
Establishing Trust in Cloud Services via Integration of Cloud Trust
Protocol with a Trust Label System
Vincent C. Emeakaroha
1
, Eoin O’Meara
2
, Brian Lee
2
, Theo Lynn
3
and John P. Morrison
1
1
Irish Centre for Cloud Computing and Commerce,
University College Cork, Cork, Ireland
2
Irish Centre for Cloud Computing and Commerce,
Athlone Institute of Technology, Athlone, Ireland
3
Irish Centre for Cloud Computing and Commerce,
Dublin City University, Dublin, Ireland
Keywords:
Cloud Trust Label, Cloud Trust Protocol, Cloud Monitoring, Quality of Service, Service Level Agreement,
Cloud Computing.
Abstract:
Cloud computing has transformed the computing landscape by enabling flexible compute-resource provision-
ing. The rapid growth of cloud computing and its large-scale nature provide many advantages to business
enterprises. Lack of trust in cloud services however remains a major barrier to the adoption of cloud comput-
ing. Trust issues typically relate to concerns about the location, protection and privacy of data. The concept of
trust includes trust in both novel technologies and cloud service providers and is composed of both persistent
and dynamic trust elements. We have previously developed a trust label system that is capable of facilitating
both persistent and dynamic trust building in both cloud services and cloud service providers; however, it
lacks reliable information delivery mechanisms. The Cloud Trust Protocol (CTP) aims to provide a reliable
information communication system for cloud service consumers and thus offers a natural complement to the
trust label system by providing a reliable and interoperable information exchange mechanism. In this paper,
we propose a novel integration of the trust label system with CTP to provide end-to-end visibility of cloud
service operational information to consumers.
1 INTRODUCTION
The adoption of cloud computing is growing at such
rates that some analysts forecast public IT cloud ser-
vices will account for more than half of worldwide
software, server, and storage spending growth by
2018 (Gens, 2014). Highly scalable, shared and dis-
tributed infrastructure that can be rapidly deployed
at arms-length can accrue many business benefits,
not least quicker response times to customer require-
ments, work efficiencies, and reduced IT costs (Buyya
et al., 2009; Hogan et al., 2011; Low et al., 2011).
Unsurprisingly, enterprises are attracted by the com-
bination of IT efficiencies and business agility that the
cloud computing model can offer (Kim, 2009).
Despite the widely reported benefits of cloud com-
puting, lack of trust in cloud services remains a ma-
jor barrier to its adoption. Such trust issues typically
relate to concerns about the location, protection and
privacy of data in storage, in transit and while being
processed in the cloud. However, these issues con-
sist of a wider class of security concerns including
increased vulnerabilities relating to virtualisation, au-
thentication and identification, web application and
network security (Leimbach et al., 2014; Bradshaw
et al., 2012; Subashini and Kavitha, 2011; Pearson
and Benameur, 2010). The concept of trust in com-
puting is complex. It involves trust in both a novel
technology and external cloud service providers and
is composed of both persistent and dynamic trust el-
ements (Lynn et al., 2016; Pearson and Benameur,
2010). The global and distributed nature of the cloud
exacerbates trust issues by introducing a lack of clar-
ity on the identity and role of various actors within the
chain of service provision, their associated responsi-
bilities, and potential liabilities in the event of service
failure.
Given these challenges, various mechanisms have
been proposed for introducing accountability and as-
surance (Pearson and Benameur, 2010; Lynn et al.,
2013; Zissis and Lekkas, 2012; Pearson, 2013) in
an effort to address trust issues but they suffer lim-
590
Emeakaroha, V., O’Meara, E., Lee, B., Lynn, T. and Morrison, J.
Establishing Trust in Cloud Services via Integration of Cloud Trust Protocol with a Trust Label System.
DOI: 10.5220/0006362906180625
In Proceedings of the 7th International Conference on Cloud Computing and Services Science (CLOSER 2017), pages 590-597
ISBN: 978-989-758-243-1
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

itations, such as lack of dynamism. Previously,
the authors have presented a validated trust label
to collate and communicate trust in both cloud ser-
vices and cloud service providers (Lynn et al., 2016;
Emeakaroha et al., 2016; Masevic et al., 2016). The
trust label system facilitates both persistent and dy-
namic trust building in cloud services and cloud ser-
vice providers; however, it assumes reliable informa-
tion delivery mechanisms are in place to communi-
cate the required data to populate the interface.
The Cloud Trust Protocol (CTP) (Cloud Security
Alliance, 2015a) is a recent initiative by the Cloud
Security Alliance (CSA). It aims to provide a reliable
information communication system for cloud service
consumers to ask for and receive information about
essential security configuration and operational char-
acteristics as applied to cloud service providers. As
such the CTP provides a natural complement to the
trust label system by providing a reliable and inter-
operable information exchange mechanism. In this
paper, we propose a novel integration of the trust la-
bel system with CTP to provide end-to-end visibil-
ity of cloud service operational information to con-
sumers. This is facilitated by the implementation of
a robust bridge library. Based on a use case scenario,
we demonstrate the efficiency of the integrated sys-
tem.
The rest of the paper is organised as follows: Sec-
tion 2 discusses the challenges and presents some
background information on the trust label system and
CTP. In Section 3, we detail the system integration
and describe the supporting components. Section 4
describes the implementation choices and the realisa-
tion of the system while Section 5 presents its evalu-
ation. In Section 6, we discuss related work and con-
clude the paper in Section 7.
2 BACKGROUND
This section discusses trust-related challenges in
cloud computing and how trust labels and the Cloud
Trust Protocol purport to address these challenges.
2.1 Challenges
There is a well-established literature base on the im-
portance of trust as a determining factor in the accep-
tance and use of online technologies (Gefen, 2003;
Pavlou and Gefen, 2004; Mcknight et al., 2011; Bente
et al., 2012). Similarly, in the cloud computing con-
text, lack of trust has been consistently identified as
a major barrier in the adoption of cloud computing
in both academic and professional literature (Hwang
and Li, 2010; Bradshaw et al., 2012; Leimbach et al.,
2014). Trust is commonly defined as a “....psycho-
logical state comprising the intention to accept vul-
nerability based on positive expectations of the inten-
tions or behavior of another” (Rousseau and Sitkin,
1998). In the context of information technology, the
object of our trust is not necessarily a human person
but a technology artefact and/or the provider of that
artefact (McKnight and Chervany, 2001). Similarly,
stakeholder expectations in relation to trusting tech-
nology are different, focussing on functionality, re-
liability and helpfulness in an IT context (Mcknight
et al., 2011). The nature of cloud computing exacer-
bates issues of trust in many different ways, primar-
ily by increasing perceived risk. Cloud computing in-
volves an element of outsourcing of system and/or in-
frastructure to a third party on a shared distributed ba-
sis. As such, in adopting cloud computing, stakehold-
ers face relational, performance, and regulatory and
compliance risks. Relational risk is concerned with
risk associated with poor cooperation and opportunis-
tic behaviour while performance risk relates to op-
erational or performance factors that may undermine
the success of an outsourcing project (Das and Teng,
1996). Compliance and regulatory risk is concerned
with the end-consumer failure to adhere to regulatory
standards because of provider errors (Anderson et al.,
2014). These high-level risks surface in commonly
cited practical concerns relating to data jurisdiction
and location, security and data protection, and porta-
bility and technology transparency (Bradshaw et al.,
2012; Pearson and Benameur, 2010).
In cloud computing, trust issues are typically ad-
dressed through contracting (Pearson and Benameur,
2010). As cloud computing involves both persistent
trust (trust in the long term underlying properties or
infrastructure) and dynamic trust (trust specific to cer-
tain states, contexts, or short-term or variable infor-
mation), parties to cloud computing contracts seek to
minimise their risk by relying on both a general con-
tract and a service level agreement.
While contracting may reduce risk and distrust,
it does not necessarily build trust in the same way
that trust mechanisms based on experience between
parties or with a service might (Lewicki and Bunker,
1996; Deitz and DenHartog, 2006).Lynn et al. (Lynn
et al., 2013) propose a dynamic trust label to en-
able and maintain consumer trust in cloud services.
Similar to a food nutritional label, they argue such a
trust label for cloud computing would work by suc-
cinctly communicating up-to-date values for a num-
ber of high-level dependability measures generated
from the underlying cloud service. Using an online
adaptation of the Delphi conference method, Lynn et
Establishing Trust in Cloud Services via Integration of Cloud Trust Protocol with a Trust Label System
591
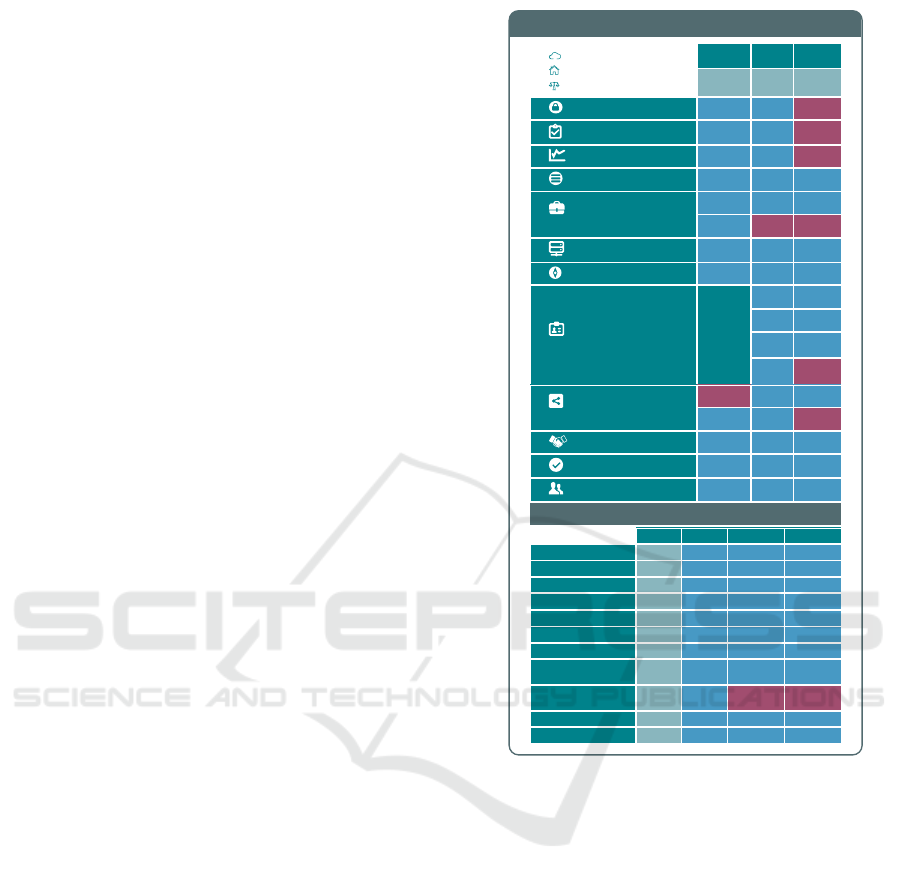
al. (Lynn et al., 2016) identified the information re-
quired for the label from a panel of 28 industry ex-
perts. Figure 1 presents a graphical view of the trust
label interface. It comprises 81 information compo-
nents, covering the cloud service provider (e.g. physi-
cal location, legal jurisdiction), the cloud service itself
(e.g. data location, security, backup, certification),
and a historical service-level summary (e.g. uptime
data, support response times).
2.2 Trust Label System
Emeakaroha et al. (Emeakaroha et al., 2016) present
the underlying trust label system as shown in Figure
1. The historic service-level summary, in particular,
is based on a monitoring framework that is capable of
monitoring the different cloud layers and presenting
service-level data to the trust label in real time. Ma-
sevic et al. (Masevic et al., 2016) report that the pro-
posed trust label performed as hypothesised in valida-
tion experiments with a sample of 227 potential cloud
consumers.
2.3 Cloud Trust Protocol
As mentioned earlier, the Cloud Trust Protocol (CTP)
(Cloud Security Alliance, 2015a) is a protocol, de-
signed by the Cloud Security Alliance (CSA), to gen-
erate evidence-based confidence that everything that
is claimed to be happening in the cloud is indeed hap-
pening as described. The CTP is a means by which
cloud service consumers ask for and receive informa-
tion about the elements of transparency, i.e. important
pieces of information concerning the compliance, se-
curity, privacy, integrity, and operational security his-
tory of service elements being executed in the cloud.
It aims to enable user confidence in the security and
performance capabilities of cloud services both when
choosing a service or continually monitoring a service
to validate its agreed SLAs.
As such CTP provides evidence to build dynamic
trust in cloud services in the vei if Pearson and
Benameur (Pearson and Benameur, 2010) Figure 2
shows an overview of CTP deployed in a multi-cloud
service provider environment. CTP presents a stan-
dardised unified API that is designed to be a RESTful
protocol. The APIs are used by consumers to query
cloud service providers for information relating to a
particular service.CTP provides the information to be
queried using a standardised data model that can be
adapted to various scenarios that implement or intend
to use CTP.
New Company Ltd
Cloud Services
Sacramento, USA
California, USA
Performance
Policy
Preference
Can I
measure ?
Is there a
policy ?
Can I
modify ?
Data Security
YES
YES
NO
Certification
YES
YES
NO
Service Levels
YES
YES
NO
Variation of Terms
YES
YES
YES
Data Portability
Onboard
YES
YES
YES
Offboard
YES
NO
NO
Backup of Data
YES
YES
YES
Data Location
YES
YES
YES
Ownership
Data
N/A
YES
YES
Meta Data
YES
YES
Service
Customisation
YES
YES
Application
Customisation
YES
NO
Sharing of Data
Commercial
NO
YES
YES
Legal
YES
YES
NO
Insurance Levels
YES
YES
YES
Audit Approvals
YES
YES
YES
Customer Service Level
YES
YES
YES
Service Level Summary
Target
Current
3-Month
12-Month
Service Uptime
100%
100%
100%
100%
Internal Network Uptime
100%
100%
100%
100%
External Network Uptime
100%
100%
100%
100%
Dynamic Load Balancing
100%
100%
100%
100%
Cloud Storage Service
100%
100%
100%
100%
Primary DNS Availability
100%
100%
100%
100%
Server Reboot
<15m
6.7E-5m
0.000067m
0.000067m
Emergency Support
Response Time
<30m
<30m
<30m
<30m
General Support Response
Time
<120m
<120m
130m
130m
Engineering Support
23 x 365
23 x 365
23 x 365
23 x 365
Physical Security
24 x 365
24 x 365
24 x 365
24 x 365
Figure 1: Trust Label Interface Overview.
3 SYSTEM ARCHITECTURE
INTEGRATION
This section describes the integration of the trust la-
bel system (Emeakaroha et al., 2016) with the Cloud
Trust Protocol.
The aim of this integration is to add compli-
ance and transparency to the communication of trust-
worthiness information in cloud service provisioning.
Such information is gathered by a monitoring frame-
work that is usually part of a provider’s management
layer. In our case, it is communicated through the
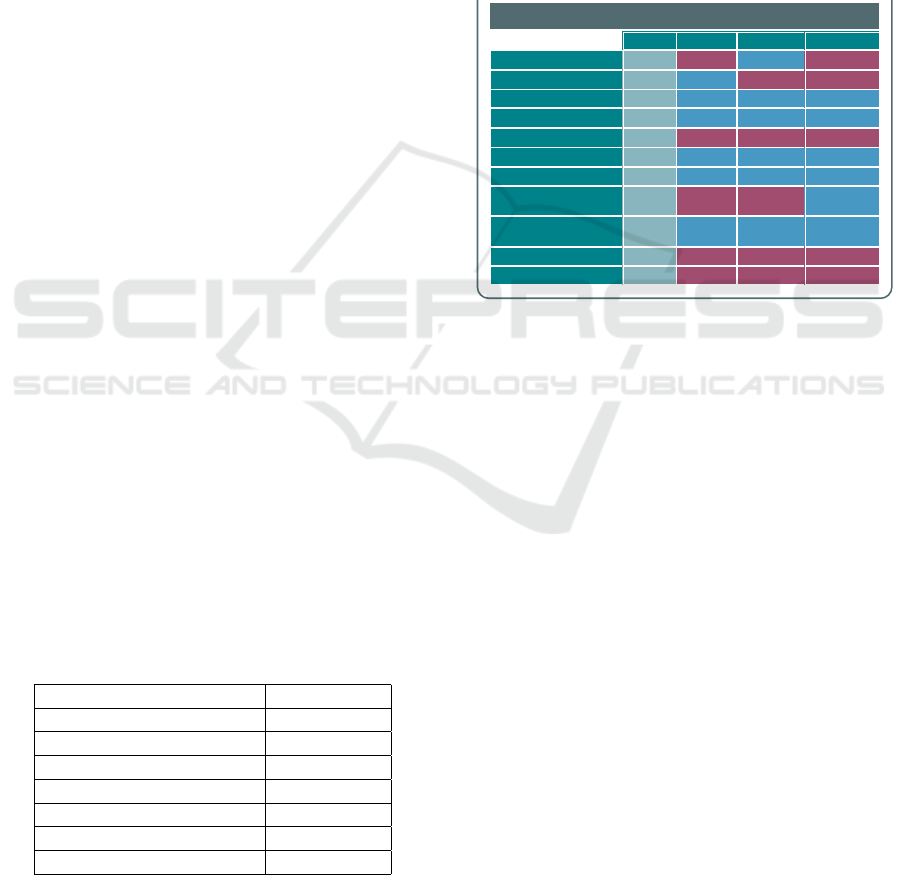
trust label interface to the cloud consumers. Figure 3
presents an overview of the system integration archi-
tecture.
This system integration demonstrates the feasibil-
ity of communicating information about cloud service
CLOSER 2017 - 7th International Conference on Cloud Computing and Services Science
592
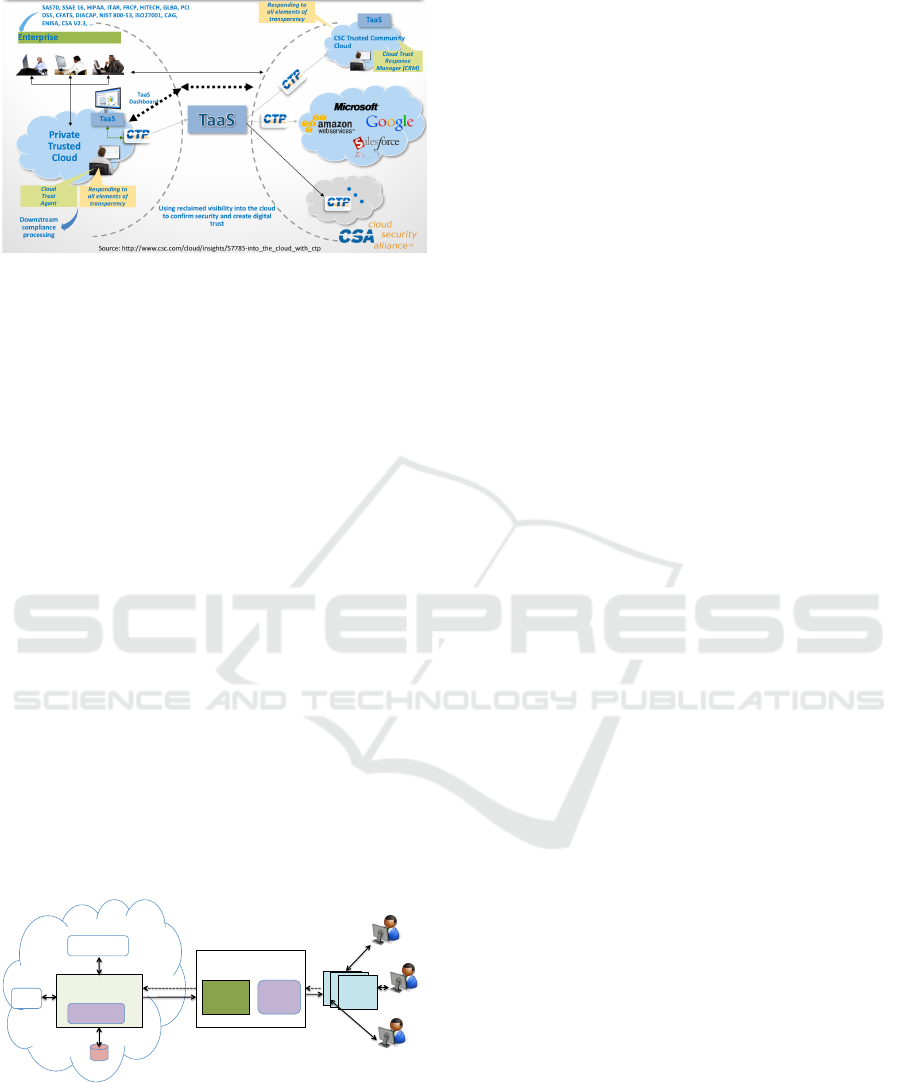
Figure 2: CTP Deployment Overview.
operations in a standards compliant and transparent
manner. As shown in Figure 3, the Monitoring Frame-
work gathers the information for eventual transmis-
sion to the Trust Label system, which displays the
data on a customisable web interface for cloud con-
sumers. To realise a standard and transparent means
of communicating this information, we adopted the
CTP Server prototype provided by the Cloud Security
Alliance.
The CTP Server provides a standard data model
for describing cloud services and management data
such as monitoring information. This is key for pro-
viding compliance and it should be clearly understood
at design and implementation time to enable interop-
erability and compatibility.
In the integrated system as shown in Figure 3, the
monitoring framework is extended with a bridge li-
brary that provides access to the CTP server. The
bridge library enables communication between the
monitoring framework and the CTP Server as well as
between the CTP server and the trust label interface.
This is realised using REST APIs. The communica-
tion directions could be both ways. We use the dot-
ted arrows to indicate that the CTP server supports a
query-response pattern of communication.
Applica'on*
VM*
Cloud Provider Platform
DB*
Monitoring
Framework
Bridge*Library*
CTP*Server*
Prototype*
Bridge*
Library*
Communication
Mechanism
Trust*
Label*
Interface*
Consumer
Consumer
Consumer
Figure 3: System Integration Architecture.
The trust label interface is customisable and can
be setup independently for different consumers based
on their Service Level Agreements (SLA) with the
cloud provider.
4 IMPLEMENTATION DETAILS
This section describes the implementation of the in-
tegrated system. We focus on the bridge library and
provide a brief overview of the components with ref-
erences for further details.
4.1 Bridge Library
The CTP bridge is a Spring Boot application writ-
ten in Java. This component implements interfaces
to the CTP server, Monitoring framework and Trust
Label interface. It provides APIs for writing monitor-
ing data after formatting them using the standard data
model into the CTP server and also for reading from
the CTP server to update the Trust label interface. The
APIs for the different communications are as follows:
• CTP Admin REST API - for updating the CTP
server prototype with the monitoring data and
other information.
• CTP REST API - for getting information/data
from the CTP server prototype.
• Trust Label REST API - for updating the Trust La-
bel interface with the information gathered from
the CTP server.
The above three APIs are supported by their own
Java classes, each a Spring component, which inherit
common code from another class for the basics of
REST API invocation, including passing tokens in
headers for security. The common code includes stan-
dard Spring mechanisms to invoke REST APIs.
The CTP Bridge uses Spring Scheduling to invoke
the code to copy from the CTP Server to Trust Label
every 10 seconds. A simple annotation on the method
to invoke it ensures it is triggered automatically by the
Spring Framework. Gradle is used as the dependency
manager and build system for the project.
4.2 Other Components
Monitoring Framework: This component is im-
plemented using the Java Programming language.
It uses monitoring agents for gathering low-level
resource metrics. At the application level, it employs
HTTP pings among other methods to supervise
application execution status. For storing monitoring
data, it uses the MySQL database. Hibernate is
used to realise easy interaction between the Java
classes and the database. Further details about this
component can be found in (Emeakaroha et al., 2016).
CTP Server Prototype: This is implemented as a
Unix-style daemon written in the Go language. It
Establishing Trust in Cloud Services via Integration of Cloud Trust Protocol with a Trust Label System
593
uses the MongoDB NoSQL database as a backend to
store data. CTP has been tested on Linux and Mac
OS X environments. The current implementation
includes APIs for reading and writing to the server.
Further information can be read from (Cloud Security
Alliance, 2015b).
Trust Label Interface: This component is realised
using Ruby on Rails. It uses a backend database to
maintain the displayed content. Due to the generic na-
ture of Ruby, it is capable of using different database
engines such as SQLite, Postgre SQL, MySQL, etc. It
implements RESTful APIs and uses the JSON data in-
terchange format for structuring data. Additional in-
formation is available from (Emeakaroha et al., 2016).
5 EVALUATION
This section presents a demonstration of the inte-
grated system as a proof of concept. We show how
quality of service information is being communicated
based on a use case scenario and evaluate the perfor-
mance of the bridge library.
5.1 Use Case Scenario
We present a use case scenario of service provisioning
between a cloud provider and a consumer. The mon-
itoring of this service and the communication of the
service status facilitate trust establishment between
the provider and the consumer. The service is a trans-
actional video-serving web application that responds
to requests and makes queries to storage databases. It
runs on top of a load balancer that distributes the in-
coming request to compute resources to sustain heavy
load. The expected quality for the service is specified
in a Service Level Agreement (SLA) document that
is signed between the provider and the consumer to
guide the provisioning of the service. Table 1 presents
the SLA metric values for this particular service.
Table 1: Service SLA Document.
Metric Name QoS Target
Service Uptime 100%
Internal Network Uptime 100%
External Network Uptime 100%
Dynamic Load Balancing 100%
Cloud Storage Service 100%
Primary DNS Availability 100%
Server Reboot Time < 5mins
The cloud provider makes every effort to guaran-
tee the QoS targets specified in the SLA. Any vio-
lation of the SLA incurs a penalty for the provider.
In order to assure consumers of their service quality,
the provider needs to provide them with real time ev-
idence of their service operations.
5.2 Quality of Service Performance
As discussed in the use case scenario, providers
should furnish consumers with continuous evidence
of their service performance in order to gain their
trust. This section details how our proposed inte-
grated system facilitates the communication of such
information.
Cloud Solutions
Dummy CRMA
New York, NY10006
State of New York, USA
Performance
Policy
Preference
Can I measure
?
Is there a
policy ?
Can I modify
?
Data Security
YES
YES
YES
Certification
YES
YES
YES
Service Levels
YES
YES
YES
Variation of Terms
YES
YES
YES
Data Portability
Onboard
YES
YES
YES
Offboard
YES
YES
YES
Backup of Data
YES
YES
YES
Data Location
YES
YES
YES
Ownership
Data
N/A
YES
YES
Meta Data
YES
YES
Service
Customisation
YES
YES
Application
Customisation
YES
YES
Sharing of Data
Commercial
NO
YES
YES
Legal
NO
YES
YES
Insurance Levels
YES
YES
YES
Audit Approvals
YES
YES
YES
Customer Service Level
YES
YES
YES
Service Level Summary
Target
Current
3-Month
12-Month
Service Uptime
100%
0%
100%
99.99%
Internal Network Uptime
100%
100%
0%
99.999%
External Network Uptime
100%
100%
100%
100%
Dynamic Load Balancing
100%
100%
100%
100%
Cloud Storage Service
100%
0%
92%
99.999%
Primary DNS Availability
100%
100%
100%
100%
Server Reboot
<15m
0.00055m
0.000094m
0.00045mins
Emergency Support Response
Time
<30m
38m
31.17m
28.05m
General Support Response
Time
<120m
118.6m
109.13m
113.1m
Engineering Support
23 x 365
YES
N/A
N/A
Physical Security
24 x 365
NO
N/A
N/A
Figure 4: QoS Performance Information.
Figure 4 depicts a screenshot of an extract of the
Trust Label interface showing in real time the com-
munication of the quality of service metrics. The in-
formation contains the current monitored values for
the SLA metrics specified in Table 1 and other infor-
mation. For simplicity, we modelled the display of
the SLA values on the Trust Label interface in terms
of 0% or 100% whereby 0% indicates a violation and
100% shows satisfied.
As shown in Figure 4, the Trust Label interface
conveys to the consumer the current performance sta-
tus and three and twelve month performance aver-
ages. These data give the consumer a clear overview
of the service operation and a basis to trust the cloud
provider. Our proposed integrated system facilitates
this trust establishment by enabling this end-to-end
communication of trustworthiness information.
5.3 Bridge Library Benchmarking
In this section, we present our benchmarking of the
bridge library communication performance. The aim
is to demonstrate the non-intrusiveness of this com-
ponent in the end-to-end integration.
Figures 5 and 6 present a plot of an extract from
the use case scenario execution. The application in the
CLOSER 2017 - 7th International Conference on Cloud Computing and Services Science
594
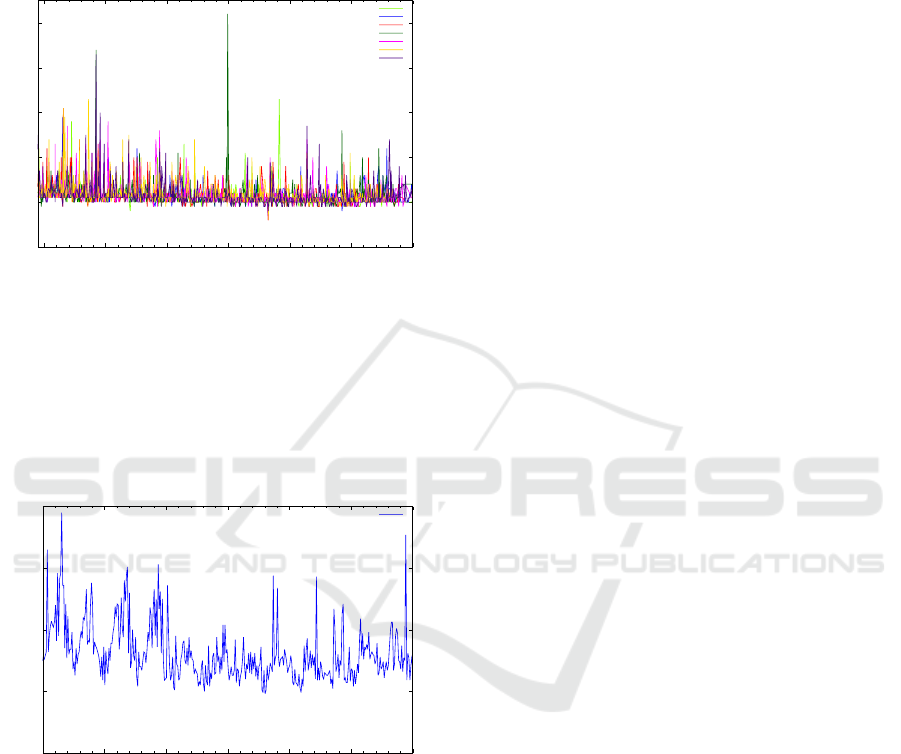
use case scenario was executed for about three hours
and we selected the middle hour execution period to
avoid startup and wind-down effects. Thus, the fig-
ures show a full hour execution.
0
10
20
30
40
50
16:20:00 16:30:00 16:40:00 16:50:00 17:00:00 17:10:00 17:20:00
Time Values (ms)
Day Timestamp (hh-mm-ss)
Performance Metrics
Service Uptime
Internal Network Uptime
External Network Uptime
Dynamic Load Balacing
Cloud Storage Service
Primary DNS Availability
Server Reboot
Figure 5: Monitor-to-CTP Performance.
Figure 5 shows the time it takes to communicate
each of the monitored SLA metrics from the cloud
platform to the CTP server in parallel. As can be ob-
served from Figure 5, the bridge library takes an aver-
age of 12 milliseconds to communicate data from the
monitoring framework to the CTP server.
300
350
400
450
500
16:20:00 16:30:00 16:40:00 16:50:00 17:00:00 17:10:00 17:20:00
Time Values (ms)
Day Timestamp (hh-mm-ss)
CTP Server to Trust label
CTP to Trust label
Figure 6: CTP-to-Trust Label Performance.
Figure 6 presents the time for communicating the
whole information gathered from the CTP server to
the Trust Label interface. This data is bundled to-
gether and sent in one communication. It can be ob-
served that it takes an average of 380 milliseconds in
this case. This is also an impressive performance for
the bridge library.
Combining the results of these two benchmarks
indicates quick communication and therefore reflects
the efficiency of the bridge library. We could not ef-
fectively evaluate the overall end-to-end communica-
tion time since the CTP server is being used as a black
box. Besides, the communication between the CTP
and Trust Label components is a pull operation at pe-
riodic intervals. This is why we opted to focus on the
implemented bridge library.
5.4 Discussion/Recommendation
This end-to-end integration demonstration for com-
municating cloud data through CTP and Trust label
system provides a practical reference. This can be
very beneficial to cloud and service providers includ-
ing brokers who are looking for a means of establish-
ing and maintaining evidence-based trust with their
consumers.
What we presented in this paper is simply a means
of adopting and integrating CTP. There are other pos-
sible ways of using these software components. In
fact, in a production environment, it is likely that the
cloud monitoring framework would be more closely
integrated with the CTP server; indeed they could
be so closely coupled that there would be no REST
API between them. Similarly the functionality of the
CTP Bridge and Trust Label could be merged. An
ideal architecture therefore would have Trust Label
use the CTP REST API to communicate directly with
the cloud provider. In this scenario, the CTP function-
ality and monitoring need not be separate services.
6 RELATED WORK
The Cloud Trust Protocol is at an early stage
of adoption and validation by both industry and
academia. Some recently completed EU funded re-
search projects have adopted this protocol to ad-
dress different challenges. The FP7 SPECS (Se-
cure Provisioning of cloud Services based on Ser-
vice Level Agreement (SLA) Management) project
(SPECS project, 2016) is adopting CTP to achieve
transparent communication between cloud providers
and cloud users. The goal of this project is to provide
comprehensible and enforceable security assurance
by cloud providers to their users. The project takes
an SLA-based approach for negotiating the cloud se-
curity parameters in the SLA and includes monitoring
of a limited number of metrics to enable their enforce-
ment. This project is similar to ours; however, we
consider a broader range of performance metrics that
can facilitate consumer trust in cloud services.
A4cloud (Cloud Accountability project, 2016) fo-
cuses on accountability for clouds. One of the ar-
eas this project investigates is means to enable cloud
providers to give their users transparent control over
how their data is being used or handled in clouds. The
Establishing Trust in Cloud Services via Integration of Cloud Trust Protocol with a Trust Label System
595

goal is to boost user confidence and to ensure compli-
ance. The project is using CTP in addressing these
challenges. This project differs from ours because it
focuses on data location management. Our trust label
system includes data location management, alongside
other trustworthiness information, to enable evidence
based trust of cloud services.
The CUMULUS (Certification Infrastructure for
Multi-Layer Cloud Services) project (CUMULUS
project, 2016) aims to provide an automated process
to certify security properties of cloud services at the
different layers of cloud stack. The goal is to over-
come the manual, costly and lengthy inspections and
auditing schemes for certification purposes. Such
schemes do not support dynamic change in the struc-
ture, deployment or configuration of resources under-
lying cloud provisioning. This project is applying
CTP towards their goal of achieving compliance in
certifying cloud services. The objective of this project
is to enable user trust through certification. This ap-
proach is similar to ours, however, we aim to com-
municate trustworthiness information directly to con-
sumers to enable evidence-based trust instead of es-
tablishing certification seals.
The Security Content Automation Protocol
(SCAP) (NIST, 2016) is also considered a cloud
trust interoperability protocol (Ron Knode, 2010).
SCAP (pronounced ess-cap) consists of a suite
of specifications for standardising the format and
nomenclature by which software flaws and security
configuration information are communicated, both
to machines and humans. The CTP developers have
however incorporated several parts of the SCAP
specification into the development of CTP and so
the two protocols can be seen as complementary
rather than as competitors. In relation to our trust
label system that provides broad metrics to facilitate
consumer trust in cloud services, these two protocols
are considered as extension possibilities as we have
demonstrated in this paper.
To the best of our knowledge, none of the exist-
ing literature has reported on practical integration of
CTP to facilitate consumer trust in cloud services and
thereby increase the adoption of cloud computing.
7 CONCLUSION
In this paper, we presented a practical integration of
Cloud Trust Protocol (CTP) with a trust label sys-
tem designed to facilitate both persistent and dynamic
trust building in both cloud services and cloud ser-
vice providers. The trust label system includes a novel
monitoring framework to supervise service provision-
ing and to gather performance metrics data.
We described the trust label system and CTP de-
ployments while highlighting the challenges to be ad-
dressed. Our focus was mainly on the integration ar-
chitecture that details the components and the realisa-
tion of the end-to-end communication of trustworthi-
ness information between cloud service providers and
consumers. The design and implementation of this ar-
chitecture including a Bridge library were presented.
For the evaluation, a practical use case scenario
was introduced. The use case describes an end-to-end
consumer service provisioning. It uses a sample SLA
document to explain how the quality of service ele-
ments of the consumer service were monitored and
communicated through the integrated system. We
demonstrated the correct working of the system and
presented some efficiency results.
In the future, we aim to carry out real validation of
the system by end-users to gather empirical evidence
about the effect of the system on their trust of cloud
services. This will inform on the novelty of our ap-
proach. We intend to publish the system code under
open source licence to open up its usage by others and
thereby buttress our vision of increasing cloud service
adoption.
ACKNOWLEDGEMENTS
The research work described in this paper was sup-
ported by the Irish Centre for Cloud Computing
and Commerce, an Irish national Technology Centre
funded by Enterprise Ireland and the Irish Industrial
Development Authority.
REFERENCES
Anderson, S. W., Christ, M. H., Dekker, H. C., and Seda-
tole, K. L. (2014). The use of management controls
to mitigate risk in strategic alliances: Field and sur-
vey evidence. Journal of Management Accounting Re-
search, 26(1):1–32.
Bente, G., Baptist, O., and Leuschner, H. (2012). To buy or
not to buy: Influence of seller photos and reputation
on buyer trust and purchase behavior. Int. J. Hum.-
Comput. Stud., 70(1):1–13.
Bradshaw, D., Folco, G., Cattaneo, G., and Kolding, M.
(2012). Quantitative estimates of the demand for
cloud computing in europe and the likely barriers to
up-take. In IDC Analize de Future.
Buyya, R., Yeo, C. S., Venugopal, S., Broberg, J., and
Brandic, I. (2009). Cloud computing and emerging
it platforms: Vision, hype, and reality for delivering
computing as the 5th utility. Future Generation Com-
puting Systems, 25(6):599–616.
CLOSER 2017 - 7th International Conference on Cloud Computing and Services Science
596

Cloud Accountability project (2016). A4Cloud.
http://www.a4cloud.eu/objectives Accessed
on 22/08/2016.
Cloud Security Alliance (2015a). Cloud trust protocol.
https://cloudsecurityalliance.org/group/
cloudtrust-protocol/ Accessed on 22/08/2016.
Cloud Security Alliance (2015b). Cloud trust proto-
col daemon prototype. https://github.com/
cloudsecurityalliance/ctpd Accessed on
07/09/2016.
CUMULUS project (2016). Certification infrastruc-
ture for multi-layer cloud services. http://www.
cumulus-project.eu/ Accessed on 22/08/2016.
Das, T. and Teng, B. S. (1996). Risk types and inter-firm
alliance structures. Journal of management studies,
33(6):827–843.
Deitz, G. and DenHartog, D. (2006). Measuring trust inside
organizations. JPersonnel Review, 35(5):557–588.
Emeakaroha, V., Fatema, K., Vanderwerff, L., Healy, P.,
Lynn, T., and Morrison, J. (2016). A trust label sys-
tem for communicating trust in cloud services. IEEE
Transactions on Services Computing, PP(99):1–1.
Gefen, D. (2003). TAM or just plain habit: A look at expe-
rienced online shoppers. Journal of End User Com-
puting, 15(3):1–13.
Gens, F. (2014). Worldwide and regional public cloud it ser-
vices 2014-2018 forecast. https://www.idc.com/
research/viewtoc.jsp?containerId=251730
Accessed on 20/10/2016. IDC Market Analysis.
Hogan, M., Liu, F., Sokol, A., and Tong, J. (2011). Nist
cloud computing standards roadmap. NIST Special
Publication, 35.
Hwang, K. and Li, D. (2010). Trusted cloud computing
with secure resources and data coloring. IEEE Inter-
net Computing, 14(5):14 –22.
Kim, W. (2009). Cloud computing: Today and tomorrow.
Journal of object technology, 8:65 – 72.
Leimbach, T., Hallinan, D., Bachlechner, D., Weber, A.,
Jaglo, M., Hennen, L., Nielsen, R., Nentwich, M.,
Strau, S., Lynn, T., and Hunt, G. (2014). Potential
and impacts of cloud computing services and social
network websites. Science and Technology Op-
tions Assessment (STOA) http://www.europarl.
europa.eu/RegData/etudes/etudes/join/2014/
513546/IPOL-JOIN_ET(2014)513546_EN.pdf
Accessed on 15/08/2016.
Lewicki, R. and Bunker, B. (1996). Developing and main-
taining trust in work relationships. Technical report,
Trust in organizations: Frontiers of theory and re-
search. edited by Roderick M. Kramer, Tom R. Tyler.
Low, C., Chen, Y., and Wu, M. (2011). Understanding the
determinants of cloud computing adoption. Industrial
management and data systems, 111:1006 – 1023.
Lynn, T., Healy, P., McClatchey, R., Morrison, J., Pahl, C.,
and Lee, B. (2013). The case for cloud service trust-
marks and assurance-as-a-service. In Intl. Conference
on Cloud Computing and Services Science Closer,
pages 8–10.
Lynn, T., van der Werff, L., Hunt, G., and Healy, P. (2016).
Development of a cloud trust label: A delphi ap-
proach. Journal of Computer Information System,
56(3):185–193.
Masevic, I., van der Werff, L., Emeakaroha, V., Morrison,
J., and Lynn, T. (2016). Validating a cloud trust label:
Influencing consumer trust. In Cloud British Academy
of Management Conference.
Mcknight, D. H., Carter, M., Thatcher, J. B., and Clay, P. F.
(2011). Trust in a specific technology: An investi-
gation of its components and measures. ACM Trans.
Manage. Inf. Syst., 2(2):12:1–12:25.
McKnight, D. H. and Chervany, N. L. (2001). What trust
means in e-commerce customer relationships: An in-
terdisciplinary conceptual typology. Int. J. Electron.
Commerce, 6(2):35–59.
NIST (2016). Security content automation proto-
col. https://scap.nist.gov/revision/1.2/
index.html Accessed on 22/08/2016.
Pavlou, P. A. and Gefen, D. (2004). Building effective on-
line marketplaces with institution-based trust. Info.
Sys. Research, 15(1):37–59.
Pearson, S. (2013). Privacy, security and trust in cloud com-
puting. In Computer Communications and Networks,
pages 3 – 42.
Pearson, S. and Benameur, A. (2010). Privacy, security
and trust issues arising from cloud computing. In
Cloud Computing Technology and Science (Cloud-
Com), 2010 IEEE Second International Conference
on, pages 693–702.
Ron Knode (2010). Cloud trust 2.0. https:
//scap.nist.gov/events/2010/itsac/
presentations/day2/Security_Automation_
for_Cloud_Computing-CloudTrust_2.0.pdf
Accessed on 22/08/2016.
Rousseau, D. M. and Sitkin, S. B. (1998). Not so different
after all: A cross-discipline view of trust. Academy of
Management Review, 23(3):393–404.
SPECS project (2016). Secure provisioning of cloud
service based on SLA management. http://
www.specs-project.eu/project/description/
Accessed on 22/08/2016.
Subashini, S. and Kavitha, V. (2011). A survey on security
issues in service delivery models of cloud computing.
Journal of network and computer applications, 34:1 –
11.
Zissis, D. and Lekkas, D. (2012). Addressing cloud com-
puting security issues. Future Generation computer
systems, 28(3):583 – 592.
Establishing Trust in Cloud Services via Integration of Cloud Trust Protocol with a Trust Label System
597
