
INTRUSION K-COVERAGE IN WIRELESS SENSOR
NETWORKS
Amir Yahyavi
ECE Department, University of Tehran, North Kargar, Tehran, Iran
Laleh Roostapour, Roohollah Aslanzadeh, Mehdi Dehghan
CEIT Department, Amirkabir University of Technology, Tehran, Iran
Nasser Yazdani
ECE Department, University of Tehran, North Kargar, Tehran, Iran
Keywords: k-Coverage, Wireless Sensor networks, Surveillance and Monitoring, Sleep Scheduling.
Abstract: One of the main applications of Wireless Sensor Networks is surveillance and monitoring. Providing and
maintaining the required coverage over the area of an intrusion (or other events of our choice) is of great
importance. The network should be able to provide different levels of coverage based on application needs
and reconfigure itself while ensuring energy efficiency. In this paper we present a dynamic approach to
provide asymptotic k-coverage over the area of an intrusion. This is a probabilistic approach which creates
full coverage over the surveillance zone and provides k-coverage over the area of an event. Our simulations
show that this approach is able to provide the requested coverage while consuming less than a third of the
static approaches. Also due to probabilistic nature of this approach communication overhead is much lower
than deterministic methods.
1 INTRODUCTION
Wireless Sensor Networks usually consist of a large
number of small sensor nodes with limited energy
source which use a low-bandwidth wireless radio for
communication. A sensor node can only last 100-
120 hours on a pair of AA batteries in the active
mode and battery capabilities are only doubled every
35 years(Ye et al., 2002). This makes energy
efficiency the main challenge in application design
for sensor networks.
Putting sensors to periodic sleep in dense sensor
networks has been suggested as a way to increase
the network longevity. (Wang and Xiao, 2005)
Sensor nodes in the sleep mode consume only 0.1%
of the energy consumed in the active mode (Kumar
et al., 2006). Low duty cycle results in higher delay,
lower coverage and connectivity in exchange for
power efficiency. Nodes in the sleep mode are
unable to detect events in their sensing range and are
unable to receive or forward any packets (MAC
layer can have a different duty cycle from the
sensing device which we will discuss later).
Several scheduling schemes have been suggested
to minimize the effect of sleeping nodes on the
desired parameter (delay, connectivity, etc) in the
network (Lu et al., 2005), (Wang et al., 2003).
Coverage is one of the important parameters that are
affected by the scheduling scheme.
In surveillance and monitoring applications, it is
usually required to have at least k sensors cover
every point in the surveillance zone (k-Coverage). In
dense networks (Ye et al., 2002) where there are
more than k sensors present in each area, sensor
nodes are put to low duty cycle. This raises the
question of which nodes should be active in each
cycle in order to maintain the same coverage
(Kumar et al., 2006), (Abrams et al., 2004) while
other nodes in the area go to sleep. It means that we
need a coordination function (Chen et al., 2002)
between neighbor nodes to determine the state of
each node in each cycle in a way that the total
41
Yahyavi A., Roostapour L., Aslanzadeh R., Dehghan M. and Yazdani N. (2008).
INTRUSION K-COVERAGE IN WIRELESS SENSOR NETWORKS.
In Proceedings of the International Conference on Wireless Information Networks and Systems, pages 41-46
DOI: 10.5220/0002024900410046
Copyright
c
SciTePress

number of sensors to cover the neighborhood is
approximately k.
The need for a mechanism to dynamically
configure the coverage provided according to the
needs of the application was mentioned in (Wang et
al., 2003). Dynamic configuration of sensor network
helps the network to adapt to different applications’
requirements and maximizes the energy efficiency.
2 RELATED WORKS
(Tian and Georganas, 2002) present a deterministic
method for providing coverage on the surveillance
zone. This method guarantees that the original
sensing coverage is maintained after the redundant
nodes are turned off. This approach assumes that all
nodes have it’s and it’s neighbors location
information. It also requires techniques to estimate
the direction of the received signal which may
require more than one antenna.
(Wang Rui et al., 2006) presents an Ant Colony
method for self organization of sensor networks.
Each sensor is regarded as an immobile ant. Each
ant at each cycle wakes up with probability . Upon
detection of an event the ant lays pheromone which
is diffused to its immediate neighbours. Neighbour
ants that receive this pheromone will increase the
probability of waking up at the next cycle. Based on
the accumulated amount of received pheromone
each node calculates the probability of going to
sleep in the next cycle. This method increases the
percentage of useful nodes (nodes that have detected
an event) in the network. This approach doesn’t
provide guaranteed detection of events.
Most deterministic methods such as (Wang et al.,
2003), (Tian and Georganas, 2002), (Ye et al., 2002)
use an eligibility rule to turn off the redundant nodes
in the area. In order to determine which nodes can be
turned off they either require the location
information of their neighbors or they need to probe
the area for other active sensors. This imposes a
higher communication and computation overhead in
comparison to probabilistic approaches.
In (Kumar et al., 2006) boundary conditions to
have k-coverage in a mostly sleepy network in three
distributions (Grid, Random Uniform, Poisson) are
presented. We use the equations presented in
(Kumar et al., 2006) to dynamically calculate the
probability of waking in the sensor nodes which is
discussed further below.
3 DYNAMIC K-COVERAGE
3.1 Problem Definition and
Assumptions
A set of N sensors },...,,{
21 n
ssss
=
in a two
dimensional area A are distributed using Random
Uniform Distribution, Grid Distribution or Poisson
distribution. All sensors have the same sensing range
r. Sensor nodes have periodic sleep/awake cycles in
which a sensor node turns its sensing device on or
off. Duty cycle of the transmission device is
controlled by the MAC protocol.
Duty cycle of sensing device in turn follows the
scheme by the wakeup probability in each cycle
which our scheme assigns to each node.
Our assumption about number of deployed
sensors, probability of parallel occurrence of events
in the network and availability of location
information are similar to (Yahyavi et al., 2008).
Similar to (Yahyavi et al., 2008), we provide 1-
coverage over the entire surveillance zone. If an
intruder in the surveillance zone is detected the
wakeup probability is adjusted to provide asymptotic
k-coverage in the effective area of the intruder (a
circle around the intruder with radius , nodes in this
area are able to detect the intruder if they are active).
We use boundary conditions presented in (Kumar et
al., 2006) to determine the wakeup probability
required for different levels of coverage.
Consider that a function
)(np
φ
is slowly growing
if it is monotonically increasing and
))(log(log(npO
,
and goes to infinity as
∞→n
. Let
)log(
)(
2
np
rnp
nc
π
=
(1)
For the Random Uniform Distribution and
Poisson Distribution, for some
)(np
φ
if
)log(log
))log(log()(
)(
np
npknp
nc
+
≥
φ
(2)
Then all the points are almost always k-covered
as n approaches infinity (Kumar et al., 2006). Where
n is the number of sensors deployed, p is the
probability of being active in each cycle, r is the
sensing radius of each sensor, and k is the level of
coverage. For Grid Distribution for some
)(np
φ
if
)log(
))log(log())log(1)((
1)(
np
npknppnp
nc
++
+≥
φ
(3)
Then all the points are almost always k-covered
as n approaches infinity. (Kumar et al., 2006)
WINSYS 2008 - International Conference on Wireless Information Networks and Systems
42

Similar to (Kumar et al., 2006), since we
assumed that the number of deployed sensors is
sufficiently large, boundary conditions (2) and (3)
hold. These boundary conditions are used to
calculate the required wakeup probability of nodes
(for a fixed number of deployed nodes) to provide a
certain level of coverage. Goal is to find the
minimum probability that satisfies above boundary
condition for the required k. Minimizing the
satisfying probability lowers the number of active
sensors in each cycle and results in higher energy
savings (while providing k-coverage).
3.2 The Basic Model
In order to be able to detect any events in the
surveillance zone we need to have at least one sensor
cover every point in the surveillance zone. To
calculate the required wakeup probability to achieve
1-coverage from conditions (2) and (3) each node
should know the distribution type and the number of
deployed sensors. These parameters can be flooded
into the network after it has been deployed. The
required k should also be flooded in the network
along with these parameters. In case these
parameters change (the required k or n) they should
be re-flooded into the network.
All nodes primarily set their wakeup probability
to 1-coverage level. As an intruder enters the area
the only active sensor in that area issues a broadcast
message to alert neighbor nodes about the intruder.
Since MAC layer does not follow our sleep schedule
the detecting node may not be able to send the
ALERT message immediately and will have to wait
till the active period of MAC layer begins. All
neighbor nodes that hear this broadcast message
increase their wakeup probability to k-coverage
level. Therefore the number of active sensors in the
next cycle is increased to approximately k nodes.
In case an active node with wakeup probability
level k-coverage doesn’t detect an intruder it reduces
its wakeup probability for the next cycle to 1-
coverage level.
3.3 Misplaced K-Coverage Problem
Since only nodes in the communication range of the
first node that has detected the intruder can hear its
broadcast message and set their wakeup probability
to k-coverage level, some nodes in the effective area
of the intruder may not hear the ALERT message.
Also the intruder might be moving and the detecting
node may not be able to send the ALERT message
until the end of its MAC layer sleep period.
Therefore all nodes in the effective area of the
intruder may not hear the ALERT message. We call
this the misplaced k-coverage problem (Figure 1.a).
To address this problem, we present three
solutions; each one is more suitable for a different
situation and application.
3.3.1 Covered Effective Area Estimation
One of the methods to solve the misplaced k-
coverage problem is to choose a higher wakeup
probability so that the number of active nodes in the
effective area of the intruder is increased. This
solves the misplaced k-coverage problem but
increases the energy consumption in comparison to
the basic model. The number of sensor nodes that
are in the effective area of the intruder and in
communication range of the detecting node is related
to the movement speed of the intruder and the
density of nodes in the area. The faster the intruder
moves the less the number of nodes in the effective
area that can hear the ALERT message.
If the sensor node is able to determine the
location of intruder, the actual number of sensors
that can hear the ALERT message can be calculated:
=−=
∫
−
dxxrs
d
r
2
0
22
4
))
2
1(sin2sin()
2
1(sin2
1212
r
d
r
r
d
r −−−
−−
(4)
Where d is the distance from intruder to the
sensor node at the time of sending the ALERT
message.
Where d is the distance from intruder to the sensor
node at the time of sending the ALERT message.
Figure 1: (a) A randomly distributed wireless sensor
network and misplaced K-Coverage problem, (b) the
Effective Covered Area.
Therefore the number of sensors in the range of
ALERT message is:
ρ
×
=−
s
k
eragek )covPr(
(5)
(a)
(b)
2
d
r −
0
r
22
xry −±=
INTRUSION K-COVERAGE IN WIRELESS SENSOR NETWORKS
43

Where is the area that is covered by ALERT
message and
ρ
is the density of nodes
)(
A
n
. In our
simulations we assumed that the sensor node does
not have location and in a pessimistic guess
considered that only 75% of the effective area is
covered by the ALERT message.
3.3.2 Delayed Reduction
As mentioned in our basic model we reduce the
wakeup probability level of a sensor that has heard
ALERT message to 1-coverage level in case it does
not detect the intruder in the following cycle.
In the delayed reduction model each node
calculates and store k wakeup levels
},...,2,1{ k
. In
case the sensor node does not detect an intruder in
the cycle after receiving an alert message it reduces
its wakeup probability by only one level. Since the
node doesn’t decrease its level to 1-coverage
immediately we call this approach the delayed
reduction method.
This method is most useful when several
intrusions with the same movement pattern occur.
For example in border monitoring usually several
consecutive intrusions occur in the same area. In this
model after an intrusion occurs the network in the
intrusion’s area remains alert for the possible
consecutive intrusions.
3.3.3 Diffusion Model
In the diffusion model all active nodes that have
heard an ALERT message will rebroadcast the
ALERT message. In the Diffusion Model the
ALERT message also contains an alert level. Nodes
that hear this message set their wakeup probability
level to the level determined by the message.
In case a node detects the intruder it broadcasts a
message with alert level k otherwise it reduces the
alert level received by one level and rebroadcasts the
alert message. Similar to Delayed Reduction model
nodes decrease their wakeup probability level by one
level in each cycle.
In case a node receives several alert messages it
chooses the maximum alert level received as its alert
level. If a node receives an alert level lower than its
current wakeup probability level it will not
rebroadcast the ALERT message since all its
neighbor nodes already have equal or higher wakeup
probability level. This situation can happen in case
there is more than one intruder in the sensing area
and it has already caused higher wakeup probability
level in that area (Figure 2).
DiffusionModel
Dela
y
edReductionModel
k‐2
k‐1
k
k‐2
k‐1
k
Figure 2: Wakeup probability levels in Diffusion Model
and Delayed Reduction Model.
This approach is more suitable for situations
where the intruder’s movement is unpredictable and
high coverage on the intruder is required. This
approach provides higher coverage and reliability in
exchange for higher messaging and computational
overhead. The probability level in the intruder’s
effective area is almost always at least k.
Several methods can be used to reduce the
messaging overhead of this approach. For example if
the number of ALERT messages that a node hears is
more than a certain threshold it does not broadcast
an ALARM message. In case location information is
available ALERT messages from nodes closer than a
certain distance will not be rebroadcasted.
3.4 MAC Support
Several MAC protocol with energy saving features
have been proposed. Sensor nodes have different
energy consumptions in off, listening, receiving and
transmission modes (Chen et al., 2002). Putting the
transceiver to sleep also reduces the energy loss due
to overhearing avoidance.
Our approach requires support from the MAC
layer to make sure that neighbor nodes can hear each
other’s ALERT messages. IEEE 802.11 always
keeps the radio transceiver active which allows the
sensor node to send an ALERT message as soon as
an intruder is detected. On the other hand IEEE
802.11 has very high energy consumption. MAC
protocols that have Sleep/Active periods should
provide synchronous wakeup of neighbor nodes so
that at the end of sleep period nodes are able to send
the ALERT messages. S-MAC (Ye et al., 2004) and
T-MAC (Dam and Langendoen , 2003) support such
synchronous wakeups. We assume that reader is
WINSYS 2008 - International Conference on Wireless Information Networks and Systems
44
familiar with S-MAC (For further information
please refer to (Ye et al., 2004)).
Since after the initial synchronization period in
S-MAC the SYNC period is rarely used (to
resynchronize the schedules) we use this period for
our broadcast messages. In case there is a SYNC
packet waiting to be sent we can piggy back our
ALERT on the SYNC message. Otherwise an
independent ALERT message is created and sent
(RTS/CTS period can be similarly used).
In case the MAC protocol of our choice doesn’t
support synchronized wakeups of neighbor nodes, in
order to ensure that all neighbor nodes hear the
broadcast message, the node has to wake up at the
wakeup time of each one of its neighbors and
rebroadcast the ALERT message which increases
the energy consumption.
4 ENERGY CONSUMPTION AND
COVERAGE ANALYSIS
Dynamic reconfiguration of wakeup probability in
the area of an intrusion can provide significant
energy savings. Since the whole surveillance zone is
not k-covered number of active sensors in the
network is much less therefore overall energy
consumption of the network is substantially
decreased. Information required to calculate the
wakeup probability levels should only be flooded
once in the network. Probability levels are also
calculated and stored once at the beginning of
network’s deployment.
In the Effective Covered Area Estimation and
Delayed Reduction model the only messaging
overhead for dynamic reconfiguration is the ALERT
message sent by the first detecting node. Since the
ALERT message is a very small packet and may be
piggybacked this overhead is negligible. On the
other hand in Diffusion Model each node
rebroadcasts the ALERT message with a lower alert
level which poses higher messaging overhead.
Since our approach is probabilistic it doesn’t
need any location or probing information unlike
(Wang et al., 2003), (Tian and Georganas, 2002), (Ye
et al., 2002) to provide the requested coverage. Also
in case better and tighter boundary conditions for
wakeup probability to provide k-coverage are found
they can be easily replaced with current ones.
5 SIMULATION RESULTS
We evaluated different approaches presented in this
paper by simulation. Sensor network is deployed in a
mm 150150
×
area. Sensing and communication range
of nodes is 4m. Higher communication range than
sensing range helps the ALERT message to cover a
larger area. Static k-coverage calculates the wakeup
probability needed to provide k-coverage and
assigns this probability to all of the deployed nodes.
This method is compared to our dynamic k-coverage
approach and different solutions to solve the
misplaced k-coverage problem are compared. Each
simulation is run ten times and the requested
coverage in all simulations is 8-coverage (some
simulation results are not included due to space
limitations).
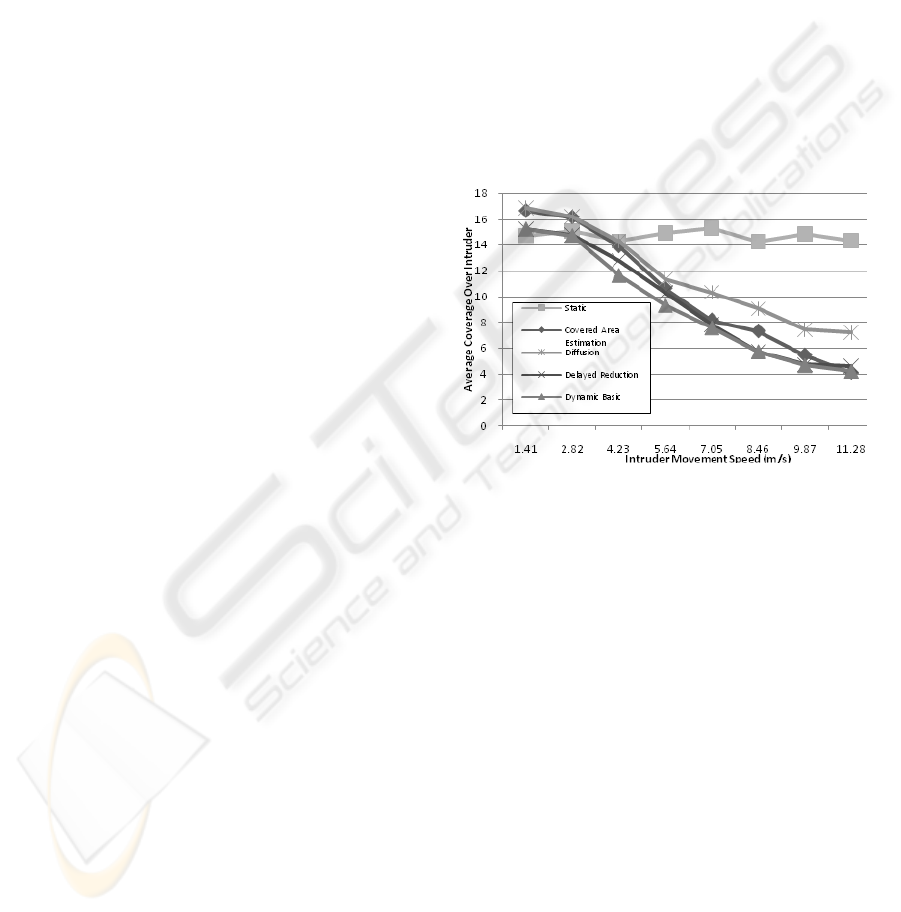
Figure 3: Average Coverage over an intruder for different
speeds.
Figure 3 shows how average coverage provided
by each method changes as the movement speed of
an intruder increases. As expected Static k-coverage
has the highest stability at the cost of higher energy
consumption. Diffusion Model and Covered Area
Estimation both provide high coverage for low
movement speeds but as the speed increases
Covered Area Estimation’s average coverage shows
a sharp decrease. This is because actual covered area
by ALERT message becomes smaller than our
guess. Diffusion Model has a more stable behaviour
which comes at the cost of higher messaging
overhead. The effect of misplaced k-coverage
problem on the coverage provided is clear.
Figure 4 compares the average coverage
provided over an intruder by different approaches. It
also shows that average coverage for these methods
doesn’t change as the number of nodes increases.
This means increasing the number of deployed
nodes will directly reduce the wakeup probability
and increase network longevity.
INTRUSION K-COVERAGE IN WIRELESS SENSOR NETWORKS
45

Figure 4: Average coverage over an intruder for different
number of nodes.
Figure 5 shows the average number of active
nodes in each cycle. As shown, to provide the
requested coverage always a fixed number of nodes
are required which means by increasing the number
of deployed nodes wakeup probability is reduced.
The main reason to use dynamic k-coverage is its
power efficiency. The number of active nodes in
each cycle is a very good measure of energy
consumption of each method. All dynamic
approaches wake less than a third of the static
approach.
Figure 5: Average number of active for different number
of nodes.
6 CONCLUSIONS
In this paper we presented a dynamic approach to
provide k-coverage over the area of an intrusion.
This approach provides 1-coverage over the
surveillance zone and k-coverage over the area of an
intrusion. Several solutions for misplaced k-
coverage problem which rises due to the dynamic
nature of approach are discussed. Each solution is
more suitable for a different kind of application. Our
simulations show dramatic improvement in energy
consumption of the network which results in higher
network lifetime. Our approach is completely
compatible with current popular MAC protocols in
WSNs. In this approach nodes do not need any
location information and due to its probabilistic
nature, minimal communication to provide k-
coverage is needed.
REFERENCES
Akyildiz I.F., Su W., Sankarasubramaniam Y., and Cayirci
E., 2002. "Wireless sensor networks: a survey,"
Computer Networks, vol. 38, pp. 393-422.
Chen B., Jamieson K., Balakrishnan H., and Morris R.,
2002, "Span: An Energy-Efficient Coordination
Algorithm for Topology Maintenance in Ad Hoc
Wireless Networks," Wireless Networks, vol. 8, pp.
481-494.
Dam T.V., and Langendoen K., 2003. "An adaptive
energy-efficient MAC protocol for wireless sensor
networks," In Proceedings of the 1st international
conference on Embedded networked sensor systems,
Los Angeles, California, USA: ACM, pp. 171-180.
Kumar S., Lai T.H., and Balogh J., October 2006. "On k-
coverage in a mostly sleeping sensor network,"
Wireless Networks.
Lu G., Sandagopan N., Krishnamachari B., and Goel A.,
"Delay efficient sleep scheduling in wireless sensor
networks, 2005." INFOCOM 2005. 24th Annual Joint
Conference of the IEEE Computer and
Communications Societies. Proceedings IEEE, vol. 4,
pp. 2470-2481 vol. 4.
Tian D. and Georganas N.D., 2002."A coverage-
preserving node scheduling scheme for large wireless
sensor networks," in Proceedings of the 1st ACM
international workshop on Wireless sensor networks
and applications, Georgia, USA: ACM, pp. 32-41.
Wang L. and Xiao Y., 2005. "Energy saving mechanisms
in sensor networks," Broadband Networks, 2005 2nd
International Conference on, pp. 777-785.
Wang Rui et al., 2006. “Swarm Intelligence for the Self-
Organization of Wireless Sensor Network,” In IEEE
congress on Evolutionary Computing, p. 838-842.
Wang X., et al. 2003, "Integrated coverage and
connectivity configuration in wireless sensor
networks," Proceedings of the 1st international
conference on Embedded networked sensor systems,
pp. 28-39.
Yahyavi A. et al., 2008. “DyKCo, Dynamic K-Coverage
in Wireless Sensor Networks,” IEEE International
Conference on Systems, Man, and Cybernetics, to
appear.
Ye F., Zhong G., Lu S., and Zhang L., 2002. "PEAS: a
robust energy conserving protocol for long-lived
sensor networks," Network Protocols, 2002.
Proceedings. 10th IEEE International Conference on,
pp. 200-201.
Ye W., Heidemann J., and Estrin D., 2004. "Medium
access control with coordinated adaptive sleeping for
wireless sensor networks," IEEE/ACM Trans. Netw.,
vol. 12, pp. 493-506.
WINSYS 2008 - International Conference on Wireless Information Networks and Systems
46
