
Situational Awareness based Risk-adaptable Access Control in
Enterprise Networks
Brian Lee, Roman Vanickis, Franklin Rogelio and Paul Jacob
Software Research Institute, Athlone Institute of Technology, Athlone, Ireland
Keywords: Risk based Access Control, RAdAC, Zero-trust Networking, Security Situational Awareness,
Abstract: As the computing landscape evolves towards distributed architectures such as Internet of Things (IoT),
enterprises are moving away from traditional perimeter based security models toward so called “zero trust
networking” (ZTN) models that treat both the intranet and Internet as equally untrustworthy. Such security
models incorporate risk arising from dynamic and situational factors, such as device location and security
risk level risk, into the access control decision. Researchers have developed a number of risk models such as
RAdAC (Risk Adaptable Access Control) to handle dynamic contexts and these have been applied to
medical and other scenarios. In this position paper we describe our ongoing work to apply RAdAC to ZTN.
We develop a policy management framework, FURZE, to facilitate fuzzy risk evaluation that also defines
how to adapt to dynamically changing contexts. We also consider how enterprise security situational
awareness (SSA) - which describes the potential impact to an organisations mission based on the current
threats and the relative importance of the information asset under threat - can be incorporated into a RAdAC
scheme.
1 INTRODUCTION
The enterprise computing landscape has evolved
considerably over the last decade with the
emergence of technologies such as cloud computing
and mobile devices, including the “bring your own
device”, (BYOD) phenomenon. These trends are
likely to be amplified even further in coming years
with the increasing deployment of Internet of Things
(IoT) applications. Also, over the same period, there
has been a dramatic escalation in both the number
and sophistication of security-attacks on business
(Broadhurst et. al. 2014).
This combination puts pressure on the traditional
perimeter based security model toward the
application of so called “zero trust networking”
(ZTN) models that treat the intranet with the same
degree, i.e. lack, of trust as the internet (Forrester
Research, 2013). Access control decisions are now
made based on the degree of trust in the user and the
device, irrespective of whether the user is inside or
outside the internal network (Ward and Beyer,
2014). Furthermore the level of access assigned to a
device or user may change over time and the access
control system is able to dynamically infer the
current trust level by consulting various data sources
and make decisions accordingly.
One approach to the capability of an access
control system to adapt dynamically to changing
context is Risk-Adaptable Access Control (RAdAC),
(McGraw, 2009). The key concept of RAdAC is the
trade-off, or balance, between operational need and
security risk when making access control decisions -
in some conditions operational need will override
security risk and access to otherwise restricted
resources will be granted. RAdAC was originally
proposed for highly variable environments such as
those in the military but is increasingly seen applied
in other situations characterised by dynamic contexts
such as medical emergencies and the IoT.
Similarly, dynamic access control for enterprise
networks has been considered for some time,
(Hernandez R., 2006) and is becoming ever more
appropriate as the variety and sophistication of
security attacks and the complexity of these
networks increases (Farroha and Farroha, 2012). The
types of factors used for access control in enterprise
ZTN scenarios includes user and device as well as
situational factors such as location and access
history, (Ward and Beyer, 2014; Vensmer and
Kiesel, 2012).
In most applications of RAdAC described to date
400
Lee, B., Vanickis, R., Rogelio, F. and Jacob, P.
Situational Awareness based Risk-adaptable Access Control in Enterprise Networks.
DOI: 10.5220/0006363404000405
In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security (IoTBDS 2017), pages 400-405
ISBN: 978-989-758-245-5
Copyright © 2017 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
the focus has been relaxation of the access controls
in order to maximise the benefit for the organisation
by granting temporary access to restricted objects. In
certain cases however the goal might be to restrict
access as e.g. in the case of heightened security
situation (Hernandez R. 2006) and it is this
particular issue we address here.
In particular we consider how enterprise security
situational awareness (SSA) - which describes the
potential impact to an organisations mission based
on the current threats and the relative importance of
the information asset under threat - can be
incorporated into a RAdAC scheme. We extend the
RAdAC model of Kandala, Sandhu and Bhamidipati
(2011), in this direction and define a framework to
manage risk based access control in zero trust
networks.
The remainder of the paper is structured as
follows: Section 2 describes the background
concepts. Section 3 describes our proposed RAdAC
approach to zero-trust networking. Section 4
describes related work while conclusions and future
work are outlined in Section 5.
2 BACKGROUND
2.1 Access Control
For many years the dominant model of access
control has been Role Based Access Control
(RBAC). RBAC is centred around the notion of
authorisation via groups or roles i.e. access rights are
allocated to a group rather than an individual.
However RBAC has limitations for the evolving
enterprise computing landscape. In particular it does
not very well support multi-factor decisions such as
those based on location, special training received
etc. as well as rank in the organisation, (Hu et al.
2013) Nor are it’s primarily static role definitions
well suited for dynamic access control decisions. As
a result a more dynamic access control approach has
been proposed i.e. Attribute Based Access Control
(ABAC), (OASIS 2013). ABAC decisions are based
on the use of subject and object attributes and
enables very flexible access control capabilities.
ABAC also introduces the concepts of obligations
and access based on environment conditions.
Obligations are additional actions required by the
subject as part of pre- or post-conditions of granting
authorisation. Environment conditions enable the
inclusion of context specific criteria into the access
control decision-making such as the location of the
user, the state of emergency in a hospital theatre etc.
ABAC systems are beginning to see significant
deployment in the enterprise including use for
dynamic access control based on environment
conditions, (Osborne et al. 2016; Vensmer and
Kiesel, 2012).
While ABAC significantly increases the
dynamic capability of access control systems it does
not include the capability to factor risk into
authorisation decision-making. To this end McGraw
(2009) proposed an extension of ABAC to manage
dynamic risk assessment - the Risk Adaptable
Access Control (RAdAC) concept. According to
McGraw (2009) – “RAdAC incorporates a real time,
probabilistic determination of security risk into the
access control decision rather than just using a hard
comparison of the attributes of the subject and object
as in traditional models”. RAdAC is based on
assessing the trade-off between security risk and
operational need. The definition of these terms is
very much context and organisation dependent
though possible inputs to security risk determination
could include e.g. trust in user or device, the current
threat level, sensitivity, or criticality to the mission,
of the requested information, role of the user etc.
(Farroha and Farroha, 2012).
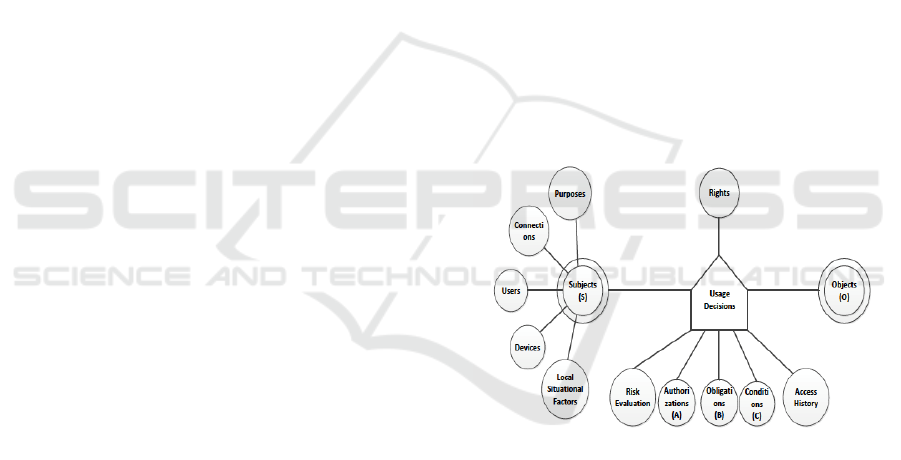
Figure 1: UCON Model with RAdAC Components. (from
Kandala, Sandhu and Bhamidipati 2011).
Kandala, Sandhu and Bhamidipati (2011) define
an abstract model for RAdAC in terms of the “Usage
Connection” (UCON) access control approach–
shown in Figure 1. UCON is an extended access
control approach that seeks to unify both traditional
access control i.e. access at the start of the
transaction with the need for on-going control of
access to the object during the transaction – what
UCON terms decision continuity. This latter
property is a significant addition to RAdAC as it
allows adaptation to changing environment
conditions. In Figure 1 above the subject concept has
been decomposed into a number of components i.e.
users, devices, connections and purposes. The
Situational Awareness based Risk-adaptable Access Control in Enterprise Networks
401

usage/access control decision process is shown to
include a Risk Evaluation component as well
predicate/rule-based components for Authorisation,
(based on the attributes) Obligations (as for ABAC)
and Conditions (captures the environmental
conditions). Usage access decision-making is based
on all three rule/predicate components i.e.
authorisation, obligation and conditions and all can
be evaluated pre, during or post the session.
2.2 Zero Trust Networking
There is an increasing move away from the
traditional perimeter-based security approach both in
the enterprise and in cloud computing (Ward and
Beyer 2014). This trend has been dubbed “Zero
Trust Networking” (Forrester, 2013). The key
element of this approach is to treat the internal
network as untrusted to the same degree as the
Internet. This usually entails partitioning the internal
network into a number of network segments or zones
each of which houses different functions and
information. Each zone may have a different trust
level that indicates the importance of the assets
housed within the zone (Gontarczyk et al. 2015). In
order to access an asset, a subject’s trust level
assignment must be equal to or greater than the
zone’s minimum trust level (Osborne et al. 2016).
Traffic between zones is thus restricted by firewalls
in accordance with the overall access control policy.
Access control in ZTN is transaction based and
dynamic i.e. a decision is made for each access
request and firewall rules are updated as a result of
each decision. Access control decisions are based on
user and device attributes as well as environment
attributes such as location. Deployments include
enterprise security e.g. Google’s BeyondCorp
(Osborne et al. 2016) as well as campus (Vensmer
and Kiesel 2012) and cloud computing security
(Giannakou et al. 2016).
2.3 Mission Impact Modelling
As outlined above environmental factors that are
critical parameters in determining situational risk
include those relating to the current threat level and
the business or mission criticality of the related
assets. This approach can also play a part in the
access control system to determine if access should
be granted based on the criticality of the resource
being accessed and the current threat level.
At the heart of this approach is the “mission
dependency graph” (Holspopple and Yang 2013;
Innerhofer–Oberperfler and Breu 2006; Jakobson
2011; Watters et al. 2009). The mission dependency
graph maps the organisations strategic mission
objectives to the IT assets by defining, and
prioritising, the dependencies between both via the
different layers of the graph i.e. business objectives
are realised (depend on) by business functions and
processes which in turn are, completely or partly,
realised (depend on) by IT capabilities and assets.
The edges in the graph record a causal
relationship/influence between two nodes and may
be assigned a weighting to reflect the extent of that
influence as in Holspopple and Yang (2013) and
Watters et al. (2009). These values are typically
assigned through consultation with key business and
IT personnel responsible for the various processes
and components that constitute the graph.
A mission graph is used for two complementary
purposes. Firstly it is used to assign to each IT asset
an asset criticality dependent on the particular
missions or business goals it supports. This is done
by trickling the mission objective priority down the
graph to the individual asset. This feature is used to
help analysts improve situational awareness as
discussed above. Secondly the degree of severity of
a particular threat to a particular asset can be
evaluated to determine the risk to the mission
objectives by percolating the risk up the graph. This
risk assessment feature can be used for off-line
what-if analyses and it also forms the basis for our
situational awareness risk based access control.
Another consideration that must be taken into
account is how the base impact -the impact to the
information asset at the root of the mission tree that
is the subject of a threat - is calculated. Watters
(2009) uses vulnerability severity as a base for his
calculation as does Jakobson (2011). Holspopple and
Yang (2013) simply assume a measure of impact
without specifying how it may be calculated while
Innerhofer–Oberperfler and Breu (2006) do not
address the issue at all.
3 FURZE
Whilst Kandala, Sandhu and Bhamidipati (2011)
have provided a sound abstract model for “UCON-
ised” RAdAC a number of significant research
questions remain open around the practical
deployment of RAdAC. Our area of interest is to
explore enforcement architecture issues for the
application of RAdAC in ZTN through the
development of a policy enforcement framework
that we designate FURZE (Fuzzy Risk Framework
for ZTN).
IoTBDS 2017 - 2nd International Conference on Internet of Things, Big Data and Security
402
Specific issues we wish to investigate include i)
the definition of a policy management architecture to
include the on-going monitoring needed to enable
decision continuity in ZTN access, ii) the design of
an access control policy language to specify and
manage such updates, iii) the design a risk
evaluation function based on fuzzy logic to enable
probabilistic access control decisions to be taken and
iv) to investigate how the proposed approach works
for enterprise security situational awareness.
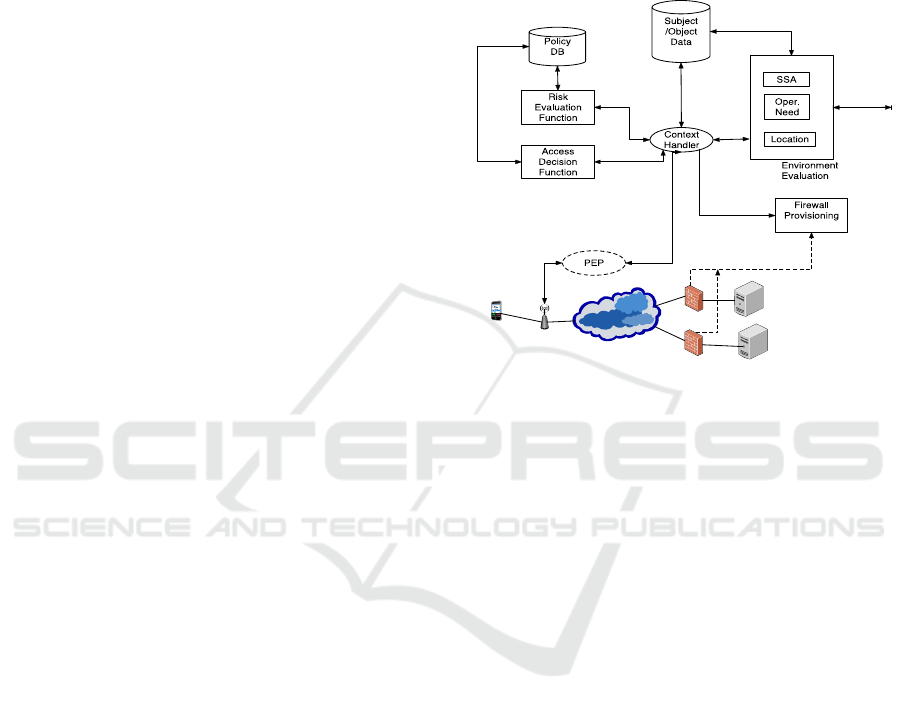
The starting point for FURZE is strongly hinted
by Kandala, Sandhu and Bhamidipati (2011) in
Figure 1. This contains a number of elements that
form the functional, logical and linguistic basis for
the proposed policy framework for ZTN shown in
Figure 2. The architecture is broadly based on the
XACML policy framework (OASIS 2013). Access
requests are received via a Policy Enforcement Point
(PEP) as e.g. a WiFi base station. The Context
Handler coordinates the access control process
including decision continuity handling. The
Environment Evaluation contains plug-in
components that convert session and other relevant
factors into attributes that can be used for risk
evaluation e.g. through the use of rules. Examples
include SSA (discussed below), operational need
and locations - for a simple access control case these
components could simply default to session
attributes. The Risk Evaluation Function and Access
Decision Function jointly act as a Policy Decision
Point (PDP) to control access while the subject and
object attributes are stored in a management
database. The Firewall Provisioning module
converts generic firewall rules to device specific
filtering rules for appropriate firewalls.
In FURZE the application of decision continuity
imposes the need on the access control function to
maintain session state information so that access
control can adapt to reflect situational or other
influencing factors that change the balance between
operational need and security risk and trigger policy
re-evaluation. Risk assessment is made as part of the
initial authorisation predicate evaluation and,
possibly, subsequently as part of either an
authorisation or condition predicate evaluation that
in turn has been triggered by some event during the
session.
The definition of the FURZE policy language
will be based on i) subject and object entities and
their attributes and ii) policy rules formed from
authorisation and condition predicates. The subject
entity is decomposed into a number of components
that including e.g. device (from which the user
requests access), purpose, which reflects operational
need and is the underlying reason for the users
access request, local situational factors impacting
the individual user e.g. location etc. Objects define
the services, data and other resources users wish to
access. Global situational factors such as enterprise
security risk are evaluated as condition predicates
independent of any individual user.
Figure 2: FURZE Framework.
For the ZTN specific case the BeyondCorp
framework gives broad hints at policy factors while
the DynFire framework also suggests some specific
factors to consider as access control credentials
(Vensmer and Kiesel 2012). Similarly previous work
on policy management for firewall access control
(e.g. Zhang et al. 2007) can contribute to the
development of the policy language. The principal
challenge here for FURZE is to combine selected
elements of previous work with language constructs
to incorporate i) decision continuity and ii) risk
evaluation. Decision continuity will be handled in
the Context Handler.
Risk evaluation is at the heart of RAdAC access
control languages, as RAdAC must include the
capability to reckon with uncertainty. The proposed
approach for risk evaluation in FURZE – through
the Risk Evaluation component- will be based on the
use of fuzzy logic inferencing. Fuzzy logic is a
mathematically sound approach to draw
unambiguous conclusions from vague or imprecise
information and subjective if-then rules (Ni, Bertini
and Lobo, 2010) and has been widely used for
decision-making under uncertainty including risk
assessment. Furthermore as Ni shows, fuzzy logic is
flexible can be used to model a variety of access
control approaches. In FURZE we propose to
leverage existing fuzzy logic language developments
Situational Awareness based Risk-adaptable Access Control in Enterprise Networks
403

– specifically the use of the Fuzzy Control Language
(FCL) (IEC 61131-7 2000). FCL is a domain
specific language (DSL) created for use in fuzzy
control application in industrial automation. It
enables the definition of domain relevant fuzzy
concepts including linguistic variables, term sets and
rule sets. The principal challenge is to wrap or
embed the FCL risk evaluation into the overall
FURZE policy language. This includes not just
seamless language syntax but also satisfactorily
resolving DSL implementation issues.
Our proposed approach to evaluate mission
impact (via the SSA component) is based on the use
of Fuzzy Cognitive Maps (FCM) (Kosko, 1986) to
model both the information asset threat impact and
the mission graph. FCM is a graph based approach
to modelling systems in which the concepts that
capture different aspects of the behaviour of the
system as represented as nodes while weighted
edges capture interactions between concepts that
represent the dynamics of the system. We base our
threat modelling on the approach proposed by
Jakobson (2009) but extend it to deal with different
aspects of impact relating to the security trio of
confidentiality, integrity and availability. We will
use Rule Based Fuzzy Cognitive Maps (RB-FCM) to
model the mission tree as it allows us to represent a
richer set relationship than standard FCM (Carvalho
and Tome, 1999).
4 RELATED WORK
In relation to RAdAC the present work can be
regarded as an extension of the earlier conceptual
work (Kandala, Sandhu and Bhamidipati (2011;
Barroha and Barroha 2012) toward implementation
of an enforcement architecture.
Google has adopted a ZTN approach for access
control that, as described, seems partly similar to the
work defined here (Ward and Beyer 2013; Osborne
et al. 2016). However they have not described the
policy language, risk management or decision
continuity implementation in detail. Vensmer and
Kiesel (2012) describe Dynfire, an access control
policy management framework for ZTN applied to a
university campus that encompasses a number of
the ideas described in our work. However it does not
include either risk management nor decision
continuity.
Giannoku et al. (2016) describe AL-SAFE a
ZTN access control implementation for cloud
computing –however they also do not include policy
language, risk management or decision continuity
aspects.
Firewall policy management is a mature research
area and a number of authors have described have
described efforts in this direction (Zhang et al. 2007;
Lobo, Marchi and Provetti 2012; Cisco 2010).
However none of these authors have described
access control risk management as part of their
contributions.
A number of researchers have modelled the
impact of information security attacks on the
organisation business and mission (Jakobsson 2008;
Innerhoffer—Oberperfler and Breu 2006;
Holspopple and Yang, 2013). However none have
included mission impact assessment as part of the
access control decision continuity process.
Cheng et al. (2007) developed a fuzzy logic
approach to access control risk assessment that
proposed the gradation of security risk as services of
levels between “allow” and “deny” where each level
has an associated risk mitigation countermeasure.
Ni, Bertini, and Lobo (2010) investigated the
applicability of fuzzy inference for risk based access
control and concluded that the approach was flexible
and scalable. Our work most closely matches that of
Ni, Bertini, and Lobo (2010) as we also propose the
use of fuzzy inference for risk calculation – however
our scope of research is somewhat wider.
5 CONCLUSIONS
We have described a novel approach to risk based
access control for ZTN networking. The key element
of our contribution is a policy control framework
based on UCON that facilitates situational
awareness based decision continuity and which
embeds a fuzzy inference component to make the
actual risk estimates. Further we have shown how
asset criticality based on mission importance can be
used as part of the situational awareness process.
Future areas of research are to implement and
evaluate the proposed approach for a ZTN scenario
and to investigate its applicability to virtualised
networking in cloud computing and software-
defined networking (SDN).
ACKNOWLEDGEMENTS
This paper has received funding from the European
Union’s Horizon 2020 research and innovation
programme under grant agreement 700071.
IoTBDS 2017 - 2nd International Conference on Internet of Things, Big Data and Security
404

REFERENCES
Broadhurst, R., Grabosky, P., Alazab, M., Bouhours, B.,
and Chon, S., 2014.An Analysis of the Nature of
Groups engaged in Cyber Crime, International
Journal of Cyber Criminology January-June 2014,
Volume 8 (1): 1-20.
Carvalho, J.P. and Tomè, J.A., 1999. Rule based fuzzy
cognitive maps-fuzzy causal relations. Computational
Intelligence for Modelling, Control and Automation,
Edited by M. Mohammadian.
Chen P-C., Rohatgi P., Keser C. ,. Karger P. A,. Wagner
G.M, and Reninger A. S.. 2007,Fuzzy multi-level
security: An experiment on quantified risk-adaptive
access control. IEEE Symposium on Security and
Privacy, pages 222–230. IEEE Computer Society,
2007.
Cisco Corp. 2010 Zone-Based Policy Firewall Design and
Application Guide. Available at <http://
www.cisco.com/c/en/us/support/docs/security/ios-
firewall/98628-zone-design-guide.html#topic6 >
Forrester Research, 2013. Developing a Framework to
Improve Critical Infrastructure Cybersecurity,
Available at <http://csrc.nist.gov/cyberframework/
rfi_comments/040813_forrester_research.pdf>.Access
ed Oct21 2016.
Farroha, B., and Farroha, D. 2012, Challenges of
“Operationalizing” Dynamic System Access Control:
Transitioning from ABAC to RAdAC, Proceedings
IEEE International Systems Conference (SysCon)
2012.
Fernandez, R., 2006, Enterprise Dynamic Access Control.
Version 2, Overview, NIST, Available.
<csrc.nist.gov/rbac/EDACv2overview.pdf> ,
Accessed Oct 15, 2016.
Gontarczyk A., McMillan P. and Pavlovski C. 2015,
Blueprint for Cybersecurity Zone Modelling,
Commonwealth Bank of Australia Sydney, IT in
Industry, Vol. 3, No. 2, 2015, pp 38-46.
Giannakou A., Rilling L, Morin C., Pasage J-L., AL-
SAFE: A Secure Self-Adaptable Application-Level
Firewall for IaaS Clouds, SEC2 2016 - Second
workshop on Security in Clouds, Lorient,. 2016.
Holspopple, J., and Yang, S.J. 2013, Handling Temporal
and Functional Changes for Mission Impact
Assessment, Proceedings International
Multidisciplinary Conference on Cognitive Methods in
Situational Awareness and Decision Support
(CogSIMA) San Diego, 2013.
Hu, V. C. et al., 2013, Guide to Attribute Based Access
Control (ABAC) Definition and Considerations, NIST
Special Publication 800-162, April 2013.
IEC 61131-7:2000 Programmable Controllers – Fuzzy
Control Programming, International Electrotechnical
Commission. Available at <https://webstore.iec.ch/
publication/4556?
Innerhofer–Oberperfler, F. and Breu, R., 2006, Using an
Enterprise Architecture for IT Risk Management,
Proceedings Information Security South Africa, 2006.
Jakobson, G., 2011, Mission Cyber Security Situation
Assessment Using Impact Dependency Graphs,
Proceedings 14th International Conference on
Information Fusion, Chicago, Illinois, USA, July 5-8,
2011.
Kandala, S, Sandhu, R. and Bhamidipati, V., 2011, An
Attribute Based Framework for Risk-Adaptive Access
Control Models, ARES 11, Proceedings of the 2011
Sixth International Conference on Availability,
Reliability and Security :236-241.
Kosko, B., 1986. Fuzzy cognitive maps. International
Journal of man-machine studies, 24(1), pp.65-75.
Lobo J., Marchi M. and Provetti. 2012 A.,Firewall
Configuration Policies for the Specification and
Implementation of Private Zones , Proceedings IEEE
International Workshop on Policies for Distributed
Systems and Networks, pp. 78-85 (2012).
McGraw, R.,, 2009, Risk Adaptable Access Control,
National Security Agency, Sept. 2009 Available at
<http://csrc.nist.gov/news_events/privilege-
management-workshop/radac-Paper0001.pdf>
Accessed Oct 18 2016.
Ni Q., Bertino E. and Lobo J., 2010,Risk-based Access
Control Systems Built on Fuzzy Inferences,
Proceedings of the 5th ACM Symposium on
Information, ASIACCS’10 April 13–16, 2010,
OASIS 2013, “eXtensible Access Control Markup
Language (XACML)”, Available at <http://www.
oasis-1690 open.org/committees/xacml/> Accessed
Nov 18 2016.
Osborne, B., Mcwillians J., Beyer B. and Saltonstall M.,
2016, BeyondCorp: Design to Deployment at Google,
;login, Vol 41, No. 1, pp. 28-34, Spring 2016.
Vensmer, A. and Kiesel, S. 2012, DynFire: Dynamic
Firewalling in Heterogeneous Networks, Proceedings
World Congress on Internet Security (WorldCIS),
2012, Pages: 57 - 58.
Ward, R. and Beyer, B., 2014., BeyondCorp: A New
Approach to Enterprise Security, ;login: December
2014.
Watters, J., Morrisey, S., Bodeau, D., Powers, S.C., 2009
The Risk-to-Mission Assessment Process (RiskMAP):
A Sensitivity Analysis and an Extension to Treat
Confidentiality Issues, The Mitre Corporation
Research Report 09-2994, July 2009.
Zhang. B. Al-Shaer E., Jagadeesan R., Riley J., Pitcher C
2007, Specifications of a high-level conflict-free
firewall policy language for multi-domain networks,
SACMAT 2007, Proceedings of the 12th AC
Symposium on Access Control Models and
Technologies, pp. 185-194.
Situational Awareness based Risk-adaptable Access Control in Enterprise Networks
405
