
CRC-16-BASED COLLISION RESOLUTION IN EPCGLOBAL
CLASS1 GENERATION2 RFID SYSTEMS
Jun-Bong Eom and Tae-Jin Lee
School of Information and Communication Engineerin, Sungkyunkwan University, Suwon 440-746, Korea
Keywords: Anti-collision algorithm, CRC-16, EPCglobal Class1 Generation2 protocol, RFID, RN16.
Abstract: The 900 MHz UHF passive RFID systems have drawn attraction because they have long access distance
and rapid identification speed. One of the most representative international standards is EPCglobal Class1
Generation2 (EPCglobal Gen2). RN16 which is used in the EPCglobal Gen2 standard assists a reader to
detect tag collision rapidly, but it may be removed because it does not have information of products. In this
paper, we propose an algorithm to replace RN16 with CRC-16 to reduce the identification time. We show
that CRC-16 has similar characteristics of RN16 and our proposed scheme reduces the number of bits
required for one tag identification.
1 INTRODUCTION
Radio Frequency Identification (RFID) is a
technology by which a reader recognizes the
information of objects to which tags are attached for
wireless communications with the reader. RFID
systems have become prevalent in supply chain
management, in manufacturing process, in the
industries to require the identification of products,
and so on, because they are able to transmit much
data rapidly with the use of wireless channel. Indeed
they are increasingly being used for automated
identification systems and come into the spotlight
for the realization of the ubiquitous society (R. want,
2006).
In RFID systems, a basic process for tag
identification is that if a reader queries tags for
information, the tags receiving the query signal
transmit their IDs to the reader. When only one tag
is in the reading range of the reader, tag
identification is very simple and easy. When,
however, many tags are in the reading range, tag
collisions may occur due to the simultaneous
transmission of their information. Thus an efficient
RFID tag anti-collision algorithm is necessarily
required in RFID systems to identify a lot of objects
in real time. One of the most popular algorithms
used for tag anti-collision is Framed-slotted ALOHA
(FSA).
In FSA-based tag anti-collision algorithms, to reduce
the probability of tag collision, a frame is divided
into several timeslots. And each tag selects
randomly one timeslot for the transmission of the
ID. When a tag transmits its information in a
timeslot, a reader can read the tag successfully.
When, however, a timeslot experiences collision by
more than one tag, the reader can not identify their
information. Unread tags must retransmit their
information in the next frame. This is inefficient due
to waste of collision timeslots. Also if there are
many idle timeslots in a frame, it is not efficient too.
The throughput of FSA may become low as the
number of tags increases. Thus it is necessary to
change the next frame size appropriately for high
efficiency after estimating the number of tags in the
reading range as in Dynamic FSA (DFSA) (S. Lee, S.
Joo and C. Lee, 2005). EPCglobal Class1
Generation2 (EPCglobal Gen2) (EPCTM Radio-
frequency Identification Protocols Class-1
Generation-2 UHF RFID Protocol For
Communications at 860MHz-960MHz Version1.0.9,
2005) is a representative international standard using
DFSA.
Unlike general DFSA having fixed timeslots for
success, idle, and collision, DFSA of EPCglobal
Gen2 adopts different timeslots. To reduce the waste
of time when a collision occurs, a relatively short
Random Number with 16 bits (RN16) is transmitted
before Electronic Product Code (EPC). Depending
on the success or failure of RN16 reading, a reader
decides whether it reads in the EPC of a tag or not.
The RN16 does not contain any information of a
61
Eom J. and Lee T. (2008).
CRC-16-BASED COLLISION RESOLUTION IN EPCGLOBAL CLASS1 GENERATION2 RFID SYSTEMS.
In Proceedings of the International Conference on Wireless Information Networks and Systems, pages 61-65
DOI: 10.5220/0002021700610065
Copyright
c
SciTePress
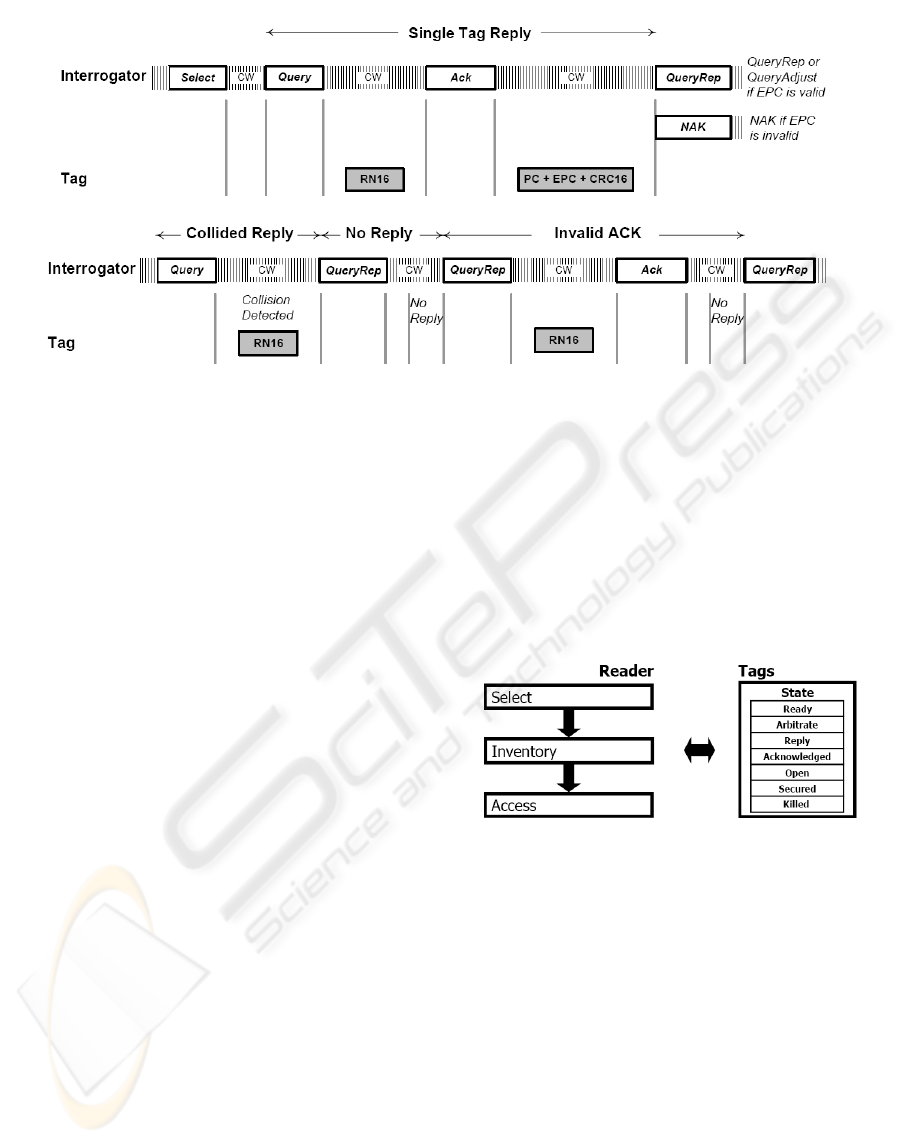
Figure 1: Tag identification mechanism using RN16 and having different time duration for success, idle, and collision.
product, and may consume extra time. Thus it would
be useful to reduce it if possible.
In this paper, we propose to use CRC-16 instead
of RN16 in EPCglobal Gen2 protocol, resulting in
reduced identification time. The outline of this paper
is organized as follows. In Section II, we summarize
the EPCglobal Class1 Generation2 standard. Our
proposed scheme is presented in Section III.
Performance evaluation and comparison via
simulations are presented in Section Ⅳ, and finally
Section Ⅴ draws conclusion.
2 EPCGLOBAL C1 GEN2
In EPCglobal Gen2, RN16 is used by a tag when it
sends the information to a reader. If long Protocol
Control (PC), EPC, and CRC-16 are transmitted
directly without transmitting short RN16 first, when
a collision occurs, it may waste time since another
PC, EPC and CRC-16 needs to be transmitted.
Figure 1 shows the mechanism using RN16 with
different time duration in success, idle, and collision.
In Figure 1, each tag randomly selects a timeslot,
and it transmits the 16 bit RN16 in the timeslot. If
the reader does not detect any such signal, it tries to
read tags in the next timeslot after waiting for few
time slots. If the reader identifies RN16 successfully,
it attempts to read the tag information by sending an
ACK command to the tag. When, however, RN16 is
not identified correctly, or there is no reply to ACK,
the reader comes to a conclusion that a collision
occurs.
In EPCglobal Gen2, communication between a
reader and tags is conducted through the steps of
Figure 2. A reader uses a Select command to select a
particular slot in which it identifies a tag. To identify
tags, the reader transmits some commands to the
tags in the Inventory round. The Access state of a
reader means that the reader reads from or writes to
individual tags after the tags are uniquely identified
Do not add any text to the headers (do not set
running heads) and footers, not even page numbers,
because text will be added electronically.
Figure 2: Reader/Tag operation and the state of tags.
The tags receiving the Select command prepare
for operation and stay at the Ready state until it
receives a Query command. The tags which receive
the Query command generate their slot counters
(0~2
Q
-1), i.e., RN16, depending on the Q value
(0~15) during the Query command by their Random
Number Generator (RNG). When the value of the
slot counter of a tag is decremented to 0, the tag
goes to the Reply state and backscatters its RN16 to
the reader. If the reader does not detect a collision of
RN16, it issues an ACK command including the
RN16 of the tag. After the ACK is received, the tag
changes its state to the Acknowledged state. If the
received ACK is valid, the tag backscatters its PC,
EPC and CRC-16, and the reader conducts the CRC
(Reader)
(Reader)
WINSYS 2008 - International Conference on Wireless Information Networks and Systems
62
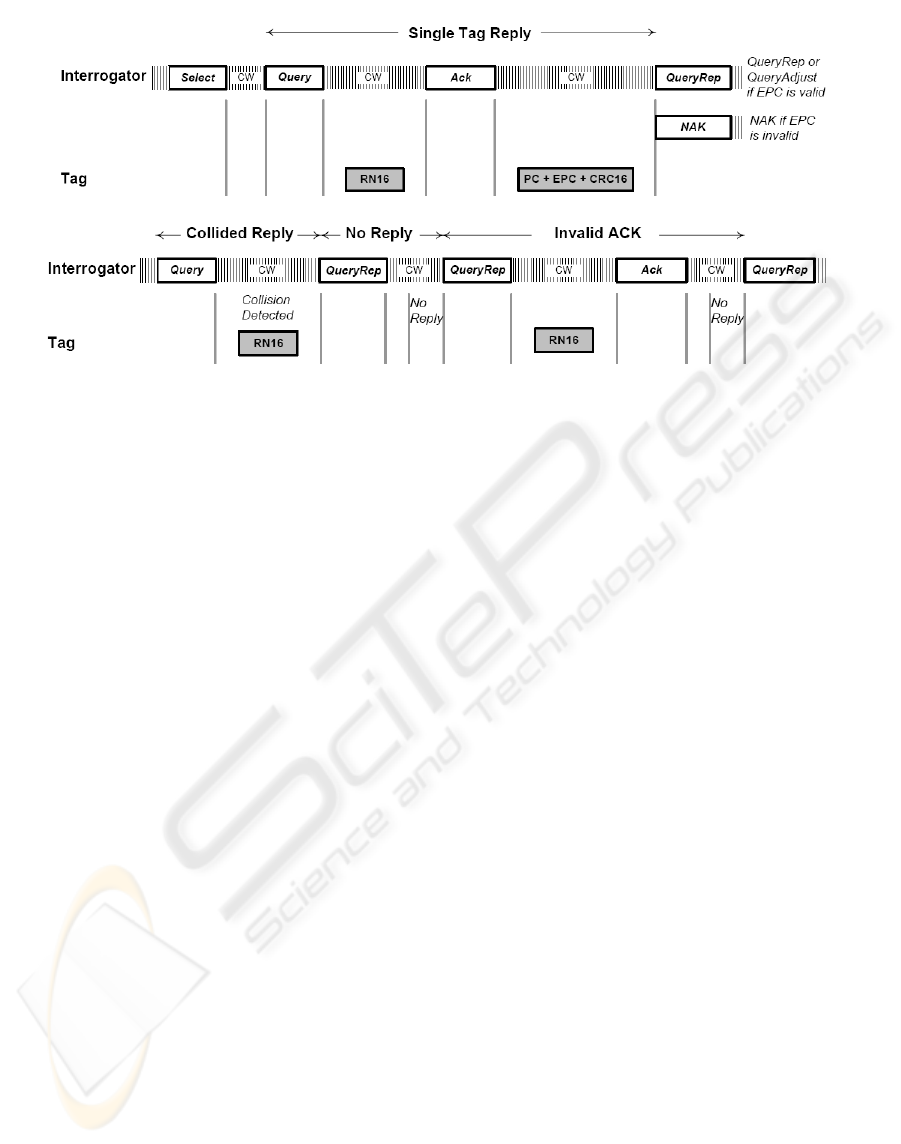
Figure 3: The proposed tag identification mechanism using CRC-16 and having different time duration for success, idle,
and collision.
check. Without any error, the reader identifies the
information of the tag successfully. Until the value
of the slot counter becomes 0, tags stay in the
Arbitrate state, holding state. And, the tags in the
Arbitrate state do not participate in the current
Inventory round until their slot counters become 0.
The tags shall decrement their slot counters by 1,
every time they receive a QueryRep command. If a
round to identify tags is over, but there are still
unread tags, the reader broadcasts a QueryAdj
command to the tags.
3 PROPOSED IDENTIFICATION
SCHEME
In this paper, we propose to use CRC-16 which has
the similar role of RN16 in the EPCglobal Gen2
protocol. In EPCglobal Gen2, when tags transmit
their information to a reader, RN16 shall be
generated before tags backscatter the information.
RN16 generated by RNG shall meet the following
randomness criteria (J. Choi, D. Lee, H. Lee, 2007).
▪ Probability of a single RN16:
The probability of an RN16 shall be bounded by
0.8/2
16
< P[RN16 = j] < 1.25/2
16
, where j is a
number created by RNG.
▪ Probability of simultaneously identical
sequences:
For tag population up to 10,000 tags, the
probability that any two or more tags
simultaneously generate the same sequence of
RN16s shall be less than 0.1%.
▪ Probability of predicting an RN16:
An RN16 shall not be predictable with the
probability greater than 0.025%.
We first investigate the property of CRC-16
whether it resembles that of RN16, and present the
proposed identification mechanism
3.1 A Uniformly Random
Characteristics of CRC-16 as in
RN16
All burst errors of length less than or equal to the
degree of the polynomial can be detected by CRC (B.
A. Forouzan, 2003). In CRC-P, assuming random
information of P bits and applying CRC-P
mechanism to the information, the CRCs from two
different random information should be different. If
the CRCs of two different information bit sequences
are the same, a burst error can not be detected by the
CRC check when one information bit sequence
becomes the same with another by channel error. It
is against the fact that all burst errors of length less
than or equal to the degree of P can be detected. For
example, let us consider two arbitrary information
part of PC+EPC, 1111000011110000 and
1100110011001100, and assume that they have the
same CRC R made by the CRC generator. When a
sender transmits the 1111000011110000 and R to a
receiver, and the altered information,
1100110011001100 and R by channel error, is
received, the receiver can not identify the error.
Thus each information with sequential P bits should
have only one corresponding and unique CRC-P.
(Reader)
(Reader)
CRC-16-BASED COLLISION RESOLUTION IN EPCGLOBAL CLASS1 GENERATION2 RFID SYSTEMS
63
In EPCglobal Gen2, a tag uses CRC-16 to check
the integrity of PC and EPC, backscattered from the
tag to a reader. And, as we examined before, all of
the CRC-16s are uniquely different for every
sequential 16 bits. It means that the probability of
any CRC-16 is 1/2
16
and it has uniformly random
characteristics as in RN16. Thus, we can know that
probability of a single CRC-16 is bounded by 0.8/2
16
< P[CRC-16=j] < 1.25/2
16
, where j is a CRC-16
number, like that of a single RN16. It also meets the
second characteristic of RN16, because the number
of tags that all 16 bits of CRC-16 are the same is
found by multiplying 10,000 by the probability of a
single CRC-16 and it is less than 0.1% of 10,000
tags. When a reader identifies tags, the tags might be
randomly selected and the probability of predicting a
CRC-16 might be 1/2
16
. And the probability that a
CRC-16 is predictable is not greater than 0.025%.
3.2 Proposed Identification Mechanism
using CRC-16
Figure 3 shows a simple proposed mechanism using
CRC-16 instead of RN16. In the proposed scheme,
slot counters of tags are also determined and
decremented by Query, QueryRep or QueryAdjust
commands. When the value of the slot counter of a
tag is 0, the tag backscatters the CRC-16 to the
reader. Note that the CRC-16 is generated from the
PC+EPC. After the tag backscatters its CRC-16, if
the reader receives CRC-16 of the tag correctly
without collision, the reader requests PC and EPC
information of the tag by transmitting an ACK
command to the tag. The reader receiving PC and
EPC conducts the CRC check with the already
backscattered and received CRC-16. In the case that
a collision of CRC-16 occurs or an invalid ACK
command is transmitted to the tag, the tag does not
reply to the reader. And, if there is no reply during
the predetermined time, the reader tries to read the
tag with the next smallest slot counter.
4 PERFORMANCE
EVALUATION
We evaluate the performance of the mechanism
using proposed CRC-16 and the existing mechanism
with RN16. We set the length of tag ID and the
commands of a reader as follows (see Table 1).
In the EPCglobal Gen2 standard, the Q selection
algorithm that tags choose Q values from Query
command is used for tag anti-collision. The Q
selection algorithm based on Framed Slotted
ALOHA (FSA) adjusts the number of timeslots in
the next round as the number of collision and idle
timeslots and tags select different random counter
values again from the reader reissuing Query or
QueryAdjust command. However, the Q selection
algorithm is not specified in the standard (G.
Khandelwal, K. Lee, A. Yener, and S. Serbetli,
2007). So we apply Dynamic Framed Slotted
ALOHA (DFSA) instead of the Q selection
algorithm to solve the problem of tag collision. And
we assume that the reader can knows the number of
tags accurately.
Table 1: The length of the tag ID and the reader
commands.
Command No. of bits Command No. of bits
RN16 16 bits Select 44 bits
PC 16 bits QueryAdj 9 bits
EPC 64 bits QueryRep 4 bits
Query 22 bits ACK 18 bits
NAK 8 bits RN16 16 bits
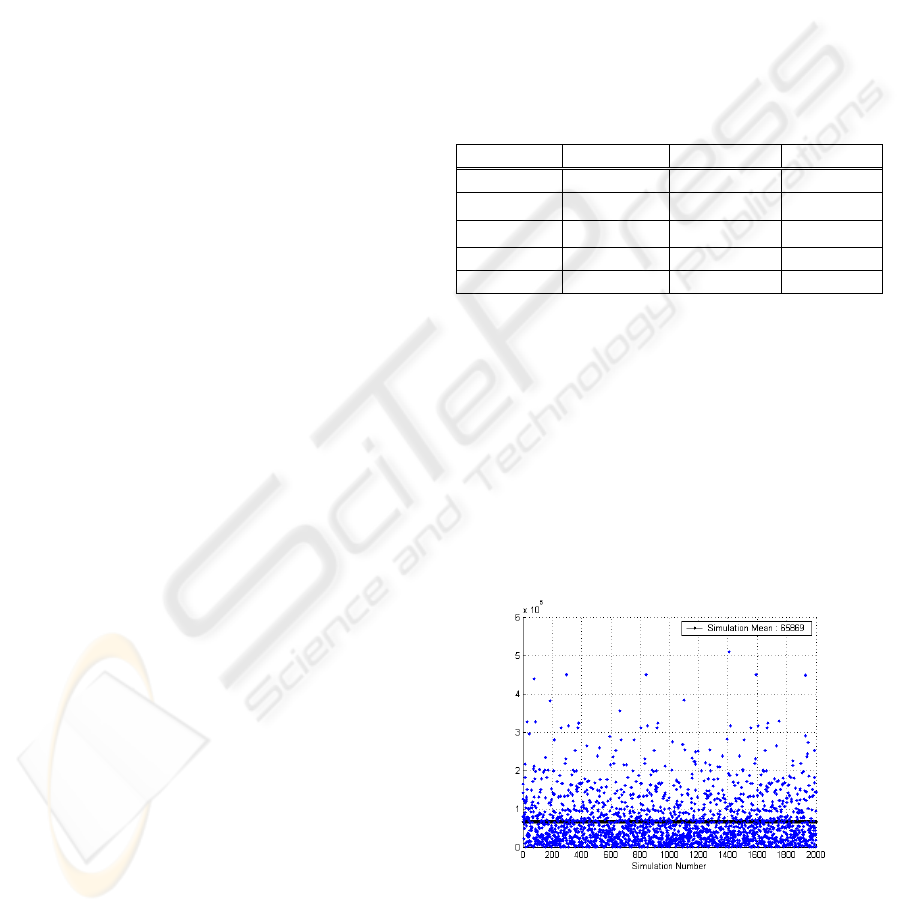
Figure 4 depicts that CRC-16 is uniformly
random. When an arbitrary CRC-16 is given, the x
axis denotes the simulation number, and y axis
represents how many repetitions are needed until the
CRC-16 of PC and EPC of a randomly selected tag
and the given CRC-16 becomes the same. If CRC-16
is uniformly random, the same CRC-16 might be
repeated every 2
16
=65536 on average. The
difference between
the expected mean, 65536, and
the simulation mean, 65869, is very close within
about 0.5%. Thus, we can verify the uniformly
random characteristics of CRC-16.
Figure 4: The uniformly random characteristics of CRC-
16.
Figure 5 shows the number of used bits per one
tag identification with the varying number of tags
under no channel error. When the number of tags is
WINSYS 2008 - International Conference on Wireless Information Networks and Systems
64
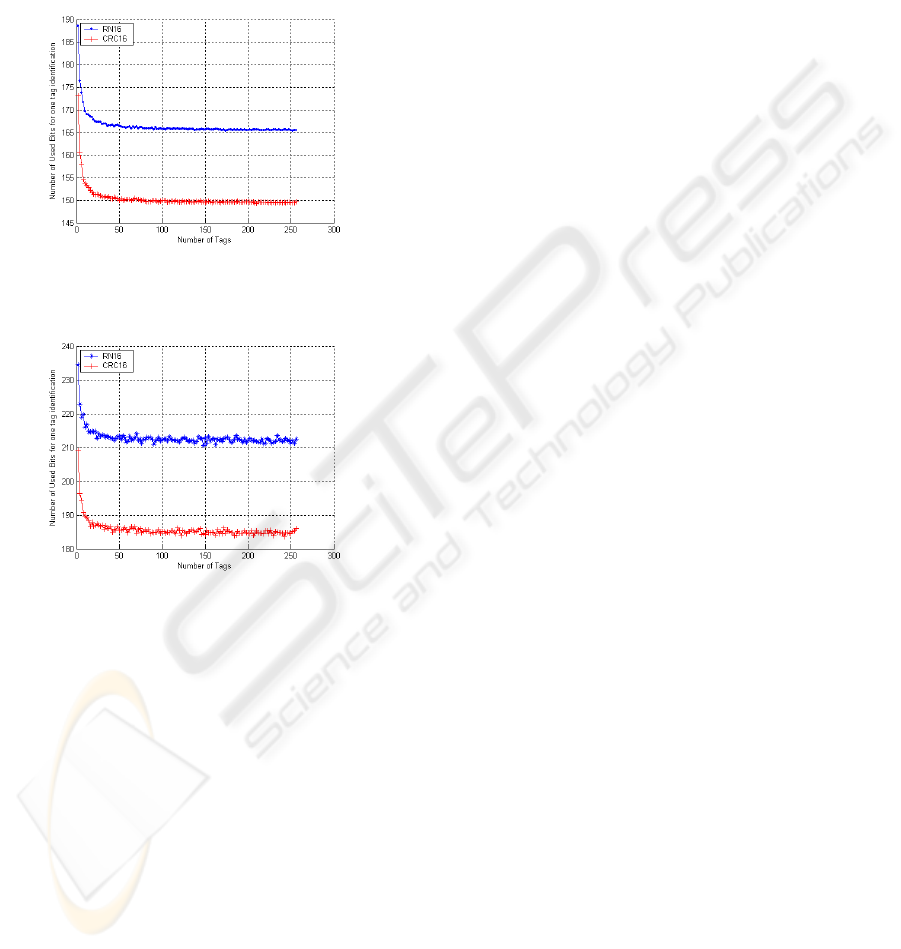
256, the proposed scheme needs 149.7 bits for one
tag identification and the scheme using RN16
requires 165.48 bits for one tag identification. The
difference between the number of bits required in
the proposed scheme and that in the existing scheme
is about 16 bits because it does not use as many bits
as RN16. Thus the performance of the proposed
scheme is improved up to 9.53%.
Figure 5: The number of used bits for one tag
identification with the varying number of tags, PER=0.
Figure 6: The number of used bits for one tag
identification with the varying number of tags, PER=0.3.
There may be lots of channel errors in RFID
systems because of low power backscattering of
tags. Figure 6 demonstrates how much improvement
in our proposed scheme is achieved under error-
prone environment. The figure shows the number of
bits per one tag identification with the varying
number of tags. Under channel error environment,
when the packet error rate (PER) is 0.3 and the
number of tags is 256, the proposed scheme uses
186.09 bits for one tag identification, while the
scheme using RN16 uses 212.62 bits for one tag
identification. This result also depicts that the
proposed scheme consumes less time than the
scheme using RN16, about 16 bits because 16 bits of
RN16 are saved as in the case of no channel error.
Thus, we can see that our proposed scheme is shown
to improve the performance about 12.5%.
5 CONCLUSIONS
We have proposed a simple and efficient tag
identification mechanism using CRC-16 instead of
RN16 in EPCglobal Gen2. In this paper, we have
verified that CRC-16 is uniformly random like
RN16, and thus it can provide the similar role of
RN16. According to the simulation results under
both error-free and error-prone environment, the
proposed algorithm using CRC-16 instead of RN16
requires less time than that using RN16 as in
EPCglobal Gen2
ACKNOWLEDGEMENTS
This work was supported by Korea Research
Foundation grant funded by the Korean Government
(MOEHRD) (KRF-2006-311-D00683), by a grant
under the Brain Korea 21 Initiative of the Korean
Ministry of Education and Human Resources, and
by the Korea Science and Engineering Foundation
(KOSEF) grant funded by the Korea government
(MOST) (No. R01-2006-000-10402-0).
REFERENCES
R. Want, “An Introduction to RFID Technology,” IEEE
Pervasive Computing, vol. 5, no. 1, pp. 25-33, Jan.
2006.
“EPCTM Radio-frequency Identification Protocols Class-1
Generation-2 UHF RFID Protocol For
Communications at 860MHz-960MHz Version1.0.9,”
EPCglobal, Jan. 2005.
S. Lee, S. Joo and C. Lee, “An Enhanced Dynamic
Framed Slotted ALOHA Algorithm for RFID Tag
Identification,” in Proc. of MobiQuitous, pp. 166-172,
Jul. 2005.
G. Khandelwal, K. Lee, A. Yener, and S. Serbetli, “ASAP:
A MAC Protocol for Dense and Time-Constrained
RFID Systems,” EURASIP Journal on Wireless
Communications and Networking, vol. 2007, Article
ID 18730, 13 pages, 2007. doi:10.1155/2007/18730,
2007.
B. A. Forouzan, Data Communications and Networking,
Third Edition, pp. 249-253, 2003.
J. Choi, D. Lee, H. Lee, “Query Tree-Based Reservation
for Efficient RFID Tag Anti-Collision,” IEEE
Communications Letters, Vol.11, No.1, pp. 85~87,
Jan. 2007.
CRC-16-BASED COLLISION RESOLUTION IN EPCGLOBAL CLASS1 GENERATION2 RFID SYSTEMS
65
