distributes the shares of the secret key corre-
sponding to the ElGamal public key. We can con-
struct the proposed scheme without the trusted dealer
by producing some parameters among authentication
servers. In this case, we can simulate the public key
by hitting the intended value similar to the distribut-
ing key generation technique (Gennaro et al., 2007).
Second, we deal with the simulation about the
stored passwords in the registration phase Regi. Since
all users register the encrypted passwords by sending
the encrypted passwords to the authentication servers,
the simulator knows all the passwords for honest
users. When a query Corrupt(S
i
) is asked, we em-
bed the DDH triple into all encrypted passwords as
follows. The simulator returns (PW
U
i
· Z
v
i
,V
v
i
) where
v
i
← Z
q
for all honest users and (PW
U
i
· pk
v
,g
v
) for
the other users. Other internal information is given to
the adversary as usual.
Third, we deal with the simulation about a partial
decryption in the authentication phase Auth. We need
to simulate the uncorrupted authentication servers for
SendServer(C
(k)
,(U,Com)). The share T
2,n
for U
i
can be computed as Z
w·v
i
·λ
L,n,0
·
∏
j∈(L\{n})
V
w·v
i
·s
j
·λ
S,n, j
without s
n
. Other parameters generated from uncor-
rupted servers can be simulated similarly to the au-
thentication process.
To detect malicious authentication servers that
publish incorrect shares, the non-interactive zero-
knowledge proof of equality of discrete logarithm is
used in our scheme. In the random oracle model,
the simulator can simulate this proof without know-
ing the secret keys as follows. The simulator chooses
(c,z) ← Z
2
q
and sends (c,z) as the proof. The hash or-
acle H
0
returns c from the hash list Λ
0
if the adversary
asks the query (q,g
1
,g
2
,u
1
,u
2
,g
z
1
/u
c
1
,g
z
2
/u
c
2
).
Therefore, the simulator assigns
(pk,g
v
,CDH(pk,g
v
)) for the given DDH triple
(U,V,Z). In Definition 7, the task of an adversary
is to guess the password of a target user. The
simulator is able to solve the DDH problem by
using the difference of success probability between
each game because all the encrypted passwords for
all honest users includes the DDH triple. In the
case of Z = CDH(U,V), the environment for the
distinguisher corresponds to Game 2. In the case
of Z 6= CDH(U,V), the environment for the distin-
guisher corresponds to Game 3. If the distinguisher
decides that the distinguisher interacted with Game
2, the algorithm outputs 1, otherwise 0.
Game 4. We change the simulation of queries to the
Execute oracle or queries sent by the oracle instances
to SendUser and SendServer oracles on the selected
session. When a query SendUser(U
(i)
,(G,C,W)) or
SendServer(C
(k)
,(U,Com)) is asked, we replace the
Diffie-Hellman key in the authenticators α and α
′
with a random element. The difference of the follow-
ing probabilities between this experiment and the pre-
vious one is negligible as long as the DDH assump-
tion holds, and we have
|Pr[Succ
pps
4
] − Pr[Succ
pps
3
]| ≤ q
exe
· Adv
DDH
A
(κ).
To evaluate the probability of this event, we
construct an algorithm to solve the DDH problem.
The algorithm obtains the DDH triple (U,V,Z) and
chooses the session (U
(i)
,C
(k)
). The distinguisher
picks a selected session as test one with the prob-
ability 1/q
exe
. We want to compute R = U
u
1
for a
query SendUser(U
(i)
,start) and W = V
u
2
for a query
SendServer(C
(k)
,(U,G,R
∗
)) where (u
1
,u
2
) ← Z
2
q
.
When a query SendUser(U
(i)
,start) is asked, we
compute R
∗
= U
u
1
/PW instead of R
∗
= g
r
/PW.
Accordingly, we set K
1
as W
u
1
u
2
on a query
SendUser(U
(i)
,(G,C,W)).
When a query SendServer(C
(k)
,(U,G,R
∗
)) is
asked, we describe the process of honest servers send-
ing and receiving the information privately and pub-
licly for corrupted parties without ephemeral keys
log
g
R and log
g
W as below. The simulator knows all
the shares w
i, j
,w
′
i, j
, the coefficients b
i,k
,b
′
i,k
, and the
public values B
i,k
due to the honest majority setting.
We assume w.l.o.g. that S
n
is in the set of uncorrupted
authentication servers in the well-defined set L. We
SECRYPT2015-InternationalConferenceonSecurityandCryptography
50

compute A
i,k
= g
b
i,k
for i ∈ (L\{n}), k = 0,...,t − 1
and set A
∗
n,0
= V
u
2
∏
i∈(L\{n})
(A
i,0
)
−1
. We assign
w
∗
n, j
= g
n
( j) for j ∈ (L\{n}) and compute A
∗
n,k
=
(A
∗
n,0
)
λ
L,k,0
·
∏
j∈(L\{n})
(g
w
∗
n, j
)
λ
L,k, j
for k = 1,...,t −
1. We broadcast A
i,k
for uncorrupted authentication
servers S
i
and A
∗
n,k
for k = 0, ...,t − 1. We broadcast
F
1,n
= (V
u
2
sv
·Z
u
1
u
2
)
λ
L,n,0
·
∏
j∈(L\{n})
(U
u
1
· pk
v
)
w
j
·λ
L,n, j
and F
2,n
= (V
u
2
v
)
λ
L,n,0
·
∏
j∈(L\{n})
(E
2
)
w
j
·λ
L,n, j
. All
other processes are handled in the same way as in the
previous game.
Since the simulation in the generation of log
g
W is
identical to the action in the previous game, the set L
can be the same as the real protocol at the end of the
protocol. Accordingly, other parameters such as w
′
i, j
are defined without contradiction. More details can be
found in (Gennaro et al., 2007). We note that the pass-
word obtained via the Execute oracle is information-
theoretically hidden in sessions because R, X, and K
1
are relatively independent in every session. On the
other hand, the passwords obtained via the SendUser
and SendServer oracles are still used in sessions.
Therefore, the simulator assigns
(R,W, CDH(R,W)) for the triple (U
u
1
,V
u
2
,Z
u
1
u
2
).
In the case of Z = CDH(U,V), the environment
for the distinguisher corresponds to Game 3. In
the case of Z 6= CDH(U,V), the environment for
the distinguisher corresponds to Game 4. If the
distinguisher decides that the distinguisher interacted
with Game 3, the algorithm outputs 1, otherwise 0.
Game 5. We change the simulation of the queries
to the SendServer oracle. When a query Send-
Server(C
(k)
,(U,Com)) is asked, we compute the au-
thenticator α
′
as H
′
2
(U k G k C k R
∗
k W) by us-
ing the private hash oracle H
′
2
. The difference be-
tween this experiment and the previous one is indis-
tinguishable unless the adversary asks a query (U k
G k C k R
∗
k W k K
1
) to the hash function H
2
where
K
1
= CDH(R
∗
· PW,W).
There is at most one password such that K
1
=
CDH(R
∗
· PW,W) for some pair (R
∗
,W) as a result
of Lemma 2 in (Bresson et al., 2004). Therefore,
the probability that this bad event occurs in the non-
concurrent setting is bounded by the probability that
an adversary guesses the password at random through
the SendServer oracle to which q
sends
is the number
of queries with at most time T and resource R where
|D| is the size of the dictionary D, we have
|Pr[Succ
pps
5
] − Pr[Succ
pps
4
]| ≤
q
sends
|D|
.
Game 6. We change the simulation of the queries to
the SendUser oracle. When SendUser(U
(i)
,start) is
asked, we compute R
∗
as g
r
∗
where r
∗
← Z
q
without
using the password pw
U
. R
∗
has been simulated, but
W has been generated by an adversary who tries to
impersonate a combiner to a user. To succeed in pass-
ing the verification done by the user, the adversary
needs to send an authenticator α which is computed
with at most one password in the non-concurrent set-
ting. Then the success probability with at most time
T and resource R is at most q
sendu
/|D| where q
sendu
is the number of queries to the SendUser oracle, we
have
|Pr[Succ
pps
6
] − Pr[Succ
pps
5
]| ≤
q
sendu
|D|
.
We note that if a user sends the hash value α
without using the commitment Com, the adversary
can compute the password of the honest user as de-
scribed in Section 4.3. This means the proof can-
not go through if we do not use the commitment
Com due to the existence of such an adversary distin-
guishing between the previous game and this game.
In the proposed scheme, however, α is information-
theoretically hidden by the commitment, so the differ-
ence between this experiment and the previous one is
indistinguishable. We note also that the user reveals α
to the authentication servers in Step 9 eventually only
when the authentication servers already sent the same
α
′
to the user, so this does not cause any harm in terms
of security.
In this game, the information of the password ob-
tained via the SendUser and SendServer oracles is
not used in sessions, so the malicious gateway cannot
do much better than guessing the password at random.
Finally, the adversary guesses the password through
the TestPassword oracle once, we have
Pr[Succ
pps
6
] =
1
|D|
.
6 CONCLUDING REMARKS
We proposed new GTPAKE which has resistance
of UDonDA and the corruption of authentication
servers. We proved the security of our GTPAKE
under standard assumptions in the random oracle
model. The proposed scheme has the stronger secu-
rity against a malicious provider compared with ex-
isting schemes, and a global roaming service used for
users regardless of places and devices is expected as
an application.
ACKNOWLEDGEMENTS
We would like to thank Shin-Akarui-Angou-
Benkyou-Kai for their valuable comments. This
GatewayThresholdPassword-basedAuthenticatedKeyExchangeSecureagainstUndetectableOn-lineDictionaryAttack
51

work was partially supported by JSPS KAKENHI
Grant Number 26330151, 26880012, Kurata Grant
from The Kurata Memorial Hitachi Science and
Technology Foundation, JSPS A3 Foresight Program,
and JSPS and DST under the Japan - India Science
Cooperative Program.
REFERENCES
Abdalla, M., Chevassut, O., Fouque, P.A., Pointcheval,
D.: A Simple Threshold Authenticated Key Exchange
from Short Secrets. ASIACRYPT 2005, LNCS
vol.3788, pp.566-584 (2005)
Abdalla, M., Izabachene, M., Pointcheval, D.: Anony-
mous and Transparent Gateway-Based Password-
Authenticated Key Exchange. CANS 2008, LNCS
vol.5339, pp.133-148 (2008)
Bellare, M., Pointcheval, D., Rogaway, P.: Authenti-
cated Key Exchange Secure against Dictionary At-
tacks. EUROCRYPT 2000, LNCS vol.1807, pp.139-
155, (2000)
Boyko, V., MacKenzie, P., Patel, S.: Provably Secure
Password-Authenticated Key Exchange Using Diffie-
Hellman. EUROCRYPT 2000, LNCS vol.1807,
pp.156-171, (2000)
Bresson, E., Chevassut, O., Pointcheval, D.: New Secu-
rity Results on Encrypted Key Exchange. PKC 2004,
LNCS vol.2947, pp.145-158 (2004)
Byun, J.W., Lee, D.H., Lim, J.I.: Security analysis and im-
provement of a gateway-oriented password-based au-
thenticated key exchange protocol. IEEE Communi-
cations Letters vol.10 no.9, pp.683-685 (2006)
Ding, Y., Horster, P.: Undetectable On-line Password
Guessing Attacks. Operating Systems Review vol.29
no.4, pp.77-86 (1995)
European Network and Information Security Agency.:
Cloud computing risk assessment. (2009)
European Network and Information Security Agency.:
Heartbleed Wake Up Call. (2014)
Gennaro, R., Jarecki, S.,Krawczyk, H., Rabin, T.: Secure
Distributed Key Generation for Discrete-Log Based
Cryptosystems. J. Cryptology vol.20 no.1, pp.51-83
(2007)
Goldreich, O., Lindell, Y.: Session-Key Generation Us-
ing Human Passwords Only. CRYPTO 2001, LNCS
vol.2139, pp.408-432, (2001)
Katz, J., Ostrovsky, R., Yung, M.: Efficient Password-
Authenticated Key Exchange Using Human-
Memorable Passwords. EUROCRYPT 2001,
LNCS vol.2045, pp.475-494, (2001)
Szydlo, M.: A Note on Chosen-Basis Decisional Diffie-
Hellman Assumptions. FC 2006, LNCS vol.4107,
pp.166-170 (2006)
Wei, F., Ma, C., Zhang, Z.: Gateway-Oriented Password-
Authenticated Key Exchange Protocol with Stronger
Security. ProvSec 2011, LNCS vol.6980, pp.366-379
(2011)
Wei, F., Zhang, Z., Ma, C.: Analysis and Enhancement
of an Optimized Gateway-Oriented Password-Based
Authenticated Key Exchange Protocol. IEICE Trans-
actions vol.96-A no.9, pp.1864-1871 (2013)
Wei, F., Zhang, Z., Ma, C.: Gateway-oriented password-
authenticated key exchange protocol in the standard
model. Journal of Systems and Software vol.85 no.3,
pp.760-768 (2012)
SECRYPT2015-InternationalConferenceonSecurityandCryptography
52
