
AUCTION BASED SYSTEM FOR ELECTRONIC COMMERCE
TRANSACTION
A. R. Dani
+
, V. P. Gulati
+
+ Institute for Development and Research in Banking Technology, Hyderabad, India
Arun K. Pujari*
* Department of Computer Science, University of Hyderabad, Hyderabad, India
Keywords: Forward auctions, reverse auctions, assignment constraints, capacity
constraints
Abstract: Auctions provide efficient price discovery mechanism for sellers. Auctions are being used for sale of variety
of objects. In last few years auction based protocols are widely used in electronic commerce. Auction based
systems have been developed for electronic procurement. In this paper we propose system for electronic
commerce transactions, which can support electronic procurement as well as help enterprises to sale items.
We also consider assignment constraints those may be required in different commercial transactions. In this
paper we consider forward and reverse auctions. We formulate the problem as mixed integer programming
problem. Then we propose an algorithm to obtain optimum solution and compute pay-off.
1 INTRODUCTION
An auction is basically a bidding mechanism which
is describ
ed by set of rules. These rules specify how
the winner is determined, from the set of competing
bids and how much winner has to pay. Auctions
have been in use for many years. They are used for
sale of variety of objects. These objects range from
bonds of public utilities to perishable items like
flowers. Governments of different countries use
auction mechanism to sale long-term securities and
treasury bonds, to raise funds to meet the borrowing
needs of government. Similar mechanisms are used
by public sector utilities to sale their bonds and raise
money. The process of procurement using
competitive bidding is another form of auction. In
this case the bidders compete for right to sell their
products or services. The private and state owned
enterprises use different types of bidding
mechanisms for procurement of variety of products
like computer stationery and this practice is fairly
wide spread.
It is also being used to dispose of waste and
scrap m
aterials
. The rights to use material resources
from public property such as mining rights, off-
shore oil leases, have been sold by means of
auctions in different countries. Communication
companies use to similar mechanisms for bandwidth
allocation. In real life large number of transactions
are carried out using different types of auction
mechanisms. Auctions are helpful to seller, as they
help them to avoid the risk of determining the price
of an object. Auctions provide mechanism, where
the price is determined by others rather than seller
himself. However seller can decide whether to
accept the bids received. Auctions are used mainly
for following three reasons
• Au
ction helps in obtaining/revealing information
abou
t buyer’s valuations
• Actions are also helpful dishonest dealing between
bu
yers and sellers
• They provide Speed of sale
Trad
itionally auctions like ascending price or
Engli
sh, descending price or Dutch, or Sealed bid
auctions were earlier used in different economic
transactions. Emergence of Internet based electronic
markets in last years has contributed significantly to
growth of different types of auction transactions.
This has resulted in significant increase in number of
transactions that are being carried out using different
types of auction mechanisms on Internet. Present
day electronic auctions support novel applications
like electronic procurement, bidding on air ticket etc.
Different companies use electronic bidding to get
market determined prices of their goods. Internet
based auction companies such as ebay, ubid carry
16
R. Dani A., P. Gulati V. and K. Pujari A. (2005).
AUCTION BASED SYSTEM FOR ELECTRONIC COMMERCE TRANSACTION.
In Proceedings of the Seventh International Conference on Enterprise Information Systems, pages 16-23
DOI: 10.5220/0002529800160023
Copyright
c
SciTePress

out large number of auctions. Internet based auction
companies have implemented many different types
of auction mechanisms, apart from traditional
auctions like English, Dutch, Sealed Bid. Auction
based protocols have been widely used in electronic
commerce. Auction mechanisms are widely used in
electronic commerce for carrying out negotiations.
One of the most important use of this mechanism
is to facilitate the transfer of assets from public to
private hands. This has been a common phenomenon
in different countries in last two decades as a result
of economic liberalization. Governments in
countries like Britain and Scandinavia have uses
auctions to privatize transportation systems. In
former Soviet Union and Easter Europe countries
auctions have been used to sale public owned
industrial enterprises. Auctions are being used for
many years to acquire rights of use of natural
resources. Such types of auctions, where
government grants access rights to use natural
resources or transfers the ownership of its
enterprises can be considered as examples of
forward and reverse auctions. When government is
transferring public owned enterprise, it may be
interested in seeing that ownership is distributed
appropriately and no one person or enterprise gets
ownership beyond certain percentage.
While granting access to natural resource it may
be interested to see that no one person or private
enterprise acquires complete control. This can give
rise to different types of constraints, while
determining the winner. In this paper we consider a
scenario of forward and reverse auctions under
constraints. The main contribution of this paper is
the development of algorithm which can minimize
procurement cost for enterprises as well as maximize
the cost selling. Then design of system for electronic
procurement and selling has been presented. Our
algorithm also takes into account different types of
constraints. We also compute Vickrey-Clake-
Grooves (Vickrey, 1961), (Clarke, 1971) (Gooves,
1973) (VCG) payments for buyers and sellers. This
ensures that our mechanism is strategy proof and
efficient. The rest of the paper is organized as
follows, in section 2, we present an example of the
problem with different types of constraints and
related work. In section 3, we discuss the problem
formulation, design aspect of our system and our
algorithm. In section 4 we discuss experimental
results. In section 5, system implementation is
discussed. We conclude in section 6.
2 RELATED WORK AND
MOTIVATING EXAMPLE
In this paper we consider the problem of single item
multi unit auction problem under different types of
constraints. We basically consider two scenarios. In
first case there is a single seller having quantity q of
an item to sell and there are n buyers. This type of
auction is usually called as forward auction. In the
second case, we consider a scenario, where there is
one buyer and who requires quantity q of certain
item and there are n sellers who can supply these
items. This type of scenario is called as reverse
auction. These types of auction problems have been
studied recently (Kothari, 2003). An approximately-
strategy proof and tractable multi unit auction
mechanism for single good multi unit allocation
problem has been presented in (Kothari, 2003). The
problem has been modeled as generalization of
classical 0/1 knapsack problem and a fully
polynomial time approximation scheme for reverse
and forward auction variations has been presented.
In this formulation capacity constraints, where buyer
or seller can express upper bounds on their
respective requirements are considered.
However in certain cases in addition to capacity
constraints, we can have constraints on number of
items that can be sold to one buyer or which can be
purchased from a single buyer. We consider an
example of Initial Public Offering (IPO) of a
government owned enterprise to illustrate this. In
IPO government invites competitive bids from
different individuals and private enterprises, for
privatization. Suppose that government wishes to
decrease its ownership in an enterprise from 100%
to say 49%. This is done by means of IPO of its
shares, wherein government invites competitive bids
from individuals and others. Even though
individuals or private enterprises may indicate their
capacity or willingness to buy certain number of
shares, it may not be feasible as per policies of
government. The enterprises may be divided in
number of categories and the there can be different
restrictions This scenario has been shown in Table 1.
A government wishes to sale say, one million shares
by means of IPO. Suppose that the bids submitted by
different companies are as given in Table 1.
AUCTION BASED SYSTEM FOR ELECTRONIC COMMERCE TRANSACTION
17
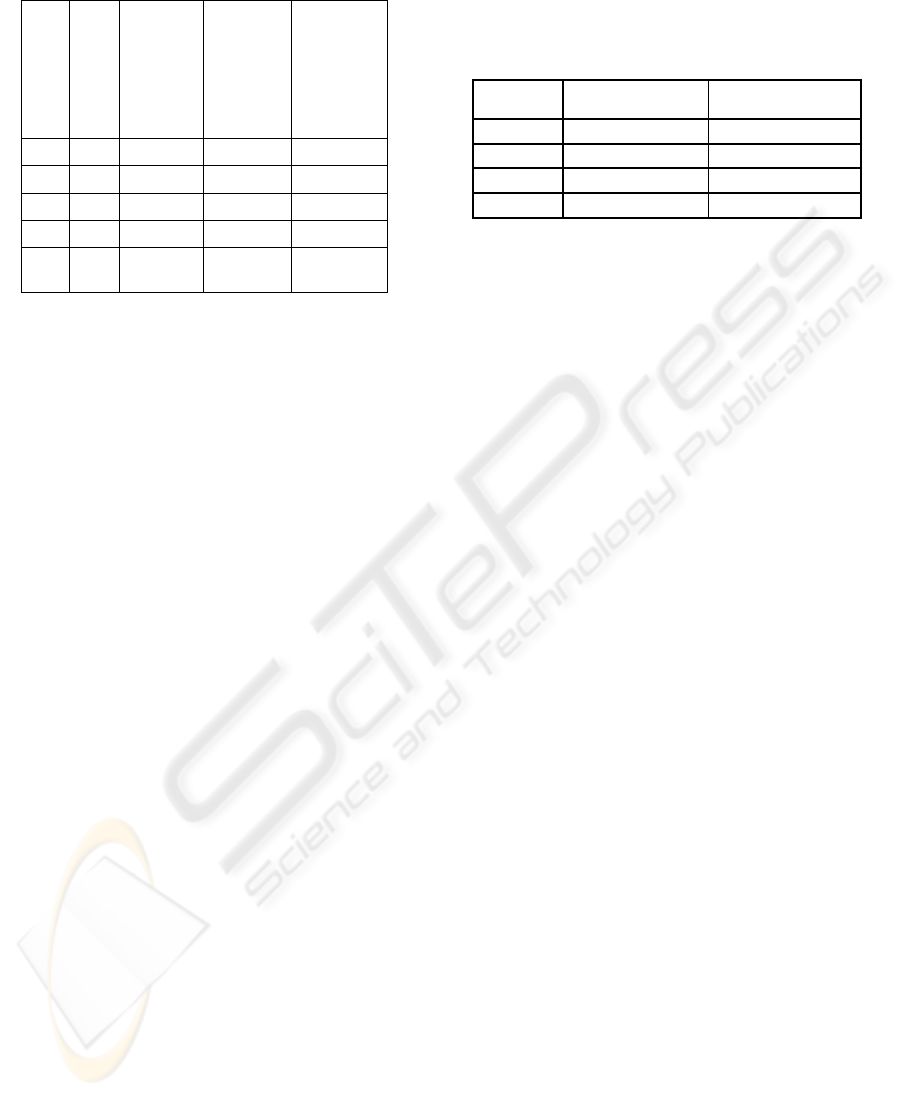
The third and fourth columns show capacity
constraints of different enterprises. The restrictions
as per rules governing IPO, are shown in fifth
column. These restrictions impose certain
constraints. However these constraints are not much
different from usual capacity constraints. This may
result in change upper bounds and lower bounds in
some cases. It can be seen that upper bound on
shares that can be sold to an enterprise, is much
smaller in respect of enterprises 1, 2 and 5 and is
much higher in case of enterprises 3 and 4. So upper
bound on capacity constraints of these enterprises
will differ. However there can be constraints like
total number of shares that can be sold to a particular
group. We illustrate these constraints in next table
in reverse auctions. In reverse auction also there can
be similar constraints e.g. An enterprise has
requirement of 10000 meters of clothes. As per
government policies, it is required to acquire certain
percentage from certain types of sellers (e.g. a small
scale enterprises run by group of women etc.). The
different quotes received by it are given in Table 2.
As per government policy, the enterprise must
acquire half of its requirement for enterprises (1) and
(4), which are small scale enterprises, run by group
of persons from weaker sections of society. It can
acquire remaining requirement from other two
enterprises. These constraints are basically on group
of sellers. Even though each seller has capacity
constraints, the group constraints will apply on a
group of sellers (1,4) and (2,3). These constraints
differ slightly from usual capacity constraints. We
formulate this problem as mixed integer
programming problem, which can handle
assignment constraints indicated above. Then we
present an algorithm, which obtains optimum
solution and then computes pay-off based on VCG
mechanism. A detailed survey of auction
mechanisms can be found in (Wolfstter, 1996). A
multi attribute auction system, for electronic
procurement has been studied in (Bichler, 1999).
Table 1 : Sale of 1 Million shares by IPO
Enter-
prise
Price
Min.
Demand
Max.
Demand
Govt.
restriction as
% of Tot.
No. of
Shares (1
Mn)
1 100 2 Lakhs 5 Lakhs 15%
2 105 5 Lakhs 8 Lakhs 30%
3 110 5 Lakhs 1 Million 30%
4 102 1 Lakhs 1 Million 20%
5 100
10 Thous-
and
1 Lakh 5%
Table 2 : Quotations Received
Enterprise Price ( per Ton) Maximum Supply
1 105 3000
2 101 10000
3 102 6000
4 103 4000
In multi attribute auctions winner determination is
based on more than one attributes unlike in
traditional English or Dutch auctions, where price is
the only attribute. An application of auction theory
in electronic procurement has also been studied in
(Eso, 2001), it also gives near optimal solution to bid
evaluation problem of the buyer. A procurement
process which minimizes the cost using auctions has
been proposed in (Kalgnanam, 2001). Another type
of auction known as Combinatorial Auctions where
seller wishes to sell a combination of goods and
buyers bid on one or more goods, has been studied
recently (Rothkopf, 1998), (Sandholm, 1999).
Double Auctions is another widely used auction
mechanism and has been used in different stock
exchange markets like (National Stock Exchange of
India) and many other stock exchanges worldwide.
It is also widely being used in commodity exchanges
such as (Multi Commodity Stock Exchange of India)
and other similar exchanges. Stocks are homogenous
goods, and buyers do not have preferences over a
designated stock. Apart from this we are not aware
of any work done in developing algorithms to
generate optimum solution in case of constraints or
exploring other approaches to solve the problem
especially in case of forward and reverse auctions.
3 SYSTEM DESCRIPTION AND
PROBLEM FORMULATION
We basically consider two scenarios- A forward
auction, where there is a single seller having
quantity q of an item to sell and there are n buyers,
and a reverse auction, where there is one buyer who
requires quantity q of certain item and there are n
sellers who can supply these items. We first
introduce the relevant concepts. One of the
important features of our system is the algorithm
which obtains the optimum solution i.e. minimum
procurement cost or the highest cost of sale under
different types of assignment constraints. This
ICEIS 2005 - SOFTWARE AGENTS AND INTERNET COMPUTING
18

algorithm always generates the optimum solution
with polynomial time complexity. Another feature of
our implementation is an algorithm, which generates
the pay off for each participant. We compute VCG
pay–off which ensures the properties like efficiency.
It also ensures that truthful bidding is the dominant
strategy.
A bid in the forward auction (an ask in reverse
auction) describes the details of the items, its
quantity and price that the buyer is willing to pay.
Without loss of generality we assume that there are n
buyers (sellers). Additionally buyer (seller) can
describe capacity constraints. A buyer (seller) can
also use the marginal decreasing piecewise bidding
language used in (Kothari, 2003). This allows buyer
to specify the quantity range and price that buyer is
willing to pay as ([10,5),5) instead of single quantity
price pair. It is also an ordered list of attribute
names and values. Let there be a set of n bids, B
1
,
B
2
,…, B
n
. Each B
i
(Ai) is of the following type:
B
i
= ( (at
1
, v
1
), (at
2
, v
2
),…, (at
k
, v
k
)),
where at
j
denotes the j
th
attribute and
v
j
is the value
of the attribute.
The attributes describe different characteristics
of the items. Each attribute assumes the values from
the set of specified domains. For instance, the price
attribute will have values from set of positive real
numbers. The price and quantity are two attributes
of asks and bids. If buyer (seller) uses marginal
decreasing piecewise bidding language, then at
i
can
be a semi closed interval, which is open at one end.
Each buyer (seller) can specify m such intervals and
price pair. In this case we select only one point (on
an interval) for each buyer.
Our system is implemented as a web based
system which can be configured to be implemented
by third party auctioneers as well as enterprises. It
has got a parameterized policy module using which
levels of security, scheduling, type of auctions etc.
can be defined. Three different implementation
levels of security are provided in the system. In the
first level authentication by means of User-Id and
Password is provided. Once the user is successfully
authenticated, it uses Secure Socket Layer (SSL)
protocol for sending any message.
In the second level combination of User-Id,
Password and Public Key Cryptography is provided.
In this level it uses Public Key Infrastructure (PKI)
for implementing security. Each participant (i.e.
buyers, sellers, auctioneers) can optionally have a
key pair. The public key must be deposited with the
specified trusted third party (TTP). In this level use
of public key cryptography is optional. In the third
level the use of public key cryptography is
mandatory. In this case all the participants must
have key pair. In this implementation a bid or ask is
acceptable only if it is digitally signed by the sender
(i.e. buyer, seller or auctioneer). These levels help to
provide different levels of security in the system.
The level of security can be selected depending upon
the value of items. The auctioneer can enforce use
of public key cryptography in case of high value
items.
Another feature of our system is that its design
based on of Event-Condition-Action (ECA) rules.
Specific ECA rules can then be bound to different
events for versatile exception handling. Number of
different types of exceptions and events have been
defined in the system.
Events of different types can occur in this system
occur because of actions of different parties. The
action by buyer of submission of a bid will cause
occurrence of event like “Bid Arrived”. This event
will trigger activity like “Bid Validations”. This
activity will validate the bid. In case the bid is
invalid i.e. some of the attributes of bid violate some
constraints “Invalid Bid” exception will be raised,
sending appropriate notification to sender. In case
bid is valid an event “Bid Accepted” will occur.
There can be two types of events database events
and negotiation events. Events in the system like
“Bid Arrived” will be caused by actions of buyers.
When the event like “Acceptance Closure” occur, it
will automatically trigger of the algorithm to
generate optimum solution.
This system can be configured as sealed bid or
open depending upon the type of auction. In case of
sealed bid option bids (asks) will be submitted in
encrypted format and will be decrypted only after
the auction has closed. In this case it will not be
possible for the buyers (sellers) to see the bids (asks)
submitted by others. The system can also be
configured to accept more than one bid or ask from a
buyer or seller. However sender must specify which
bid or ask is final. If the information is not specified
then the last submitted bid (ask) is treated as final.
The complete cycle of stages in our system is as
follows:
(1) User Registration: The system requires that each
participant must register with system, before it
can be used. The user details are captured in
this phase.
(2) Auction Notification: Once the users are
registered with the system they can notify the
auction. The details of auctions like item
description, type, security level required etc. are
submitted by the users to the system. This
indicates the start of auction. An auction can be
initiated by a buyer or a seller. Optionally it is
also possible to submit the reservation price.
(3) Bid/Ask Submission: Once the auction is
notified the bids and asks can be submitted by
the registered users. At this time price and
quantity details are required to be submitted. In
AUCTION BASED SYSTEM FOR ELECTRONIC COMMERCE TRANSACTION
19
some cases asks and bids are required to be
digitally signed by the sender. Multiple asks and
bids can be submitted by any buyer or seller,
however only one of these bids or asks will be
considered. It can be the last submitted bid/ask
or any one of the submitted as indicated by the
buyer.
(4) Closure: The bids and asks can be accepted for
only fixed period of time. After this period asks
or bids cannot be accepted. At the end of
closing period the auction is cleared.
(5) Clearing and Pay-off: Once the acceptance of
bids (asks) is closed, the optimization problem
is constructed from the received bids and asks.
Then the optimum solution is obtained. After
finding out optimal solution, system generates
the pay-off of each buyer and seller.
(6) Notification: After generation of optimum
solution, VCG pay-off for each buyer and seller
is generated. In this phase each buyer and seller
is notified about the result of auction and his
pay-off.
At present the system is not linked with banking
system to execute payments. In the next phase it will
be linked with banking system, so that payments can
also be effected automatically. In the following
paras we describe and state our algorithm for finding
optimum solution.
Our algorithm is based on branch and bound
method. At each stage it finds out maximum
possible improvement. At any given price,
maximum improvement is possible only by selecting
maximum quantity that can be available at that price.
Our algorithm is based on this and works as follows:
(1) We start with the highest (lowest) available
price.
(2) Determine the maximum quantity that is
available at that price after taking into account
all the constraints. If there are two bids (asks)
with same price then we combine them.
(3) Save the value of buyer’s (seller’s) contribution
in separate table.
(4) Repeat above two steps till requirement is
completely fulfilled.
(5) Then determine VCG Payoff for each buyer
(seller).
Let A be the list of asks and B be the list of bids.
The algorithms are as follows:
Algorithm (1) forwauct /* Main Algorithm */
1. Sort all bids on descending order of price within
same price sort on descending order of quantity
2. While (there is an unmarked bid or unfulfilled
demand) repeat steps 3thru 7
3. Find out maximum quantity available for price
p
i
after capacity constraints on buyers
and other
constraints
4. Calculate and save the buyer’s contribution
5. Calculate the value of objective function
6. Mark the bid
7. Add quantity to demand_fulfilled
Algorithm (2) revauct /* Main Algorithm */
1. Sort all asks ascending order of price within
same price sort on descending order of quantity
2. While (there is an unmarked ask or unfulfilled
supply) repeat steps 3thru 7
3. Find out maximum quantity available for price
p
i
after capacity constraints on sellers
and other
constraints
4. Calculate and save the seller’s contribution
5. Calculate the value of objective function
6. Mark the ask
7. Add quantity to supply_fulfilled
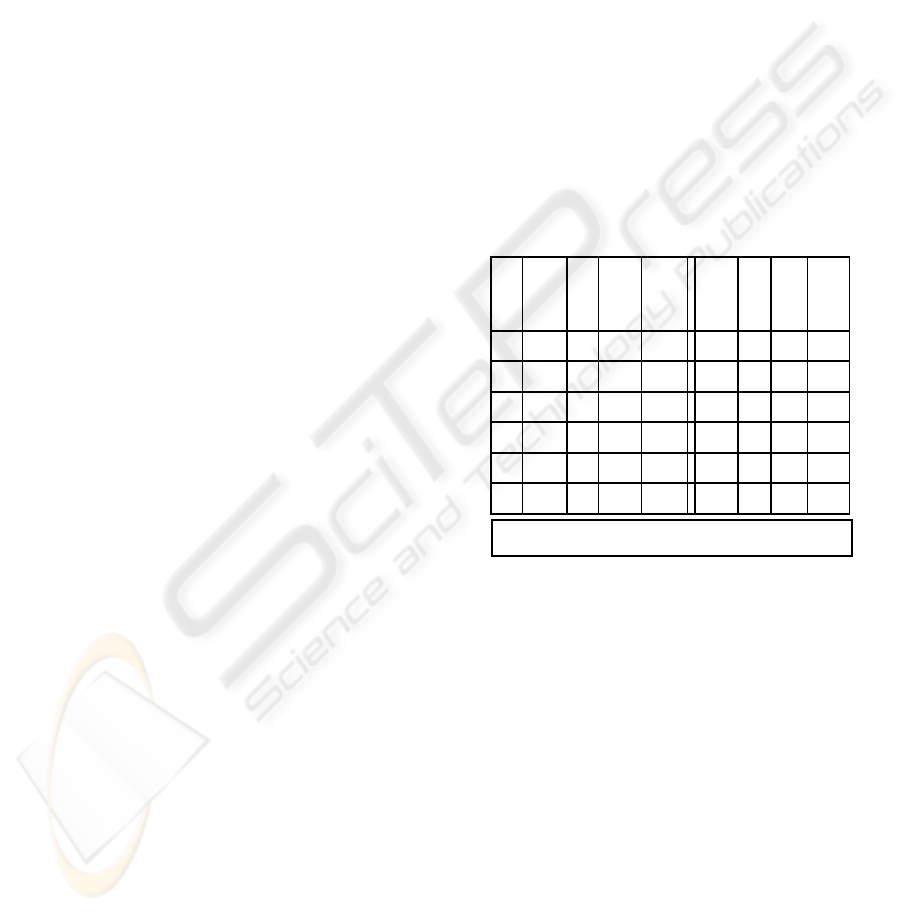
Example: The working of the algorithm is illustrated
in the following simple example. There are four asks
and five bids. The capacity and other constraints are
shown in maximum demand and supply column.
Bid Price
Qty
Avl.
Max.
Possi
ble
Tot.
Price
Ask
Price
Ask
Qty
Qty.
Req Cost
1 45 5 3 135 12 5 50
2 40 8 5 200 12 4 60
3356 6 210 08480
4 30 6 4 180 8 4 100
5258 8 200
33 925
The output of our algorithm shown in column 4
(forward auction) and last column for reverse
auction.
4 EXPERIMENTAL RESULTS
The algorithm has been implemented in C++. The
data sets of asks and bids of different sizes were
generated randomly. Each data set consisted of
number of asks with ask price, quantity, ask size, bid
size, bid price and bid quantity. Size of data sets
varied from 5 to 1500. The results were compared
with unconditional optimum solution and some
solutions obtained with the help of MATLAB
package. It can also be seen that time complexity of
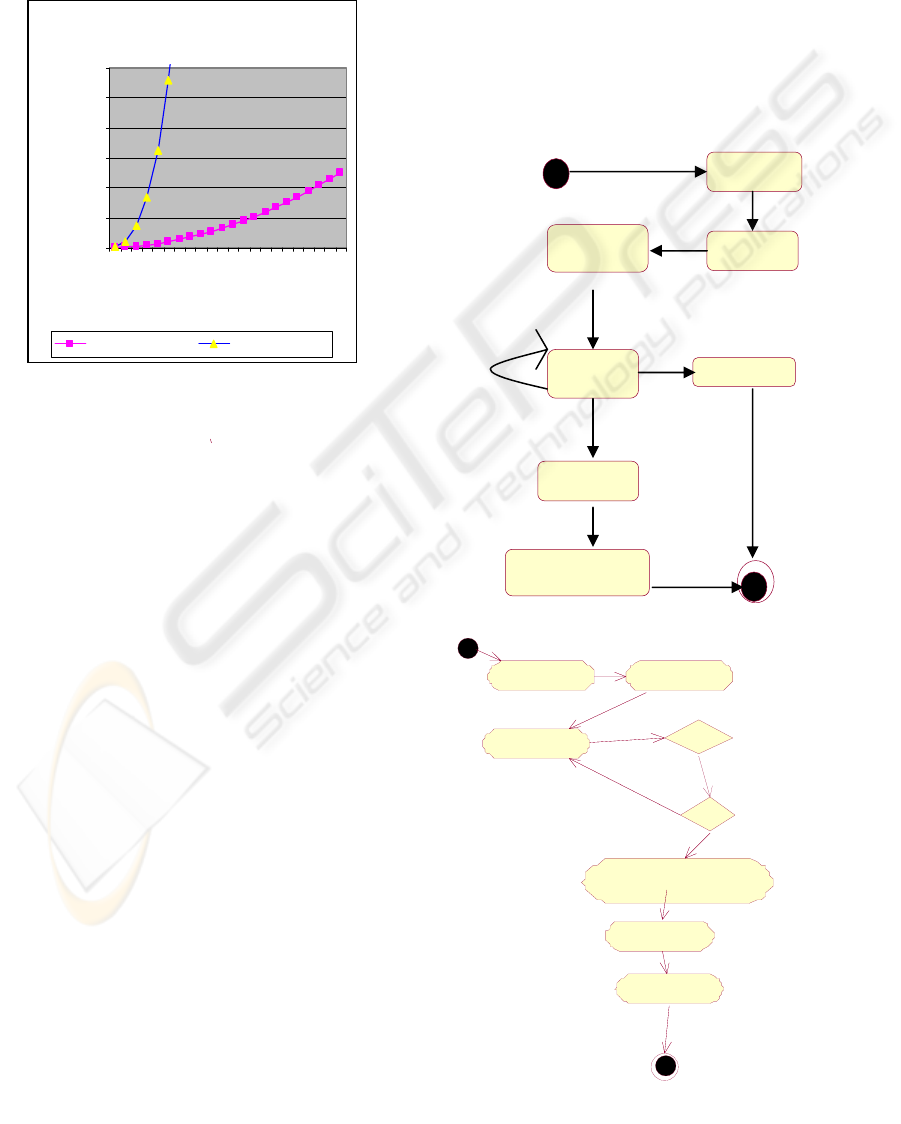
our algorithm is always polynomial. The Figure 1
indicates the comparative performance of proposed
solution against algorithm proposed in (Kothari,
10
15
2
25
Solution Exam
p
le
ICEIS 2005 - SOFTWARE AGENTS AND INTERNET COMPUTING
20
2003). The maximum (minimum) quantity at any
price can be obtained by scanning at most n asks and
bids each time. Apart from this sorting is the hardest
part. Since sorting time complexity is of the order of
O(nlogn), the time complexity of this algorithm is
O(n
2
) + O(nlogn) in worst case, which compares
favorably with the time complexity order O(n3)
presented in(Kothari,2003). Additionally VCG pay-
off gets computed in linear time complexity.
5 SYSTEM IMPLEMENTATION
The auction system for purchase a
nd sale
elps
elps users to
transactions which minimizes the procurement cost
and maximizes cost of selling based above algorithm
has been implemented. The system can handle
forward as well as reverse auctions and is
configurable. An enterprise can configure the system
for forward or reverse auctions and once it is
configured buyers can submit bids and sellers can
submit asks. Then our algorithm computes optimum
solution based on submitted asks and bids. The
optimum solution will be either minimum
procurement cost or maximum cost of sale. Then it
also computes VCG pay-off of each buyer and
seller. As VCG implementation has different
properties like efficiency, strategy-proof ness, our
implementation has also these properties. It ensures
that no buyer or seller can gain by untruthful
bidding. The UML State Chart Diagram of Figure 2
captures different states of our auction based system.
The UML activity diagram is shown in Figure 3.
The different modules in the system are
User Registration Module: This module h
buyers and sellers to register with the system. The
details of the users are captured here. The users can
also submit their respective public keys to the
system using this module. The users can also update
their respective details. A web interface has been
created for submitting the user details.
Notification Module: This module h
notify about the auction. An auction can be initiated
by a buyer or a seller. A web-based interface has
been defined using which users can specify the
different parameters. The users can specify the
details like whether auction is open or sealed bid, the
period for which the auction will remain open, type
of auction, constraints and reservation price etc.
Once the auction details are submitted this module
notifies different buyers and sellers about it. This
module also informs users about various activities
and status of auctions. Once auctions are notified
buyers and sellers can submit respective bids and
Comparision of Algorithms
0
5000
10000
15000
20000
25000
30000
5
2
0
35
50
65
80
9
5
11
0
No. of Bids
No. of Asks scannced / bid
Proposed algorithm
Existing algorithm
Figure 1: Comparative Performance
N
otifie
d
Bid/Ask
S
Re
g
istere
d
ubmitted
Data
Validated
Acceptance
Closed
Optimum allocation
Payoff Generation
Rejected
Figure 2: State Chart diagram
Register User Notify Users
A
ccept Bids
Is Data Valid?
Y/N
Generate optimum
and Asks
Allocation
Is Period Over ?
Co
Y/N
mpute Pay
Off
Notify Result
Figure 3: Activity diagram
AUCTION BASED SYSTEM FOR ELECTRONIC COMMERCE TRANSACTION
21
asks. It also notifies the result of auction and payoff
of each buyer and seller.
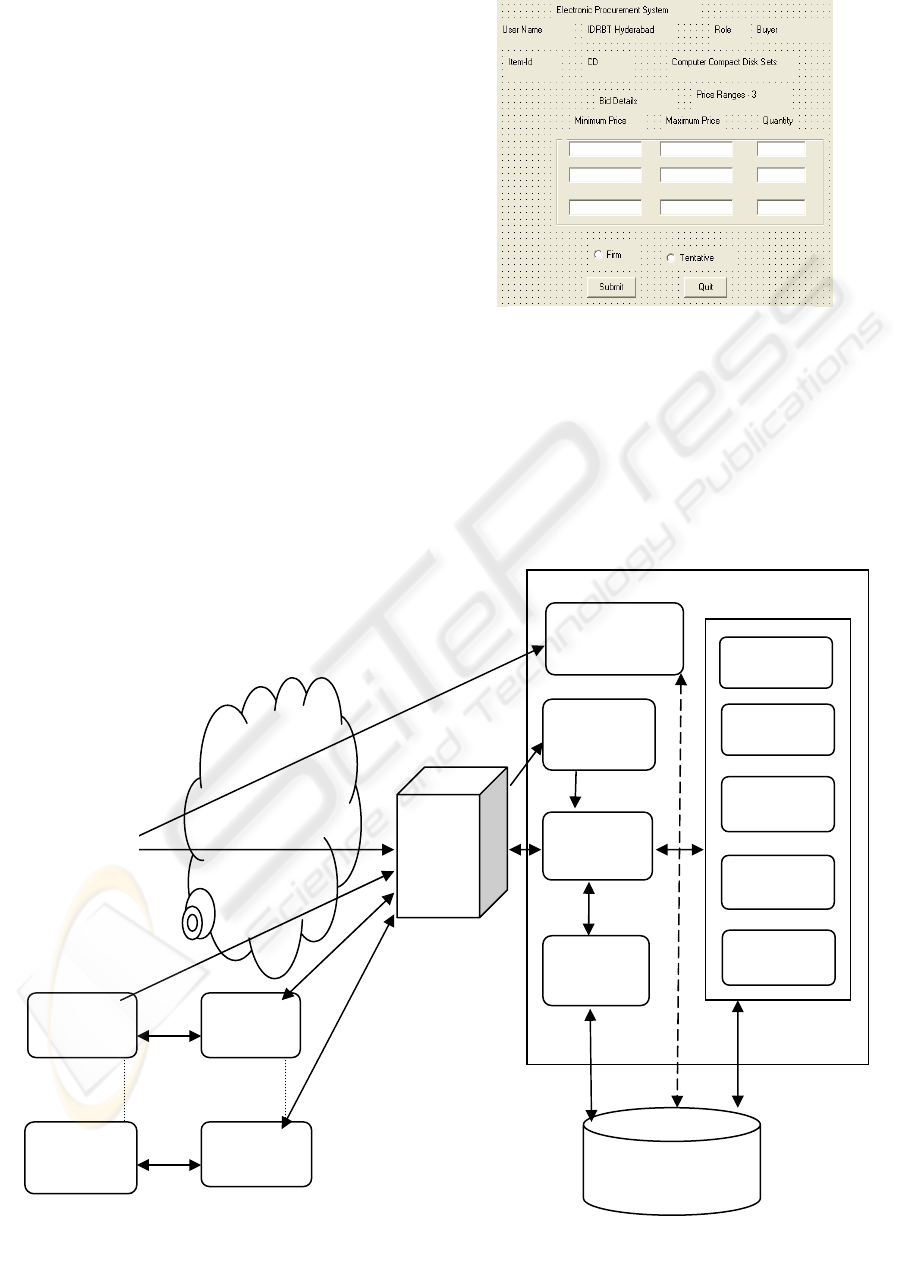
Figure 5: Auction Screen
Bid/Ask Submission: This interface helps buyers
and sellers to submit their respective bids and asks.
The buyers and sellers can specify capacity
constraints using this module. It allows multiple
submission till closing time. It helps users to specify
their firm bid or ask. It allows the users to digitally
sign their respective bid or ask. It can also ensure
that each message is encrypted if required.
Validation Module: This module validates the data
submitted by users. Each bid or ask is validated.
Only bids and asks are considered for further
processing. If bid or ask is invalid then
corresponding message is returned. It validates the
user details and the auction details. If the submitted
details are invalid then the data is rejected.
Optimization Module: This module first formulates
the optimization problem depending upon the
options, attributes and constraints specified. It then
implements the algorithm described in section 3 of
the paper. It finds out optimum procurement cost or
cost of sale. This is one of the main important
feature of our system.
Scheduler Module: This module schedules various
activities in the system. Once the auction is
submitted it schedules activities like auction
notification, closure of bid and ask acceptance,
clearing of market etc.
Configuration Module: It helps enterprises to
configure the auction system. Different parameters
like security level, period, type etc, can be
configured based on user requirements. It also helps
in User Administration.
Auction System
Enterprise
Application
Enterprise
Application
Internet
Enterprise
Application
Enterprise
Application
Auction
Server
Database
Security
Module
Pay off
Module
User
Registration
Scheduler
Module
Configuration
Module
Optimization
Module
Validation
Module
Bid / Ask
Submission
Notification
Module
Buyer /
Seller
Figure 6: Auction System Architecture
ICEIS 2005 - SOFTWARE AGENTS AND INTERNET COMPUTING
22

Payoff Module: It computes the payoff of each
buyer and seller. It computes VCG Pay-off by fast
computation. This module can also backtrack and
generate the solution, even if one of the participant
backs off.
Security Module: This module provides the
security components in the system. It provides
services for storage of public keys. It has modules
for encryption, decryption and digital signing.
The screen shot our system is shown in figure 5 and
architecture in figure 6.
6 CONCLUSION AND FUTURE
WORK
In this paper we have presented the design of an
auction-based system, which can handle assignment
constraints. The two types of auctions considered
here are forward auction and reverse auctions.This
system can handle different types of assignment
constraints in addition to capacity constraints. Its
two main components are the optimization
algorithm, which generates optimum solution to
problem of minimizing procurement cost or cost of
sale, considering different types of assignment
constraints and pay-off algorithm. This can help
enterprises to procure and sell items. It is also
helpful in carrying out IPOs for sale of share of any
enterprise. They can specify the assignment
constraints of different types, so the problem is
handled more general settings. The algorithm can
also handle unconstrained cases. Our system also
ensures that the truthful bidding is the dominant
strategy. The future work includes extending this
work to solve the problem where quantity is not
constrained to be integer. Another extension will be
interfacing the system with the existing systems of
different enterprises and adding payment
component. One of the extension will be to provide
secure payment capabilities by incorporating one or
more banks in the system.
REFERENCES
Bichler Martin, Kaukal Marion, Segev Marion, 1999.
Multi Attribute Auctions for Electronic Procurement,
In the proceedings of First IBM IAC Workshop on
Internet Based Negotiation Technologies, Yorktown
Heights, NY, Marz.
Clarke E. H., 1971.
Multi Part Pricing of Public Goods,
Public Choice, 11:17-33.
Eso M., Ghosh S., Kalagnanam J.,Ladanyi L., 2001.
Bid
evaluation in procurement auctions with piece-wise
linear supply curves
, IBM Research Report RC 22219
Grooves T., 1973.
Incentives in Teams, Econometrica,
41:617-631.
Kalgnanam Jayant R., Lee Ho. S., 2001.
Minimizing
Procurement Costs for Strategic Sourcing
, IBM White
Paper
Kothari Anshul, Parkes David C., Suri Subhash, 2003.
Approximately Strategyproof and Tractable Multi-
Unit Auctions
. Proceedings of 4
th
ACM Conference on
Electronic Commerce, Pages 166-175.
Multi Commodity Stock Exchange of India,
www.mcxindia.com
National Stock Exchange of India, www.nse-india.com
Rothkopf, M.H., Pekec A., Harstad R.M., 1998.
Computationally Manageable Combinatorial
Auctions, Management Science
, 44(8), 1131-1147.
Sandholm T., 1999.
An Algorithm for Optimal Winner
Determination in Combinatorial Auction
, In
proceedings of IJCAI 1999, Morgan Kaufmann
Vickey W., 1961.
Counter Speculation, Auctions and
Competitive Sealed Tenders
, Journal of Finance, 16:8-
37.
Wolfstter E., 1996.
Auctions: An Introduction, Journal of
Economic Surveys, 10(4): 367-420
AUCTION BASED SYSTEM FOR ELECTRONIC COMMERCE TRANSACTION
23
