
Authentication and Authorization Issues
in Mobile Cloud Computing: A Case Study
V. Carchiolo
1
, A. Longheu
2
, M. Malgeri
2
, S. Ianniello
3
, M. Marroccia
3
and A. Randazzo
3
1
Dipartimento di Matematica ed Informatica, Universit
`
a degli Studi di Catania, Catania, Italy
2
Dip. di Ingegneria Elettrica, Elettronica e Informatica, Universit
`
a degli Studi di Catania, Catania, Italy
3
STMicroelectronics, ICT Technical Excellence Center, Catania and Naples, Italy
mario.marroccia@st.com, giuseppe-angelo.randazzo@st.com
Keywords:
Cloud Computing, Authentication, Authorization, Accounting, Security, Mobile Devices.
Abstract:
Mobile Cloud Computing incorporates Cloud computing paradigma into the mobile environment, the set of
technologies that enable to access network services anyplace, anytime and anywhere. This faces many techni-
cal challenges, such as low bandwidth, availability, heterogeneity, computing offloads, data accessing, security,
privacy, and trust. In this paper the MCC security solution developed and applied within the STMicroelectron-
ics plants is presented.
1 INTRODUCTION
We are living in the Age of Networked Intelligence
and our individual environment as well as company’s
world is being re-imagined.
The key enablers of this radical mutation include
a wide range of voracious consumers, a business cul-
ture and a rise in global flows of goods, services, cap-
itals and information. Moreover, a constellation of
technologies endorses this phenomena: Internet, mo-
bile and broadband networking, big data and analytic
and smart, digitally interconnected things. This eas-
ily leads to the Cloud Computing, that enables con-
sumers, small and big businesses, corporations and
governments to easily access computing resources
with little or no effort, upfront investment or commit-
ment.
Mobile Cloud Computing (MCC) incorporates
Cloud computing into the mobile environment, the set
of technologies that enable people to access network
services anyplace, anytime, and anywhere.
MCC refers to an infrastructure where both data
storage and the processing occur outside of the mobile
device. Mobile Cloud applications move the comput-
ing power and data storage away from mobile phones
and into the Cloud, bringing application and mobile
computing to a much broader range of mobile sub-
scribers than just smartphone users.
The integration of Cloud computing and mobile
networks faces many technical challenges, such as
low bandwidth, availability, heterogeneity, computing
offloads, data accessing, security, privacy, and trust,
all enforced by the dramatic increase in the use of
smartphones in recent years.
According to this scenario, a specific aspect of
mobile Cloud computing security is addressed in this
work: authentication and authorization. As in several
works arises (Todorov, 2007) (Alizadeh et al., 2016),
resources that discuss in depth authentication tech-
nologies either focus on mechanisms provided by spe-
cific products or services, or on the theory behind user
authentication with complete detachment from indus-
try solutions. Here we illustrate the MCC security so-
lution developed and applied within the STMicroelec-
tronics® IC manufacturer plants; the proposed system
allows users authentication and authorization accord-
ing to the security standards and lies in the Cloud and
mobile Cloud environment introduced previously. In
particular, the solution addresses the following issues
• Reduce and/or eliminate the need to store multi-
ple passwords and multiple username for different
services
• Reduce time spent re-entering passwords and
username for the same identity
• Simplify the definition and management of secu-
rity policies
In addition, the solution also has to take into ac-
count the complexity of both the geographical and
Carchiolo, V., Longheu, A., Malgeri, M., Ianniello, S., Marroccia, M. and Randazzo, A.
Authentication and Authorization Issues in Mobile Cloud Computing: A Case Study.
DOI: 10.5220/0007658602490256
In Proceedings of the 9th International Conference on Cloud Computing and Services Science (CLOSER 2019), pages 249-256
ISBN: 978-989-758-365-0
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
249

organizational extension of the company with all the
resulting constraints, also considering many intercon-
nected ERP activities as supply chain (including fac-
tory automation), finance, purchasing, sales and mar-
keting (compliant with today’s cutting-edge Cloud
platforms, e.g. (salesforce, 2019)) and business intel-
ligence.
The rest of paper is organized as follows: in sec-
tions 2 and 3 we first introduce the Cloud paradigm
shifting towards the MCC extension, providing an
overview of relevant architectures, issues and applica-
tions and finally its security issues, in authentication
and authorization. In section 4 the solution adopted
within STMicroelectronics is shown, together with a
description of the tools and technologies used. Our
conclusions are finally discussed in section 5.
2 MCC AND RELATED ISSUES
Cloud Computing is a model for enabling ubiquitous,
convenient, on demand, network access to a shared
pool of configurable computing resources that can be
rapidly provisioned and released with minimal man-
agement effort or service provider interaction (Pe-
ter Mell, 2009).
According to (Sanaei et al., 2014), the Mobile
Cloud Computing (MCC) is ”a rich mobile comput-
ing technology that leverages unified elastic resources
of varied clouds and network technologies toward un-
restricted functionality, storage, and mobility to serve
a multitude of mobile devices anywhere, anytime ...
based on the pay-as-you use principle”.
MCC is actually an extension of cloud comput-
ing and incorporates mobile computing and wireless
networking aiming to provide typical cloud services
to the mobile consumers. Substantial difference with
the classic cloud computing service is that in MCC
execution time and energy consumption are funda-
mental aspects and both are significantly improved
by transferring execution of resource-intensive appli-
cation from the hosting mobile device to the cloud-
based resource, therefore mobile devices exploiting
MCC are not required high resources. In addition to
data processing, in MCC also data storage is shifted to
cloud servers. Migrating these two workloads made
MCC an useful solution to obtain higher-level service
performance on mobile devices despite their (local)
resources.
2.1 Security
MCC joins several technologies, therefore it inherits
their pros and cons.
Here we want to focus on security issues, there-
fore we first consider generic cloud services, shifting
afterwards to MCC case. Cloud services can be gen-
erally considered high risky since they may:
• permit risky behaviour such as anonymous use
• lack basic security features such as encryption in
transit and admin activity logging
• have sneaky terms and conditions that put data at
risk
Cloud-based information systems are exposed to
threats that can have adverse effect on organizational
assets; risks to be addressed occur at three levels:
organizational, mission and business process and in-
formation system level. As well as traditional infor-
mation systems, in cloud-based information systems
risks must be managed throughout the system devel-
opment life cycle. Moreover, in a cloud ecosystem,
the complex relationship among cloud actors and their
processes require an integrated, ecosystem-wide risk
management framework.
When considering MCC, although several secu-
rity mechanisms have been developed, it is still not
safe enough for many users to offload their personal
data to the cloud. This perception is stronger than in
Cloud Computing because of the problems inherent
in the mobile environment.
While different measures can be implemented to
improve security of the services offered in the MCC,
its vulnerabilities are still related to technologies it is
based on (mobile computing, wireless networks, and
cloud computing), in particular:
1. Security of mobile devices
At this level, the main concern is the security of
handheld devices which have open operating sys-
tems, third-party applications, and wireless access
to the Internet anywhere, anytime, therefore, they
are vulnerable to the threats and risks as in PCs
and desktops. There are different approaches to
lessen the security issues related to mobile de-
vices. Antimalware programs are run on the de-
vices to identify and delete Trojan horse, viruses,
and worms. Periodically updating the OS and
downloading applications from known vendors
such as Google, Apple, and Microsoft can also
help. Also, unexplained links should not be tried,
receiving data transmission from strange phones
should be avoided, new, unauthorized software
should not be installed, and the interface of Blue-
tooth, Wi-Fi, and so on, should be shut down. If
a device is stolen or lost, there must be some re-
mote data wiping technique so that the data can-
not be misused. The mobile device can also use
CLOSER 2019 - 9th International Conference on Cloud Computing and Services Science
250

hardware-based encryption techniques for inter-
nal and external memory support.
2. Security of Wireless Communication Channel.
This level deals with issues related to securing
the wireless communication channel between the
mobile and cloud servers. Mobile devices ac-
cess their resources and services deployed in the
cloud environment through communication chan-
nels from cloud servers. This increases the num-
ber of wireless application protocol gateways and
IP multimedia subsystem equipment in the IP net-
work, giving rise to many new security threats in
the mobile Internet. These mobile terminals ac-
cess phone service, SMS, and other Internet ser-
vices using 3G, 4G, Wi-Fi, WiMax, and Blue-
tooth. These broad access methods may increase
security risks associated with networks, causing
information leakage and malicious attacks.
To protect data from leakage during communica-
tion between mobile device and cloud environ-
ment, several solutions are available. The mobile
users mainly encrypt data white transmitting into
the cloud so that an adversary cannot understand
or even be able to get the data. Secure transmis-
sion protocols such as TLS/SSL or VPNs can be
used to transfer data. Socket programming is also
used for secure transmission of sensitive data in a
cloud environment. Also, public key encryption is
used for protecting from Man-In-The-Middle at-
tacks. Strong password and biometric authentica-
tion should be used to enhance data security dur-
ing transmission. Even the rough access points in
public places should be avoided for security rea-
sons. Switching off the wireless interfaces, such
as Wi-Fi and Bluetooth, after using the mobile de-
vice will also help.
3. Security of Cloud Infrastructure.
At this level, users offload their data to the cloud
and lose control over this data. Cloud comput-
ing is based on virtualization technology, and if
there is some vulnerability in the virtualization
software, the data of one user on the same physical
server can be leaked to that of other users. There
is also the necessity of proper access control and
data management, according to the needs of the
consumer. Different techniques and mechanisms
for the protection of data in the cloud are provided
by cloud services vendors. To increase the trust of
customers for storing data in the cloud server, it
should provide privacy, authentication, confiden-
tiality, and availability of services. These secu-
rity mechanisms must be strong enough to handle
attacks by adversaries and hackers. There must
be also a mechanism to recover the user’s data if
lost or erased by an attacker. There should also
be a secure and efficient key management mecha-
nism for the cloud environment. Cloud should use
an implicit authentication technique to reduce the
risk of fraud in a mobile cloud.
Offloading personal information, data, and appli-
cation to the remote cloud as well as in communica-
tion channel raise various questions regarding secu-
rity, privacy, and trust; they involve both the commu-
nication and cloud level described before and can be
outlined as follows:
• Regulatory compliance: Cloud service providers
should have external audits and security certifica-
tion
• Privileged user access: When sensitive data get
offloaded to the cloud, it may appear that the data
are no longer under the direct physical, logical,
and personal control of the user owner of data.
• Data location: Exact physical location of user’s
data is not transparent, and this may result in con-
fusion in particular authorities and commitments
on local privacy needed.
• Recovery: Cloud providers should provide proper
recovery management schemes for data and ser-
vices when a technical fault or disaster arises.
• Data segregation: As cloud data are usually stored
in a shared space in a multi-tenant environment,
each user’s data should be separated and isolated
from the others with efficient encryption method-
ologies.
• Long-term viability: It must be ensured that user’s
data would be safe and accessible even in the
event the cloud company itself goes out of busi-
ness.
• Investigative support: For multiple customers,
logging and data may be co-located. Thus, it may
be vital, but hard, to predict any inappropriate or
illegal activity.
Installing and running local security software can
help get rid of various kind of malicious codes such
as viruses, worms, bugs and so on.
2.2 Authentication, Authorization and
Accounting
Whether a security system serves the purposes of in-
formation asset protection or provides for general se-
curity outside the scope of IT, it is common to have
three main security processes:
Authentication and Authorization Issues in Mobile Cloud Computing: A Case Study
251

• Authentication is used to determine and validate
user identity. It is often referred to as identi-
fication and authentication, the former provides
user identity to the security system (typically in
the form of a user ID), the latter is the pro-
cess of validating user identity by verifying user-
provided credential (e.g. password, PIN, certifi-
cates); in particular, the supplicant (authenticat-
ing user client) provides its identity and evidences
for it to the authenticator (i.e. the server), that
uses the Security authority/database as the stor-
age mechanism to check user credentials. Prac-
tical authentication process can be session-based
(i.e. using cookies) or HTTP-based (Basic or Di-
gest Authentication). Moreover, the growth of ap-
plications endorse the concept of Single Sign On
(SSO), i.e. a unified authentication for access in-
frastructure and service. Two SSO mechanisms,
namely OpenId and OAuth, are beginning to at-
tract users.
OpenID(Recordon and Reed, 2006)(OpenID
Foundation, 2019) is an open standard and de-
centralized authentication protocol. It was pro-
moted by the non-profit OpenID Foundation, it
allows users to be authenticated by co-operating
sites (known as Relying Parties or RP) using a
third party service, eliminating the need for web-
masters to provide their own ad hoc login systems,
and allowing users to log into multiple unrelated
websites without having to have a separate iden-
tity and password for each.
OAuth(Parecki, 2019) is a protocol framework
that attempts to facilitate interactions between ap-
plications in a properly secure manner. In partic-
ular, while OpenId just checks the user’s identity
and sends back a response confirming it, OAuth
sends back a token. This token can be used in
subsequent requests almost as a substitute for a
valid user session (avoiding password sharing),
to allow access to restricted resources. The 2.0
version of OAuth extends beyond the sort of data
exchange between Web sites, and can be applied
to authorizing mobile and desktop clients to ac-
cess restricted resources, and to authorization per-
formed by client-side scripts without an interven-
ing server application
• Authorization provides users the access to re-
sources that they are allowed to have and pre-
vents users from accessing resources that they are
not allowed to access. Typical implementations
are account-based, where rights to perform opera-
tions are associated with individual user accounts,
or role-based, where users are linked to a specific
role for which rights are granted.
• Accounting provides an audit trail of user actions.
This is sometimes referred to as auditing.
3 AUTHENTICATION IN MCC
User authentication in Mobile Cloud Computing is a
critical requirement in securing cloud-based computa-
tions and communications and with authorization are
one of the most important security issues for MCC
users. Both mobile device and cloud server should
authenticate each other in order to secure the com-
munication when the user with its device accesses the
cloud from any geographical location in the world,
using different networks and various mobile devices.
Adoption of MCC highly necessitates robust and
effective authentication solution by which users can
utilize the cloud-based services with any mobile de-
vices (e.g. smartphones, tablets) anytime, anywhere,
with low computing cost of the native resource. There
is a substantial difference between MCC and typical
mobile device authentication, in the first environment
the mobile devices connect to the Internet to perform
authentication. Moreover, the hungry-resource part
of authentication mechanism can be moved and pro-
cessed by the cloud servers.
User authentication in MCC is the process of
identifying and validating the mobile user to en-
sure that it is legitimate to access mobile cloud re-
sources. Due to limited resources of mobile devices,
optimal MCC authentication mechanisms should be
lightweight with the least possible computing, mem-
ory, and storage requirements.
3.1 MCC versus CC
Although the goal still remains to minimize security
threats, authentication mechanisms in MCC somehow
differs from those adopted in non-mobile cloud com-
puting. Some of the most important security threats to
mobile users are information leakage, denial of ser-
vice, malfunction and loss of device. These threats
have to be included in security threats that can man-
ifest as attacks via the services offered through the
wireless network, including network profiling, infor-
mation leakages, session hijacking, and jamming.
The capabilities and limitations of mobile devices
introduce some challenges for developing effective
and efficient authentication system. The most rele-
vant causes of discrepancy are linked with Network
heterogeneity, Resource limitations, Mobile and de-
vice sensors, High mobility (Carchiolo et al., 2019).
In table 1 the main differences between authentica-
tion requirements and principles in MCC and cloud
CLOSER 2019 - 9th International Conference on Cloud Computing and Services Science
252

Figure 1: Multi-factor authentication architecture.
computing are shown. In the following, MCC au-
thentication is discussed, both cloud-side as well as
the user-side approach.
Table 1: MCC vs CC comparison.
Metrics MCC CC
Resource limitation challenge not effective
Mobile device feature opportunity not effective
High mobility challenge not effective
Network heterogeneity challenge challenge
Wired or wireless comm. challenge not effective
3.2 Cloud-side MCC Authentication
As intuition suggests, in this case authentication is
performed on the cloud server and this is consid-
ered more flexible, efficient, and adjustable compared
to other methods due to the (possibly) unlimited re-
sources of cloud servers.
Such authentication can be either identity- or
context- based; in identity-based methods, several
credentials as unique ID, password, and biometrics
can be used; their combination leads to two-factor au-
thentication (easier) or even multi-factor (safer) au-
thentication (Jeong et al., 2015)(Mohsin et al., 2017).
This architecture (Fig.1) includes four main enti-
ties, i.e. mobile device, storage, a management server,
and a cluster host. Usually, Transport Layer Security
(TLS) protocol is used for communications between
the authentication service provider and wireless ac-
cess point. Five parameters are exploited to authenti-
cate the mobile user: ID/password, International Mo-
bile Equipment Identity (IMEI), International Mobile
Subscriber Identity (IMSI), voice and face recogni-
tion; for these last two note that privacy issues must
be addressed, though biometric methods seems more
appealing to users than passwords(Braz and Robert,
2006)).
The cluster host distributes these five parameters
to individual virtual machines (VM) to improve per-
formance of the authentication process. The manage-
ment server handles the load balancing on the VMs
in the clustered host. Users information are protected
in case of loss and theft using IMEI and IMSI; these
are encrypted with a hash function to avoid their clear
exposure.
As opposed to identity-based, in context-based
methods users are authenticated by analyzing mul-
tiple passive user information and requires minimal
user interaction. However, the accuracy is lower than
identity-based method because the authentication pro-
cedure depends on the accuracy of pattern analysis re-
sults.
3.3 User-side MCC Authentication
In user-side authentication method, steps are pro-
cessed in mobile devices that nowadays largely sup-
port such approach thanks to their significant per-
formance improvement. Also User-side authentica-
tion methods can be identify- or context-based; like
identity-based methods in cloud-side, it uses user
identity information to authenticate the user, but here
is the mobile device that processes and analyzes
user attributes to check user authentication instead
of cloud servers. User sensitive information as bio-
metrics are stored locally in the mobile device during
authentication procedure, which increase the privacy
and security issues; applications can be found in (Oh
et al., 2011) and (Schwab and Yang, 2013).
Context-based user-side methods are similar to the
corresponding cloud-side methods; the only differ-
ence lies in that the mobile device processes and eval-
uates user information instead of cloud server. Gener-
ally, a context-based authentication mechanism needs
more computation resource compared to the identity-
based methods, thus introducing performance issue
due to resource limitations of mobile devices. There-
fore, context-based user-side authentication methods
are less appropriate in MCC compared to cloud-based
methods. In addition, various types of user sensitive
information are stored in mobile devices, increasing
users privacy risk due to device loss compared to the
more reliable cloud environment.
4 AUTHENTICATION IN
STMicroelectronics
The case study of STMicroelectronics authentication
mechanism, presented in this section, complaints with
constraints and specifications of such a complex cor-
porate context. In our proposal we use a CMS-
style web application using the PHP framework Lar-
avel(Taylor, 2017)(Bean, 2015) for what concerns the
application and OAuth 2 for the authentication and
authorization process. A relevant factor to be consid-
ered was that this mechanism must work with both
Authentication and Authorization Issues in Mobile Cloud Computing: A Case Study
253

mobile devices as well as PCs desktop, and more-
over, it must also work from an Intranet network
through a corporate firewall. Using a web applica-
tion is therefore a suitable choice, because it can be
used via mobile and non-mobile devices, and it also
relies on standard HTTP/HTTPS protocols commu-
nicability through corporate intranet firewalls. Since
the security of the entire application was a key as-
pect of the specification, a SSL/TLS public certifi-
cate was adopted to support HTTPS using Let’s En-
crypt(Internet Security Research Group, 2017) a free,
automated, and open certificate authority endorsed
by the non-profit Internet Security Research Group
(ISRG).
As shown in Fig. 2, the client may be any device
(also mobile) with browsing capabilities. Clients’ re-
quests are forwarded through a dynamic DNS ser-
vice provided by No-IP(Vitalwerks Internet Solu-
tions, 2017) to the Web Server, hosted by Amazon
EC2 instance(Amazon Web Services, 2017). Deploy-
ment of the application on the server is realized using
SFTP protocol.
As cited previously, the application develop-
ment frameworks adopted is Laravel, free, open-
source and PHP based framework that complies with
model–view–controller (MVC) architectural pattern
as frequently occurs.
In addition, Laravel also provides a simple, con-
venient way to authenticate with OAuth providers us-
ing Laravel Socialite(Taylor, 2019) using Facebook,
Twitter, Google, LinkedIn, GitHub and Bitbucket. In
particular, every request that an application sends to
the Google+ API needs to identify the application to
Google. Either an API key, or an OAuth 2.0 client ID
can be used. A client ID should be used when calls
are made on behalf of a given user. Google supports
incremental authorization, which enables applications
to request initial permissions at sign-in and later ad-
ditional permissions can be granted, typically just be-
fore they are needed. This feature can improve the
sign-in conversion rate if initial scopes are configured
to be only the minimum that application requires to
get the user started.
Twitter API Authentication Model instead sup-
plies either user or app-only authentication. In the
former, a user access token grants permission to app’s
API calls, whereas in the latter API requests are is-
sued without user context information.
Laravel HTTP requests handling aims to provide
authentication and it is carried out with a routing
mechanism that operates in two phases, one to redi-
rect the user to the OAuth provider, and another to
receive the callback from the provider after authenti-
cation.
To access Socialite, the Socialite facade is used,
together with Auth facade to access various Auth
methods as shown in the listing 2:
namespace App\ Ht t p \ C o n t r o l l e r s ;
us e App\ R o l e ;
us e App\ U s e r ;
us e I l l u m i n a t e \ Ro u t i ng \ C o n t r o l l e r ;
us e I l l u m i n a t e \ S u p p o r t \ Fa c a d es \ Auth ;
us e L a r a v e l \ S o c i a l i t e \ F a c a d e s \ S o c i a l i t e ;
c l a s s A u t h C o n t r o l l e r e x t e n d s C o n t r o l l e r
{
/
* *
*
@param $ p r o v i d e r
*
@re t u r n Res p o ns e
*
/
p u b l i c f u n c t i o n r e d i r e c t T o P r o v i d e r ( $ p r o v i d e r )
{
r e t u r n S o c i a l i t e : : d r i v e r ( $ p r o v i d e r )−> r e d i r e c t ( ) ;
}
/
* *
*
@param $ p r o v i d e r
*
@re t u r n Res p o ns e
*
/
p u b l i c f u n c t i o n h a n d l e P r o v i d e r C a l l b a c k ( $ p r o v i d e r )
{
t r y {
$ u s e r C o n t e x t = S o c i a l i t e : : d r i v e r ( $ p r o v i d e r )
−>u s e r ( ) ;
$ a u t h U s e r = $ t h i s −>f i n d O r C r e a t e U s e r (
$ u s e r C o n t e x t ) ;
Auth : : l o g i n ( $ a u t hU s er , t r u e ) ;
r e t u r n r e d i r e c t ( ’ home ’ ) ;
}
c a t c h ( \ E x c e p t i o n $e ) {
r e t u r n b a c k ( ) ;
}
}
p r i v a t e f u n c t i o n f i n d O r C r e a t e U s e r ( $ u s e r C o n t e x t )
{
i f ( $ a u t h U s e r = User : : w here ( ’ e m a i l ’ ,
$ u s e r C o n t e x t −>em a i l )−> f i r s t ( ) ) {
r e t u r n $ a u t h U s e r ;
}
e l s e {
$new User = new Us e r ;
$newUser−>em a i l = $ u s e r C o n t e x t −>em a i l ;
$newUser−>name = $ u s e r C o n t e x t −>name ;
$newUser−>pa s sw o r d = b c r y p t ( s e l f : :
g e n e r a t e p a s s w o r d ( ) ) ;
$newUser−>sa v e ( ) ;
$ d e f a u l t R o l e = R o l e : : wher e ( ’ name ’ , ’ g u e s t ’ )
−> f i r s t ( ) ;
$newUser−>ad d R o le ( $ d e f a u l t R o l e ) ;
r e t u r n $new User ;
}
th r o w new \ E x c e p t i o n ( ) ;
}
}
Listing 1: AuthController.php.
The redirectToProvider sends user
info to the OAuth provider, while the
handleProviderCallback method will read
the incoming request and retrieves the user’s informa-
tion from the provider; finally, findOrCreateUser
method looks up the user object in the database
returning it if present, or creating a new user
otherwise.
OAuth2 server is a service provider allowing ac-
cess to API endpoints for the authorized user or au-
thorized applications. This is obatianed by integrat-
ing OAuth2orize, an authorization server toolkit for
CLOSER 2019 - 9th International Conference on Cloud Computing and Services Science
254
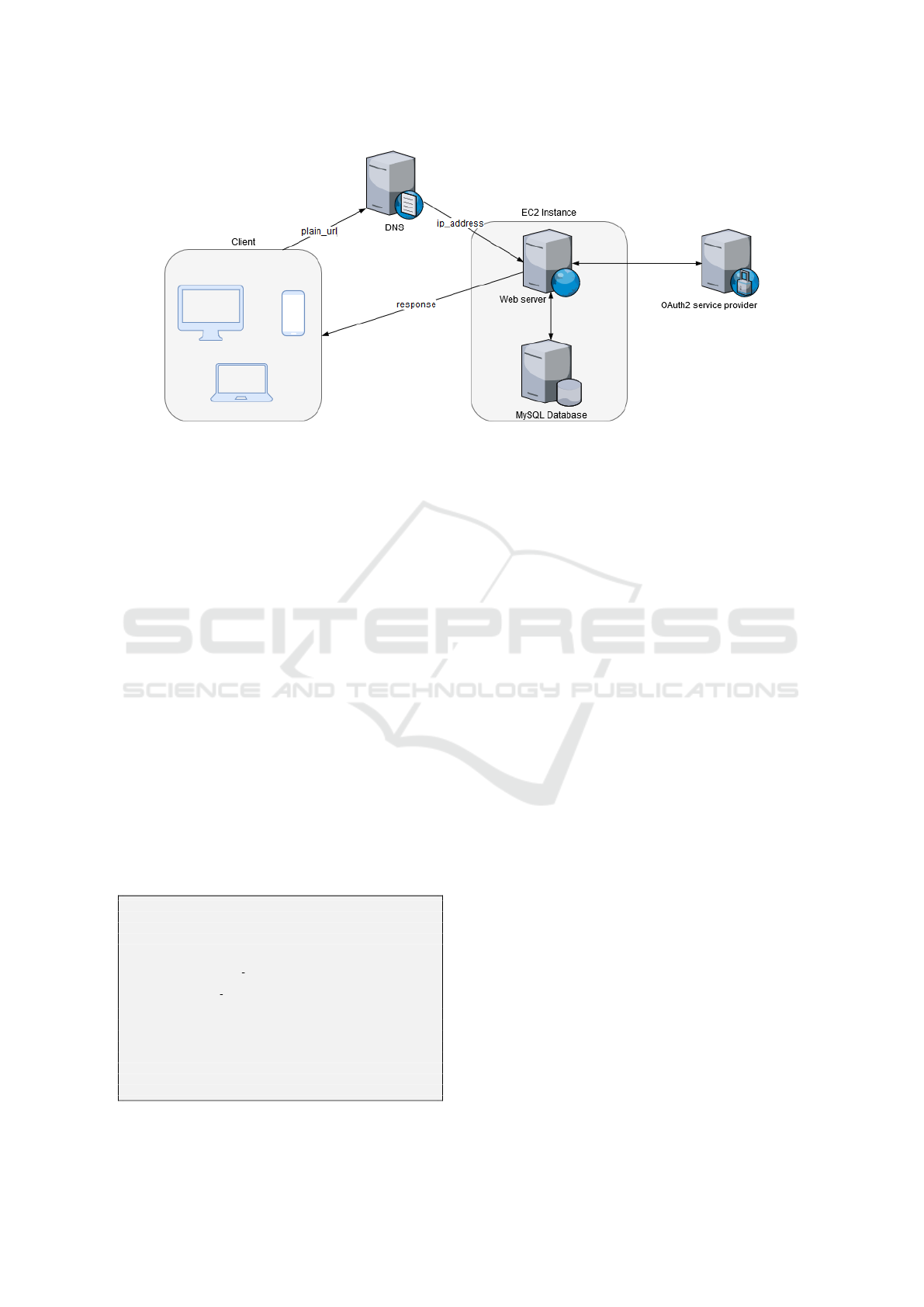
Figure 2: Application’s architecture.
Node.js, into the application. It provides a suite of
middleware that, combined with Passport authentica-
tion strategies and application-specific route handlers,
can be used to settle up a server that implements the
OAuth 2.0 protocol.
OAuth 2.0 defines an authorization framework, al-
lowing an extensible set of authorization grants to
be exchanged for access tokens. Implementations
can choose what grant types to support, by using
the bundled middleware (to support common types)
or plugins (to support extension types). It provides
a large number of modules for interoperability with
various services. One of these in particular, Mon-
goose(mongoose, 2017), was used to connect with the
non-relational database MongoDB(MongoDB, Inc,
2019). Using a non-relational database, such as Mon-
goDB gives several benefits as high performance,
low latency, simplicity, scalability and rapid object-
relational mapping.
OAuth2orize requires session state for the express
application in order to properly complete the autho-
rization transaction. In order to do this, the express-
session package was needed to use it in the express
application.
/ / R e g i s t e r a u t h o r i z a t i o n co d e g r a n t t y p e
s e r v e r . g r a n t ( o a u t h 2 o r i z e . g r a n t . c o d e ( f u n c t i o n ( c l i e n t ,
r e d i r e c t U r i , u s e r , a r e s , c a l l b a c k ) {
/ / C r e a t e a new a u t h o r i z a t i o n c o d e
v a r co d e = new Code ({
v a l u e : u i d ( 1 6 ) ,
c l i e n t I d : c l i e n t . i d ,
r e d i r e c t U r i : r e d i r e c t U r i ,
u s e r I d : u s e r . i d
}) ;
/ / S a v e t h e a u t h c o d e and c h e c k f o r e r r o r s
code . s a v e ( f u n c t i o n ( e r r ) {
i f ( e r r ) { r e t u r n c a l l b a c k ( e r r ) ; }
c a l l b a c k ( n u l l , c o de . v a l u e ) ;
}) ;
}) ) ;
Listing 2: controllers/oauth2.js.
When a client redirects a user to user authoriza-
tion endpoint, an authorization transaction is initiated.
To complete the transaction, the user must authenti-
cate and approve the authorization request. Because
this may involve multiple HTTP request/response ex-
changes, the transaction is stored in the session and
a new authorization code model for the user and ap-
plication client it is stored in MongoDB so it can be
accessed to exchanging for an access token.
5 CONCLUSIONS
In this paper, the MCC authentication and authoriza-
tion issues were discussed, from Cloud computing
questions to specific MCC scenario. We then pre-
sented the solution developed and applied within the
STMicroelectronics IC manufacturer plants. Further
works include measurements and performance assess-
ment of the proposed solution, and also its improve-
ment by introducing stronger mechanisms as trust-
worthiness (Buzzanca et al., 2017), (Gai et al., 2016).
Another interesting challenge is related to the ex-
ploitation of techniques derived from complex net-
works and communities (Song et al., 2018), useful
for the study of reliability and robustness of the pro-
posed MCC solution (Carchiolo et al., 2015) (Carchi-
olo et al., 2018).
ACKNOWLEDGEMENTS
This work has been supported by the Universit
´
a degli
Studi di Catania, ”Piano della Ricerca 2016/2018
Linea di intervento 2”.
Authentication and Authorization Issues in Mobile Cloud Computing: A Case Study
255

REFERENCES
Alizadeh, M., Abolfazli, S., Zamani, M., Baaaharun, S., and
Sakurai, K. (2016). Authentication in mobile cloud
computing: A survey. Journal of Network and Com-
puter Applications, 61:59–80.
Amazon Web Services (2017). Amazon elastic compute
cloud - ec2. //https//aws.amazon.com/it/ec2/. Last acc.
14 June 2017.
Bean, M. (2015). Laravel 5 Essentials. Packt Publishing.
Braz, C. and Robert, J.-M. (2006). Security and usability:
The case of the user authentication methods. In Proc.
of IHM 06, pages 199–203, New York, NY, USA.
ACM.
Buzzanca, M., Carchiolo, V., Longheu, A., Malgeri, M., and
Mangioni, G. (2017). Direct trust assignment using
social reputation and aging. Journal of Ambient Intel-
ligence and Humanized Computing, 8(2):167–175.
Carchiolo, V., Grassia, M., Longheu, A., Malgeri, M., and
Mangioni, G. (2018). Exploiting long distance con-
nections to strengthen network robustness. In IDCS.
Carchiolo, V., Longheu, A., Malgeri, M., Iannello, S., Mar-
roccia, M., and Randazzo, A. (2019). Cloud in mobile
platforms: managing authentication/authorization. In
Advances in Intelligent Systems and Computing. In
Press.
Carchiolo, V., Longheu, A., Malgeri, M., and Mangioni,
G. (2015). The cost of trust in the dynamics of best
attachment. Computing and Informatics, 34:167–184.
Gai, K., Qiu, M., and Elnagdy, S. A. (2016). A novel secure
big data cyber incident analytics framework for cloud-
based cybersecurity insurance. In 2016 IEEE 2nd Big-
DataSecurity, HPSC, and IDS, pages 171–176.
Internet Security Research Group (2017). Let’s Encrypt.
https://letsencrypt.org/. Last acc. 14 June 2017.
Jeong, Y.-S., Park, J. S., and Park, J. H. (2015). An efficient
authentication system of smart device using multi fac-
tors in mobile cloud service architecture. Intl Journal
of Communication Systems, 28(4):659–674.
Mohsin, J. K., Han, L., Hammoudeh, M., and Hegarty, R.
(2017). Two factor vs multi-factor, an authentication
battle in mobile cloud computing environments. In
Proceedings of ICFNDS ’17, pages 39:1–39:10, New
York, NY, USA. ACM.
MongoDB, Inc (2019). MongoDB Atlas. https://www.
mongodb.com. Last acc. 12 Febraury 2019.
mongoose (2017). mongoose ODM. http://mongoosejs.
com/. Last acc. 15 September 2017.
Oh, D.-S., Kim, B.-H., and Lee, J.-K. (2011). A Study
on Authentication System Using QR Code for Mo-
bile Cloud Computing Environment, pages 500–507.
Springer Berlin Heidelberg, Berlin, Heidelberg.
OpenID Foundation (2019). OpenID. http://openid.net/.
Last acc. 19 Feb. 2019.
Parecki, A. (2019). OAuth. https://oauth.net. Last acc. 19
Feb. 2019.
Peter Mell, T. G. (2009). The NIST Definition of Cloud
Computing. https://www.nist.gov/sites/default/files/
documents/itl/cloud/cloud-def-v15.pdf. Last acc. 13
June 2017.
Recordon, D. and Reed, D. (2006). Openid 2.0: A platform
for user-centric identity management. In Proc. of DIM
’06, pages 11–16, New York, NY, USA. ACM.
salesforce (2019). SalesForce. https://www.salesforce.com.
Last acc. 5 Feb. 2019.
Sanaei, Z., Abolfazli, S., Gani, A., and Buyya, R. (2014).
Heterogeneity in mobile cloud computing: Taxonomy
and open challenges. IEEE Communications Surveys
Tutorials, 16(1):369–392.
Schwab, D. and Yang, L. (2013). Entity authentication in
a mobile-cloud environment. In Proc. of CSIIRW ’13,
pages 42:1–42:4, New York, NY, USA. ACM.
Song, Z., Sun, Y., Yan, H., Wu, D., Niu, P., and Wu, X.
(2018). Robustness of smart manufacturing informa-
tion systems under conditions of resource failure: A
complex network perspective. IEEE Access, 6:3731–
3738.
Taylor, O. (2017). Laravel - The PHP Framework for Web
Artisans. https://laravel.com/. Last acc. 30 Aug. 2017.
Taylor, O. (2019). Laravel Socialite. https://laravel.com/
docs/5.7/socialite. Last acc. 18 Febraury 2019.
Todorov, D. (2007). Mechanics of User Identification and
Authentication: Fundamentals of Identity Manage-
ment. CRC Press.
Vitalwerks Internet Solutions, L. (2017). No-IP. https://
www.noip.com/. Last acc. 15 Sept. 2017.
CLOSER 2019 - 9th International Conference on Cloud Computing and Services Science
256
