
Probability Preservation Property with Relative Error and Its
Applications
Yuanyuan Gao
1,2,3
and Kunpeng Wang
1,2,3
1
State Key Laboratory of Information Security, Institute of Information Engineering,
Chinese Academy of Sciences, Beijing, 100093, China
2
Data Assurance and Communication Security Research Center, Chinese Academy of Sciences, Beijing, 100093, China
3
School of Cyber Security, University of Chinese Academy of Sciences, Beijing, 100049, China
Keywords:
Probability Preservation, R
´
enyi Divergence, Preimage Sampleable Functions, Gaussian Sampling Algorithm,
Smoothing Parameter.
Abstract:
Probability preservation property plays an important part in security proofs of lattice-based cryptography,
which bounds the closeness of two probability distributions. Recent works revolve around different measures.
We reform probability preservation properties with relative error which simplify analysis of the security re-
ductions of preimage sampleable functions (PSFs) via different measures and demonstrate R
´
enyi divergence
with order ∞ (RD
∞
) can coordinate performance with security well. We apply RD
∞
-based reduction to PSFs
over lattices, which reduces the smoothing parameter of Gaussian sampling algorithm by a factor O(
√
λ)
without security loss. We further extend the optimized parameter to the secret extraction of identity-based
encryption (IBE) over the general lattices by Gentry et al. in STOC 2008 and NTRU lattices proposed by
Ducas et al. in Asiacrypt 2014. As a consequence, the size of secret key can be shortened by a factor O(
√
λ)
accordingly.
1 INTRODUCTION
Background. An essential tool named probability
preservation property in cryptography is the use of
divergence measures to prove the security of lattice-
based cryptographic schemes. To measure the close-
ness, the classical statistical distance (SD) is naturally
adopted in probability preservation property.
As an introductory example, the SD-based pro-
bability preservation property works as follows: Let
P (Q) be the probability distributions in the real
(ideal) scheme. If the adversary succeeds with non-
negligible probability under the distribution P, and
if the SD between P and Q is negligible, then the
adversary succeeds with non-negligible probability
under the distribution Q. Similar to the case of
SD, Kullback-Leibler Divergence (KL) (P
¨
oppelmann
et al., 2014; Ducas et al., 2014) and R
´
enyi diver-
gence (RD) (Langlois et al., 2014; Bai et al., 2015;
Takashima and Takayasu, 2015; Prest, 2017) enjoy
analogical property and have been demonstrated to
enable security reductions with better parameters than
SD for search problems. A new metric called max-log
distance was introduced in (Micciancio and Walter,
2017). The new measure is closely related to the stan-
dard notion of relative error and the R
´
enyi divergence
of order ∞.
Our Contribution. The contribution of this paper
is twofold. In theory, we propose RD-based pro-
bability preservation properties with relative error in
the reduction proof of one-way preimage sampleable
functions. In practice, we improve the Gaussian sam-
pling algorithm (Gentry et al., 2008) and the secret
key extraction of the IBE scheme in (Gentry et al.,
2008; Ducas et al., 2014) with the R
´
enyi divergence.
Firstly, we explicitly express the RD-based pro-
bability preservation property with relative error by
two theorems. Our theoretical result is not limited to
the Gaussian distribution and can be extended to ot-
her distributions by means of Taylor series expansion.
Furthermore, it is convenient for analysis with our
uniform representations. We give an immediate con-
clusion that RD
∞
outperforms other measures which
enjoys both the good performance and the tight re-
duction.
Then with the above technique, we improve the
smoothing parameter of Gaussian sampling algorithm
(Gentry et al., 2008) and the secret key size of the IBE
Gao, Y. and Wang, K.
Probability Preservation Property with Relative Error and Its Applications.
DOI: 10.5220/0006717204610468
In Proceedings of the 4th International Conference on Information Systems Security and Privacy (ICISSP 2018), pages 461-468
ISBN: 978-989-758-282-0
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
461

scheme in (Gentry et al., 2008; Ducas et al., 2014). In
the security proof of the Gaussian sampling algorithm
(Gentry et al., 2008), the parameter named tolerance
in the Gaussian sampling algorithm can be relaxed,
which results in the smaller smoothing parameter by
O(
√
λ). Thus shorter vectors are outputted without
security loss. Accordingly, the user secret key size
in the IBE scheme (Gentry et al., 2008; Ducas et al.,
2014) is shortened by a factor O(
√
λ).
Paper Organization. This paper is organized as fol-
lows. In Sect 2, we introduce some basic definitions
and properties about discrete Gaussian distributions
on lattices and measures of probability distributions.
In Sect 3, We provide the security reductions of one-
way PSFs with relative error in order to give straight-
forward analysis and comprehensive comparisons. In
Sect 4, we improve the smoothing parameter of Gaus-
sian sampling algorithm and the user secret keys of
the IBE schemes over general lattices and NTRU lat-
tices. Finally, Sect 5 is the conclusion.
2 PRELIMINARIES
2.1 Notation
Some notations throughout the paper are listed below.
The security parameter is λ. A negligible function,
denoted by negl(λ), is a function f (λ) such that
f (λ) = λ
−ω(1)
. The probability 1 −negl(λ) indica-
tes that it is overwhelming. f (λ) = ω(
p
logλ) deno-
tes that f (λ) grows asymptotically faster than
p
logλ.
f (λ) =
e
O(g(λ)) denotes f (λ) = O(g(λ) ·log
c
λ). m =
poly(n) shows that m is polynomial times of n.
We denote vector by lower-case bold letters (e.g.,
v) and denote matrices by upper-case bold letters
(e.g., B). The ith column vector of a matrix B is de-
noted b
i
. For a vector v ∈ R
m
, kvk =
√
< v,v >
denotes its Euclidean norm. The norm of a ma-
trix B ∈ R
m×n
is the maximal norm of its columns:
kBk = max
n
i=1
kb
i
k.
2.2 Lattices and Gaussian
Let B = {b
b
b
1
,...,b
n
} ⊆ R
m
consist of n linearly inde-
pendent vectors. The lattice Λ generated by B is de-
fined as Λ = L(B) = {
n
∑
i=1
z
i
b
i
: z ∈ Z
n
}, where B is a
basis of the lattice, the rank of the lattice is n, and the
dimension of the lattice is m. When m = n, the lattice
is full rank. In Gaussian sampling algorithm, we work
on non-full rank lattice.
For a lattice Λ and any i ≤ n, the ith successive
minimum λ
i
(Λ) is the smallest radius r such that the
lattice points inside a ball of radius r span a space of
dimension i.
For a full-rank lattice Λ, its dual lattice Λ
∗
is defi-
ned as Λ
∗
= {x ∈ R
m
: ∀v ∈ Λ, hx,vi∈ Z}.
We usually use q-ary integer lattice in the crypto-
graphy primitive constructions below.
Λ
⊥
(A) = {z ∈ Z
m
: Az = 0 mod q}
Λ(A
t
) = {z ∈Z
m
: ∃s ∈Z
n
s.t. z = A
t
s mod q}.
Λ
⊥
(A) and Λ(A
t
) up to a q scaling factor are dual
lattices: q ·Λ
⊥
(A)
∗
= Λ(A
t
) and q·Λ(A
t
)
∗
= Λ
⊥
(A).
For any u ∈Z
n
, x as an integral solution to Ax = u
mod q, the coset is defined Λ
⊥
u
(A) = {z ∈Z
m
: Az = u
mod q} = Λ
⊥
(A) + x.
The preimage sampled in the Gaussian algorithm
can be viewed as coset given the basis of Λ
⊥
(A)
and the outputs conditional distribution is identical to
preimage from Gaussian distribution.
For any vector c ∈ R
m
and any real s > 0, the (sp-
herical) Gaussian function with standard deviation pa-
rameter s and center c is defined as: ∀x ∈R
n
,ρ
s,c
(x) =
exp(−πkx −ck/s
2
).
The (spherical) discrete Gaussian distribution over
a lattice Λ ⊆ R
m
, with standard deviation parameter
s > 0 and center c is defined as: ∀x ∈ Λ,D
Λ,s,c
=
ρ
s,c
(x)
ρ
s,c
(Λ)
, where Gaussian mass ρ
s,c
(Λ) =
∑
x∈Λ
ρ
s,c
(x).
D
Λ,s,c
is merely a normalization factor and it is
simply proportional to ρ
s,c
(x).
Micciancio and Regev (Micciancio and Regev,
2004) proposed a lattice quantity called the smoothing
parameter. We will recall some fundamental proper-
ties of the smoothing parameter.
Lemma 1 ((Gentry et al., 2008), Lemma 3.1). For
any m-dimensional lattice Λ with basis B and ε >
0, we have η
ε
≤
q
ln(2m(1+1/ε))
π
·k
e
Bk, where k
e
Bk =
max
m
i=1
k
e
b
i
k denotes the maximal length of the Gram-
Schmidt orthogonalized vectors
e
b
i
of the ordered ba-
sis B = {b
i
}. In particular, for any ω(
√
logm)
function, there is a negligible ε(m) for which η
ε
≤
k
e
Bk·ω(
√
logm).
Many works of cryptography over lattices rely on
the discrete Gaussian probability distributions. When
s > η
ε
(Λ), it has the following properties.
Lemma 2 ((Gentry et al., 2008), Lemma 5.2). Let
A ∈ Z
n×m
q
, ε ∈ (0, 1/2), s ≥ η
ε
(Λ
⊥
(A)), then for e ∼
D
Z
m
, the distribution of the syndrome u = Ae mod q
is within statistical distance 2ε of uniform over Z
n
q
.
Furthermore, let u ∈ Z
n
q
be fixed and t ∈ Z
m
be an
arbitrary solution to At = u mod q, then given Ae =
ICISSP 2018 - 4th International Conference on Information Systems Security and Privacy
462

u mod q, the conditional distribution of e ∼ D
Z
m
is
t + D
Λ
⊥
,s,−t
.
The tail inequality of Gaussian distribution in the
next lemma shows a sample from D
Z
m
,s
is at most
s
√
m away from the center with overwhelming pro-
bability.
Lemma 3 ((Micciancio and Regev, 2004), Lemma
4.4). For any n-dimensional lattice Λ, c ∈ R
m
, ε ∈
(0,1) and s > η
ε
(Λ), c ∈ span(Λ), Pr
x←D
Λ,s,c
[kx −ck ≥
s
√
m] ≤
1−ε
1+ε
·2
−m
.
NTRU lattice is a lattice with special algebra
structure. For a power-of two integer N, a posi-
tive integer q, and f ,g ∈ R , R , Z[x]/(x
N
+ 1), let
h = g ∗f
−1
mod q, NTRU lattice is defined as Λ
h,q
=
{(u,v) ∈ R
2
|u + v ∗h = 0 mod q}.
The last lemma provides the theoretical lower
bound of the maximal length of Gram-Schmidt ort-
hogonalized vectors over NTRU lattices.
Lemma 4 ((Ducas et al., 2014), Lemma 2). Let B
f,g
be a basis of NTRU lattice, b
1
,··· , b
2N
be the row
vectors of B
f ,g
, then k
e
B
f,g
k = max{k
e
b
1
k,k
e
b
N+1
k}.
2.3 Measures of Distributions Closeness
Referring to (R
´
enyi, 1961; van Erven and Harremo
¨
es,
2014), the definitions are given as follows. For con-
venience, our definition of the RD is the exponential
of the usual definition used in information theory(van
Erven and Harremo
¨
es, 2014).
The support of the distribution P is defined as
Supp(P) = {x : P(x) 6= 0}. u ∼ U (Z
n
) denotes the
distribution of u ∈ Z
n
is uniform.
Let P and Q be two distributions over the counta-
ble support Supp(P) ⊆ Supp(Q).
The Statistical distance between P and Q is defi-
ned as
∆(PkQ) =
1
2
∑
x∈Supp(P)
|P(x) −Q(x)|.
The Kullback-Leibler Divergence of Q from P is
defined as:
D
KL
(PkQ) =
∑
x∈Supp(P)
P(x)ln
P(x)
Q(x)
.
For α ∈ (1, +∞), the R
´
enyi divergence of order α
is defined as:
R
α
(PkQ) = (
∑
x∈Supp(P)
P(x)
α
Q(x)
α−1
)
1
α−1
.
For α = 1 and α = ∞, R
´
enyi divergences are re-
spectively defined as:
R
1
(PkQ) = exp (
∑
x∈Supp(P)
P(x) ·ln
P(x)
Q(x)
)
and
R
∞
(PkQ) = max
x∈Supp(P)
P(x)
Q(x)
.
SD denotes the difference of two probability dis-
tributions, RD denotes the ratio of two probability dis-
tributions. RD and KL have similar properties with
SD as follows:
Lemma 5 ((van Erven and Harremo
¨
es, 2014; Lang-
lois et al., 2014; Bai et al., 2015)). Let P and Q de-
note probability distributions over the countable set
Supp(P) ⊆ Supp(Q), α ∈ [1,+∞]. For any function
f :
• Additivity.
∆(
∏
i
P
i
k
∏
i
Q
i
) =
∑
i
∆(P
i
kQ
i
).
KL(
∏
i
P
i
k
∏
i
Q
i
) =
∑
i
KL(P
i
kQ
i
).
• Multiplicativity.
R
α
(
∏
i
P
i
k
∏
i
Q
i
) =
∏
i
R
α
(P
i
kQ
i
).
• Data Processing Inequality.
∆(P
f
kQ
f
) ≤ ∆(PkQ)
KL(P
f
kQ
f
) ≤ KL(PkQ)
R
α
(P
f
kQ
f
) ≤ R
α
(PkQ)
where P
f
(resp.Q
f
) denotes the distribution of
f (x) induced by sampling x ←P(resp.x ←Q).
Lemma 6 (Probability Preservation (van Erven and
Harremo
¨
es, 2014; Langlois et al., 2014; Bai et al.,
2015)). Let P (Q) be the probability distributions over
Supp(P) ⊆ Supp(Q), A ⊆ Supp(Q) be an arbitrary
event.
SD-based probability preservation property:
Q(A) ≥ P(A) −2∆(PkQ)
KL-based probability preservation property:
|Q(A) −P(A)| ≤
1
√
2
p
D
KL
(PkQ)
RD-based probability preservation:
Q(A) ≥
(P(A))
α
α−1
R
α
(PkQ)
Q(A) ≥
P(A)
2
R
2
(PkQ)
Q(A) ≥ P(A) −
p
lnR
1
(PkQ)/2
Q(A) ≥
P(A)
R
∞
(PkQ)
.
Since R
1
(PkQ) is the exponential of the Kullback-
Leibler divergence. For a random event set
A ⊆ Supp(P) ⊆ Supp(Q), then we have Q(A) ≥
P(A) −
p
lnR
1
(PkQ)/2.
Probability Preservation Property with Relative Error and Its Applications
463

3 SECURITY REDUCTION
Inspired by the Taylor series expansion technique in
(P
¨
oppelmann et al., 2014) and the idea of relative er-
ror in (Micciancio and Walter, 2017), we provide the
bound of two probability distributions closeness with
relative error. Then, we obtain probability preserva-
tion properties with relative error. It is easy to ana-
lyse and compare the bound of the success probability
with our uniform representations.
3.1 Bound of Distributions Closeness
We describe the bound of closeness of two probabi-
lity distributions with relative error by Taylor series,
where we give a tight factor by analyzing the tail-cut
of the Taylor expansion explicitly.
Theorem 1 (Bound of Distributions Closeness). Let
P and Q be two probability distributions over the
same countable S. Assume that for any x ∈ S, there
exists |P(x) −Q(x)| ≤ δ(x)Q(x), where δ(x) ∈ (0,
1
α
)
and α > 2. Then we have:
R
α
(PkQ) ≤ 1 + αmax
x∈S
δ(x)
2
.
R
2
(PkQ) ≤ 1 + max
x∈S
δ(x)
2
.
R
1
(PkQ) ≤ 1 + max
x∈S
δ(x)
2
.
R
∞
(PkQ) ≤ 1 + max
x∈S
δ(x).
We also present the SD and KL bounds of distri-
butions closeness with relative error.
SD bound:
∆(PkQ) ≤
1
2
max
x∈S
δ(x).
KL bound:
D
KL
(PkQ) ≤ max
x∈S
δ(x)
2
.
Main proofs of theorem are given in Appendix A.
In fact, as the special relation that R
1
(PkQ) is the ex-
ponential of KL, the derivation of the bound of dis-
tributions closeness via R
1
(PkQ) relies on the com-
putation of KL. The proof of KL was proposed in
(P
¨
oppelmann et al., 2014). In essence, it is identical
to the work of (Prest, 2017). We extend to other clo-
seness measures and different parameter settings. The
essential derivation process amounts to preprocessing
distributions closeness bound.
3.2 Bound of Success Probability
Let P (Q) be the probability distributions over the
same countable set S in the real (ideal) scheme. For a
probabilistic polynomial-time adversary A against the
scheme, if A succeeds in the attack, Suc
A
( f (x)) = 1,
otherwise Suc
A
( f (x)) = 0, where f is any efficiently
computable function, then the advantage of adversary
A succeeding in the attack is defined as Adv
A
(P,Q) =
| Pr
x←P
[Suc
A
( f (x)) = 1] − Pr
x←Q
[Suc
A
( f (x)) = 1]|.
Assume that P is the probability distribution over
S in the real scheme, Q is the probability distribution
over S in the ideal scheme. If A succeeds with signi-
ficant probability in the real scheme and Adv
A
(P,Q)
is negligible, then A succeeds with significant pro-
bability in the ideal scheme. In other words, if the
adversary succeeds with negligible probability in the
ideal scheme and Adv
A
(P,Q) is negligible, then it
also succeeds with negligible probability in the real
scheme. The property is named the probability pre-
servation property. According to Theorem 1 and
Lemma 6, we acquire Theorem 2 by the substitution
method.
Theorem 2 (Bound of Success Probability). Let P
(Q) be the probability distribution over S in the real
(ideal) scheme. Assume that for any x ∈ S, there ex-
ists |P(x) − Q(x)| ≤ δ(x)Q(x), where δ(x) ∈ (0,
1
α
)
and α > 2. A is a probabilistic polynomial-time
adversary making at most q queries an oracle. If
A succeeds in the attack, Suc
A
( f (x)) = 1, other-
wise Suc
A
( f (x)) = 0, where f is a one-way trapdoor
function. Let ε
P
= Pr
x←P
[Suc
A
( f (x)) = 1], ε
Q
=
Pr
x←Q
[Suc
A
( f (x)) = 1], then
RD-based probability preservation property:
RD
α
: ε
Q
≥
(ε
P
)
α
α−1
(1 + α max
x∈S
δ(x)
2
)
q
.
RD
2
: ε
Q
≥
ε
2
P
(1 + max
x∈S
δ(x)
2
)
q
.
RD
1
: ε
Q
≥ ε
P
−
r
q
2
max
x∈S
δ(x).
RD
∞
: ε
Q
≥
ε
P
(1 + max
x∈S
δ(x))
q
.
SD-based probability preservation property:
ε
Q
≥ ε
P
−
q
2
max
x∈S
δ(x).
KL-based probability preservation property:
|ε
Q
−ε
P
| ≤
r
q
2
max
x∈S
δ(x).
ICISSP 2018 - 4th International Conference on Information Systems Security and Privacy
464

From all the formulas above in the Theorem 2, We
can give straightforward analysis and comprehensive
comparisons. The times of query q, the order of α and
the max relative error max
x∈S
δ(x) act on the tightness of
the reduction. The goal in (Takashima and Takayasu,
2015; Prest, 2017) is to achieve R
α
(PkQ)
q
= Ω(1) (
e.g. (1 + αmax
x∈S
δ(x)
2
)
q
≤ e
1/4
≤
√
2 ). Our method
is different from theirs. We deal with q in the next
section, which is closely related to iteration times of
sampling algorithm.
In the analysis of the SD-based probability preser-
vation property with relative error, the success proba-
bilities in the ideal and real schemes demand for the
same magnitude O(2
−λ
), the advantage is limited to
the magnitude O(2
−λ
), so the max
x∈S
δ(x) is limited to
the magnitude O(2
−λ
).
In the analysis of the KL-based probability pre-
servation property with relative error, if the success
probability of the adversary is the magnitude O(2
−λ
)
in both the ideal and real schemes, the max
x∈S
δ(x) is li-
mited to the magnitude O(2
−λ
). Comparing to SD,
max
x∈S
δ(x) in the KL-based reduction can be larger by
q
q
2
than max
x∈S
δ(x) in the SD-based reduction remai-
ning the same security, which is one of the main con-
tributions of works in (P
¨
oppelmann et al., 2014).
In the analysis of the RD-based probability pre-
servation property with relative error, the security be-
comes looser when the order is α, particularly to
order = 2. The security remains almost the same
when the order of RD is ∞.
We give a comprehensive comparison of distri-
bution and security parameters in Table 1, where
max
x∈S
δ(x) range is O(2
−λ
) in SD and KL rows and
max
x∈S
δ(x) range is O(2
−λ
) and O(
1
λ
) in RD rows. We
can observe the performance and security parameters
by the different bounds of max
x∈S
δ(x). From the column
named security, it shows that when order = ∞, the se-
curity is almost the same when max
x∈S
δ(x) relaxes to
1
λ
.
We come to a conclusion that RD
∞
gains both the
optimized performance and same security magnitude,
which relax the relative error of two probability distri-
bution from 2
−λ
to
1
λ
. In summary, probability preser-
vation property with relative error is easy to analyse
and compare.
4 OPTIMIZATION
In this section, we optimize the smoothing parameter
of Gaussian sampling algorithm by RD
∞
-based proba-
bility preservation property. We improve the user key
size of IBEs over general lattices and NTRU lattices
by optimizing the smoothing parameter.
4.1 Optimization of Gaussian Sampling
Algorithm
A collection of one-way preimage sampleable functi-
ons is defined as follows (Gentry et al., 2008):
• TrapGen(1
λ
): (a,t) ← TrapGen(1
λ
), where a is
a function description: f
a
: D
λ
→R
λ
, D
λ
is domain
of f
a
, R
λ
is range of f
a
, t is trapdoor information
for f
a
.
• SampleDom(1
λ
): x ← SampleDom(1
λ
), where x
is from some distribution over D
λ
, for which the
distribution of f
a
(x) is uniform over R
λ
.
• SamplePre(1
λ
): x ← SamplePre(1
λ
), for ∀y ∈
R
λ
, SamplePre(t,y) samples from the distribution
of x ←SampleDom(1
λ
), given f
a
(x) = y.
• one-wayness without trapdoor: For any proba-
bilistic poly-time algorithm A, Pr[A(1
λ
,a, y) ∈
f
−1
a
(y)] ≤ negl(λ).
These properties of probability distribution de-
fined above only hold in the ideal trapdoor functi-
ons construction. The properties in the real trapdoor
functions construction will be relaxed.
PSFs over lattices based on the average-case hard-
ness of ISIS are f
A
= Ae = u mod q, where the
domain is {e ∈ Z
m
: kek < s
√
m} and the range is
Z
n
. They have two essential properties as follows:
u ∈ Z
n×m
is statistically close to uniform and the dis-
tribution of e is statistically close to D
Z
m
,s
. According
to Lemma 2, Given a good basis T ⊂ Λ
⊥
(A), prei-
mage e can be sampled by the trapdoor inversion al-
gorithm and e ∼ D
Λ
⊥
,s
statistically.
We require e is distributed according to the ex-
act Gaussian distribution D
Z
m
,s
in the ideal scheme
and define its distribution as Q. However, we get
e from the trapdoor inversion algorithm in the real
scheme and define its distribution as P. First, choose
via linear algebra t ∈ Z
m
such that At = u mod q.
Then sample v ∼ D
Λ
⊥
,s,−t
statistically using Gaus-
sian sampling algorithm and output e = t + v. Re-
ferring to proof of algorithm, we have the output pro-
bability distribution of Gaussian sampling algorithm
P ∈ [(
1−ε
1+ε
)
m
,(
1+ε
1−ε
)
m
] ·D
Z
m
,s
, where e is the output
of the trapdoor inversion algorithm, as detailed in
Probability Preservation Property with Relative Error and Its Applications
465
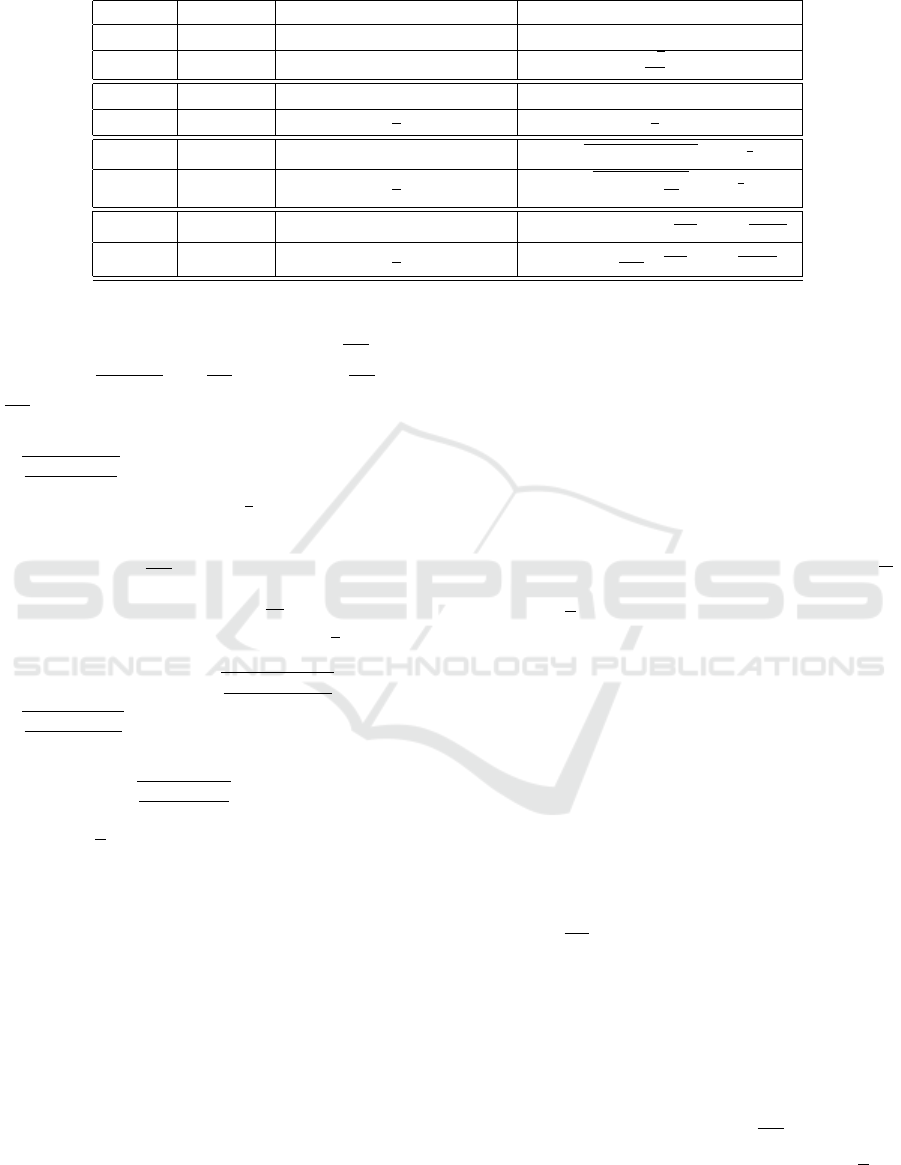
Table 1: Comparisons of distribution and security parameters.
number measures max relative error maxδ(x) security ε
P
1 SD 2
−λ
2 ·2
−λ
2 KL 2
−λ
(1 +
√
2
2
) ·2
−λ
3 RD
∞
2
−λ
(1 + 2
−λ
) ·2
−λ
4 RD
∞
1
λ
(1 +
1
λ
) ·2
−λ
5 RD
2
2
−λ
p
2
−λ
(1 + 2
−2λ
) ≈ 2
−
λ
2
6 RD
2
1
λ
q
2
−λ
(1 +
1
λ
2
) ≈ 2
−
λ
2
7 RD
α
2
−λ
(2
−λ
(1 + α2
−2λ
))
α−1
α
≈ 2
−
(α−1)λ
α
8 RD
α
1
λ
(2
−λ
(1 +
1
αλ
2
))
α−1
α
≈ 2
−
(α−1)λ
α
(Gentry et al., 2008). The relative error to the desi-
red distribution is therefore bounded by (
1+ε
1−ε
)
m
−1,
δ(x = e) =
P(x)−Q(x)
Q(x)
= ((
1+ε
1−ε
)
m
−1) ≈1 +
2mε
1−ε
−1 =
2mε
1−ε
≤ max
x∈Λ
⊥
u
δ(x).
According to Lemma 1, We have η
ε
≤
q
ln(2m(1+1/ε))
π
· k
e
B k. It is easy to get η
ε
from
ε. When max
x∈Λ
⊥
u
δ(x) relaxes to
1
λ
(even approximating
to 1/2), it is easy to find out that the tolerance ε
is shortened to
1
2mλ
(when max
x∈Λ
⊥
u
δ(x) reaches the
upper bound 1/2, ε reaches
1
4m
) and the secu-
rity parameter of RD
∞
remains (1 +
1
λ
) · 2
−λ
on
the 4th row of Table 1. So the smoothing para-
meter decreases from
q
ln(2m(1+2m·2
λ
))
π
· k
e
B k to
q
ln(2m(1+2mλ))
π
· k
e
B k (when max
x∈Λ
⊥
u
δ(x) approximates
the upper bound 1/2, the smoothing parameter
approximates
q
ln(2m(1+4m))
π
· k
e
B k). We come to a
conclusion the smoothing parameter declines by a
factor O(
√
λ) via RD
∞
and the security remains the
same.
4.2 Optimization of IBE
We give two illustrative examples of instantiations
over general lattices and NTRU lattices. We start with
the IBE system in(Gentry et al., 2008), then we extend
to the IBE system in(Ducas et al., 2014).
IBE consists of four algorithm: IBESetup, IBEEx-
tract, IBEEnc, IBEDec.
• IBESetup(1
n
): (A,T ) ← IBESetup(1
n
), where T
is trapdoor of function f
A
. The Master public key
is A, the secret key is T.
• IBEExtract(A, T, id): e ← IBEExtract(A, T, id)
such that Ae = u = H(id), where e is user secret
key for the user id and H is an oracle.
• IBEEnc(A,id,b): (p,c) ← DualEnc(u, b).
• IBEDec(e,(p,c)): b ←DualDec(e,(p,c)).
In (Gentry et al., 2008) preimage sampleable (trap-
door) function is f
A
(e) = Ae mod q, where A ∈
Z
m×n
q
is a random matrix and e ∈ Z
m
q
is short vector.
In the algorithm IBEExtract(A, T,id), the decryption
key e ← f
−1
(u) is obtained by using the preimage
sampler with trapdoor T. e is the output of Gaussian
sampling algorithm with short basis T. According to
the tail inequality Lemma 3, we have e : kek≤s ·
√
m,
so the size of user secret key e can be reduced by a
factor O(
√
λ) as the smoothing parameter is optimi-
zed.
Because the discrete Gaussian sampling descri-
bed in (Gentry et al., 2008) involves sequential ite-
rations and the Gram-Schmidt orthogonalized opera-
tions, it is rather inefficient. So making adjustments
to some of tunable parameters of the main opera-
tions about trapdoor generation and inversion algo-
rithms may provide better combinations of efficiency
and concrete security.
In (Ducas et al., 2014) Gaussian sampling algo-
rithm of NTRU lattices is applied to sampling (s
1
,s
2
)
such that s
1
+ s
2
∗h = t by a short basis B of Λ
h,q
.
The output of Gaussian sampling algorithm has the
length s ·
√
2N, where s > η
ε
. The improvements in-
volve the tolerance ε and the Gram-Schmidt norm of
the trapdoor. According to Lemma 1, the optimization
of the tolerance is orthogonal to the optimization the
Gram-Schmidt norm of the basis. B is a short basis of
Λ
h,q
. Referring to Lemma 4 the Gram-Schmidt norm
computation of the trapdoor basis is simplified and
public key size is reduced owing to the structure of
ring. With RD ε can be reduced to
1
4Nλ
. In summary,
two optimization methods can be combined well. The
user secret key size is lowered by a factor O(
√
λ) in
the terms of our optimization.
ICISSP 2018 - 4th International Conference on Information Systems Security and Privacy
466

5 CONCLUSION
In this work, we reform preservation property of one-
way preimage sampleable functions with relative er-
ror. We give straightforward analysis and compre-
hensive comparisons of probability and show that
RD
∞
has improved performance without security loss.
Furthermore, we optimize the smoothing parameter
of Gaussian sampling algorithm by RD
∞
-based proba-
bility preservation property. Finally, we improve the
user key size of IBEs over general lattices and NTRU
lattices by optimized the smoothing parameter. We
can improve them with shorter parameters and better
efficiency without compromising the security.
ACKNOWLEDGEMENT
The authors would like to thank anonymous reviewers
for their helpful comments and suggestions. The work
of this paper was supported by the National Natural
Science Foundation of China (Grants Y610112103).
REFERENCES
Bai, S., Langlois, A., Lepoint, T., Stehl
´
e, D., and Steinfeld,
R. (2015). Improved security proofs in lattice-based
cryptography: Using the r
´
enyi divergence rather than
the statistical distance. In Advances in Cryptology -
ASIACRYPT 2015 - 21st International Conference on
the Theory and Application of Cryptology and Infor-
mation Security, Auckland, New Zealand, November
29 - December 3, 2015, Proceedings, Part I, pages 3–
24.
Ducas, L., Lyubashevsky, V., and Prest, T. (2014). Efficient
identity-based encryption over NTRU lattices. In Ad-
vances in Cryptology - ASIACRYPT 2014 - 20th Inter-
national Conference on the Theory and Application of
Cryptology and Information Security, Kaoshiung, Tai-
wan, R.O.C., December 7-11, 2014, Proceedings, Part
II, pages 22–41.
Gentry, C., Peikert, C., and Vaikuntanathan, V. (2008).
Trapdoors for hard lattices and new cryptographic
constructions. In Proceedings of the 40th Annual ACM
Symposium on Theory of Computing, Victoria, British
Columbia, Canada, May 17-20, 2008, pages 197–206.
Langlois, A., Stehl
´
e, D., and Steinfeld, R. (2014). Gghlite:
More efficient multilinear maps from ideal lattices. In
Advances in Cryptology - EUROCRYPT 2014 - 33rd
Annual International Conference on the Theory and
Applications of Cryptographic Techniques, Copenha-
gen, Denmark, May 11-15, 2014. Proceedings, pages
239–256.
Micciancio, D. and Regev, O. (2004). Worst-case to
average-case reductions based on gaussian measu-
res. In 45th Symposium on Foundations of Compu-
ter Science (FOCS 2004), 17-19 October 2004, Rome,
Italy, Proceedings, pages 372–381.
Micciancio, D. and Walter, M. (2017). Gaussian sampling
over the integers: Efficient, generic, constant-time.
In Advances in Cryptology - CRYPTO 2017 - 37th
Annual International Cryptology Conference, Santa
Barbara, CA, USA, August 20-24, 2017, Proceedings,
Part II, pages 455–485.
P
¨
oppelmann, T., Ducas, L., and G
¨
uneysu, T. (2014). En-
hanced lattice-based signatures on reconfigurable har-
dware. In Cryptographic Hardware and Embedded
Systems - CHES 2014 - 16th International Workshop,
Busan, South Korea, September 23-26, 2014. Procee-
dings, pages 353–370.
Prest, T. (2017). Sharper bounds in lattice-based crypto-
graphy using the r
´
enyi divergence. IACR Cryptology
ePrint Archive, 2017:480.
R
´
enyi, A. (1961). On measures of entropy and informa-
tion. In Proceedings of the Fourth Berkeley Sympo-
sium on Mathematical Statistics and Probability, Vo-
lume 1: Contributions to the Theory of Statistics, pa-
ges 547–561, Berkeley, Calif. University of California
Press.
Takashima, K. and Takayasu, A. (2015). Tighter security for
efficient lattice cryptography via the r
´
enyi divergence
of optimized orders. In Provable Security - 9th Inter-
national Conference, ProvSec 2015, Kanazawa, Ja-
pan, November 24-26, 2015, Proceedings, pages 412–
431.
van Erven, T. and Harremo
¨
es, P. (2014). R
´
enyi divergence
and kullback-leibler divergence. IEEE Trans. Infor-
mation Theory, 60(7):3797–3820.
APPENDIX A
We now provide Proof of Theorem 1.
Proof. 1) Firstly, we prove the RD bound with the
order α.
We set f (P(x)) =
P(x)
α
Q(x)
α−1
, then give the partial de-
rivative ∂
n
f /∂P(x)
n
at P(x) = Q(x),
f (P(x))|
P(x)=Q(x)
=
P(x)
α
Q(x)
α−1
|
P(x)=Q(x)
= Q(x),
f
(1)
(P(x))|
P(x)=Q(x)
= α
P(x)
α−1
Q(x)
α−1
|
P(x)=Q(x)
= α,
f
(2)
(P(x))|
P(x)=Q(x)
= α(α −1)
P(x)
α−2
Q(x)
α−1
|
P(x)=Q(x)
= α(α −1)
1
Q(x)
Probability Preservation Property with Relative Error and Its Applications
467

according to Taylor series expansion, it holds that
f (P(x)) = f (P(x))|
P(x)=Q(x)
+
f
(1)
(P(x))|
P(x)=Q(x)
(P(x) −Q(x))
+
f
(2)
(P(x))|
P(x)=Q(x)
2!
(P(x) −Q(x))
2
+ R(P(x))
= Q(x) + α(P(x) −Q(x)) +
α(α −1)(Q(x) −P(x))
2
2!Q(x)
+ R(P(x))
= Q(x) + α(P(x) −Q(x)) +
α(α −1)
2
Q(x)(
P(x) −Q(x)
Q(x)
)
2
+R(P(x)),
where R(P(x)) is the tail-cut of the Taylor expan-
sion.
R(P(x) =
∞
∑
i=3
C(α, i)Q(x)(
P(x) −Q(x)
Q(x)
)
i
=
∞
∑
i=3
C(α, i)
α(α −1)
(
P(x) −Q(x)
Q(x)
)
i−2
Q(x)
α(α −1)(
P(x) −Q(x)
Q(x)
)
2
.
As
C(α,i)
α(α−1)
<
α
i−2
2
and (
P(x)−Q(x)
Q(x)
)
i−2
≤
1
α
i−2
,
max
x∈X
(R(P(x))) ≤
1
2
∑
x∈S
Q(x)(
P(x)−Q(x)
Q(x)
)
2
. As P(x)
and Q(x) sum over x ∈ S, we have
∑
x∈S
f (P(x)) ≤
∑
x∈S
Q(x) + α
∑
x∈S
(P(x) −Q(x)) +
α(α −1)
∑
x∈S
Q(x)(
(P(x) −Q(x)
Q(x)
)
2
.
Since S is the support of both P and Q, it holds that
∑
x∈S
P(x) =
∑
x∈S
Q(x) = 1. So
∑
x∈S
f (P(x)) ≤ (1 + α(α −1)
∑
x∈S
δ(x)
2
Q(x).
R
α
(PkQ) = (
∑
x∈S
P(x)
α
Q(x)
α−1
)
1
α−1
≤ (1 + α(α −1)
∑
x∈S
δ(x)
2
Q(x))
1
α−1
= 1 +
1
α −1
(α(α −1)
∑
x∈S
δ(x)
2
Q(x))
+R
0
,
where the tail-cut of the Taylor expansion R
0
< 0,
so we have
R
α
(PkQ) ≤ 1 + α(max
x∈S
δ(x))
2
.
By the same deduction, we get R
2
(PkQ) =
∑
x∈S
P(x)
2
Q(x)
= 1 +
∑
x∈S
δ(x)
2
Q(x) ≤ 1 + (max
x∈S
δ(x))
2
when the order is 2.
2) Then, we prove the RD bound with the order 1
and ∞.R
1
(PkQ) is the exponential of the Kullback-
Leibler divergence.
R
1
(PkQ) = expD
KL
(PkQ) ≈1+D
KL
(PkQ) = 1+
∑
x∈S
Q(x)(δ(x))
2
= 1 + (max
x∈S
δ(x))
2
. R
∞
(PkQ) =
max
x∈S
P(x)
Q(x)
≤ max
x∈S
(1+δ(x))Q(x)
Q(x)
≤ 1+max
x∈S
δ(x).
Finally we give the SD bound of distributions clo-
seness with relative error.
Proof. ∆(PkQ) =
1
2
∑
x∈S
|P(x) − Q(x)| ≤
1
2
∑
x∈S
δ(x) ·Q(x) ≤
1
2
∑
x∈S
maxδ(x) ·Q(x) =
1
2
max
x∈S
δ(x).
Since S is the support of Q, it holds that
∑
x∈S
Q(x) =
1, therefore the last equation holds.
ICISSP 2018 - 4th International Conference on Information Systems Security and Privacy
468
