
Novel Access Control Approach for Inter-organizational Workflows
Asmaa El Kandoussi and Hanan El Bakkali
Information Security Research Team, ENSIAS, Mohammed V University, Rabat, Morocco
Keywords:
Access Control Policy, Inter-organizational Workflows, Conflict Resolution.
Abstract:
Inter-organizational workflows have become increasingly used by companies to improve their productivity by
sharing resources and activities. These systems have proven their effectiveness in several areas. However, the
sensitivity of the exchanged data, push participating organizations to set authorization rules in order to protect
their data and processes. At this level, the cohabitation of different security policies arises as a problematic
issue. In fact, how can we combine different or even conflicting policies with regard to privacy preserving and
collaboration objectives?
In this paper, we propose a new Inter-Organizational Workflow Based Access Control (IOW-BAC) approach.
Besides, we present a new algorithm to resolve potential detected conflicts occurring during the composition
of the global Access Control policy. This algorithm is based on a set of important parameters which are
organization’s weight, object owner, task criticality and object sensitivity.
1 INTRODUCTION
Currently, Workflow Management Systems (WfMSs)
(Specification, 1999) are increasingly used by compa-
nies to manage their activities through the creation of
intra and inter-organizational workflows.In fact, the
internet and business globalization greatly rise the
creation of inter-organizational workflows. These col-
laborative workflows allow organization to share re-
sources and complete common activities. However,
this collaboration poses new security challenges and
access control is the most crucial one. For that pur-
pose, many access control models exist in the litera-
ture, the most common and used model is Role-based
access control (RBAC)(Sandhu et al., 1996). By
granting permissions to roles played by users rather
than to users themselves, it has greatly facilitated the
access control administration in companies. However,
it was difficult for RBAC to satisfy the WfMSs secu-
rity requirements . Thus, many works was raised to
bridge this gap such as; Task Based Access Control
(TBAC) (Thomas and Sandhu, 1998) where permis-
sions are assigned to tasks and users can only get the
permissions within the execution of tasks. Authors
in (Atluri and Huang, 2000) added time constrains
in their proposed solution Workflow Authorization
Model (WAM) ; In Task-Role-Based Access Control
(T-RBAC) (Oh and Park, 2003), authors add tasks into
RBAC model, T-RBAC made permissions to be asso-
ciated with tasks directly. Nevertheless, these mod-
els are more suitable for the centralized environment.
On the other hand, many other researches ((Le et al.,
2012),(Gouglidis and Mavridis, 2012),(Yang and Liu,
2012),(Wang et al., 2015)) were presented for dis-
tributed environment.
However, and to the best of our knowledge, none of
the existing models propose an adequate model for
Inter-Organizational Workflows, especially, the co-
habitation of multiple access control policies of par-
ticipating organization in the global workflow with
the respect of organization autonomy and data secu-
rity. In fact, each organization has local access control
policy; the problem that arise is how to combine dif-
ferent or even conflicting access control policy rules.
Yet, the challenge is to resolve potential conflicts and
generate global access control policy . Few works
devote the concern of conflict in distributed collab-
orative workflows such as ((Duan et al., 2015),(Ma
et al., 2009),(Wang et al., 2010),(Hu et al., 2013)).
However, they overlook how multiple access con-
trol policies can compose global access control pol-
icy . For that purpose, we propose a new approach
named Inter-organizational Workflow Based Access
Control model (IOW-BAC) that extends the RBAC
model with the introduction of a new concepts and
associations. Besides, we present a new algorithm to
resolve potential detected conflicts occurring during
the composition of the global Access Control policy.
This algorithm is based on a set of important parame-
ters which are organization weight, object owner, task
kandoussi, A. and bakkali, H.
Novel Access Control Approach for Inter-organizational Workflows.
In Proceedings of the 4th International Conference on Information Systems Security and Privacy (ICISSP 2018), pages 345-352
ISBN: 978-989-758-282-0
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
345

criticality and object sensitivity.
The rest of the paper is organized as follows: Sec-
tion 2 presents the main access control requirements
in the inter-organizational workflows followed by re-
lated works in section 3. Section 4 details our pro-
posed Inter-organizational Workflow Based Access
Control (IOW-BAC) approach. The global access
control policy composition was explored in section 5
. Section 6 presents un illustrative example. The last
section concludes the paper with future works.
2 THE MAIN ACCESS CONTROL
REQUIREMENTS
Many access control requirements have to be consid-
ered in Inter-organizational workflows. Among the
main needs are policy cohabitation, privacy preserv-
ing and role mapping. Other specific requirements are
presented in our previous works(Elkandoussi and El-
bakkali, 2014),(Elkandoussi et al., 2015) :
1. Policies cohabitation: Policies cohabitation aim
to conciliate different or even conflicting access
control policies, and resolve detected conflicts. In
fact, each organization must be able to protect its
own data while respecting the global security pol-
icy of the global workflow.
2. Privacy preserving: Privacy arises as a major con-
cern in todays collaboration. In fact, how to use
suitable control to preserve privacy and perform
cooperation needs.
3. Role mapping: role equivalence among different
domains by mapping a local role to its equivalent
global role.
4. Inter-organizational security contracts: To govern
collaborations, security contracts are established.
They aim to detail the objectives and tasks to be
achieved, to attribute responsibilities to each party
and to specify penalties in case of abuses.
5. Workflow Satisfiability: When different policies
are combined potential conflicts may occur. Such
situation may cause the workflow incompleteness.
The challenge is to guarantee the workflow com-
pleteness with the respect of the global access
control policy.
In order to guarantee a secured environment for
participating organizations in the global workflow, the
above-mentioned requirements should be considered.
3 RELATED WORKS
There are several models that have been proposed for
distributed enviremenents. Among these models we
highlight the following.
An enhanced RBAC was proposed in (Le et al., 2012)
to facilitate information access management in the
context of team collaboration and workflows. Au-
thors in (Gouglidis and Mavridis, 2012) present a
new access control model for collaborative applica-
tions capable to support collaboration under secure
interoperation and cardinality constraints. In (Yang
and Liu, 2012), an extented model GT-RBAC (Group-
Task-Role-Based Access Control) was explored. GT-
RBAC introduces organization unit and hierarchies
into T-RBAC model. Also, the authors present a
new algorithm to meet the requirement of dynamic
rights constraints of workflow. In (Wang et al., 2015),
the proposed model combines Task and Role-based
Access Control with multi-constraint. In the model,
workflow is broken down into tasks, which are di-
vided into public tasks and private tasks. It defines the
mutually exclusive roles and binding tasks and formu-
lates dynamic users allocation policies by establishing
a users execution history table to improving the effi-
ciency.
As mentioned before, the policies cohabitation is one
of the main security requirements that should be re-
spected. Yet, in the litterature few works devote the
concern of conflict in distributed collaborative work-
flows. Authors in (Duan et al., 2015) present an au-
tomated policy combination for data sharing across
multiple organizations. They made it possible by
adopting bottom-top approach in the decomposition
of the policy rules into different classes based on the
subject constraints; each rule in a class that has the
same subjects is combined by the condition-based at-
tribute combination based algebraic operations. Their
proposed approach makes the combined policy more
restrictive, that is, the combined policy permits a re-
quest when all the policies permit it, denies a request
when any one of policies denies it. Unlike our so-
lution that take into account multiple parameters to
prioritize rules. In (Ma et al., 2009), authors propose
conflict detection and resolution in WFMSs. In this
work, authors define a set of rules to detect and re-
solve static and dynamic conflict. Furthermore, they
classify conflicts into two categories (i) policy-policy
conflicts which occur when two or more authorization
policies are considered incompatible, (ii) policy con-
straint conflicts which occur when the performance of
two or more authorization policies will lead to situa-
tions that are prohibited by other constraints in the
system. The proposed solution is based on prece-
ICISSP 2018 - 4th International Conference on Information Systems Security and Privacy
346

dence rule priority which defines the order of priority
to resolve conflict. In (Hu et al., 2013), a purpose-
based access control model was presented in orderto
preserve privacy, also a new algorithm was described
to resolve conflicting policies based on purpose.The
key component is purpose involved in access control
models for expressing privacy-related policies. Nev-
ertheless, authors did not present how to resolve inter-
organizational policies conflict. In the context of On-
line Social Networks, authors in (Hu et al., 2013)
, present a multiparty access control model to cap-
ture the essence of multiparty authorization require-
ments, also they propose Multiparty Policy Evalua-
tion Process that include two steps and propose sys-
tematic conflict resolution mechanism to resolve con-
flicts during multiparty policy evaluation. Several
solutions were proposed to resolve potential conflict
such Threshold-based conflict resolution, Strategy-
based conflict resolution with privacy and Decision
Voting.
In the literature, there are many works that enhance
the existing models and propose a new extended ap-
proach to support the distributed access control need.
Yet, to my knowledge, none of them presents how
to conciliate multiple access control policies and cre-
ate global one free of conflicts in the context of dis-
tributed workflow. Furthermore, our proposed ap-
proach define a new associations and entities to meed
inter-organizational workflows requirements.
4 PROPOSED
INTER-ORGANIZATIONAL
WORKFLOW ACCESS
CONTROL APPROACH
From the security point of view, the creation of new
global security policy that respects organizations se-
curity concerns is a critical requirement. Neverthe-
less, the enforcement of access control policy in inter-
organizational workflows may cause the incomplete-
ness of the workflow. In fact, many tasks could not
be executed due to a lack of permission or policy rule
conflict. In this paper, we propose new approach to
conciliate different or even conflicting access control
policies in whole one.
Hereafter we set out assumptions concerning this
study
4.1 Preliminaries and Assumptions
In conducting this study the following assumptions
were made. It was assumed that:
• We have persistent inter-organizational work-
flow: Cooperation between partners within inter-
organizational workflows can be dynamic or per-
sistent. When collaboration is based on perma-
nent relation between known partners to satisfy a
pre-established global workflow, the cooperation
is called persistent. On the other side, the coop-
eration is dynamic, when organizations could join
or leave the coalition based on the business needs.
• Local policies are coherent: we assume that local
policies are free of conflicts.
• The initiator of the collaboration is considered as
the mean participating organization in the global
workflow.
• Organization weight can be calculated based on
specific values (trust, importance for the collabo-
ration ), or predefined by the collaborating enter-
prise as agreement. For example, the organization
who initiates the global workflow can set differ-
ent weights values to other participating entities
based on their activities dependency and organi-
zation strength in the global workflow.
• Role mapping is established between different
originations, in order to map local roles into
global roles that have the adequate permission to
execute specific global task.
4.2 Main Steps for the Proposed
Appraoch
Our approach is basically based on the definition of
cooperative tasks and global access control policy.
Different steps to create new global access control
policy are presented in our previous work (Elkan-
doussi et al., 2015), we summarize the most important
steps:
1. Workflow collaboration: In this step we identify
the participating organizations, their weights and
the global tasks assigned to each partner. We con-
sider that global tasks are atomic tasks.
2. Public access control policy: Each partner defines
how to access to his resource and under which
condition.In this step the organizations can define
the criticality parameters of their tasks and also
the sensibility levels of their shared data (defined
hereafter).
3. Security policy mapping: The security manager
must control the role mapping and policy rules
mapping in order to respect the local security poli-
cies.
Novel Access Control Approach for Inter-organizational Workflows
347

4. Access control policies cohabitation and conflict
resolution: this step aims to check different ac-
cess control policy rules issued by participating
organizations and resolve detected conflict. At the
end of this step new global access control policy
is created. Our main contribution is in this step.
5. E-contract: in order to govern the collaboration
between different organization, contact is estab-
lished.It contains the objective of the collabo-
ration, the organizations responsibilities and the
global access control policy.
At the end of the predefined phases, the policy of
global access control of the inter-organizational work-
flow will be established.
4.3 The Proposed IOW-AC Model
Each participating organization in the global work-
flow may already have adopted an access control
model. As RBAC is the most popular access con-
trol model, we assume that participating enterprises
use RBAC or TRBAC as an extension of RBAC. In
the IOW-BAC, a set of organizations participate to
a global workflow which is composed of multiple
global tasks. Each global task is assigned to global
role; global roles are mapped to local roles.
As shown in figure 1 , IOW-BAC model includes
many entity sets, as well as the relations and functions
between them, we will give the formalized definition
of IOW-BAC, only increased or changing definitions,
the local access control models deployed in partici-
pating enterprises will not be detailed.
• Entities:
Users, Roles, Global Roles, Permissions, Global
Workflow, Organizations and Global Tasks are:
1. U =
{
u
i
|
i = 1, 2, . . ., n
}
is a set of users, each
user belongs to an organization
2. R =
{
r
i
|
i = 1, 2, . . ., n
}
is a set of roles, each
role belongs to an organization
3. P =
{
p
i
|
i = 1, 2, . . ., n
}
is a set of permissions,
The permission P
i
= (Op
i
, Ob j
i
) denotes the set
of operations on objects
4. Op =
{
Op
i
|
i = 1, 2, . . ., n
}
is a set of atomic
operations on objects
5. Ob j =
{
Ob j
i
|
i = 1, 2, . . ., n
}
is a set of objects
GW =
{
GW
i
|
i = 1, 2, . . ., n
}
is a set of global
workflows
6. O =
{
O
i
|
i = 1, 2, . . ., n
}
is a set of organizations
7. GR =
{
GR
i
|
i = 1, 2, . . ., n
}
is a set of global
roles
8. GT =
{
GT
i
|
i = 1, 2, . . ., n
}
is a set of global
tasks
9. GW =
{
O, GR, GT
}
is a global workflow
We define a global task GT as GT =
{
O
t
, GT
name
, GR
t
, P
t
}
where: O
t
is a set of
all organizations that can perform the task T
GT
name
is the name of the task
GR
t
is a set of all global roles can perform the
task T
P
t
is a set of all necessary permissions to per-
form the global task GT , P
t
=
{
Op
t
, Ob j
i
}
a
set of operations actions on objects
• Associations
In addition to the existing association in the
RBAC model, we define new association for IOW-
BAC ,
1. U-O-A ⊆ U × R is User Organization Assigne-
ment, (u, o) ∈ U-O-A shows that user u is the
member of organization O
2. U-R-A ⊆ U × R is User Role Assignement
3. O-R-A ⊆ O × R is Organization Role Assigne-
ment , (r, o) ∈ O-R-A shows that role r is be-
longed to user Organization O
4. O-GW-A ⊆ O × GW is Organization Global
Workflow Assignement, (o, gw) ∈ O-GW-A
shows that organization o is participating in the
global workflow gw
5. GR-GT-A ⊆ GR× GT is the Global Role
Global Task Assignement
6. GT-O-A ⊆ GT × O is the Global Task Organi-
zation Assignement,(t,o) ∈ GT-O-A shows that
global task GT is executed by o
7. Obj-O-A ⊆ Ob j ×O is Object Organization As-
signement
8. GT-GW-A ⊆ GT × GW Global Workflow
Global Task Assignement
9. GT-P-A ⊆ GT × P is Task Permission Assigne-
ment RM (R
i
, GR
i
) define Global Roles that can
execute Global Tasks. Role mapping provides
a decentralized access control. RM (R
i
, GR
i
)
means that the Role R
i
is mapped to Global
Role GR
i
. That means that R
i
can execute GT
i
with permission assigned to GT
i
, in order to re-
spect least privilege.
• Functions
1. Roles functions: GT ∪ R ∪ GR → 2
R
f
r
(T
i
) =
{
r ∈ R
|
((T
i
, GR) ∈ RG-GT-A
∧RM (R, GR))
}
this function relies the
Role R to the global tasks T.
2. Global Tasks functions: O → 2
GT
f
t
(O
i
) =
{
t ∈ GT
|
(O
i
,t) ∈ O-GT-A
}
3. User functions: GT ∪ GR ∪ R → 2
U
f
u
(GR) =
{
u ∈ U
|
((u, r) ∈ U-R-A
∧RM (R, GR))
}
ICISSP 2018 - 4th International Conference on Information Systems Security and Privacy
348
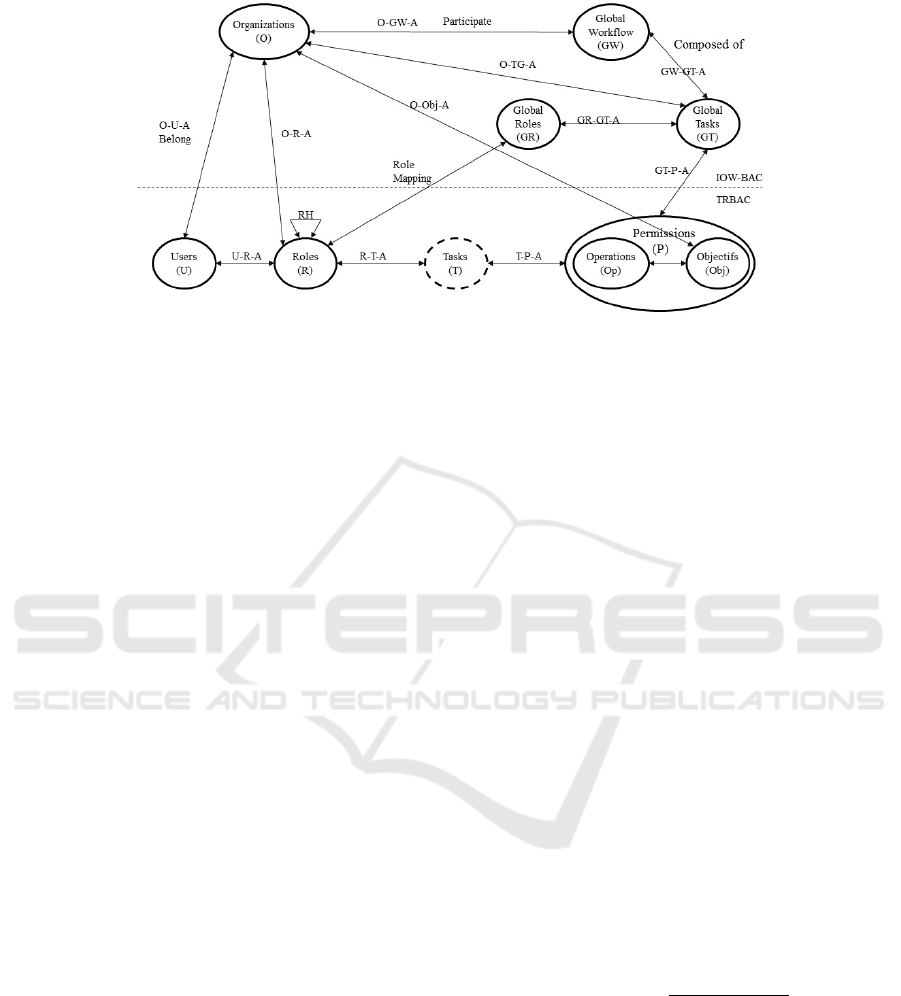
Figure 1: Proposed IOW-AC model.
f
u
(T
i
) =
{
u ∈ U
|
∃r ∈ R , (u, r) ∈ U-R-A
∧(R, GR)∧ (GR, GT ) ∈ GR-GT-A
}
f
u
(T
i
) denotes eligible users set that can
execute Global Task T.
4. Organization functions: Ob j → 2
O
f
ob j
(o
i
) =
{
ob j ∈ Ob j
|
(ob j
i
, o) ∈ Obj-O-A
}
5 GLOBAL ACCESS CONTROL
POLICY COMPOSITION
In this paper, we aim to compose global policy P
g
based on multiple public policies. A proposed ap-
proach is based on organization weight, task critical-
ity and object sensitivity.
5.1 Access Control Policy
We define access control rules in our model as AR =
{
O, GT, GR, Op, Ob j
}
Where O is organization, GT
is global task, GR is global role, in our example
role includes staffs of hospitals such as doctor and
nurse, Op is operation, Obj is an object. The AR =
{
O, GT, GR, Op, Ob j
}
indicates that any user in orga-
nization O with global role GR is authorized to ex-
ercise operation Op on object Obj when he/she per-
forms global task GT .
5.2 Criteria Specification
In our approach we define new essential criteria that
are used to resolve potential policy conflicts; organi-
zation weight, Object sensitivity level and Task criti-
cality level. We chose the main requirements in work-
flows system in order to compose coherent global ac-
cess control policy, hereafter their definition.
1. Organization weight: this parameter can be calcu-
lated based on specific values (trust, importance
for the collaboration ), or predefined by the col-
laborating enterprise as agreement. In our case
study, we assume that the organization who initi-
ates the global workflow can set different weights
values to other participating entities based on their
contribution in the global workflow. each organi-
zation has a specific value α
i
, we have
n
∑
i=1
α
i
= 1
2. Object Sensitivity Level: each organization
should specify the object sensitivity level of his
data that refers to her privacy concern. The OSL
has range between [0,1] based on the object con-
fidentiality level.
For example if the confidentiality is: High →
OSL=1 , Medium → OSL=0.5, Low → OSL= 0
The Global Object Sensitivity Level GOSL is de-
fined as the sum of each organization O
i
for a
specific data. The global Object sensitivity level
should take into account the organization weight.
Organization weights are represented as α
i
and n
is the number of participating organization in the
collaboration. A GOSL is calculated as follows:
GOSL (Ob j, O
i
) =
n
∑
i=1
(α
i
× OSL
i
)
n
∑
i=1
α
i
, i = 1, . . . , n
(1)
3. Task Criticality Level (TCL): TCL is based on the
importance of the task. Each organization should
define this parameter for a set of tasts that will ex-
ecute.
For example if importance of the task is High →
OSL=1, Medium→ OSL=0.5, Low → OSL= 0.
Organizations weight is introduced in the Global
Task Criticality Level (GTCL) .A GTCL is calcu-
Novel Access Control Approach for Inter-organizational Workflows
349

lated as follows:
GTCL (T, O
i
) =
n
∑
i=1
(α
i
× TCL
i
)
n
∑
i=1
α
i
, i = 1, . . . , n (2)
If the task is urgent, the policy should be permissive
especially in health domain
5.3 Our Proposed Conflict Resolution
Algorithm
As we defined previously, Access Control
Policy Rule in organization O
i
is AR
ih
=
{
O
i
, GT
ih
, GR
ih
, Op
ih
, Ob j
ih
}
, AR
ih
indicates that
any user in organization O
i
with global role
GR
ih
is authorized to exercise operations Op
ih
on object Ob j
ih
when he/she performs the global
task GT
ih
. Also in organization O
k
, we define
AR
km
=
{
O
k
, GT
km
, GR
km
, Op
km
, Ob j
km
}
, AR
km
indicates that any user in organization O
k
with global
role GR
km
is authorized to exercise operations Op
km
on object Ob j
km
when he/she performs task T
km
.
The algorithm 1 hereafter describes the conflict rule
detection between two different access control rules.
Algorithm 1: Conflict rule detection.
Input:
n is the number of organizations in the collaboration
AR
ih
is pol Access Control Policy Rule h in organization O
i
where AR
ih
=
{
O
i
, GT
i
h, GR
i
h, Op
i
h, Ob j
i
h
}
AR
km
is Access Control Policy Rule m in organizationO
k
where AR
km
=
{
O
k
, GT
k
m, GR
k
m, Op
k
m, Ob j
k
m
}
nb
AR
(O
i
)is the number of Access Control Policy Rule in
organization O
i
nb
AR
(O
k
) is the number of Access Control Policy Rule in
organization O
k
Output :ConfRule is a list of conflicting rules
1: for i ← 1 to n − 1
2: for k ← i + 1 to n
3: for h ← h to nb
AR
(O
i
)
4: for k ← m to nb
AR
(O
k
)
5: if (GT
ih
= GT
km
) ∧ (GR
ih
= GR
km
) ∧
(Ob j
ih
= Ob j
km
) ∧ (Op
ih
∩ Op
km
6= ∅) then
6: Con f Rule ← (AR
ih
, AR
km
)
7: else
8: m ← m + 1
9: end if
10: end for
11: h ← h + 1
12: end for
13: k ← k + 1
14: end for
15: i ← i + 1
16: end for
17: return Con f Rule ← (AR
ih
, AR
km
)
In our algorithm 1, we compare the Access Con-
trol Policy Rule two by two for all participating orga-
nizations in the collaboration. In our case the conflict
is detected if we have different set of operations for
the same global task executed by the same global role
on the same object.
Algorithm 2: Global Access Control Policy Composition.
Input:
α is the organization weight,we have α
i
> α
j
f
ob j
(O
i
) =
{
ob j ∈ Ob j
|
(ob j, O
i
) ∈ Ob j − O − A
}
fonction that return a set of objects that belong to
organization O
i
f
ob j
O
j
=
ob j ∈ Ob j
ob j, O
j
∈ Ob j − O − A
fonction that return a set of objects that belong to
organization O
j
GTCL
GT, O
i
, O
j
is Global Task Critical-
ity Level
|
| GTCL is define in section X,
GTCL
GT, O
i
, O
j
=
(α
i
TCL
i
(GT )+α
j
TCL
j
(GT ))
α
i
+α
j
GOSL
Ob j, O
i
, O
j
is Global Object Sensitiv-
ity Level
|
| GOSL is define in section XX,
GOSL
Ob j, O
i
, O
j
=
(α
i
OSL
i
(Ob j)+α
j
OSL
j
(Ob j))
α
i
+α
j
Output :
AR
g
is Global Access Control Policy Rule , AR
g
=
GT, GR, Op
g
, Ob j
list ← Con f Rule
AR
i
, AR
j
1: if list 6= ∅ then
2: for each
AR
i
, AR
j
∈ list
3: if Ob j ∈ f
ob j
(O
i
) then
4: AR
g
← AR
i
|
| if the organization with
higher weight is the object owner then we prioritize its
rule and put it in the global policy
5: else
6: if Ob j ∈ f
ob j
(O
j
) then
|
| if the Obj belong
to the organization with lower weight, we have two case
7:
8: if Op
i
⊂ Op
j
then AR
g
← AR
i
9: end if
10: if Op
j
⊂ Op
i
then
11: if GTCL
GT, O
i
, O
j
>
GOSL
Ob j, O
i
, O
j
then
12: AR
g
← AR
i
|
| if the task is criti-
cal and must be executed, we prioritize the permissive
rule.
13: else GTCL
GT, O
i
, O
j
<
GOSL
Ob j, O
i
, O
j
14: AR
g
← AR
j
|
| if the object is
more sensitive and confidential we prioritize the restric-
tive rule to preserve privacy.
15: end if
16: end if
17: end if
18: end if
19: end for
20: end if
Our proposed algorithm 2, if the organization with
higher weight is the owner of the object , we prioritize
ICISSP 2018 - 4th International Conference on Information Systems Security and Privacy
350
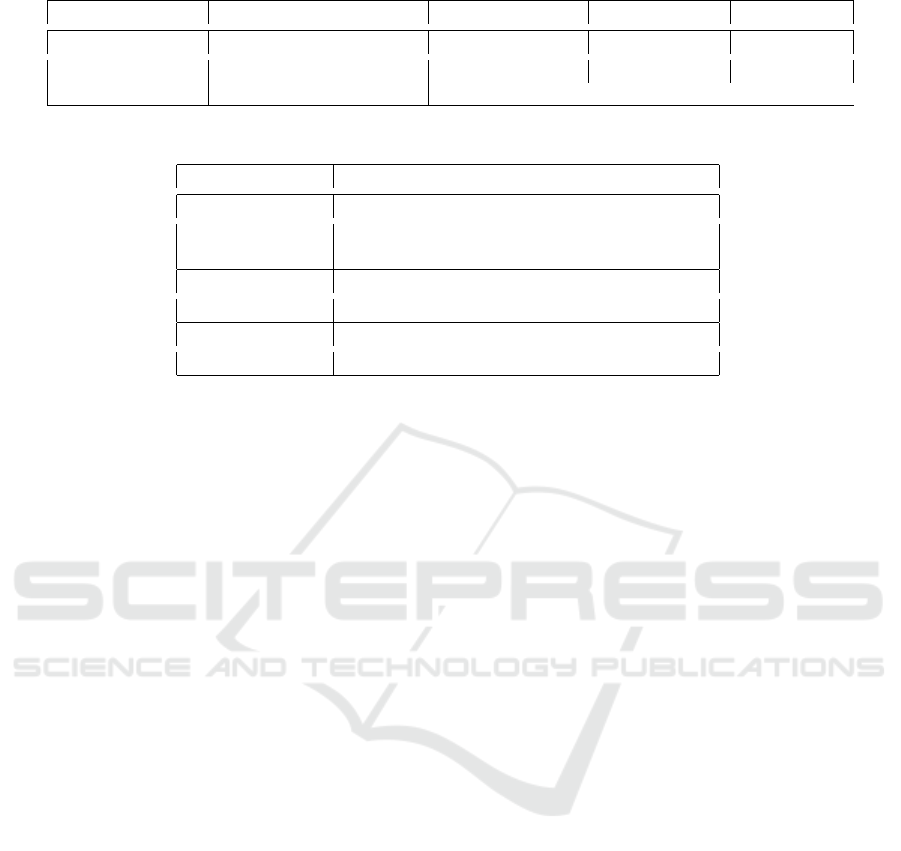
Table 1: Global Inter-Organizational Workflow specifications.
Organization O
i
Global Tasks GT Global Roles GR Operations Op Objects Ob j
O
1
= HospitalA GT
1
= radio exam GR
1
= doctor Op
1
= read Ob j
1
= F
1
O
2
= HospitalB GT
2
= blood test GR
2
= nurse Op
2
=write Ob j
2
= F
2
O
3
= Lab
1
GT
3
= ask other opinion
Table 2: Access Control Policy Rules.
Organization O
i
Access Rule
O
1
AR
11
= O
1
, GT
1
, GR
1
, (Op
1
∪ Op
2
),
AR
12
= O
1
, GT
2
, GR
2
, Op
1
, F
1
AR
13
= O
1
, GT
3
, GR
1
, (Op
1
∪ Op
2
), F
1
O
2
AR
21
= O
2
, GT
1
, GR
1
, Op
1
, F
1
AR
22
= O
2
, GT
3
, GR
1
, (Op
1
∪ Op
2
), (F
1
∪ F
2
)
O
3
AR
31
= O
3
, GT
1
, GR
1
, (Op
1
∪ Op
2
), (F
1
∪ F
2
)
AR
32
= O
3
, GT
2
, GR
1
, (Op
1
∪ Op
2
), (F
1
∪ F
2
)
its access policy rule. However, if the object belongs
to the organization with lower weight, we compare
GTCL and GOSL in order to decide which policy is
privileged. In fact, if the task is critical and must be
executed, we prioritize the permissive rule.Otherwise
, the object is more sensitive and confidential we pri-
oritize, then we prioritize restrictive rule to preserve
privacy.
6 ILLUSTRATIVE EXAMPLE
Healthcare organizations are currently facing pressure
to improve productivity and to reduce costs while at
the same time the demand for more hospital services
is increasing. In order to provide optimal care for pa-
tients, Healthcare organizations decide to use WFMSs
to establish inter-organizational collaboration. How-
ever, these systems are facing security threads and are
requiring a security mechanism, particularly access
control.
6.1 E-health Inter-organizational
Workflow Example
Hospital A would like to create an inter-
organizational workflow with other hospitals
and health centers to execute specific tasks. In fact,
Hospital A would like to create collaboration with
hospital B for the task Radio Exam and specialist
opinion, and with lab
1
for radio exam task and blood
test task ( in emergency case, overloaded work or
specific radio not covered by the hospital). On the
example mentioned before, we have the flowing AR
defined by each organization. Potential conflicts can
be detected. For example, for the task radio exam, the
doctor in O
2
can read and write in the object F
1
based
on the AR
11
, but he cannot write in F
1
based on A
21
.
6.2 Global Access Control Policy
Composition
Based on the information given by O
1
and O
2
,
we have to calculate GTCL (GT
1
, O
1
, O
2
) and
GOSL (F
1
, O
1
, O
2
) .
we assume that TCL (GT
1
, O
1
) = 0.5 ,
TCL (GT
1
, O
2
) = 0.5, OSL (F
1
, O
1
) = 1,
OSL (F
1
, O
2
) = 0.5, α
1
= 0.5, α
2
= 0.3.
we calculate the GTCL and GOSL based on equation
(1) and (2) we have:
GTCL (GT
1
, O
1
, O
2
) = 0.875, GOSL (F
1
, O
1
, O
2
) =
0.812.
Based on Global Access Control Policy Composition
algorithm, we have :
1. If F
1
∈ f
ob j
(O
1
)thenAR
g
← AR
11
2. If F
1
∈ f
ob j
(O
2
)andOp
2
⊂ Op
1
then we compare
GTCL and GOSL
In our case GTCL (GT
1
, O
1
, O
2
) >
GOSL (F
1
, O
1
, O
2
) Then AR
g
← AR
11
The proposed algorithm helps as to combine multiple
access control policy rules in order to compose global
access control policy free of conflicts. However, po-
tential conflict may persist if the participating orga-
nization did not accept the proposed solution to re-
solve it. In this case, we can go to the negotiation step
where other specific criteria should be considered.
Novel Access Control Approach for Inter-organizational Workflows
351

7 CONCLUSION AND FUTURE
WORK
In this paper, we propose a new Inter-Organizational
Workflow Based Access Control (IOW-BAC) ap-
proach. The new approach extends RBAC model with
a new entities and associations in order to support the
main requirements of distributed workflow systems.
Besides, we present a new algorithm to resolve po-
tential detected conflicts occurring during the compo-
sition of the global Access Control policy. This algo-
rithm is based on a set of important parameters. The
organization weight, the object owner, object sensi-
tivity level and the task criticality level to evaluate the
importance of the executed task.
The next stage of our work is the implementation
of our approach using the eXtensible Access Control
Markup Language (XACML) standard. Moreover, we
look to propose a new approach based on automated
negotiation.
REFERENCES
Atluri, V. and Huang, W.-K. (2000). A petri net based safety
analysis of workflow authorization models1. Journal
of Computer Security, 8(2-3):209–240.
Duan, L., Chen, S., Zhang, Y., Liu, C., Liu, D., Liu, R. P.,
and Chen, J. (2015). Automated policy combina-
tion for data sharing across multiple organizations. In
Services Computing (SCC), 2015 IEEE International
Conference on, pages 226–233. IEEE.
Elkandoussi, A. and Elbakkali, H. (2014). On access con-
trol requirements for inter-organizational workflow. In
Security Days (JNS4), Proceedings of the 4th Edition
of National, pages 1–6. IEEE.
Elkandoussi, A., Elbakkali, H., and Elhilali, N. (2015). To-
ward resolving access control policy conflict in inter-
organizational workflows. In Computer Systems and
Applications (AICCSA), 2015 IEEE/ACS 12th Inter-
national Conference of, pages 1–4. IEEE.
Gouglidis, A. and Mavridis, I. (2012). domrbac: An ac-
cess control model for modern collaborative systems.
computers & security, 31(4):540–556.
Hu, H., Ahn, G.-J., and Jorgensen, J. (2013). Multiparty
access control for online social networks: model and
mechanisms. IEEE Transactions on Knowledge and
Data Engineering, 25(7):1614–1627.
Le, X. H., Doll, T., Barbosu, M., Luque, A., and Wang,
D. (2012). An enhancement of the role-based access
control model to facilitate information access manage-
ment in context of team collaboration and workflow.
Journal of biomedical informatics, 45(6):1084–1107.
Ma, C.-h., Lu, G.-d., and Qiu, J. (2009). Conflict detection
and resolution for authorization policies in workflow
systems. Journal of Zhejiang University-Science A,
10(8):1082–1092.
Oh, S. and Park, S. (2003). Task–role-based access control
model. Information systems, 28(6):533–562.
Sandhu, R. S., Coyne, E. J., Feinstein, H. L., and Youman,
C. E. (1996). Role-based access control models. Com-
puter, 29(2):38–47.
Specification, W. (1999). Workflow management coali-
tion terminology & glossary (document no. wfmc-tc-
1011). Workflow Management Coalition Specifica-
tion.
Thomas, R. K. and Sandhu, R. S. (1998). Task-based autho-
rization controls (tbac): A family of models for active
and enterprise-oriented authorization management. In
Database Security XI, pages 166–181. Springer.
Wang, B. Y., Zhang, W. X., and Zhang, S. M. (2015). An
improved task and role-based access control model
with multi-constraint. In Applied Mechanics and Ma-
terials, volume 713, pages 2532–2535. Trans Tech
Publ.
Wang, H., Sun, L., and Varadharajan, V. (2010). Purpose-
based access control policies and conflicting analysis.
In SEC, pages 217–228. Springer.
Yang, W. and Liu, Y. (2012). An organization-based access
control model for workflow and dynamic constraints
implementation. I JACT: International Journa lof Adv
ancements in Computing Technology, 4(1):477–484.
ICISSP 2018 - 4th International Conference on Information Systems Security and Privacy
352
