
A Customized Educational Booster for Online Students in Cybersecurity
Education
Mohamed Rahouti
1,4 a
and Kaiqi Xiong
2,3,4 b
1
Department of Electrical Engineering, University of South Florida, Tampa, FL, 33620, U.S.A.
2
Cyber Florida, University of South Florida, Tampa, FL, 33620, U.S.A.
3
Department of Mathematics and Statistics, University of South Florida, Tampa, FL, 33620, U.S.A.
4
Intelligent Computer Networking and Security Lab, University of South Florida, Tampa, FL, 33620, U.S.A.
Keywords:
Cyber Security, Applied Cryptography, Computer Networking and Security, Virtual Environment, Online
Teaching.
Abstract:
Real-world lab experiments have been an integral part of computer science and engineering curriculums.
However, human and computing resources as well as financial support to courses may be limited at many
universities ranging from small to large universities and from liberal arts colleges to top research universities
as there is a dramatic increase of student enrollments in computer science and engineering for the past ten
years. Nowadays, like many other universities nation wide, University of South Florida (USF) in collabo-
ration with the Cyber Florida center offers online cyber security degrees as well as certificates. Throughout
such programs, online students are expected to acquire knowledge via an interdisciplinary set of core courses
prior to taking a deep dive into one of four following concentrations: cyber intelligence, digital forensics,
information assurance and computer security fundamentals. However, when it comes to training student with
real-world cyber security labs, both instructors and students face various challenges with regard to resources
and virtual environment for exploring and running a broad range of security experiments and tests. In order
to achieve the goal of our funded NSF project, in this paper we will discuss our teaching contributions to the
development of a broad range of cyber security labs, facilitation of applied cryptography learning through
experimental modules, and our customized virtual machine that fits the needs of various online computer
networking and security courses. Specifically, we will first present our methodology for the design of our
experimental modules and then present in details our pre-built Linux-based portable virtual machine. Those
learning and experimental modules have been developed at different levels to meet the need of students with
different academic and industrial backgrounds.
1 INTRODUCTION
In recent years, technological advances have lead
to revolutionary improvement and facilitation of e-
learning through smart educational systems. There-
fore, it becomes very important to befit a broad range
of subjects and teaching materials into curriculums
that fulfil the industrial and technological require-
ments and goals (Bauer et al., 2018).
Moreover, because of the dramatic increase of all
technologies and practices of computer systems and
electronic data, living in a world where more and
more of our social lives and business are online, cyber
security is an enormously growing area.
a
https://orcid.org/0000-0001-9701-5505
b
https://orcid.org/1111-2222-3333-4444
In the past, people widely considered cyber se-
curity as an IT department’s responsibility. It
was naively thought that as long as proper security
tools and software (e.g., firewall, antivirus, encryp-
tion/decryption protocols, etc.) were put in place,
people could just neglect concerns security problems
and left them for IT departments to deal with.
These days, the international research and advi-
sory firm, GartnerInc., estimates spending on secu-
rity worldwide to pass 96.3 billion dollars by the end
of 2018, which is about 8% increase within one year.
In addition, for the last several years, the need for
shielding and protecting information from illegitimate
usage/access and malicious actors has evolved at the
highest levels of institutions, business and govern-
ment.
Rahouti, M. and Xiong, K.
A Customized Educational Booster for Online Students in Cybersecurity Education.
DOI: 10.5220/0007767205350541
In Proceedings of the 11th International Conference on Computer Supported Education (CSEDU 2019), pages 535-541
ISBN: 978-989-758-367-4
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
535

Moreover, with an increasing cybercrimes that af-
fect the government, individuals, and organizations,
online cyber security certificates or degrees help re-
mote students (could even be overseas in military du-
ties sometimes) to pursue new opportunities that per-
mit them to contribute in maintaining information and
data secure from illegitimate usage. In the online
teaching, the curricula must align with the material
on cyber security certification exams such as Certified
Information Systems Security Professional (CISSP),
Security +, and Information Systems Audit and Con-
trol Association (ISACA) exams. Therefore, the cur-
ricula should be designed in a suitable way to befit
hands-on skills and requirements of cyber security
industry, whereas the university must guarantee the
availability of all necessary tools and resources for
students to practice and apply teaching material rel-
evant to the workplace.
However, there exist various difficulties and key
challenges with regard to the teaching of cyber se-
curity in the educational structure of online courses.
These difficulties range from, but are not limited to,
the broad range of student backgrounds and availabil-
ity of computing resources (e.g., computers, network
devices, software). Based on our past teaching expe-
rience of the Applied Cryptography, a core course in
the curriculum of the online cyber security program at
the University of South Florida, students enroll in the
program with weak computer science and mathemat-
ics background, for example, without the completion
of some basic computer science courses, such as oper-
ating system basics, computer networking fundamen-
tals, computer programming skills, etc. According to
a recent survey we conducted in our course, more than
70% of total students do not have any computer sci-
ence and security background, where many students
come from a completely unrelated educational back-
ground, e.g., sociology, business, music studies.
Moreover, the insufficiency and or even lack of
hardware resources at universities (i.e. computer labs)
is another grand challenge that limits students capa-
bility to practice advanced cyber security labs. Stu-
dents are not in local, so it is very inconvenient or
even infeasible for students to come to the univer-
sity campus to work on their assigned labs. These
remote students could be overseas in military duties
or work displacement, which renders it impossible
for them to utilize physical labs at the Such key chal-
lenges place obstacles for implementations of suitable
infrastructure of such smart teaching. Furthermore,
difficulties of guaranteeing virtual resources, such as
remote virtual access to computers in physical com-
puter labs might even aggravate when labs require
multiple machines for running fundamental security
experiments (e.g., Client-sever communication, intru-
sion detection systems, Denial of Service and Dis-
tributed Denial of Service attacks, and Man-in-the-
Middle attack), or even powerful computation and
networking resources (e.g., hardware memory and In-
ternet speed).
In our past teaching for different cyber security
courses and workshops, we have developed a broad
range of hands-on labs. Our readily-available experi-
mental labs are conducted in our own pre-built virtual
machine image as we have installed and customized
all the necessary libraries, tools, and software that are
needed to accomplish such a diverse range of secu-
rity and cryptography labs. Students only need to be
handed our virtual machine and run it on their own
computers using a cross-platform virtualization ap-
plication (e.g., VirtualBox and VMware) that will let
them run our virtual operating system on their com-
puters.
The rest of this paper is organized as follows. Sec-
tion 2 presents an explanatory and detailed overview
of some efforts that were done in the past to enhance
and facilitate online cyber security learning experi-
ence. Section 3 then presents our research efforts to-
wards the development of a broad range of cyber se-
curity labs and experimental modules, as well as our
developed virtual environment for online computer
networking and security courses in general and on-
line Applied Cryptography in particular in order to
achieve the goal of our funded NSF project. In Sec-
tion 4 we present a taxonomic overview of students
experience assessment. Finally, in Section 5 we dis-
cuss our future work. We then conclude our research
study in Section 6.
2 RELATED WORK
In the past, many online educators have investi-
gated the advantages and disadvantages of online
courses (Kinnunen and Eriksson, 2018). The pros and
cons strictly rely on all parties of the online instruc-
tional process, instructors, students, and the univer-
sity.
In brief, Fedynich (Fedynich, 2013), Cook (Cook,
2007), and Baleni (Baleni, 2015) provided a taxo-
nomic overview of the advantages as: (1) flexibil-
ity of where and when to study, (2) feasibility of a
broad range of teaching mechanisms, and (3) effi-
ciency in term of cost for universities. Importantly,
Cook (Cook, 2007) highlighted more critical pros of
the online teaching, such as (1) the freedom for study
pace adjustment, (2) possibility of adopting particular
teaching techniques that are impractical in traditional
CSEDU 2019 - 11th International Conference on Computer Supported Education
536
(face-to-face) teaching, such as virtual platforms and
virtual simulations (particular types of virtual labo-
ratory as presented in Figure 1), and (3) easiness of
delivering prompt and synchronous feedback and for-
mative performance assessments.
On the other hand, there are numerous cons and
challenges of online teaching. In summary, typical
online courses (1) impose students to have computers
and online access, as well as (2) might have a weak
instructional design and (3) scarcity of face-to-face
interactions that could lead to the poor performance
of students (Fedynich, 2013), (Cook, 2007).
Additionally, teaching an online cyber security
course is even more challenging. More challenges
might add-up to the aforementioned list. Such
courses require advanced resources, e.g., computa-
tionally powerful computers, cryptographic libraries
and software, and multiple physical hosts or virtual
machines for particular security experimentation sce-
narios. Therefore, it becomes more and more chal-
lenging to help students reach their full potential in
such online cyber security core courses.
Concentrating on our online Applied Cryptog-
raphy for higher education (HE) involves topics
on secure software development, digital signatures,
symmetric-key/asymmetric-key encryptions, and eth-
ical hacking. Such topics must be accompanied with
hands-on lab modules and exercises to better help stu-
dents with understanding and practicing the course
concepts and material (Topham et al., 2016). It has
been used in education as well Xiong et al
Willems and Meinel (Willems and Meinel, 2012)
presented a software-based solution to evaluate prac-
tical cyber security labs and experiments in an on-
line laboratory-based on a virtual machine technol-
ogy. Herein, the authors guaranteed a formal pa-
rameterization of lab scenarios and implementation
of a dynamic toolkit for re-configuring virtual ma-
chines and therefore adopted the training environment
with according to the defined parameters. Xiong and
Pan (Xiong and Pan, 2013) presented an education
approach to deploy ProtoGENI, one of GENI testbed
resources, for teaching computer networking. Partic-
ularly, they have designed various capstone projects
and lab modules that provide students with an op-
portunity to utilize a real-world testbed for different
learning and research purposes.
While Sharma and Sefchek (Sharma and Se-
fchek, 2007) surveyed different types of laboratories
for cyber security teaching and learning, Mirkovic
and Benzel (Mirkovic and Benzel, 2012) introduced
DeterL ab, an open Emulab-based technology experi-
mental facility sponsored by the US National Science
Foundation and Department of Homeland Security.
This lab is hosted by USC/ISI and UC Berkeley. This
experimental facility is dedicated for online cyber se-
curity teaching, where students can reserve available
nodes (out of 400 computing nodes in total) through a
web-based interface. However, the students are only
permitted to posses the virtual sessions to these com-
puting nodes for a very short period of time in order
to grant as many users as possible access to the lab
resources.
Figure 1: Virtual laboratory hierarchy.
Differently from previous teaching efforts that lack
convenience and easiness for online cyber security
teaching. In this paper, we discuss and detail our
efficient academic guidelines in offering a readily-
available virtual environment for online cyber secu-
rity teaching along with a broad range of cryptog-
raphy and cyber security-based labs, as well as our
learning and experimental modules. In our devel-
opment and implementation processes, we consider
students with various academic backgrounds where
many of these students might lack basic computer sci-
ence fundamentals and cyber security knowledge.
3 METHODOLOGY: ADOPTING
INNOVATIONS
The objectives of the education research discussed
here are to enhance the efficiency of teaching on-
line cyber security courses (even our own experience
was induced from our online Applied Cryptography
course at the University of South Florida). In par-
ticular, this study aims at developing convenient vir-
tual laboratory experiments that meet the needs of cy-
ber security students with different academic back-
grounds. Moreover, in our education research we in-
vestigate how our students interact with our teaching
A Customized Educational Booster for Online Students in Cybersecurity Education
537

Figure 2: Our customized pre-built open-source Linux-
based virtual machine.
methods and ready-to-use virtual environment for cy-
ber security lab experiments.
3.1 Lab Development
In the past few years, we have been offering Ap-
plied Cryptography, a core course for the fully on-
line cyber security program at the University of South
Florida. This course aims at familiarizing remote stu-
dents with common cryptographic building blocks,
including state-of-the art techniques to encrypt data,
digital signature schemes, and protocols for estab-
lishing secret keys across public networks. Students
are expected to understand the strengths and limita-
tions of common and widely used cryptographic se-
curity models, and how side-channel leakage in an
unprotected implementation can subvert a theoreti-
cally strong algorithm. At the end of this course,
students should know how cryptographic mechanisms
secure data in today’s computers and networks, and
how ”best practices” are applied to protect informa-
tion.
Therefore, in order to fulfil such curriculum ob-
jectives, we have been dedicating great efforts to de-
velop lab experiments that meet today’s cyber secu-
rity advances and needs. Given that in this program,
students usually have a very broad range of academic
backgrounds and many of them might even lack the
fundamentals of computer systems and cyber security,
and therefore, it is of a great challenge to provide labs
that align with the majority of student backgrounds.
Furthermore, universities are proven cumbersome
to respond to cyber security education needs. It is
widely common that computer science students have
to go through at least four years of the undergradu-
ate schooling without taking any mandatory course
on security (Cheung et al., 2011). Thus, such stu-
dents graduate without acquiring any knowledge of
cyber security. In addition, admission requirements
for graduate cyber security programs enrolment at
universities are not strictly imposed, and therefore
students with a weak background in computer sci-
ence are allowed in online graduate cyber security
programs.
To consider such weaknesses in student back-
grounds and to overcome the previously discussed
key challenges, inspired by existing advanced cyber
security labs such as SEEDLab projects (Du, 2011),
we develop our own labs with detailed step-by-step
instructions. These labs are shown in Table 1 and
mainly focus on applied cryptography, which cov-
ers three essential mechanisms in cryptography, in-
cluding secrete-key encryption, one-way hash func-
tion, public-key encryption and Public Key Infrastruc-
ture (PKI). Besides, we also cover vulnerabilities of
common cryptographic algorithms. Prior to assign-
ing these labs to students, we require them to finish
an introductory lab. This lab is about downloading
our virtual machine (it will be described in Subsec-
tion 3.2) and importing it into their own computers
after installing an open-source virtualization platform
(e.g., VMware and VirtualBox).
Moreover, we develop detailed Instructor Manu-
als. For the majority of our developed labs, we create
corresponding manuals, which are only for instructors
use. These manuals basically come from reports of
graduate teaching assistants and graduate research as-
sociates. These detailed reports describe how tasks of
each lab modules can be accomplished. These man-
uals are for the sake of assisting educators with the
preparation for their labs.
Figure 3: Our customized pre-built open-source Linux-
based virtual machine is equipped and pre-configured in a
convenient way to help students with a weak background to
get started on course labs. It also comes with all necessary
implementations of libraries and tools.
3.2 Virtual Environment
Implementation
In order to address the key challenges discussed in
Section 1, we have built a Linux-based virtual ma-
chine environment for students use in their lab exper-
iments by using Ubuntu with a variety of latest ver-
CSEDU 2019 - 11th International Conference on Computer Supported Education
538
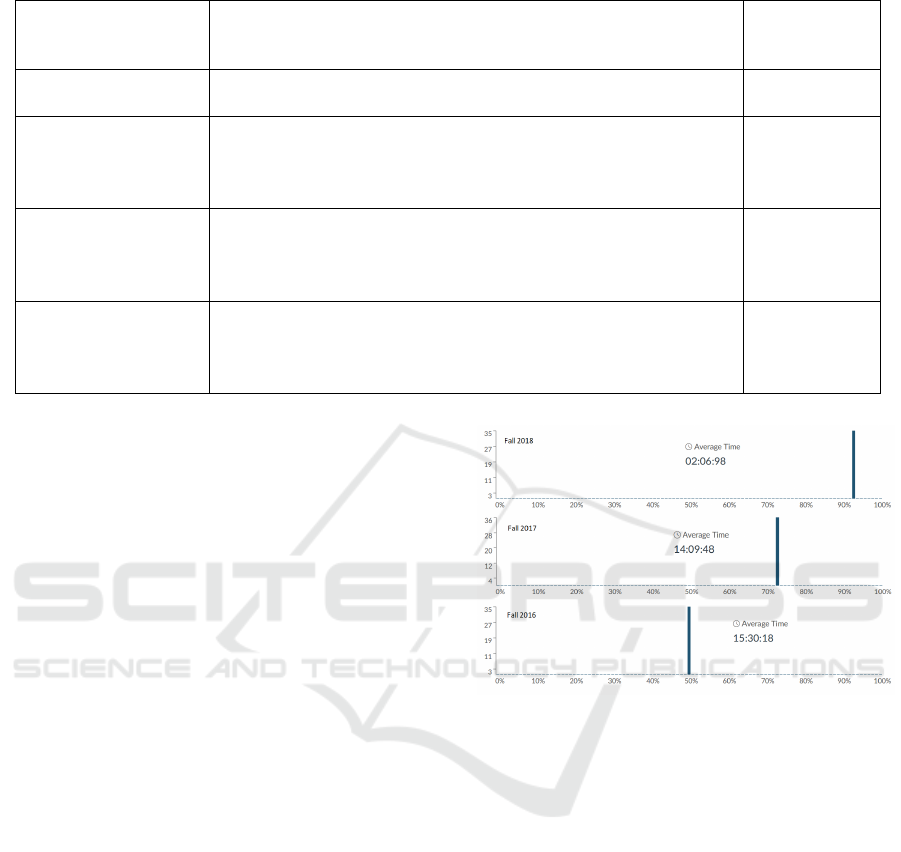
Table 1: A sample of our developed labs for Applied Cryptography course at the University of South Florida.
Lab Objectives Duration
(Hrs)
Getting started Virtual environment set up 5
Secret Key cryptog-
raphy
(1) Getting familiar with symmetric-key encryption (2)writing
programs to encrypt and decrypt different messages (3) Encryp-
tion modes (4) Encryption padding (5) Initial vectors (IV)
15
Hash functions and
MAC
Getting familiar with (1) hash functions and Message Authenti-
cation Code (MAC) (2) exploring strengths and weaknesses of
common hash functions properties
8
Digital certificates
and CA creation
Getting familiar with (1) digital certificates (2) create own cer-
tificate authority (CA) (3) signing and validation of digital cer-
tificates
8
sions for different semesters. For your information,
the virtual environments depicted in Figures 2 and 3
are screen-shots taken before and after students log
into the virtual machine, respectively. Based on dif-
ferent levels of students, we have provided the vir-
tual machines with different levels of configurations.
That is, students with better backgrounds receive less
configured virtual machines. Generally speaking, the
virtual machine environments are customized and ad-
justed to fit our online teaching goals. They are pre-
configured in a convenient way to fit students with
different background needs and shortages in hands-on
and computer science skills. Particularly, we imple-
ment all necessary libraries, packages, and software
that students need to work on our applied cyber secu-
rity labs. Moreover, our virtual machine is delivered
to students via the university course web page. All
what students need to do is downloading the virtual
machine and importing it into their own computers
without the need of changing any settings or param-
eterization. Such a ready-to-use virtual machine pro-
vides a portable environment for our remote students
such that they do not need to struggle with affording
computationally powerful computers and cyber secu-
rity software. Furthermore, this virtual environment
is equipped with all necessary material for labs ac-
complishment starting from labs manuals to directory
hierarchy for each corresponding lab and experimen-
tation modules.
Figure 4: Students performance before and after the devel-
opment of our own virtual environment and new lab mod-
ules (i.e., before and after Fall 2018, respectively).
4 EVALUATION
Figures 4 and 5 depict students assessment in our on-
line Applied Cryptography course for three semesters
in the last three years in a row, starting from Fall 2016
through Fall 2018. Stating that before 2018, we have
used existing SEEdLab (Du, 2011) machine along
with existing laboratories developed by the SEEDLab
project. Figure 4 shows that our students performance
has been enhanced since we offer them a convenient
and efficient virtual environment along with newly
developed labs that meet the necessities and consid-
erations of weaknesses in student backgrounds. The
overall grades were significantly improved whereas
the time spent on labs dramatically decreased.
Moreover, Figure 5 shows students assessment
of difficulty level of our labs for the same three
semesters between 2016 and 2018. The figure demon-
A Customized Educational Booster for Online Students in Cybersecurity Education
539
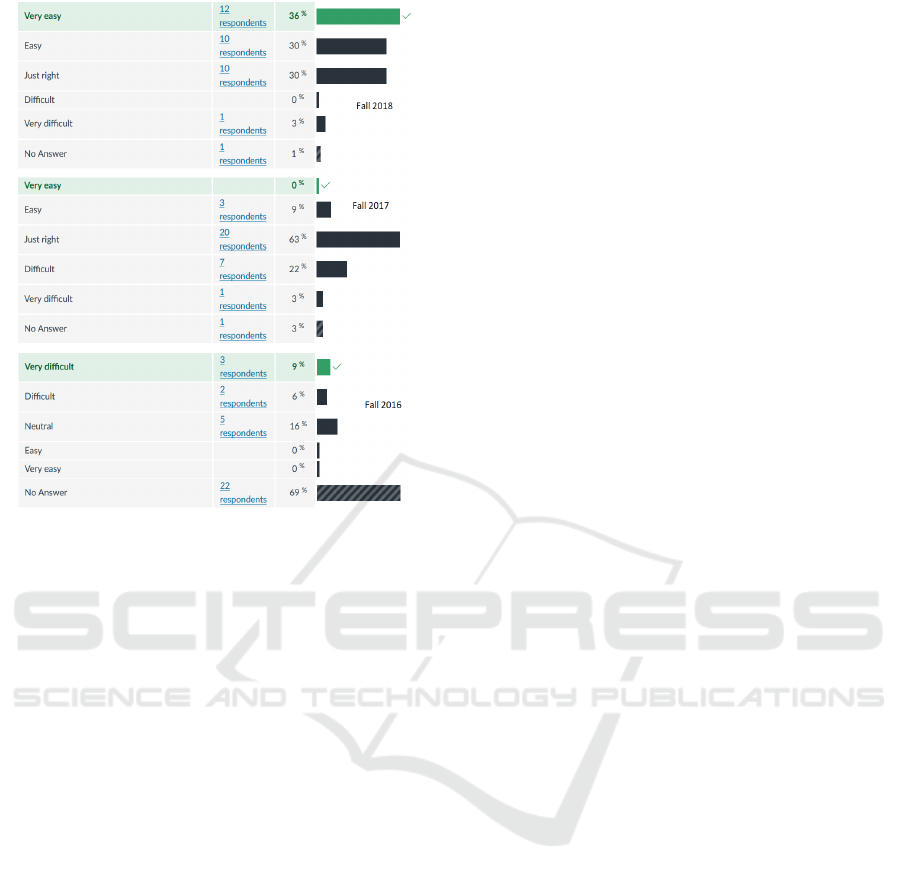
Figure 5: The feedback of our students in Applied Cryp-
tography course regarding the difficulty level of labs before
and after developing/implementing our new lab modules.
strates the satisfaction of our online cyber security
students with our newly developed lab modules. It
is obviously demonstrated that based on our student
assessments the difficulty level of these cyber se-
curity labs has been significantly reduced. Noting
that throughout these successive semesters, our labs
cover the same tasks and experimentation scenarios.
The reason our newly introduced labs are less dif-
ficult than previously used ones from the SEEDLab
project (Du, 2011) is that our virtual machine pro-
vides students with necessary demos, training exer-
cises, tutorials, and step-by-step manuals to under-
stand labs content, goals, and findings. These inte-
grated demos and manuals in our virtual machine are
intended to help students who need additional tuto-
rials and guidance to catch up on basic fundamen-
tals, such as Linux operating system, shell scripting,
OpenSSL library, etc.
5 DISCUSSIONS AND FUTURE
WORK
Hands-on lab experiments have been an integral part
of computer science and engineering curriculums.
However, human and computing resources as well as
financial support to courses may be limited at many
universities ranging from small to large universities
and from liberal arts colleges to top research univer-
sities as there is a dramatic increase of student en-
rollments in computer science and engineering for the
past ten years.
As future work for facilitating and improving
large-scale cyber security experimentation, we plan
to adopt the Global Environment for Network In-
novations (GENI), a real-world, repeatable, pro-
grammable, at-scale, virtual infrastructure for ex-
periments in a variety of computer science areas
such as networking, security, and distributed com-
puting sponsored by National Science Foundation
(NSF) (Berman et al., 2014), (Thomas et al., 2016),
(Riga et al., 2016), (Chin et al., 2018).
Furthermore, Software-Defined Networking
(SDN) has been a core technology in cloud comput-
ing and other cyber-physical systems where SDN
facilitates network management and enables network
programmability and efficient network configuration
to improve network performance, monitoring, and
security (Chin et al., 2017). In our future work, we
will dedicate great efforts in the development of
GENI and SDN learning and experimental modules
for computer networking and security courses in
order to achieve the goal of today’s advanced cyber
security needs. Specifically, we will introduce our
methodology for the design of our modules and
then provide the details of GENI and SDN modules
including GENI account setup and resource reserva-
tion, measurement tool labs, as well as SDN labs for
network traffic management and the detection and
mitigation of several well-known security attacks,
such as Denial of Service Attacks (DoS), Distributed
Denial of Service Attacks (DDoS), phishing attacks,
and Domain Generation Algorithm (DGA) malware
detection. Those learning and experimental modules
will be developed at different levels to meet the need
of students with different academic backgrounds.
6 CONCLUSIONS
In computer science and engineering curriculums,
hands-on lab experiments have been an integral part,
especially in cyber security paths. However, the key
challenges always relate to human and computing re-
sources as well as financial support to such online
courses. These resources could be limited at many
higher education institutions ranging from small to
large colleges as there is a dramatic increase of stu-
dent enrollments in online cyber security programs
ranging from degrees to certificates.
In collaboration with the Cyber Florida center,
CSEDU 2019 - 11th International Conference on Computer Supported Education
540

University of South Florida offers accredited online
cyber security programs. Throughout such online
programs, remote students have the opportunity to
gain knowledge through an interdisciplinary set of
core courses and then take a deep dive into the field
of cyber security.
Therefore, in order to fulfil the industrial needs
of cyber security and while considering the afore-
mentioned challenges, in this paper, we have pre-
sented our great efforts in facilitating the learning pro-
cess of the online cyber security learning. Specif-
ically, we have presented our methodology for the
design of our modules and then given the detail of
our pre-built Linux-based portable virtual environ-
ment. Those learning and experimental modules have
been developed at different levels to meet the need of
students with different academic and industrial back-
grounds. Moreover, we provided an evaluation of
our teaching experience as well as students perfor-
mance in Applied Cryptography, the online cyber se-
curity course we have been teaching for the last few
years. Finally, in our future work, we will bring the
Global Environment for Network Innovations (GENI)
testbed in classroom and integrate it with this teach-
ing design and even conduct advanced computer net-
working and security laboratories.
ACKNOWLEDGEMENTS
We would like to acknowledge the National Sci-
ence Foundation (NSF) who partially sponsored the
work under grants #1620868, #1620871, #1620862,
#1651280, and BBN/GPO project #1936 through
NSF/CNS grant. The views and conclusions con-
tained herein are those of the authors and should not
be interpreted as necessarily representing the official
policies, either expressed or implied of NSF.
REFERENCES
Baleni, Z. G. (2015). Online formative assessment in higher
education: Its pros and cons. Electronic Journal of e-
Learning, 13(4):228–236.
Bauer, M., Br
¨
auer, C., Schuldt, J., and Kr
¨
omker, H. (2018).
Adaptive e-learning technologies for sustained learn-
ing motivation in engineering science. In Proceed-
ings of the 10th International Conference on Com-
puter Supported Education, volume 1. CSEDU 2018.
Berman, M., Chase, J. S., Landweber, L., Nakao, A., Ott,
M., Raychaudhuri, D., Ricci, R., and Seskar, I. (2014).
Geni: A federated testbed for innovative network ex-
periments. Computer Networks, 61:5–23.
Cheung, R. S., Cohen, J. P., Lo, H. Z., and Elia, F. (2011).
Challenge based learning in cybersecurity education.
In Proceedings of the International Conference on Se-
curity and Management (SAM), page 1. The Steering
Committee of The World Congress in Computer Sci-
ence, Computer . . . .
Chin, T., Rahouti, M., and Xiong, K. (2018). Applying
software-defined networking to minimize the end-to-
end delay of network services. ACM SIGAPP Applied
Computing Review, 18(1):30–40.
Chin, T., Xiong, K., and Rahouti, M. (2017). Sdn-based ker-
nel modular countermeasure for intrusion detection.
In International Conference on Security and Privacy
in Communication Systems, pages 270–290. Springer.
Cook, D. A. (2007). Web-based learning: pros, cons and
controversies. Clinical Medicine, 7(1):37–42.
Du, W. (2011). Seed: hands-on lab exercises for com-
puter security education. IEEE Security & Privacy,
9(5):70–73.
Fedynich, L. V. (2013). Teaching beyond the classroom
walls: The pros and cons of cyber learning. Journal
of Instructional Pedagogies, 13.
Kinnunen, P. and Eriksson, T. (2018). Teachers’ viewpoint
on online courses. In Proceedings of the 10th Interna-
tional Conference on Computer Supported Education,
volume 1. CSEDU 2018.
Mirkovic, J. and Benzel, T. (2012). Teaching cybersecurity
with deterlab. IEEE Security & Privacy, 10(1):73–76.
Riga, N., Edwards, S., and Thomas, V. (2016). The Ex-
perimenter’s View of GENI, pages 349–379. Springer
International Publishing, Cham.
Sharma, S. K. and Sefchek, J. (2007). Teaching informa-
tion systems security courses: A hands-on approach.
Computers & Security, 26(4):290–299.
Thomas, V., Riga, N., Edwards, S., Fund, F., and Korakis,
T. (2016). Geni in the classroom. In The GENI Book,
pages 433–449. Springer.
Topham, L., Kifayat, K., Younis, Y. A., Shi, Q., and
Askwith, B. (2016). Cyber security teaching and
learning laboratories: A survey. Information & Se-
curity, 35(1):51.
Willems, C. and Meinel, C. (2012). Online assess-
ment for hands-on cyber security training in a vir-
tual lab. In Global Engineering Education Conference
(EDUCON), 2012 IEEE, pages 1–10. IEEE.
Xiong, K. and Pan, Y. (2013). Understanding protogeni
in networking courses for research and education.
In Research and Educational Experiment Workshop
(GREE), 2013 Second GENI, pages 119–123. IEEE.
A Customized Educational Booster for Online Students in Cybersecurity Education
541
