
REAL-TIME RFID-ENABLED HEALTHCARE-ASSOCIATED
MONITORING SYSTEM
Belal Chowdhury, Xiaozhe Wang
School of Management, La Trobe University, Melbourne 3086, Australia
Nasreen Sultana
Emergency Department, Frankston Hospital, Frankston 3199, Australia
Keywords: Radio frequency identification, Infectious diseases, Healthcare-associated infectious diseases.
Abstract: In healthcare context, the use of Radio Frequency Identification (RFID) technology has been employed to
reduce health care costs and to facilitate the automatic streamlining of healthcare-associated infectious
disease outbreak detection. RFID is playing an important role in monitoring processes in health facilities
such as hospitals, nursing homes, special accommodation facilities and rehabilitation hospital. In this paper,
we present a design of healthcare system using a real-time RFID-enabled application, called “Healthcare-
associated Infectious Outbreak Detection and Monitoring System (HIODMS)”.
1 INTRODUCTION
Infectious or communicable diseases have been an
ever-present threat to human society since the great
Plague of Athens in ancient times. The changing
face of healthcare poses new challenges for the
detection, treatment and prevention of infectious
diseases. Historically local public health
organizations, hospitals and clinics have been at the
forefront of infectious disease outbreak detection
and treatment. Healthcare-associated infections
encompass almost all clinically evident infections
that patients acquire during the course of receiving
treatment for other conditions within a healthcare
setting. Most infections after 48 to 72 hours of
hospitalization are considered Healthcare-associated
acquired. Healthcare-associated infections (also
known as hospital-acquired infections) are referred
as nosocomial. Most common healthcare-associated
infections are: i) respiratory infections (pneumonia)
and Catheter-associated urinary tract infections, ii)
surgical wound infections, result from contamination
of the surgical wound, and iii) infections associated
with intravascular cannulas or central venous
catheter.
Healthcare-associated infectious diseases (such
as Tuberculosis, Legionnaires’ disease and
gastroenteritis) can affect any person regardless of
age, gender, or race and common among residents of
long-term care facilities (e.g., nursing homes, special
accommodation facilities and rehabilitation
hospitals). Patients with weakened immune systems
are likely admitted to the healthcare facilities (e.g.,
hospitals) and sometimes do not realize that they are
already incubating the virus while in hospital. Also
visitors, staff, and residents constantly come and go,
bringing in pathogens from both the hospital and the
community (Larry et al., 2003). Tuberculosis (TB)
poses specific risks to health care staffs, which can
be responsible for spreading the disease to patients
in their care. Legionnaires' disease has been reported
from many hospitals since the first outbreak and
water cooling towers are identified to the cases of
the disease, which apparently causing pneumonia. A
new study by the School of Medicine, University of
Pittsburgh has determined that environmental
monitoring of institutional water systems can help to
predict the risk of hospital-acquired Legionnaires'
disease (ScienceDaily, 2007). A viral gastroenteritis
outbreak presents a growing challenge in health care
and long-term care facilities. Influenza Epidemics in
the United States result in an average of 136,000
deaths and 114,000 hospitalizations per annum
(Thompson, 2003).
163
Chowdhury B., Wang X. and Sultana N. (2009).
REAL-TIME RFID-ENABLED HEALTHCARE-ASSOCIATED MONITORING SYSTEM.
In Proceedings of the 11th International Conference on Enterprise Information Systems - Software Agents and Internet Computing, pages 163-166
DOI: 10.5220/0001997601630166
Copyright
c
SciTePress

Figure 1: Main components of RFID-enabled HIODMS
Architecture.
The risk of acquiring an infection while
hospitalized is very real and can be responsible for
spreading the highly contagious disease to other
patients, medical professionals, equipment, air,
water and fomites. The impact of healthcare-
associated infections is enormous: the patient may
need longer hospital treatment, re-admission, or
even further surgery, and use of hospital and
community resources (Jenney et al., 2000).
Healthcare-associated infections are one of the top
ten leading causes of death in the United States,
recent data suggests that the rate of hospital-acquired
infections has increased over the past two decades
(Spelman, 2002). In most countries, healthcare
infectious outbreaks are a notifiable disease where
the patient needs to be accurately identified, isolated
and monitored while infected with the virus. The
Institute of Medicine strongly recommended that
monitoring leads to reduction and prevention of
healthcare associated infections.
Information systems plays a vital role in
developing an effective approach and facilitate
infected or healthcare-associated patient’s
information, (e.g., patient medical history,
diagnosis) and associated equipments or assets to
address this emerging or re-emerging outbreaks
threat (Buehler et al., 2004). Mobile or wireless
technology is expected to provide real-time
information about vital signs and other physiological
indicators of one’s health and fitness. Such
monitoring systems are expected to find greater use
in such applications in long-term health care
facilities. In this paper, we demonstrate an
application of real-time monitoring system can be
facilitated by the use of the wireless technology such
as Radio Frequency Identification (RFID). We
integrate RFID technology with a multi-layer
architecture for a Healthcare-associated Infectious
Outbreak Detection and Monitoring System
(HIODMS) via both wireless and wired network.
Following section demonstrate the RFID-
enabled HIODMS architecture. Section 3 illustrates
the application of the RFID-enabled HIODMS and
the security issues.
2 RFID-ENABLED HIODMS
ARCHITECTURE
The main components of RFID-based HIODMS (as
shown in Figure 1) are: patient tags (RFID encoded
wristband), a reader (fixed and handheld), and health
care provider IT systems (i.e., Real-Time RFID-
Based HIODMS). RFID is one of the emerging
wireless technologies that play an integral role to
halt the spread of such outbreak diseases, prevent
and control further outbreaks by isolating infected
patients and associated medical equipments or assets
in real-time. Each unique patient tag can be passive,
semi-passive or active. Passive patient tags can be
used for both reading and writing capabilities by the
reader and do not need internal power. They get
energized by the reader through radio waves and
have a read range from 10mm to almost 10 meters.
We suggest the use of passive patient tags with the
read range of one meter, and RFID-based PDA
readers (e.g., Motorola MC9090-G) for the real-time
Healthcare-associated Outbreak Management
System application. The reason to select a 13.56
MHz (High Frequency) solution is for the low cost,
better read range, and faster read rate.
The passive patient tag antenna picks up radio
waves or electromagnetic energy beamed at it from a
PDA-based RFID reader device and enables the chip
to transmit healthcare-associated infected patient’s
unique ID, and location to the reader device,
allowing the patient to be remotely identified. The
reader converts the radio waves reflected back from
the patient tag into digital information then pass onto
HIODMS for processing. Patient’s basic infection
information is stored in the backend server for
processing data. The patient database can also be
linked to other health centres databases for retrieving
patients past history using Internet via a wireless
network. In addition to monitoring healthcare-
associated infected patients, the system can also
track associative equipments or assets (e.g.,
wheelchairs), staff member, and surgical equipments
in real-time to isolate them and prevent further
outbreaks. RFID-based HIODMS enables healthcare
ICEIS 2009 - International Conference on Enterprise Information Systems
164
staff to follow an infected patient through the
hospital, from admission to discharge. In case of
isolation, if an infected patient enters an
unauthorized area in the healthcare settings, the
RFID based system issues an alert to the healthcare
staff with information that indicate the identity and
location of the particular patient.
An application of RFID-based HIODMS consists
of five layers, namely: physical device layer,
middleware layer, health IT infrastructure
management layer, data layer, and graphical user
interface layers. The physical device layer consists
of the actual RFID hardware components that
integrate with HIODMS for capturing data
automatically. In this layer we used passive HF
read/write RFID readers and patient tags. The
middleware layer or framework acts as the standard
mechanism to get a quick connectivity between
healthcare-associated outbreaks detection tags and
RFID-based HIODMS as shown in Figure 1. The IT
infrastructure management layer is responsible for
managing and controlling healthcare organization’s
IT components such as computers, back-end servers,
networks, and printers. In addition, this layer enables
data mapping, formatting, business rule execution
and the service interactions with back-end databases.
The data layer composed of a Relational Database
Management System and it interacts with a back-end
database (e.g. SQL server). Finally, the graphical
user interface (GUI) layer is comprised of an
extensible GUI, which helps in detecting,
monitoring and managing hospital-acquired various
infectious outbreaks (i.e., wound infection)
information, generating various reports and analyzes
the health information at various stages in the entire
value chain.
3 RFID-ENABLED HIODMS
APPLICATION AND SECURITY
In this paper, we demonstrate some interfaces of the
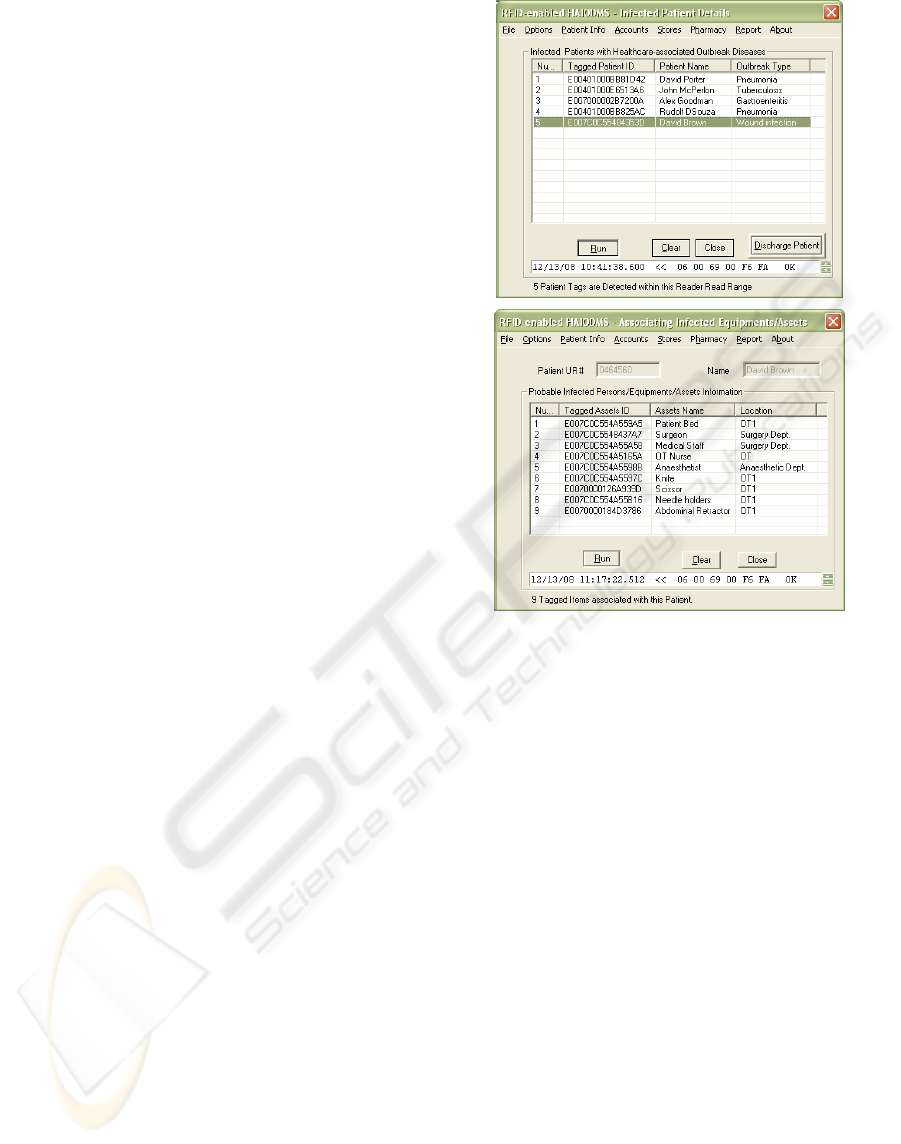
RFID-enabled HIODMS application as shown in
Figure 2, which can be integrated with the healthcare
IT System for capturing healthcare associated
infectious diseases (e.g., wound infection,
Gastroenteritis, Tuberculosis) data automatically and
wirelessly. The system is developed in Microsoft
Visual Studio.net 2003 environment using Visual
C++.
The RFID-based HIODMS application registers
a reader and issues a unique wristband (patient ID)
to every patient at registration/admission in
healthcare facilities (e.g., hospitals), and also issues
Figure 2: Two examples of RFID-based HIODMS
application.
RFID tags to hospital equipments/assets (e.g., beds,
and surgical instruments) relating to the particular
patient. The RFID then uses the patient ID as a key
to information and perhaps other information (e.g.
name, DOB, drug allergies, and blood group) stored
in the health providers back-end databases (i.e., SQL
server). The patient tag is used to identify patients
all the way from observation, investigation, and
treatment to discharge while in hospital. In case of
healthcare-associated infectious outbreak (e.g.,
wound infection), this tag is used to identify exact
outbreaks area or location, time, and list of
associated hospital equipments/assets in real-time as
shown in Figure 2. For example, an RFID patient tag
contains a unique tag ID, which a HIODMS
application uses to retrieve an infected patient record
stored in the database. When a patient appears with a
wristband within a reader read range, the application
reads and lists the tagged patient IDs, names and
displays the patient admission information
automatically on a selection of a particular infected
patient. The application then transfers these
healthcare-associated outbreaks data to the SQL
server for permanent storage and further analysis
over the mobile network in real-time.
REAL-TIME RFID-ENABLED HEALTHCARE-ASSOCIATED MONITORING SYSTEM
165

While RFID provides promising benefits such as
healthcare organizations business process
automation, some significant challenges (e.g.,
security concerns, process, and manage RFID-based
infectious data) need to be addressed before these
benefits can be realized. To overcome this challenge,
sophisticated security measures are needed. Without
security, illegal activities can cheat RFID systems
easily for the air interface between infected
patient/equipment tags and RFID readers, and the
interface between RFID readers and the back-end
database system. In addition, healthcare-associated
infected patient’s privacy is also an issue, since
anyone can intercept communication between the
patient tags and readers, or between readers and the
back-end system, and then they can obtain
information about an infected patient. To remove
security vulnerabilities and protect patient’s privacy,
a number of existing RFID security measures can be
considered and adopted as a measure of security.
In our RFID-enabled HIODMS, communication
between patient tags and readers, readers and back-
end database is one-way. Our patient tags are
passive, inexpensive and have a minimum amount of
memory. We require very little information in the
patient tag (e.g., Tag ID only). When the outbreak
infected patient tag comes in to contact with the
reader within a range of one meter. The Pocket PC
(PDA-based RFID reader) reads and processes the
patient/equipment tag identification number. Within
this proximity and with the mobile/wireless
environment, there will be no scope to intercept
communication between patient tags and a reader. In
a worst case situation, if an intruder intercepts and
gets the patient/equipment tag ID, he or she gains
nothing because the tag does not contain any
additional information.
To achieve the secure transfer of integrated
patient/equipment data from Pocket PC to back-end
database server via wireless network, we use a Hash
Function-based Mutual Authentication Scheme (Lee,
2005). This scheme, utilizing a hash function, is
widely used for secure communication between
mobile/wireless devices (such as PDA-based IODM
system) and back-end SQL servers in a RFID-based
healthcare environment.
4 CONCLUSIONS AND FUTURE
WORK
We presented a RFID-enabled monitoring system
(HIODMS) to help healthcare providers to overcome
challenges of hospital-acquired infectious outbreak
diseases by providing accurate, automatic and real-
time information on patients, associative medical
equipments or assets as they move to the value
chain. Using HIODMS, health care organizations
have a chance to track rapidly and accurately of
outbreak patients, their location, and associative
assets identification; to improve patient’s safety by
capturing infected patient data; to prevent or reduce
medical errors, to increase efficiency and
productivity, and to save costs in real-time via
wireless network.
In future research, the application based on
HIODMS can be expanded to include a variety of
tracking or sensor (such as temperature) features
using RFID. RFID patient tag (wristband) can
transmit not only its unique identification number,
but also the ambient temperature, which can help
healthcare facilities IT departments to remotely
monitor the room’s temperature or to receive alerts
via mobile phone or emails. We also plan to extract
the healthcare-associated infectious outbreaks data
provided by this proposed RFID-based HIODMS to
analyze the diseases behaviour and outbreak patterns
using data mining techniques. We then could predict
the next step towards controlling these serious
hospital-acquired diseases, enhancing preparedness,
and providing rapid response health measures.
REFERENCES
Barraclough, B.H., 2001. Safety and quality in Australian
healthcare: making progress, The Medical Journal of
Australia, Vol. 174, p. 616-617.
Buehler, J., Hopkins, R., Overhage, J., Sosin, D., Tong V.,
2004. Framework for Evaluating Public Health
Surveillance Systems for Early Detection of
Outbreaks: Recommendations from the CDC Working
Group. Morbidity and Mortality W. Report,53, p.1-13.
Spelman, D.W., 2002. Hospital-acquired infections, The
Medical Journal of Australia, Vol. 176 (6), p.286-291.
Jenney, A.W., Harrington, G.A., Russo, P.I., Spelman,
D.W., 2000. The cost of surgical site infection
following coronary artery bypass surgery. Journal of
CHEST –CHICAGO-, Vol. 118, p. 397-402.
Strausbaugh, L.J., Sukumar, S.R., and Joseph, C.L., 2003.
Infectious Disease Outbreaks in Nursing Homes: An
Unappreciated Hazard for Frail Elderly Persons,
School of Medicine, Oregon Health and Sciences
University, Portland, Oregon.
Lee, S., 2005. Mutual Authentication of RFID System
using Synchronized Information, M.Sc. Thesis, School
of Engineering, Information and Communications
University, South Korea.
ScienceDaily, 2007, Environmental Tests Help Predict
Hospital-acquired Legionnaires' Disease Risk,
ScienceDaily, 23 August.
ICEIS 2009 - International Conference on Enterprise Information Systems
166
