
CONTEXT-AWARENESS SIMULATION TOOLKIT
A Study on Secure Context-based Learning in Ubiquitous Computing
InSu Kim, HeeMan Park, BongNam Noh
Department of Information Security, Chonnam National University, Gwangju 500-757, Korea
YoungLok Lee, SeungYong Lee
Linux Security Research Center, Chonnam National University, Gwangju 500-757, Korea
HyungHyo Lee
Division of Information and EC, Wonkwang University, Iksan 570-749, Korea
Keywords: Ubiquitous learning, Context-Awareness, security.
Abstract: The study deals with the most important elements of ubiquitous computing, that is, the toolkit to acquire,
express and safely use the context information. To do so, we introduce CAST(Context-Awareness
Simulation Toolkit) and show how it works. CAST generates users and devices in a virtual home domain,
designates their relation and creates virtual context information. The created context information is reused
by the request of application and put into use for learning. Particularly, we have given a consideration to
security in the process of context creation and its consumption. That is, we applied SPKI/SDSI to test if the
created context information was valid information and if the application that called for the context had
legitimate authority to do so. CAST not only captures virtual context information, but it also guarantees the
safe sharing of the context information requested by the application.
1 INTRODUCTION
Context Awareness is the most important research
area in ubiquitous computing, on which many
researches are recently being done. It was because
Mark Weiser, who first suggested the notion
'ubiquitous computing', noted that basically the
following 4 should be reflected (Mark Weiser,
1993), (Mark Weiser, 1993) and (Mark Weiser,
1994): ① Human-friendly interface, ② Computing
connection at anytime, anywhere, ③ Calm
technology, ④ Dynamic service.
Like this, Context Awareness is very important
to ubiquitous computing that is intended to enable
natural and convenient computer use in everyday
lives regardless of location and time.
Since Context Awareness is important, there
have been lots of preceding researches on it.
However, there are some limitations and our
approach to the resolution of it is as follow:
• The vagueness of the definition of context
• Although there have been many preceding
researches, there is no agreed definition of it yet.
The main reason of it is that we generalize and then
try to define all the domains. Here, we are going to
focus on the context of just a certain domain of
home.
• The difficulty in acquiring context
• In real world, context information is acquired
by physical sensors. However many researchers
have hard time in their getting context information
since they have mostly majored in S/W part rather
than H/W part. For the reason, the majority of the
related researchers are apt to do their modeling and
research context conceptually without the real
context information. The study provides a
Simulation Toolkit by which those researchers of
Context Awareness in the S/W part may acquire
context and share in their acquired context.
• The validity of acquired context information
and its safe sharing
: Preceding studies on the things such as Context
Toolkit have not given any consideration to security
190
Kim I., Park H., Noh B., Lee Y., Lee S. and Lee H. (2006).
CONTEXT-AWARENESS SIMULATION TOOLKIT - A Study on Secure Context-based Learning in Ubiquitous Computing.
In Proceedings of WEBIST 2006 - Second International Conference on Web Information Systems and Technologies - Internet Technology / Web
Interface and Applications, pages 190-198
DOI: 10.5220/0001256901900198
Copyright
c
SciTePress

while acquiring context. That is, there have been no
consideration to if the acquired context information
was valid or if the application requesting the
acquired context is duly authorized. The ubiquitous
computing system should protect individual privacy
from ubiquitous sensors. That was why we have
considered security.
The development of CAST(Context-Awareness
Simulation Toolkit) which the study suggests was
motivated while the author was watching a play in
the theater. Figure 1 is a scene from the featuring of
famous Korean musical named NANTA. The
performers( of Figure 2) play with their all might
and main in their gestures() following the
scenario() of the playwright() against the
stage() garnished with various stage
properties().
The CAST suggests will create a valid context
information for us via a S/W agent concocted virtual
sensor instead of a physical sensor. Just like the
performers in the play moves us by their
performance in their virtual lives, we are going to
safely share and reuse the created context
information and utilize it in the user adaptation by
the context learning.
The study is composed of the following. In
section 2, it will take a look at related research and
in section 3, it will introduce CAST. In section 4, it
will discuss the feasibility and its comparison with
existing research by a proposed prototype of CAST.
Finally, in section 5, it will present the conclusion
and the direction of future studies.
2 RELATED WORK
There have been lots of preceding researches on
Context-Awareness. Except the Context Toolkit of
A.K.Dey (G. D. Abowd, 1999) and (A. K. Dey et al.,
2000), All preceding researches acquire context
information through physical device in H/W part
(Seiie jang et al., 2004) and (N. Davis et al., 2001).
2.1 The Context Toolkit of Dey et al.
The approach of the Context Toolkit by Dey et al
(G. D. Abowd, 1999), (A. K. Dey, G. D. Abowd,
2000), (A. K. Dey et al., 2001) and (Dey, A.K. et al.,
2001) origins from the area of location-aware
services. Its main focus is to provide a
comprehensive conceptual framework together with
a toolkit for representing and processing context
information independent of an application, thus
establishing an external customisation architecture.
The context toolkit which realises only a subset
of the frameworks' concepts has been implemented
using Java and XML (W.S. Means and E.R. Harold,
2001) Various applications have been developed on
basis of the toolkit, including, e.g., an in/out board
for indicating those persons which are inside a
building, a personalised information display which
shows the user in front relevant information and a
context-aware mailing list sending emails only to
those subscribed users which are currently in a
certain building.
2.2 The CIVE of Seiie Jang et al.
The CIVE(Context-based Interactive system for
distributed Virtual Environment) is a system that
connects real world with virtual world by sharing
user's context (Seiie jang et al., 2004).
It consists of ubi-UCAM for generating user's
context, NAVER for managing virtual
environments, and Interface for linking ubi-UCAM
with NAVER. Interface transforms contexts or
commands into events that influence virtual
environment, and converts events into contexts for
context-based services in real environment.
Figure 1: Korean musical named NANTA.
Virtual Home
-
Map Editor
Virtual Device Manager
Virtual Person Manager
Policy Repository
CAST
(C
ontex
t
-A
wareness
S
imulation
T
oolkit)
CAST
middleware
CAST
admin
Scenario
& Policy
Manager
Event
Manager
Contex
t
Manager
Context Repository
CAST
home
Figure 2: Architecture of CAST.
CONTEXT-AWARENESS SIMULATION TOOLKIT - A Study on Secure Context-based Learning in Ubiquitous
Computing
191
2.3 The GUIDE of Cheverst et al.
The GUIDE system of Cheverst et al. (N. Davis et
al., 2001), (K. Cheverst et al., 2000), (Mitchel and
N. Davis, 2002) (N. Davies et al., 2001) stems from
the area of location-based services. The focus is to
provide tourists with up-to-date and context-aware
information about a city via a PDA.
3 CAST
CAST that we suggest defines context with our
focus on a specific domain of home, unlike the
preceding researches with wide-range definitions of
context. The domain can be a school, a hospital, an
office or the like.
• Context
home
: Context is the information that can
particularize the conditions of all
entities constituting home and be put
into use in decision-making. The
entity includes people, place and all
objects in the actual world.
3.1 CASThome
We have used by Macromedia’s Flash MX 2004 in
laying out a home environment with virtual people
and devices (J. Kaye and D. Castillo, 2005) and
(Craig Swann and Gregg Caines, 2002). We chose
the technology because it's quite useful with its
visual convenience and easy interface. It also has a
big merit of its ability to be interlocked with external
programs (M. L. Liu, 2004) since it supports the
inter-communication function with the programs
such as JAVA, C++, C# via the XMLsocket Class
provided by Flash.
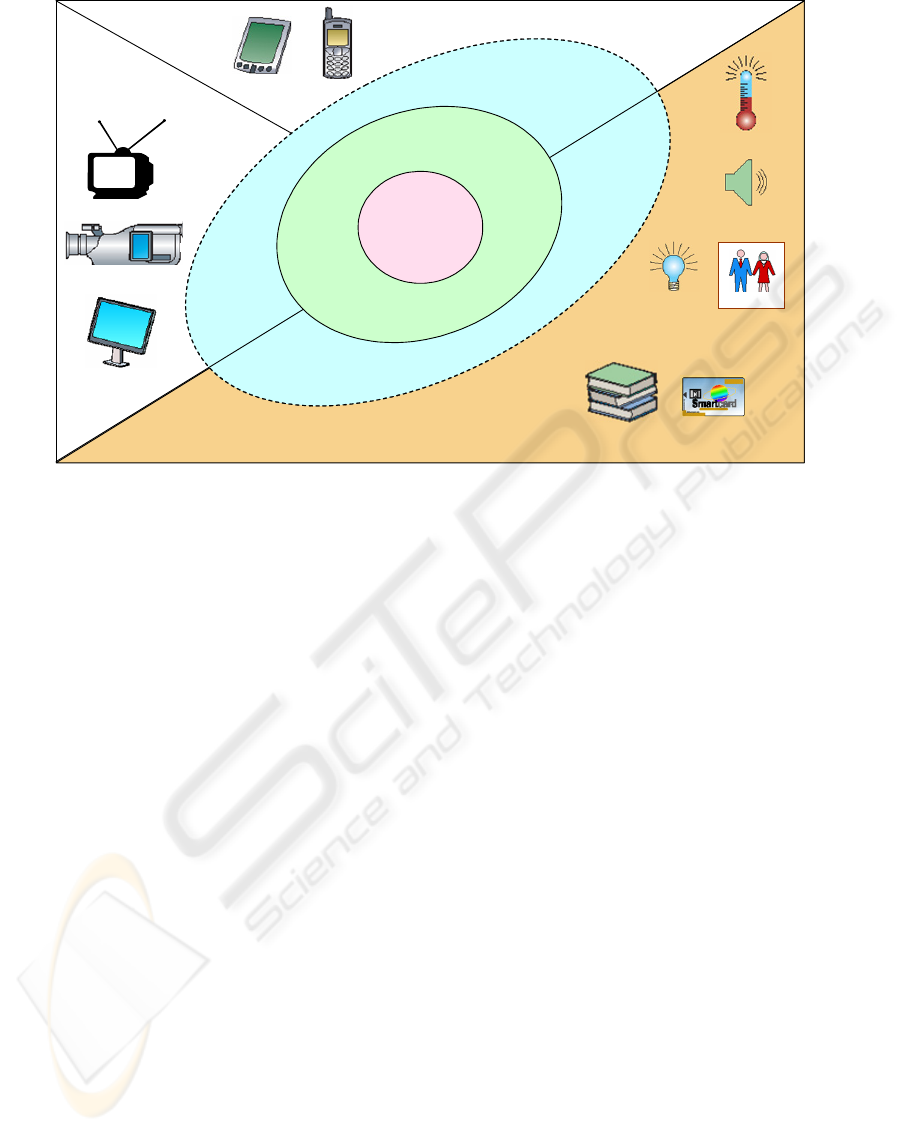
3.1.1 Virtual Device Manager
We have realized virtual S/W devices by using the
Flash MX 2004 (J. Kaye and D. Castillo, 2005) and
(Craig Swann and Gregg Caines, 2002) as well as
the JAVA sockets. The devices are classified in their
production and consumption of virtual context as
Figure 3.
• Sensor device(=Producer): This is a device,
with no calculation capability, that only generates
context information and that is classified as the
following:
①Environment sensors: This is a sensor that
produces physical environmental information
that is exposed to everybody.
Application Device
Sensor Device
Prosumer
Consumer
Producer
②
Smart tag sensors (Diary, RFID,...)
①
Environment sensors
Contex
t
Manage
r
Event Manager
PDA
LocationLocation
Temperature
Soun
d
LightLight
TV
Monitor
Video
CP
Figure 3: Virtual Devices of CAST.
Diary
WEBIST 2006 - INTERNET TECHNOLOGY
192

(temperature, sound, light force, location etc.)
② Smart tag sensors: Smart tag sensor
connected to private information.(Diary, RFID
etc)
• Application device: A device with
calculation capability with itself. Classified as
the following:
①Consumer: A device that just asks Context
manager for context and consumes context.
(TV, video, monitor, etc)
② Prosumer: A device that not only asks
Context manager for context to consume it, but
also is able to update its private information-
related context.(PDA, cellular phone, etc)
3.1.2 Virtual Home-Map Editor
It generates a virtual home environment as the
domain of CAST. A virtual home, like a home in
real world, may consist of rooms, a living room,
bath room and kitchen. Also, the Sensor and,
Application devices generated by Virtual Device
Manager will be put into appropriate places in the
virtual home.(Figure 6)
3.1.3 Virtual Person Manager
This generates family members that belong to the
virtual home environment. The profile of each
member will be stored in their cellular phones and
will be updated at all times. The profile will be
written in SOUPA(Standard Ontology for
Ubiquitous and Pervasive Applications) (Harry Chen
et al., 2004), (Harry Chen et al., 2004) and (H. Chen,
2003) and includes the information of their
respective domain homes as well as the application
device.
The following shows a partial ontology descriptiion
of the person Kim In-su:
<per:Person>
<per:firstName
rdf:datatype="&xsd;string>Kim</per:
firstName>
<per:lastName
rdf:datatype="&xsd;string>In-
su</per:lastName>
<per:gender rdf:resource="&per;Male"/>
<per:birth
rdf:datatype="&xsd;string>04041974<
/per:birth>
<per:homepage
rdf:resource="http://www.cyworld.com
/agisong"/>
<per:email
rdf:resource="mailto:agisong@lsrc.jnu
.ac.kr"/>
<per:hasHomeContact
rdf:resource="#InsuHomeContact"/>
</per:Person>
<per:ContactProfile
rdf:ID="InsuHomeContact">
<per:address
rdf:datatype="&xsd;string">
LSRC,300,Yongbong-dong,Puk-
gu,Gwangju,Korea
</per:address>
<per:phone rdf:datatype="&xsd;string">
+82-62-530-3714</per:phone>
</per:ContactProfile>
<dev:SamsungCellphone>
<dev:hasUser>
<foaf:Person>
<foaf:homepage
rdf:resource=http://www.cyworld.c
om/agisong"/>
</foaf:Person>
</dev:hasUser>
<dev:modelNumber
rdf:datatype="&xsd;string>
SCH-
E120</dev:modelNumber>
<dev:serialNumber
rdf:datatype="&xsd;string>
R24W114948</dev:seri
alNumber>
<dev:phoneNumber
rdf:datatype="&xsd;string>
Application Device
web
server
Event
Consumer
SPKI/SDSI
certificates
Remote
Event
Listener
JS
-
ES
SSCM
Event
Producer 2
ACLs
①
retrieval( )
⑤
download listener_stub
②
-
1
registerConsumer
( )
③
reply permit or deny
⑥
event Notification
②
-2
validateCert( )
④
-2
registerListener ( )
④
-
1
registerListener
( )
s
tore( )
NRC
LRC
Event
Manager
v
alidateCert( )
r
egister Producer( )
publish( )
Sensor Device
1
Event
Producer 1
ACLs
Sensor Device
2
publish( )
r
egister Producer( )
②
-3
Figure 4: Event Manager process realized authentication and authorization.
CONTEXT-AWARENESS SIMULATION TOOLKIT - A Study on Secure Context-based Learning in Ubiquitous
Computing
193

017-365-
8477</dev:phoneNumber>
</dev:SamsungCellphone>
3.2 CASTmiddleware
CAST
middleware
performs the communication role
among the virtual people and devices set in
CAST
home
. It is composed of Event Manager and
Context Manager. Their respective roles are like the
following.
3.2.1 Event Manager (YoungLok Lee et al.,
2005)
Ubiquitous services must appropriately adapt to the
context information of the user. In need of privacy
protection and proper adaptation, context
information should be generated from the accurate
event information and only right possessor of the
authority about the event should utilize it. The ad
hoc network environment introduces fundamental
new problems. One is the absence of an online
server, and another is secure transient association.
Authentication and Authorization are the most
interesting security problems in ad hoc networking,
because much of the conventional wisdom from
distributed systems does not quite carry over. For
solving these problems, we use SPKI/SDSI(Simple
Public Key Infrastructure/Simple Distributed
Security Infrastructure) certificates. (YoungLok Lee
et al., 2005) and (M. L. Liu, 2004)
• ACL and SPKI/SDSI Certificate
: The consumer of events will have the following
Name Certificate(<Issuer, Local Name, Subject,
Validity>) and Authorization Certificate(<Issuer,
Subject, Delegation bit, Authorization-tag,
Validity>) (YoungLok Lee et al., 2005). The event
consumer sends Name Certificate and Authorization
Certificate bundled together to LRC when
registering event listeners.
ACL includes security policy which event
producer endows the beneficiary event consumer the
authority and is expressed as the Authorization
Certificate.
The following explains S-expression of
Authorization Certificate. Bob grants subject, called
InSu Kim in his local name space, its authority, “get
notification 2” from Nov.20,2005 to June.18,2006.
(cert (display plain)
(issuer (public-key (rsa (e
#010001#)
(n |APsREOm+tJQsyS6f7ddzrY4A
...|))))
(subject (name InSu Kim))
(tag “get notification2”)
(valid (not-before "2005-11-
20_06:51:33")
(not-after "2006-6-
18_21:51:33"))
(comment "test certificate"))
(signature (hash sha1
|aj5Le4mGJ1BltdNdhU...|)
(public-key (rsa (e #010001#)
(n
|APsREOm+tJQsyS6f7ddzrY4ACM9fmQC
...|)))
(rsa-pkcs1-sha1
|mSWhfa2GBJ3YKwkEYL/7yCP...|))
• SPKI/SDSI Certificate Manager
: SSCM(SPKI/SDSI Certificate Manager)
includes “ Certificate Chain Discover” algorithm
which carries out the work of retrieving from its
certificate cache authority certificates and name
certificates provided to verify the authority for the
consumer to perform the given calculation(2-3 of
Figure 4) (YoungLok Lee et al., 2005).
• Listener Registration Controller
(The first security challenge: Authorization)
: LRC(Listener Registration Controller) registers
only the event listener of authorized
consumer(Application Device) to JS-ES(2-1). LRC
sends the event type and certificate bundle which it
received from consumer to SSCM for authority
probation(2-2) and decides by the feedback whether
to register the event listener(3)(Philip Bishop and
Nigel Warren, 2002) and (W. Keith Edwards, 2000).
• Notification Registration Controller
(The second security challenge: Authentication)
: NRC(Notification Registration Controller)
registers only the events of authenticated
producer(=sensor device)(, ) and produces valid
context(). It tests the event type registered by
producer and checks for any error for ACLs and for
any overlapping of the event registered(3)(Philip
Bishop and Nigel Warren, 2002) and (W.Keith
Edwards, 2000) and (W. Keith Edwards, 2000).
Sensor devices
Application devices
Event Manager
Context Manager
Event Consumer
Context Repository
TV Interface(*.sw
f
)
Sofa Sensor Interface(*.sw
f
)
xmlsocketClass
j
avaspace.write
(… )
j
avaspace.notify
(…)
j
avaspace.write(eventType,..)
j
avaspace.notify
(…)
Event Channel 1 of JS
-
ES
Event Channel 2 of JS
-
ES
Event Consumer
Event Producer
Event Producer
xmlsocketClass
Context Query Context store
Location
Sensor
Light Sensor
Figure 5: Overall architecture of our prototype.
WEBIST 2006 - INTERNET TECHNOLOGY
194
• extended JavaSpace-based Event Service
(3)(Philip Bishop and Nigel Warren, 2002) and
(W.Keith Edwards, 2000).
: JS-ES(extended Java Space-based Event
Service) takes the stub of the Remote Event Listener
for the communication with the event consumer
through web server(5). If sensor 1(=Event producer
1) produces a context information, Event producer 1
publishes it on NRC of Event Manager. Through JS-
ES, NRC notifies the event(=context information)
published by to Event Consumer of Application
device(6).
3.2.2 Context Manager
The context manager processes context information
coming from sensors, stores it, and converts it into
high layer's context information according to the
inference policy. The context information, stored in
the database, is reused later in the study of user sign
or when the application demands. This context
information is the events which application devices
want, so to inference those events the context
manager provides GUI for setting the inference
policy. On the account of limited space in the thesis,
we omit the explanation for this.
3.3 CASTadmin
CAST
admin
defines the relations between the Device
deployed in the CAST
home
as a domain and the
Person belonged to it, and generates policy and
scenario. The defined relations and policy are to
decide who can own and use which device. And
person actually behaves following the scenario, then
the subsequent virtual device is going to produce or
consume context via the communication with
CAST
middleware.
The detailed explanation of it is
omitted due to space consideration here.
4 IMPLEMENTATION AND
ANALYSIS
To probe the feasibility of the suggested CAST, we
implemented in Linux/Windows OS, Macromedia’s
Flash MX 2004 (J. Kaye and D. Castillo, 2005) and
(Craig Swann and Gregg Caines, 2002), JDK 1.3
and Jini 1.2 development environment ()(Philip
Bishop and Nigel Warren, 2002) and (W. Keith
Edwards, 2000). We set up a scenario, and
subsequently observed that virtual certified device
produce valid context information in accordance
with the scenario and that authorized device TV
share and consume it.
Location Senso
r
Sofa senso
r
TV Device(On
)
Light senso
r
Living room
Bob
’
s room
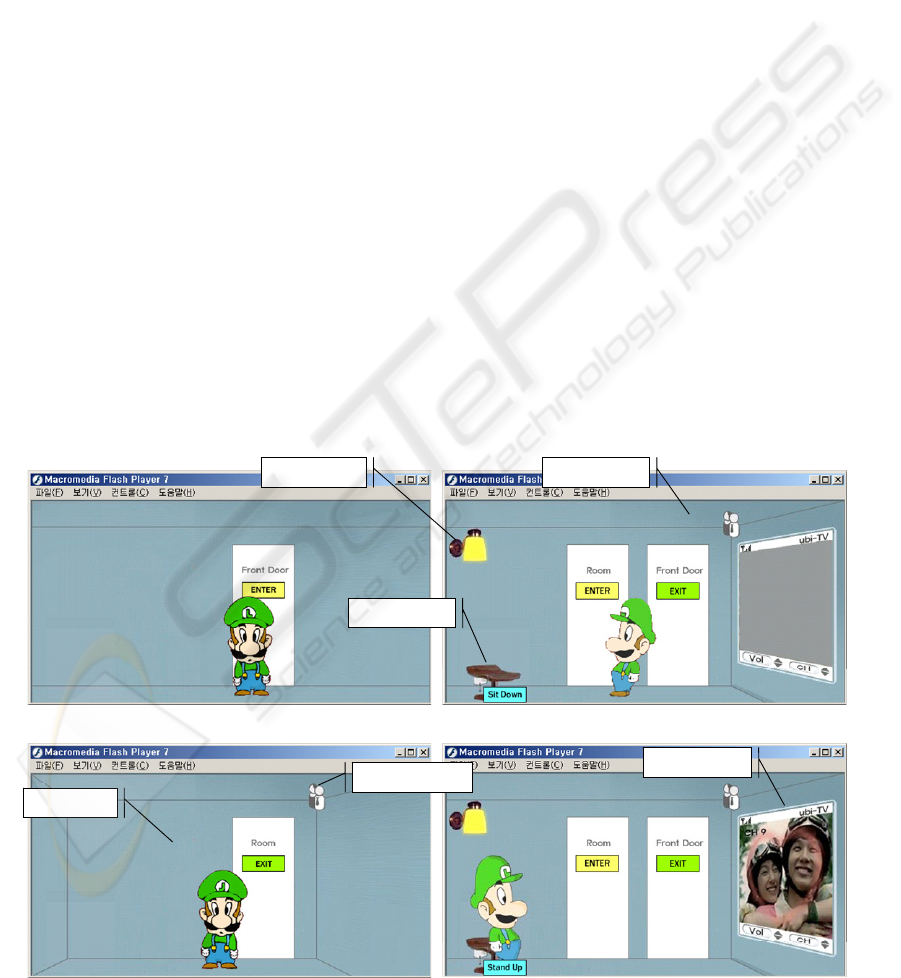
Figure 6: Demo of our prototype .
(a) Bob in the front of the doorway
(b) Bob is standing at the living room
(c) Bob is standing at the his room
(d) Bob sit on the sofa in front of the TV device
CONTEXT-AWARENESS SIMULATION TOOLKIT - A Study on Secure Context-based Learning in Ubiquitous
Computing
195

4.1 Scenario
We chose TV for an example of the application. It
was because, though with an infamy of being a fool
box, it is one of the media that have the greatest
impact on contemporary lives. In addition, more
than anything else, in the prospect of the
technologically converging trend of broadcast and
telecommunication, it will become the most
influential media in the future. We realized the
prototype scenario as the following:
“On July 5, 2005, PM 6:00, Bob heads for home
after work. In the way, he stops by a grocery store to
buy some fruits. When he arrives home, the light
goes on and after certification, he enters home. First,
he changes his clothes in his home, then he has a
brief dinner and sits on the sofa. The context
manager, detecting his sitting on the sofa, turns on
the TV to a channel based on Bob's appetite. Bob
runs out to the grocery store to retrieve his wallet
that he had mistakenly dropped there, with the TV
on. When Bob came back, the TV is off, but turns on
to the same channel that he viewed when he sits on
the sofa.”
4.2 Prototype Implementation
4.2.1 Scenario Process
The Figure 5 explains the communication flow
between CAST
device
and CAST
middleware
that takes
place once Bob sits on the sofa. The information
generated by the sofa sensor is transmitted to
Context Manager through JS-ES of Event Manager
and stored there. Since the acquired information is
the one that is called to turn the TV On/Off, it is
automatically transmitted to the TV through JS-ES
of Event Manager. Of course, the information of
whether the TV has the authority to use the context
information generated will be transmitted only when
it is probed in SSCM of Event Manager.
4.2.2 TV On/Off Class and Algorithm
The event class that the virtual TV device is going to
use will be the following:
public class TvOnOffEvent extends
JSEvent {
public Boolean flag;//
False:TvOn,True: TvOff
public Integer counter;//number of
the family
public String[] living;//family in
living room
public String[] sofa; // family in
sofa
public TvOnOffEvent(Integer family,
Boolean s) {
counter = family;//total number of
family
flag = s;//current TV’s On/Off
State
living = new String[counter];
sofa = new String[counter];
}
}
The TV On/Off adaptation algorithm
of event consumer after receiving TVs
On/Off events is as follows:
Algorithm: TV Adaptation(TvOnOffEvent
tvevent)
Input: tvevent // TV On/Off Event
Type
Method:
begin
switch(tvevent.flag);//TV’s state
begin
Case FALSE://in the case of TV Off
event
if((tvevent.livingroom ∩
tvevent.sofa) ≠ Φ)
TvOn( );
Case TRUE://in the case of TV On
event
if((tvevent.livingroom ∪
tvevent.sofa)=Φ)
TvOff( );
End
End
4.2.3 Demo
Bob moves left(“Home” key) or right(“End” key) by
Keyboard and his home consists of living room,
Bob’ room. Location, light, sofa, TV device are put
GUIDE
Context
Toolkit
CIVE
CAST
Kind
O
O
O
O
Representation
of Context
--O--OO-
O-O-O--O
--O--OO-
OOO-O--O
DynamicicityAutomation
Sharing
of
Context
Acquisition of Context
GUIDE
Context
Toolkit
CIVE
CAST
Kind
O
O
O
O
Representation
of Context
--O--OO-
O-O-O--O
--O--OO-
OOO-O--O
DynamicicityAutomation
Sharing
of
Context
Acquisition of Context
Reusability
Abstraction
manual
semi-
automatic
automatic
static
dynamic
Device Authentication
Authorization
Approach
Security
Table 1. result of analysis
Table 1: Result of Analysis.
WEBIST 2006 - INTERNET TECHNOLOGY
196

into living room in Bob’s home and only location
device is put into his room.
In Figure 6-(a), Bob stands in front of door.
When Bob enters into living room by clicking
“ENTER” button of Front Door in Figure 6-(a), the
location sensor detects his presence and turns the
light on. But the TV does not go on by the Rule
designated by the TV On/Off Adaptation
Algorithm(Figure 6-(b)). If Bob enters into his room
by clicking “ENTER” button of Room in Figure 6-
(b), the location sensor detects his presence(Figure
6-(c)). In Figure 6-(b), If Bob sits on the sofa by
clicking “Sit Down” button of sofa in living room,
by the rule, the TV goes on(Figure 6-(d)).
4.3 Analysis
We have compared and reviewed CAST realized by
a prototype and preceding studies, focusing on the
following (Gerti Kappel and Birgit Proll, 2003). As
a result, we could find a big merit of guaranteed
security in the aspects of context acquirement(The
first security challenge) and sharing(The second
security challenge) in Table 1.
The comparison detail would be the following
(Gerti Kappel and Birgit Proll, 2003):
• Automation. Concerning the acquisition of
context, first it has to be defined who is in charge for
gathering appropriate context information, be it
either a human(manual acquisition) or the
system(automatic acquisition) or a combination
thereof(semi-automatic acquisition).
• Dynamicity. Another important aspect is when
context acquisition takes place. Considering the
frequency of context changes, context can be either
static, i.e., determined once at application start
up(e.g., the device used to select the appropriate
interaction style), without considering any further
changes or dynamic, i.e., determined on every
change during runtime(e.g., the bandwidth to adapt
the resolution of an image on the fly).
• Abstraction. According to the level of
abstraction where context properties are represented
it should be distinguished between physical context
and logical context. Whereas physical context is at a
very low level of abstraction which can be directly
sensed from the environment, logical context would
enable to enrich its semantics thus making it meani
ngful for customisation purposes.
• Authentication. It means which context
information acquired from certain types(manual,
semi-automatic, automatic) is valid, that is, if the
context is attained from certified source.(The first
Security challenge)
• Authorization. It means whether it provides
the acquired context information to only the
application with due authority.(The second Security
challenge)
5 CONCLUSION & FUTURE
WORK
The study suggested CAST for the purpose of
acquiring, expressing and safely using context
information in the previous sections and probed its
feasibility by a Demo of a realistic prototype. In
particular, CAST acquires valid context and supports
the function of sharing it with only authorized
applications. This is significant because it provides
virtual experimental environment to the S/W-major
context researchers who find it difficult to fabricate
physical sensors.
Future studies are called for the following area.
First, the automation of CAST components is
necessary. For the present prototypes, only Device
interface, agent and CAST
middleware
(Event Manager,
Context Manager) have been realized. In the future,
through the automation of all the components, a
more useful CAST will be developed and be open to
the context researchers. Second, the extension of
domain is necessary. Later studies will include other
such various domains as schools and hospitals
besides home in their research. Finally, it is expected
to have a study on context modeling that is more
typical and acceptable as the standard performed at
the same time.
ACKNOWLEDGMENTS
This study was financially supported by Chonnam
National University.
REFERENCES
G. D. Abowd, 1999, “Software Engineering Issues for
Ubiquitous computing”, Int. Conf. on Software
Engineering, Los Angeles,
A. K. Dey, G. D. Abowd, 2000, “The Context Toolkit:
Aiding the Development of Context-Aware
Applications”, Workshop on Software Engineering for
Wearable and Pervasive Computing, Limerick, Ireland
A. K. Dey, G. Kortuem, D. R. Morse, A. Schmidt, 2001,
“Situated Interaction and Context-Aware Computing”,
editorial, Personal Ubi Comp, Vol. 5 No. 1, pp. 1-3
Dey, A.K., Salber, D. Abowd, G.D., 2001, “A Conceptual
Framework and a Toolkit for Supporting the Rapid
Prototyping of Context-Aware Applications”, anchor
article of a special issue on Context-Aware Computing
CONTEXT-AWARENESS SIMULATION TOOLKIT - A Study on Secure Context-based Learning in Ubiquitous
Computing
197

Human-Computer Interaction (HCI) Journal, Vol. 16,
No. 2-4, pp. 97-166
W.S. Means, E.R. Harold, 2001, “XML in a Nutshell, A
Desktop Quick Reference”, O’Reilly
Seiie jang, Youngho Lee and Woontack Woo, 2004,
“CIVE: Context-based Interactive System for
Distributed Virtual Environment”
Harry Chen, Filip Perich, Tim Finin, Anupam Joshi, 2004,
“SOUPA: Standard Ontology for Ubiquitous and
Pervasive Applications”
Harry Chen, Tim Finin, Anupam Joshi, Lalana Kagal,
2004, “Intelligent Agents Meet the Semantic Web in
Smart Spaces”, the IEEE Computer Society
H. Chen, T. Finin, and A. Joshi, 2003, “An ontology for
context-aware pervasive computing environments.
Special Issue on Ontologies for Distributed Systems”,
Knowledge Engineering Review
N. Davis, K. Cheverst, K. Mitchel, A. Efrat, 2001, “Using
and Determining Location in a Context Sensitive Tour
Guide”, IEEE Computer
K. Cheverst, N. Davies, K. Mitchell, A. Friday, 2000,
“Experiences of Developing and Deploying a Context-
Aware Tourist Guide: The GUIDE Project”, Proc. Of
the 6th Int. Conference on Mobile Computing and
Networking(MOBICOM), Boston MA USA, ACM
Mitchel, N. Davis, 2002, “The role of adaptive
hypermedia in a context-aware tourist guide”,
Communications of the ACM (CACM), Vol. 45, No. 5
N. Davies, K. Cheverst, K. Mitchell, A. Efrat, 2001,
“Using and Determining Location in a Context-
Sensitive Tour Guide”, IEEE Computer, Vol.34.No.8
YoungLok Lee, Seoungyong Lee, InSu Kim, HyungHyo
Lee, BongNam Noh, 2005, “Development of Event
Manager and Its Application in Jini Environment”,
IFIP International Conference on NCUS 2005,
Nagasaki, Japan, pp. 704-713
YoungLok Lee, Seoungyong Lee, HeeMan Park,
HyungHyo Lee, BongNam Noh, 2005, “The Design
and Implementation of Secure Event Manager Using
SPKI/SDSI Certificate”, IFIP International Conference
on UISW 2005, Nagasaki, Japan, pp. 490-498
J. Kaye, D. Castillo, 2005, The Book, “Flash
TM
MX for
Interactive Simulation”,ISBN:14-0181-291-0
Craig Swann, Gregg Caines, 2002, The Book, “XML in
Flash
TM
”, ISBN:0-672-32315-X, QUE Publishing
M. L. Liu, 2004, The Book, “Distributed Computing:
Principles and Applications”, ISBN:0-201-79644-9,
PEARSON ADDISON-WESLEY
Gerti Kappel, Birgit Proll, 2003, Werner Retshitzegger,
Wieland Schwinger, “Customisation for Ubiquitous
Web Applications: A Comparison of Approaches”,
International Journal of Web Engineering and
Technology, Vol.1, No.1, pp. 79-111
Mark Weiser, 1993, “Some Computer Science Problems
in Ubiquitous Computing”, ACM
Mark Weiser, 1993, “Ubiquitous Computing”, Nikkei
Electronics, pp.137-143
Mark Weiser, 1994, “The World is Not a Desktop”,
Interaction, pp.7-8
PHILIP BISHOP AND NIGEL WARREN, 2002, The
Book, “JavaSpaces
TM
in Practice”, ISBN: 0-321-
11231-8, Addison-Wesley
W.KEITH EDWARDS, 2000, The Book, “Core JINI(2
nd
Edition)”, ISBN: 0-13-089408-7, Prentice Hall PTR
WEBIST 2006 - INTERNET TECHNOLOGY
198
