
A
GROUP AUTHENTICATION MODEL FOR WIRELESS
NETWORK SERVICES BASED ON GROUP KEY MANAGEMENT
Huy Hoang Ngo, Xianping Wu and Phu Dung Le
Faculty of Information Technology, Monash University, Australia
Keywords:
Group authentication, group key management, forward secrecy.
Abstract:
Group authentication provides authentication for members of communication group between services and
users in insecure environments such as wireless networks. Most of the group authentication models do not
consider the risk of compromised share secrets in the group under various security threats such as cryptanal-
ysis. Although authentication key exchange in groups can benefit from group key management to minimise
this risk, the group key management schemes are inefficient for authentication services. In this paper, a group
authentication model for wireless networks services using a group key management is presented. The group
key management is specially designed with forward secrecy and session keys for efficient and secure key
exchange. Based on this secure session keys, a dynamic group authentication scheme provides a secure and
efficient group authentication for wireless network users and services.
1 INTRODUCTION
Authentication is the major security component in
information systems. Authentication protects the
systems from unauthorised accesses from malicious
sources. The classical authentication scheme deals
with two trusted parties communicating over an inse-
cure environment. In this scheme, these parties share
secrets with each other. By proving the ownership of
the secrets, a party can create the trust on its iden-
tity. The source of the authentication can be either
an individual user, an application or a single service
in the system. Normally the target of the authenti-
cation process is a service. Each service maintains a
database of its own user identities and authentication
keys. The cost to maintain the user identity databases
for different services is expensive especially in wire-
less networks.
Instead of verifying individual identities as in
the classical authentication scheme, group authenti-
cation allows members to prove their memberships of
the group from a centralised user identity database.
There has been much research on group authentica-
tion. In (Dijk et al., 1998), (Hanaoka et al., 2002),
and (Zwierko and Kotulski, 2005)schemes, the secret
sharing is used to provide group authentication. How-
ever, these schemes did not consider the compromised
secret keys risk. Using the non compromised authen-
tication keys assumption, Homage (Handley, 2000)
utilised Diffie-Hellman and group signatures to pro-
vide a secure group authentication. However, Jaul-
mes and Poupard(Jaulmes and Poupard, 2002) men-
tioned the vulnerability of forgeable valid proof and
compromised identity. Martucci et. al. (Martucci
et al., 2004) proposed the use of hash function to
calculate the challenge and authentication key from
the time stamp. To prevent replay attacks, clock syn-
chronisation and limited challenge life time were em-
ployed. On one hand, the pre-shared key as input for
hash function becomes vulnerability cryptanalysis at-
tacks. Group key management (Rafaeli and Hutchin-
son, 2003), (Challal and Seba, 2005), (Amir et al.,
2001) is another approach of authentication key ex-
change in group authentication. On the other hand,
the previous group key management mechanisms did
not focus on efficiency for group authentication.
In this paper, we present a group authentication
model based on group key management. In this group
authentication model, the users and services are di-
vided into clusters. Each cluster has its own secure
policy and requirement. A modified version of group
key management is employed to exchange authentica-
tion keys in the clusters. This group key management
is built for efficient authentication key exchange in
wireless networks. Users can anonymously authenti-
cate to services in the same cluster by using the cluster
182
Hoang Ngo H., Wu X. and Dung Le P. (2008).
A GROUP AUTHENTICATION MODEL FOR WIRELESS NETWORK SERVICES BASED ON GROUP KEY MANAGEMENT.
In Proceedings of the Tenth International Conference on Enterprise Information Systems - ISAS, pages 182-188
DOI: 10.5220/0001687201820188
Copyright
c
SciTePress
authentication key from the group key management.
The rest of the paper is organised as follows. Sec-
tion 2 introduces the authentication model. The group
key management is illustrated in section 3. Section 4
presents the group authentication module. The model
is analysed in section 5. A case study is investigated
in section 6 and section 7 concludes the paper.
2 THE GROUP
AUTHENTICATION MODEL
The group authentication model contains two main
components: a group authentication module and an
authentication group key management. The authenti-
cation module uses the group key management to ex-
change authentication keys of the clusters. Based on
these keys, the authentication module provides a se-
cure and anonymous authentication service to mem-
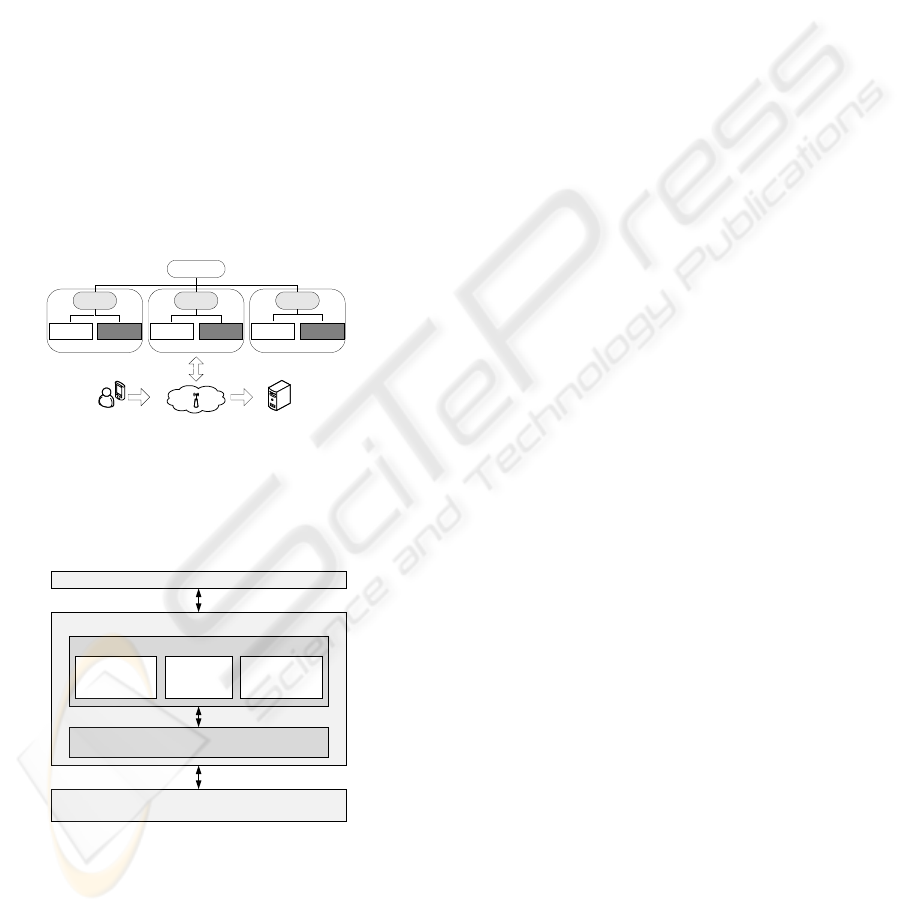
bers in the clusters. The model is shown in Fig 1.
Cluster
3
Cluster
2
Cluster
1
GKM
C
2
C
3
C
1
UG
1
SG
2
UG
2
SG
3
UG
3
Services
User
SG
1
Figure 1: Group Authentication Model.
The group authentication module and the group
key management are two different layers in the group
authentication framework. These layers are shown in
Fig 2.
Group Authentication Framework
Group Authentication Module
Authentication Group Key Management
Users , Applications and Services
Wireless Network Architecture and Technology
Authentication
Scheme
Rekeying
Scheme
Policy
Manager
Figure 2: Group Authentication Architecture.
3 THE GROUP KEY
MANAGEMENT
Group key management is the most important frame-
work for secure group communication. In (Chal-
lal and Seba, 2005), Challal and Seba implied that
the major problems of group key management are
confidentiality, authentication, watermarking and ac-
cess control. Based on the above problems, there
are five security requirements for group key man-
agement: forward secrecy, backward secrecy, colli-
sion freedom, key independence and minimal trust.
Among these security requirements, forward secrecy
and backward secrecy are very important for group
communication confidentiality. Forward secrecy im-
plies that users who have left the group cannot obtain
any future key. Backward secrecy means that users
who have joined the group cannot obtain any previ-
ous keys.
Although authentication is among the issues for
group key management, most of proposed group key
management protocols focus on data confidentiality
which requires both forward secrecy and backward
secrecy. On the other hand, authentication does not
need backward secrecy. In other words, users that join
a group can obtain the previous keys. These keys are
neither re-used for authentication nor used for encryp-
tion sensitive data in group communication. There-
fore, when a new user or a service joins a group, the
re-keying process in group key management is un-
necessary. Based on this characteristic, an efficient
group key management for group authentication is
proposed.
3.1 Notation
• ug
1
,ug
2
: groups of users.
• sg
1
,sg
2
: groups of services.
• c
1
,c
2
: clusters.
• s
11
,s
12
: services in service group sg
1
.
• u
21
,u
22
: users in user group ug
2
.
• K
S11
,K
S12
,K
S22
: individual authentication key of
services.
• K
U12
,K
U21
,K
U22
: individual authentication key
of users.
• K
S1
,K
S2
: group key of service group sg
1
and sg
2
.
• K
U1
,K
U2
: group key of user group ug
1
and ug
2
.
• K
C1
,K
C2
: the current cluster authentication keys
of cluster c
1
and c
2
.
• GKM: group key management server.
• N
1
,N
2
: nonces (random number).
• {x}k: message x is encrypted by the key k.
• h(x,y): hash function of message x and key y.
• DK: distributed key
A GROUP AUTHENTICATION MODEL FOR WIRELESS NETWORK SERVICES BASED ON GROUP KEY
MANAGEMENT
183

• SK
1
,SK
2
,...SK
N
: session keys
• A → B{message}: A sends message to B using
unicast.
• A ⇒ B{message}: A sends message to B using
multicast or broadcast.
3.2 The Group Key Management
Architecture
In this group key management framework, the ser-
vices and users are divided into n clusters. The ser-
vices in a cluster are grouped into one service group.
Users in this cluster are also grouped into one user
group. Users in the cluster C
1
share the cluster au-
thentication key K
C1
to authenticate to the service
group sg
1
in this cluster. In this group key manage-
ment, one user may present in several groups. This
situation illustrates that one user can have authorisa-
tion access to multiple services in different service
groups in different clusters. The group key manage-
ment can have a tree structure as shown in Fig 3. The
second level of the tree encloses the clusters.The third
level of the tree contains the users and service groups.
Each service group ug
1
is depicted by a key K
S1
. Each
user group ug
2
is depicted by a key K
U2
. Service
group sg
1
shares the cluster key K
C1
with user group
ug
1
in the second level.
k
root
k
C1
k
C2
k
S1
k
U1
k
S2
k
U2
k
S11
k
S12
k
U11
k
U12
k
S21
k
S22
k
U21
k
U22
s
11
s
12
u
11
u
12
s
21
s
22
u
21
u
22
Figure 3: Group Key Management Tree.
Because services in the system have higher priv-
ilege than the users, the services are separated from
the users in the cluster. If an application wants to join
the service group in a cluster to provide the service,
it has to authenticate itself to the group key manage-
ment first. Therefore, not anyone in the system has
authorisation to provide services. These services are
divided into different clusters because of their differ-
ent requirements of security. Each service group has
different security policy and requirements. The ser-
vices in the same group share the same security policy
and requirements. Therefore, users in group ug
1
can
use the same key K
C1
to authenticate to different ser-
vices in the same service group gs
1
. These services
share not only the same authentication key K
C1
but
also the same security requirements.
In the following sections, we explain the proce-
dures of the group key management for authentica-
tion in wireless networks. Similar to the group key
management in (Damodaran et al., 2006), the session
keys are used for three operations in this group key
management: join, leave and manual rekeying.
3.2.1 Service Join
When the service s
22
wants to join a service group,
it sends the join request to the key server. Attached
to the join request is a distributed key DK. The dis-
tributed key DK is a key generated by the service and
exchanged with the key server. This key is used to
compute session key SK. When the key management
server receives the join request, it generates and sends
back to the user a random number N
1
as a challenge.
Both service s
22
and key management server compute
the set of session keys {SK
1
, ... SK
N
} from the dis-
tributed key DK as following procedures:
SK
1
= h(DK,K
S22
)
SK
2
= h(DK,SK
1
)
...
SK
N
= h(DK,SK
N−1
).
The session keys in the key set {SK
1
,...SK
N
} are
used to encrypt communication messages between the
service and key management server. These session
keys can be used once. Service s
22
encrypts the chal-
lenge N
1
by the first session key SK
1
. Key manage-
ment server sends back to the service a response with
the current cluster keys K
C2
and the current group key
K
S2
. Because the backward secrecy is not required to
prevent service from accessing previous group com-
munication, rekeying after joining in other group key
management architecture is redundant. The messages
between service and key management server are illus-
trated as follows:
1. s
22
→ GKM : { join, s
22
,sg
2
,{DK}K
S22
}
2. GKM → s
22
: {N
1
}
3. s
22
→ GKM : {N
1
,N
2
}SK
1
4. GKM → s
22
: {N
2
+ 1,K
C2
,K
S2
}SK
2
3.2.2 User Join
The join operation of users is similar to that of ser-
vices. If u
12
wants to join user group ug
1
, four fol-
lowing messages are used.
1. u
12
→ GKM : { join, u
12
,ug
1
,{DK}K
U12
}
2. GKM → u
12
: {N
1
}
3. u
12
→ GKM : {N
1
,N
2
}SK
1
4. GKM → u
12
: {N
2
+ 1,K
C1
,K
U1
}SK
2
ICEIS 2008 - International Conference on Enterprise Information Systems
184

3.2.3 Service Leave
Opposite to join operation, forward secrecy is very es-
sential to leave operation. When a member in service
group leaves the group, it is warranted that the ser-
vice cannot receive future group communication de-
tails. In other words, the service can no longer get
future authentication keys to provide services to that
group. The leave operation can either be invoked by
services or initiated by the key server. The leave op-
eration for services has two steps. The first step is the
leave request. The second step is the rekeying pro-
cedure. The rekeying procedure only affects one ser-
vice group and its correlative user group in the same
cluster. If s
11
wants to leave group, it sends a leave
request encrypted by the next session key SK
S11
in
the session key set of service s
11
. The next step is
to rekey the group key K
S1
and cluster key K
C1
. The
key management server sends to all other members in
the service group using uni-cast the new keys K
S1
and
K
C1
encrypted by the next session keys in their ses-
sion key sets. When all the keys in the key set are
used, the service generates a new distributed key DK
itself and sends it to the key management server to in-
voke the operation that re-generates the new session
key set. In the rekeying process, the key server also
multi-casts the new cluster key to user group ug
1
. The
messages in the system is described as follows:
1. s
11
→ GKM : {leave,sg
1
,s
11
,h(K
C1
,SK
S11
)}
2. GKM → s
12
: {newK
S1
,newK
C1
}SK
S12
3. GKM ⇒ u
11
,u
12
: {newK
C1
}K
U1
3.2.4 User Leave
The leave operation for users is also similar to the
leave operation for services. It can also be either in-
voked by the users or initiated by the key server. The
first step is the leave request. The second step is the
rekeying procedure. The rekeying procedure warran-
tees that the users leaving the group can no longer au-
thenticate to the services in that group. If u
21
wants to
leave the group ug
2
, the following messages are sent
for rekeying:
1. u
21
→ GKM : {leave,ug
2
,u
21
,h(K
C2
,SK
U21
)}
2. GKM → u
22
: {newK
U2
,K
C2
}SK
U22
3. GKM ⇒ s
21
,s
22
: {newK
C2
}K
S2
3.2.5 Manual Rekeying
The manual rekeying is a group and cluster keys re-
newing process in the system. It is not related to either
join or leave operation. After a number of authentica-
tion attempts, group and cluster keys used for authen-
tication become vulnerable under key compromised
and cryptanalysis attack risks. This manual rekeying
operation helps the system to reduce the above risks.
The more regularly rekeying process is invoked, the
more secure the group authentication model is. How-
ever, regular rekeying also uses a great deal of re-
source in the authentication model. Different groups
of services require different security policies. The
policy manager in the group authentication frame-
work determines when and how the manual rekeying
to be invoked to obtain the security and efficiency re-
quirement for services. The rekeying process of clus-
ter C
1
is specified as the following messages.
1. GKM ⇒ sg
1
: {newK
C1
}K
S1
2. GKM ⇒ ug
1
: {newK
C1
}K
U1
4 THE GROUP
AUTHENTICATION MODULE
The group authentication module has two parts: an
authentication protocol and a policy manager. The
authentication module uses the cluster keys from the
group key management to perform group authenti-
cations to the services. The policy manager decides
when the manual rekeying operation is invoked to re-
new cluster and group keys to obtain the most suitable
security and efficiency requirement.
4.1 The Group Authentication Protocol
4.1.1 Notation
• U: user.
• S: service.
• K
C
: the current authentication key.
• h(X ,Y ): hash function of message X with the key
Y
• K
U
S: the session key.
4.1.2 The Group Authentication Protocol
In the group authentication protocol, user U uses the
secrets K
C
to authenticate to the services in the same
clusters. These keys are the current and previous clus-
ter keys from the group key management. There-
fore, all the members in user group and service group
share this secrets as authentication keys. Based on
this group authentication keys, U can authenticate to
the services without revealing its identity. The au-
thentication protocol is shown below:
1. U
→
S
:
N
1
2. S → U : {N
1
+ 1,N
2
,K
US
}K
C
A GROUP AUTHENTICATION MODEL FOR WIRELESS NETWORK SERVICES BASED ON GROUP KEY
MANAGEMENT
185

3. U → S : {N
2
+ 1}K
US
U generates a nonce N
1
and sends it to S as the
authentication request. S generates a session key K
US
and sends to U with the nonce N
1
and another nonce
N
2
as a challenge encrypted by the cluster key K
C
.
U decrypts the challenge to extract the session key
K
US
and N
2
. He trusts the session key K
US
. The last
message is the exchange of nonces N
2
, encrypted by
the session key K
US
. The nonces exchange process is
used to prove the ownership of the session key K
US
and cluster K
C
.
4.2 Policy Manager
The services in different clusters have different se-
curity and efficiency requirements. Security require-
ments often conflict with efficiency requirements.
Higher security requirement often demands many
system resources. The policy manager is the com-
ponent that sets the policy when the cluster and group
keys are manually rekeyed to match with the security
and efficiency requirements of each cluster. For each
cluster in the system, the policies can be set for rekey-
ing as follows:
• after each authentication request to a service in a
group.
• after a constant period of time (depend on the
number of users and services in the group and the
average amount of authentication).
• both two above conditions.
5 DISCUSSION AND ANALYSIS
We highlight the important issues that are raised in the
group authentication model: security and efficiency.
5.1 Security
The security of this authentication model is analysed
through its two layers: the authentication module and
group key management. The security of the group
authentication module heavily depends on the group
authentication keys. This group authentication keys
are managed by the group key management.
5.1.1 Security of Group Key Management
The proposed group key management inherits the se-
curity features of the previous group key management
schemes. Although this group key management does
not enforce backward secrecy, it satisfies the follow-
ing security goals:
1. Non Group Key Confidentiality: Members
who are not members of the group cannot obtain the
shared secrets group keys within the group. Therefore
a principal that does not belong to a cluster cannot
obtain the current cluster key. When another principal
leaves a group, he is also no longer able to obtain the
current cluster key.
2. Key Authenticity: The key management server
only accepts requests from authenticated group mem-
bers.
The final issue of group key management for
group authentication is the risk of compromised clus-
ter keys from replayed and cryptanalysis attacks. In
order to obtain the current cluster key to authenti-
cate, attackers capture messages from group key oper-
ations to extract the cluster key. However, the cluster
key is manually rekeyed after a period. This opera-
tion can reduce the risk of compromised cluster keys
from cryptanalysis attacks. Although the cryptogra-
phy using in group key management is symmetric
encryption, cryptographic keys encrypting the clus-
ter keys are short term session keys. If a session key
is compromised, it has a new value in the next mes-
sage. Even in the worst scenario, when an attacker
has guessed all the correct values of session keys, the
current set of session keys is expired after a period of
time. A new set of session keys is generated for the
authorised parties. This feature can minimise the risk
of compromised session keys and cluster keys.
5.1.2 Security of the Authentication Module
The following notations description are the BAN
notations (Rubin and Honeyman, 1993) using in
analysing the security of the protocol.
Notation
• U
K
US
←−→ S: U and S may use the shared key K
US
to
communicate.
• S|≡X: S believes X.
• ](X ): X is fresh. X has not been sent before in any
messages.
• S Z⇒ X: S has jurisdiction over X: S’s beliefs about
X should be trusted.
• U /Y : U has received message Y . U can read and
repeat Y .
• U |∼X : U has sent a message including the state-
ment X. U believes X when he sends it.
The group authentication protocol is analysed using
BAN Logic(Burrows et al., 1990) . First, it is trans-
formed into the idealised form.
1. U → S : N
1
ICEIS 2008 - International Conference on Enterprise Information Systems
186

2. S → U : {N
1
,N
2
,U
K
US
←−→ S}K
C
3. U → S : {N
2
,U
K
US
←−→ S}K
US
To analyse the security of the group authentication
protocol, we make the following assumptions:
U |≡U
K
C
←→ S S|≡U
K
C
←→ S
U |≡ S Z⇒ U
K
←→ S S|≡U
K
US
←−→ S
U |≡ ](N
1
) S|≡](N
2
)
Once we have the assumption and the idealised
form, we can start to verify the authentication proto-
col. Sending message 2 leads to:
U / {S|∼(N
1
,N
2
,U
K
US
←−→ S)}K
C
in more details
U |≡ S|∼(N
1
,N
2
,U
K
US
←−→ S)
This message contains nonce N
1
that U believes to
be fresh. So we can deduce:
U |≡ ]((N
1
,N
2
,U
K
US
←−→ S))
Hence, U knows S exists. Using the nonce verifi-
cation rule, we have:
U |≡ S|≡(N
1
,N
2
,U
K
US
←−→ S)
or
U |≡ S|≡U
K
US
←−→ S
From the jurisdiction rules, we can deduce
U |≡U
K
US
←−→ S (1)
In the third message, again, since S believes that
nonce N
2
is fresh, we can deduce
S|≡U |≡(N
2
,U
K
US
←−→ S)
and make the conclusion
S|≡U |≡U
K
US
←−→ S
or
S|≡U
K
US
←−→ S (2)
From (1) and (2), we can obtain the final belief to
conclude that the protocol achieves its goals.
5.2 Efficiency
The efficiency of the authentication model is also de-
rived from two main components: the group key man-
agement and the authentication module.
5.2.1 The Efficiency of Group Key Management
The following problems are discussed:
1. Rekeying is a process to re-new authentication
and group keys after being used. This process
reduces the compromised key risks and other se-
curity risks. Not many group authentications
have this process. In comparison with the ap-
proaches using centralised and synchronised dis-
tributed key database, the rekeying process in
group key management is clearly more secure and
efficient with the hierarchical tree structure.
2. In comparison with other group key manage-
ments, the proposed group key management has
more efficient join operation without rekeying
overhead.
3. Handoff is a regular problem in wireless net-
works. Handoff can cause major perfomance
header in rejoining to a group key management.
The rejoin procedure after an handoff often causes
the major overhead from rekeying to warrantee
backward secrecy in the other group key man-
agements. However, this group key management
does not have backward secrecy. Therefore hand-
off does not affect the efficiency of this group key
management and the group authentication model.
5.3 Anonymity
Group authentication provides users and other ser-
vices partially anonymous authentication to the ser-
vices. Although group members have to authenticate
individually with the group key management, their
identities are not revealed to the services in the same
cluster which they authenticate to. The only informa-
tion that services can extract from the authentication
messages includes the group keys and group, clus-
ter identities. Therefore the group authentication can
provide anonymous authentication to the services.
For some services that require clear identity for
authentication, the authentication can combine the
group identity with the individual identity for authen-
ticate individually to the services. This combination
can form two-factor authentication for the services.
6 CASE STUDY
In this section, an authentication system for a por-
tal of wireless multimedia content services is exam-
ined. In this system, users are allowed to access ser-
vices through paid memberships from different wire-
less service providers. Services are provided by dif-
ferent companies. These services are classified into
four groups of services based on the package that
the portal provides. The service group one contains
online news, music, mobile games and video on de-
mand. These services are provided by a wireless me-
dia company. This company also provides the ser-
vices in service group two as an advanced package.
Service group two has wireless news, music, video
on demand, children education games, and wireless
TV. Service group three includes stock exchange in-
formation, currency exchange and real estate services.
The last group encloses adult services from an adult
entertainment company for restricted memberships.
A GROUP AUTHENTICATION MODEL FOR WIRELESS NETWORK SERVICES BASED ON GROUP KEY
MANAGEMENT
187
The group authentication model is applied to provide
anonymous authentication for the portal. The user is
only required to authenticate to the group key man-
agement at portal once. After that he is allowed to
access the different services from different groups de-
pend on his subscription.
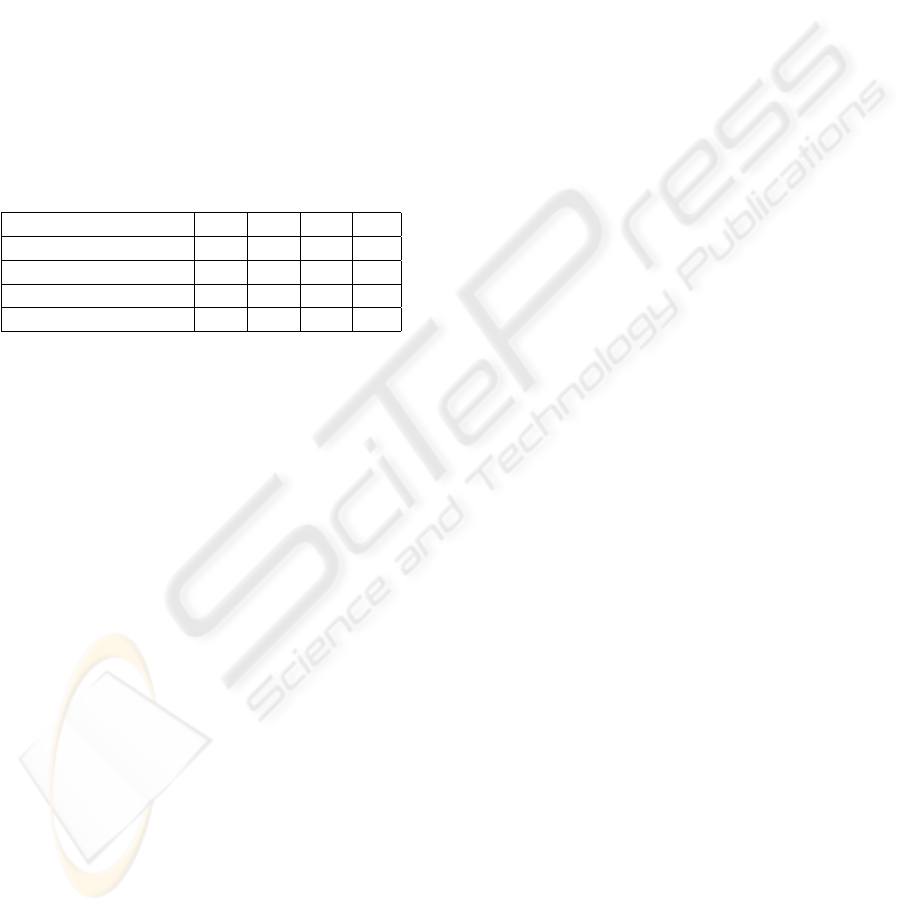
The following table compares the advantages and
disadvantages between
1. this group authentication,
2. Zwierko’s group authentication scheme (Zwierko
and Kotulski, 2005),
3. Damodaran’s group key management for group
authentication (Damodaran et al., 2006), and
4. the traditional individual authentication Kerberos
model in this case study.
Table 1: Comparison between different group models.
1 2 3 4
Anonymity Yes Yes Yes No
Number of Messages 3 6+ 3 6+
GKM Yes No Yes No
Rekey Yes Yes Yes No
The comparison table shows that this group au-
thentication model is more efficient in rekeying and
authentication operations in groups. It is also more
secure by using session keys in every authentication
session. Besides, it also can provides the anonymity
which is very important in wireless networks commu-
nities. In this model, not all processes can provide
services freely to the system. They have to authenti-
cate to the group key management to obtain the right
to provide the services to a certain group. So that an
adult entertainment service cannot provide access to
the users in the normal children entertainment groups.
7 CONCLUSIONS
The paper proposes a group authentication using for-
ward secrecy group key management. The forward
secrecy group key management is used for secure
authentication key exchange. Based on this effi-
cient group key management, the group authentica-
tion protocol uses three messages to provide anony-
mous group authentication for the users and the ser-
vices in the same clusters. Depending on the secu-
rity and efficiency policy of each cluster, the rekey-
ing operation is invoked to renew the previous clus-
ter and group keys. The rekeying operation makes
the group authentication keys become one time ses-
sion group authentication keys. The rekeying process
in group key management can minimise the compro-
mised authentication key risks from security threats.
The authentication model can be applied securely and
efficiently for group of services and users in wireless
networks.
REFERENCES
Amir, Y., Nita-Rotaru, C., and Stanton, J. R. (2001). Frame-
work for authentication and access control of client-
server group communication systems. Lecture Notes
in Computer Science, 2233:128.
Burrows, M., Abadi, M., and Needham, R. (1990). A logic
of authentication. ACM Transactions on Computer
Systems, 8(1):18–36.
Challal, Y. and Seba, H. (2005). Group key management
protocols: A novel taxonomy. International Journal
of Information Technology, 2(1):105–118.
Damodaran, D., Singh, R., and Le, P. D. (2006). Group
key management in wireless networks using session
keys. Proceedings of the Third International Confer-
ence on Information Technology: New Generations,
pages 402–407.
Dijk, M. V., Gehrmann, C., and Smeets, B. (1998). Un-
conditionally secure group authentication. Designs,
Codes and Cryptography, 14(3):281–296.
Hanaoka, G., Shikata, J., Hanaoka, Y., and Imai, H. (2002).
Unconditionally secure anonymous encryption and
group authentication. Lecture Notes In Computer Sci-
ence, 2501:81–99.
Handley, B. (2000). Resource-efficient anonymous group
identification. Financial Cryptography, 1962:295–
312.
Jaulmes, E. and Poupard, G. (2002). On the security of
homage group authentication protocol. Lecture Notes
In Computer Science, 2339:106–116.
Martucci, L., Carvalho, T., and Ruggiero, W. (2004). A
lightweight distributed group authentication mecha-
nism. INC2004 - Fourth International Network Con-
ference, pages 393–400.
Rafaeli, S. and Hutchinson, D. (2003). A survey of key
management for secure group communication. ACM
Computing Surveys, 35(3):309–329.
Rubin, A. D. and Honeyman, P. (1993). Formal methods for
the analysis of authentication protocols. (CITI Tech-
nical Report 93-7).
Zwierko, A. and Kotulski, Z. (2005). A new protocol
for group authentication providing partial anonymity.
Next Generation Internet Networks, pages 356–363.
ICEIS 2008 - International Conference on Enterprise Information Systems
188
