
NFCARE
Possible Applications of NFC Technology in Sanitary Environments
Giuliano Benelli and Alessandro Pozzebon
Department of Information Engineering, University of Siena, Via Roma 56, Siena, Italy
Keywords:
NFC, RFID, Informative Systems, Electronic case history, Electronic medical prescription, Wireless Commu-
nication.
Abstract:
In this paper we discuss the introduction of the NFC technology in the management of the assistance opera-
tions in the hospitals. NFC is a new short range communication system based on RFID technology.
NFC systems can work like traditional RFID systems, where a master device reads some information from a
slave device, but they can also set up a two-way communication between two items. In particular, NFC devices
can be integrated on mobile phones, widely enhancing the intercommunication capabilities of the users.
The introduction of NFC in sanitary environments can help to make safer all the assistance operations. Next
to the realization of a NFC electronic case history, we also studied the realization of electronic medical pre-
scription and the use of this technology for the exchange of patient data between doctors and between nurses,
in order to avoid errors in the attendance operations.
The final idea is to change a mobile phone into an interactive multipurpose assistant for people working in
hospitals or in harness with patients.
1 INTRODUCTION
The acronym NFC stands for Near Fields Communi-
cation and indicates a new communicationtechnology
directly deriving from RFID identification systems.
Like many RFID systems, NFC works at the fre-
quency of 13.56MHz and is based on the physical
principle of inductive coupling.
The main difference between the two systems de-
rives from the fact that, while RFID is strictly an
identification technology, NFC has been studied to be
properly used as a wireless communication technol-
ogy between devices brought to a short distance be-
tween them.
Nowadays many mobile devices producers are be-
ginning to realize phones and PDAs equipped with
NFC circuitry, also providing the software to realize
applications using this technology.
The main fields of application of NFC include
proximity payments, peer-to-peer communication and
obviously, strictly deriving from RFID, access con-
trol.
In sanitary environments RFID has found many
applications: one of these has been the managing and
the identification of patients.
In particular an electronic case history located on
passive RFID bracelets has been studied and realized
in a previous work (Benelli, Parrino and Pozzebon,
2008), showing the benefits deriving from the chance
to get vital information directly form the electronic
support, with a reduction of the times of assistance
and of the risks deriving from human errors.
The idea of this article is to show how much the
performances of RFID systems can be widen moving
to NFC technology, which can be used to execute the
same operations made by mobile RFID devices, but
adding many new functions once unfeasible.
2 NFC TECHNOLOGY
Before talking about how to introduce NFC in sani-
tary environments it’s important to describe its main
technological features.
It’s obviously impossible to speak about NFC without
briefly introducing RFID, which represents a funda-
mental technological background.
In the second subsection are then described the main
characteristics of NFC communication protocol, in
order to understand the various ways of interaction
58
Benelli G. and Pozzebon A. (2009).
NFCARE - Possible Applications of NFC Technology in Sanitary Environments.
In Proceedings of the International Conference on Health Informatics, pages 58-65
DOI: 10.5220/0001546700580065
Copyright
c
SciTePress

between different devices.
2.1 The Origins: RFID
The technological structure of NFC systems is quite
the same as the one of RFID systems. NFC uses the
same physical principles and partly the same kind of
devices.
It’s therefore difficult to understand the structure
and the possible uses of NFC with investigatinga little
the main features of Radio Frequency Identification
technology.
RFID is an automatic identification technology
which uses the electromagnetic field as the mean of
identification (Finzkeller, 2003). Usually RFID sys-
tems are composed by two devices: a Reader, which
generates the interrogating electromagnetic field, and
the Transponder, which is located on the item to be
identified and returns back to the reader the ID (Iden-
tification) code and the additional information.
When the Transponder comes inside the EM
(Electromagnetic) field of the reader it can be inter-
rogated and it can send back the data using the same
field.
There are many kinds of RFID systems, working
at different operativefrequencies. In particular we can
find Low Frequency (125-135kHz), High Frequency
(13.56MHz), Ultra High Frequency (868-915MHz)
and Microwave (> 2GHz) systems.
Every different RFID application needs a particu-
lar care in the choice of the right technological solu-
tion: for example even if Ultra High Frequency sys-
tems can provide large read ranges, they have a lot of
problems od electromagnetic compatibility.
The same happens for the powering methods of
the transponders: in fact we can find passive, active or
semipassive transponders, offering very different fea-
tures. While an active transponder can be read from a
distance ten times wider than a passive one, his higher
price can make it unsuitable in applications in which
the number of items to be identified is very high.
2.2 NFC Technological Features
NFC belongs to the family of RFID, but it has specific
technological features (Innovision, 2007).
It only works at the frequency of 13.56MHz, that
is an unregulated band. This means there aren’tany li-
censes required and restrictions concern only the elec-
tromagnetic emissions, in order to limit the impact of
the system on human body.
Differently from traditional RFID technology,
passive and active devices can be integrated into the
same system.
NFC can reach a maximum read range of around
20cm but common devices are not able to read from
distances larger than 4 or 5cm. The decision to create
products with low read ranges comes not only from
the physic limitations of the technology but also from
the fact that short ranges ensure a bigger protection
from outside intrusions. These requirements mainly
come from the aim to use NFC to implement proxim-
ity wireless payment systems.
NFC devices can currently communicate at three
different speeds, 106kbit/s, 212kbit/s and 424kbit/s
but in the future higher rates will be probably
achieved.
NFC protocol differentiates the device initiating
and controlling the communication, called Initiator
and the device answering the request from the initia-
tor, called Target (ECMA, 2007).
NFC protocol also presents two different opera-
tive modalities: a passive mode, with a single device
generating the field and the other one using this field
to exchange the data, and an active mode, in which
the two devices generate their own EM field.
As a consequence NFC devices have studied to in-
tegrate on the same support the functions covered by
the Reader an the Transponder. This means that we
can have three different types of communication:
• The traditional communication protocol of RFID
systems, in which the NFC equipped device acts
as a Reader and it can get the information stored
onto a Transponder and can also write on it.
• A bidirectional communication, in which two
NFC devices exchange data between themselves.
This case is particularly interesting because, even
if the bit rates currently available are not too high,
the particular protocol implemented makes the es-
tablishing of the communication very easy.
• A communication between a turned on device and
a turned off one. In this case the second item
is seen by the first one simply as a Transponder,
making it suitable for identification and access
control purposes.
All these different methodologies of data ex-
change have brought to the realization of many kinds
of systems covering a wide range of applications not
only in the field of identification but also in the one of
personal communication.
Moreover, the short reading range of the devices
makes NFC systems considerably safe, because in-
truders should arrive too much close to the devices
to steal the data.
The large number of possible applications has fi-
nally led to the integration of the NFC technology
onto the most common communication devices cur-
NFCARE - Possible Applications of NFC Technology in Sanitary Environments
59
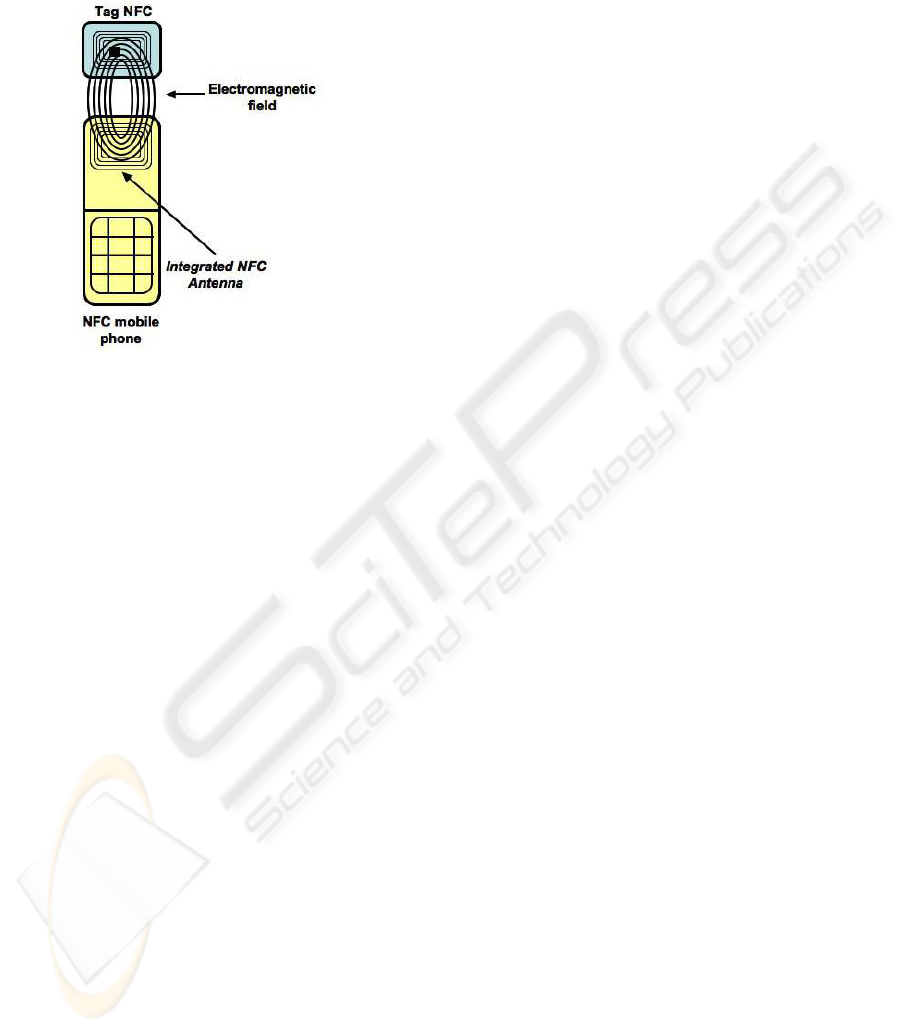
rently available on the market: the mobile phones.
NFC phones can then be used as keys, credit cards
or business cards and the number of possible applica-
tions is virtually infinite.
Figure 1: An NFC system.
3 NFC IN THE REAL WORLD
Even if quite new, NFC is a technology whose intro-
duction is supposed to be very fast. In this sense the
number of possible devices and applicative fields is
growing day by day, making necessary a deep knowl-
edge of the possible technological solutions.
In the following sections we describe briefly the most
important typologies of NFC devices and the main ap-
plications.
The last subsection describes all the work that has
been made in order to create worldwide accepted stan-
dards for NFC systems.
3.1 NFC Devices
NFC systems can integrate three different kinds of de-
vices:
1. Fixed Read/Write or Read Only terminals;
2. Mobile Read/Write or Read Only devices;
3. Read Only Tags.
The fixed terminal can be common RFID readers
working at 13.56MHz ISO14443 compliant or can be
specifically studied devices created to perform spe-
cific actions deriving from the particular operation
they have to execute.
Some examples of ad-hoc devices can be the NFC
POS systems or the electronic ticketing terminals.
Mobile devices are mainly represented by phones
or PDA, even if in this case too specific platforms can
be studied to satisfy particular requirements.
Many mobile phones producers, including big
companies like Nokia, Samsung and Motorola are
studying and realizing particular phones with NFC
technology integrated, and specific studies assert that
by the year 2010 half of all mobile devices will sup-
port NFC.
In particular, while many companies have begun
to sell specific versions of common phones equipped
with NFC infrastructure, Nokia has been the first
brand to put on the market a totally NFC phone.
The last kind of devices is represented by Tags. In
this case common ISO14443 RFID tags can be used,
even if specific products have nevertheless been real-
ized.
Currently four different types of tag can be used
in NFC systems:
• Type 1 is based on ISO14443A, is produced only
by Innovision Research & Technology and has a
96-byte memory. This kind of tags are very cheap;
• Type 2 is based on ISO14443A, is produced only
by Philips (MIFARE UltraLight), and has only a
48-byte memory;
• Type 3 is based on FeLica (a specification compat-
ible with the ISO18092 standard for passive com-
munication mode) and produced only by Sony.
These tags have higher memory capacities (up to
2 kbytes) and reach the 212kbit/s rate;
• Type 4 is compatible with the ISO14443A/B stan-
dard and is produced by several manufacturers.
It has a large addressing-memory capability and
reaches rates up to 424kbit/s.
These four kinds of tags represent four strongly
different products, and every time that an NFC appli-
cation has to be realized, the choice of the right kind
of tag has to been made extremely carefully.
3.2 NFC Applications
NFC can be used in several different fields. Three
different categories of possible applications havebeen
identified (Innovision, 2007):
• Service initiation;
• Peer-to-Peer;
• Payment and Ticketing.
In the ‘Service Initiation’ scenario NFC is used in
a way similar to RFID. The NFC device reads the ID
code or the saved data from a tag and uses them in
many different ways.
HEALTHINF 2009 - International Conference on Health Informatics
60

In this case the NFC reader can be a fixed terminal
or a mobile device, while the Identification device can
obviously be a transponder, but can also be a turned-
off mobile device. In fact the ID code of the internal
tag of NFC phones can be read even if the device is
off, allowing for example the use of the phone as an
electronic key.
The information retrieved from the transponder
(stored data or UID code) can be simply read and dis-
played, can be used to set up a connection (in this case
data can be a URL or a phone number) or can be used
for access control in the same way as RFID keys.
One example of this kind of applications can be
the ‘smart poster’. In this application an NFC tag is
located near an informative point: the user brings an
NFC phone near the tag, reads an URL stored on it
and uses it to connect to the Internet site providing
the information requested.
The ‘Peer-to-Peer’ category is something totally
different from RFID systems. In this kind of appli-
cations a two-way communication is set up between
two devices working in Active mode.
If the amount of data to be exchanged is not too
large this can be done using directly the NFC channel.
If the amount of data is too big (for example an im-
age), NFC channel can be used to set up another wire-
less connection (Bluetooth, Wi-Fi) in a way totally in-
visible to the user, and then send the data through this
connection.
In this case NFC is used exclusively to set up the
connection. For example in an Internet Point the user
can get the Wi-Fi settings touching a specific hot-spot
with the NFC terminal and then transfer them, also
with NFC, to the device to be connected to Internet.
The last scenario ‘Payment and ticketing’ is cur-
rently the most studied due to high the interest of
many banking companies in this technology (Smart
Card Alliance, 2007).
The idea is to turn a mobile phone in an electronic
wallet or in an electronic credit card. While nowadays
a card can be used for a single payment function, with
NFC will be possible to collect many different func-
tions on a single multimodal platform.
As we told before NFC is implicitly safe due to its
short ranges.
The possible payment operations can be divided
in two main groups: micro-payments and macro-
payments.
Micro-payments are represented by the electronic
wallet. An amount of virtual money is loaded onto
the phone and the user can pay various services like
tickets or car parks simply bringing the phone next to
payment terminal.
Macro-payments can be a little more complicated
because they necessarily involve the collaboration
with banks. In this case the phone will replace the
Credit Cards or Bancomats in payment operations
working with POS system. In macro-payments it’s
mainly used the identification capability of NFC.
3.3 NFC Standards and Organizations
The high interest in NFC technology has brought
many companies, coming from very different busi-
ness areas, to join together into an organization called
NFC Forum (NFC Forum, 2007).
In particular the Forum is composed by manufac-
turers of devices, developers of applications and fi-
nancial institutions. Among the most important we
can cite Hewlett-Packard, Microsoft, Sony, Texas In-
struments, Nokia, Motorola, Samsung, IBM, Master-
Card, Visa and AT&T, but the most important fact is
the the Forum has been joined by companies from all
over the world.
The forum has the main purpose to promote the
introduction of NFC technology in common appli-
cations on a worldwide scale and tries to do this by
proposing standard-based specifications, interopera-
ble solutions, and providingstable frameworks for ap-
plication development.
Being basically an RFID technology, NFC sys-
tems are compliant with the ISO14443 standard for
proximity cards used for identification.
Next to this specific standards for NFC have been
developed. In particular the following standards have
been published:
• ISO18092: Near Field Communication - Interface
and Protocol - 1 (NFCIP-1): this standard basi-
cally specifies the modulation schemes, coding,
transfer speeds and frame format of the RF inter-
face of NFC systems;
• ISO21481: Near Field Communication - Interface
and Protocol - 2 (NFCIP-2): this standard speci-
fies the mechanism to detect and select the com-
munication mode out of the possible NFC com-
munication modes;
• ISO22536: Near Field Communication Interface
and Protocol (NFCIP-1) - RF Interface Test Meth-
ods: this standard defines the test methods for the
RF-interface of NFC systems;
• ISO23917: NFCIP-1 - Protocol Test Methods:
this standard complements the previous one and
specifies the protocol tests;
• ISO28361: Near Field Communication Wired In-
terface (NFC-WI), this standard specifies the dig-
ital wired interface between two components, a
NFCARE - Possible Applications of NFC Technology in Sanitary Environments
61

Transceiver and a Front-End, including the signal
wires, binary signals, the state diagrams and the
bit encodings for three data rates.
4 NFC IN SANITARY
ENVIRONMENTS
Even if currently the most studied application field
regards the payment scenarios, the versatility of NFC
technology encourages its use in many other fields not
directly involved in commercial operations.
In particular the availability of common mobile
phones equipped with NFC hardware encourages its
wide use in applications with high interactivity and
security requirements.
In sanitary environments the assistance operations
usually involve a high number of actors, including
doctors, nurses and obviously patients. Moreover
all these operations require a high level of reliabil-
ity in the interaction among different people because
a wrong medical prescription can cause big problems
to the patients while in the assistance operations in
Emergency Rooms 5 minutes can make the difference
between life of death.
The informative and communicative capabilities
of NFC can be therefore used to reduce all the er-
rors or misunderstandings deriving from wrong data
exchanges or from slow information access.
If the NFC Forum predictions on NFC devices dif-
fusion will demonstrate to be true in the next years
many people all over the world will be provided with
NFC devices and, due to the standardization of the
technology, simply downloading a specific software
on their phone they will be able to access at some ser-
vices modeled on the needs of their particular working
environment.
The final idea is to turn the personal mobile phone
of doctors and nurses into a multipurpose device join-
ing the personal uses with the common working ac-
tivities of these categories of people. The phone may
therefore become a key, a pen, a sheet of paper, an
organizer and, obviously, a communication device.
In the specific case of sanitary environments we
studied and developed a set of applications deriving
from the first two applicativefields, i.e. Service initia-
tion an Peer-to-Peer because the Payment and Ticket-
ing field is evidently more distant than these two from
the specific needs of an hospital.
Figure 2: NFC applications in sanitary environment.
4.1 Service Initiation Applications in
Sanitary Environments
Service Initiation doesn’t mean only identification or
access control. In this applicativefield are included all
the applications which use transponders as contactless
memories to be read from mobile or fixed devices.
What can be read is not only the UID code of
the transponder, but also the information stored on it,
which can be codified in order to use in the best pos-
sible way the small amount of memory available, and
can be ciphered in order to make it unreadable from
external users.
Taking care of patients means the performing of
a lot of different activities, from the care of wounded
people in the Emergency Room to the administration
of medicines. Some of these activities can be made
safer an faster with the use of NFC phones as reader
devices.
In particular the following applications have been
studied and developed:
• Access control: entrance in reserved areas and
tracking of the working hours of employees;
• Electronic case history;
• Electronic communication of assistance opera-
tions;
• Electronic medical prescriptions.
The first application is evidently the closest to the
original target of RFID, the automatic Identification.
In fact, as we said before, NFC phones can be identi-
fied from NFC readers exactly as transponders, even
when they are turned off.
HEALTHINF 2009 - International Conference on Health Informatics
62

This allows to use phones as key to obtain access
to restricted areas in the same way as magnetic strip
cards. Moreover, the phone can be used to record the
accesses and the exits from the working place, a func-
tion currently managed in italian hospitals with cards.
In this case the main advantage derives from the
incorporation of these functions on the mobile device,
preventing the employees to bring with them the re-
quested cards.
The Electronic Case History application derives
from a previously studied similar system based on
RFID technology (Benelli, Parrino and Pozzebon,
2008).
In many assistance operations the quickness of in-
tervention is one of the most important features to be
achieved. Next to this there are some vital informa-
tion concerning the patient that must be provided to
the doctor before performing the intervention: data
like blood type, allergies or vaccines are fundamental
to avoid dangerous errors.
One of the best ways to ensure a correct and fast
reading of the information is to store them into an
electronic device and retrieve it with a multimedia
support. In this sense the idea is to provide to pa-
tients an electronic bracelet concerning mainly of an
NFC transponder, where data can be stored and read
quickly with a phone in case of need.
Obviously NFC transponder cannot store large
amounts of data. As a consequence a severe choice
has to be made between strictly vital information,
which has necessarily to be provided to the doctor and
will be then kept directly on the bracelet, and less im-
portant data, like for example the chronologyof all the
medical interventions made on a patient, which can be
stored into a remote database and then retrieved only
on request using Wi-Fi, GPRS or UMTS connection
(Bing, 2002).
Even if our application has been studied and tested
using MIFARE 4K transponders, which provide a 4
kbyte EEPROM, we studied an organization of the
information to make it storable also into 256 byte
transponders.
This is the bytes subdivision chosen in our appli-
cation:
• 40 bytes for first name and family name;
• 16 bytes for the tax code, whose decoding allows
the recoverof birth date, place of birth and gender;
• 10 bytes for the sanitary code;
• 8 bytes for allergies: every byte is a flag indicat-
ing the presence/absence of the corresponding al-
lergy;
• 8 bytes for vaccines: every byte is a flag indi-
cating the presence/absence of the corresponding
vaccine;
• 8 bytes for infectious diseases: every byte is a
flag indicating the presence/absence of the corre-
sponding disease;
• 8 bytes for various information like blood type
(1 byte encoding), HIV positivity or smoking/non
smoking;
• 100 bytes with a specific codification for the 10
last hospitalizations. Every hospitalization is cod-
ified with 10 bytes where the first to bytes are a
code corresponding to the specific medical ward,
the third and the fourth indicate the kind of inter-
vention and the last six bytes are the date;
• 50 bytes for textual accessory information.
Once the NFC device is brought in proximity of
the bracelet, it reads the string of bytes, decodes it
and shows the data into a grafic interface. It also gets
the UID code of the tag in order to use it as the identi-
fication mean to retrieve the information stored inside
a remote database.
The application which manages the reading, de-
coding, recover and reproduction of the information
is a Java Midlet, also incorporating simple read and
write tag functions.
These functions will be used in the third appli-
cation, in which transponders are seen as the means
to communicate the type of assistance operations per-
formed on a specific patient.
The idea is that every bed in the hospital will be
equipped with a transponder. Every time that an inter-
vention is made, before performing the operations the
doctor or the nurse reads on the transponder the pre-
vious treatment made to the patient, in order to avoid
dangerous errors like repetitions in drug administra-
tion.
After the assistance has been made the operation
performed is written on the transponder with the NFC
phone, in the same way as are written SMSs, in or-
der to inform the ones who will make the following
intervention.
In the last application we studied the realization
of an electronic medical prescription where sheets of
paper are replaced with transponders.
The technological infrastructure is the same of the
former task, allowing then to incorporate its function-
alities into the same software developed for all the
other applications.
Instead of writing the medical prescription on a
paper, the doctor writes it into a transponder in the
same SMS way of the other application. Usually the
length of a prescription is less than 200 characters so
usually there are no problems of shortage of memory.
NFCARE - Possible Applications of NFC Technology in Sanitary Environments
63

Anyway 4kbyte cards can be used in order to avoid
any risk of incomplete descriptions.
Once the prescription has been written the
transponder can be brought to the chemist who can
read it with its own NFC phone.
In many cases handwritten medical prescriptions
are very difficult to be read: such a kind of sys-
tem will help to avoid errors in the administration of
medicines, making safer the treatment of patients.
Figure 3: Electronic case history - allergies and electronic
medical prescription.
4.2 Peer-to-Peer Applications in
Sanitary Environments
As described before the Peer-to-Peer scenario is the
one in which the most interesting innovations are in-
troduced.
The phone is in fact used as a short range com-
munication device allowing people to exchange data
simply bringing close to them their mobile phones.
The absence of direct interaction from the users to set
up the communicationchannel makes very fast the be-
ginning of the process of information exchange.
This functionality can be joined with the system
described in the previous section in order to make the
information about patients retrieved with the reading
of the electronic bracelets transferable among the peo-
ple operating around a specific patient.
In fact, usually many different people attend at the
assistance of people in a hospital, and in some cases
the operations can last even some hours.
Every time that a doctor replaces another one
he can download the electronic case history simply
bringing his phone close the one of the former doctor.
This operation can be performed for every kind of
data that has to be exchanged between two different
employees.
For example a doctor can download from a re-
mote server a particular information about a patient
like an image of an x-ray and then he can send it to all
the other doctors operating with him simply using the
NFC channel.
As described before, if the amount of information
to be exchanged is too big to be transferred with NFC,
this technology can be used to set up a connection in a
fast way with other technologies like Bluetooth which
can then be used as the real transfer channel.
Figure 4: Phone menu interface.
4.3 NFC Devices used in the Realization
of the System
The devices used in the realization of this study are a
mobile phone provided with an ad-hoc development
kit, a set of transponders and a reader.
The mobile phone used is a Nokia 6131 NFC: it’s
a particular version of the common 6131 phone with
the NFC circuitry embedded. Nokia sells this product
in a particular ‘Experimental’ version, which allows
the developers to use all the features of the telephone
without the need to validate their applications.
Moreover Nokia provides a Java Development Kit
with all the APIs needed to realize NFC Midlet and
with a Simulation Environment which can be used to
test the applications but can also work as an emulated
phone interacting through a NFC reader, connected to
the computer, with an external phone.
The Simulation Environment also provides some
different simulated transponders in order to fully test
several kinds of applications.
HEALTHINF 2009 - International Conference on Health Informatics
64

In the real testing phase we used MIFARE
transponders of different types. In particular we used
a MIFARE UltraLight transponder, which is very thin
(like a sheet of paper), but it has a small memory (only
512 bit), and a MIFARE 4k, which is thicker but can
store up to 4 kbytes of data. Both these transponders
are ISO 14443 compliant.
Finally we used a common RFID reader to study
the access control application because, once turned
off, the phone is read like a common RFID transpon-
der and no specific hardware is requested.
5 CONCLUSIONS AND FUTURE
WORK
The aim of this work was to show how much NFC
technology can increase the quality of service in situ-
ations very distant from the standard payment scenar-
ios.
The performances of NFC systems have proved to
be extremely high for what concerns the reliability of
the communication channel.
During the reading of the transponder no error has
been recorded, especially in the case of the electronic
case history, which involved the largest amount of
data to be moved.
In addiction the reading and decoding of the data
took only some fractions of second, making the in-
formation immediately available when the phone was
brought in proximity of the transponder.
The modularity of this system, due to the fact that
single tasks can be easily integrated into the same
software, makes it upgradeablesimply adding the new
functions to the underlying structure.
Among new applications to be studied we can find
some ones deriving from already existing RFID sys-
tems, but now made simpler from the presence of mo-
bile phones. In particular we can list the following
fields:
• The identification between mother and baby with
the use of transponders located onto the cradles or
with electronic bracelets.
• The tracking and identification of blood sacks.
• The assistance operations inside the ambulance,
which can be made safer using the traditional
GPRS and UMTS connections available on mo-
bile phones.
Next to these in many other situations NFC can
be used to increase the level of reliability without the
need to enlarge the number of devices to be bought.
This fact is extremely important because in many
cases the introduction of a new service is prevented
due to the high costs.
The only expenses to be made to introduce such
a system are basically the ones for the mobile phone
and for the readers to control the accesses, because
currently transponders can be bought with few euro
cents, making this expense virtually unimportant.
If the NFC Forum valuations will demonstrate to
be true, in the next years we will see a vast diffusion of
NFC phones, making the applications described be-
fore simply downloadable and executable on the per-
sonal phones of doctors and nurses, without the need
to buy specific devices.
REFERENCES
Benelli, G., Parrino, S. and Pozzebon, A. (2008). RF-
Health: an integrated management system for a hos-
pital based on passive RFID technology. In EHST’08,
2nd International Workshop on e-Health Services and
Technologies. INSTICC Press.
Bing, B. (2002). Wireless local area networks. Wiley.
ECMA International (2007). Near Field Communication
White Paper. ECMA International.
Finzkeller, K. (2003). RFID handbook fundamentals and
applications in contactless smart card and identifica-
tion. Wiley.
Innovision Research and Technology (2007). Near Field
Communication in the real world: turning the NFC
promise into profitable, everyday applications. Inno-
vision Group.
NFC Forum (2007). Near Field Communication and the
NFC Forum: The Keys to Truly Interoperable Com-
munications. NFC Forum.
Smart Card Alliance (2007). Proximity Mobile Payments:
Leveraging NFC and the Contactless Financial Pay-
ments Infrastructure. Smart Card Alliance.
NFCARE - Possible Applications of NFC Technology in Sanitary Environments
65
