
Leveraging Use of Software-license-protected Applications in Clouds
Wolfgang Ziegler
1
, Hassan Rasheed
2
and Karl Catewicz
2
1
Fraunhofer Institute SCAI, Department of Bioinformatics, 53754 Sankt Augustin, Germany
2
Fraunhofer Institute FIT, User-Centered Computing Department, 53754 Sankt Augustin, Germany
Keywords:
Cloud Computing, Software, IPR.
Abstract:
Running software license-protected commercial applications in IaaS or PaaS Cloud environments is still an
issue that is not resolved in a satisfying way that benefit both the independent software vendor (ISV) and its
customers. Due to the mandatory centralised control of license usage at application run-time, e.g. heartbeat
control by the license server running at the home site of a user, traditional software licensing practices are not
suitable especially when the distributed environment stretches across administrative domains. Although there
have been a few bilateral agreements between ISVs and Cloud providers in the past to allow customers of these
ISVs to run some of the ISVs license-protected applications in Clouds of certain providers a general solution
is still lacking. In this paper we present an approach for software licensing that allows location independent
use of software licenses both in form of delegation of already purchased on-site licenses to the Cloud and with
authorisations for individual application executions in the Cloud.
1 INTRODUCTION
Cloud computing starts fulfilling its promise to pro-
vide a more flexible and cost-effective approach de-
livering infrastructure services than traditional IT ser-
vices. However, cost-effectiveness and flexibility are
foiled when the Cloud customer starts using commer-
cial software on the acquired infrastructure resources
since both the licensing technology and the business
models of the independent software vendors (ISV)
are not in line with the Cloud computing paradigm.
Running software license-protected commercial ap-
plications in IaaS or PaaS Cloud environments is still
an issue that is not resolved in a satisfying way that
benefit both the independent software vendor (ISV)
and its customers. The current technology and con-
tracts force the customer to restrict the use of license-
protected applications to internal private Clouds with-
out the possibility of Cloud bursting or the use of
multi-Clouds. The ISV on the other side is faced
with increased usage of its software under the same
yearly flat rate. Although there have been a few bilat-
eral agreements between ISVs and Cloud providers
in the past (see Section 2) to allow customers of these
ISVs to run some of the ISVs’ license-protected ap-
plications in Clouds of certain providers a general so-
lution is still lacking. The objectives of the work de-
scribed in the following sections are facilitating the
use of license protected software in Clouds, increas-
ing the flexibility of end-users to run their commercial
applications in the most suitable and/or less costly en-
vironment, protecting the IPR of the ISV, and laying
the foundations for new business models of ISVs by
providing a novel software licensing and license man-
agement technology that is designed for todays dis-
tributed computing infrastructures. The solution is
• facilitating the use of license protected software
in Clouds,
• increasing the flexibility of end-users to run
their commercial applications in the most suitable
and/or less costly environment,
• protecting the IPR of the ISV,
• laying the foundations for new business models of
ISVs.
In this paper we present research and development
results from the European project OPTIMIS (OPTI-
MIS, 2013) and their application in the industrial do-
main through a number of experiments in the Euro-
pean project Fortissimo (Fortissimo, 2016). The work
in OPTIMIS was using the results of the European
project SmartLM (SmartLM, 2011) as a basis for de-
veloping software licensing and license management
for Cloud computing. The OPTIMIS results extend
the prototype for use in multi-Cloud environments,
Ziegler, W., Rasheed, H. and Catewicz, K.
Leveraging Use of Software-license-protected Applications in Clouds.
In Proceedings of the 6th International Conference on Cloud Computing and Services Science (CLOSER 2016) - Volume 2, pages 265-273
ISBN: 978-989-758-182-3
Copyright
c
2016 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
265

both in form of delegation of already purchased on-
site licenses to the Cloud and with authorisations for
individual application executions in the Cloud. The
approach supports both the traditional yearly flat rate
licensing but also the pay-per-use approach, which is
more appropriate for agile Cloud usage.
The remainder of this article is organised as fol-
lows. Section 2 presents related work in the area of li-
cense management in Clouds, Section 3 describes the
basic technology upon which the OPTIMIS solution
was build upon. The developments in OPTIMIS are
described in Section 4. Section 5 presents the results
of the evaluation of the implementation in a commer-
cial Cloud infrastructure and Section 6 concludes the
paper.
2 RELATED WORK
So far, commercial software has been and still is
rarely used in Grids and public Clouds due to the lim-
itations both with respect to the license management
technology and the missing business models of the
independent software vendors (ISV) for using their
software in the Grid or the Cloud. Only in 2009
MathWorks has provided a technical solution (and a
business model) allowing to use their MATLAB suite
in the EGEE Grid environment (MATLAB, 2009).
However, this is a bilateral agreement only and has
so far no implications for using MathWorks software
in other Grids like the German D-Grid. Lately, IBM
launched a cooperation with Amazon allowing IBM’s
customers to use own software licenses for a lim-
ited number of applications under certain conditions
in the Amazon Elastic Compute Cloud (EC2), which
is extending BYOSL from the IBM Cloud to a pub-
lic Cloud. However, the use of the ”bring your own
software and license” (BYOSL) (BYOSL, 2013) op-
tion would have to be settled by IBM with each Cloud
provider where a user wants to deploy and use an
application. In addition to iBM’s BYOSL presented
above there are first offerings of companies for Soft-
ware Digital Rights Management technologies to be
used in Clouds. Following we present approaches
of those three that together have a market share of
more than 80% (Sullivan, 2010): SafeNet, Flexera
and Wibu (in descending order of the individual mar-
ket share).
SafeNet as the market leader provides their prod-
uct Sentinel Cloud Service (Sentinel, 2014), which
is a framework for protecting software and data in
the Cloud. This software has been provided since
2011. Sentinel Cloud Services is software for licens-
ing and entitlement management delivered as a ser-
vice for cloud services. It is supporting vendors of
SaaS and PaaS service offerings. SafeNet Sentinel
Cloud Services provides an alternative to traditional
billing and payments services through its catalog-
driven licensing and entitlement management solu-
tion. The solution includes the ability to package
and re-package service offerings and pricing models,
the ability to control what aspects of a service a spe-
cific end user can access including the particular ac-
cess rights. In addition to the traditional approach of
a license server on-site with firewall ports opened to
control the application execution in the Cloud or a li-
cense server deployed in the Cloud, there is no spe-
cific support for IaaS. Drawbacks of these approaches
are the additional security risks having open ports for
bi-directional protocols and additional licenses liable
to pay costs needed for the deployed license server.
In 2010, Flexera announced they would provide
in 2011 Cloud-specific extensions to their product
FlexNet Licensing (FLEXERA, 2014). The basic idea
of the technology is binding the licensing process to
the hosting environment or to the underlying hard-
ware. The developments were made including coop-
eration with VMWare (vmware, 2014) and allow re-
placing the current binding of a license to a physical
server (where the license server is running) to a virtual
machine hosting the license server or the hardware the
virtual machine is running on. However, the informa-
tion on the Flexera web-site about the outcome of this
cooperation still are more than vague. From the Flex-
era web-site it is not evident as to whether or not the
development has achieved a mature state until today
as planned.
Wibu, the third company among the big three,
is a German SME providing solutions for protecting
intellectual properties ranging from software to me-
dia. While the initial focus of the company was on
dongle-based solutions, the company has extended its
technology to software-based protection mechanisms.
For Cloud environments, Wibu started research co-
operation with the Fraunhofer institute ITWM to in-
vestigate in a solution based on the (Dalheimer and
Pfreundt, 2009) license management (development
of Fraunhofer ITWM). The state of the joint project
S4Cloud is unclear as both partners don’t provide
more actual information other than a short article on
the Wibu web-pages and ITWM’s press release of
2010 (S4Cloud, 2015), (ITWM, 2010). The S4Cloud
approach is based on software tokens that include a
Hash of the input data of an application run. While
this is a similar approach as taken by SmartLM, the
major difference is that when the token is created, the
ISV of the license-protected applications have to be
contacted to get an online electronic authorisation. In
CLOSER 2016 - 6th International Conference on Cloud Computing and Services Science
266

contrast, SmartLM does not need online authorisation
of the ISV for creating a token since the ISV already
authorised the license server of the licensee to act on
his behalf.
To the best of our knowledge little public research
has been focusing on licensing technology since the
new IT infrastructure paradigms - Grids, Clouds and
SOA - became serious extensions and replacements
of traditional IT infrastructures. Early approaches
like (Dong et al., 2005), (FU et al., 2007) and (Guofu
et al., 2006) propose front-ends to the FlexNet Li-
cense manager (FlexnetManager, 2015) providing
scheduling and reservation of licenses. However,
both approaches assume open firewall ports at run-
time to enable the communication between license
manager and application. (Dong et al., 2006) focusses
on maximisation of license usage and resource usage
in Grids. Like the previously mentioned approaches
open firewall ports at runtime are a prerequisite. Other
approaches like (Kwok and Lui, 2002) and (Liu et al.,
2007) stem from the P2P environment. The former
addressing licensing of music sharing while the sec-
ond one is more generally addressing content shar-
ing. However,both approaches grant unlimited access
or usage once a license has been issued and thus do
not support a business model useful for ISVs. (Kat-
saros et al., 2009) finally is proposing a license mech-
anism suitable for SOA environments. However, the
paper sketches the architecture and some possible in-
teractions but lacks an implementation and experi-
ments with real applications. Moreover, the approach
also assumes open firewall ports at runtime. Only re-
cently when these new paradigms gained ground in
productive environments where e.g. more commer-
cial simulation codes are used than in the e-Science
domain license technology came to the fore. In (Li
et al., 2008) the authors give an overview on current
licensing technologyand models and describe two ap-
proaches developed in European projects to overcome
the limitations. One of the presented approaches
breaks with the current technology and has been im-
plemented as prototype in the SmartLM project while
the second approach circumvents some of the limi-
tations imposed by the de-facto standard of software
licensing. In the European project BEinGRID an-
other approach was developed which allows the use
of existing licenses in Grid environments through tun-
nelling of the communication of the license server to
the application (Raekow et al., 2009). While techni-
cally feasible this approach raises a number of legal
issues since many license contracts prohibit the use
of a software license outside a company or outside a
certain radius from the company. Furthermore, this
approach is no longer maintained since the end of the
BEinGRID project.
As of today (and as far as can be judged from
the publications on the respective web-sites) the ap-
proaches of the major players in he field of Soft-
ware Digital Rights Management are still requiring
network connectivity to the user’s site license server
during application execution in the Cloud, manual in-
teraction with the ISV and are not transparent for the
user. The SmartLM baseline technology for licensing
and license management extended in OPTIMIS over-
comes these limitations.
3 OPTIMIS LICENSE
MANAGEMENT BASELINE
TECHNOLOGY
The key for flexible software licenses that can follow
applications into Clouds without the need to access
an on-site license server at runtime is the separation
of (1) authorisation for license usage and (2) autho-
risation for application execution. (1) is done at the
site of the user considering the local policies for us-
ing licenses, e.g. department quota. The result of a
successful authorisation is a reservation of a license
for a certain time and a software token, that contains
all information to allow the policy enforcement point
in the application to decide on the execution. (2) is
done later in the Cloud where the token is examined
when starting the application. The prototype solution
developed in the European project SmartLM imple-
mented this separation and provides a software to-
ken mechanism that contains all authorisation infor-
mation required by the application API to validate the
request for executing an application and forward the
license information to the applications policy enforce-
ment point in case of a successful validation of the
token.
While usually unreachability of license servers,
e.g. due to firewall rules, leads to applications abort-
ing during start-up the token provides off-line access
to licenses for authorising the execution of an appli-
cation in a Cloud beyond the administrative domain
of the site running the license server .
4 CLOUD
ENVIRONMENT-SPECIFIC
PROVISIONS
Figure 1 depicts the structure of a license token high-
lighting the different levels of protection against fraud
Leveraging Use of Software-license-protected Applications in Clouds
267
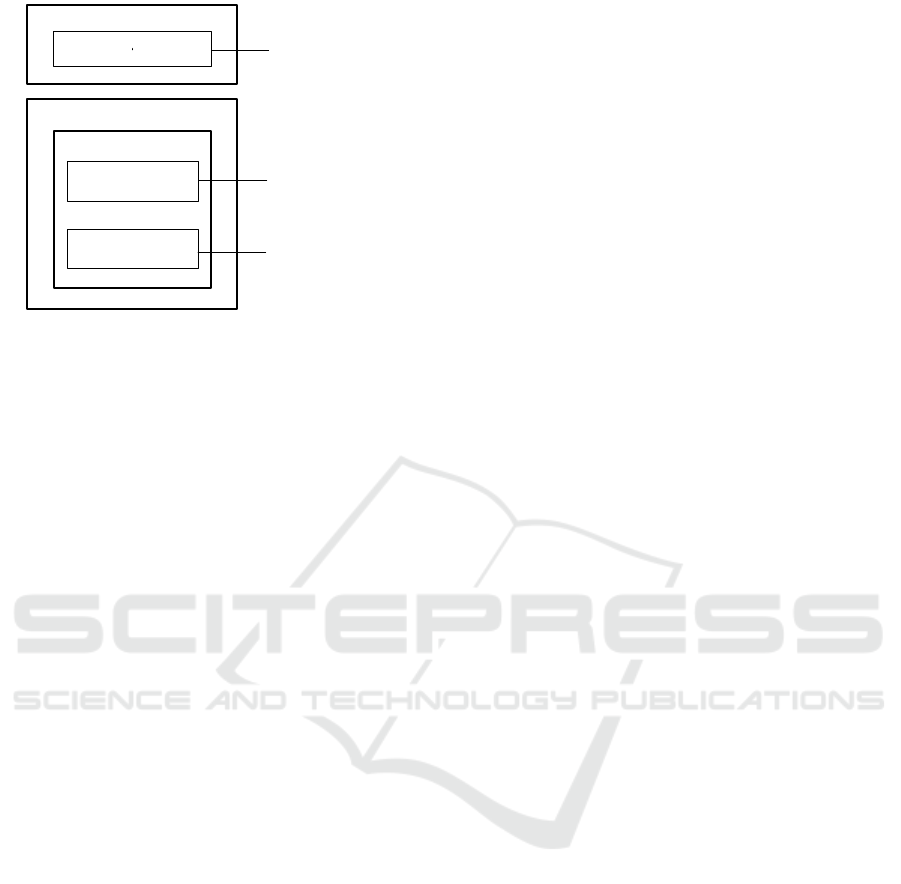
Application
Certificate of the ISV
Token
Authorisation
Certificate of the license server
(Tag SubjectPublicKey)
Certificate of the ISV
(Tag Signature)
The public key of this certificate
is used by the elasticLM system
to validate the signature of the
authorization
The public key of this certificate
is used by the elasticLM system
to validate the signature of the
token
Is used by the method
isTokenAuthorizedBy to verify
that the token was authorised
by a certain ISV
Figure 1: Structure of the license token.
though a chain of trust created with signatures of all
actors involved in the creation of a token. Besides this
internal protection the token may also contain a SHA-
2 hash of the input data needed to run the application.
This has binds the token to the input data and allows
execution of an application only with these input data.
As a result, the token can be copied but the copies can
never used with other data than the token was created
for.
In OPTIMIS additional approaches have been im-
plemented enhancing the SmartLM solution: (i) dy-
namic deployment of a trusted instance managing a
number of tokens for one or multiple applications
and for one or multiple users, and (ii) dynamic de-
ployment of a full license service with a subset of
the licenses available at the home organisation of the
user. The configuration of the dynamically deployed
license service is also managed by the VM contex-
tualiser. The second approach is especially useful
when the same Cloud resources are used over a longer
period of time for running license protected applica-
tions. In the first approach both the user and the con-
textualiser can be responsible for configuring and de-
ploying the trusted instance for the respective network
environment and to transfer tokens.
4.1 Contextualisation
All necessary applications, tools and probably cor-
responding input data to be processed using Cloud
resources can be included in images prepared in ad-
vance for deployment in a IaaS Cloud. These im-
ages can be used multiple times in different environ-
ments. As a consequence, environment specific data,
like e.g. networking configuration, security customi-
sation or software license information are not part of
these images and need to be inserted prior to deploy-
ment. As part of this contextualisation process in OP-
TIMIS also the necessary license tokens for execut-
ing a license-protected application are created dynam-
ically and inserted into the image (Armstrong et al.,
2011), hence, realising License as a Service (LaaS).
In case of multiple applications in a VM, e.g. for a
workflow, the VM contextualizer assures that all re-
quired licenses are in place when the applications start
up. No communication between the application and
the license server that issued the token is required at
runtime.
4.2 License Delegation
This approach is based on the license delegation de-
veloped in OPTIMIS and the deployment of a license
server as part of the contextualisation. It further re-
quires a trustworthy Cloud provider willing to pro-
vide an additional service for retrieving environment-
specific data in form of a hash value of this data. We
suggest using SHA-2, which we consider being safe
enough given the time constraints encoded in the to-
ken and the limited life-time of the delegated licenses
while the time requirements for this algorithm are
suitable for a user-steered on-line process. The trusted
instance is operating on tokens that are created before-
hand when it is known in advance which applications
will be used and which licenses are required. The
tokens can be prepared at the user’s premises. The
license server deployed on the IP’s Cloud infrastruc-
ture supports dynamic, on-the-fly creation of tokens
that are needed for running the applications. See Fig-
ure 2 for the details of the splitting process. Since
the license server creating the tokens is running in the
Cloud environment, it may use the provider’s service
to get the hash of some environment-specific parame-
ters.
When creating the token the hash can be included
and be verified online when the token is processed in
the Cloud. The deployed license service (Server B) is
a copy of the license service that runs locally at the
premises of the user (Server A). This license service
is part of the VM so it can be deployed on the desig-
nated Cloud infrastructure together with the applica-
tions and data. However, the total number of licenses
and features initially procured from the ISV must re-
main the same when a license service is running in
the premises of the user and in the Cloud. To achieve
this, the licenses and features made available for the
license service in Server B in the Cloud are blocked
in Server A and cannot be used locally anymore. Fig-
ure 2 depicts the process of preparing a subset of the
licenses and features available at Server A to be added
to Server B in the Cloud (license delegation).
As shown above, the initial authorisation issued
by the ISV for Server A to install and use a license
CLOSER 2016 - 6th International Conference on Cloud Computing and Services Science
268
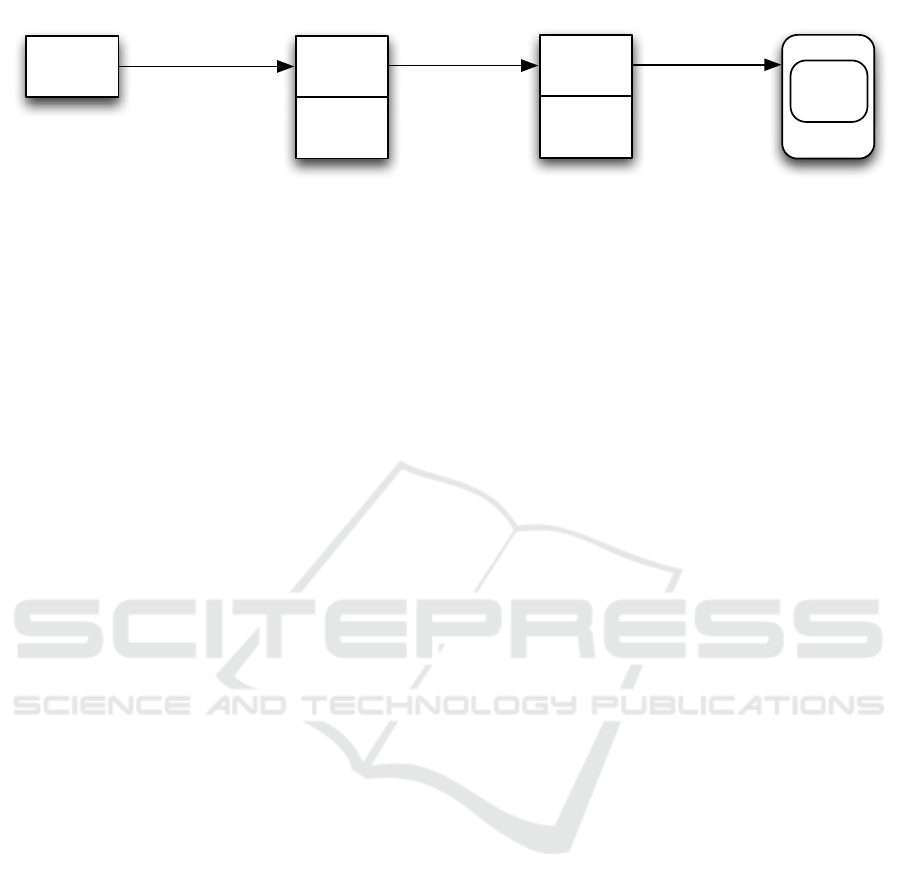
ISV
Customer
License
Service
Signed
license,
features,
Authorisation
ISV authorisation for Server A,
signed licensefile
Server A
Cloud
License
Service
Signed
license,
features,
Authorisation
Server B
ISV authorisation
embedded in Server A
authorisation for Server B,
signed licensefile
issues Token
signed by Server B
Token
Server A authorisation:
ISV authorisation
- Server A
certificate
- ISV signature
Server B certificate
Server A signature
Figure 2: Process of license splitting.
procured from the ISV can be delegated by Server A
to Server B. This delegated authorisation includes the
authorisation of the ISV, the certificate of Server B
and is signed by Server A. Server B includes the au-
thorisation of Server A into each created token. This
allows the API to validate the entire chain of trust up
to the ISV when a token is processed. The authorisa-
tion for using the application is not rejected when the
chain is broken, i.e. when the token is not created by
Server B but by another copy of the license service
running on another server. Moreover, the API can
check at runtime whether the license and features con-
tained in the token are blocked for local use at Server
A.
As an extension of this mechanism we consider
the Cloud provider offering a service that allows re-
trieving key parameters of the Cloud environment en-
coded in a SHA-2 hash key. The parameters should
be significant for the respective environment and thus
deliver a distinct hash key per Cloud environment.
Some kind of standardized set of parameters should
possibly be defined to achieve the goal of uniqueness
across different providers. A first set of parameters to
start the evaluation included: Cloud provider’s name,
Cloud provider’s access point IP address, type of Vir-
tualisation Software, operating system, date/time un-
til the hash key is valid, some unique properties of the
hardware the VMs will be executed upon.
With this extension, the license delegation mech-
anism would look like the diagram depicted in Fig-
ure 3. The tokens created by the license server in
the Cloud contain the hash key of the local Cloud en-
vironment as additional information. When the ap-
plication starts executing, the API validates the to-
ken as usual. In addition, it also makes a call to
the provider’s information service to retrieve the hash
key. If the hash key matches the one in the token,
the API continues providing the license information
in the token to the policy enforcement point in the
application to grant or deny further execution of the
application.
Adding the hash key of the provider’s environment
adds additional protection against fraud. E.g. just
cloning the VM with the license server and running
it in a different Cloud environment is not easily pos-
sible. Of course, the level of desirable protection (and
the effort spent for achieving this) strongly depends
on the value that is to be protected. Also, the effort
put into breaching a mechanism depends on the value
that is protected by this mechanism. While this ap-
proach is able to increase the token protection against
fraud, it also limits the flexibility that the usage of
Cloud resources may provide. Binding the token to
information retrieved from the execution environment
inhibits Cloud dynamics like Cloud bursting. In this
approach we would need a provider to cooperate and
implement the hash function. In contrast to the trusted
instance described before in section 4.2, the solution
depends on a third party the Cloud provider deliver-
ing the hash key and as such is not as easy/fast to
implement as the previously described approach.
Clearly, the ISV has to allow license delegation.
The ISV can do this implicitly through providing an
extended API that is able to validate the delegation
chain. Any non-enhanced API would reject the to-
kens that were created based on a delegated license.
In case the ISV does not allow license delegation an-
other possibility for providing multiple execution au-
thorisations in the Cloud is the Trusted Instance de-
scribed in the next section.
4.3 Trusted Instance
The rationale behind the trusted instance is twofold:
providing a secure container for tokens that in addi-
tion is able to communicate with the API (the applica-
tions policy decision point) and to deliver all informa-
tion to the API required to authorise a user’s request
to launch an application. As depicted in Figure 4 the
same mechanism for binding tokens to the respective
Cloud environment can be used as with license dele-
gation.
The trusted instance verifies that the token is valid.
Additionally, depending on firewall restrictions, it
may provide a secure channel that can be used for
communication with the license server located at the
user’s premises (e.g. to verify the status of a token
prior and during the operation of the license-protected
application or to cancel a reservation). If renegotia-
tion of the license terms is allowed (which is defined
Leveraging Use of Software-license-protected Applications in Clouds
269

ISV
Customer
License
Service
Signed
license,
features,
Authorisation
ISV authorisation
for Server A,
signed licensefile
Server A
Cloud
License
Service
Signed
license,
features,
Authorisation
Server B
ISV authorisation
embedded in Server A
authorisation for Server B,
signed licensefile
issues Token
signed by Server B
Token
Server A authorisation:
ISV authorisation
- Server A
certificate
- ISV signature
Server B certificate
Server A signature
A
Validate authorisations
Validate hash key
Figure 3: Process of the license delegation.
in the token) and the secure channel is available, rene-
gotiation of license terms could be started in case of
shortage of resources, e.g. time running out or ad-
ditional features needed due to the dynamic nature
of the application. The trusted instance is in a VM
that can be deployed in the Cloud together with the
application VM(s). The OPTIMIS contextualiser is
responsible for setting-up and configuring the trusted
instance in the VM at deployment. This includes net-
work address configuration, adding an initial set of
tokens, etc. The necessary contextualisation informa-
tion is provided in the service manifest, which is used
in OPTIMIS to allow a service provider or user to de-
scribe its requirements regarding the Cloud environ-
ment and the services provided by the infrastructure
provider.
The major benefit of using a trusted instance is
that the token does not need to be accessible by the
applications API where it potentially may be accessed
by a malicious user to replicate it. Rather, the trusted
instance provides an assertion to the API, which in-
cludes the content of the token. Another benefit in
terms of software development effort is that this ap-
proach does not require changes in the processing of
the authorisation in the API, because the only differ-
ence is the source of information, namely the trusted
instance instead of a local token file read by the API.
It only requires the implementation of a protocol that
retrieves the authorisation from the trusted instance.
Finally, multiple tokens can be generated in ad-
vance according to the requirements of the service to
be run in the Cloud and deployed with the trusted in-
stance during the contextualisation of the virtual ma-
chines for a service deployment. This reduces the
communication requirements during the service ex-
ecution time and re-contextualisation caused by miss-
ing tokens.
5 EVALUATION
Evaluation was organised in two phases. First, we
asked the commercial UK Cloud provider Flexiant
(a partner of the OPTIMIS project) to run a number
of test cases in their production infrastructure to test
and evaluate the implementation. The tests comprised
the license delegation (7 test cases), the trusted in-
stance (12 test cases). including integration tests and
tests that simulate users that on purpose or acciden-
tally messed around with license tokens. We also did
some measurements regarding the overhead in terms
of additional time needed (results are discussed be-
low). Second, the software was used in the Fortissimo
More.Cloud experiment
1
to realise a one-stop-shop
solution for simulations provided by an ISV. Here we
focused on the license delegation.
Summary of Results: The test cases passed with
the expected outcome with the exception of one inte-
gration test, which was only partly satisfied. The rea-
son for the failure was identified as an invalid config-
uration file which was fixed afterwards. The License-
Token validation checks successfully passed. Mul-
tiple cycles of the test cases were performed, each
yielding similar results and little deviation to the test
case result pattern. Overall, the test all cases passed
as expected.
1
Main Routing Architecture Optimisation Research Ex-
periment. MORE is aimed at reducing weight and cost for
wiring systems for complex products such as aircraft.
CLOSER 2016 - 6th International Conference on Cloud Computing and Services Science
270
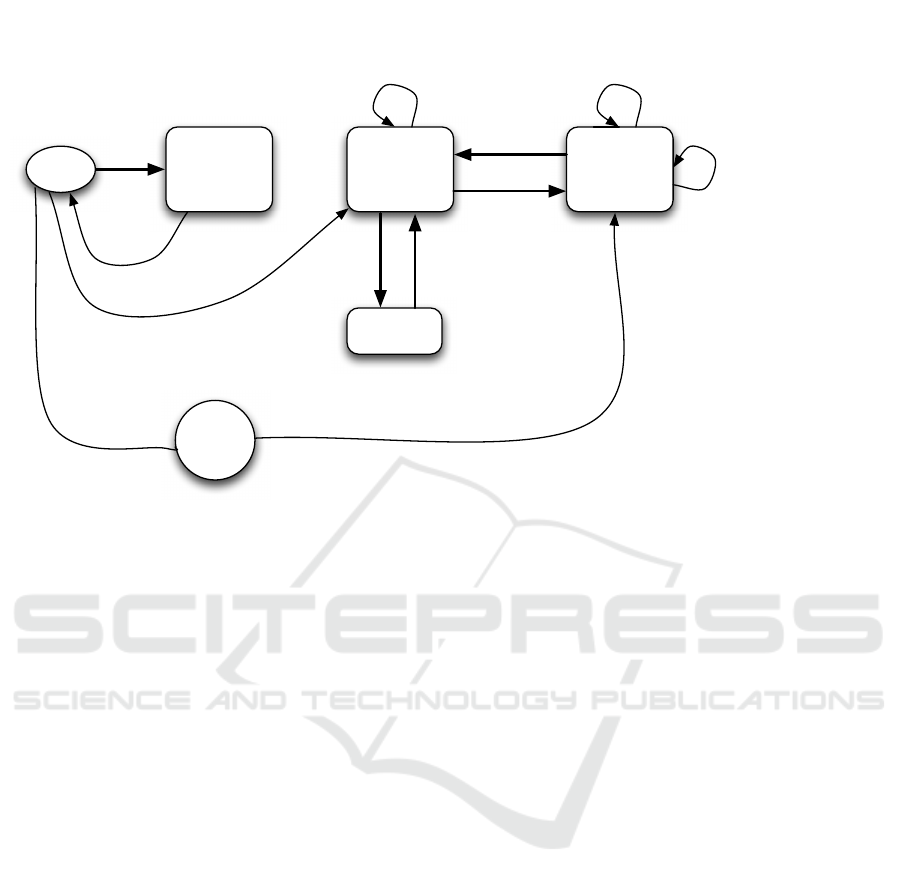
User
License
Service
Lsdl
Trusted
Instance
API
Cloud Info
Service
User
Author-
isation
Lsdl: Token request file
addToken
Token
Check User Authorizsation
- Select Token from Lsdl
- Get Execution Context
- Select Execution Authorization
Execution
Authorizsation
User
Authorizsation
Check User Authorisation
Validate & verfify
Execution Authorization
Execution Context
Lsdl
Cloud Info Service URL
Validity
Figure 4: Deployment of the Trusted Instance in a Cloud.
Incurred Overhead: Adding license tokens to a
VM is part of the contextualisation process that hap-
pens anyway. Thus there is no additional overhead. If
multiple license tokens are required (i) or if license to-
kens need to be created dynamically depending on the
outcome of applications in a workflow (ii) then for (i)
a VM with a trusted instance needs to be deployed or
for (ii) a license needs to be split at the license server
running at the user’s site, included through contextu-
alisation into a VM with a license server that is then
deployed to the Cloud as any other VM. The overhead
is in the range of about 3-5 minutes which is negligi-
ble since is happens only once and many (short) jobs
can be run afterwards using the license or license to-
kens deployed.
Risk of Fraud: The use of a trusted CA for cre-
ating the required certificates is essential to avoid at-
tacks on the level of the signatures. Of course, once
the code responsible for evaluating the validity of a to-
ken (the policy decision point, PDP) in the API of the
application, or the policy enforcement point in the ap-
plication that used the outcome of the PDP is hacked
the application may be used without limitation just as
with any other software licensing solution.
6 CONCLUSION
In this paper we described the work on software li-
censes and software license management done in the
European OPTIMIS project which is now used in
the European project Fortissimo. We introduced the
baseline technology taken from the European project
SmartLM which developed a licensing solution for
Grids. Based on this baseline two extensions have
been developed and implemented in OPTIMIS: the li-
cense delegation and the trusted instance. These ex-
tensions allow execution of license-protected applica-
tions in the Cloud without reducing the level of pro-
tection of the ISVs IPR. Furthermore, the token based
license management allows new business models like
pay-per-use where each token can be used as a secure
off-line authorisation for running an application and
account for exactly this execution without the need
to have an on-line connection to the license server at
run-time.
As a next step towards commercialisation of elas-
ticLM (elasticLM, 2015) we used it in a produc-
tive environment for simulations of aircraft wirings
in the European funded project Fortissimo (Fortis-
simo, 2016). A one-stop-shop solution for ISVs has
been developed allowing an ISV to offer its SME
customers the a customised infrastructure needed for
simulations in a Cloud environment. The offering
Leveraging Use of Software-license-protected Applications in Clouds
271

is based on a pay-as-you-go model that requests the
SME only to pay for resources (including temporary
licenses) actually required to perform the simulation
work needed for its business. The solution developed
in Fortissimo includes access to the Cloud resources
determined by the size of the problem, access to the
simulation application deployed in the Cloud, and dy-
namic access to the necessary software licenses to
run the simulation application. Currently elasticLM
is used in another productive environment for simula-
tions of metal sheet forming processes in the automo-
tive industry within the Fortissimo project.
The experiments in Fortissimo have proved that li-
cense server can easily installed in a virtual machine,
furnished with the licenses required for running soft-
ware in a contextualisation step, and deployed into an
arbitrary Cloud infrastructure: public, private, hybrid.
The software framework will now be made available
for download in the Fortissimo marketplace (Fortis-
simoMarketplace, 2015) and later - based on the ex-
perience in the Fortissimo Marketplace - also in the
AWS Marketplace (AWSmarketplace, 2016).
ACKNOWLEDGEMENTS
Some of the work reported in this paper has been
funded by the European Commissions ICT pro-
gramme in the FP7 project SmartLM under grant
#216759 and in the FP7 project OPTIMIS under grant
#257115.
REFERENCES
Armstrong, D., Djemame, K., Nair, S., Tordsson, J., and
Ziegler, W. (2011). Towards a Contextualization So-
lution for Cloud Platform Services. In 2011 IEEE
3rd International Conference on Cloud Computing
Technology and Science (CloudCom), pages 328–331.
IEEE.
AWSmarketplace (2016). Amazon Webs Services market-
place. Website. Online at https://aws.amazon.com/
marketplace, visited 31 January 2016.
BYOSL (2013). IBM Licensing for Amazon Cloud web
site. Website. Online at http://www-01.ibm.com/
software/passportadvantage/eligible
public cloud
BYOSL policy.html, visited 10 November 2015.
Dalheimer, M. and Pfreundt, F.-J. (2009). GenLM: License
Management for Grid and Cloud Computing Envi-
ronments. In Proceedings of the CCGrid conference
2009.
Dong, X., Wang, Y., Zheng, F., Guo, H., Yang, S., and Wu,
W. (2005). Floating license sharing system in grid en-
vironment. In SKG, page 96.
Dong, X., Wang, Y., Zheng, F., Qin, Z., Guo, H., and Feng,
G. (2006). Key techniques of software sharing for on
demand service-oriented computing. In GPC, pages
557–566.
elasticLM (2015). elasticLM - License as a Service (LaaS) .
Website. Online at http://www.elasticlm.com, visited
10 November 2015.
FLEXERA (2014). FlexNet Licensing. Website. Online
at http://www.flexerasoftware.com/products/flexnet-
licensing.htm, visited 10 November 2015.
FlexnetManager (2015). Flexera web site. Website.
Online at http://www.flexerasoftware.com/products/
flexnet-manager.htm, visited 10 November 2015.
Fortissimo (2016). Fortissimo - Enabling European Small
and Medium Enterprises (SMEs) in the manufac-
turing sector to benefit from high-performance dig-
ital simulation and modelling. Website. Online
at http://www.fortissimo-project.eu/index.html, vis-
ited 10 January 2016.
FortissimoMarketplace (2015). Fortissimo Market-
place. Website. Online at https://www.fortissimo-
marketplace.com/infopage/, visited 31 January 2016.
FU, W., XIAO, N., and LU, X. (2007). Sharing software
resources with floating license in grid environment.
In NPC ’07: Proceedings of the 2007 IFIP Inter-
national Conference on Network and Parallel Com-
puting Workshops, pages 288–294, Washington, DC,
USA. IEEE Computer Society.
Guofu, F., Yinfeng, W., Hua, G., and Xiaoshe, D. (2006).
Research on software license manager and sharing
system in grid. In GCCW ’06: Proceedings of the
Fifth International Conference on Grid and Cooper-
ative Computing Workshops, pages 35–38, Washing-
ton, DC, USA. IEEE Computer Society.
ITWM (2010). ITWM S4Cloud project. Website. On-
line at http://www.itwm.fraunhofer.de/presse-und-
publikationen/pressearchiv/pressearchiv-2010/04032010-
itwm-mit-wibu-systems-auf-der-cebit.html, visited 10
May 2015.
Katsaros, Gregory, A., Savvas, K., Dimosthenis, and Var-
varigou, T. (2009). Service Oriented License Pro-
viding. In Proceedings of IEEE International Con-
ference on Service-Oriented Computing and Applica-
tions (SOCA).
Kwok, S. H. and Lui, S. M. (2002). A license manage-
ment model for peer-to-peer music sharing. Interna-
tional Journal of Information Technology and Deci-
sion Making, 1(3):541–558.
Li, J., W¨adrich, O., and Ziegler, W. (2008). Towards sla-
based software licenses. pages 139–152.
Liu, Y., Yuan, C., and Zhong, Y. (2007). Implementing dig-
ital right management in p2p content sharing system.
In ICA3PP, pages 348–355.
MATLAB (2009). The MathWorks Enables MATLAB
Parallel Computing Tools to Run on the EGEE Grid.
Website. Online at http:// www.mathworks.com/
matlabcentral/fileexchange/21426-enhancing-e-
infrastructures-with-advanced-technical-computing–
parallel-matlab%C2%AE-on-the-grid, visited 10
November 2015.
CLOSER 2016 - 6th International Conference on Cloud Computing and Services Science
272

OPTIMIS (2013). OPTIMIS - Optimised Infrastructure
Services. Website. Online at http://www.optimis-
project.eu, visited 10 November 2015.
Raekow, Y., Simmendinger, C., and Kr¨amer-Fuhrmann, O.
(2009). License management in grid and high per-
formance computing. Computer Science, Research +
Development, 23(3-4):275–281.
S4Cloud (2015). Wibu S4Cloud project. Website. On-
line at http://www.wibu.com/data-security-research/
s4cloud.html, visited 10 November 2015.
Sentinel (2014). SafeNet Sentinel Cloud Services. Web-
site. Online at http://www.safenet-inc.com/software-
monetization/sentinel-cloud-services-overview/, vis-
ited 10 November 2015.
SmartLM (2011). SmartLM - Grid-friendly software licens-
ing for location independent application execution .
Website. Online at http://www.smartlm.eu, visited 10
November 2015.
Sullivan, F. . (2010). World Software Digital Rights Man-
agement Market. Technical Report N671-70.
vmware (2014). Flexera-VMWare cooperation. Web-
site. Online at http://www.flexerasoftware.com/
partners/licensing-entitlement-management-alliance-
partners.htm, visited 10 September 2015.
Leveraging Use of Software-license-protected Applications in Clouds
273
