
Reach to Teach: Preparing Cybersecurity Experts as Adjunct
Community College Faculty
Rachelle Heller
a
, Costis Toregas and Lance Hoffman
The George Washington University, Department of Computer Science, Washington DC, U.S.A.
Keywords: Active Learning, Cybersecurity, Community Colleges, Faculty Development, Learning Environment.
Abstract: While the nation should maintain and expand the educational capabilities in cybersecurity given the current
high demand for this sector, currently there exists a capacity issue: students cannot readily be added to the
education system, especially at the Community Colleges level, because trained faculty to accommodate
expanded academic demand are scarce. Cybersecurity experts in the workforce have the potential to fill the
need for part-time cybersecurity faculty at the Community College level. The challenge is to prepare these
technology-savvy individuals with classroom pedagogical insights and skills which not usually part of a
cybersecurity experts skillset.
A research question for this development project is “Can we use an online environment to provide pedagogy
training for potential adjunct community college faculty.” Currently, the Reach To Teach project is exploring
this possibility through a research effort engaging current faculty, as well as education experts, and a pilot
Reach To Teach online course that is being made available to these cybersecurity experts. The Reach to Teach
pilot is a set of six sessions, each of which includes the following: introduction to Community Colleges, ethics,
and ideas for classroom pedagogy (e.g. the general structure of a course, crafting goals and objectives,
techniques for moving explanations from the concreate to the abstract, using group work using case studies,
and using discussions in classes).
The team hosted a content review with community college educators and the pilot has been evaluated by 12
members of the target population. Their suggestions for improvement included. In addition to addressing these
concerns, the revised pilot includes a modified interactive experience, Viewers are now able leave comments
that can be read and replied to by course leaders or other individuals viewing the material.
1 THE NEED
In order to maintain and expand capabilities in the
world of cybersecurity – whether planning new
technologies for the internet of things (IoT),
preparing defenses, constructing offensive tactics, or
developing appropriate policies – a well-educated
workforce is needed (Gray, 2016; Heritage
Organization, 2013; NSF 2013; The White House,
2014). In the United States alone, to fill available
government jobs which the Department of Homeland
Security indicates is in the many thousands,
numerous pathways have to be opened including on
the job training, community college programs as well
as traditional four year and graduate programs. Each
of these avenues educates and trains individuals to
a
https://orcid.org/0000-0000-0000-0000
work at different levels and in different capacities in
our ‘cyber’ world.
The most recent Cybersecurity Commission
Report (Cybersecurity Commission, 2016) includes
Imperative 4 which addresses building workforce
capabilities. As they note, building such a workforce
is not possible without an education pathway for
potential members of the cyber-workforce. Currently,
there is a capacity issue: students cannot readily be
added to the education system, especially, at the
community college level, because trained faculty are
scarce. The weak link in the cybersecurity workforce
supply chain is often finding faculty and teacher
effectiveness. Therefore, the success of Imperative 4
depends, in large part, on the capacity of our
educational institutions and capabilities of our
educators.
338
Heller, R., Toregas, C. and Hoffman, L.
Reach to Teach: Preparing Cybersecurity Experts as Adjunct Community College Faculty.
DOI: 10.5220/0007612603380343
In Proceedings of the 11th International Conference on Computer Supported Education (CSEDU 2019), pages 338-343
ISBN: 978-989-758-367-4
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

One solution has been the National Science
Foundation (NSF) supported Scholarship for Service
(SFS CyberCorps) program both at the university and
now the community college level. The SFS Program
provides scholarship funding for students in the areas
of cybersecurity. All recipients are required to work
within the Federal, State, Local or Tribal Government
as a cybersecurity professional for a period of time
equal to the length of the scholarship So far, however,
graduates have primarily gone to federal government
agencies, national labs, or Federally Funded Research
and Development Centers.
Community colleges are institutions of higher
education, typically two-year experiences that have
an “open enrollment” for students who have
graduated from high school. A community college
usually provides workforce education as well as
college transfer academic programs. The nation is
looking to our community colleges as an untapped
source of cybersecurity workers for the various
workforce needs. According to the NSF,
“Community colleges can play a critical role in giving
students the hands-on skills that are needed on the
front lines (of) defending computer networks,
(Heritage Organization, 2013)”. And, while some
community colleges have existing programs in
cybersecurity and have dedicated full time faculty,
according to the Center for Community College
Student Engagement, more than 58% of community
college classes are taught by adjunct faculty.
Although the data is not broken out by discipline,
informal conversations with local community college
leaders revealed that they rely heavily on adjunct
faculty, and most of these have no teaching
experience when they begin. Lankard (1993) says
part-time faculty are employed primarily for their
professional competence rather than their
pedagogical training, therefore many lack the
teaching skills and teaching experience required to
ensure instructional integrity in the classroom. In fact,
“No formal preparation for a teaching position is
required other than the desired academic credential”
Twombley and Townsend (2008, p15) and for
students who complete a community college
education is the quality, preparation, and pedagogical
skills of the faculty have to be central. According to
the American Association of Community Colleges,
there has been huge growth in the percentage of
higher education faculty teaching in community
colleges and the biggest group contributing to that
growth are the part time faculty.
A typical advertisement indicating the
requirements for a cyber-security faculty member at
a community college includes: Bachelor's degree
(Master's preferred) and five years of work
experience as a Computer Forensics professional.
They are also expected to have technical
qualifications and certifications such as: CompTIA
Network+, CompTIA Security+, CISCO
certifications, CISSP, SANS, Certified Ethical
Hacker (CEH)), as well as a knowledge of
Programming Languages, excellent written and oral
communications skills, experience in leadership
including a history initiating and managing change,
working with others toward shared goals and
developing others.
Nearly 4 in 10 students in higher education attend
a community college. A typical community college,
unlike a student in a 4-year research university or
liberal arts college, are employed at least part-time,
have a family, are enrolled only part time, or a
combination of all three. Personal and global
economics have a great deal to do with an individual’s
choice to attend a community college as they offer a
lower cost option and different time demands. As a
group, community college students are not as
homogeneous as students in four-year programs.
Many entering community college students are older
than 19-year-old freshmen in 4-year universities, and
more are returning students seeking new employment
opportunities. Community college students can have
bachelors or advanced degrees, and are likely
working full- or part- time with huge demands
(including children) on their non-class time. The
community college student, like every student, is not
monolithic –some are more prepared that others but
as a group they are like other students; however, their
experiences provide them with choices towards either
a terminal degree or as a pathway as a stepping stone
to a 4-year institution or are enrolled at both a
community college and a 4-year at the same time
using the community college to fill in gaps (thereby
often ‘serving two masters’).
2 FILLING THE NEED
The Reach to Teach pilot focuses on the more than
2,200 nationwide SFS CyberCorps alumni, all of
whom have at least a bachelor’s degree and most have
a master’s degree (some even a PhD). They are highly
educated and have unique experiences that they can
bring to the classroom. These men and women, as
current or former government employees, have had
access to the latest technologies, wrestled with the
current problems and policies facing the nation, have
taken leadership roles and have a wide network upon
which to rely for developing academic and career
Reach to Teach: Preparing Cybersecurity Experts as Adjunct Community College Faculty
339

goals. Even those who have left government service
usually work with cybersecurity content on a daily
basis. Graduates from the 2013 cohort, and before,
have at least 5 years of cybersecurity work experience
The pilot program for Reach to Teach concept
offers SFS cyber-experts the opportunity to
participate in this online program with the expectation
that they will consider working with one of their local
community colleges as an adjunct faculty member.
As noted above, cyber-experts have the requisite
cybersecurity content knowledge and experience to
teach at this level. However, they typically do not
have teaching experience or knowledge of diverse
classroom learning and assessment techniques.
Furthermore, most are not (yet) a product of the
community college pathway and they do not
understand the community college student and their
challenges/opportunities.
Educator capacity building is built upon
classroom research. The Reach to Teach pilot
provides an asynchronous, online course to build
teaching capacity as framed by (Newmann et al.,
2000; King and Newmann, 2004) research. This work
asserts that educational change requires
improvements to staff knowledge, skills and
dispositions. Reach to Teach coursework is designed
to build faculty capacity in key areas such as
assessment, curriculum resources, expectations for
students, building sense of self-efficacy, learner
characteristics, legal obligations, and the use of online
learning to support individual and collaborative
projects. Reach to Teach uses Angelo and Cross’
(1993) Classroom Assessment Techniques to support
participants’ ability to facilitate learning. Typical
classroom Assessment Techniques (CATs) which are
short, anonymous assessments such as requiring
students to complete a one sentence summary of
material, or a student-generated list of real-world
applications, have been demonstrated to increase
faculty-student interactions and active classroom
participation (Angelo and Cross, 1993; Morris, 1994;
Samanta, 1994; Simkins, 2018)
3 REACH TO TEACH
3.1 The Six Sessions
Reach to Teach is designed to address target faculty
expectations concerning the pedagogy for successful
classroom teaching. This is crucial because an
educator’s expectations for their student is critical for
student success (Newmann et al, 2000).
The content of this course provides background
information and learning experiences to build an
understanding of the community college
environment, the
student body and the related learning
opportunities. The material addresses the following
questions:
What is the role of a community college in
cybersecurity career preparation? What do
employers expect from community college
students and their preparation?
What support do community college students
need to advance – those who are less experienced
as well as those with experience?
What opportunities can be provided to develop
each student’s skills, while still offering the most
dedicated students a chance to pursue their
academic interests as fully as possible?
What challenges and benefits does classroom
diversity bring to classroom discussions and
projects?
How do you harness the community college
students’ life and work experiences to improve the
classroom and projects?
What pedagogic tools are worthwhile in this
setting?
Cyber-experts who complete Reach to Teach would
be in a position to serve both as technically and
pedagogically prepared adjunct faculty. This
potential increase in available adjunct faculty would
enable the education of more cybersecurity students
which would in turn add qualified workers to the
cybersecurity work-force in numbers higher than
currently possible. As the cyber-experts move into
adjunct teaching positions at community colleges, the
community college students will benefit from the
intellectual and employment experiences of cyber-
experts who were previously not adjunct faculty at
community colleges.
3.2 Development of the Online Reach
to Teach Program
In the fall of 2017, we convened an online focus
group of Community College faculty and researchers
and one face to face workshop of community college
faculty, 4-year CyberCorps faculty and teacher
education faculty to provide detailed direction on the
learning science and resources to include in the
course. The workshops and follow-on work resulted
in actual teaching strategies and units for Reach to
Teach. The online focus group produced a scope and
sequence chart. The face to face, 2-day workshop in
CSEDU 2019 - 11th International Conference on Computer Supported Education
340
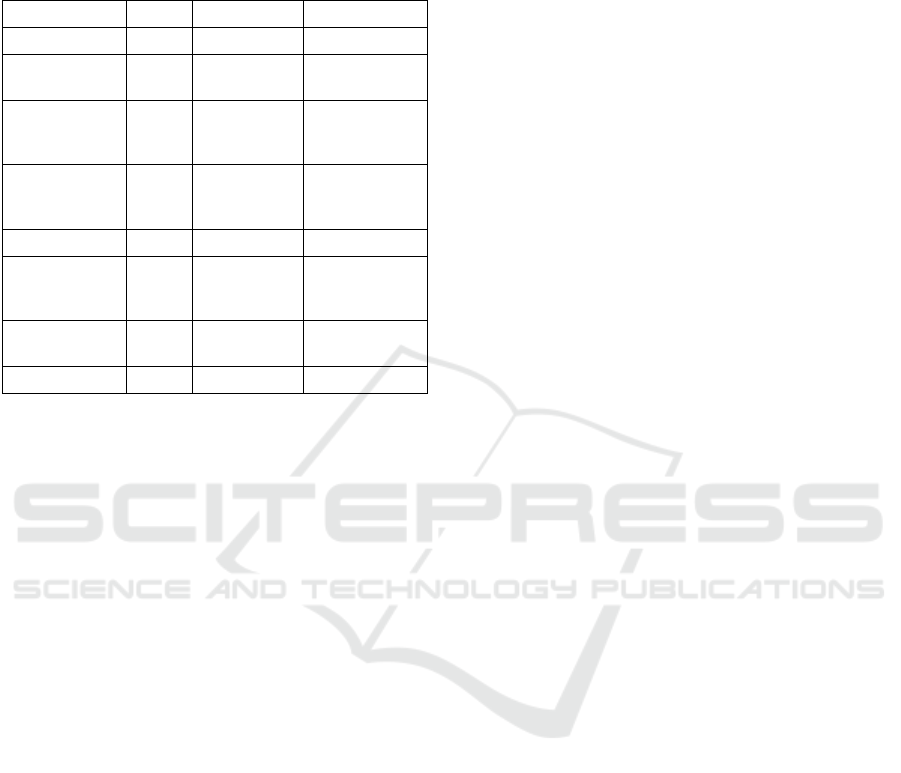
January 2018 found the resulting chart too
complicated and overly pedantic. The result of the
workshop was a revised scope and sequence chart, of
which Sessions 1 and 2 are shown in Figure 1.
Topic Time Session 1 Session 2
Introduction 3 min.
Community
College Context
5 min.
Legal and
Ethical Issues
5 min.
Ethical
concerns in
the classroom
Definition of
plagiarism
Instructional
strategy
27 min.
Setting
Objectives
Going from
concrete to
abstract
Applications 7 min.
Assessment 5 min.
Formative
assessment
Feedback and
Performance
Assessment
Engaging
students
5 min. Ice breakers
Providing
Support
Review 3 min. Review Review
Figure 1: Sample Scope and Sequence: Sessions 1 and 2.
3.3 Pilot
Based on the results of the online discussion group
and the workshop, a series of 6 sessions were
sketched out. Requests for interviews on first person
experiences were made to community college
colleagues. Community College leaders were
interviewed concerning the mission, benefits and
challenges of teaching at a community college.
Content was gathered that was consistent with the
scope and sequence developed after the face to face
workshop. Videos available on You-tube and other
sources were included to avoid re-inventing the
wheel. The content of the six sessions, presented in a
very simple Power Point series with minimal layout
and with video snippets, was reviewed by our two
community college experts of the grant. Before
handing the material over to a graphic artist to prepare
the distribution version, it was imperative to resolve
two issues – how to make the sessions independent of
a leader but at the same time have an interactive feel
and how to make the sessions easily accessible. While
the latter was readily addressed by storing the Power
Point sessions on a public Dropbox, the former was
more of challenge.
Reach to Teach encourages active learning in the
session discussions, but without a moderator it would
be difficult to support true active learning. And,
creating the materials that would depend on a
moderator limited, we believed, the access to the
materials themselves. “Students” would have to be
gathered into some sort of cohorts and the sessions
run on some schedule. Our vision was more of an
independent resource that could be used in the true
engineering education concept of ‘just in time
learning’ (Simkins, 1994). The decision was to ask
questions during the sessions and encourage the
students to think about their answers before
proceeding to the next slide or to do the homework
before the next session. In either case, subsequent
slides asked the students “Did you think of this?” and
suggested a few possible answers or homework
solutions.
With these two issues (temporarily) resolved, the
graphics expert prepared a template for all sessions.
The consistent look and feel of the visuals contribute
to the ‘moderator independent’ structure of Reach to
Teach. Additionally, the templates make edits and
revisions easy to accomplish. Finally, all sessions
were narrated. Final versions were distributed for
evaluation.
4 EVALUATION
As noted above, while pedagogic training is important,
there is typically no required classroom training for adjunct
faculty and therefore nothing against which we might
compare our material. If there is training at all, it is related
to forms and procedures of the college than to pedagogy.
Some community colleges encourage that departments
assign mentors to new adjunct faculty. Our evaluation
was based on multiple reviews: content literature
review, content validation with adjunct coordinators
at community colleges, content refinement through
community participation, and content review by
community participation. Feedback in these
categories was received from educators and potential
students.
The content validation was achieved by reviews
from working adjunct and permanent community
college faculty through the online blog and through
conference workshops and presentations. The
sessions were made available online
(https://blogs.gwu.edu/seas-reachtoteach/). (The
authors continue to welcome comments from readers
who access these sessions. A comment sheet is
available at the site). The sessions have been
informally reviewed at one Community College
Cybersecurity Conference (3CS, 2018) and were well
received.
A team of students, who were not part of the
design or development of the 6 sessions created an
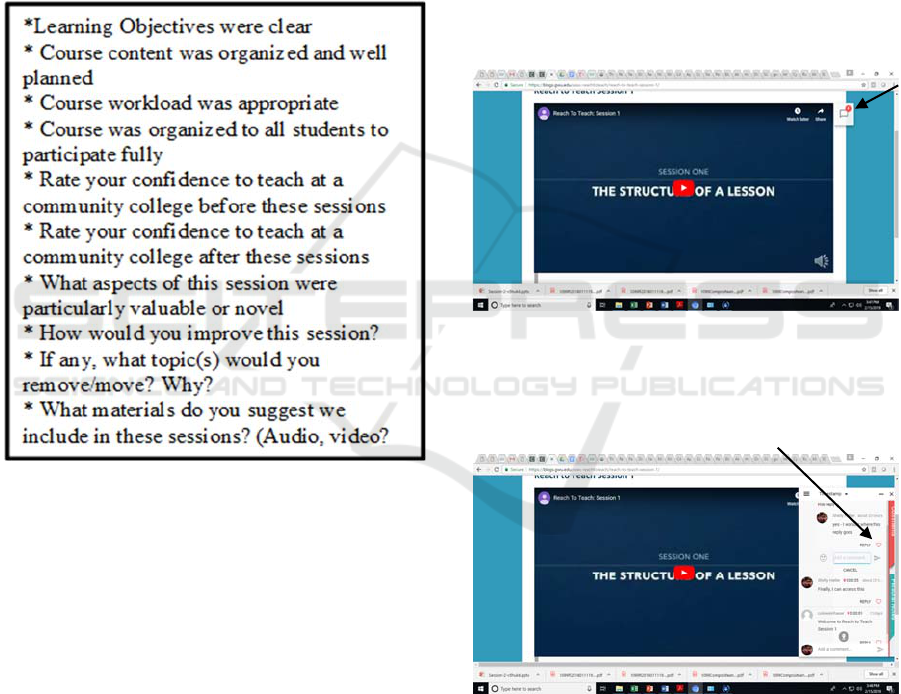
evaluation rubric (Figure 2) and shared the sessions
Reach to Teach: Preparing Cybersecurity Experts as Adjunct Community College Faculty
341
with 12 SFS CyberCorps alumni, the typical target of
the project. Of the 12, none had ever taught at the
community college. One had been a teaching assistant
during some graduate work, but was responsible only
for grading homework, not for creating a lesson. All
indicated they thought they might enjoy teaching at a
community college. None felt that they would be
teaching in the next six months, but would consider it
in the future. Respondents reported that they required
about an hour to review the material and comment the
evaluation form. Since the sessions themselves are
about an hour long, it seems that reviewers may not
have watched every moment of the various videos.
Figure 2: Survey Questions for Each Session.
The survey review yielded 4 positive outcomes.
All respondents agreed that the learning objectives
were clear and the course organization was such that
all students could participate fully. Reviewers
positively commented concerning the course content
and the novel aspects of the session(s).
For example: “I Strongly Agree; Teaching and the
history of community colleges was interesting;
Highlighting the importance of class objectives
having observable results was immediately useful”
“It (sic the session) provided examples of what the
instructor is trying to teach. The embedded guest
presentations were very engaging the iterative
approach shown for refining objectives was engaging
and felt useful”.
There were two categories of outcomes to be
addressed to improve the sessions. The editorial ones
were easily resolved and they included correcting a
broken link and a typo or two. One comment
suggested the annotated video about the structure of a
lesson could be removed, but others considered it
valuable. Suggestions for improvements included
adding closed captioning, suggested moving the
password discussion and expanding the discussion on
case studies for clarity on the importance of goals and
objectives for their use.
One of the biggest challenges continued to be how
to make the sessions as interactive as possible without
requiring a leader or a cohort structure. We are
currently reviewing Annoto
(https://www.annoto.net/) as a tool to provide
asymmetric interactivity to the site. Figure 3 shows
the opening of Session 1 with the interactive
comment icon in the upper right-hand corner.
Figure 3: Reach to Teach.
Figure 4 indicates what the system looks like
when a viewer has left a comment or started a
dialogue.
Figure 4: Asynchronous comments and replies.
5 FUTURE WORK
The sessions are now readily available and we expect to
host a wide-reaching field study to determine whether the
cybersecurity experts can, and will, use these sessions. And,
if they do use them, do they find them useable and useful
for their adjunct teaching experience.
CSEDU 2019 - 11th International Conference on Computer Supported Education
342

ACKNOWLEDGMENTS
Reach to Teach was developed at the George
Washington University under a grant from the
Department of Defense: Grant# H98230-17-1-0371
Special acknowledgements go to Cole Weinhauer,
Stephen Salas and David Matcham
REFERENCES
3CS Conference. Available on the web at
http://www.my3cs.org/
Angelo, T. A. & Cross, K. P. 1993. Classroom assessment
techniques: A handbooks for college teachers. San
Francisco: Jossey-Boss.
Cybersecurity Commission Report, 2016. Available on the
web on December 5, 2016: https://www.whitehouse.
gov/sites/default/filers/docs/cybersecurity_report.pdf
Grey, D., 2016. Available on the web: November30,2016
http://www.baesystems.com/enus/artcile/deette-gray-s-
keynote-speech-to-the-national-initiative-for-cybersec
urity-educationconference
Heritage Organization, 2013. Available on the web on
December 1, 2016. http://www.heritage.org/research/
reports/201304/a-congressiona-guide-seven-steps-to-
ussecurity-prosperity-and-freedom-in-cyberspace
King, M. and Newmann, F., 2004, Key link: Successful
professional development must consider school
capacity. Journal of Staff development 25 (1), 26-30.
Lankand, B. A. 1993. Part-time faculty in adult and
vocational education. Columbus Ohio: ERIC
Clearinghouse on Adulty, Career and Vocational
Education.
Newmann, F. King, M., Youngs, P. 2000, Professional
Development that addresses school capacity: Lessons
from urban elementary schools. American Journal of
Education, 108(4) 259-299.
NSF, 2013. Available on the web on December8, 2016.
http://www.nsf.gov/news/special_reports/science_nati
on/cybersecurity,jsp
The White House, 2016, National Security Action Plan.
Available on the web August 25, 2018. https://
obamawhitehouse.archives.gov/the-press-office/2016/
02/09/fact-sheet-cybersecurity-national-action-plan.
Morris, B., 1994. CATS Project: Reinvigorating our
classrooms: Positive results of using classroom
assessment techniques. In Patricia Malinowski (ed.)
Classroom implementation: Issues in assessment (14-
23) Canadaigua, NY Finger Lakes Community College.
Murphy, B., 1994. CATS project: Seeing problems, finding
solutions. In Patricia Malinowski (ed.) Classroom
implementation: Issues in assessment (14-23)
Canadaigua, NY Finger Lakes Community College.
Samanta, S., 1994, CATS in cooperative physics. In
Patricia Malinowski (ed.) Classroom implementation:
Issues in assessment (14-23) Canadaigua, NY Finger
Lakes Community College.
Simkins, S., Using just-in-time teaching (JiTT) to
understand student thinking, improve preparation for
class and enhance student learning. Available on the
web August 23, 2018 at http://www.elon.edu/dosc/e-
web/academics/teaching/tlconference/JiTT%20Hando
ut%20-%20August%202012.pdf
Twomble, S. & Townsend, B., 2008. Community College
Faculty: What we know and need to know. Community
College Review 6 (1).
Reach to Teach: Preparing Cybersecurity Experts as Adjunct Community College Faculty
343
