
DRIVERS AND BARRIERS TO THE ADOPTION OF WEB 2.0
Ashutosh Tiwari
1
, Rafael Navarro Fontestad
2
and Chris J. Turner
1
1
Decision Engineering Centre, School of Applied Sciences, Cranfield University, Bedfordshire, U.K.
2
Airbus CIMPA, New Filton House, Golf Course Lane, Filton, Bristol, U.K.
Keywords: Web 2.0, Business transformation, Knowledge management.
Abstract: Today, information overload and the lack of systems that provide employees with the right knowledge and
skills are common challenges that large organisations face. This can lead to knowledge workers re-inventing
the wheel due to problems in the retrieval of information from both internal and external sources. Web 2.0
tools aim to address this type of issue facilitating collaboration and knowledge sharing in a corporate
setting. This paper describes the benefits and constraints associated with the use of Web 2.0 tools and
identifies the drivers behind the adoption of such tools in industry. A number of landscape overview models
are presented here that attempt to describe the effect of using Web 2.0 tools on a knowledge based
organisation. An organisation, active in the construction industry, is the focus of a case study where Web
2.0 tools are matched to real knowledge sharing and collaboration problems.
1 INTRODUCTION
Implementing knowledge management practices
within a large organisation has always been a
challenge (Robinson et al., 2005). There are a
number of key reasons for this such as the division
of work into specialist functions, geographically
distributed teams and movement of team members
between functions and organisations. This poses a
problem for an organisation wishing to capture and
share the knowledge of its workforce; and often
leads to the need to ‘re-invent the wheel’ when staff
with the requisite knowledge are no longer available
to the organisation.
The emergence of a new set of web delivered
communication and collaboration technologies,
branded by some as Web 2.0 technologies (O’Reilly,
2005), has allowed for a reassessment of the
viability of IT enabled knowledge management
practice within industry. However, despite the clear
advantages that ‘Enterprise 2.0’ can bring, some
authors (Hoover, 2007; Wiens, 2007) have
expressed concerns about adoption hurdles that Web
2.0 technologies have to overcome. Some of those
concerns are security, lack of expertise of the
knowledge workers to be familiar with the new
tools, integration with legacy technologies,
difficulties in providing a measure on Return On
Investment (ROI) and reluctance to share
information (Daniel, 2007). This paper presents the
work carried out on a project to examine the role
Web 2.0 technologies could play in the knowledge
management strategies of industry. A case study is
presented concerning the re-evaluation of an intranet
portal of a large industrial organisation (involved in
the construction industry). The drivers and barriers
inherent in the adoption of Web 2.0 technologies in
industry are identified in this paper along with the
key technologies encompassed under the Web 2.0
banner.
2 METHODOLOGICAL
APPROACH
In essence a combination of interviews and
secondary research was used to deduce the
landscape overview models that result from this
work. The following phases were undertaken in the
completion of this project:-
Phase I: Characterising Web 2.0 – identifying
the main technology segments and products
that comprise Web 2.0
Phase II: Strengths and weaknesses of Web 2.0
for knowledge sharing – a detailed
examination of each of the software products
identified from phase I and a study of the
current knowledge architecture of the case
study organisation, including detailed
375
Tiwari A., Navarro Fontestad R. and J. Turner C.
DRIVERS AND BARRIERS TO THE ADOPTION OF WEB 2.0.
DOI: 10.5220/0002711803750378
In Proceedings of the 6th International Conference on Web Information Systems and Technology (WEBIST 2010), page
ISBN: 978-989-674-025-2
Copyright
c
2010 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
discussions with staff members of the
organisation
Phase III: Consolidation and
recommendations – the collation of the views
on Web 2.0 technologies and
recommendations on the future technologies
that are most likely to be important for the
learning organisation
Phase I involved the completion of an extensive
literature review in the area of Web 2.0
technologies. The review focussed on the use of
Web 2.0 in a corporate setting and also involved the
identification of technology areas Web 2.0 products
interact with. In total 17 experts (in the field of Web
2.0) were consulted (via. their professional blogs) in
the completion of this research.
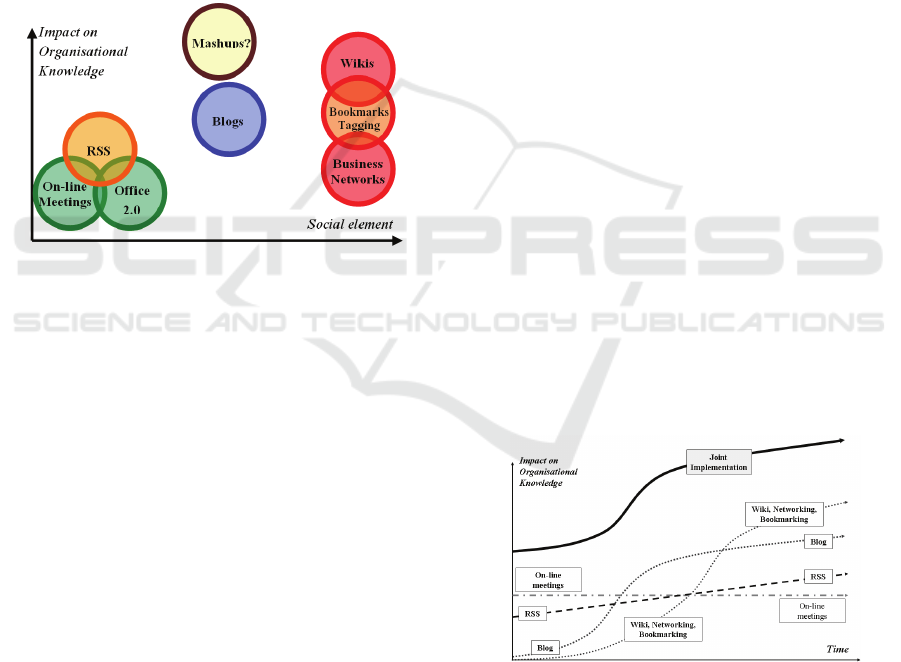
Figure 1: Landscape overview of Web 2.0 technologies
representing their impact on organisational knowledge
against the social element involved.
A landscape overview was constructed
identifying technology segments and products
(presented as a pictorial view of segments and
products and shown in Figure 1). This was
completed with the help of a number of senior
managers in a set of brainstorming sessions held at
the case study organisation. This information was
combined with the findings from secondary
published sources and expert opinions (via their
professional blogs). The location of the segments in
the landscape overview graphs shown in Figure 1
was based on the findings from this phase. A
research gap was drawn from this initial stage. In the
completion of phase II it was necessary to carry out
a new set of interviews and workshop sessions in
order to establish the current use of the case study
organisation’s intranet portal as a means for
knowledge sharing and re-use. An is-is of the current
intranet portal was constructed and from this
features of the portal were challenged against
potential benefits of Web 2.0 technologies (this
activity was carried out in a number of workshop
sessions completed at the case study organisation,
involving both managers and users of the portal).
Each identified Web 2.0 technology was tested and
evaluated for its relevance to the case study
organisation as part of this research. Phase III
brought together the findings of phase I and II and
delivered a set of recommendations for the
improvement of the intranet portal and an overview
of the technologies most likely to impact facilitation
of organisation knowledge sharing and re-use in the
future. Gap analysis was used to produce a set of
factsheets outlining the benefits of Web 2.0
technologies over the case study organisations
existing intranet based tools.
3 CHARACTERSING WEB 2.0
As mentioned in the methodology section of this
paper a landscape overview was constructed
identifying technology segments and products that
comprise Web 2.0 (shown in Figure 1). Figure 1
shows the impact on organisational knowledge that
each technology sustains if it succeeds in its
implementation against the social input required to
present reliable results. Figure 2 shows a second
landscape overview which details the impact on
organisational knowledge over time after
deployment of Web 2.0 technologies (the landscape
overview in Figure 2 is based on views expressed in
papers at the literature review stage and expert
opinion). Attention must be given to the shape of the
curves and their relative value in Figure 2. The top
curve in Figure 2 represents the synergy achieved
through a joint implementation (when all of the
technologies are implemented simultaneously).
Figure 2: Landscape overview of Web 2.0 technologies
representing their impact on organisational knowledge
against the time after they have been deployed.
This research has identified the following
technology segment classifications relevant to Web
2.0:
Corporate blogs
Enterprise wikis
WEBIST 2010 - 6th International Conference on Web Information Systems and Technologies
376

RSS platforms (Really Simple Syndication)
Business networks
Social bookmarking and tagging
Office 2.0 tools
On-line meetings
Enterprise mash-ups
Each of these segments satisfies drivers and
presents constraints for an organisation wishing to
implement the technologies the segments categorise.
An organisation wishing to address strategic drivers
in its business must weigh up the following benefits
and constraints presented for each segment:
Corporate blogs
Drivers: information dissemination, thought
leadership initiatives, community building
Constraints: culture change required
Representative products: Blogger, MovableType,
WordPress.
Enterprise wikis
Drivers: bridge gap between knowledge and its
development, Consensus building.
Constraints: culture change required
Representative products: Wikipedia, JotSpot,
SocialText, Kwiki, Editme.
RSS platforms
Drivers: email overload
Constraints: security, message content
Representative products: Google Reader, Feed
Burner, Attensa, Newsgator, Knownow.
Business networks
Drivers: user interaction, time reduction
Constraints: social rather than business use,
employee acceptance
Representative products: Face book, LinkedIn,
Xing BC
Social bookmarking and tagging
Drivers: time reduction in searching
Constraints: security, no standardisation
Representative products: Del.icio.us, Dogear,
Cogenz, Connectbeam.
Office 2.0 tools
Drivers: outsourcing of common desktop software
Constraints: security, bandwidth constraints, some
features missing
Representative products: GoogleDocs, Zoho,
24SevenOffice.
On-line meetings
Drivers: time savings, cost reduction
Constraints: need still exists for face to face
meetings
Representative products: TeamSlide, WebEx,
PresenterNet.
Enterprise mashups
Drivers: encourages re-use and recombination
Constraints: no common format, lack of suitably
enabled data sources
Representative products: Datamashups, JackBe,
AboveAll.
4 INDUSTRIAL CASE STUDY
The industrial case study consisted of a profound
review of the organisations intranet in order to
discover the areas in which ‘Web 2.0’ capabilities
would provide business benefits in their deployment
and use in a corporate setting. The analysis and
recommendations were carried out at strategic level.
4.1 Portal ‘as-is’ Model
The following sections characterised the original
portal –
People – each staff member had their own
self maintained profile page.
Projects – all current and previous project
descriptions were available from a set of
pages generated from a database.
Networks – provision of an on-line tool for
the user creation of a community of
practice.
Insight – best practices and feedback were
recorded on this page, allowing for their
retrieval.
Corporate – contained formal procedures,
policies and other corporate content.
4.2 Portal ‘to-be’ Model
The analysis was focused on delivering a set of
identified weaknesses in the portal and a set of
recommended solutions based on the potential of
‘Web 2.0’ and using both enterprise and user
focused web-based products. The results are listed
by the different ‘Web 2.0’ segments mentioned in
this paper.
News Customisation (RSS News Feeds). In the ‘as-
is’ portal there was limited scope for customisation
of the news service. The portal did not allow
subscriptions to either particular keywords, specific
news (depending on who was posting it), or external
news services such as journals, articles databases,
etc. It was suggested that the Google RSS reader
should be used due to its ability to organise, track
and share items based on keywords.
Incorporation of Social Bookmarking and a
Tagging Policy. The ‘as-is’ portal did not allow for
DRIVERS AND BARRIERS TO THE ADOPTION OF WEB 2.0
377

bookmarking. It was recommended that
bookmarking should become a feature of the ‘to-be’
portal. If the results have the capability of showing
which other users already have certain key words in
their bookmarking lists, it is likely that highlighted
users will possess other bookmarks relevant for that
search. The Cognez tool was recommended for this
task. It was also suggested that a policy should be
introduced for the tagging of discussion forum
threads.
Personal Network Capability. The ‘as-is’ portal
neglected to display the links between users of the
personal network facility. It was recommended that
a Social Network Analysis (SNA) tool should be
used to discover network hubs and key people inside
the organisation based on their network use.
Use of Wikis for Group Document Authorship. It
was recommended that the organisation should use a
wiki for the group authoring of documents such as
best practice guides where experts could add and
review document contents in an interactive fashion.
It was also recommended that this authoring method
could also be used for more formal documents. Such
documents require a final quality review by
definition, but group authorship through wiki
technology provides added value in a number of
cases:-
Best practice documents elaborated
between colleagues in the same ‘skills
network’
Technical documentation, user-case for
customer relationship management, project
life-cycle management among colleagues in
the same project team
Job profile description developed among
colleagues from different departments
possibly located in different offices
Contract development between the case
study organisation and its supply chain
partners
Project requirements, specifications,
contract details etc. which may be
developed in collaboration between the
case study organisation and its customers
White papers, strategic discussions, etc.
between the case study organisation and its
partners
Improvements on Email Management. It was
identified that employees in the case study
organisation experienced email overload. This
problem was seen as key, by the case study
organisation, creating difficulties in their
collaboration and communication processes.
Certainly the use of technologies such as RSS and
wikis (mentioned earlier in this section) can be used
to divert and manage a large amount of email traffic.
To address this it was suggested that the
organisation could utilise a social networking
platform, such as Face book to organise and filter a
large proportion of the email communication.
Limitations. It must be noted that there were a few
limitations encountered in the implementation of
these recommendations at the case study
organisation. For security purposes the case study
organisation limited the online methods for
communication between users. Instant messaging
was not allowed and blogging and media sharing
platforms were also limited. Also the introduction of
new email practices did not end the practice of group
emails.
5 CONCLUSIONS
The landscape overviews provided by this research
can help industrial organisations to better understand
the opportunities offered by Web 2.0 technologies
and drivers and constraints behind their adoption by
industry. Even with the continual evolution of
technology the principles behind the landscape
overviews remain relevant.
REFERENCES
Daniel, D., 2007. Seven Ways CIOs can introduce Web
2.0 technologies into the enterprise. CIO Business
Technology Leadership. Available at:
www.cio.com.au/index.php/id;1146975385 (Last
accessed: 8 January 2010)
Hoover, I., 2007. Web 2.0 tools in business: Proceed with
caution - enterprise 2.0 must overcome concerns about
security and ROI to gain a foothold in business. Bank
Systems & Technology, 44(4), pp. 41.
O’Reilly, T., 2005. What is web 2.0, Available at:
oreilly.com/web2/archive/what-is-web-20.html (Last
accessed: 8 January 2010)
Robinson, H.S., Carrillo, P., Anumba, C., and Al-
Ghassani, A., 2005. Knowledge management practices
in large construction organizations, Engineering,
Construction and Architectural Management, 12(5),
pp. 431 – 445.
Wiens, J., 2007. Is web 2.0 inherently insecure? Network
Computing, 18(7), pp. 22.
Wittemburg, K., 1995. Group asynchronous browsing on
the world wide web, Proceedings of the 4th
International World Wide Web Conference 1995,
Boston, MA.
WEBIST 2010 - 6th International Conference on Web Information Systems and Technologies
378
