
SCHEDULING AND QOS FOR LEAK RATE IN POLICING
MECHANISMS OVER TELECOMMUNICATIONS NETWORK
Somchai Lekcharoen *and
Chanintorn Jittawiriyanukoon **
* Faculty of Information Technology, Rangsit University
, Thailand
** Faculty of Science and Technology, Assumption University, Thailand
Keywords: VDSL, Fuzzy Control Policing Mechanisms and Queue Leak Rate (QLR).
Abstract: High-performance frame communication networks including VDSL have been conceived to carry traffic
sources and support a continuum of transport rates ranging from low bit-rate to high bit-rate traffic. As a
number of telecommunications traffic (bursty traffic) fluctuates on a certain network it results in
congestion. The traditional policing mechanisms are finite-sized buffers with queue management techniques
and fixed leak rate. Most queue management schemes employ fixed thresholds or a limited number of
arrival frames, to determine when to allow or discard the entry of frames. However, traditional policing
mechanisms have proved to be inefficient in coping with the conflicting requirements of ideal policing
mechanisms, that is, low dropping frames and high conforming frames. An alternative solution based on
artificial intelligence techniques, specifically, in the field of fuzzy systems is introduced. In this paper, a
fuzzy control queue leak rate (QLR) of the buffer prior to policing mechanism is investigated. The
performance of this alternative method is then compared with traditional policing mechanisms. Simulation
results show that over VDSL network, the fuzzy control scheme helps improve performance of QLR in
policing mechanisms. The performance of proposed method is much better than traditional policing ones.
1 INTRODUCTION
In VDSL networks, large number of traffic sources
always arises, resulting in network congestion. To
prevent this situation, some congestion control
mechanisms depending on type of traffic sources are
introduced. Also, some policing mechanisms can be
considered to help improve the main performance
measures, such as queueing delay, transmission
delay, bandwidth allocation, and throughput.
Presently, VDSL is getting very significant attention
from implementers and service providers as it
guarantees to deliver highest bandwidth data rates to
dispersed locations with little changes to the existing
infrastructure. VDSL services ensure dedicated,
point-to-point, public network access over twisted-
pair copper wire. As it is difficult to model a
complicated control system, especially at the
scheduling or at the queue leak rate (QLR), the
development of alternative modeling and control
techniques including fuzzy logic is necessary. Fuzzy
model may lead to describe the behavior of systems
well whenever the decision has to be made for the
ambiguous application in control. Thus due to the
demand for an inexpensive but reliable system, the
fuzzy approach may turn out to be a useful
mechanism to control cases with both the
complexity and uncertainty. There are many
previous studies involving traffic policing
mechanisms (Lekcharoen et al, 2004),(Pakdeepinit
et al, 2002),(Chen, 2000), however QLR is not
mentioned. In this paper, the idea of QLR control is
proposed to help improve the system performance.
The performance after being controlled by QLR is
compared to the previous one (uncontrolled by
QLR).
This paper is organized as follows. An overview
of traffic policing mechanisms is proposed in section
II. Section III defines the model of a fuzzy control
QLR in policing mechanisms. Section IV describes
the simulation model and section V discusses about
a performance evaluation of the proposed QLR and
then a comparison to traditional policing
mechanisms is produced. Section VI summarizes the
conclusion and makes recommendation for future
research.
358
Lekcharoen S. and Jittawiriyanukoon C. (2005).
SCHEDULING AND QOS FOR LEAK RATE IN POLICING MECHANISMS OVER TELECOMMUNICATIONS NETWORK.
In Proceedings of the Second International Conference on e-Business and Telecommunication Networks, pages 359-363
DOI: 10.5220/0001409203590363
Copyright
c
SciTePress
2 DESCRIPTION AND
MODELING OF TRAFFIC
POLICING MECHANISM
2.1 Requirement for policing
mechanism
Traffic policing allows us to control the maximum
rate of traffic sent or received on an interface during
the entire active phase and must operate in real time.
The mechanisms have been proposed which are
described in the following sections.
2.1.1 Traffic source model
In our simulation, a burst traffic stream from a
single source is modeled as a burst/silence traffic
stream. The burst-period model is single flow and
silence-period model is silent. Burst-periods and
silence periods are strictly alternating (Lekcharoen
et al, 2004).
2.1.2 Policing mechanisms
Various congestion control traffic policing
mechanisms are also introduced in (Lekcharoen et
al, 2004). In this paper, three policing mechanisms
are investigated including the Leaky Bucket(LB),
the Jumping Window Mechanism(JW) and the
triggered jumping window(TJW) for our
analysis(Pakdeepinit et. al, 2002), (Chen, 2000).
3 FUZZY CONTROL POLICING
MODEL
In this section, we will first describe a new fuzzy
control policing mechanism which meets the
requirements of performance, flexibility and cost-
effective implementation of VDSL networks.
Concepts of fuzzy sets and fuzzy logic control have
been introduced and developed by (Rose and
David,2000), (You-Chang et. al, 2001).
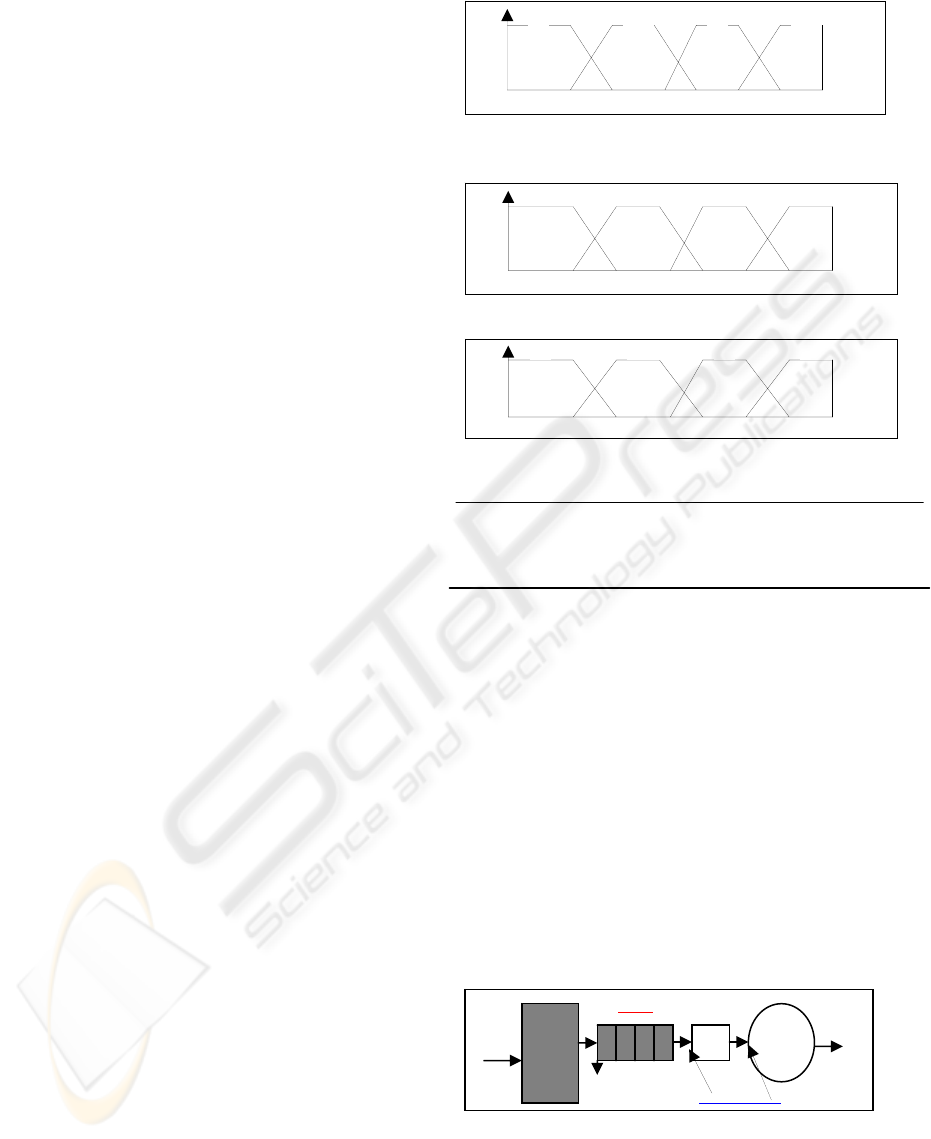
3.1 Regulator input fuzzification
Input variables are transformed into fuzzy set
(fuzzification) and manipulated by a collection of
IF-THEN fuzzy rules, assembled in what is known
as the fuzzy inference engine, as show in figure
below.
i. .
Figure 1: Library of fuzzy sets used in the fuzzification
process (The input variable I).
Figure 2: The term set of output variable Q.
Figure 3.The term set of output variable D.
Table 1: The fuzzy rules
IF I is Low (L) THEN Q is Low and D is Low
IF I is Medium (M) THEN Q is Medium and D is Medium
IF I is High (H) THEN Q is High and D is High
IF I is VeryHigh (VH)THEN Q is High and D is High
In our experiment, fuzzy control QLR in
policing mechanism uses a set of rules as specified
above (figure 1,2,3 and table 1). The selection of
rule base is based on our previous research
(Lekcharoen et al, 2004), (Rose and David, 2000),
(Ruy and Torsten, 2004) and assumptions of how
the system should respond. The assumptions and set
of rules may not relate to the practical point of view
but at least it could pinpoint how to improve the
performance of the system.
4 SIMULATION MODEL
The following figure 4 shows a simulation model
used in this paper.
Figure 4: Simulation model.
1 5 6 9 10 12 13 14Mbps
I
L
M
H
VH
Q
L M H VH
1 8 9 14 15 22 23 105 frames
D
L
M
H
VH
Input
traffic
Fuzzy
Controll
er
Dropped FR
QLR
VDSL
Output
Scheduler
Policer
MQL
1 4 5 8 9 11 12 35 Mb
p
s
SCHEDULING AND QOS FOR LEAK RATE IN POLICING MECHANISMS OVER TELECOMMUNICATIONS
NETWORK
359
4.1 Input traffic
This paper confines the discussion on mainly data.
Data source are generally bursty in nature whereas
voice and video sources can be continuous or bursty,
depending on the compression and coding
techniques used.
4.2 Characteristics of queuing model
There are three components with certain
characteristics that must be examined before the
simulation models are developed.
4.2.1 Arrival characteristics
The pattern of arrivals input traffic is mostly
characterized to be Poisson arrival processes
(Pakdeepinit et al, 2002). Like many random events,
Poisson arrivals occur in such a way that for each
increment of time (T), no matter how large or small,
the probability of arrival is independent of any
previous history. These events may be individual
labels, a burst of labels, label or packet service
completions, or other arbitrary events.
4.2.2 Service facility characteristics
In this paper, service times are randomly distributed
by the exponential probability distribution. This is a
mathematically convenient assumption if arrival
rates are Poisson distributed. In order to examine the
traffic congestion at output of VDSL downstream
link with capacity 15Mbps
(www.dlink.pl/docs/datenblatt/DEV3001_datasheet
_en.pdf), the service time in the simulation model is
specified by the speed of this VDSL link, resulting
that a service time is set to be exponential
distribution with mean 216 µs ,where the frame size
is 405 bytes (www.etsi.org). The buffer size at the
entrance to VDSL network is set to be 1,024 frames
(www.dlink.pl/docs/datenblatt/DEV3001_datasheet
_en.pdf). Once it is exceeding the buffer size then it
is considered to be non-conforming frames (or
dropped frames).
4.2.3 Source traffic descriptor
The source traffic descriptor is the subset of traffic
parameters requested by the source (user), which
characterizes the traffic that will (or should) be
submitted during the connection. The relation of
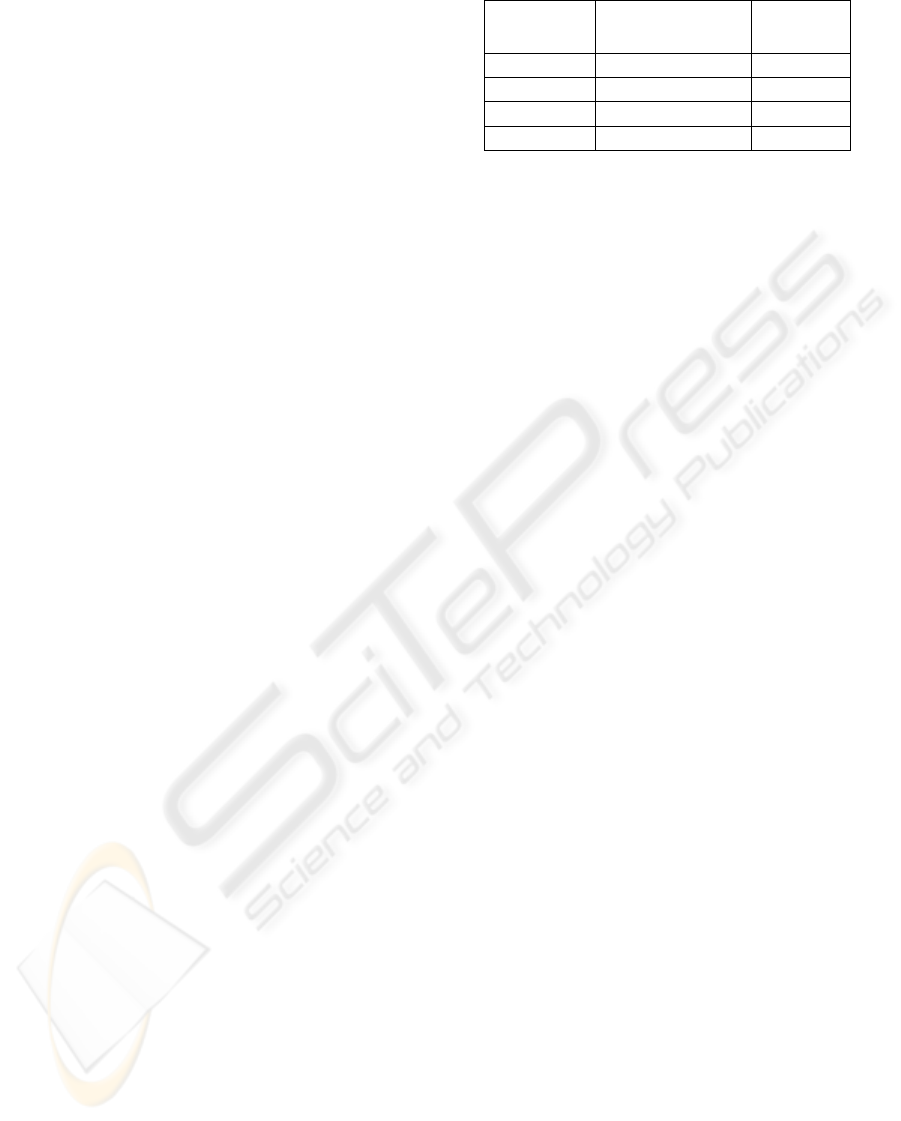
each traffic parameter used in the simulation model
is defined in table 2.
Table 2: Input parameters
5 RESULTS AND ANALYSIS
The comparison of results before and after applying
QLR in policing mechanisms is shown in figure: 5,
6, 7, 8 and 9. They are listed as LB, JW, TJW and
FLB, FJW and FTJW respectively. This This section
focuses on the simulation results as of LB, JW,
TJW, FLB, FJW and FTJW. The input traffic rate
(frame rate varies from 1 Mbps to 35 Mbps) with
burst/silence ratio of 100:100 was simulated and
results were shown in figure 5. It clearly determines
that the fuzzy control QLR in policing mechanism
(that is FLB,FJW and FTJW) is much better
throughput than traditional policing mechanism (LB,
JW, TJW). Throughput is one of QoS to help
guarantee higher reliability of network performance.
In conclusion, the FLB, FJW and FTJW can handle
real time applications such as multimedia traffic.
Figure 6 demonstrates that we can help conserve the
conforming frames by simply reducing number of
dropped frames. The highest number of dropped
frames as shown in this figure is produced by
traditional policing mechanisms (LB,JW and TJW).
A regular network may cause a poor QoS by higher
non-conforming frames. Especially, a quality of
multimedia traffic such as video conference, video
on demand during the online display mode must
guarantee QoS while high dropped frames will
cause unclear pictures and retransmission.
Furthermore It will lead to higher delay time.
In figure 7, the simulation result determines
more utilization of fuzzy control prior queue length
and depleting rate in policing mechanisms compared
to traditional policing mechanisms with burst/silence
ratio of 100:100. The increment of utilization factor
does not seem to be relevant to the performance
improvement. The higher utilization may cause
approach of a bottleneck situation which can boggle
down the system. In fact the 78% in FLB, FJW and
FTJW will not affect the situation of bottleneck.
Positively this factor will rather improve the cost
effectiveness of the VDSL devices.
Figure 8 and 9 show that all fuzzy control prior
queue length and depleting rate in policing
Arrival rate
(Mbps)
Max Queue Length
(MQL in frames)
QLR
(Mbps)
1- 5 9 6
6-9 15 10
11-12 23 13
13-35 105 14
ICETE 2005 - SECURITY AND RELIABILITY IN INFORMATION SYSTEMS AND NETWORKS
360

mechanisms, all frames have to wait longer in the
buffer next to the entrance of VDSL network. The
consequence of long waiting hour is compatible to
results shown in figure 8and 9. We can observe
many more frames in average reside in the queue
prior to the entrance of VDSL network. This is trade
off fuzzy control policing mechanism. We can help
ease this congestion by increasing the data rate in
VDSL network to be higher.
6 CONCLUSIONS AND
RECOMMENDATIONS FOR
FUTURE RESEARCH
In this paper, we carried out a comprehensive study
to investigate the performance of three selected
traditional policing mechanisms; namely LB, JW,
TJW and fuzzy control QLR in policing mechanism;
namely FLB, FJW, FTJW with fixed bursty/silence
sources. This study was conducted through
simulation for which a model was developed.
We found from simulation result in general that
the fuzzy control QLR in policing mechanisms are
better than traditional policing mechanisms with
fixed bursty/silence sources. The fuzzy control QLR
in policing mechanisms will also help ease the
tremendous amount of traffic fluctuations into the
VDSL network and prevent the network from
nonconforming frames with 58% reduction of traffic
load as shown in figure 9. Fuzzy control QLR in
mechanisms can guarantee that they are better than
traditional policing mechanisms.
In the future work, we will focus on the
investigation of a network of queue (NoQ) for
central pool prior to the VDSL network.
0
500
1000
1500
2000
Conform
Frame (fram
e
)
FLB LB FJW JW FTJW TJ
W
Figure 5 illustrates the conforming frames by comparison
between FLB, LB, FJW, JW, FTJW and TJW at burst :
silence = 100:100.
0
500
1000
1500
2000
Non-confor
m
Frame (fram
e
)
FLB LB FJW JW FTJW TJ
W
Figure 6 illustrates the non-conforming frames by
comparison between FLB, LB, FJW, JW, FTJW and TJW
at burst : silence = 100:100.
0
0
.
5
1
Utiliza
FLB LB FJW JW FTJW TJ
W
Figure 7 illustrates the utilization by comparison between
FLB, LB, FJW,JW, FTJW and TJW at burst : silence =
100:100.
0
5
10
Mean qu
e
length ( fram
e
)
FLB LB FJW JW FTJW TJ
W
Figure 8 illustrates the mean queue length by comparison
between FLB, LB, FJW, JW, FTJW and TJW at burst :
silence = 100:100.
0
500
1000
1500
2000
Mean queue time (Micr os
e
.
)
FLB LB FJW JW FTJW TJ
W
Figure 9 illustrates the mean time in queue comparison
between FLB, LB, FJW, JW, FTJW and JW at burst :
silence = 100:100
SCHEDULING AND QOS FOR LEAK RATE IN POLICING MECHANISMS OVER TELECOMMUNICATIONS
NETWORK
361

REFERENCES
S. Lekcharoen et. al, “Performance Evaluation of VDSL
Network with Fuzzy Control Policing Mechanisms”,
Proceeding of International Conference on
Telecommunications and Computer Networks
(TCN’04), 2004, pp. 56-60.
P. Pakdeepinit et. al, “Performance Comparison of ATM
Policy Mechanisms with Telecommunications
Traffic", Proceeding of The 6th World
Multiconference on Systematics, Cybernetics and
Informatics, 2002, pp. 373-378.
Y. W. Chen, "Study on the prevention of SYN flooding by
using traffic policing", NOMS 2000 - IEEE/IFIP
Network Operations and Management Symposium,
no. 1, 2000, pp. 593-604.
Rose Qingyang Hu and David W. Peter, “A Predictive
Self-Tuning Fuzzy-Logic Feedback Rate Controller”,
IEEE/ACM transactions on networking, 2000, pp.
697-709.
Ruy de Oliveira and Torsten Braun, "A delay-based
approach using fuzzy logic to improve TCP error
detection in ad hoc networks", WCNC 2004 - IEEE
Wireless Communications and Networking
Conference, vol. 5, no. 1, 2004.
You-Chang Ko, Sun-Chun Park, Chong-Youn Chun,
Hyong-Woo Lee, Choong-Ho Cho, "An adaptive QoS
provisioning distributed call admission control using
fuzzy logic control", ICC 2001 - IEEE International
Conference on Communications, no. 1, 2001.,
pp. 356-360.
www.dlink.pl/docs/datenblatt/DEV3001_datasheet_en.pdf
www.etsi.org.
ICETE 2005 - SECURITY AND RELIABILITY IN INFORMATION SYSTEMS AND NETWORKS
362
