
SAFE REVERSE AUCTIONS PROTOCOL
Adding Treatment Against Collusive Shill Bidding and Sniping Attacks
Ribeiro Leonardo and Guerra Ruy
Computer Center, Federal University, Recife, Pernambuco, Brazil
Keywords:
Safe Reverse Auction Protocol, DSA Digital Certificate, Hash Chain, Keys Exchange, Signature Verification,
Collusive Shill Bidding, Sniping.
Abstract:
Many secure auction protocols were created. BJK (Byoungcheon Lee, Kwangjo Kim e Joongsoo Ma 2001)
defined an efficient protocol for English auctions that can be used also for Reverse auctions. Chung (Yu Fang
Chung 2008) created an improvement of BJK, however there are still some security faults that can be explored
by attackers in these two protocols. In this article, we define a protocol based on BJK that is an improvement
of it with the addition of security’s treatment to attacks of Collusive Shill Bidding e Sniping.
1 INTRODUCTION
Internet auction is today a very popular and profitable
industry. Many enterprises like Ebay, Arremate, etc;
have invested in non-presence auctions. The fact
that the auctions participants are not committed to
be in same place brought many benefits however also
many ways to cheat. There are a lot of mechanisms
of cheating and many safe auctions protocols were
created to solve them. These protocols were based
on many cryptographic concepts like: Group Signa-
ture, Threshold Cryptography, Schnorr Signature, etc.
Each solution was created to fulfill characteristics for
each type of auction (English, Reverse, Sealed, etc).
In this article we will present a protocol for reverse
auctions. The presented protocol is based in the one
proposed by BJK(Byoungcheon Lee, Kwangjo Kim
e Joongsoo Ma 2001) that works very well for En-
glish and Reverse auctions. Our protocol comes to
improve protocol with the use of digital certificates
and a module to avoid frauds techniques known as
Collusive Shill Biddings and Sniping (Trevathan, Jar-
rod and Read, Wayne 2006) that are not considered
in any actual secure auction protocol (This protocol
is being proposed to brazilian government that uses
reverse auctions to buy services).
2 EXISTING PROTOCOL
The BJK protocol is one of the best already created
but it still has some problems:
1. K
i
keys exchange are done using Diffie-Hellman
without authentication which enables ”Man in the
Middle” attack.
2. It uses Schnorr signature for authentication of bid-
der that is not very used in commercial certifi-
cates(RSA and DSA are the most used).
3. It does not consider attacks like Shill Bidding and
Sniping.
We propose a protocol wich is an improvement of
BJK where:
1. All auction’s bidders will use DSA digital certifi-
cates for authentication.
2. The keys exchange using Diffie-Hellman will be
done using DSA certificates for authentication
with bidder doing this exchange with Auctionner
through Register Manager(RM).
3. A fraud module(FM) will implement Shill Bid-
ding detection.
4. Anti Sniping policies will be implemented by
RM.
2.1 Our Protocol
2.1.1 Phases
1. Registration
(a) B
i
has a private key x
i
and a public key y
i
de-
fined in his DSA digital certificate.
239
Ruy G. and Leonardo R. (2009).
SAFE REVERSE AUCTIONS PROTOCOL - Adding Treatment Against Collusive Shill Bidding and Sniping Attacks.
In Proceedings of the International Conference on Security and Cryptography, pages 239-244
DOI: 10.5220/0002228902390244
Copyright
c
SciTePress
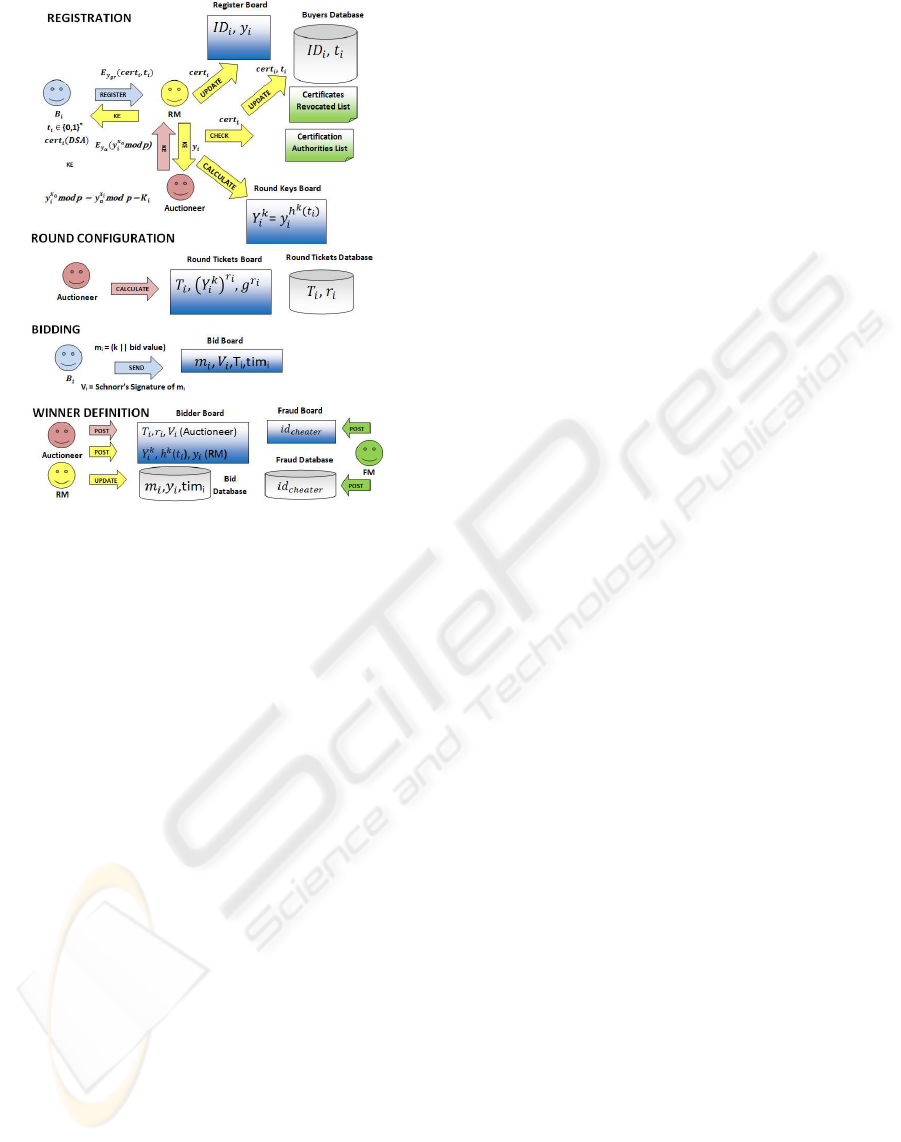
Figure 1: Protocol Phases Representation.
(b) B
i
registers in auction connecting to RM using
his certificate to create a SSL conection with
mutual authentication. The certificate is veri-
fied against CAs database. It’s verified the val-
idation of certificate’s expiration date and if it’s
in list of revocated certificates of the cerficate’s
CAs. I’t also verified if bidder id and/or public
key are in the list of mean bidders.
(c) After B
i
is authenticated, he/she chooses a ran-
dom string t
i
∈ {0,1}
∗
, keeping it safely by en-
cripting it whith his private key defined in his
digital certificate.
(d) B
i
sends t
i
and his certificate cert
i
to RM en-
cripting them with RM’s public key.
(e) RM decripts data and publish (ID
i
,y
i
) in ”Reg-
istration” board where ID
i
comes from digi-
tal certificate(Seee picture above). RM keeps
(ID
i
,t
i
) secretly in bidders database.
(f) RM calculates round key as: Y
k
i
= y
h
k
(t
i
)
i
for all
n valid bidders.
(g) RM publishes them in ”Round Keys” board.
(h) RM sends y
i
to auctioneer and ask him to gen-
erate y
x
a
i
mod p.
(i) The auctioneer calculates y
x
a
i
mod p, encrypt
it with RM’s public key and send it back to RM.
(j) RM receives data and decrypts it, send y
x
a
i
mod p to B
i
encrypting it with his public key.
(k) B
i
receives y
x
a
i
mod p , decrypts it and stores
it localy encrypts it using El Gamal algorithm.
Remember that K
i
= y
x
a
i
= y
x
i
a
defined by Diffie-
Hellman key exchange algorithm.
Remarks:
The bidder B
i
can verify if his round key is in
”Round Keys” board.
No one except RM and B
i
know the correspon-
dence of y
i
and (Y
k
i
).
2. Round Configuration
(a) Auctioneer takes the list of round keys (Y
k
i
)
from ”Round Keys” board.
(b) Auctioneer generates n random numbers
r
1
,...., r
n
∈ Z
q
for each valid bidder where q
is retrieved from public key of Auctionner
certificate (Rembering that g, p and q are the
same for all certificates of entities participating
in auction).
(c) Auctioneer calculates ((Y
k
i
)
r
i
,g
r
i
i
) where k is
the number of round, g is retrieved from public
key of Auctionner certificate and r
i
is the ran-
dom number defined as above for each bidder
B
i
.
(d) Auctioneer calculates round ticket as T
i
=
h((Y
k
i
)
x
a
) where x
a
is auctioneer’s private key.
(e) Auctioneer publishes round ticket
(T
i
,(Y
k
i
)
r
i
,g
r
i
) on ”Round Tickets” board.
(f) Auctioneer stores (T
i
,r
i
) secretly in ”Round
Tickets” database.
Remarks:
The Auctioneer does not know the correspon-
dence of y
i
and (Y
k
i
) as RM does not know from
T
i
and r
i
.
See that a bidder can verify round ticket T
i
calcu-
lating:
Let K
i
= y
x
a
i
= y
x
i
a
like defined in registration phase
and (T
i
,(Y
k
i
)
r
i
,g
r
i
)
Then
T
i
= h((Y
k
i
)
x
a
) = h((y
h
k
(t
i
)
i
)
x
a
) = h((y
x
a
i
)
h
k
(t
i
)
) =
h((y
x
i
a
)
h
k
(t
i
)
) = h(K
h
k
(t
i
)
i
) and this value can be cal-
culated by B
i
because he/she has K
i
and t
i
and
he/she knows how to calculate h
k
(t
i
).
3. Bidding
The bidder B
i
that wants to participate in round
k of auction must follow the steps defined below
while the auction’s round has not expired:
(a) Calculates his round key Y
K
i
= y
h
k
(t
i
)
i
and ver-
ifies if it’s in ”Round Keys” board defined by
RM.
(b) Calculates T
i
= (h(y
h
k
(t
i
)
a
))
x
i
and takes his ticket
(T
i
,(Y
k
i
)
r
i
,g
r
i
) in ”Round Tickets” board.
SECRYPT 2009 - International Conference on Security and Cryptography
240

(c) Verifies the ticket through ((g
r
i
)
h
k
(t
i
)
)
x
i
=?
(Y
k
i
)
r
i
. If there’s a problem, tell Auctioneer.
(d) Prepares his bid (T
i
,m
i
,V
i
) as defined below:
i. m
i
= (auction’s round number || bid’s value)
ii. Signs m
i
with Schnorr’s Signature of Knowl-
edge to assure anonymity: V
i
= (c,s)
where c = h(m
i
||(Y
k
i
)
r
i
||g
r
i
||(g
r
i
)
k
i
), s = z
i
−
c.h
k
(t
i
)x
i
mod q and z
i
∈ Z
q
.
(e) B
i
updates ”Bids” board with (T
i
,V
i
,m
i
). It’s
stored the tuple (T
i
,V
i
,m
i
,tim
i
) where tim
i
is
the time of bidding.”Bids” board verifies if bid
value is lower than current for V
i
. No one ex-
cept the bidders can update ”Bids” board.
(f) RM controls the round’s auction time. He ver-
ifies the rate of bids per minute in auction’s
round based on changes of ”Bids” board. If
there’s an anormal rise of bids in round’s last
2 minutes, time is extended more x minutes (x
is a parameter defined in auction’s round begin-
ning), avoiding this way Sniping attack.
Remarks:
Note that V
i
can be verified by anyone
that knows r
j
, h
k
(t
j
) and Y
k
j
accord-
ing to Schnorr’s signature of knowledge
c? = h(m
i
||(Y
k
i
)
r
i
||g
r
i
||(g
r
i
)
s
((Y
k
i
)
r
i
)
c
).
4. Winner Definition
(a) After auction’s round has finished, RM and
Auctionner take the lists of ”Bids”, ”Round
Keys” and ”Round Tickets” boards and find
bidders identities following the steps:
i. Auctionner takes (V
j
,m
j
,T
j
,time
j
) from
”Bids” board.
ii. Auctionner posts (T
j
,r
j
,Y
k
j
) on ”Bidders”
board that reveals the correspondence of Y
k
j
and (Y
k
j
)
r
j
. Bidder’s information becomes
(V
j
,T
j
,r
j
).
iii. RM posts (Y
k
j
,h
k
(t
j
),y
j
) on ”Bidders” board
that reveals the correspondence of Y
K
j
=
y
h
k
(t
j
)
j
and y
j
. Bidder’s information becomes
(V
j
,T
j
,r
j
,Y
k
j
,h
k
(t
j
),y
j
).
iv. RM updates ”Bids” database with m
i
, bidder’s
public key y
j
and tim
j
.
v. Anybody can verify the bidder’s signature V
j
using the announced public values r
j
, h
k
(t
j
)
and (Y
k
j
).
(b) Fraud module verifies the existence of ”Collu-
sive Shill Bidding”(See next section for more
explanations) based on ”Bids” database. If it’s
found a collusive shill bidding, the auction’s
round is invalidated and bidders found to be
cheating are included in ”Fraud” board and in
”Fraud” database.
(c) If no frauds were found, the bidder with lowest
bid value is announced as winner.
3 FRAUD MODULE
3.1 Shill Bidding
3.1.1 Introduction
Jarrod Trevathan and Wayne Read (Trevathan, Jar-
rod and Read, Wayne 2005) proposed an algorithm
for Shill Bidding Detection of only one shill. After,
the same authors proposed an improvement of this
algorithm for the case of a shill with more than one
bidder, also known as Collusive Shill Bidding (Tre-
vathan, Jarrod and Read, Wayne 2007). We are going
to use this last algorithm to propose a module that can
be used in our protocol for detecting collusive shill
bidding. This algorithm doesn’t run on real time but
after an auction is finished. The algorithm, based in
ratings, calculates what is called shill score. The score
informs if a specific bidder is working with others to
form a collusive shill bidding. Based on this score, an
auction can be invalidated and bidders are denied to
participate in more auction’s rounds. The detection of
a shill is based in calculation of these ratings:
1. α: Percentage of auction’s rounds a bidder i has
participated.
2. β: Percentage of bids that bidder i has submitted
throughout all the auction’s rounds he/she has par-
ticipated in.
3. γ: How many times the bidder has won over the
auction’s rounds he participated in.
4. δ: The average inter bid time of bidder in the auc-
tion’s rounds he participated in.
5. ε: The average inter bid increments in the auc-
tion’s rounds he participated in.
6. ζ: indicates how early in an auction’s round bid-
der i started bidding.
These ratings are defined in interval (0,1). The
higher values, more suspicious the bidder is. If zero
values, bidder has won the auction.
Based on these ratings, we can calculate a shill
score for one bidder as:
SS = ((θ
1
α+θ
2
β+θ
3
γ+θ
4
δ+θ
5
ε+θ
6
ζ)/(θ
1
+θ
2
+
θ
3
+ θ
4
+ θ
5
+ θ
6
)) × 10 where 1 ≤ θ
i
≤ 6
For the case of Collusive Shill Bidding, there are
more than one bidder working together and the calcu-
lation of these ratings and their scores doesn’t imply
SAFE REVERSE AUCTIONS PROTOCOL - Adding Treatment Against Collusive Shill Bidding and Sniping Attacks
241

that the bidders are in an agreement. Only using these
parameters to detect shills can include legitimate bid-
ders. Then, other techniques should be used. There
are three ways a collusive shill bidding act and we
can create mechanisms to detect them.
3.1.2 Forms of Collusive Shill Bidding
1. Alternating bids: Shills (a shill is a bidder that
participates in a collusive Shill Bidding) bid in
only one auction’s round to increase or decrease
the price.
2. Alternating rounds: Bidders take turns bidding as
a collusive shill in different auction’s rounds with
one shill per round.
3. Hybrid: Bidders take turns bidding as a collusive
shill in more than one auction’s round simultane-
ously.
3.1.3 Detection Mechanisms using Graphs
Collusion Graph
To detect the collusive shill biddings, it’s defined the
concept of Collusion Graphs. A collusion graph is
defined as G=(V,E) where V is the set of bidders and
E is the edges between them. Each edge e
i, j
exists
if they participated in a same auction’s round. Each
edge has a weight w
i
that defines the number of times
two bidders v
i
and v
j
participated in same auction’s
round. If the two bidders participated together in only
one auction’s round, w
i
= 0 and w
i
>= 1 otherwise.
Each edge has a weight w
i
, 1 <= i <= l, where l is
the number of bidders, that defines the number of
times two bidders v
i
and v
j
participated in more than
one auction’s round together.(See example on figure
2 below).
Figure 2: Collusiong Graph Normalization.
The graph above was generated for the se-
quence: (s
1
,b
1
,s
2
,b
1
,s
1
,b
1
) for first auction’s
round, (s
2
,b
2
,s
1
,b
2
) for second auction’s round
and (s
2
,b
3
,s
1
,b
3
,s
2
,b
3
) for third auction’s round (s
i
means shill i and b
i
bidder i). Based in the Collusion
Graph, it’s calculated a collusion rating for each
bidder v
i
as:
n
′
i
=
∑
k
j
w
j
where k means the degree of bidder
i in graph and 1 <= j <= l where l is the number of
bidders.
Each bidder collusion rating is normalized as:
n
′
j
=
(n
′
i
−n
min
)
(n
max
−n
min
)
where n
min
is the lowest value
of all values n
′
i
and n
max
the highest.
According to n
′
j
normalized values, suspicious
bidders are separated as sets denoted by C
k
and
C = {C
1
,C
2
,C
3
,.,C
k
} is the set of bidders grouped by
n
′
j
. If two bidders, b
i
and b
j
, are suspicious and they
have similar collusion rate, i.e., n
′
j
= n
′
i
+ λ where λ
is an error factor, they will be in a same collusion
set. Bidders not suspicious will be in a set of one
element. See that 1 <= k <= l where l is the total
number of bidders. The n
′
j
values are then used to
join suspicious in a same set and preserve the correct
bidders.
The collusion graph is used in Alternating bids
form.
Dual Graph
It’s a graph used in Alternating rounds form. It’s
the opposite of Collusion graph. In this graph, two
nodes are connected if they didn’t participate in same
auction’s round. In this graph, we are not interested in
the quantity of how many auctions they participated
but in if they weren’t cooperating or not in same
round. So weight information has value one(1) if
there’s cooperation and zero(0) if not.In example
with auction’s round one sequence as (s
1
,b
1
,s
1
,b
2
)
and auction’s round sequence two as (s
2
,b
1
,s
2
,b
2
),
it can be defined a Collusion graph as figure 3 and a
Dual graph as figure 4.
Figure 3: Collusion Graph.
Figure 4: Correspondent Dual Graph.
Based in the Dual Graph, it’s calculated a collu-
sion rating for each bidder v
i
as:
θ
′
i
=
∑
k
j
w
j
where k means the degree of bidder
i in graph and 1 <= j <= l where l is the number of
bidders.
Each bidder collusion rating is normalized as:
θ
j
′
=
(θ
′
i
−θ
min
)
(θ
max
−θ
min
)
where θ
min
is the lowest
SECRYPT 2009 - International Conference on Security and Cryptography
242

value of all values θ
′
i
and θ
max
the highest.
According to θ
′
j
values, bidders are separated as
sets denoted by C
θ
k
and C
θ
= {C
θ
1
,C
θ
2
,C
θ
3
,.,C
θ
k
} is the
set of bidders grouped by θ
′
j
. If two bidders, b
i
and
b
j
, are suspicious and they have similar collusion
rate, i.e., θ
′
i
= θ
′
j
+ λ where λ is an error factor,
they will be in a same collusion set. Bidders not
suspicious will be in a set of one element. See that
1 <= k <= l where l is the total number of bidders.
The dual graph is used in Alternating rounds form.
3.1.4 Alternating Bids
Bidders with similar collusion ratings defined by
collusion graph will have high probability to be in a
same shill. However this parameter isn’t enough to
define that a bidder belongs to a shill. It’s observed
that shill bidders in alternating bids have identical
β ratings. Based on that, a variable called bidding
factor is defined as:
φ
β
i, j
= 1 if β
i
= β
j
β
i
β
j
if β
i
< β
j
β
j
β
i
if β
i
≥ β
j
It defines how similar two bidders are for this
type of collusive shill.
The parameters n
′
i
, φ
β
i, j
, γ, δ and ε are then
combined together to define a new parameter called
Collusion Score.
CS
n
i
= (
(γ+δ+ε+n
′
j
+φ
β
σ
)
5
) × 10, where φ
β
σ
is
the average of all φ
β
i, j
.
For each set C
k
that is not singleton, it is
calculated bidder’s collusion score and bidders with
similar collusion score will be defined as bidders of a
same shill.
3.1.5 Alternating Rounds
In alternating rounds, as in alternating bids, we
can define collusive bidders based on parameter
Collusion Score. However to calculate it, we observe
a different characteristic. It’s observed that shill
bidders in alternating rounds have identical α ratings.
Based on that, the bidding factor is defined as:
φ
α
i, j
= 1 if α
i
= α
j
α
i
α
j
if α
i
< α
j
α
j
α
i
if α
i
≥ α
j
It defines how similar two bidders are for this type
of collusive shill.
These parameters θ
′
i
, φ
α
i, j
, ζ, δ and ε are then com-
bined together to define a new parameter called Col-
lusion Score.
CS
n
i
= (
(ζ+δ+ε+θ
′
j
+φ
α
σ
)
5
) × 10, where φ
α
σ
is the
average of all φ
α
i, j
.
For each set C
θ
k
that is not singleton, it is calcu-
lated bidder’s collusion score and bidders with simi-
lar collusion score will be defined as bidders of a same
shill.
3.1.6 Hybrid
The hybrid’s form combines the alternating bids and
alternating rounds form. It uses both graphs for de-
tection of shills. It uses the Collusion Score as:
CS
h
i
= (
(δ+ε+η+φ
β
σ
+φ
α
σ
)
5
)×10, where φ
β
σ
and φ
β
σ
are calculated for alternating bids and rounds forms
like already defined in the last sections.
3.2 Sniping
To avoid sniping in an auction, it should be followed
policies to avoid them. The most used technique to
avoid it is to extend auction time if there are bids sent
in the last minutes. In this paper, as defined in Bidding
phase of protocol, the auction is extended x minutes
if there are bids sent in the last 2 minutes (x is a pa-
rameter defined by auctineer). It avoids bids run in
the last minutes. Sniping is a very known technique
used by bidders in the most popular auctions of in-
ternet like Ebay, etc; but this behavior of bidders is
not accepted because it does not allows the real En-
glish(Reverse) auction process of price increasing(or
decreasing) in a period of time. Sniping transforms
English(Reverse) auction in a sealed auction because
almost all the bidders bid at the very end of auction’s
round time with each one sending a sealed letter at the
same time.
4 ANALYSIS
4.1 Protocol
1. Anonym bidder: The RM cannot know the bid-
ders from (Ti, (Y
k
j
)
r
j
,g
r
i
) and (T
i
,m
i
,V
i
) because
SAFE REVERSE AUCTIONS PROTOCOL - Adding Treatment Against Collusive Shill Bidding and Sniping Attacks
243

know Y
k
j
and (Y
k
j
)
r
j
is a problem of calculation
discrete logarithm. Without K
i
, RM does not
know T
i
and find V
i
is also a discrete logarithm
problem. The auctioneer has no knowledge of Y
k
j
from (Y
k
j
)
r
j
and also does not know V
i
.
2. Publicly Verifiable: With RM and auctioneer data,
B
i
winner can be verified.
3. Bids not Forgeable: RM, the auctioneer and any-
one cannot forge the signature V
i
of bidder B
i
.
4. No repudiate: The B
i
winner cannot refuse his bid
because it’s signed with V
i
.
5. Efficiency:
(a) The bidder registration: takes one generation
of signature and a verification of signature
through SSL authentication(1SG + 1SV). One
encryption for sending certificate and t
i
val-
ues, two encryptions and decryptions for Diffie-
Hellman exchange with authentication(Bidder,
RM and Auctioneer communication).
(b) Round key generation takes a modular expo-
nentiation (1E).
(c) Auction ticket generation takes three modular
exponentiations (3E).
(d) The bid sending takes two modular exponenti-
ations and a signature generation (2E + 1SG).
(e) The winner’s definition takes two modular ex-
ponentiations and one signature verification
(2E + 1SV) for each bidder.
(f) Module fraud detection cost: Construction
of Collusive graph using adjacency lists to
build an adjacency matrix + scan adjacency
matrix(O(n)) + calculation of shill’s rates
(O(n)) + calculation of collusion rates (O(n)) +
construction of collusive rate sets(O(1)) + cal-
culation of collusive score (O(n)).
4.1.1 Sniping
There are not cost associated to this part of module
because the techniques to avoid Sniping are very sim-
ple according to section above.
5 CONCLUSIONS
It’s already known the efficiency of BJK protocol for
English auctions, but it does not consider none cryp-
tographic attacks. Our protocol intends to improve
BJK’s one adding techniques for treatment of Col-
lusive Shill Bidding and Sniping attacks.It also adds
authentication through DSA digital certificates. Our
protocol is built in a such form to protect reverse auc-
tions against these forms of attacks.
We are simulating all protocol to prove his effi-
ciency with real data. We are also trying to implement
improvements like the ones proposed by Chung.
ACKNOWLEDGEMENTS
To professor Ruy Guerra to all his help and advices.
Following always the idea to never give up.
REFERENCES
Trevathan, Jarrod and Read, Wayne (2006). Undesirable
And Fraudulent Behaviour In Online Auctions In Se-
curity and Cryptography Conference (SECRYPT), 450
458
Byoungcheon Lee, Kwangjo Kim e Joongsoo Ma (2001).
Efficient Public Auction with One-time Registration
and Public Verifiability. In Second International Con-
ference on Cryptology in India, Indocrypt’01, 162-
174, Springer-Verlag, LNCS 2247
Trevathan, Jarrod and Read, Wayne (2005). De-
tecting Shill Bidding in Online English Auc-
tions. Technical Report, 2005. Available at
http://auction.maths.jcu.edu.au/research/shill.pdf
Trevathan, Jarrod and Read, Wayne (2007). Detecting Col-
lusive Shill Bidding. In International Conference on
Information Technology – ITNG’07, page 799-808
Jame Cook University, North Queensland , Australia.
Yu Fang Chung 2008. Bidder-anonymous English Auction
Scheme with privacy and public verifiability. In Sci-
ence Direct, The Journal of Systems and Software 81,
2008, 113-119.
SECRYPT 2009 - International Conference on Security and Cryptography
244
