
Automatic Attendance Control System based on BLE Technology
Miran Bori
´
c, Ana Fern
´
andez Vilas and Rebeca P. D
´
ıaz Redondo
Information & Computing Lab., AtlantTIC Research Center, School of Telecommunications Engineering,
University of Vigo, 36210 Vigo, Spain
Keywords:
Bluetooth Low Energy, iBeacons, Experiment, Data Collection, Broadcasting.
Abstract:
As an emerging low power wireless technology, Bluetooth Low Energy lately has become an essential part
of the Internet of Things world. Its pervasiveness has given the possibility for many different, otherwise
manually driven, concepts to work in a different, enhanced, and more automated fashion. In this paper, we
present an automatic attendance control system based on the interaction between a modified BLE iBeacon
mechanism and users’ smart devices. As such, the system can recognize users according to predefined profiles
and eventually broadcast valuable information that corresponds to recognized profiles. The proof of concept
shows that this is a promising approach regarding automating specific tasks, recognizing users and interacting
with them less complexly.
1 INTRODUCTION
Since the release of Apple’s iBeacon protocol back
in 2013 (Newman, 2014), Bluetooth Low Energy be-
came a dominant technology for many projects in the
Internet of Things and human life. From small user
appliances to big industry wireless solutions, every-
thing is trying to be connected. With an estimated 21
billion devices possibly connected by the year 2020,
data generating a massive amount of data becomes a
usual daily routine. With that said, businesses can no
longer ignore such growth and should adjust to this
revolution swiftly. Along with the IoT, a new concept
called ”The Physical Web” embedded itself into BLE
technology and lately is on the rise. Such idea allows
us to connect the physical and virtual world with each
other. Better said, it enables us to interact with the
objects that surround us, such as user appliance de-
vices. The product of such interaction is sharing and
processing of different data to gain a better knowledge
and to facilitate everyday activities.
Surely, with the smart environment and the IoT,
the door to different technological approaches, where
devices share essential information is wide open. We
do see that BLE is taking over the world, mainly in
the consumer device area, where the whole ecosystem
proceeds to grow continually. Especially with the lat-
est BLE concept called Bluetooth proximity beacons
often referred to as the Beacons (ibeacons), where LE
peripherals advertise themselves to the nearby devices
by using advertisement packets (Martin et al., 2014).
An iBeacon represents an electromagnetic sig-
nal that can be processed by every BLE enabled de-
vice. In more details, iBeacons are small transmit-
ters that advertise a specific BLE payload that is rep-
resented by particular identifiers: UUID (Universally
Unique Identifier) 128-bit value, Major value (16-bit
unsigned integer), and Minor value (16-bit unsigned
integer). The last two values are optional and are in-
cluded in case of more hierarchical system implemen-
tations. As already said, an iBeacon signal can repre-
sent a specific object or process in some defined en-
vironment. Later, when received by a BLE enabled
device, that signal triggers some action that means
something to the user or some other object.
Nowadays, numerous beacon maker companies
exist, and every company has something different to
offer. Their products differ in various sizes, function-
alities, but the majority of them are static. In other
words, a single beacon device can only broadcast one
iBeacon combination of UUID, Major, and Minor val-
ues at the same time, and any further classification is
handled by the application that is usually installed on
the users’ smartphones. If we want to broadcast dif-
ferent type of data, we need another beacon device
with separate iBeacon combination. Developing an
app became a primary focus and the central point of
all the processing, leaving the iBeacon hardware as a
static device without any advanced functionality. As
already mentioned, many solutions exist on this sub-
ject, but most of the processing is done on the appli-
cation side. In most cases, it became mandatory for
Bori
´
c, M., Vilas, A. and Redondo, R.
Automatic Attendance Control System based on BLE Technology.
DOI: 10.5220/0006830202890295
In Proceedings of the 15th International Joint Conference on e-Business and Telecommunications (ICETE 2018) - Volume 1: DCNET, ICE-B, OPTICS, SIGMAP and WINSYS, pages 289-295
ISBN: 978-989-758-319-3
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
289

the user to have an application installed on his smart-
phone. Let us not forget that the beacon device ini-
tially can not collect BLE signals since it is a one-way
broadcasting technology.
To overcome such a static method of broadcasting
iBeacon BLE signal, in our previous work we have
proposed a dynamic solution where a modified BLE
beacon device can simultaneously transmit and re-
ceive different signals according to various user pro-
files (Boric et al., 2018), as well as the implementa-
tion part and the challenges (M. Boric et al., 2018).
By modified beacon, we refer to a device that in the
same moment can work in a scanning mode, and
an iBeacon mode (advertising specific information to
corresponding users) (Townsend et al., 2014). Ad-
ditionally, these two modes complement each other,
what allows the device to broadcast information to a
specific group of users that share the same profile.
The profile can be created manually by predefined
taxonomy, or automatically by users’ movement post
processing and detailed analytics. For this simultane-
ous broadcasting of information to different profiles,
the device needs to have a particular mechanism and
the background infrastructure that allows the profile
recognition and the broadcast. Now, we are expand-
ing that system with real-world examples to show its
usage and benefit for different purposes.
The recognition concept above could contribute
to solving the problem of manual presence detection
through automatically collecting users’ smartphones
BLE signals in any scenario environment where such
detection is required. To show the proof of concept we
utilize the mentioned system for collecting students’
lecture attendance in the academic environment. Our
scenario experiment took place at the Faculty of En-
gineering and Telecommunications of Vigo in Spain.
We have planted one beacon device in the hallway,
for testing the dynamic beacon broadcasting, and an-
other device in one of the classrooms of the Faculty
for collecting student attendance.
The experiment was conducted in a one-month pe-
riod, and we present the details in the following sec-
tions. In this work, we show how our dynamic sys-
tem can be used in the academic environment to au-
tomatically collect students lecture attendance when
students are in beacon proximity, without any appli-
cation installed on the user side. However, with the
application installed on the user side, a system may
eventually broadcast information to him, e.g., dif-
ferent events, classes timetable, homework, faculty
changes, and so on.
The remainder of this paper we divide into several
sections. Section 2 gives the related work and what
was our primary motivation. Part 3 explains the sys-
tem architecture and how we use it to for proposed
system. In section 4 we present the implementation
part with the results, wherein section 5 we conclude
the paper.
2 RELATED WORK
Researchers have been advancing in the Bluetooth
Low Energy field lately. This progress gave some
great examples of the use of such technology in to-
day’s world, from retail business (Shende et al., 2017)
and giving a better experience to the customers, to
monitoring different processes in industry or health
(Srinivasan et al., 2016) (Komai et al., 2016). When
speaking of beacon involvement in the academic en-
vironment, few projects have been proposed and de-
ployed. Researchers in (S. Barapatre et al., 2017)
have proposed the smart college management system
with the ability of automatic student class attendance.
However, for the system to be able to recognize a par-
ticular student, a student has to use an Android app
and to mark his attendance during a particular class.
Similarly, authors in (Apoorv and Mathur, 2016) have
built a system that facilitates the teachers to collect
student attendances. For this purpose, the Android ap-
plication communicates with the BLE beacon planted
in the classroom and collects the sensor data, from ID
cards, that matches the student’s attendance. How-
ever, to collect attendance, a teacher has to collect all
the BLE signals manually through the app.
Furthermore, authors in (Saraswat and Garg,
2016) are using beacons for faculty administrative
tasks and interacting with the students by sending
them Web links and the corresponding notifications.
Another feature of this system is the automatic stu-
dent attendance collection, where students according
to their stay in the classroom, during particular lec-
ture, get recorded by the system. That said, when the
specific student is near beacon a clock time starts in
the application background automatically and accord-
ing to its proximity (near, immediate), local clock-
time increases. However, the majority of the work is
done on the application side (student’s smartphone).
In our case, a dynamic beacon is the focal point of
all the processing that includes sending information
to the students, collecting their attendance, analyzing
their building usage and giving an insight to the fac-
ulty personnel.
Also, the reason for electing BLE technology is
because of its low power consumption, comparing to
Wi-Fi for instance (Putra et al., 2017). Also, Wi-Fi
technology asks for previously established connec-
tion between two hosts which is not convenient in our
WINSYS 2018 - International Conference on Wireless Networks and Mobile Systems
290
case. In case of the Wi-Fi direct and classic Blue-
tooth, they ask for secure pairing to unknown devices
(Trifunovic et al., 2011).
3 SYSTEM ARCHITECTURE
The idea is to have a unique system that recognizes
users while in a proximity of a beacon and triggers
some actions based on that recognition. The user’s
smart device can be used to monitor the proximity lo-
cation of a user in the beacon vicinity. Based on this
location information, a user’s presence record will
get updated automatically on the system. For bet-
ter understanding, we will take the example of stu-
dents lecture attendance. Usually, when students en-
ter a specific classroom, a professor manually checks
the students’ participation, either on a piece of pa-
per or using some application. This kind of work is
time-consuming and introduces complexity in further
school analysis, e.g., If the school board wants to get
better student/classes/subject insight, everything has
to be done manually. However, by using BLE in com-
bination with the student’s smartphone, or some other
BLE enabled device, this work can be automatized
and can save much time for the future faculty analy-
sis.
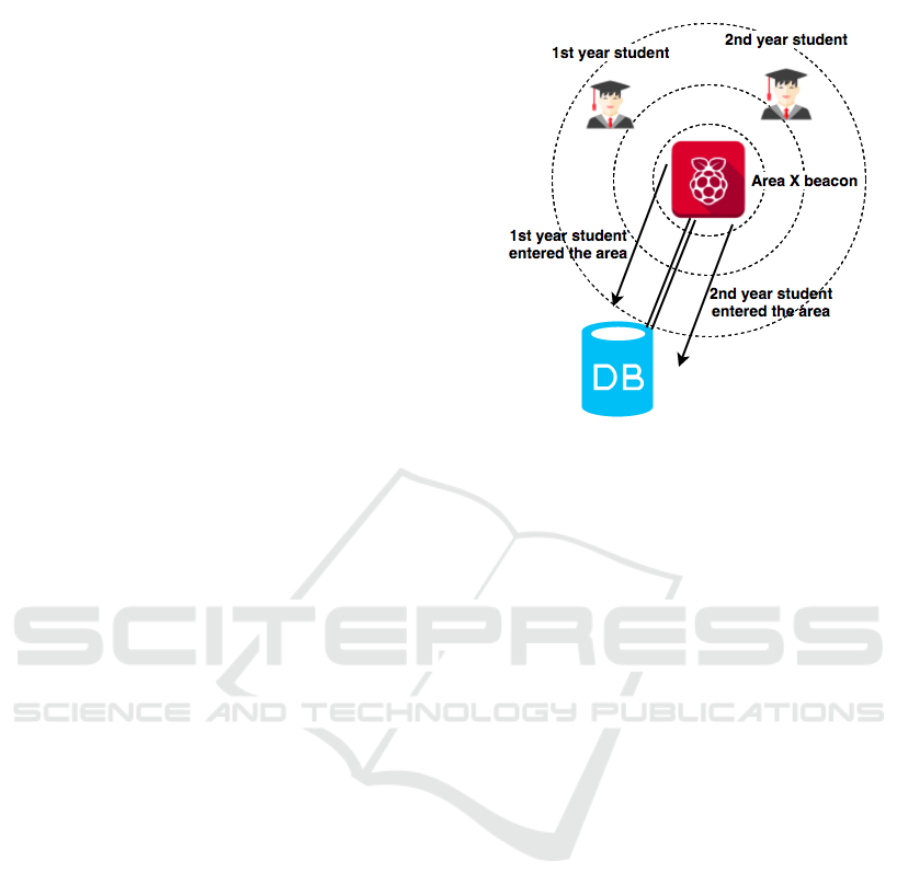
For better system explanation, we give the con-
cept in Figure 1, where the beacon device works in
two modes, the discovery, and the advertising mode
that uses the iBeacon technology. The discovery
mode, as already mentioned, is in a constant search
for the nearby devices (BLE devices) and the adver-
tising mode optionally sends some relevant interest-
based data to the recognized users. When a partic-
ular user enters a classroom (broadcasting area), his
smartphone BLE MAC address gets recognized by
the classroom beacon device that works in a discov-
ery (passive scanning) mode. For the user to be iden-
tified, it is not obligatory to have an installed applica-
tion on his smartphone, or even connect to the system
since the user is recognized automatically. Next, the
beacon device sends the user’s BLE MAC address to
the database through the back-end infrastructure. The
back-end can be based on any connection technology,
or even implemented on the same device where the
beacon functionality is installed. In our case, it is in-
stalled on one of the Raspberries and connected via
secured Wi-Fi connection. To send some information
to the recognized user, we need to use the advertising
mode of the beacon device (iBeacon mode). How-
ever, this step is optional and asks for an application
on the user’s side.
The database is nothing else but a student reposi-
Figure 1: Dynamic beacon functionality.
tory where all his relevant data is saved (Student year,
subjects, classroom he attended and time, personal
info, and so on.). Personal user information can be in-
serted through the faculty information system, while
all the other information (student movement activity)
can be collected from the database. Also, the database
contains a student attendance report of his every atten-
dance, for which the beacon device is used in the first
place. In that case, the system would suffer from false
attendance inputs. This presence is not marked at the
same moment when the student enters the classroom
but after a specific period. This period depends on
how the faculty organizes and schedules their classes,
and also how does it handle students attendance. For
example, if the faculty agrees for the lessons to be
held for 2 hours than the beacon device can be config-
ured in that manner. A minimum number of student
acknowledgments by the system, during the lecture
time, is flexible and configurable, and it is a subject of
a faculty policy, as mentioned before. If the student
is present in the classroom during the whole lecture
period (e.g., two hours), the system marks his atten-
dance as the database record.
Nevertheless, we have to consider a problem of
the signal overlapping, especially if the beaconing ar-
eas are a close one to another (two classrooms, of-
fices, and so on). For example, if two students are
attending classes in the different classrooms, and the
classrooms are close as mentioned, it is possible for
the signal to overlap. This behavior would result
in collecting false data. In that case, the system
would not correctly process the inputs, and the out-
put would not be trustworthy. Even with the excellent
and planned site survey, we have to take into account
Automatic Attendance Control System based on BLE Technology
291
a certain amount of false positives. First, a precise
positioning of the beacon device and the proper site
survey of the classroom need to be done. Second, an
additional mechanism to prevent such behavior needs
to be introduced. In our case, that is a door scanner
positioned correctly at the classroom entrance, so that
the system can scan students when entering the room.
For that matter, we can use the infrared technology or
something similar and connect it and configure it to
the Raspberry device, dynamic iBeacon in our case.
The beacon device can work simultaneously for many
different profiles. In other words, it can recognize dif-
ferent profiles, if profile recognition is implemented
into the database. In this case, all we need is one bea-
con device per every classroom. That said, we lower
the broadcasting congestion and network latency that
represent the problem for most of the IEEE 802 net-
works. The beacon device does not have to be a part
of the school infrastructure (school Wi-Fi, Ethernet,
and so on).
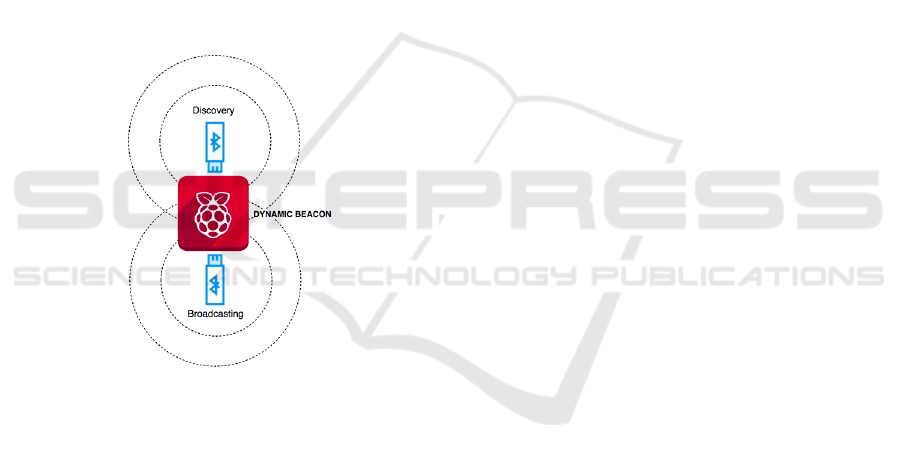
Figure 2: Beacon device architecture.
Although, every beacon device has to connect to
the central beacon repository. In our case, this repos-
itory is the database. As mentioned before, for the
beacon to function dynamically, constant connection
to DB is necessary. This way, the beacon advertiser
is changing his beacon combination ID, depending
on profile entrance and, if needed, disseminates the
corresponding information to the users. Every profile
is represented by a different combination ID (UUID,
Major, and Minor number). The most critical piece
of information for the system to be functional is the
user’s device MAC address with which the system
recognizes a particular user and his profile. A user de-
vice does not have to be his private mobile phone ex-
plicitly, but any piece of hardware that supports BLE
(BLE token, smart card, and so on). However, if we
want to utilize a full system capacity, advertising in-
formation to the students, using smartphones repre-
sents a better approach. For the system to work ap-
propriately, student phone MAC addresses need to
be inserted into the database before the student at-
tendance collection. Achieving beacon to operate in
a dynamic mode is not an easy task. Usually, bea-
cons work in a static mode where every beacon sig-
nal identifier (UUID, Major, and Minor values) cor-
responds to only one information, and they were ini-
tially imagined as such. However, having many bea-
con devices in a single area brings network latency
and congestion, as mentioned before. To overcome
that problem, we offer a solution where beacon de-
vice recognizes the users dynamically when near the
discovery/broadcasting area. Dynamically means that
the beacon can serve and acknowledge many user pro-
files simultaneously without degrading its functional-
ity (see Figure 2). In our case, we use such solution
for automatic student attendance, as mentioned ear-
lier. Additionally, if positioned correctly (along the
faculty area), the beacon system can collect all the
faculty users on a regular basis and save them into the
database. That said, this information could be valu-
able for building managers for better space analytics,
building management, on so on. If so, the faculty
board can use this insight for different future planning
regarding their assets and faculty management.
4 IMPLEMENTATION AND THE
RESULTS
As already mentioned, a single beacon device con-
tains two major parts; the discovery (scanning) and
the advertising part (iBeacon) where every element
works separately and includes its methodology. That
said, for the beacon device we use a Raspberry Pi
small computer and corresponding BLE USB module
devices that play a vital role in the dynamic broadcast-
ing. Beacon device is based on Raspberry Pi 3 Model
B device along with the Bluetooth 4.0 CSR8510 USB
Module. Reason for this is because the Raspberry
device is Linux based and in that manner, it is very
flexible and scalable for this kind of solution. One
BLE USB module device is used for the discovery
part, while the other for advertising part (see Figure
2). The beacon device is connected to the database,
”Student Profile DB” in our case. We have to mention
that the database can be implemented separately from
the beacon device on a different device, or it can be in-
stalled on the same device where the beacon resides.
This implementation is possible due to the flexibility
of the Raspberry Pi Linux operating system. ”Stu-
dent Profile DB” is based on the MySQL open-source
relational database management system. It is worth
WINSYS 2018 - International Conference on Wireless Networks and Mobile Systems
292
mentioning that detailed database structure is not pre-
sented since it was not relevant for the paper. In our
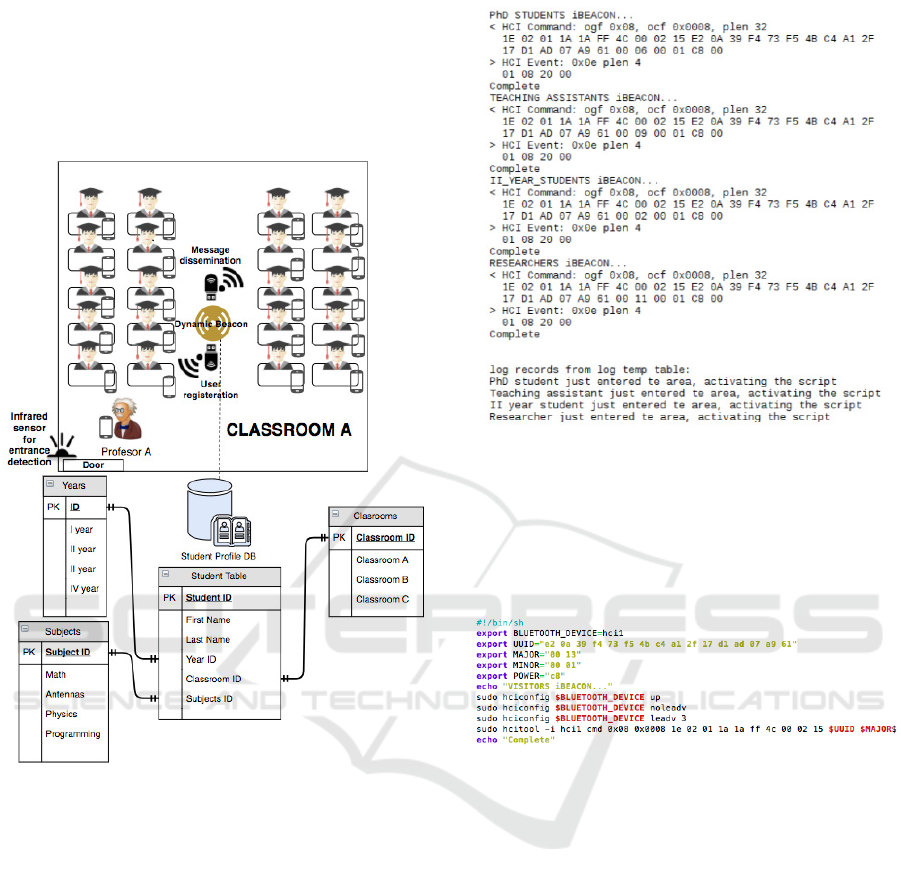
case, a single dynamic beacon device is planted in the
middle of the ceiling of one of the classrooms, for the
uniform distribution of signal, and it is activated to
work in a discovery mode (see Figure 3).
Figure 3: System architecture.
To evaluate the performance of the proposed
system, we have conducted an experiment on the
premises of the Faculty of Engineering and Telecom-
munications of Vigo in Spain. To show that single
beacon device is capable of acquiring different user
profiles, we planted it in one part of the faculty area
and gathered information during a short period. As
already mentioned before, user profiles had to be im-
plemented, according to some taxonomy and inserted
into the ”Student Profile” database. We were able to
recognize and collect four users simultaneously what
can be seen in Figure 4. From the Figure 4 we can
see that the device after recognizing specific profile
(user), by scanning his phone’s MAC address, it acti-
vates the script for some information distribution. The
device broadcasts an iBeacon combination ID (UUID,
Major, and Minor values) that corresponds to a partic-
ular user profile. An example of the iBeacon combi-
nation and how the BLE advertising device (hci1) is
Figure 4: Simultaneously recognized users.
activated before sending the corresponding combina-
tion ID can be seen from the Figure 5. Let us not
forget that for the notification part, an application has
to be developed and installed on the users’ smart de-
vices.
Figure 5: Combination ID script activation.
To acquire student attendance, we planted another
beacon device in one of the classrooms for precisely
one month and monitored the lecture that students
had on Monday’s from 9 h to 11 h. After collecting
and processing all the data (students’ devices MAC
addresses), the results were following: a) four users
were recognized continuously during the periods of
the lecture on different days (18th, 25th of Septem-
ber, 2nd, 9th of October) (see Table 1). b). All the
users were recognized by the system approximately
every 5 minutes, which is satisfying if we consider
that the beacon was configured to discover users the
same amount of time. The beacon device could have
been configured to collect the student attendance af-
ter less amount of time. However, in our case, that
was not necessary since we found convenient that a
five minute period was more than enough. We have to
take into account that student entered the classroom
pretty much around the same time. On the other hand,
they left the class at different times (September 18 of
Automatic Attendance Control System based on BLE Technology
293
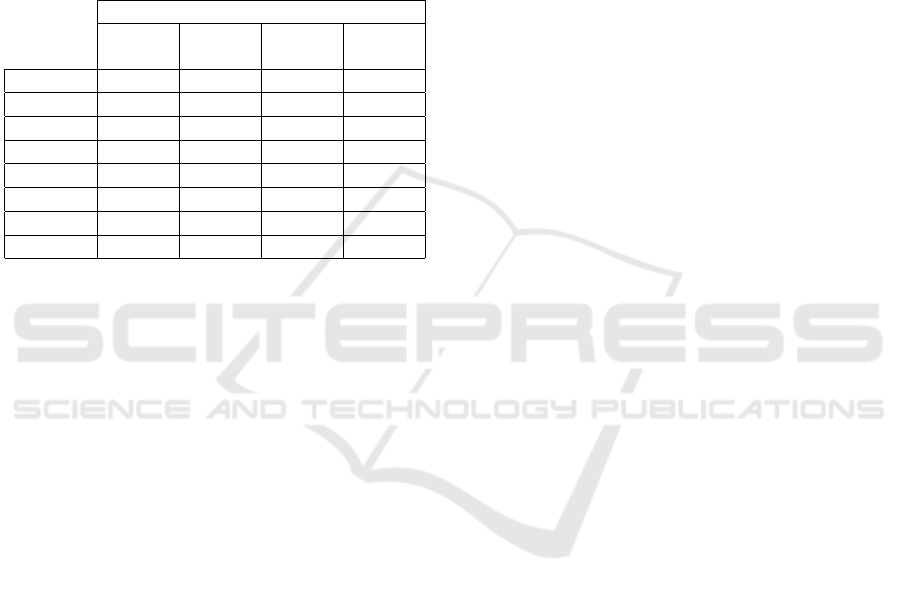
at 10:50 h, September 25 at 11 h, October 2 at 10:41
h, and on the 9th of October at 10:29 h) (see Table
1). Furthermore, two users that were not part of the
class were discovered by the system on October 9th.
This behavior is probably due to the signal overlap-
ping what we explained before in the paper. Also,
the students do not meet the class period requirements
since they were only recognized once in two hour pe-
riod, and we can consider them as not valid for the
specific lecture attendance list.
Table 1: Recognized users in the classroom.
Classroom 218
08:57 -
10:50
09:01 -
11:00
09:01 -
10:41
09:03 -
10:29
User 18/09 25/09 02/10 09/10
Hanna 25 29 20 16
David 24 27 21 19
Marion 26 31 25 19
Anna 28 30 21 17
Jane 1
Luke 1
Average 5 4 6 7
We have to mention that no influence on users was
done, regarding their smart devices and activating the
BLE protocol, whatsoever. Also, for the sake of user
privacy, we had to change users MAC addresses for
randomly generated names.
5 CONCLUSION
Even though beacon devices are becoming more pop-
ular and it is evident that lately are included in many
research and business projects, their potential is un-
derutilized. That said, the majority of processing is
handled by the application, which resides on a user’s
smartphone or some other compatible device. How-
ever, letting the software part to do all the process-
ing can become application saturated, and if we take
into account that today’s users have many apps in-
stalled on their device, the problem is evident. In
this work, we presented the solution where a part of
the processing job is shifted and assigned to the bea-
con device. Such method can help us to overcome
the early mentioned problem of possible application
over-processing. It does that by recognizing and serv-
ing simultaneously many user profiles and can have a
significant potential in any message dissemination or
collecting data environment.
This method of including beacon device into more
active processing and system involvement according
to particular inputs can be used in many areas. It
makes it even easier since Raspberry Pi accepts broad
types of sensors for different requirements and it
makes a perfect device for any beacon solution. That
being said, we give an indicative list of applications
where this solution can find a use:
• Space analytics, where users are monitored
through their movements while using building as-
sets. Such analytics are especially useful for
building managers and their future planning of
building expansion and better management of the
building environment.
• Hospital system and indoor localization, where
the patients are divided into different groups and
the hospital personnel are in charge of its patient
group. This way the doctor when in beacon prox-
imity can receive an instant update and the loca-
tion of his patients without any extra processing.
• Any extending of cloud computing to the edge of
an enterprise’s network, better known as Fog com-
puting, where the operation of computing, net-
working services, and storage is facilitated be-
tween end devices and cloud computing data cen-
ters.
In this work, we offer preliminary results, and for
the future work, we plan to implement the system
through all Faculty areas and along with obtaining
student attendance through more extensive tests. We
also expect to pair the dynamic beacon solution with
the corresponding application. The application would
be installed on users’ phones and interact with stu-
dents on a daily basis by sending them interest-based
information. The additional part would be collecting
student movement data that later would be processed
for better space analytics.
ACKNOWLEDGEMENTS
This work is funded by: the European Regional De-
velopment Fund (ERDF) and the Galician Regional
Government under agreement for funding the At-
lantic Research Center for Information and Com-
munication Technologies (AtlantTIC); the Spanish
Ministry of Economy and Competitiveness under the
National Science Program (TEC2014-54335-C4-3-
R and TEC2017-84197-C4-2-R); and the European
Commission under the Erasmus Mundus Green-Tech-
WB project (Smart and Green technologies for inno-
vative and sustainCable societies in Western Balkans;
551984-EM-1-2014-1-ES-ERA MUNDUS-EMA21)
WINSYS 2018 - International Conference on Wireless Networks and Mobile Systems
294

REFERENCES
Apoorv, R. and Mathur, P. (2016). Smart attendance man-
agement using Bluetooth Low Energy and Android. In
2016 IEEE Region 10 Conference (TENCON), pages
1048–1052.
Boric, M., Fernandez Vilas, A., and P. Diaz Redondo, R.
(2018). Analysing the potential of ble to support dy-
namic broadcasting scenarios. International Journal
of Ad hoc, sensor and Ubiquitous Computing (IJA-
SUC).
Komai, K., Fujimoto, M., Arakawa, Y., Suwa, H.,
Kashimoto, Y., and Yasumoto, K. (2016). Elderly
person monitoring in day care center using Bluetooth
Low Energy. In 2016 10th International Symposium
on Medical Information and Communication Technol-
ogy (ISMICT), pages 1–5.
M. Boric, R. P. Diaz Redondo, and A. Fernandez Vilas
(2018). Dynamic Content Distribution over BLE
iBeacon Technology: Implementation Challenges.
Thessaloniki. IEEE Xplore.
Martin, P., Ho, B.-J., Grupen, N., Munoz, S., and Srivas-
tava, M. (2014). An ibeacon primer for indoor lo-
calization: demo abstract. In Proceedings of the 1st
ACM Conference on Embedded Systems for Energy-
Efficient Buildings, pages 190–191. ACM.
Newman, N. (2014). Apple iBeacon technology briefing. J
Direct Data Digit Mark Pract, 15(3):222–225.
Putra, G. D., Pratama, A. R., Lazovik, A., and Aiello, M.
(2017). Comparison of energy consumption in Wi-Fi
and bluetooth communication in a Smart Building. In
2017 IEEE 7th Annual Computing and Communica-
tion Workshop and Conference (CCWC), pages 1–6.
S. Barapatre, A., A. Shelake, V., Y. Pawar, G., and D.R., A.
(2017). Smart College System using IoT BLE Bea-
cons. Internation Jurnal of Advanced Research in
Computer and Communication Engineering, 6. DOI:
10.17148/IJARCCE.2017.6485.
Saraswat, G. and Garg, V. (2016). Beacon controlled cam-
pus surveillance. In 2016 International Conference on
Advances in Computing, Communications and Infor-
matics (ICACCI), pages 2582–2586.
Shende, P., Mehendarge, S., Chougule, S., Kulkarni, P., and
Hatwar, U. (2017). Innovative ideas to improve shop-
ping mall experience over E-commerce websites us-
ing beacon technology and data mining algorithms. In
2017 International Conference on Circuit ,Power and
Computing Technologies (ICCPCT), pages 1–5.
Srinivasan, V. S., Saleem, Kumar, T., and Yasarapu, D. K.
(2016). Raspberry Pi and iBeacons as environmental
data monitors and the potential applications in a grow-
ing BigData ecosystem. In 2016 IEEE International
Conference on Recent Trends in Electronics, Infor-
mation Communication Technology (RTEICT), pages
961–965.
Townsend, K., Cuf, C., and Davidson, R. (2014). Getting
started with Bluetooth low energy: Tools and tech-
niques for low-power networking. ” O’Reilly Media,
Inc.”.
Trifunovic, S., Distl, B., Schatzmann, D., and Legendre, F.
(2011). WiFi-Opp: Ad-hoc-less Opportunistic Net-
working. In Proceedings of the 6th ACM Workshop
on Challenged Networks, CHANTS ’11, pages 37–42,
New York, NY, USA. ACM.
Automatic Attendance Control System based on BLE Technology
295
