
Secure Strassen-Winograd Matrix Multiplication with MapReduce
Radu Ciucanu
1
, Matthieu Giraud
2
, Pascal Lafourcade
2
and Lihua Ye
3
1
INSA Centre Val de Loire, Univ. Orl
´
eans, LIFO EA 4022, Bourges, France
2
LIMOS, UMR 6158, Universit
´
e Clermont Auvergne, Aubi
`
ere, France
3
Harbin Institute of Technology, China
Keywords:
Matrix Multiplication, Strassen-Winograd Algorithm, MapReduce, Security.
Abstract:
Matrix multiplication is a mathematical brick for solving many real life problems. We consider the Strassen-
Winograd algorithm (SW), one of the most efficient matrix multiplication algorithm. Our first contribution is
to redesign SW algorithm MapReduce programming model that allows to process big data sets in parallel on
a cluster. Moreover, our main contribution is to address the inherent security and privacy concerns that occur
when outsourcing data to a public cloud. We propose a secure approach of SW with MapReduce called S2M3,
for Secure Strassen-Winograd Matrix Multiplication with Mapreduce. We prove the security of our protocol
in a standard security model and provide a proof-of-concept empirical evaluation suggesting its efficiency.
1 INTRODUCTION
Matrix multiplication is a mathematical tool of many
problems spanning over a plethora of domains e.g.,
statistics, medicine, or web ranking. Indeed, Markov
chains applications on genetics and sociology (Char-
trand, 1985), or applications such that computation
of shortest paths (Shoshan and Zwick, 1999; Zwick,
1998), convolutional neural network (Krizhevsky
et al., 2012) deal with sensitive data processed as
matrix multiplication. In such applications, the
size of the matrices to be multiplied is often very
large. Whereas a naive matrix multiplication algo-
rithm has cubic complexity, many research efforts
have been made to propose more efficient algorithms.
One of the most efficient algorithms is Strassen-
Winograd (Strassen, 1969) (denoted as SW in the se-
quel), the first sub-cubic time algorithm, with an ex-
ponent log
2
7 ≈ 2.81. The best algorithm known to
date (Le Gall, 2014) has an exponent ≈ 2.38. Al-
though many of the sub-cubic algorithms are not nec-
essarily suited for practical use as their hidden con-
stant in the big-O notation is huge, the SW algorithm
and its variants emerged as a class of matrix multipli-
cation algorithms in widespread use.
In this paper, we propose a distributed ver-
sion of SW that relies on the popular MapReduce
paradigm (Dean and Ghemawat, 2004) for outsourc-
ing data and computations to the cloud. Indeed, with
the development of the cloud, outsourcing data and
computations is nowadays a common fact. A plethora
of cloud service providers (e.g., Google Cloud Plat-
form, Amazon Web Services, Microsoft Azure) are
available. They allow companies to use large data
storage and computation resources on demand for
a reasonable price. Despite these benefits, cloud
providers do not usually address the fundamental
problem of protecting the privacy of users’ data. In
our case, we consider the problem of matrix multi-
plication, hence we aim at preserving the privacy of
input and output matrices. With a naive algorithm,
the cloud would learn all matrices, which may con-
tain sensitive information that the owner of the matri-
ces does not want to disclose.
Problem Statement. The data owner has two com-
patible matrices A and B. The final user is allowed
to query the product C = A × B, but is not allowed to
know the input matrices A and B.
First, the data owner is expected to encrypt the
input matrices A and B before outsourcing them to
the public cloud. The matrices are then spread over a
set of nodes of the public cloud to run the first phase
called the deconstruction phase. Then, these results
are used by the second phase called the combination
phase. Finally, the encryption of C = A × B is sent
to the user for decryption. We expect the following
properties:
1. the user cannot learn any information about input
matrices A and B,
220
Ciucanu, R., Giraud, M., Lafourcade, P. and Ye, L.
Secure Strassen-Winograd Matrix Multiplication with MapReduce.
DOI: 10.5220/0007916302200227
In Proceedings of the 16th International Joint Conference on e-Business and Telecommunications (ICETE 2019), pages 220-227
ISBN: 978-989-758-378-0
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

2. the public cloud cannot learn any information
about matrices A, B, and C.
Contributions. We summarize our contributions as
follows:
• Our first contribution is a MapReduce version of
the SW matrix multiplication algorithm. We call
our algorithm SM3 for Strassen-Winograd Ma-
trix Multiplication with MapReduce. It improves
the efficiency of the computation compared to the
standard matrix multiplication with MapReduce,
as found in Chapter 2 of (Leskovec et al., 2014).
• Our second contribution is a privacy-preserving
version of the aforementioned algorithm. Our new
algorithm S2M3 (for Secure Strassen-Winograd
Matrix Multiplication with MapReduce) relies on
the MapReduce paradigm and on Paillier-like
public-key cryptosystem. The cloud performs the
multiplication on the encrypted data. At the end
of the computation, the public cloud sends the re-
sult to the user that queried the matrix multipli-
cation result. The user has just to decrypt the re-
sult to discover the matrix multiplication result.
The cloud cannot learn none of the input or out-
put matrices. We formally prove in the extended
paper
1
, using a standard security model, that our
S2M3 protocol satisfies the aforementioned secu-
rity property.
• To show the practical efficiency of SM3 and
S2M3 protocols, we present a proof-of-concept
experimental study using the Apache Hadoop
2
open-source implementation of MapReduce.
Related Work. Chapter 2 of (Leskovec et al., 2014)
presents an introduction to the MapReduce paradigm.
The security and privacy concerns of MapReduce
have been summarized in a survey by Derbeko et
al. (Derbeko et al., 2016). More precisely, the state-
of-the-art techniques for execution of MapReduce
computations while preserving privacy focus on prob-
lems such as word search (Blass et al., 2012), in-
formation retrieval (Mayberry et al., 2013), group-
ing and aggregation queries (Ciucanu et al., 2018),
equijoins (Dolev et al., 2016), and matrix multipli-
cation (Bultel et al., 2017). The general goal of these
works is to execute MapReduce computations such
that the public cloud cannot learn any information on
the input or output data.
In this paper, we focus on the matrix multipli-
cation computation. Recently, (Bultel et al., 2017)
1
https://hal.archives-ouvertes.fr/hal-02129149
2
https://hadoop.apache.org
secured the two standard MapReduce algorithms for
matrix multiplication using one and two MapReduce
rounds as found in Chapter 2 of (Leskovec et al.,
2014). For each algorithm, they proposed two dif-
ferent approaches called SP for Secure-Private and
CRSP for Collision-Resistance Secure-Private. The
two approaches are based on the Paillier-like some-
what homomorphic cryptosystem. Contrary to the
CRSP approach, the SP approach assumes that dif-
ferent nodes of the cloud do not collude.In our paper,
we assume that all nodes of the public cloud can col-
lude, hence we consider the public cloud as only one
entity; hence our secure protocol S2M3 can be con-
sidered as a CRSP approach. We show that the matrix
multiplication is performed faster using the Strassen-
Winograd algorithm with MapReduce than with the
standard matrix multiplication with MapReduce for
the no-secure and the secure approaches.
Distributed matrix multiplication has been thor-
oughly investigated in the secure multi-party compu-
tation model (MPC) (Du and Atallah, 2001; Dumas
et al., 2016; Dumas et al., 2017; Amirbekyan and
Estivill-Castro, 2007; Wang et al., 2009), whose goal
is to allow different nodes to jointly compute a func-
tion over their private inputs without revealing them.
The aforementioned works on secure distributed ma-
trix multiplication have different assumptions com-
pared to our MapReduce framework: (i) they as-
sume that nodes contain entire vectors, whereas the
division of the initial matrices in chunks as done
in MapReduce does not have such assumptions, and
(ii) in MapReduce, the functions specified by the
user (Dean and Ghemawat, 2004) are limited to map
(process a key/value pair to generate a set of inter-
mediate key/value pairs) and reduce (merge all inter-
mediate values associated with the same intermediate
key) while the MPC model relies on more complex
functions than map and reduce. Moreover, generic
MPC protocols (Ma and Deng, 2008; Cramer et al.,
2001) allow several nodes to securely evaluate any
function such that matrix multiplication computation.
Such protocols could be used to secure MapReduce.
However, due to their generic nature, they are ineffi-
cient and require a lot of interactions between parties.
Our goal is to design an optimized protocol to secure
Strassen-Winograd algorithm with MapReduce.
Moreover, (Li et al., 2011) and (ul Hassan Khan
et al., 2016) study optimizations to compute Strassen-
Winograd matrix multiplication. However, they do
not consider any privacy issues and do not propose a
secure approach of the algorithm.
To the best of our knowledge, we are the first
to secure the Strassen-Winograd algorithm with the
MapReduce paradigm.
Secure Strassen-Winograd Matrix Multiplication with MapReduce
221

Outline. In Section 2, we outline the SW algo-
rithm and the cryptographic tools on which we rely.
Then, we present the Strassen-Winograd algorithm
with MapReduce (SM3) in Section 3, the secure ap-
proach (S2M3) in Section 4, and experimental results
in Section 5.
2 PRELIMINARIES
We start by recalling the Winograd’s variant of
Strassen algorithm (Gathen and Gerhard, 2013) called
Strassen-Winograd algorithm and denoted SW in the
rest of the paper. Then we give cryptographic tools
used in the rest of the paper.
2.1 Strassen-Winograd Algorithm
Let A and B be two square matrices of size d × d
where d = 2
k
with k ∈ N
?
. The standard matrix multi-
plication algorithm computes the product C = A×B in
O(d
3
) while SW computes C in O(d
2.807
) (Strassen,
1969).
First, the SW algorithm splits matrices A and B
into four quadrants of equal dimensions such that A =
A
11
A
12
A
21
A
22
and B =
B
11
B
12
B
21
B
22
.
Using these submatrices, SW computes 8 addi-
tions, 7 recursive multiplications, and 7 final additions
as follow:
S
1
= A
21
+ A
22
,
S
2
= S
1
− A
11
,
S
3
= A
11
− A
21
,
S
4
= A
12
− S
2
,
T
1
= B
12
− B
11
,
T
2
= B
22
− T
1
,
T
3
= B
22
− B
12
,
T
4
= T
2
− B
21
,
R
1
= A
11
× B
11
,
R
2
= A
12
× B
21
,
R
3
= S
4
× B
22
,
R
4
= A
22
× T
4
,
R
5
= S
1
× T
1
,
R
6
= S
2
× T
2
,
R
7
= S
3
× T
3
,
C
1
= R
1
+ R
2
,
C
2
= R
1
+ R
6
,
C
3
= C
2
+ R
7
,
C
4
= C
2
+ R
5
,
C
5
= C
4
+ R
3
,
C
6
= C
3
− R
4
,
C
7
= C
3
+ R
5
.
The final result: A ×B =
C
1
C
5
C
6
C
7
.
Since, we assume that d = 2
k
with k ∈ N
?
, we can
iterate this process k times (recursively) until the sub-
matrices have a size equal to 1×1. The SW algorithm
is generalizable to matrices for wich d is not a power
of 2, as we point out in Section 4.3.
2.2 Cryptographic Tools
We recall the definition of a public-key encryption
scheme and the the Paillier’s cryptosystem used in our
secure protocol.
Definition 1 (Public-Key Encryption). Let η be a
security parameter. A public-key encryption (PKE)
scheme is defined by three algorithms (G,E, D):
G(η): returns a public/private key pair (pk, sk).
E
pk
(m): returns the ciphertext c.
D
sk
: returns the plaintext m.
In the following, we require an additive homo-
morphic encryption scheme to secure the compu-
tation of SW using MapReduce. There exist sev-
eral schemes that have this property (Okamoto and
Uchiyama, 1998; Paillier, 1999; Damg
˚
ard and Ju-
rik, 2001; Naccache and Stern, 1998). We choose
Paillier cryptosystem (Paillier, 1999) to illustrate spe-
cific required homomorphic properties. Our proto-
cols and proofs are generic, since any other encryp-
tion schemes having such properties can be used.
2.3 Paillier’s Cryptosystem
Paillier’s cryptosystem is an indistinguishable under
chosen plaintext attack (IND-CPA) scheme (Sako,
2011), we recall the key generation, the encryption
and decryption algorithms.
Key Generation. We denote by Z
n
, the ring of
integers modulo n and by Z
×
n
the set of inversible
elements of Z
n
. The public key pk of Paillier
cryptosystem is (n, g), where g ∈ Z
×
n
2
and n = p · q
is the product of two prime numbers such that
gcd(p,q) = 1. The corresponding private key sk is
(λ,µ), where λ is the least common multiple of p − 1
and q − 1 and µ = (L(g
λ
mod n
2
))
−1
mod n, where
L(x) = (x − 1)/n.
Encryption Algorithm. Let m be a message such that
m ∈ Z
n
. Let g be an element of Z
×
n
2
and r be a random
element of Z
×
n
. We denote by E
pk
(·) the encryption
function that produces the ciphertext c from a given
plaintext m with the public key pk = (n, g) as follows:
c = g
m
· r
n
mod n
2
.
Decryption Algorithm. Let c be a ciphertext such that
c ∈ Z
×
n
2
. We denote by D
sk
(·) the decryption function
of c with the secret key sk = (λ,µ) defined as follows:
m = L
c
λ
mod n
2
· µ mod n.
2.4 Homomorphic Properties
Paillier cryptosystem is a partial homomorphic en-
cryption scheme. We present its properties.
Homomorphic Addition of Plaintexts. Let m
1
and m
2
be two plaintexts in Z
n
. The product
of the two associated ciphertexts with the public
SECRYPT 2019 - 16th International Conference on Security and Cryptography
222

key pk = (n,g), denoted c
1
= E
pk
(m
1
) = g
m
1
· r
n
1
mod n
2
and c
2
= E
pk
(m
2
) = g
m
2
· r
n
2
mod n
2
, is
the encryption of the sum of m
1
and m
2
, i.e.,
E
pk
(m
1
) · E
pk
(m
2
) = E
pk
(m
1
+ m
2
mod n). We also
remark that: E
pk
(m
1
)/E
pk
(m
2
) = E
pk
(m
1
− m
2
).
Specific Homomorphic Multiplication of Plaintexts.
Let m
1
and m
2
be two plaintexts in Z
n
and c
1
∈ Z
×
n
2
be the ciphertext of m
1
with the public key pk. With
Paillier cryptosystem, c
1
raised to the power of m
2
is
the encryption of the product of the two plaintexts m
1
and m
2
, i.e., E
pk
(m
1
)
m
2
= E
pk
(m
1
· m
2
mod n).
Interactive Homomorphic Multiplication of Cipher-
texts. Cramer et al. (Cramer et al., 2001) show that an
interactive protocol makes possible to perform mul-
tiplication over ciphertexts using additive homomor-
phic encryption schemes. More precisely, Bob knows
two ciphertexts c
1
,c
2
∈ Z
×
n
2
of the plaintexts m
1
,m
2
∈
Z
n
with the public key of Alice, he wants to obtain the
cipher of the product of m
1
and m
2
without revealing
to Alice m
1
and m
2
. In order to do this, Bob has to in-
teract with Alice. Bob first picks two randoms δ
1
and
δ
2
and sends to Alice α
1
= c
1
· E
pk
A
(δ
1
) and α
2
=
c
2
· E
pk
A
(δ
2
). By decrypting respectively α
1
and α
2
,
Alice recovers respectively m
1
+ δ
1
and m
2
+ δ
2
. She
sends to Bob β = E
pk
A
((m
1
+ δ
1
) · (m
2
+ δ
2
)). Then,
Bob can deduce the value of E(m
1
· m
2
) by comput-
ing: β/E
pk
A
(δ
1
· δ
2
) · c
δ
1
1
· c
δ
2
2
, since E
pk
A
((m
1
+ δ
1
) ·
(m
2
+ δ
2
)) = E
pk
A
(m
1
· m
2
) · E
pk
A
(m
1
· δ
2
) · E
pk
A
(m
2
·
δ
1
) · E
pk
A
(δ
1
· δ
2
).
3 STRASSEN-WINOGRAD
MATRIX MULTIPLICATION
We present our protocol SM3 for Strassen-Winograd
Matrix Multiplication with MapReduce. The aim is
to compute the multiplication of two square matrices
A and B of order d = 2
k
(where k ∈ N
?
) using SW
algorithm with MapReduce.
The cloud runs two different MapReduce phases:
the deconstruction phase and the combination phase,
each of them being repeated k = log
2
(d) times. At the
end of the combination phase, the matrix C = A × B
is sent to the user.
We can think of each element a
i j
∈ A (resp. b
i j
∈
B) as a tuple (A,d,i, j,a
i j
) (resp. (B,d,i, j,b
i j
)). Note
that A and B are not the matrices themselves but the
names of the matrices. In order to run the SW al-
gorithm with MapReduce, a key called tag initial-
ized to 0 is added to each tuple. Hence tuples are
key-value pairs of the form (0,(A, d,i, j,a
i j
)) and
(0,(B,d, i, j,b
i j
)). All these key-value pairs establish
a relation that is outsourced to the cloud.
3.1 Deconstruction Phase
We present the deconstruction phase of SM3. This
phase computes recursively all the needed submatri-
ces of dimension 2 × 2 to multiply in order to con-
struct the final matrix.
The Map Function. This function is the identity.
For every input element with key t and value v, it pro-
duces the key-value pair (t,v).
The Reduce Function. This function is presented
in Fig. 1. If δ > 2, i.e., the dimension of matri-
ces formed by elements a
i, j
and b
i, j
associated to the
key t, it produces 7 couples of submatrices of dimen-
sion δ/2. These couples of submatrices correspond
to the recursive multiplications in SW algorithm and
are keyed with a different tag in order to distribute
the compution using MapReduce. When δ = 2, the 7
multiplications are between integers (and not between
matrices), results are sent to the combination phase.
Input: (key, values).
// key: a tag t.
// values: collection of (A,δ, i, j,a
i, j
)
// or (B,δ, i, j,b
i, j
).
A ← (a
i, j
)
1≤i, j≤δ
; B ← (b
i, j
)
1≤i, j≤δ
;
A
11
A
12
A
21
A
22
= A;
B
11
B
12
B
21
B
22
= B;
S
1
← A
21
+ A
22
; S
2
← S
1
− A
11
; S
3
← A
11
− A
21
;
S
4
← A
12
− S
2
; T
1
← B
12
− B
11
; T
2
← B
22
− T
1
;
T
3
← B
22
− B
12
; T
4
← T
2
− B
21
;
L ←
[A
11
,B
11
],[A
12
,B
21
],[S
4
,B
22
],[A
22
,T
4
],[S
1
,T
1
],
[S
2
,T
2
],[S
3
,T
3
]
;
if δ 6= 2 then
for 1 ≤ u ≤ 7 do
(a
?
i, j
)
1≤i, j≤δ/2
= A
?
← L[u − 1][0];
(b
?
i, j
)
1≤i, j≤δ/2
= B
?
← L[u − 1][1];
foreach (v,w) ∈ J1,δ/2K do
emit (tku,(A, δ/2,v,w, a
?
v,w
));
emit (tku,(B, δ/2,v,w, b
?
v,w
));
else
for 1 ≤ u ≤ 7 do
r ← L[u − 1][0] · L[u − 1][1];
emit (t,(R
u
,1, 1,1, r)).
Figure 1: Reduce function of the deconstruction phase for
SM3.
Secure Strassen-Winograd Matrix Multiplication with MapReduce
223

3.2 Combination Phase
We present the combination phase of SM3 which is
executed k times where k = log
2
(d). This phase con-
structs the matrix C = A ×B using all results received
from the deconstruction phase.
The Map Function. This function is the identity.
For every input element with key t and value v, it pro-
duces the key-value pair (t,v).
The Reduce Function. This function is presented
in Fig. 2. At each round, each key is associated to
elements forming 7 submatrices of dimension δ. Fol-
lowing SW algorithm, these submatrices are used to
construct a matrix of dimension 2 · δ. At the end of
the combination phase (after k rounds), the reduce
function sends to the user key-value pairs of the form
(−,(C,i, j,c
i j
)) forming matrix C = A × B. We do not
specify key value since all these elements are part of
the final matrix.
Input: (key, values).
// key: a tag t.
// values: collection of (R
i
,δ, j, k,r
j,k
).
for 1 ≤ i ≤ 7 do
R
i
← (r
j,k
)
1≤ j,k≤δ
such that (R
i
,δ, j, k,r
j,k
) is in
values;
C
1
← R
1
+ R
2
; C
2
← R
1
+ R
6
; C
3
← C
2
+ R
7
;
C
4
← C
2
+ R
5
; C
5
← C
4
+ R
3
; C
6
← C
3
− R
4
;
C
7
← C
3
+ R
5
;
C =
C
1
C
5
C
6
C
7
;
if δ 6= d then
foreach (i, j) ∈ J1,2 · δK do
emit (t[: −1],(R
t[−1]
,2 · δ, i, j,c
i, j
));
else
foreach (i, j) ∈ J1,dK do
emit (−,(C,i, j,c
i, j
)).
Figure 2: Reduce function of the combination phase for
SM3.
4 SECURE
STRASSEN-WINOGRAD
MATRIX MULTIPLICATION
We now present our secure approach, called S2M3
(for Secure Strassen-Winograd Matrix Multiplication
with Mapreduce), in order to ensure privacy of ele-
ments of matrices. Similarly to SM3, the secured ver-
sion S2M3 considers matrices A and B as a relation.
However, instead of sending key-value pairs of the
form (0,(A, d,i, j,a
i, j
)) and (0,(B, d,i, j,b
i, j
)) to the
cloud, we encrypt each element of matrices and send
key-value pairs of the form (0, (A,d,i, j,E
pk
(a
i, j
)))
and (0,(B,d, i, j,E
pk
(b
i, j
))). Note that pk is the pub-
lic key of the user that queried the matrix multiplica-
tion to the data owner.
4.1 Deconstruction Phase
We present the deconstruction phase of S2M3. This
phase computes recursively all the needed submatri-
ces of dimension 2 × 2 to multiply in order to con-
struct the final matrix.
The Map Function. This function is the identity.
For every input element with key t and value v, it pro-
duces the key-value pair (t,v).
The Reduce Function. This function is pre-
sented in Fig. 3. It computes 8 submatri-
ces S
1
,. .. ,S
4
,T
1
,. .. ,T
4
using functions P.Add and
P.Sub. Function P.Add(A,B) (resp. P.Sub(A,B))
computes E
pk
(a
i, j
) · E
pk
(b
i, j
) (resp. E
pk
(a
i, j
) ·
E
pk
(b
i, j
)
−1
) for each pair (i, j); due to Paillier homo-
morphic properties, these multiplications (resp. divi-
sions) of elements is equal to E
pk
(a
i, j
+ b
i, j
) (resp.
E
pk
(a
i, j
− b
i, j
)).
If δ > 2, i.e., the dimension of matrices formed
by elements E
pk
(a
i, j
) and E
pk
(b
i, j
) associated to the
key t, it produces 7 couples of submatrices of dimen-
sion δ/2. When δ = 2, we need to compute 7 mul-
tiplications between integers encrypted with Paillier
cryptosystem. Hence we use Paillier interactive mul-
tiplication and denoted P.Interactive. Then results are
sent to the combination phase.
4.2 Combination Phase
We present the combination phase of S2M3 run k
times where k = log
2
(d). This phase constructs the
matrix C
0
= (E
pk
(c
i, j
))
1≤i, j≤d
with c
i, j
∈ C = A × B
using all results received from the deconstruction
phase.
The Map Function. This function is the identity.
For every input element with key t and value v, it pro-
duces the key-value pair (t,v).
The Reduce Function. This function is presented
in Fig. 4. At each round, each key is associated to
elements forming 7 submatrices of dimension δ. As
for the deconstruction phase, we use Paillier homo-
morphic properties in order to construct a matrix of
SECRYPT 2019 - 16th International Conference on Security and Cryptography
224

Input: (key, values).
// key: a tag t.
// values: collection of (A,δ, i, j,E
pk
(a
i, j
))
// or (B,δ, i, j,E
pk
(b
i, j
)).
A ← (E
pk
(a
i, j
))
1≤i, j≤δ
; B ← (E
pk
(b
i, j
))
1≤i, j≤δ
;
A
11
A
12
A
21
A
22
= A;
B
11
B
12
B
21
B
22
= B;
S
1
← P.Add(A
21
,A
22
);
S
2
← P.Sub(S
1
,A
11
);
S
3
← P.Sub(A
11
,A
21
);
S
4
← P.Sub(A
11
,S
2
);
T
1
← P.Sub(B
12
,B
11
);
T
2
← P.Sub(B
22
,T
1
);
T
3
← P.Sub(B
22
,B
12
);
T
4
← P.Sub(T
2
,B
21
);
L ←
[A
11
,B
11
],[A
12
,B
21
],[S
4
,B
22
],[A
22
,T
4
],[S
1
,T
1
],
[S
2
,T
2
],[S
3
,T
3
]
;
if δ 6= 2 then
for 1 ≤ u ≤ 7 do
(a
?
i, j
)
1≤i, j≤δ/2
= A
?
← L[u − 1][0];
(b
?
i, j
)
1≤i, j≤δ/2
= B
?
← L[u − 1][1];
foreach (v,w) ∈ J1,δ/2K do
emit (tku,(A, δ/2,v,w, a
?
v,w
));
emit (tku,(B, δ/2,v,w, b
?
v,w
));
else
for 1 ≤ u ≤ 7 do
r ← P.Interactive(L[u − 1][0],L[u − 1][1]);
emit (t,(R
u
,1, 1,1, r)).
Figure 3: Reduce function of the deconstruction phase for
S2M3.
dimension 2 · δ. At the end of the combination phase
(after k rounds), the reduce function sends to the user
key-value pairs of the form (−,(C
0
,i, j, c
i, j
)) forming
the encryption of matrix C = A × B. We do not spec-
ify key value since all these elements are part of the
final matrix.
4.3 Padding and Peeling: On a Quest
for All Dimensions
Default SW algorithm works for square matrices of
dimension d = 2
k
with k ∈ N
?
. In this section, we
recall the dynamic padding and the dynamic peel-
ing (Huss-Lederman et al., 1996) methods allowing
to perform matrix multiplication with SW algorithm
for square matrices of arbitrary dimension.
Dynamic Padding. For each round of the decon-
struction phase, the Reduce function checks the di-
mension’s parity of the two considered matrices. If
matrices have an odd number of rows and columns,
then it adds an extra row and an extra column of zeros
for SM3 protocol, and of E
pk
(0) for S2M3 protocol.
In the other case, the Reduce function works as usual.
Then, the Reduce function of the combination phase
Input: (key, values).
// key: a tag t.
// values: collection of (R
i
,δ, j, k,r
j,k
).
for 1 ≤ i ≤ 7 do
R
i
← (r
j,k
)
1≤ j,k≤δ
such that (R
i
,δ, j, k,r
j,k
) is in
values;
C
1
← P.Add(R
1
,R
2
);
C
2
← P.Add(R
1
,R
6
);
C
3
← P.Add(C
2
,R
7
);
C
4
← P.Add(C
2
,R
5
);
C
5
← P.Add(C
4
,R
3
);
C
6
← P.Sub(C
3
,R
4
);
C
7
← P.Add(C
3
,R
5
);
C
0
=
C
1
C
5
C
6
C
7
;
if δ 6= d then
foreach (i, j) ∈ J1,2 · δK do
emit (t[: −1],(R
t[−1]
,2 · δ, i, j,c
0
i, j
));
else
foreach (i, j) ∈ J1,dK do
emit (−,(C
0
,i, j, c
i, j
)).
Figure 4: Reduce function of the combination phase for
S2M3.
removes, when it is required, the extra row and the
extra column.
Comparing to the static padding, the dynamic
padding avoids huge memory allocations. Indeed, the
static padding method pads matrices to obtain a num-
ber of rows and columns equal to a power-of-2.
Dynamic Peeling. As the previous method, the Re-
duce function checks for each round of the decon-
struction phase the dimension’s parity of the two con-
sidered matrices. If matrices have an odd number
of rows and columns, then it splits each of the two
considered matrices into four blocks as illustrated in
Fig. 5. Then, for SM3 and S2M3 protocols, it uses
the two square blocks for the recursive multiplication,
while other blocks are used for the block matrix mul-
tiplication. We note that the block matrix multiplica-
tion can be performed in the encrypted domain due to
the homomorphic properties of Paillier’s cryptosys-
tem. Otherwise, the Reduce function works as usual.
Then, the Reduce function of the combination phase
combines the resulted matrices to build the final re-
sult.
M =
m
1,1
.. . m
1,d−1
m
1,d
.
.
.
.
.
.
.
.
.
.
.
.
m
d−1,1
.. . m
d−1,d−1
m
d−1,d
m
d,1
.. . m
d,d−1
m
d,d
.
Figure 5: Splitting of matrix M of dimension d according
the dynamic peeling method, with d an odd number.
Secure Strassen-Winograd Matrix Multiplication with MapReduce
225
5 EXPERIMENTAL RESULTS
We present the experimental results for our SM3 and
S2M3 protocols using the Hadoop implementation of
MapReduce. All computations have been done on
a computer running on Ubuntu 16.04 with Hadoop
3.2.0. The computer has an Intel® Core™ i7-4790
CPU cadenced at 3.60GHz, and 16Gb of RAM.
240 270 300 330
360
390 420
450
0
50
100
Matrices’ dimension.
CPU time (in seconds).
SM3-dPad SM3-dPeel
SM3-sPad MM-1R
Figure 6: CPU time vs the matrices’ dimension for SM3
protocol with the static padding (SM3-sPad), dynamic
padding (SM3-dPad), and dynamic peeling (SM3-dPeel),
and comparisons with the standard matrix multiplication
using one MapReduce round (Leskovec et al., 2014)
(MM-1R).
90 120
150
180 210 240 270 300
0
200
400
600
Matrices’ dimension.
CPU time (in seconds).
S2M3-dPad S2M3-dPeel
S2M3-sPad CRSP-1R
Figure 7: CPU time vs the matrices’ dimension for S2M3
protocol with the static padding (S2M3-sPad) and dy-
namic padding (S2M3-dPad), and the dynamic peeling
(S2M3-dPeel), and comparisons with the CRSP-1R proto-
col (Bultel et al., 2017).
We generate two random square matrices A and B
of order d such that 240 ≤ d ≤ 450 for the no-secure
approaches, and 90 ≤ d ≤ 300. Moreover, we build
A and B such that A,B ∈ Z
d×d
10
. For each order d, we
perform matrix multiplication between A and B with
SM3 and S2M3 protocols using static padding, dy-
namic padding, and dynamic peeling methods. We
also run the standard matrix multiplication using one
MapReduce round (Leskovec et al., 2014) and the se-
cure approach denoted CRSP-1R (Bultel et al., 2017).
As proof of concept, we use Paillier’s cryptosystem
with the public key pk = (n, g) where n is 64-bits
long.
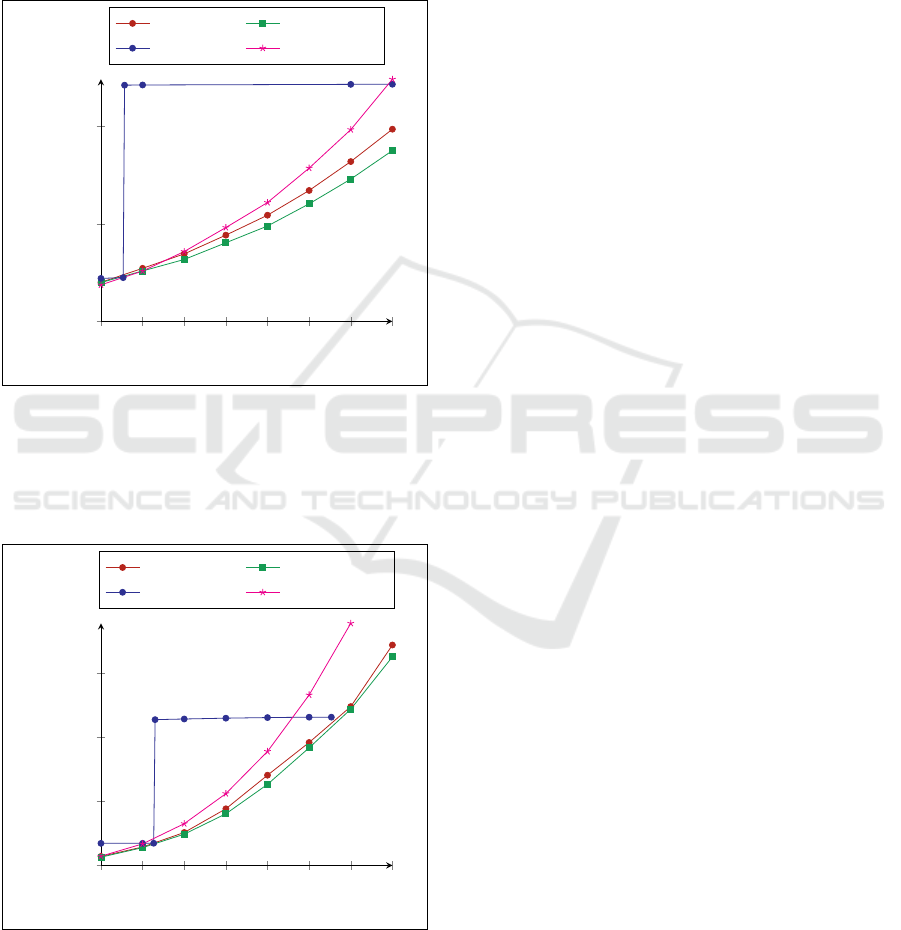
Scalability. We present in Fig. 6 the CPU time for
our SM3 protocol using static and dynamic padding
methods, and dynamic peeling method. Without any
security, our SM3 protocol using dynamic padding
and peeling methods performs the matrix multiplica-
tion faster than the standard matrix multiplication for
the largest dimensions.
For secure protocols, CPU times are presented in
Fig. 7. We also remark that our S2M3 protocol using
dynamic padding and peeling methods performs the
matrix multiplication faster than the CRSP-1R proto-
col (Bultel et al., 2017).
6 CONCLUSION
We have presented SM3, an efficient algorithm to
compute the Strassen-Winograd matrix multiplication
using the MapReduce paradigm. We have also pre-
sented S2M3, a secure approach of SM3 that satisfies
privacy guarantees such that the public cloud does not
learn any information on input matrices and on the
output matrix. To achieve our goal, we have relied
on the well-known Paillier cryptosystem. We have
compared our protocol S2M3 to the CRSP matrix
multiplication with MapReduce proposed by Bultel et
al. (Bultel et al., 2017) and shown that S2M3 is more
efficient.
Looking forward to future work, we aim to inves-
tigate the matrix multiplication with privacy guaran-
tees in different big data systems (e.g. Spark, Flink)
whose users also tend to outsource data and computa-
tions as MapReduce.
REFERENCES
Amirbekyan, A. and Estivill-Castro, V. (2007). A New Ef-
ficient Privacy-Preserving Scalar Product Protocol. In
Australasian Data Mining Conference AusDM.
SECRYPT 2019 - 16th International Conference on Security and Cryptography
226

Blass, E., Pietro, R. D., Molva, R., and
¨
Onen, M. (2012).
PRISM - privacy-preserving search in mapreduce. In
Privacy Enhancing Technologies Symposium, PETS.
Bultel, X., Ciucanu, R., Giraud, M., and Lafourcade, P.
(2017). Secure matrix multiplication with mapreduce.
In International Conference on Availability, Reliabil-
ity and Security, ARES.
Chartrand, G. (1985). Introductory Graph Theory. Dover.
Ciucanu, R., Giraud, M., Lafourcade, P., and Ye, L. (2018).
Secure Grouping and Aggregation with MapReduce.
In International Joint Conference on e-Business and
Telecommunications, SECRYPT.
Cramer, R., Damg
˚
ard, I., and Nielsen, J. B. (2001). Mul-
tiparty Computation from Threshold Homomorphic
Encryption. In EUROCRYPT, International Confer-
ence on the Theory and Application of Cryptographic
Techniques.
Damg
˚
ard, I. and Jurik, M. (2001). A generalisation, a sim-
plification and some applications of paillier’s proba-
bilistic public-key system. In International Workshop
on Practice and Theory in Public Key Cryptography:
Public Key Cryptography, PKC.
Dean, J. and Ghemawat, S. (2004). Mapreduce: Simplified
data processing on large clusters. In 6th Symposium on
Operating System Design and Implementation, OSDI.
Derbeko, P., Dolev, S., Gudes, E., and Sharma, S. (2016).
Security and privacy aspects in mapreduce on clouds:
A survey. Computer Science Review, 20.
Dolev, S., Li, Y., and Sharma, S. (2016). Private and se-
cure secret shared mapreduce (extended abstract) -
(extended abstract). In Data and Applications Secu-
rity and Privacy XXX - 30th Annual IFIP.
Du, W. and Atallah, M. J. (2001). Privacy-Preserving Co-
operative Statistical Analysis. In Annual Computer
Security Applications Conference ACSAC.
Dumas, J., Lafourcade, P., Orfila, J., and Puys, M. (2016).
Private Multi-party Matrix Multiplication and Trust
Computations. In International Joint Conference on
e-Business and Telecommunications SECRYPT.
Dumas, J., Lafourcade, P., Orfila, J., and Puys, M. (2017).
Dual protocols for private multi-party matrix multipli-
cation and trust computations. Computers & Security,
71.
Gathen, J. v. z. and Gerhard, J. (2013). Modern computer
algebra. Cambridge University Press, 3rd edition.
Huss-Lederman, S., Jacobson, E. M., Johnson, J. R., Tsao,
A., and Turnbull, T. (1996). Implementation of
strassen’s algorithm for matrix multiplication. In
ACM/IEEE Conference on Supercomputing.
Krizhevsky, A., Sutskever, I., and Hinton, G. E. (2012). Im-
agenet classification with deep convolutional neural
networks. In Annual Conference on Neural Informa-
tion Processing Systems.
Le Gall, F. (2014). Powers of tensors and fast matrix mul-
tiplication. In International Symposium on Symbolic
and Algebraic Computation, ISSAC.
Leskovec, J., Rajaraman, A., and Ullman, J. D. (2014). Min-
ing of Massive Datasets, 2nd Ed. Cambridge Univer-
sity Press.
Li, J., Ranka, S., and Sahni, S. (2011). Strassen’s matrix
multiplication on gpus. In IEEE International Con-
ference on Parallel and Distributed Systems, ICPADS.
Ma, Q. and Deng, P. (2008). Secure Multi-party Protocols
for Privacy Preserving Data Mining. In Wireless Algo-
rithms, Systems, and Applications Conference, WASA.
Mayberry, T., Blass, E., and Chan, A. H. (2013). PIRMAP:
efficient private information retrieval for mapreduce.
In Financial Cryptography and Data Security, FC.
Naccache, D. and Stern, J. (1998). A new public key cryp-
tosystem based on higher residues. In Conference on
Computer and Communications Security, CCS.
Okamoto, T. and Uchiyama, S. (1998). A new public-key
cryptosystem as secure as factoring. In EUROCRYPT,
International Conference on the Theory and Applica-
tion of Cryptographic Techniques.
Paillier, P. (1999). Public-key cryptosystems based on com-
posite degree residuosity classes. In EUROCRYPT,
International Conference on the Theory and Applica-
tion of Cryptographic Techniques.
Sako, K. (2011). Goldwasser-micali encryption scheme. In
Encyclopedia of Cryptography and Security, 2nd Ed.
Shoshan, A. and Zwick, U. (1999). All pairs shortest paths
in undirected graphs with integer weights. In 40th
Annual Symposium on Foundations of Computer Sci-
ence, FOCS.
Strassen, V. (1969). Gaussian elimination is not optimal.
Numerische Mathematik, 13(4).
ul Hassan Khan, A., Al-Mouhamed, M., Fatayer, A., and
Nazeeruddin, M. (2016). Optimizing the matrix multi-
plication using strassen and winograd algorithms with
limited recursions on many-core. International Jour-
nal of Parallel Programming, 44(4).
Wang, I.-C., Shen, C.-H., Zhan, J., Hsu, T.-s., Liau, C.-J.,
and Wang, D.-W. (2009). Toward empirical aspects
of secure scalar product. IEEE Transactions on Sys-
tems, Man, and Cybernetics, Part C (Applications and
Reviews), 39(4).
Zwick, U. (1998). All pairs shortest paths in weighted di-
rected graphs exact and almost exact algorithms. In
39th Annual Symposium on Foundations of Computer
Science, FOCS.
Secure Strassen-Winograd Matrix Multiplication with MapReduce
227
