
On the Use of CEP in Safety-critical Systems
Veronika Abramova
1
, Bruno Cabral
2
and Jorge Bernardino
1,2
1
Polytechnic Institute of Coimbra, ISEC - Coimbra Institute of Engineering, Coimbra, Portugal
2
University of Coimbra – CISUC, Centre for Informatics and Systems of University Coimbra, Coimbra, Portugal
Keywords: Safety-critical, CEP, Systems, Event Processing.
Abstract: Safety-critical systems have to continuously manage risks, in order to handle hazardous situations and still
be able to fulfil their purpose. While being composed by a variety of software, as well as hardware
components, it is necessary for each part of these systems, alone and as a whole, to exhibit a required set of
characteristics, necessary to ensure the correct system functioning. Complex Event Processing (CEP)
systems have been used in a diversity of applications and, while they focus on fast data gathering and
processing as well as in providing intelligence to their users, there is incomplete information about how they
are adequate to integrate safety-critical systems. In this paper we investigate if the mainstream off-the-shelf
CEP systems are suitable for safety-critical applications. We describe the use of complex event processing
engines in safety-critical systems and how some authors enhance those to better correspond to the critical
system requirements. We demonstrate that, although dependability is well handled in most CEP systems, the
same cannot be assumed about security and safety attributes.
1 INTRODUCTION
Safety-critical systems are projected and designed to
be used in avionics, medical devices, automotive
braking systems, nuclear power plant management,
flight management systems, chemical processes,
nuclear power plants and other potentially life
threatening systems, when failure in the system
endangers human lives directly or indirectly.
Therefore, these systems should be able to provide
the required safety functions and overall system
integrity (Knight, 2002). In order to be able to
mitigate the potential impact of hazardous situations,
safety-critical systems must be certified by a
regulatory agency to ensure their correct operation.
Consequently, it is important that systems in use are
reliable while it is possible to detect design and
functional problems. Also, those should be able to
meet some of the most important quality attributes,
such as dependability, reliability, safety and security
(Malm et al., 2011). It is important to mention that
those are complex systems, which are mostly build
using different operational modules and systems
combined together, such as Complex Event
Processing (CEP) systems. CEP systems have been
around for quite some time and have been constantly
tested, improved and developed (Mendes et al.,
2009). Due to the wide range of possible application
domains, CEP system capabilities have been
constantly improving over the past years. Figure 1
presents an example of a CEP system architecture –
ESPER.
Figure 1: ESPER architecture (Esper, 2016).
Currently they are used in a variety of software
systems as a customizable tool for data processing
and analysis. These systems have the ability to
completely adapt to the desired system purpose and
be able to process and present most important data,
based on previously defined rules. Therefore,
traditionally, CEP systems are part of more complex
systems, inside which they are used to process
102
Abramova, V., Bernardino, J. and Cabral, B.
On the Use of CEP in Safety-critical Systems.
DOI: 10.5220/0006308401020109
In Proceedings of the 2nd International Conference on Complexity, Future Information Systems and Risk (COMPLEXIS 2017), pages 102-109
ISBN: 978-989-758-244-8
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

incoming information, create alerts based on a
collection of rules, and posteriorly provide filtered
and summarized data to the final user (Eckert and
Bry, 2009). Consequently, those systems are focused
on information extraction and processing of
important data in real-time environments.
We investigate if current off-the-shelf CEP
systems are suitable for usage in safety-critical
applications, and are capable of performing designed
operations in the required (acceptable) time. As our
main contribution, we study some critical systems
that use CEP engines, as well the improvements that
were made to these CEP engines by some of the
authors. We start by identifying the key quality
attributes of safety-critical systems and use these to
study how some of the available systems manage
those requirements. This analysis allowed us to
identify different characteristics of CEP systems that
require more research.
The remainder of the paper is structured as
follows: section 2 presents the state of the art and
some of the application areas of CEP systems.
Section 3 describes some of the most important
quality attributes for safety-critical systems. Section
4 studies the usage of CEP in safety-critical
applications and Section 5 evaluates if those quality
attributes were considered by the authors and
describes possible gaps of usage of CEP in safety-
critical systems in some of the existent studies.
Finally, Section 6 presents our conclusions and
proposes some future research directions.
2 STATE OF THE ART
CEP systems have been used in a large number of
systems for data processing and alarm triggering.
Although our focus is on safety-critical applications,
in this section, to correctly assess the state-of-the-art,
we will also consider works reporting on the
application of complex event processing in other
areas.
For example, (Aidi, 2006) describes some of the
most common areas of application of complex event
processing systems, where these engines are capable
of exploring their full potential. The author presents
some of the key benefits brought by those systems.
A more focused study is performed by (Oracle,
2012) and (Aidi et al., 2006), who emphasize their
approach on financial area and propose solutions
using CEP engines. All of the authors state that CEP
systems have a high potential for processing data
when it arrives and are capable of providing data of
interest in a satisfactory amount of time. Since the
main goal of CEP is to be agile and efficient in data
presentation to the end user, (Cockburn, 2016),
(Schmidt et al., 2012) and (Ammon et al., 2009)
investigate the efficiency of those systems in alarm
triggering and alert management. These authors
present the advantages of CEP systems in those
cases and describe how those can be tuned to be able
to provide all the required information. Those
systems may be focused on alarms in dangerous
environments as well as noncritical businesses that
completely rely on getting information in time.
Therefore, (Daum et al., 2012) focused mainly on
BPM - Business Process Management Systems and
describe if CEP are capable of satisfying all the
requirements of those systems.
Healthcare is another highly important area that
could potentially take advantages of CEP systems.
(Wang et al., 2010) describe real-time healthcare
applications and state that CEP engines can
efficiently monitor patient behaviour and control
medical regulations. Similarly, (Foley and Churcher,
2009) and (Naqishbandi et al., 2015) propose
architecture solutions and required characteristics of
the systems using complex event processing in
healthcare domain. Authors state that CEP engines
are highly useful for large and critical data
processing and are capable of improving medical
systems.
Our work presents some of the available
solutions and studies, performed by other authors,
which focus on application of CEP engines in
safety-critical systems. We attempt describing some
of the systems developed by them and some of the
authors’ conclusions.
3 SAFETY-CRITICAL
REQUIREMENTS
While developing a safety-critical system there is a
wide range of standards that must be followed as
well as system requirements (Bowen and Stavridou,
2002). Those requirements may be also translated
into system quality attributes and define the system
characteristics without getting deep inside into its
functionalities. Currently software systems present,
in most cases, a long list of quality attributes
(Laranjeiro et al., 2015) and, therefore, we decided
to consider in this work the most general ones,
which are fundamental in safety-critical systems (see
Figure 2).
On the Use of CEP in Safety-critical Systems
103

Figure 2: Quality attributes.
We based our choice on the available standards and
attributes presented by (Barbacci et al., 1995),
(Sommerville, 2004), (Atoum and Bong, 2015).
Therefore, the considered quality attributes are:
Dependability. Can be directly translated into
trustworthiness of the developed system and
represents the confidence in the correct
functioning of its functions. One of the
dimensions of dependability is fault tolerance
that states that failure in a part of the system
cannot compromise the whole system. Also,
should be considered the repair capability of the
designed system, which describes if the system is
capable of recovering without any intervention,
as expected.
Security. Ensure that extracted, stored and
processed by the system data is not easily
intersected or corrupted. There should not be
intentional disruption by the third parties.
Authentication mechanism is also a requisite
since it allows user identification and extends up
to the possibility of the system to recognize the
configured devices and treat them as trusted. The
collected data will be recognized as viable
modifications and not by others. System
vulnerability should be reduced as much as
possible in order to prevent possible harm by
attackers and important data exposure.
Reliability. Describes the probability of the
system of performing designed operations in
expected time. This attribute is tightened with the
availability of the system that states that the
system should have the ability to work with
limited amount of data when it cannot be
collected. There should be available backup data
collectors that would gather at least part of the
necessary data. Therefore, reliability considers
not only software but hardware and firmware
modules that are required for correct system
functioning.
Safety. This is another quality attribute highly
related to the reliability. Thus, safety reflects the
system’s ability to operate, normally or
abnormally, without danger of causing human
injury or death and without damage to the
system’s environment. Some of related safety
terms are: hazard, damage and risk. All of those
are considered by the standards and usually are
described as a prevention list of measures instead
of qualities.
We believe that, among others, those are some of
the most important requirements of critical
software. Also, chosen attributes enclose other
vital software system characteristics, for example,
performance, resilience, availability, etc.
4 CEP IN SAFETY-CRITICAL
SYSTEMS
(Baldoni et al., 2015) proposed a solution that
combines Complex Event Processing (CEP) and
Hidden Markov Models (HMM) to analyse system
failures and their symptoms considering specifically
defined metrics. The anomalies conditions are
detected using the defined rules and creating alert
events. CEP provides all the necessary data as well
as performance metrics while HMM are used for
system state specification and recognition. Authors
state that it is important to be able to detect faults in
system components in order to be able to prevent the
entire system to be compromised. Hence, this work
proposes a failure prediction architecture, focused on
the traffic control systems, named CASPER.
Authors state that CASPER exhibits pretty good
accuracy and it is able to generate predictions with a
margin of time that allows recovery actions to
mitigate the upcoming occurrence of a failure of the
system.
Considering usage of CEP in different domains
and with increased interest in CEP systems, (Zappia
et al., 2012) describe the design and the
implementation of a lightweight and extensible
Complex Event Processing engine, called LiSEP.
During the system design specification, authors were
driven by the principle of minimizing dependency
on external software components and, therefore,
LiSEP depends solely on the Java Standard Edition
libraries, thus minimizing deployment requirements.
Moreover, the LiSEP logic is strictly focused on
core event processing, consequently resulting in a
lightweight and minimal implementation. The
proposed solution is complemented by the
specification of the Event Processing Language,
based on the SQL syntax. As a proof of the
architecture, authors propose experimenting the use
of the LiSEP engine in a case study on dangerous
goods monitoring during maritime transport as a part
COMPLEXIS 2017 - 2nd International Conference on Complexity, Future Information Systems and Risk
104

of Italian Ministry for Economic Development
research project, called SITMAR - Integrated system
for goods maritime transport in multi-modal
scenarios. More data-focused approach is presented
by (Evchina and Lastra, 2016). This work aims
aiding end users of monitoring systems by delivering
selected information to each user based on their role
in the system. The proposed approach combines
Semantic Web (SW) technologies and Complex
Event Processing (CEP) for configuration purposes
and run-time data processing and analysing. Authors
state that final developed solution should be able to
provide ways to deal with multiple devices and
multiple users of the system; should be
reconfigurable to reflect changes in the environment
and/or user information needs; and finally, the
device updates should be delivered to users within
reasonable amount of time. Considering those
requirements, the developed approach provides two
major advantages. Firstly, the behaviour of the
system could be easily changed by configuring only
underlying ontology and, secondly, CEP usage at
runtime makes system event-driven and reactive to
frequent changes in the environment.
(Itria et al., 2014) present an approach for critical
situation detection that uses CEP architecture for
real time event analysis as well as event correlation.
While event analysis consists of data processing,
event correlation corresponds to establishing a
relation between input events that were gathered
from various sources, for detecting patterns and
situations of interest in the emergency management
context. This solution describes the engine,
developed in the context of the Secure! Project
(Secure, 2016). That solution has two main
requirements: the correlation module has to be
adaptable to the possible changes of the source
environment, and it has to process available
historical data in order to evaluate the actual events
considering also what has happened before. After
submitting the system for testing, authors state that
their approach can be easily used and maintained. It
is also extensible to other scenarios where the
application requires nearly real-time correlation, like
intrusion detection system (Ficco and Romano,
2011) and monitoring of critical infrastructures.
Solution for power grid monitoring using CEP is
presented by (Cerullo et al., 2014). Authors claim to
be able to provide a detailed treatment of the
security issues resulting from the adoption of
Wireless Sensor Networks and QoS-enabled IP
connections. The proposed solution attempts
enhancing current information security and event
management technology, by improving its capability
of detecting and mitigating attacks targeting the
heterogeneous network infrastructure. As an
example, in power grid scenario, the attacker may
prevent some nodes from sending events to the
connected collector, thus hiding changes in the
power grid conditions. The WSN security probe
generates alarms based on the analysis of the
network and periodically calculates the package
generation rate at every node and the developed
engine is capable of correlating those alarms to
protect the visualization server. (Wang and Kuang,
2015) propose a traffic prediction method based on
Predictive Complex Event Processing (PreCEP) and
Bayesian networks to improve the prediction
accuracy. The prediction model is trained with
historical data and it is used to predict future events
based on the recent output of basic CEP engine.
Authors address the prediction problem for moving
objects that can be vehicles or even pedestrian and
conclude that the performance of PreCEP still needs
to be improved. Currently the parallel method only
works when learning the structure of models and
training models for different context.
Cloud platform monitoring system, JTangCMS -
JTang Cloud Monitoring System, is proposed by (Lu
et al., 2016). Authors claim that proposed solution
can deal with the flexibility, scalability, efficiency
and performance challenges of cloud monitoring.
The system gathers all the data using dissemination
framework that allows transferring huge amount of
runtime information with high throughput and low
latency using DDS - Data Distribution Service
which partitions the input into smaller parts. After
transferring all the data, it has to be analysed and,
therefore, was developed a decision-making support
system using CEP, named JTangCMS. Performed
evaluations of the implemented algorithm and DDS-
based data delivery system state that JTangCMS is
efficient solution and does support intelligent
decision making. In (Li et al., 2013) authors propose
the overall structure and workflow for a CEP-based
monitoring system, which can be applied to a private
cloud to alert system failures.
(Bruns et al., 2014) proposed ambulance
coordination architecture that provides real-time data
processing and deliver comprehensive data to the
end users. The developed architecture consists of
two core components: CEP and FSM- Finite State
Machines. CEP focuses on gathering and analysis of
the sensor data streams, emitted by the ambulance in
order to automatically detect changes of the
operational states defined in the FSM. Authors
defend that efficient and fast patient care requires
reliable and up to date information and, therefore,
On the Use of CEP in Safety-critical Systems
105

present an approach that determines the actual state
of all ambulances as well as possible relevant
mission incidents. Presented solution attempts
completing research of (Brotcorne et al., 2003), (Li
et al., 2011), (Ciampolini et al., 2004). (Zappia et al.,
2014) also present patient related data and usage of
CEP systems in healthcare area. The goal is to use
RFID technology to be able to support clinical
management of the patients. Proposed solution is
focused mainly on the following scenarios: patient
identification and tracking, and drug administration.
The proposed distributed system is based on event
abstraction, event aggregation and event
transformation, and uses those to offer a hierarchical
and distributed data processing architecture where
CEP used data is provided by different processing
nodes. Overall, the projected solution, based on CEP
and RFID technologies, is used to support clinical
risk management by means of detecting possibly
dangerous patient conditions as well as patient take
care. Solution for critical situation detection in
elderly daily life is proposed by (Xu et al., 2014).
Authors focus their study on personal assistance as
well as possible risks and identification of the
required assistance situations. These situations are
detected by analysing data received from the
sensors. This study is focused on ALL – Ambient
Assisted Living technologies and uses sensors to
monitor welfare parameters and environmental
conditions as described by (Wolf et al., 2009).
Another RFID solution is proposed by (Yao et
al., 2011). Authors propose an RFID framework,
using CEP, for managing hospital data, gathered
from different sources, and try detecting patterns and
medically significant events. Therefore, authors
created prototypes that attempt showing that CEP
has the ability of providing alerts to the healthcare
professionals as well as increasing quality of
healthcare and patient safety. One of the main goals
consists of identifying the patient and tracking all
the necessary procedures since there may be
mistakes from part of the hospital staff. Also, the use
of the system provides all the necessary historical
data for emergency handling as well as for health
problems and medication identification and
response. All of those characteristics show that this
approach may reduce errors as well as provide faster
and more efficient risk management.
CEP scaling solution for processing CPS -
Cyber-Physical System data (Ollesch, 2016) uses
elevator example to describe the challenges of CEP
technology in a CPS context. One of the main
aspects is the calculation of the floor, since it may be
calculated wrongly as well as the sensors themselves
are subject to errors and can be disturbed (in the
example was considered the use of Kinect sensor)
since, for example, passengers would obstruct the
Kinect sensor. CEP systems are based on rules and
using this example was possible to proof that some
parts of the system design should be adjusted.
Considering Esper system (Esper, 2016) as example,
its rules are embedded inside program code and
cannot be externalized. Consequently, each change
affects the source code of the CEP application. In
particular, (Wang et al., 2014) also study Esper as
example and define the event process functions, like
event attribution extraction and composition
determination. Authors investigate the challenges in
designing a CEP method for Cyber-Physical System,
and propose a semantic enhancement CPS event
model. (Balogh et al., 2016) propose a conceptual
architecture for system monitoring that ensures the
correct behaviour of the system considering a set of
different monitoring rules. It was developed a
prototype using the VIATRA-CEP Event Processing
Language (Viatra, 2016). Posteriorly monitoring
rules are distributed over the nodes. System
evaluation was based on development and
monitoring of safety-critical embedded systems in
the railway domain.
(Beer and Heindl, 2007) overview the state of art
in testing dependable event-based systems and
identify the challenges that have to be addressed in
the future. Authors consider two case studies during
their testing: large-scale project for business-unit
transportation systems and a small-scale
telecommunications project for AIRBUS. Authors’
main focus is on testing and they state that it is an
important topic and cost reduction of testing may be
achieved by developing new and more efficient
techniques of requirements tracing as well as test-
case design and validation. Authors based part of
their work on (Luckham, 2002) who proposed CEP
usage for managing multiple events and event
causality in order to elicit meaningful events in an
event-based information system. This is because
CEP can analyse incoming data and transform it into
out coming events. (Lang and Capík, 2014) present a
procedure for performing predictive analysis of
complex events occurrence in time critical complex
event processing systems. Similarly, to (Tendick et
al., 2016), authors state that using CEP it is possible
to identify and apply business intelligence rules over
the streams of events and this technology is critical
in an environment where time plays an important
role, such as, real time decision making. Authors
analyse the possibilities and use of the available
methods and techniques for classification and
COMPLEXIS 2017 - 2nd International Conference on Complexity, Future Information Systems and Risk
106
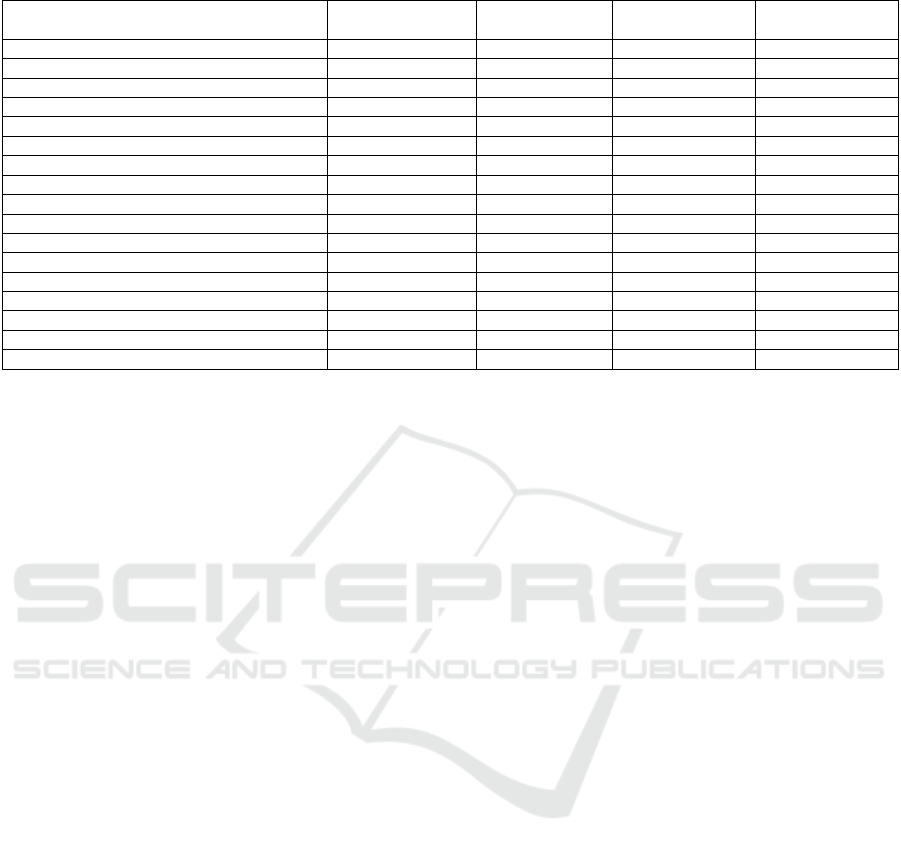
Table 1: Quality attributes.
Dependability
Reliability
Security
Safety
(Baldoni et al., 2015
X
X
(Zappia et al., 2012)
X
(Evchina and Lastra, 2016)
X
X
(Itria et al., 2014)
X
(Cerullo et al., 2014)
X
X
(Wang and Kuang, 2015)
X
(Lu et al., 2016)
X
X
(Li et al., 2013)
X
X
(Bruns et al., 2014)
X
(Zappia et al., 2014)
X
(Xu et al., 2014)
X
(Yao et al., 2011)
X
(Ollesch, 2016)
X
(Wang et al., 2014)
X
(Balogh et al., 2016)
X
(Beer and Heindl, 2007)
X
(Lang and Capík, 2014)
X
prediction in complex event processing. For this
purpose, it was designed and implemented an
application CepPredictiveAnalysis, which uses
defined methods for predictions and despite certain
limitations, the system gives acceptable accuracy in
financially-oriented applications.
Over the next section we present our analysis of
the described solutions, concerning previously stated
quality attributes.
5 REQUIREMENTS ANALYSIS
After briefly describing the considered quality
attributes in Section 2, we consider that it is
important to confirm whether described systems and
solutions of CEP systems in safety-critical
applications consider any of those.
The summary of quality attributes analysis is
presented in Table 1. It is important to notice that
some of the solutions may have partially addressed
some of the quality attributes, but we just consider
overall approach and the authors focus and goals in
the designed architecture.
The summary of quality attributes analysis is
presented in Table 1. It is important to notice that
some of the solutions may have partially addressed
some of the quality attributes, but we just consider
overall approach and the authors focus and goals in
the designed architecture.
After analysing the results, we concluded that
most of the systems are focused on their
performance and operability and do not consider
safety neither security. Those quality attributes are
often considered less important than assuring system
proper functioning or performance. Most of the
authors, as expected, consider the proper functioning
of their systems and focus on Dependability and
Reliability attributes. Those are more functional
characteristics and any designed and developed
system is expected to work as intended. Some of the
authors consider how their system is affected by
security attributes and if their data is secure and only
one study considers risk and hazardous situations
management and system awareness of those. It is
important to notice that we performed our analysis
of quality attributes based on authors’ description
and designed system specifications.
Though, some of the described works may
provide parts of considered by us quality attributes,
but those were not mentioned. Also, although we
just have one level analysis, as previously stated, we
investigated authors’ main focus and what their
work was trying to achieve.
6 CONCLUSIONS AND FUTURE
DIRECTIONS
Safety-critical systems are necessary to perform
critical operations if safe environment that will not
endanger any life or property. Thus, those systems
should be carefully designed and have a set of
qualities and characteristics that would attempt
ensuring their proper functioning. In this paper we
present some of the most important studies that
incorporate the use of CEP engines in software-
critical systems. We describe performed studies and
some of the authors main goals and conclusions.
After considering the main system characteristics
On the Use of CEP in Safety-critical Systems
107

and quality attributes we attempt investigate which
of those are considered in the selected
investigations.
We conclude that there are some characteristics,
which are highly important, that are not considered
by all the authors. Those may have high impact
while dealing with critical data as well when
processing received information. Both safety and
security are focused on providing correct system
data by concerning authenticity of the received
information, system components safekeeping. Our
goal was to analyse some of the available solutions
of application of CEP engines in safety-critical
environments and describe some of the most
common areas where those are used. We believe that
there are still some system characteristics that have
not been fully covered by existing works and we
presented two of those, namely, safety and security.
After concluding our research and while
considering the results, we believe that security and
safety are equally important quality attributes and
have been neglected by some of the available
solutions. Therefore, as our future research direction,
we will investigate some of the mechanisms that
should be considered in safety-critical systems and
that would provide necessary system safety.
Currently, there are some protection mechanisms
that are already used by most of the developed
systems, such as, authentication, data encryption,
safe connections, hardware authentication and
register, etc. As future work we consider
investigating methods from which safety-critical
systems could benefit and that would not
compromise systems performance.
REFERENCES
Aidi, A. 2006. Complex Event Processing. IBM Haifa
Labs.
Aidi, A., Botzer, D., Nechushtai, D., Sharon, G. 2006.
Complex Event Processing for Financial Services.
Services Computing Workshops, 2006. SCW '06.
IEEE.
Ammon, R., Emmersberger, C., Springer, F., Wolff, C.
2009. Event-Driven Business Process Management
and its Practical Application Taking the Example of
DHL.
Atoum, I., Bong, C. 2015. Measuring Software Quality in
Use: State-of-the-Art and Research Challenges.
Measuring Software Quality in Use: State-of-the-Art
and Research Challenges.
Baldoni, R., Montanari, L., Rizzuto, M. 2015. On-line
failure prediction in safety-critical systems. Future
Generation Computer Systems 45 (2015) 123–132.
Balogh, L., István, D., István, R., Dániel, V., András, V.
2016. Distributed and Heterogeneous Event-based
Monitoring in Smart Cyber-Physical Systems.
Barbacci, M., Longstaff, T., Klein, M., Weinstock, C.
1995. Quality Attributes. Software Engineering
Institute Carnegie Mellon University. Technical
Report CMU/SEI-95-TR-021; ESC-TR-95-021.
Beer, A., Heindl., M. 2007. Issues in Testing Dependable
Event-Based Systems at a Systems Integration
Company. Second International Conference on
Availability, Reliability and Security (ARES'07).
Bowen, J., Stavridou, V. 2002. Safety-Critical Systems,
Formal Methods and Standards. Software
Engineering Journal 8(4).
Brotcorne, L., Laporte, G., Semet, F. 2003. Ambulance
location and relocation models. European journal of
operational research, vol. 147, no. 3, pp. 451–463.
Bruns, R., Dunkel, J., Billhardt, H., Lujak, M., Ossowski,
S. 2014. Using Complex Event Processing to Support
Data Fusion for Ambulance Coordination. Information
Fusion (FUSION), 2014 17th International
Conference.
Cerullo, G., Formicola, V., Iamiglio, P., Sgaglione, L.
2014. Critical Infrastructure Protection: having SIEM
technology cope with network heterogeneity.
Ciampolini, A., Mello, P., Storari, S. 2004. A multi-agent
system for medical services synergy and coordination.
in International ECAI 2004 workshop on Agents
applied in health care, J. Nealon, U. Cortes, J. Fox,
and A. Moreno, Eds., p. 3846.
Cockburn, D. 2016. Dealing with Quality Defects and
Rapid Alerts. Available at: http://www.emAmmona.
europa.eu/docs/en_GB/document_library/Presentation/
2009/12/WC500017884.pdf.
Daum, M., Götz, M., Domaschka, J. 2012. Integrating
CEP and BPM: how CEP realizes functional
requirements of BPM applications. DEBS '12
Proceedings of the 6th ACM International Conference
on Distributed Event-Based Systems. Pages 157-166.
Eckert, M. and Bry, F. 2009. Complex Event Processing.
German language in Informatik Spektrum, Springer
2009.
Esper. 2016. http://www.espertech.com/products/esper.
php.
Evchina, Y., Lastra, J. L. 2016. Hybrid approach for
selective delivery of information streams in data
intensive monitoring systems. Advanced Engineering
Informatics 30 (2016) 537–552.
Ficco, M., Romano, L. 2011. A generic intrusion detection
and diagnose system based on complex event
processing. Proceedings on the 1st International
Conference on Data Compression, Communication,
and Processing, p. 275-284.
Foley, J., Churcher, G.E. 2009. Applying Complex Event
Processing and Extending Sensor Web Enablement to
a Health Care Sensor Network Architecture.
Conference: Proceedings of the 4th International
Conference on COMmunication System softWAre and
MiddlewaRE (COMSWARE 2009).
COMPLEXIS 2017 - 2nd International Conference on Complexity, Future Information Systems and Risk
108

Itria, M.L., Daidone, A., Ceccarelli, A. 2014. A Complex
Event Processing Approach for Crisis-Management
Systems. EDCC Workshop Big4CIP.
Knight, J. C. 2002. Safety critical systems: challenges and
directions. Proceedings of the 24th International
Conference on Software Engineering, ICSE '02. Pages
547-550.
Lang, J., Capík, Z. 2014. Prediction based on hybrid
method in complex event processing. SAMI 2014.
IEEE 12th International Symposium on Applied
Machine Intelligence and Informatics, January 23-25,
2014. Herl’any, Slovakia.
Nuno Laranjeiro, Seyma Nur Soydemir, Jorge Bernardino:
A Survey on Data Quality: Classifying Poor Data. 21st
IEEE Pacific Rim International Symposium on
Dependable Computing, PRDC 2015, Zhangjiajie,
China, pp. 179-188.
Li, L., Cao, B., Liu, Y. 2013. A study on CEP-based
system status monitoring in cloud computing systems,
in: 2013 6th International Conference on Information
Management, Innovation Management and Industrial
Engineering, 1, pp. 300–303.
Li, X., Zhao, Z., Zhu, X., Wyatt, T. 2011. Covering
models and optimization techniques for emergency
response facility location and planning: a review.
Mathematical Methods of Operations Research, vol.
74, no. 3, pp. 281–310.
Lu, X., Yin, J., Xiong, N., Deng, S., He, G., Yu, H. 2016.
JTangCMS: An efficient monitoring system for cloud
platforms. Information Sciences 370–371 (2016) 402–
423.
Luckham, D. 2002. The Power of Event, Addison Wesley.
Malm, T., Vuori, M., Rauhamäki, J., Vepsäläinen, T.,
Koskinen, J., Seppälä, J., Virtanen, H., Hietikko, M.,
Katara, M. 2011. Safety-critical software in machinery
applications. VTT, Espoo, Finland.
Massimiliano, L. I., Daidone, A., Ceccarelli, A. 2014. A
Complex Event Processing Approach for Crisis-
Management Systems.
Mendes, M., Bizarro, P. and Marques, P. 2009. A
Performance Study of Event Processing Systems.
Volume 5895 of the series Lecture Notes in Computer
Science pp 221-236.
Naqishbandi, T., Sheriff, I., Qazi, S. 2015. Big Data, CEP
and IoT: Redefining Holistic Healthcare Information
Systems and Analytics. International Journal of
Engineering Research & Technology (IJERT). Vol. 4
Issue 01.
Ollesch, J. 2016. Doctoral Symposium: Adaptive Steering
of Cyber-Physical Systems with Atomic Complex
Event Processing Services. DEBS ’16 June 20 - 24,
2016, Irvine, California, USA.
Oracle. 2012. Financial Services Data Management: Big
Data Technology in Financial Services. An Oracle
White Paper.
Secure. 2016. Secure! Project, http://secure.eng.it/.
Schmidt, K., Anicic, D., Stuhmer, R. 2012. Event-driven
Reactivity: A Survey and Requirements Analysis.
Sommerville, I. 2004. Software Engineering (7th Edition).
Pearson Addison Wesley ©.
Tendick, P., Denby, L., Ju, W. 2016. Statistical methods
for complex event processing and real time decision
making. WIREs Comput Stat 2016, 8:5–26.
Viatra. 2016. VIATRA-CEP Documentation.
https://wiki.eclipse.org/VIATRA/CEP.
Wang, D., Rundensteiner, E., Wang, H., Ellison, R. 2010.
Active complex event processing: applications in real-
time health care. Proceedings of the VLDB. Volume 3
Issue 1-2, September 2010, Pages 1545-1548.
Wang, Y., Kuang, L. 2015. Traffic prediction method
based on complex event processing and adaptive
bayesian networks. The 2015 International Academic
Research Conference, 3-6 August, University of
London.
Wang, Y., Zhou, X., Shan, L., Miao, K. 2014. Study on
Complex Event Processing for CPS: An Event Model
Perspective.
Wolf, P., Schmidt, A., Klein, M. 2009. Applying Semantic
Technologies for Context-Aware AAL Services: What
we can learn from SOPRANO In: Workshop on
Applications of Semantic Technologies 09.
Xu, Y., Wolf, P., Stojanovic, N., Happel, H. 2014.
Semantic-based Complex Event Processing in the
AAL Domain. Mechatronic and Embedded Systems
and Applications (MESA), IEEE/ASME 10th
International Conference.
Yao, W., Chu, C., Li, Z. 2011. Leveraging complex event
processing for smart hospitals using RFID. Journal of
Network and Computer Applications, 34 (2011) 799–
810.
Zappia, I., Paganelli, F., Parlanti, D. 2012. lightweight and
extensible Complex Event Processing system for sense
and respond applications. Expert Systems with
Applications 39 (2012) 10408–10419.
Zappia, I., Ciofi, L., Paganelli, F., Iadanza, E., Gherardelli,
M., Giuli, D. 2014. A distributed approach to Complex
Event Processing in RFID-enabled hospitals. Euro
Med Telco Conference (EMTC).
On the Use of CEP in Safety-critical Systems
109
