
ON THE EVALUATION OF A SECURE SOLUTION TO ACCESS
802.11 NETWORKS
Fernando da Costa Junior, Luciano Gaspary, Jorge Barbosa,
Gerson Cavalheiro, Luciano Pfitscher
Universidade do Vale do Rio dos Sinos
Programa Interdisciplinar de P
´
os-Graduac¸
˜
ao em Computac¸
˜
ao Aplicada
Av. Unisinos, 950 – 93.022-000 – S
˜
ao Leopoldo, Brazil
Jos
´
e Dirceu G. Ramos
Hewlett Packard do Brasil
Keywords:
WiFi networks, data reception rate, PDA energy consumption, IPSec.
Abstract:
Despite offering the possibility to develop and distribute a new set of applications to its users, the widespread
and unrestricted use of mobile computing depends on the provisioning of a secure network environment. Re-
garding the communication established from mobile devices such as PDAs (Personal Digital Assistants), one
of the most currently used standards is the IEEE 802.11b, which presents known security flaws. To overcome
them, some alternative setups are commonly deployed, based on link, network, transport or application-layer.
In this paper we evaluate the impact on data reception rate and energy consumption of IPSec-based PDAs
access to 802.11b (WiFi) wireless LANs. As a result of this work we identify the overhead imposed by the
security mechanisms and the capacity of the device to run CPU and network-intensive applications.
1 INTRODUCTION
1
The miniaturization of electronic components and the
growing offer of wireless communication technolo-
gies have stimulated the development of small and
high capacity computational devices, which enable
the concrete implementation of the mobile computing
concept. In a mobile context it is common to have
portable devices such as PDAs interconnected to the
wired network infrastructure through wireless links.
The easiness of connection and physical mobility of
these devices leads to the possibility of providing the
users of this technology with a new set of applications
(e.g. location-aware and video on demand). How-
ever, in order to execute these applications in a pro-
duction environment some security issues need to be
addressed.
One of the most currently used standards to allow
network connectivity from mobile devices is the IEEE
802.11b, which has several security flaws (Cam-
Winget et al., 2003). In order to overcome them, some
alternative security setups, ranging from link to appli-
cation layer, have been widely deployed in production
environments (e.g. IPSec and SSL). These additional
components are essential to enable the secure commu-
nication of millions of devices using IEEE 802.11b
1
This work was partially developed in collaboration
with HP Brazil R&D.
that have already been sold, and cannot be replaced
by other equipment without extra investments.
Regardless of the security mechanism used, it leads
to an overhead in terms of both the data sent/reception
rates achieved by the mobile device and its energy
consumption. Identifying this overhead and determin-
ing which applications can be executed by mobile de-
vices such as PDAs (keeping their autonomy) is valu-
able, because one can adjust security mechanisms to
achieve the best tradeoff between security and con-
sumption.
In this paper we evaluate the impact on data re-
ception rate and energy consumption of IPSec-based
PDAs access to 802.11b wireless LANs. We have
chosen IPSec because it is the most current, widely
adopted setup. Furthermore, since it is a network-
layer technology, all applications can take advantage
of the security mechanisms that it provides: authenti-
cation, privacy, and integrity.
The paper is organized as follows: section 2 de-
scribes some related work. Section 3 presents the
setup configured to achieve a secure wireless network
environment. In sections 4 and 5 we detail the ex-
periments carried out. Section 6 presents some final
considerations.
73
da Costa Junior F., Gaspary L., Barbosa J., Cavalheiro G. and Pfitscher L. (2005).
ON THE EVALUATION OF A SECURE SOLUTION TO ACCESS 802.11 NETWORKS.
In Proceedings of the Second International Conference on e-Business and Telecommunication Networks, pages 74-79
DOI: 10.5220/0001416800740079
Copyright
c
SciTePress
2 RELATED WORK
Measuring and characterizing the current limits of
portable devices in terms of both communication ca-
pabilities and energy consumption, to mention just a
few aspects, are issues that have been gaining atten-
tion recently. This topic grows in importance when
secure wireless communications are demanded. Since
a lot of extra computation is required to guarantee
properties such as authentication, privacy, and in-
tegrity, the feasibility to run a variety of applications
is directly affected.
Potlapally, Ravi, Raghunathan, and Jha present in
(Potlapally et al., 2003) an analysis of the energy con-
sumed by mobile devices when using several com-
binations of security mechanisms in SSL-based ap-
plications. Various cryptography (RSA, DSA, and
ECDSA) and hashing (MD2, MD4, MD5, SHA,
SHA1, and HMAC) algorithms have been used in the
experiments.
Other work related to PDA energy consumption
was published by Karri and Mishra in (Karri and
Mishra, 2003). The authors measure the energy con-
sumed by the device (i) when secure WAP (Wireless
Application Protocol) sessions are established and (ii)
during secured data transfer. An additional contri-
bution of the paper is the proposal of techniques to
reduce energy consumption. By applying techniques
based on information compression, session negotia-
tion protocol optimization, and hardware acceleration
of crypto-mechanisms, the energy consumed for ses-
sion establishment has been reduced by more than 6.5
times, when compared to the normal power consump-
tion. Similarly, the energy for data transmission has
diminished more than 1.5 times.
The overhead introduced by WEP (Wireless Equiv-
alent Privacy) and IPSec protocols in IEEE 802.11b
wireless networks has been measured by Maciel et al.
in (Maciel et al., 2003). The data throughput achieved
by desktop computers (with wireless cards attached
to them) has been calculated under two different con-
figurations: employing (i) solely WEP and (ii) both
WEP and IPSec. This comparison is of little practi-
cal utility, however. WEP becomes unnecessary when
IPSec is used, because besides being vulnerable, the
first leads to an undesired additional overhead.
In this paper we measure the data reception rate and
the energy consumed by a Personal Digital Assistant
with and without the employment of IPSec protocol.
We identify the type of applications that can be ef-
ficiently executed by the portable device even when
security mechanisms are employed. We also charac-
terize how much these mechanisms impact the auton-
omy of the PDA.
3 A SECURE WIRELESS LOCAL
AREA NETWORK SETUP
There are several approaches that can be applied to
secure current IEEE 802.11b wireless networks with
no extra investments in hardware: IPSec (IP Secu-
rity) (Kent and Atkinson, 2004), CIPE (Crypto IP En-
capsulation) (cip, 2004), and VTUN (Virtual Tunnel)
(vtu, 2004) at the network-layer; SSL (Secure Socket
Layer) (Freier et al., 1996) at the transport-layer;
SET (Secure Electronic Transaction) (set, 2004), and
OpenVPN (ope, 2004) at the application layer.
CIPE, VTUN, and OpenVPN are not supported
by mobile device operating systems such as PalmOS
and PocketPC 2003. SSL and IPSec are by far the
most deployed schemes. The former is used to pro-
vide application-specific end-to-end encrypted trans-
fers. The latter, on the other hand, offers a general
purpose cryptographic tunnel capable of providing se-
cured communication to any application running on
the PDA. Due to this generality, we have chosen to
use IPSec in our experiments.
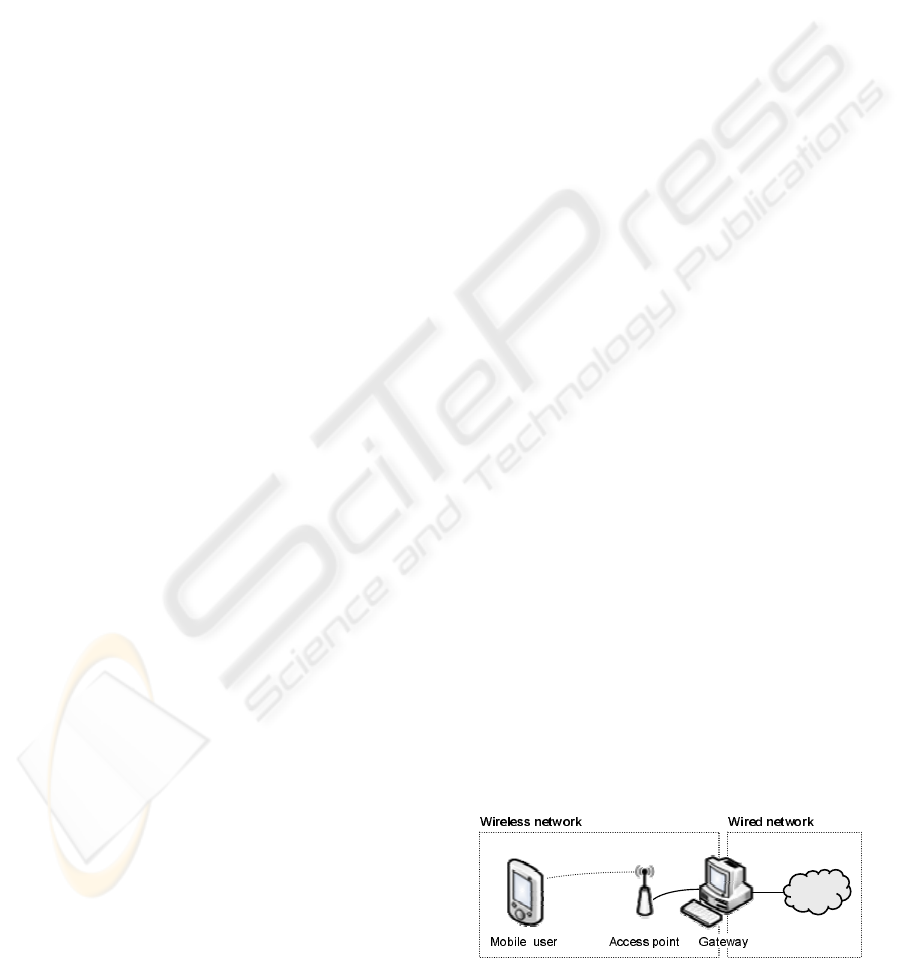
The setup is composed of a L2TP (Layer 2 Tun-
neling Protocol) (Townsley et al., 1999) and an IPSec
server (FreeS/WAN (fre, 2004)) running on the gate-
way (figure 1). L2TP/IPsec is one the mechanisms
that can be used by Pocket PC 2003 to acquire a
virtual IP address from the internal network. This
scheme has been chosen because (i) it is used by
Pocket PC 2003’s built-in VPN client (which is free!)
and (ii) it is an official IETF standard.
We have configured the IPSec server to run in tun-
nel mode, i.e. both the header and the payload of
packets sent/received by the PDA to/from the gateway
are encrypted. Although this is a very conservative
setup, it has been used so that worst case measure-
ments could be made.
The authentication process used was PSK (Pre-
shared Key). A Pre-shared Key is a secret pass-
word that is shared by both sides of the IPSec tun-
nel. Preferably, the PSK is distributed through “out-
of-band” medium, such as phone call, paper, face to
face, and should not be transmitted over public net-
works.
Figure 1: IPSec-based PDAs access to 802.11b wireless
LANs
ICETE 2005 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
74

4 EXPERIMENTAL SETUP
Mobile devices face problems on battery working
time and packet processing, which get critical when
CPU and network-intensive applications are executed.
Due to these restrictions, it is important to figure out
the impact of the security mechanisms intended to be
used in the wireless network infrastructure (the idea
is to avoid imposing many extra limitations to the use
of the device). To better understand the relation be-
tween data reception rate and energy consumption un-
der different scenarios, we have carried out some ex-
periments (described henceforth).
4.1 Testing Environment
The setup of the experiments was composed of a
client and a server (gateway). The client was an iPAQ
5550 with a 400MHz Xscale processor 128MB RAM,
running Pocket PC 2003 operating system. The gate-
way was an Intel Celeron 500MHz 128MB RAM. In
order to provide support for IPSec in the gateway,
we have installed the following software: Debian
Linux, kernel 2.6 (ker, 2004) (with native support for
IPSec), FreeS/WAN
2
, and L2TP. The communication
between the client and the gateway was done through
a Linksys WAP11 access point (IEEE 802.11b), lo-
cated around 15 meters far from the client.
The energy consumed by the mobile device during
the data transmissions has been measured through the
battery output voltage and the electric current data,
which were acquired with an oscilloscope. The circuit
implemented for acquiring these signals is showed
in figure 2. The oscilloscope used was an Agilent
54622D MegaZoom, 100MHz, 200MSa/s. To mon-
itor the electric current, a shunt resistor of 0.1Ω has
been applied.
Figure 2: Circuit for measuring the energy consumed by the
mobile device
The determination of the energy consumed (W) has
2
FreeS/WAN had to be patched to support NAT-T (Tra-
versal NAT for UDP packets).
been obtained by the integration of the voltage x elec-
tric current, and can be expressed by the following
equation: W =
v.i.dt(Joule).
4.2 Experiments
We have carried out three experiments in order to ver-
ify the impact of IPSec on the mobile device. Each
experiment has been repeated five times to calculate
the average and the standard deviation. To execute
them we have developed two applications. The first,
running on the gateway, was responsible to send UDP
packets to the mobile device. The second, running on
the PDA, was responsible to analyze the number of
received UDP packets so that we could measure the
reception rate in Mbps.
The first experiment assessed the maximum recep-
tion rate achieved by the mobile device (using IPSec).
In this test we analyzed the data flow with no speed
control during a 180-second period. We have used
different PDU sizes: 256, 512, and 1024 bytes. 3DES
and SHA1 algorithms have been applied, respectively,
for encryption and integrity checking.
The second experiment aimed at measuring energy
consumption and packet reception rate in controlled
speed UDP stream transmissions. We have divided it
in two groups: low speed (56, 128, and 256Kbps) and
high speed stream transmissions (1, 2, 4, and 8Mbps).
In low speed tests each transmission lasted 8 minutes
(for better accuracy), while in high speed tests they
ran for 3 minutes. For all these tests 1024-byte PDUs
have been used. Again, IPSec traffic has been en-
crypted using 3DES and SHA1.
In order to get a more refined view on energy con-
sumption and packet reception rate we have repeated
the previous UDP stream transmission at 2Mbps us-
ing several PDU sizes (256, 512, 1024, and 2048
bytes).
In the third experiment we have evaluated the im-
pact of using some combinations of encryption and
hashing algorithms on the PDA energy consumption.
We transmitted 1024-byte UDP packets at 2Mbps
from the gateway to the PDA, using DES and 3DES
cryptographic algorithms combined with SHA1 and
MD5 integrity algorithms.
5 RESULTS
Figure 3 shows the maximum UDP stream reception
rate achieved by the mobile device. From the graph
one can observe that although the nominal capacity of
WiFi wireless LANs is 11Mbps, the maximum recep-
tion rate achieved by the PDA was 3,109Mbps (using
1024-byte PDUs). This low rate is due to the mobile
device limited CPU, which is not able to process so
ON THE EVALUATION OF A SECURE SOLUTION TO ACCESS 802.11 NETWORKS
75

PDU Without VPN With VPN
Pkts rcvd Pkts rcvd
256 107.644 78.762
512 93.756 61.820
1024 71.633 47890
PDU Without VPN With VPN
Avg Std Dev Avg Std Dev
256 1,168 0,039 0,855 0,004
512 2,035 0,013 1,342 0,048
1024 3,109 0,066 2,079 0,012
Figure 3: Maximum reception rate achieved by the mobile
device
many packets in a short time period. As expected, the
PDU size affects directly the reception rate regard-
less of whether IPSec is used or not. However, the
use of IPSec always cause the reception rate to de-
crease compared to the non-encrypted transmission:
27% with 256-byte PDUs, 34% with 512-byte PDUs,
and 33% with 1024-byte PDUs.
In the second experiment two aspects have been
analyzed: successful packet reception rate and en-
ergy consumption overhead
3
. As already mentioned
in section 4.2, this experiment has been divided in
two groups: high speed and low speed stream trans-
missions. The packet reception rate for the low speed
data stream transmissions was almost 100%. This was
expected, since in the previous experiment we have
shown the PDA is able to cope with the 3,109Mbps
reception rate.
Figure 4 shows the energy overhead consumed by
the mobile device to receive low speed UDP streams.
The consumption is directly affected by the transmis-
sion speed (the higher the speed, the higher the num-
ber of packets to be processed). It is worth observing
in the graph how much the use of IPSec affects energy
consumption in each transmission rate. The overhead
of using IPSec at 56kbps is 18%. This difference gets
bigger as the transmission rate increases, achieving
47% for 256kbps. Taking into account the total bat-
3
The overhead has been calculated by decreasing the
PDA absolute energy consumption value after a fixed period
data transmission from the energy consumed by the device
during an equivalent time period when it was idle.
Speed Without VPN With VPN
Avg Std Dev Avg Std Dev
56 10,200 23,091 12,500 12,261
128 17,000 2,646 25,000 9,899
256 20,500 2,121 29,000 11,314
Figure 4: Mobile device energy consumption overhead to
receive low speed UDP streams
tery energy is 13.72KJ (measured prior to the experi-
ments), the consumption of 25J to receive a 8-minute
UDP stream at 128Kbps using 1024-byte packets cor-
responds to 0,001% of the battery capacity.
For the high speed data stream transmissions it is
valuable to illustrate two graphs: successful packet re-
ception rate (figure 5) and energy consumption over-
head (figure 6). The first shows the number of UDP
packets received and processed by the mobile device
in relation to the number of packets transmitted by the
gateway under different speeds (from 1 to 8Mbps).
From the graph one can infer that 2Mbps is the max-
imum reception rate the PDA using IPSec is able to
handle with less than 20% of packet loss. When VPN
is not used this rate grows up to 4Mbps. Above these
rates the PDA receives less than 60% of the packets,
which is not acceptable for applications such as video
streaming.
The second graph (figure 6) shows the energy over-
head consumed by the mobile device to receive high
speed data stream transmissions. Since its maximum
reception rate is 3.109Mbps (figure 3), the energy
consumption reaches the maximum value between 2
and 4Mbps (around 90J). The PDA consumes 37%
more energy when IPSec is used to transmit/receive
streams at 1Mbps, and 64% at 2Mbps. At 4Mbps and
8Mbps the energy consumed does not grow propor-
tionally, because the number of packets received and
processed is similar to what happens at 2 Mbps (figure
5); most of the packets are lost in these rates.
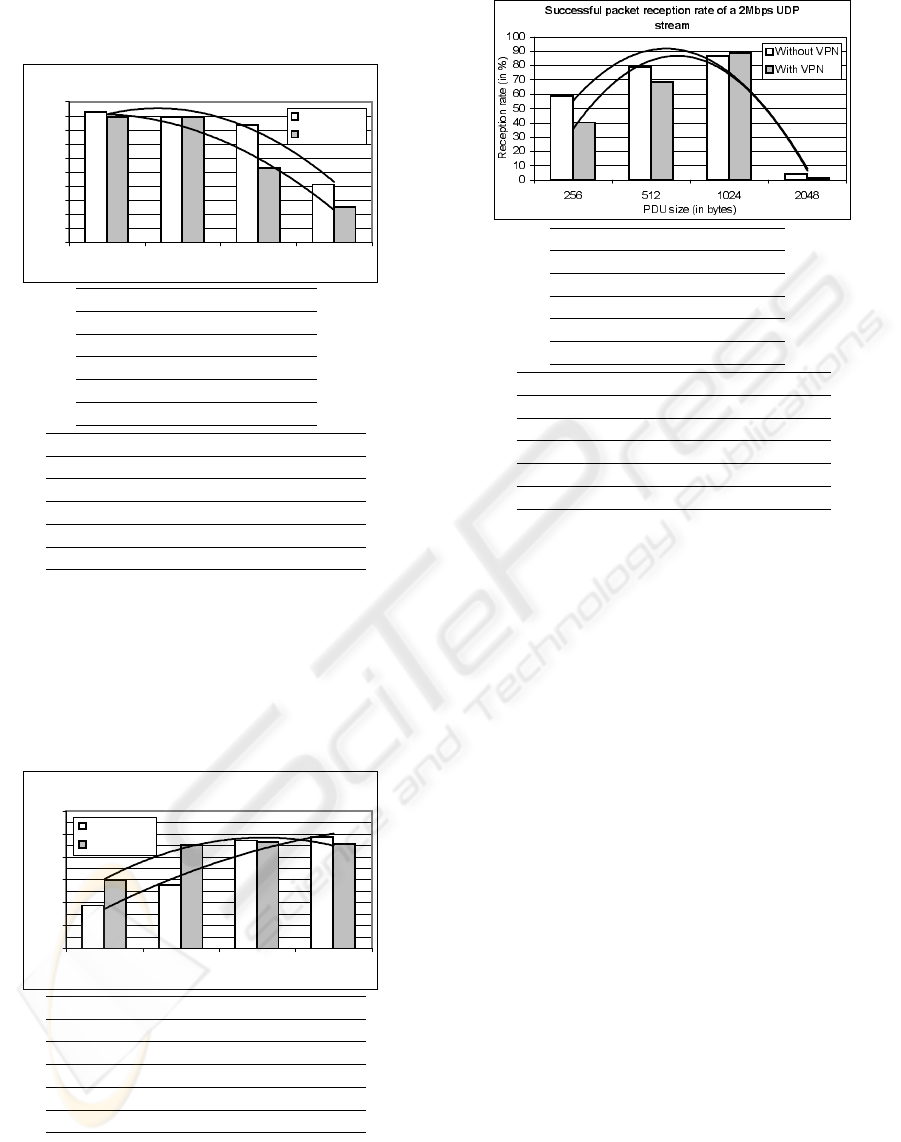
Figures 7 and 8 illustrate a zoomed view of the
mobile device successful packet reception rate and
energy consumption overhead when UDP streams at
2Mbps are transmitted to it. As one can notice in fig-
ure 7, the reception rate increases as larger packets
are used (up to 1024 bytes). When 2048-byte long
packets are transmitted by the gateway, they are frag-
ICETE 2005 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
76
Successful packet reception rates of high speed UDP
streams
0
10
20
30
40
50
60
70
80
90
100
1248
Speed (in Mbps)
Reception rate (in %)
Without VPN
With VPN
Speed Without VPN With VPN
Pkts rcvd Pkts rcvd
1 20.864 19.975
2 39.990 39.995
4 75.203 47.834
8 73.885 45.125
Speed Without VPN With VPN
Avg Std Dev Avg Std Dev
1 92,729 9,793 88,778 0,050
2 88,867 0,031 88,878 0,003
4 83,558 0,034 53,148 0,276
8 41,047 0,192 25,069 0,004
Figure 5: Mobile device successful packet reception rates
of high speed UDP streams
Energy overhead consumed by the mobile device to
receive high speed UDP streams
0
20
40
60
80
100
120
1248
Speed (in Mbps)
Consumption (in Joules)
Without VPN
With VPN
Speed Without VPN With VPN
Avg Std Dev Avg Std Dev
1 37,333 4,243 59,333 0,000
2 55,083 5,620 90,333 0,000
4 94,333 8,185 93,333 0,000
8 97,333 2,828 90,833 0,707
Figure 6: Mobile device energy consumption overhead to
receive high speed UDP streams
PDU Without VPN With VPN
Pkts rcvd Pkts rcvd
256 106.273 72.514
512 71.167 61.748
1024 39.058 39.983
2048 867 324
PDU Without VPN With VPN
Avg Std Dev Avg Std Dev
256 59,041 8,630 40,285 5,452
512 79,074 1,758 68,609 2,377
1024 86,796 0,566 88,850 0,024
2048 3,851 0,651 1,440 0,314
Figure 7: Packet reception rate of a 2Mbps UDP stream
using different PDU sizes
mented and the mobile device reception rate drops un-
expectedly to less than 10%. This is a good indicative
that network intensive applications such as streaming
video should be tuned to use the largest packet size
that can be sent without fragmentation.
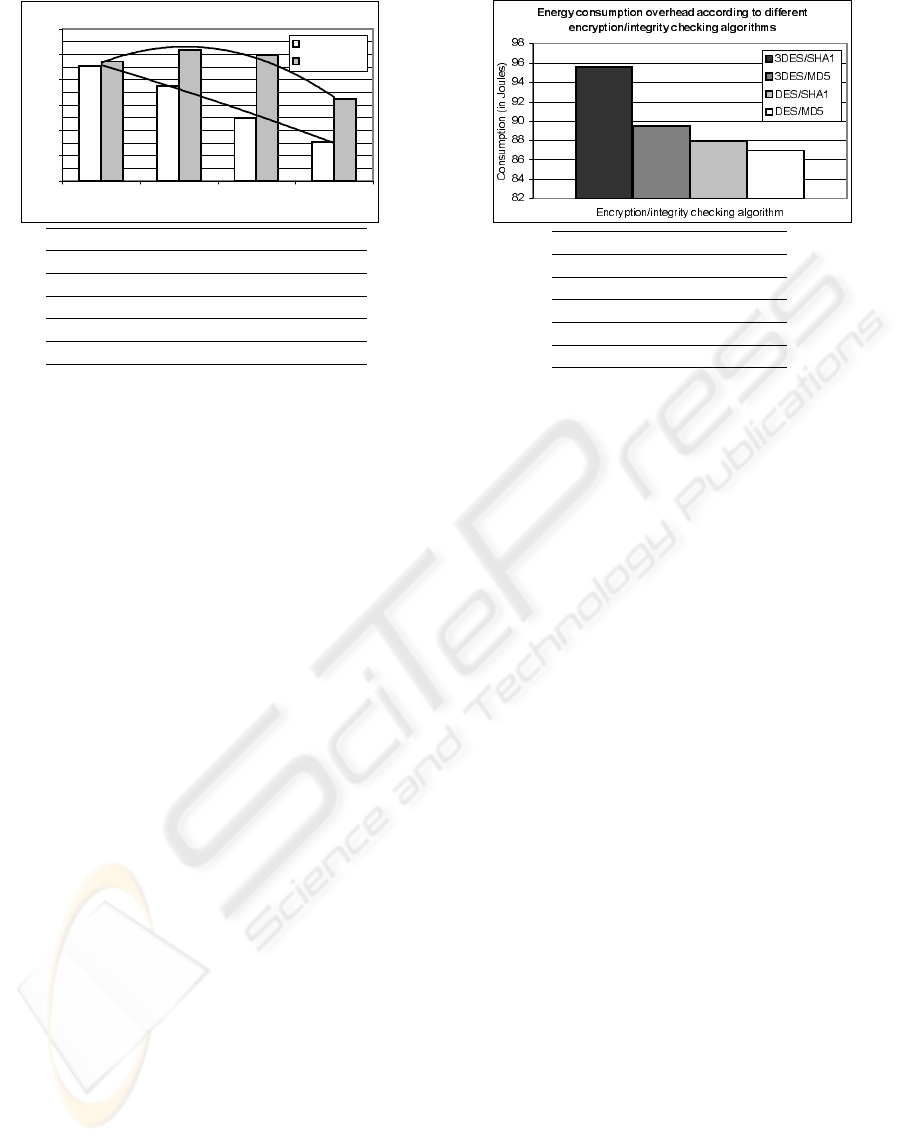
The energy overhead consumed by the mobile de-
vice to receive a 2Mbps UDP stream is shown in fig-
ure 8. The use of IPSec imposes a considerable over-
head in the energy consumption compared to the non-
encrypted transmissions: 3,72% for 256 byte packets,
27,67% for 512 byte packets, 50,22% for 1024 byte
packets, and 53,12% for 2048 byte packets. Regard-
ing the consumption associated with the first three
transmissions, they are almost equivalent. This is ex-
plained in figure 7, where one may notice the packet
reception rates increase as less, larger packets are
transmitted by the gateway. When 256 byte PDUs
were used, 72.514 packets have been received and
processed by the PDA. On the other hand, only 39.983
packets have been received when 1024 byte PDU
were transmitted. A lot of the consumption in the first
case is related to header protection. Therefore, the
best tradeoff between successful reception rate and
energy consumption is reached when 1024-byte long
packets are used.
Figure 9 shows the results of the third experiment,
where we have assessed the impact of using different
encryption (DES and 3DES) and integrity checking
(MD5 and SHA1) algorithms on the PDA energy con-
ON THE EVALUATION OF A SECURE SOLUTION TO ACCESS 802.11 NETWORKS
77
Energy consumption overhead of a 2Mbps UDP stream
0
20
40
60
80
100
120
256 512 1024 2048
PDU size (in bytes)
Consumption (in Joules)
Without VPN
With VPN
PDU Without VPN With VPN
Avg Std Dev Avg Std Dev
256 90,494 12,021 93,994 8,485
512 74,494 0,707 102,994 1,414
1024 49,494 0,707 99,438 0,707
2048 30,438 2,121 64,938 1,414
Figure 8: Energy consumption overhead to receive a 2Mbps
UDP stream
sumption. As depicted in the graph, the combination
3DES/SHA1 is the most computational intensive. It
is explained by the higher complexity of both algo-
rithms compared to DES/MD5 (Stallings, 2002).
6 CONCLUSIONS
In this paper several approaches to solve some of the
existing flaws in 802.11b networks have been com-
mented. Then we have described the IPSec-based
setup and the testing environment. The experiments
carried out aimed at assessing the impact on data re-
ception rate and energy consumption of IPSec-based
PDAs access to 802.11b wireless LANs.
From the results obtained, it is important to high-
light the maximum reception rate achieved by the mo-
bile device is less than 50% of the nominal capac-
ity (it gets worse when IPSec is used). The PDA
energy consumption increases considerably when the
security mechanisms are employed. It is also worth
mentioning that the mobile device does not cope well
with fragmentation. Depending on the number and
size of the UDP packets it is not able to process
more than 50% of them. Finally, we found out
3DES/SHA1, which are the the most common used
encryption/integrity checking algorithms, are the ones
that consume more. In a mobile computing envi-
ronment, where maximizing the battery working time
is highly desirable, DES/MD5 could alternatively be
used.
Algorithms Consumption
Average Std Dev
3DES/SHA1 95,605 6,658
3DES/MD5 89,438 2,121
DES/SHA1 87,938 0,000
DES/MD5 86,938 1,414
Figure 9: Energy consumption using different encryp-
tion/integrity checking algorithms
REFERENCES
(2004). Crypto ip encapsulation. http://www.extra300.nl.
(2004). Linux frees/wan. http://www.freeswan.org.
(2004). Linux kernel archives. http://www.kernel.org/.
(2004). Openvpn. http://openvpn.sourceforge.net.
(2004). Secure electronic transaction. http://www.setco.org.
(2004). Virtual tunnels over tcp/ip networks.
http://vtun.sourceforge.net.
Cam-Winget, N., Housley, R., Wagner, D., and Walker, J.
(2003). Security flaws in 802.11 data link protocols.
In Communications of the ACM.
Freier, A. O., Karlton, P., and Kocher, P. C. (1996). The ssl
protocol version 3.0. In IETF Internet Draft.
Karri, R. and Mishra, P. (2003). Optimizing the energy con-
sumed by secure wireless sessions: Wireless transport
layer security case study. In Mobile Networks and Ap-
plications.
Kent, S. and Atkinson, R. (2004). Security architecture for
the internet protocol. In IETF RFC 2401.
Maciel, P., Nunes, B., Campos, C., and Moraes, L. (2003).
Sobrecarga introduzida nas redes 802.11 pelos mecan-
ismos de segurana wep e vpn/ipsec. In 3rd Brazilian
Workshop on Security of Computing Systems.
Potlapally, N., Ravi, S., Raghunathan, A., and Jha, N.
(2003). Analyzing the energy consumption of security
protocols. In Dept. of Electrical Engineering, Prince-
ton University.
Stallings, W. (2002). Network Security Essentials. Prentice
Hall.
Townsley, W., Valencia, A., Rubens, A., Pall, G., Zorn, G.,
and Palter, B. (1999). Layer two tunneling protocol
l2tp. In IETF RFC 2661.
ICETE 2005 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
78
