
THE POLYNOMIAL MULTICOMPOSITION PROBLEM IN
(Z/nZ)
Neculai Daniel Stoleru and Victor Valeriu Patriciu
Department of Mathematics and Informatics, Military Technical Academy, Caraiman Str. 116, Bucharest, Romania
Keywords: Polynomial composition, identification, key agreement.
Abstract: Generally, the public-key cryptographic schemes base their security on the difficulty of solving hard
mathematical problems. The number of such problems currently known is relative reduced. Therefore the
further investigation of mathematical problems with applications in cryptography is of central interest. This
paper explores a new problem based on polynomial composition. We analyze the connections between the
proposed problem and the RSA problem. Adjacent, we derive from it a zero – knowledge identification
protocol. We show that the method allows the definition of a commutative class of polynomials. Based on
this class, a “Diffie – Hellman like” key exchange protocol can be devised. .
1 INTRODUCTION
In cryptography, an asymmetric algorithm is based
on a type of function first suggested by Diffie and
Hellman (Diffie, Hellman, 1976) that has special
properties known as trapdoor one-way functions. A
trapdoor one-way function, if given some additional
secret information, allows much easier computation
of its inverse function. The one-way functions are
based on hard mathematical problems, like factoring
large composites into prime factors or the discrete
logarithm problem.
Nevertheless, the number of hard mathematical
problems with applications in cryptography
currently known is rather reduced. Even considering
the known problems of this type, there are still
questionable items. As an example, the Optimal
Asymmetric Encryption Padding (OAEP) has never
been proven secure against the chosen ciphertext
attack in the adaptive scenario (RSA, 2007).
In this context, the further research of such
problems is of central interest. Similarly, finding
general procedures supporting the study of a larger
class of problems is also important.
The Polynomial Composition Problem (PCP)
was first introduced in (Joye, Naccache, Porte, 2004)
and can be enounced as follows:
Problem 1.
Let P and Q be two polynomials in (Z/nZ)[X]where
n is an RSA modulus. Given polynomials Q and
S:=Q(P), find P.
Joye et al. shown that generally the Polynomial
Composition Problem is easier than the RSA
problem – that is the computation of roots in Z/nZ -
and gave a new version of this problem called
“Reduced Polynomial Composition Problem”
(RPCP), which can be proven to be equivalent with
the RSA problem.
A number of cryptographic algorithms like the
key agreement protocols based on asymmetric
techniques (Menez, van Oorschot, Vanderstone,
1997) require operating in commutative groups. It is
well known that generally, the polynomial
composition is not commutative.
The present paper introduces a new problem
called Polynomial Multi - Composition Problem
(PMCP) based on a commutative class of
polynomials.
In a proper approach, the security of the
cryptographic scheme should be proven in a
mathematical sense, i.e. establishing theorems
claiming that illegal actions such as impersonation
are as difficult as solving a specific problem, whose
difficulty is well-established. Among these
problems, as already mentioned, are integer
factorization, or the computation of discrete
logarithms in a finite group. This will also be the
approach in the present paper, relating the new
269
Daniel Stoleru N. and Valeriu Patriciu V. (2007).
THE POLYNOMIAL MULTICOMPOSITION PROBLEM IN (Z/nZ).
In Proceedings of the Second International Conference on Security and Cryptography, pages 269-272
DOI: 10.5220/0002123402690272
Copyright
c
SciTePress

introduced polynomial multi-composition problem
to the reducible polynomial composition problem
suggested in (Joye, Naccache, Porte, 2004).
Half-way between heuristic validation and
formal proofs are proofs in a model where concrete
objects are replaced by some ideal substitutes.
Applying this paradigm to hash functions for
example, yields the so-called oracle model described
in (Bellare, Rogaway, 1993).
Using the following notation for a polynomial
composed k – times with itself:
43421
4434421
ooo
timesk
timesk
k
PPPPPPP
−
−
=⋅⋅⋅= )...)...((:
)(
(1)
we can enounce the Polynomial Multi –
Composition Problem as follows:
Problem 2.
Let P be a polynomial in (Z/nZ)[X] where n is an
RSA modulus and k a big positive integer,
11 −≤< nk
. Given k and the polynomial
)(
:
k
PS =
find P .
We observe that choosing polynomials of type
)(
:
k
PS =
can lead to the definition of a commutative
class of polynomials. For example, if we consider P,
Q, R polynomials in Z/nZ[X] and
1,1
−
≤
< nlk
integers such that
)(
:
k
PS =
and
)(
:
l
PR =
, then the
polynomials R and S are commutative over Z/nZ.
For any
nZZ /∈
ω
we have
))(())((
)()(
ωω
lk
PPRS =
)()(
)()(
ωω
kllk
PP
++
==
))((
)()(
ω
kl
PP=
))((
ω
SR=
.
(2)
This property allows us to devise a key exchange
protocol based on polynomials in (Z/nZ)[X]
similarly with the Diffie-Hellman key exchange
protocol ((Menez, van Oorschot, Vanderstone, 1997)
Protocol 12.47).
2 ANALYSIS OF THE
POLYNOMIAL
MULTI-COMPOSITION
PROBLEM
In analyzing the security of the PMCP we relate the
suggested problem to the Reduced Polynomial
Composition Problem (RPCP) as given in (Joye,
Naccache, Porte, 2004).
Consider a polynomial
()
[]
XnZZP /∈
, a big
integer r,
11
−
≤
<
nr
and the polynomial
)(
:
k
PS =
.
We can write:
∑
=
=
r
p
t
t
t
XcXS
0
)(
(3)
where
p
p
r
p
i
p
i
tpiii
pii
p
p
t
uu
ii
ii
c L
L
L
L
L
0
21
0
0
2
1
0
0
!!
)!(
∑
=++
−=++
+
+
=
(4)
Intuitively, the hardness of the Polynomial Multi
- Composition Problem depends on how we choose
the polynomial P in (Z/nZ)[X]. Nevertheless,
generally, PMCP cannot be harder than the RSA
Problem.
Example 1.
Consider
0
2
2
)( uXuXP +=
, r = 3 and the PMCP:
“Given
)3(
: PS =
find P”. Then the equations system
given by relation (4) will be in this case:
⎪
⎪
⎪
⎩
⎪
⎪
⎪
⎨
⎧
+++=
+=
+=
=
=
02
2
0
2
2
3
0
3
2
4
00
3
2
2
0
4
2
3
02
4
20
5
2
2
04
6
206
7
28
2
44
26
4
uuuuuuuc
uuuuc
uuuuc
uuc
uc
(5)
After some simple algebraic manipulations we
obtain:
⎟
⎟
⎠
⎞
⎜
⎜
⎝
⎛
−=
8
2
6
4
8
6
2
42 c
c
c
c
c
c
(mod n)
and analogue from the last equation in (5):
2
6
2
82
0
6
6
48
3
8
3
6
0
4
2
4
64 c
cc
u
c
c
cc
c
c
c +
⎟
⎟
⎠
⎞
⎜
⎜
⎝
⎛
−=
(mod n)
(6)
With
80
,, cc K known we can determine u
0
from
equation (6). Then u
2
can be determined through the
direct substitution of u
0
in (5).
Consequently, we need to define a stronger
problem in order to meet the usual cryptographic
requirements. We introduce in the following the
Reducible Polynomial Multi – Composition Problem
(RPMCP).
Problem 3.
Let P be a polynomial in Z/nZ[X] where n is an RSA
modulus and r a big integer
11 −≤< nr
. Given the
(deg(P) + 1) coefficients of
)(
:
k
PS =
find P.
SECRYPT 2007 - International Conference on Security and Cryptography
270
As proven in (Joye, Naccache, Porte, 2004) (see
Theorem 1) the Reducible Polynomial Composition
Problem is equivalent to the RSA Problem. We give
the following result:
Proposition 1. Let P a polynomial in Z/nZ[X] where
n is an RSA modulus, r a big integer
11
−
≤
< nr
,
)(
:
r
PS =
and
)1(
:
−
=
r
PQ
. If the Polynomial Multi –
Composition Problem “given S and r find P” is
reducible then the Polynomial Composition Problem
“given
)(: PQS =
and Q find P” is also reducible.
Proof. (Sketch) We can write the coefficients k
i
of Q
based on the relation (4) for r – 1:
p
p
r
p
i
p
i
ipiii
pii
p
p
i
uu
ii
ii
k L
L
L
L
L
0
21
1
0
0
2
1
0
0
!!
)!(
∑
=++
−=++
−
+
+
=
(7)
for
)deg(0 Qi ≤≤
. Therefore, every k
i
can be written
as a combination of
p
uu ,,
0
K .
On the other hand, if the Polynomial Multi –
Composition Problem is reducible, then the values
of
1)1(
0
1
,,
−−
−r
pp
cc K
can be deduced from
rr
ppp
cc ,,
)1(
1
K
−
−
which is equivalent to deriving the
values of
1)1(0
,,
−−qp
cc K
based on
pqqp
cc ,,
)1(
K
−
and
11
,,
−q
kk K
in the related Polynomial
Composition Problem.
3 CRYPTOGRAPHIC
APPLICATIONS
3.1 A Simple PMCP – based
Identification Protocol
We suggest the following identification protocol
based on PMCP:
In order to set up the system, a Trusted Third
Party (TTP) selects and publishes an RSA modulus
n. Each user chooses a polynomial P in (Z/nZ)[X]
and some big integers q, r and s
1,,1
−
≤
< nsrq
such as q + r = s. Afterwards, the user computes
)(
:
s
PS =
,
)(
:
q
PQ =
and
)(
:
r
PR =
(8)
in (Z/nZ)[X] and registers the polynomials S and Q
and the integers q, r and s with the TTP. S and Q
represent user’s public key and will be made
publicly available. Nevertheless, after calculating R,
the user will keep it secret. P is user’s secret key.
To prove the knowledge of P the user executes l
times the following protocol:
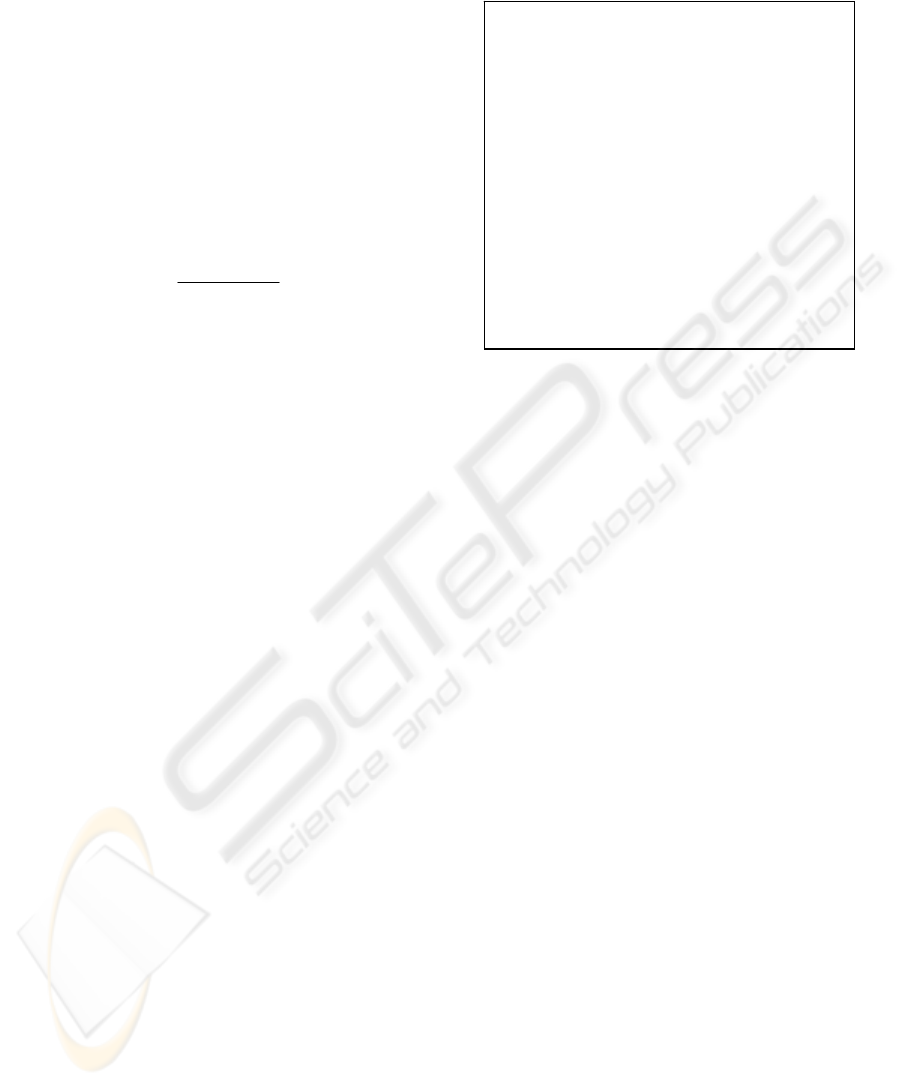
Figure 1: A simple identification protocol.
3.2 A Diffie – Hellman Like Key
Agreement Protocol based on
PMCP
Based on the property (2) we can deduce that the
polynomials defined as
)(
:
k
PS = - with k a big
integer
11
−
≤
<
nk where n is an RSA modulus
and
][/, XnZZPS
∈
- define an abelian finite
group regarding to the polynomial composition.
This property allows us to devise the following
key agreement protocol:
SUMMARY: A and B each send the other one
message over on open channel.
RESULT: shared secret K known to both parties A
and B.
1. One-time setup. An RSA modulus n, an
nZZ /
∈
ω
and a polynomial
])[/( XnZZP
∈
are selected and
published.
2. Protocol messages.
BA →
:
(
)
nP
l
mod
)(
ω
(i)
AB →
:
(
)
nP
r
mod
)(
ω
(ii)
3. Protocol actions.
Perform the following steps each time a shared
key is required.
(a) A chooses a random secret l,
21
−
≤< nl
,
and sends B the message (i).
(b) B chooses a random secret r,
21
−
≤< nr
,
and sends A the message (ii).
1. The prover selects a random
nZZ /
∈
ω
, evaluates
)(:
ω
Sc =
and
sends c to the verifier;
2. The verifier sends to the prover a
random bit b;
3. If
0
=
b
the prover reveals
ω
=t
and the verifier checks
ctS =)(
;
If
1
=
b
the prover reveals
)(
ω
Rt
=
and the verifier checks
ctQ
=
)(
.
THE POLYNOMIAL MULTICOMPOSITION PROBLEM IN (Z/nZ)
271

(c) B receives
)(
)(
ω
l
P
and computes the shared
key as
(
)
nPPK
lr
mod)(
)()(
ω
=
(d) A receives
)(
)(
ω
r
P
and computes the shared
key as
(
)
nPPK
rl
mod)(
)()(
ω
=
.
Note that in the set scenario, the polynomial
])[/( XnZZP ∈
is known but the big integers l and r
are secret. An adversary tapping the communication
between A and B can catch the messages of type (i)
and (ii) sent between the two parties. The adversary
can also calculate
)(
ω
P as P and
ω
are public.
Nevertheless, in order to determine the values l and r
and therefore to be able to determine the shared key
K, she will have to solve a problem equivalent to the
discrete logarithm problem, which is known as being
hart.
4 CONCLUSIONS AND FUTURE
WORK
The present paper introduced a new cryptographic
primitive called Polynomial Multi – Composition
Problem. We shown that this polynomial class
define a commutative group towards polynomial
composition. This propriety gave us the possibility
to define a key exchange protocol. A zero-
knowledge identification scheme based on the
mentioned primitive was also presented.
It is interesting to note that the Polynomial
Composition Problem gives a general framework for
studying a wider class of cryptographic primitives.
We believe that a deeper study of the Polynomial
Composition Problem could lead to a better
understanding of the actual cryptographic problems.
REFERENCES
M. Bellare and P. Rogaway, 1993, Random Oracles are
Practical: A Paradigm for Designing Efficient
Protocols. In Proceedings of the 1st ACM-CCS, pages
62-73. ACM Press, New York.
W. Diffie and M. Hellman, 1976, New Directions in
Cryptography, IEEE Trans. Info. Theory 22(6), pages
644–654.
Marc Joye, David Naccache, and Stéphanie Porte, 2004,
The Polynomial Composition Problem in (Z/nZ)[X],
Article retrieved April 3, 2007 from
http://citeseer.ist.psu.edu/joye04polynomial.html.
Alfred J. Menezes, Paul C. van Oorschot, and Scott A.
Vanderstone, 1997, Handbook of Applied
Cryptography, CRC Press.
RSA report “Recent Results on OAEP Security, study
retrieved May 27, 2007 from
”http://www.rsa.com/rsalabs/node.asp?id=2147.
SECRYPT 2007 - International Conference on Security and Cryptography
272
