
NMIX: AN IDEAL CANDIDATE FOR KEY MIXING
Jaydeb Bhaumik
G. S. Sanyal School of Telecommunications, Indian Institute of Technology, Kharagpur, India
Dipanwita Roy Chowdhury
Department of Computer Science and Engineering, Indian Institute of Technology, Kharagpur, India
Keywords:
Boolean function, Nonlinearity, Reversibility.
Abstract:
Boolean functions play an important role in cryptography. In this paper, a Boolean function ‘Nmix’ has been
proposed which is balanced, reversible and highly nonlinear in nature. It has been proved that the bias of each
of the bits decrease exponentially with the bit position. Thus the Boolean function provides high resistance
against linear cryptanalysis compared to addition modulo 2
n
, the popularly known non-linear function used
in cryptographic primitives. The cryptographic properties of Nmix are compared with similar cryptographic
functions and the result justify to select it as as an ideal choice for key mixing.
1 INTRODUCTION
Boolean functions play a vital role in the design of
cryptographic primitives. They have been employed
as key mixing functions in block ciphers. In case of
AES and DES, XOR function is used as a key mix-
ing function. But XOR function does not provide
any nonlinearity and it is provided by the substitu-
tion boxes (S-box) solely. Addition mod 2
n
is another
popular key mixing technique which is used in block
ciphers like IDEA, MARS, FEAL, SEA. In these ci-
phers, addition mod 2
n
provides extra nonlinearity be-
sides the nonlinearity provided by S-boxes. However
modular addition has the demerit that the bias (Mat-
sui, 1993) of the XOR of consecutive output bit posi-
tions is held constant at
1
4
. Recently another nonlinear
and reversible function modular Slash has been pro-
posed in (Bhattacharya, 2007). The Slash function
has a strong resistance against linear cryptanalysis.
Also it has been shown that hardware implementation
cost and time delay of Slash is less compared to ad-
dition mod 2
n
. However like modular addition, Slash
has the demerit that the bias of the XOR of consec-
utive output bit positions is held constant at
1
4
. Also
recent findings shows that S-boxes make the block ci-
phers unsuitable for light weight cryptography (Koo,
2008). Highly nonlinear Boolean functions are well
suited for application of light weight cryptography
(Bhaumik, 2009). Thus it may be prudent at this point
to look into Boolean circuits which provide high non-
linearity to light weight block ciphers.
In this work, a new Boolean function Nmix has
been proposed which is nonlinear, balanced and also
reversible in nature. It provides better resistance
against linear cryptanalysis compared to addition and
Slash. It has been shown that the bias of the XOR
of consecutive bits position in the output also smaller
than the value for addition modulo 2
n
. The function
Nmix can be used as a better key mixing function in
block ciphers because it is nonlinear, reversible.
The rest of the work is organized as follows. Sec-
tion 2 discusses some preliminaries required for this
work. Our proposed function is elaborated in section
3. Performance of the proposed function has been dis-
cussed in section 4 and section 5 concludes the work.
2 PRELIMINARIES
In this section, some basic definitions and notations
have been discussed.
Affine Function. An n variable Boolean func-
tion ξ(x
1
,x
2
,...,x
n
) is said to be an affine
function if the ANF of ξ is of the form
ξ(x
1
,x
2
,...,x
n
) = p
0
⊕ p
1
x
1
⊕ p
2
x
2
⊕ ... ⊕ p
n
x
n
,
where p
0
, p
1
,...p
n
∈ {1,0}. If p
0
is 0 then the
function is said to be linear.
Hamming Distance. The Hamming distance be-
285
Roy Chowdhury D. and Bhaumik J. (2009).
NMIX: AN IDEAL CANDIDATE FOR KEY MIXING.
In Proceedings of the International Conference on Security and Cryptography, pages 285-288
DOI: 10.5220/0002260702850288
Copyright
c
SciTePress

tween two binary strings (say x and y) of equal length
is measured by wt(x⊕ y).
Nonlinearity. Nonlinearity of an n variable Boolean
function ξ is defined as the minimum Hamming
distance from the set of all affine function of n
variables.
Bias of Linear Approximation. It is defined as
p
i
−
1
2
, where p
i
is the probability of linear approxi-
mation.
Piling-up Lemma. (Stinson, 1995) Let the biases
of k of independent random variables X
i
1
, . . . ,
X
i
k
be denoted by ε
i
1
, . . ., ε
i
k
and ε
i
1
,i
2
,...i
k
denote
the bias of the random variable X
i
1
⊕ ... ⊕ X
i
k
. Then
ε
i
1
,i
2
,...i
k
= 2
k−1
∏
k
j=1
ε
i
j
Bent Function. (Rothaus, 1976) A Boolean function
ξ(x) of n variable, where n is even, is called a Bent
function if it has a nonlinearity value 2
n−1
− 2
n/2−1
.
This is the highest possible nonlinearity for an n
variable Boolean function if n is even.
Theorem 1. (Sarker, 2004) The nonlinearity of
Boolean function f(x
n
,...,x
1
) ⊕ g(y
m
,...,y
1
) is
2
n
nl(g) + 2
m
nl(f) − 2nl( f)nl(g), where f(x
n
,...,x
1
)
and g(y
m
,...,y
1
) are the two boolean function of n and
m variables respectively, {x
n
,...,x
1
}∩{y
m
,...,y
1
} = φ
and nl(f), nl(g) denote the nonlinearity of f and g
respectively.
3 PROPOSED NONLINEAR
FUNCTION
In this section, a new nonlinear mixing function
called ‘Nmix’ and inverse mixing function ‘I-Nmix’ is
introduced.
Forward Nonlinear mixing (Nmix). Nmix
function operates on two n−bit variables
X = (x
n−1
x
n−2
... x
0
), K = (k
n−1
k
n−2
... k
0
) and pro-
duces a n−bit output variable Y = (y
n−1
y
n−2
... y
0
),
where each output bit is related to the input bits by
the following relationship
y
i
= x
i
⊕ k
i
⊕ c
i−1
c
i
=
i
M
j=0
x
j
· k
j
⊕ x
i−1
x
i
⊕ k
i−1
k
i
(1)
where 0 ≤ i < n, c
−1
= 0, x
−1
= 0, k
−1
= 0 and c
i
is the carry term propagating from i
th
bit position to
(i+ 1)
th
bit position. The end carry c
n−1
is neglected.
Each output bit y
i
is balanced for all 0 ≤ i < n. We
will use the notation Y = (X†K) mod 2
n
= F(X,K)
in the rest of the paper, where † is the Nmix operator.
Inverse Nonlinear Mixing (I-Nmix). In inverse
mixing, the mixer takes two n-bit variables Y =
(y
n−1
y
n−2
. . . y
0
), K = (k
n−1
k
n−2
. . . k
0
) as inputs
and produces an n−bit output X = (x
n−1
x
n−2
. . . x
0
).
Inverse mixing operation can be defined as
x
i
= y
i
⊕ k
i
⊕ d
i−1
d
i
=
i
M
j=0
x
j
· k
j
⊕ x
i−1
x
i
⊕ k
i−1
k
i
(2)
where 0 ≤ i < n, d
−1
= 0, x
−1
= 0, k
−1
= 0, and
d
i
is the carry term propagating from i
th
bit position
to (i + 1)
th
bit position. The end carry d
n−1
is ne-
glected. In the rest of the paper we will use the no-
tation X = (Y ∗ K) mod 2
n
= G(Y, K), where ∗ is the
I-Nmix operator. Function G is the inverse function of
F. The following section discusses the performance
of the proposed nonlinear function, Nmix against lin-
ear and differential cryptanalysis.
4 PERFORMANCE OF NMIX
4.1 Linear Cryptanalysis
Linear cryptanalysis (LC) tries to take advantage of
high probability of occurrences of linear expressions
involving input bits, key bits and output bits. Follow-
ing theorem explains the strength of Nmix against LC.
Theorem 2. The bias for best linear approximation of
output bit y
i
of Nmix is 2
−i
, where 2 ≤ i < n
Proof. Assume Nmix function operates on two n−bit
variables X = (x
n−1
. . . x
0
), K = (k
n−1
. . . k
0
) and
generates an n-bit variable Y = (y
n−1
. . . y
0
) such
that Y = F(X,K). From the definition of F, it is evi-
dent that in the output y
i
= x
i
⊕ k
i
⊕ c
i−1
, where c
i−1
is the carry input into the i
th
bit position and c
i−1
for
2 ≤ i < n can be expressed as
c
i−1
= x
0
k
0
⊕ . . . ⊕ x
i−1
k
i−1
⊕ k
i−1
k
i−2
⊕ x
i−1
x
i−2
(3)
After simplification c
i−1
can be expressed as
c
i−1
= x
0
k
0
⊕ ... ⊕ x
i−3
k
i−3
⊕ (x
i−1
⊕ k
i−2
)(k
i−1
⊕ x
i−2
)
(4)
Let f (x
0
,k
0
,...,x
i−3
,k
i−3
) = x
0
k
0
⊕ ... ⊕x
i−3
k
i−3
and
g(x
i−1
,k
i−1
,x
i−2
,k
i−2
) = (x
i−1
⊕ k
i−2
)(k
i−1
⊕ x
i−2
).
Since f is a function of 2(i − 2) variables and it is
in the form of bent function. Therefore, non-linearity
of f is 2
2i−5
− 2
i−3
, where 2 ≤ i < n. Also it is
found that nonlinearity of the four variable function
g is 4. The nonlinearity of c
i−1
= f ⊕ g is com-
puted using Theorem 1 in section 2. The nonlinearity
of c
i−1
is 2
2i−4
.4 + (2
2i−5
− 2
i−3
).2
4
− 2.4.(2
2i−5
−
2
i−3
) = 2
2i−1
− 2
i
. Therefore the nonlinearity of y
i
is
2
2
(2
2i−1
− 2
i
) = 2
2i+1
− 2
i+2
(using Theorem 1). So,
number of matches in the best linear approximation is
2
2i+2
− 2
2i+1
+ 2
i+2
= 2
2i+1
+ 2
i+2
and hence proba-
bility of matches is
1
2
+ 2
−i
. Therefore, bias of best
SECRYPT 2009 - International Conference on Security and Cryptography
286

linear approximation is 2
−i
, where 2 ≤ i < n. Since,
y
0
= x
0
⊕ k
0
, so bias of best linear approximation is
1
2
. For y
1
= x
1
⊕ k
1
⊕ x
0
k
0
, the bias is
1
4
. Therefore,
except the first two bits Nmix posses high nonlinearity
at all other bits.
4.2 Bias for XOR of Consecutive
Output Bits
From the definition of F, it is found that y
0
⊕ y
1
=
x
1
⊕k
1
⊕x
0
⊕k
0
⊕x
0
k
0
. Let f(x
0
,k
0
) = x
0
⊕k
0
⊕x
0
k
0
.
Since f is OR function so it has nonlinearity 1. There-
fore y
0
⊕ y
1
has nonlinearity = 2
2
.1 = 4 and bias
0.25. Similarly expression of y
1
⊕ y
2
is y
1
⊕ y
2
=
x
2
⊕ k
2
⊕ x
1
⊕ k
1
⊕ x
1
k
1
⊕ x
0
x
1
⊕ k
0
k
1
= x
2
⊕ k
2
⊕
x
1
(1⊕ k
1
⊕ x
0
) ⊕ k
1
(1⊕ k
0
) = x
2
⊕ k
2
⊕ x
1
p
1
⊕ k
1
q
1
,
where p
1
= 1⊕ k
1
⊕ x
0
and q
1
= 1⊕ k
0
. The nonlin-
earity of y
1
⊕ y
2
is 2
2
.6 = 24 and bias is 0.125. For
2 ≤ i < n, y
i
⊕ y
i+1
can be exressed as
y
i
⊕ y
i+1
= x
i+1
⊕ k
i+1
⊕ x
i
⊕ k
i
⊕ x
i
k
i
⊕
x
i−1
(x
i
⊕ x
i−2
) ⊕ k
i−1
(k
i
⊕ k
i−2
) (5)
If we assume a
i
= x
i
⊕ x
i−2
and b
i
= k
i
⊕ k
i−2
,
then y
i
⊕ y
i+1
= x
i+1
⊕ k
i+1
⊕ x
i
⊕ k
i
⊕ x
i
k
i
⊕ x
i−1
a
i
⊕
k
i−1
b
i
= f ⊕ g, where f = x
i+1
⊕ k
i+1
⊕ x
i
⊕ k
i
⊕ x
i
k
i
and x
i−1
a
i
⊕ k
i−1
b
i
. It is observed that f has nonlin-
earity 4 and g is in the form of four variable bent func-
tion, so it has nonlinearity 6. Therefore nonlinear-
ity of y
i
⊕ y
i+1
is 2
4
.6+ 2
4
.4− 2.4.6 = 112 and bias
of best linear approximation for y
i
⊕ y
i+1
is 0.0625,
where 2 ≤ i < n. In case of addition and Slash
modulo 2
n
the bias for best linear approximation of
y
i
⊕ y
i+1
= 0.025 for 0 ≤ i < n. Therefore, Nmix is
cryptographically stronger than other two functions.
4.3 Enhancing Nonlinearity of Nmix
It has been observed that bias for best linear approxi-
mation of the first (starting from y
0
) four/five output
bits of Nmix are not negligible. Therefore linear
cryptanalysis could be applied to recover at least few
key (K) bits. But twice application of Nmix : 1st
right to left and then from left to right using different
sequences, increases the overall nonlinearity hence
bias decreases drastically to a low value which makes
linear cryptanalysis difficult. As the number of bits
in a word increases the bias decreases more. Assume
Y = F
l←r
(X,R), where F
l←r
is the Nmix function
operates from right to left and X = (x
n−1
... x
1
x
0
),
Y = (y
n−1
... y
1
y
0
), R = (r
n−1
... r
1
r
0
) are three n-bit
variables. The bitwise expression of Y as follows
y
0
= x
0
⊕ r
0
y
1
= x
1
⊕ r
1
⊕ x
0
r
0
y
2
= x
2
⊕ r
2
⊕ x
0
r
0
⊕ x
1
r
1
⊕ x
0
x
1
⊕ r
0
r
1
.
y
n−1
= x
n−1
⊕ r
n−1
⊕ x
0
r
0
⊕ x
1
r
1
⊕ . . . ⊕
x
n−2
r
n−2
⊕ x
n−3
x
n−2
⊕ r
n−3
r
n−2
(6)
If Z = F
l→r
(Y, K), where F
l→r
is the Nmix function
operates from left to right and Y = (y
n−1
... y
1
y
0
),
K = (k
n−1
... k
1
k
0
), Z = (z
n−1
... z
1
z
0
) are three n-
bit variables then bitwise expression of Z is
z
n−1
= y
n−1
⊕ k
n−1
z
n−2
= y
n−2
⊕ k
n−2
⊕ y
n−1
k
n−1
z
n−3
= y
n−3
⊕ k
n−3
⊕ ... ⊕ y
n−1
y
n−2
⊕ k
n−1
k
n−2
.
z
0
= y
0
⊕ k
0
⊕ y
n−1
k
n−1
⊕ y
n−2
k
n−2
⊕ . . . ⊕
y
2
k
2
⊕ y
1
k
1
⊕ y
1
y
2
⊕ k
1
k
2
(7)
Using pilling-up lemma we compute bias for best
linear approximation of z
i
for 0 ≤ i < n.
Bias of z
0
is 2× 2
−1
× 2
−(n−1)
= 2
−(n−1)
Bias of z
1
is 2× 2
−2
× 2
−(n−2)
= 2
−(n−1)
Bias of z
2
is 2× 2
−2
× 2
−(n−3)
= 2
−(n−2)
Bias of z
n−1
is 2× 2
−1
× 2
−(n−1)
= 2
−(n−1)
Therefore after twice application of Nmix, the bias
for best linear approximation of z
i
depends on word
size n and maximum value of bias is
1
2
n−2
. Even for
8-bit word the maximum bias is
1
64
which makes
linear cryptanalysis more difficult.
4.4 Differential Cryptanalysis
Key mixing using nonlinear function Nmix offers dif-
ferential resistance. But the key mixing which is
done by XOR operator,does not provide any differen-
tial resistance as always ∆y = ∆x, which is indepen-
dent of the key. Assume X = (x
n−1
x
n−2
...x
0
), K =
(k
n−1
k
n−2
...k
0
) are two n-bit inputs of Nmix func-
tion and corresponding output is Y = (y
n−1
y
n−2
...y
0
),
where Y = F(X,K) and c
i
represents the carry from
the i
th
level. Let X
′
= (x
′
n−1
x
′
n−2
. . . x
′
0
) be another
n-bit input for same K = (k
n−1
k
n−2
...k
0
) and the out-
put is Y
′
= (y
′
n−1
y
′
n−2
. . . y
′
0
), where Y
′
= F(X
′
,K)
and c
′
i
represents the carry from the i
th
level. Then
∆y
i
= (y
i
⊕ y
′
i
) = ∆x
i
⊕ ∆c
i−1
, where ∆x
i
= x
i
⊕ x
′
i
and ∆c
i−1
= c
i−1
⊕ c
′
i−1
From equation (1) it can be
shown that
∆y
i
= ∆x
i
⊕ x
i−2
x
i−1
⊕ x
′
i−2
x
′
i−1
i−1
M
j=0
k
j
∆x
j
(8)
NMIX: AN IDEAL CANDIDATE FOR KEY MIXING
287
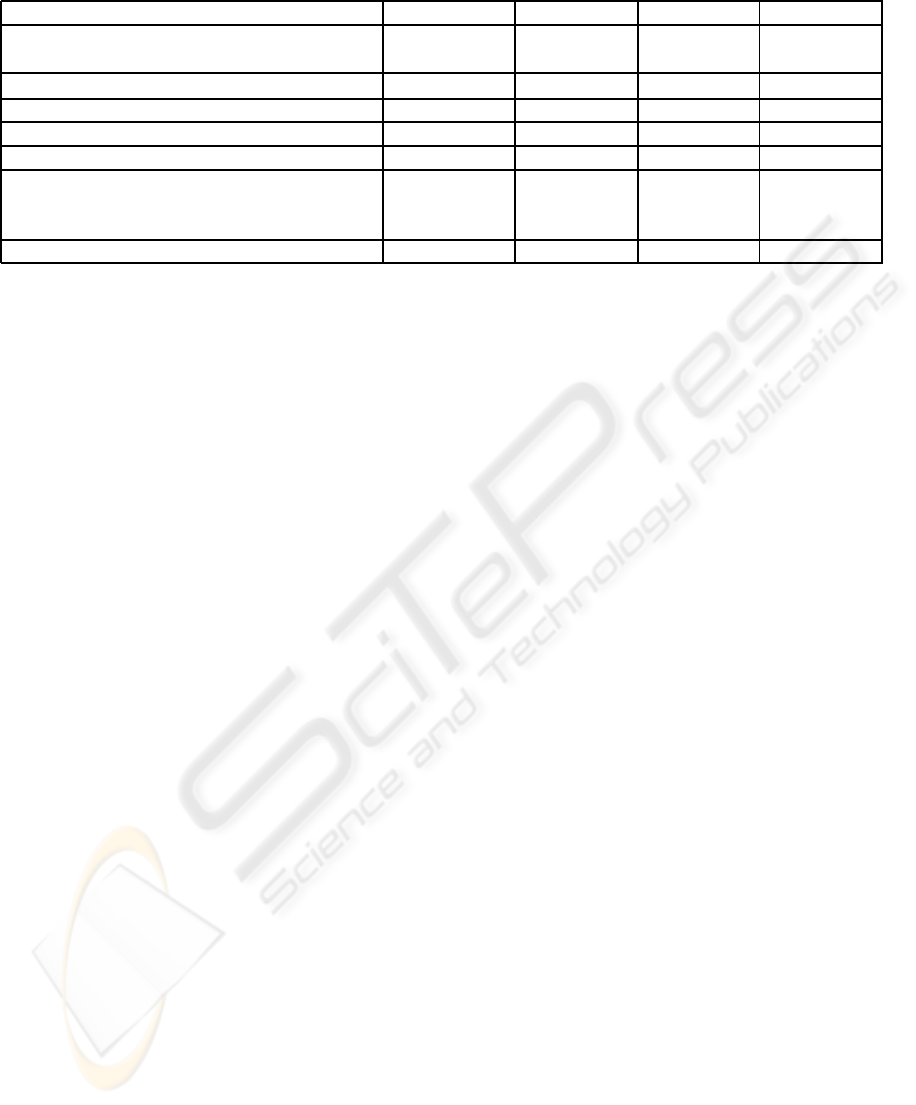
Table 1: Comparison of Over all Performance.
Parameters Bitwise XOR Addition Slash Nmix
Nonlinearity of output bit y
i
0 2
2i
2
2i+1
− 2
i+1
2
2i+1
− 2
i+2
Bias for best linear approx. of output bit y
i
0.5 0.25 2
−(i+1)
2
−i
Bias for best linear approx. of y
i
⊕ y
i+1
0.5 0.25 0.25 0.0625
Provide differential resistance No Yes No Yes
Algebraic degree of output bit y
i
1 i+ 1 2 2
Number of gates to implement n-bit function n XOR 2n+ 1 XOR 3n− 3 XOR 5n− 7 XOR
(froward transformation) 0 AND 2n− 4 AND n− 1 AND 3n− 5 AND
0 OR n− 2 OR 0 OR 0 OR
Time Complexity O(1) O(n) O(n) O(n)
So it is observed that the probability of a particu-
lar output difference ∆Y occurs given a particular in-
put difference ∆X is function of all x
i
’s and x
′
i
’s for
a fixed K. In other words Nmix has the property that
a given XOR difference does not necessarily yield a
fixed output difference. Therefore the proposed func-
tion provides differential resistance.
4.5 Comparison
In this section, we discuss cryptographic properties,
hardware and time complexity of our proposed func-
tion as well as exiting modular addition and Slash.
Table 1 shows a comparison of the proposed function
with the similar existing key mixing functions. From
table 1, it is observed that XOR provides no nonlin-
earity, modulo Slash has maximum nonlinearity and
Nmix has nonlinearity greater than modulo addition
but less compared to Slash. The bias for best lin-
ear approximation of y
i
decreases exponentially with
bit position in case of Nmix and Slash but remains
constant both in modulo addition and bitwise XOR.
Also the proposed function has lowest value for bias
of best linear approximation of y
i
⊕ y
i+1
compared
to other three functions. Similar to modulo addition,
Nmix provides differential resistance but bitwise XOR
and Slash does not provide any differential resistance.
Addition has higher algebraic degree compared to
both Slash and Nmix. To implement a n-bit key mix-
ing layer bitwise XOR requires minimum number of
logic gates. Proposed function needs 5n − 7 XOR
gates and 3n−5 AND gates to implement a n-bit mix-
ing layer. Bitwise XOR requires minimum computa-
tion time, whereas other three nonlinear mixing func-
tions have O(n) time complexity. Therefore Nmix is
an ideal key mixing function for cryptographic prim-
itives.
5 CONCLUSIONS
In this work, a highly nonlinear, balanced and re-
versible Boolean function Nmix has been proposed
which can be used as nonlinear key mixing func-
tion in block ciphers. It has been shown that the
proposed function provides higher nonlinearity com-
pared to modular addition. Therefore Nmix gives bet-
ter resistance against linear cryptanalysis. Also Nmix
provides resistance against differential attack.
REFERENCES
Bhaumik, J., Roy Chowdhury, D. (2009). An Integrated
ECC-MAC Based on RS code, In Transcations on
Computational Science, vol. 4, LNCS. 5430
Koo, W. K., Lee, H., Kim, Y. H. and Lee, D. H. (2008). Im-
plementation and Analysis of New Lightweight Cryp-
tographic Algorithm Suitable for WirelessSensor Net-
works, In ISA 2008, IEEE Computer Socity.
Bhattacharya, D., Mukhopadhyay, D., Saha, D. and Roy
Chowdhury, D. (2007). Strengthening NLS against
Crossword Puzzle Attack, In ACISP-2007, LNCS,
vol. 4586.
Sarkar, P.and Mitra, S. 2004. Construction of Nonlinear Re-
silient Boolean Functions Using “Small” Affine func-
tions, In IEEE Transactions on Information Theory,
vol. 50, no. 9.
Stinson, D. R. (1995). Cryptography Theory and Practice,
CRC Press, 1
st
edition.
Matsui, M. (1993). Linear cryptoanalysis method for DES
ciphers, In Eurocrypt 1993, LNCS, vol. 765.
Rothaus, O. S. (1976). On “Bent” Functions, In Journal of
Combinatorial Theory, vol. 20(A).
SECRYPT 2009 - International Conference on Security and Cryptography
288
