
Area Coverage Optimization in Wireless Sensor Network by
Semi-random Deployment
Adda Boualem
1
, Youcef Dahmani
2
, Abdelkader Maatoug
2
and Cyril De-runz
3
1
The High National School of Computer Science, ESI, Algiers, Algeria
2
The EECE Lab, Ibn Khaldoun University, Tiaret, Algeria
3
The CReSTIC, University of Reims Champagne-Ardenne, Reims, France
Keywords:
Semi-random Deployment, Area Coverage, Power Consumption, Wireless Sensor Network.
Abstract:
Area Coverage is a difficult problem to solve with a minimum number of sensor nodes for maximum time
duration, especially in wide areas. Among the solutions proposed for this problem there is the deployment
with its two types random and deterministic. The disadvantages of deterministic deployment are configured in
the Area of Interest (AoI) limitation, and random deployment is configured in the non-equitable distribution
of sensor nodes on AoI. This problem affects power consumption and connectivity; as a result, it affects the
coverage of the area of interest. In this paper we have proposed a third type of hybrid deployment that gathers
the advantages and minimizes the disadvantage of the application of the random deployment and deterministic
deployment. This type has two steps; the anticipate configuration step and the scheduling process step. A
comparative study was done to show the effectiveness of this type to optimize coverage in the vast area of
interest less danger and more interests.
1 INTRODUCTION
The advancement in Micro Electro-Mechanical Sys-
tems (MEMS) technology has lead to production of
thin, cheaper and reliable sensors nodes. A network
of sensors suffers from several technical weak points
such as communication range, monitoring range, low
battery, and network deployment circumstance prob-
lems such as the difficulty of building a sensor net-
work in volcanoes, mountains, or in the oceans. The
deployment with its two types considered a very ef-
fective solution to optimize the problem of coverage
in networks of wireless sensors, power consumption,
routing, connectivity, and others. Deterministic de-
ployment is effective in very limited areas where man
can intervene to troubleshoot, configure, change bat-
teries, and replace or move nodes. Random deploy-
ment is effective in unrestricted areas where human
intervention is impossible or difficult. Advancement
in MEMS technology has lead to production of very
thin sensor nodes that are less expensive and yet pow-
erful in terms of storage and processing. Increasing
network lifetime by keeping the entire coverage of the
area of interest is one of the compromises desired by
researchers in their work using deployment. Among
the disadvantages of this solution for the random type
are the non-equitable distribution of the sensor nodes
and the difficulty of applying the process of activating
sensor nodes in the network. The necessity of know-
ing positions (best distribution) and remote-control in
geographical areas is mandatory, where human inter-
vention is difficult in certain danger zones. In this
paper, we have defined a new type of deployment
known as the semi-random deployment. This deploy-
ment uses deterministic advantages like knowing the
distribution of positions. It also employs random de-
ployment mechanisms of dispersing nodes randomly.
The semi-random deployment protocol consists of
two steps i.e, the anticipate configuration step and the
scheduling process step. The anticipate configuration
step consists of the configuration of certain necessary
parameters and storing them in the memory only once
for the used in the nodes scheduling process. Our sim-
ulations showthat, the semi-random deploymentis ef-
ficient compared to existing methods of deployment.
The rest of this paper is organized as follows. Section
2 formally defines the problem. Sections 3 reviews
some related work. Sections 4 proposes our sensor
deployment type. Simulation results are presented in
Section 5. The Results Analysis are discussed in Sec-
tion 6. Finally, the Conclusion is drawn in Section
7.
Boualem, A., Dahmani, Y., Maatoug, A. and De-runz, C.
Area Coverage Optimization in Wireless Sensor Network by Semi-random Deployment.
DOI: 10.5220/0006581900850090
In Proceedings of the 7th International Conference on Sensor Networks (SENSORNETS 2018), pages 85-90
ISBN: 978-989-758-284-4
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
85

2 RELATED WORK
Currently, the use of wireless sensor networks is
a major need in various surveillance applications,
such as monitoring applications in; the environment,
battlefields, borders, forests, intelligent spaces, and
in the control of industrial and biological disasters.
The main objective of using of the wireless sensors
network is how to monitor with sufficient coverage
an area of interest with a fewer sensor nodes in a
longtime (cardie and Wu, 2004), (C.-F and Tseng,
2005).The guarantee of the perfect coverage leads
to guarantee the connectivity of the area of inter-
est (AoI). Coverage is difficult to control, measured
and guaranteed using a minimal number of sensors
nodes deployed on AoI; so, coverage is an optimiza-
tion problem. Deployment is one of the solutions
proposed to solve this problem. Deterministic de-
ployment is preferred in areas where human inter-
vention is possible to; replace, or to change sensor
nodes. On the other hand; random deployment is nec-
essary in the terrain that represents the danger and
the impossibility of the intervention of the human be-
ing. The treatment of the deployment-based cover-
age problem is extensively addressed using different
domains strategies as: using the scheduling process
between the Active / Passive states of the nodes in
the network (M. Zaied, 2003), using the geometric
angles and distances between the nodes (Aurenham-
mer, 2001), using the disjoint dominating setsand grid
strategies (Shen and Sun, 2006), using the Voronoi
diagram and the Delaunay triangulation (Aurenham-
mer, 2001), using the heuristics (M. Zaied, 2003), and
others technics . (Wen-Hwa Liao, 2001) Presents the
Glowworm Swarm Optimization (GSO) protocol; a
new system process based on random deployment to
improve of the nodes coverage. GSO protocol con-
siders each node as a single glowworms transmitter
and luminant substance like ”luciferin”. The luciferin
force considered as the link between the transmit-
ter node and its neighboring sensors. A sensor node
move to the low-density area if necessary. A cover-
age maximization was achieved when a sensor node
can move to the low-density area. The disadvantage
of GSM is that the nodes must provide by mobilizers
and a GPS position detection system, which quickly
depletes the network. (X. M. Guo, 2012) divides the
area of interest into grid and the selected sensor node
in the next round is there situated in the best case.
The goal behind this method is to select a smallest
set of nodes to guarantee the target coverage and de-
termine the precise positions for the deployed sensor
nodes in the network. This method is not efficient
in the area coverage and in the wide area where the
monitoring of each point is necessary. (Alduraibi Fa-
had and Younis, 2016) considers the coverage as an
optimization problem, where they dress the problem
with the deployment of a smallest set of nodes to
maximize the coverage. The authors propose three
models optimization models. The first is minimiz-
ing the sensor nodes number deployed into the area
of interest to attain the high reliability level detec-
tion. The second model based on the determination
of available nodes positions with nodes number con-
strain for attain perfect coverage. The third optimiza-
tion model is to minimize the nodes number deployed
in some locations that require low coverage and ad-
just the nodes number deployed in others locations
that require higher coverage. (O. Banimelhem, 2013)
the implementation of a genetic algorithm (GA). This
algorithm specifies the positions and the number of
sensor nodes to be deployed in the zone of interest
in order to achieve optimal coverage. The applica-
tion of this algorithm overloads the nodes by calcula-
tions that always leave the nodes in active state, the
thing that quickly exhausts the network. The remedy
proposed for this is the repetitive deployment of sen-
sor nodes in locations where coverage has reached a
minimal threshold, which is not always possible es-
pecially in danger zones. In (Shen and Sun, 2006),
the different strategies are used to maximize cover-
age in WSN. These strategies are classified into three
categories: (a) Force Based, (b) Grid Based, and
(c) Geometry Computational Based. Force-based de-
ployment strategies depend on the mobility of sen-
sor nodes, where; Sensor nodes are forced to move
away or approach each other until they reach the per-
fect coverage. The Force Based strategy uses a vir-
tual force as a repugnant and attractive force. The
study in (Howard and Sukhatme, 2002) considers
that AoI contains sensor nodes and objects that ex-
ert a virtual repulsive force to move the sensor nodes
away from the objects and also from each other so
that their surveillance areas do not overlap. The sen-
sor nodes will continue to move until they reach the
steady state in AoI. This strategy provides coverage
and connectivity on AoI, but it is extremely depen-
dent on mobility and complex computations, which
quickly depletes the network. The grid-based deploy-
ment strategy consists of determining the precise po-
sitions of the sensors. This is the strategy in which the
coverage is evaluated as the ratio between the points
of the covered grid and the total number of points of
the grid in the AoI. The accuracy of the assessment
is determined by the size of each grid, the smallest
in size is the most accurate in the assessment. (Shen
and Sun, 2006) mentions three types of grids used
in the deployment to provide the best coverage; (A)
SENSORNETS 2018 - 7th International Conference on Sensor Networks
86
Triangular grid, (b) Square grid, and (c) Hexagonal
grid. The triangular strategy is the best type because
it is the smallest area of overlap, so fewer sensors,
then the other types (Sanjay Shakkottai, 2003), and
the hexagonal grid is the worst of all, since it has
the largest area Overlap. Computational geometry is
frequently used to optimize coverage in WSN, (Au-
renhammer, 2001) mentions two geometric computa-
tional approaches used in deployment to provide the
best coverage; (A) Voronoi diagram, and (b) Delau-
nay triangulation. The Voronoi diagram is the divi-
sion of the area of interest on locations (sites) so that
the points in a polygon are closer to the site in the
polygon than the other sites. The Voronoi diagram
can be used as a sampling method to determine cov-
erage, and measure the holes of in WSN; the sensors
act as sites, if all vertices of the Voronoi polygons are
covered, then the AoI is fully covered, otherwise the
coverage holes exist. The Delaunay triangle is formed
by three sites provided if and only if the sites (Wang
and Porta, 2003) circulate do not contain other sites.
Delaunay triangulation coverage strategy: it is fre-
quently used in coverage optimization in WSN. The
Delaunay triangulation is used to evaluate the worst
and best case of coverage (Megerian and Srivastava,
2005). The complexity of these approaches lays in the
use of computational complexity geometry methods,
which quickly depletes the network.
In (Faten Hajjej and Zaied, 2016), a Flower Polli-
nation Algorithm (FPA) was introduced as a solution
for deployment and coverage problem. A deployment
approach based on FPA was proposed for the sensor
placement problem for WSN. This approach can find
the optimal placement topology in terms of Quality of
service (QoS) metric. But FPA uses too many param-
eters to calculate for specify the positions of active
nodes, which quickly depletes the network.
3 ASSUMPTIONS
To apply our strategy of area coverage in large areas,
which consists of using semi-random deployment by
mixing between the two types (random and determin-
istic), we took into consideration the following as-
sumptions:
1. The subdivision of AoI under sub-areas, in order
to cover the vast areas well, to achieve an equi-
table distribution of the nodes in the geographical
area, to control connectivity, and to conserve en-
ergy consumption in the network.
2. The deployment of a large number of sensor nodes
on each sub-area (sub-zone) by a device on a
height a little lower and in calm circumstances
around each of the sub-zones z
i
, in order to guar-
antee a good distribution in the network.
3. The nodes used in our study are of two types; the
first type is made to have a storage memory more
than the ordinal nodes, the second type has the
same characteristics of the first but a little heavy
than the nodes of the first type.
4 DESCRIPTION OF OUR
APPROACH
Our protocol consists of two main steps, the anticipate
configuration step and the scheduling process step.
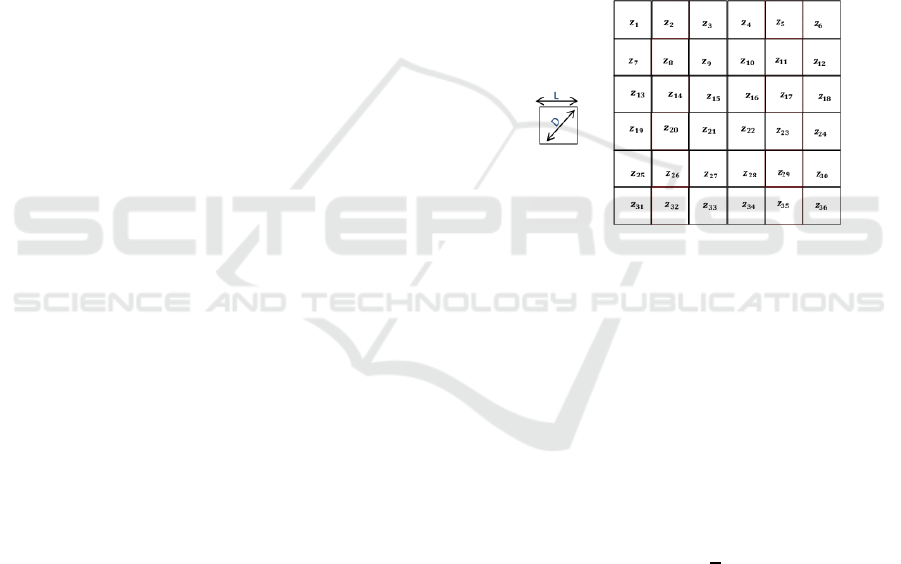
Figure 1: (a) one sub-area, and (b) subdivision of AoI in n
sub-areas.
4.1 Anticipate Configuration Step
The area of interest must be divided geographically
by n sub-areas of dimension L×L and diagonal D, as
shown in Figure1. Anticipate configuration consists
of the following steps:
1. The communication radius R
c
, and monitoring ra-
dius R
s
have the following features:
R
c
= R
s
(1)
R
c
=
√
2×L (2)
We have taken the case where the communication
radius equals the surveillance radius, as shown
in relation to equation (1). For a single sen-
sor node to be able to fully cover the sub-area
that belongs to it and communicate the collected
data to the base station, the communication ra-
dius and the monitoring radius would have to be
1.42×(thesub−areaside) , As the relation (2).
2. The nodes used in this study are homogeneous
and endowed with a memory capable of storing
the following parameters:
Area Coverage Optimization in Wireless Sensor Network by Semi-random Deployment
87
• T
act
: Contains the duration of activation or the
time of one revolution.
• T
att
: Contains the time to wait for the confirma-
tion message by the node that will be active in
the next round. The time T
att
, T
act
(the waiting
time is less than the activation time (the time of
one round)) .T
att
,T
act
times are chosen accord-
ing to the confidentiality of the task to be per-
formed and the danger of the zone.
• Num: Contains the number of the node, this pa-
rameter is unique for each node, varied by 1..n.
For each sub-area.
• Num −zone: Contains the number of the sub-
zone (sub-area) to be deployed.
• Each node N
i
has the ability to generate a ran-
dom number ρ
i
,
• A special node Nsp
i
(sink
i
), it was manufac-
tured for each sub-zone z
i
, must be heavier
compared to the other nodes of z
i
, to fall around
the center at the time of deployment. This node
must be programmed to be active at the time of
their arrival on z
i
to allow selecting their neigh-
boring nodes by sending a message Hello. The
other objective of this sink is the communica-
tion of all data collected to the main base sta-
tion (BS).
4.2 Scheduling Process Step
The scheduling process step consists of the following
steps:
1. All nodes are passive after deployment except the
sinks (special nodes).
2. The special node Nsp
i
(sink
i
) sends a message
Hello contains the parameter Num −zone to the
neighboring nodes, and aims to know the nodes
that belong to its own sub-zone. The recipient
nodes update their old Num −zone (ie become
neighbors of the new Nsp
i
).
3. In the first round, the node Nsp
i
generates a ran-
dom number ρ
i
and determines the next active
node in its own subarea to act as the coverage
and transmission of the data harvested according
to the following formula:
N
i
= [ρ
i
×n
i
] (3)
Such as:
• The generate number ρ
i
/ ρ
i
∈]0..1[ , and
• n
i
represents the total number of nodes de-
ployed in the appropriate sub-zone z
i
.
• [ρ
i
×n
i
] represents the integer part of the calcu-
lated number n
i
×n
i
.
4. The node selected to be active in the next round
must activate their transmitter and respond with
a confirmation message to the transmitter node (a
Hello message contains the number of the trans-
mitter node). If the transmitter node has not re-
ceived the confirmation message in a time T
att
, the
latter will remain active until the final exhaustion
of their battery.
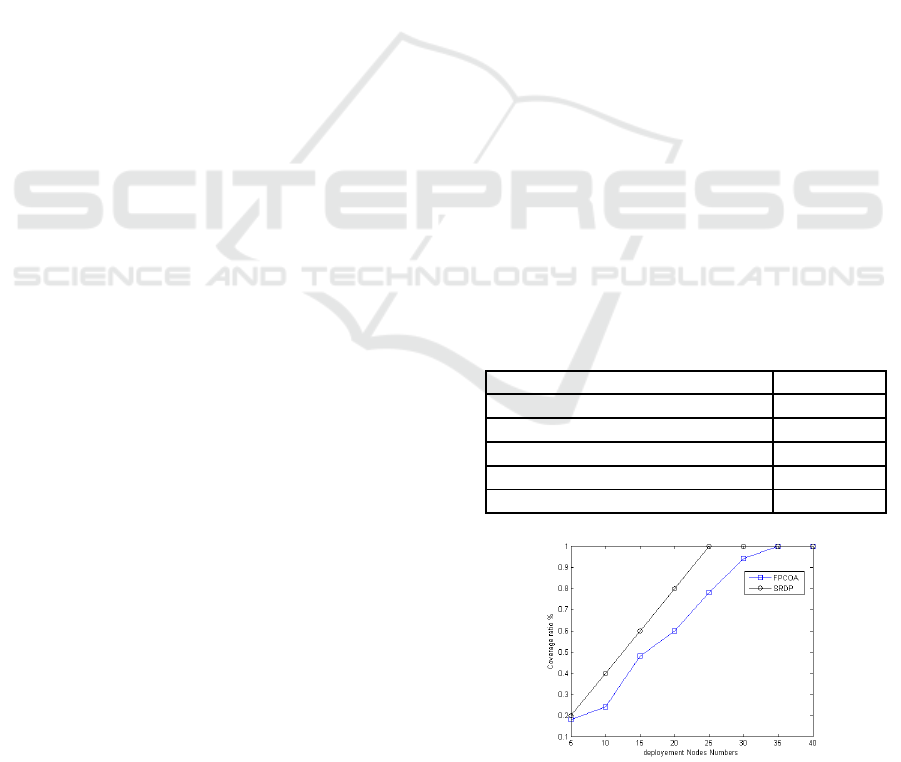
5 SIMULATION
We compared this type of deployment with the pro-
tocols that use deployment and the Active / Passive
scheduling process in this case study. The data used
in this evaluation are recorded in Table1.
To compare our protocol called Semi-Random De-
ployment Protocol (SRDP) with the protocol named
Flower Pollination Coverage Optimization approach
(FPCOA) cited in (Faten Hajjej and Zaied, 2016),
and mount our improvements over it; we took the
same simulation data cited in (Faten Hajjej and Zaied,
2016).The deployment of a number of sensor nodes
between 5 and 40; and an area of interest of dimen-
sions 50m 50m; to measure the coverage ratio, and
thus to calculate the energyconsumed duringthe 1000
registered primary time units.
To apply our protocol, we divide the area of inter-
est into L-side of sub-areas such that: L = R
c
/1.42 =
15/1.42 = 10.56m ie: 25sub −areas. The results of
simulation are shown in Figure2 and Figure3.
Table 1: Common data used in the simulations.
Configurations Value
Area of Interest (AoI) 50m×50m
Communication Radius (R
c
) 15m
Sensing Radius (R
s
) 15m
Deployed Sensor Nodes Number 5to40
Time Units 1000units
Figure 2: The Comparison of Coverage Ratio with SRDP
and FPCOA protocols.
SENSORNETS 2018 - 7th International Conference on Sensor Networks
88
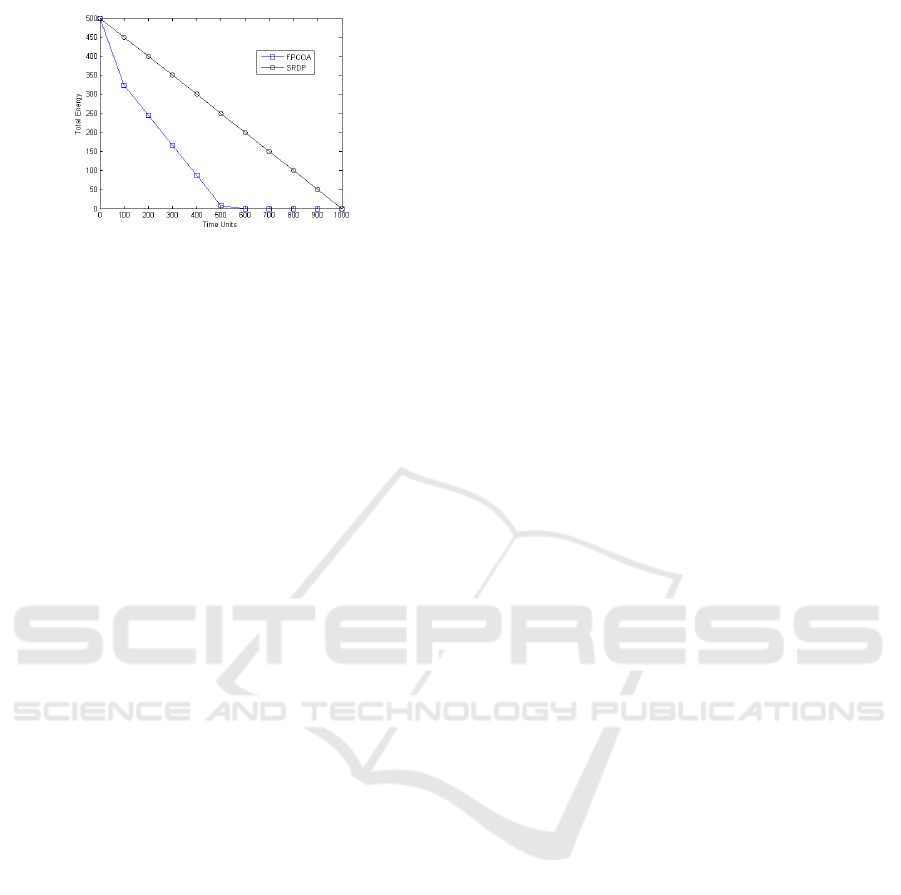
Figure 3: The Comparison of total energy consumption with
SRDP and FPCOA protocols.
6 RESULTS ANALYSIS
We simulated the total energy consumption data, thus
the coverage ratio in the network for both protocols,
the Semi-Random Deployment Protocol (SRDP) and
the Flower Pollination Coverage Optimization Ap-
proach (FPCOA).
6.1 In Terms of Coverage
The SRDP protocol arrives at a ratio of 1 if the num-
ber of nodes deployed reaches 25. On the other hand,
the coverage ratio by applying FPCOA arrives at 1 if
the number of nodes arrives at 35 nodes as shown in
Figure2; Which shows a gain at the minimum sensor
node number that can be deployed to achieve a per-
fect coverage of the area of interest. In addition, the
network keeps a perfect coverage lifetime more than
applies the protocol FPCOA; Because SRDP uses
the clustering concept with the activation of a single
Cluster-Head by a Cluster to act as a monitoring and
communication role of the data captured at the base
station.
6.2 In Terms of Energy Consumption
Figure3 shows an equitable energy consumption in
the network by the application of the SRDP, modeled
and proved by the function Y = 500−X. On the other
hand, the graph representing the energy consumption
of the FPCOA isa graph of the fractions; which shows
unfair energy consumption in the network. Figure3
shows that the network is exhausted during the 500
prime time units if by applying the FPCOA; On the
other hand the network consumes half of their total
energy in this time, and it happens to consume their
total energy during the 1000 units of prime time. This
shows the effectiveness of SRDP versus FPCOA.
6.3 The Advantages of this Strategy
Compared to the Previous
Scheduling Strategies
1. Not interested in the number of turns for the ap-
plication of the active / passive process made by
each node in the network.
2. Not interested in implementing a process to select
the nodes of each subfield (of each cluster) that
overloads the node processor and wastes energy
and time.
3. Not interested in knowing geographical position,
as a result do not need a location system like GPS
except in the initial deployment step (anticipate
configuration step).
4. Activate a single node in each sub-zone to bal-
ance the network in terms of power consumption,
guarantee connectivity, and increase the network
lifetime.
5. Activation of a single node per sub-zone guaran-
tees full coverage of the area of interest for maxi-
mum time without having to implement strategies
for measuring coverage.
6. Each asset plays a dual role; a monitoring role and
a communication role.
7. The compromise between the two types of de-
ployment brings benefits and minimizes their dis-
advantages.
7 CONCLUSIONS
In this paper, we proposed a new type of deployment
based on anticipate configuration that serves to ini-
tialize some parameters help to balance energy con-
sumption, offer connectivity and serves in the entire
coverage of the area of interest, thus helps to avoid the
different scheduling process and clustering processes
used in the sensor network implementation without
affecting the connectivity. The subdivision of the area
of interest in small areas of diameter equal to the mon-
itoring radius R
s
, and putting R
s
= R
c
provides fair re-
source consumption in the network, thus guaranteeing
connectivity in AoI throughout the network lifetime.
The generation of a random number by each node
helps to select the next active node for each subfield
without the need for different active / passive mecha-
nisms used for this purpose. Using memory settings
helps to avoid too much computation and to save en-
ergy. The coverage considering R
s
= R
c
is shown
to be effective in area coverage when we subdivide
Area Coverage Optimization in Wireless Sensor Network by Semi-random Deployment
89

the AoI in subareas of diameter D, (R
s
= R
c
= D), in
contrast in previous protocols proposed in (Faten Haj-
jej and Zaied, 2016), (Yang, 2012).The only inconve-
nient is the use of memory parameters that it will be
processed in the upcoming works.
REFERENCES
Alduraibi Fahad, N. L. and Younis, M. (2016). Coverage-
based node placement optimization in wireless sen-
sor network with linear topology. In (ICC), C., editor,
IEEE International Conference on. IEEE. IEEE Inter-
national Conference on. IEEE.
Aurenhammer, F. (2001). Computational geometry : Some
easy questions and their recent solutions. Journal of
Universal Computer Science, 7(5).
C.-F, H. and Tseng, Y.-C. (2005). A survey of solutions
to the coverage problems in wireless sensor networks,
journal of internet technology. Journal of internet
Technology, 6(1):1–8.
cardie, M. and Wu (2004). Coverage problem in Wireless
Ad Hoc Sensor Networks, Handbook of Sensor Net-
works, chapter 19. CRC Press.
Faten Hajjej, R. E. and Zaied, M. (2016). An efficient
deployment approach for improved coverage in wire-
less sensor networks based on flower pollination algo-
rithm. pages 117– 129. Computer Science and Infor-
mation Technology (CS and IT).
Howard, A., M. M. and Sukhatme (2002). Mobile sen-
sor network deployment using potential fields: A
distributed, scalable solution to the area coverage
problem. In 6th International Symposium on Dis-
tributed Autonomous Robotics Systems, pages 299–
308, Fukuoka, Japan.
M. Zaied, C. Ben Amar, M. A. A. (2003). Award a new
wavelet based beta function. In International con-
ference on signal, system and design, SSD03 1, vol-
ume 1, pages 185–191.
Megerian, S., K. F. P. M. and Srivastava, M. (2005). Worst
and best-case coverage in sensor networks. In IEEE
Transactions on Mobile Computing, volume 1, pages
84 – 92. IEEE CS, CASS, ComSoc, IES, and SPS.
O. Banimelhem, M. Mowafi, W. A. (2013). Genetic algo-
rithm based deployment in hybrid wireless sensor net-
works. Communications and Network.
Sanjay Shakkottai, R. Srikant, N. S. (2003). Unreliable sen-
sor grids: Coverage, connectivity and diameter. In
Twenty-Second Annual Joint Conference of the IEEE
Computer and Communications Societies, volume 2,
pages 1073–1083, Austin TX, USA.
Shen, X., C. J. W. Z. and Sun, Y. (2006). Grid scan: A sim-
ple and effective approach for coverage issue in wire-
less sensor networks. Istanbul, Turkey. Communica-
tions, 2006. ICC 06. IEEE International Conference.
Wang, G., C. G. and Porta, T. (2003). A bidding protocol for
deploying mobile sensors network protocols. In 11th
IEEE International Conference on Network Protocols,
pages 315 – 324.
Wen-Hwa Liao, Yucheng Kao, Y.-S. L. (2001). A sensor
deployment approach using glowworm swarm opti-
mization algorithm in wireless sensor networks. EL-
SEVIER Journal, Expert Systems with Applications,
38(10):12180–12188.
X. M. Guo, C. J. Zhao, X. T. Y. e. a. (2012). A deterministic
sensor node deployment method with target coverage
based on grid scan. Chinese Journal of Sensors and
Actuators, 25(1):104–109.
Yang, X.-S. (2012). Flower pollination algorithm for global
optimization. In on Unconventional Computing, I. C.
and Computation, N., editors, Flower Pollination Al-
gorithm for Global Optimization, volume 7445, pages
240–249.
SENSORNETS 2018 - 7th International Conference on Sensor Networks
90
