
NEW PSEUDO NEAR COLLISION ATTACK ON TIGER
Dibyendu Mallik and Debdeep Mukhopadhyay
Department of Computer Science and Engineering, IIT Kharagpur, Kharagpur, India
Keywords:
Hash function, Tiger, Collision attacks, Pseudo collision, Meet in the middle attack.
Abstract:
Tiger is a cryptographic hash function created by Anderson and Biham in 1996 with hash value of 192 bits.
Reduced round variants of Tiger have shown some weaknesses recently. Kelsey and Lucks have shown a
collision attack on Tiger reduced to round 16 and 17. Mendel and Rijmen have found 1 bit pseudo near
collision for full round Tiger. In this article we discover a new key schedule differential for Tiger which leads
to the finding of message pairs for 1-bit pseudo near collision.
1 INTRODUCTION
Tiger is a cryptographic hash function proposed by
Anderson and Biham in 1996 (Anderson and Biham,
1996). It has a block cipher like construction and op-
erates on 512 bit messages, which serves as the key
in the block cipher mode. In addition, there is a 192
bit Initial Values (IV). The final hash value is of 192
bit. There are 24 rounds in the hash function plus an
additional feedforward step at the end. Recent works
show well known hash function families, like MD4
(Rivest, 1990) can be subjected to collision attacks
by the techniques proposed in (Yu and Wang, 2007;
Dobbertin, 1998). However till now no collision at-
tacks on full round Tiger have been discovered.
Tiger has drawn the attention of several re-
searchers around the world and there has been some
interesting works on collision attacks on reduced vari-
ants of the hash function. In FSE 2006 Kelsey
and Lucks presented a collision attack on 16 and 17
rounds of Tiger, out of the total 24 rounds (Kelsey
and Lucks, 2006). The complexity of the attack is
2
44
evaluations of the compression function of Tiger.
They also presented a 1 bit pseudo near collision
for a variant of Tiger reduced to 20 rounds with a
complexity of 2
64
. In Indocrypt 2006 Mendel et
al. presented collision attack on Tiger reduced to
19 rounds(Mendel et al., 2006). In Asiacrypt 2007,
Mendel and Rijmen presented a pseudo collision at-
tack on full round Tiger (Mendel and Rijmen, 2007).
The complexity of the attack was around 2
47
compu-
tations of the compression function of Tiger.
Contribution. In the present paper, we revisit the
collision problem in Tiger Hash function and present
some new results. We identify a new key schedule dif-
ferential which leads to 1-bit pseudo near collision of
full round Tiger. To find key schedule differential we
have ensured that the message differences generated
by the key scheduler, should have large number of ze-
ros at the starting and final rounds, to reduce the num-
ber of conditions on the message bits in the first and
last round. Hence the key schedule helps in easy find-
ing of consistent colliding pairs, which are reported in
the paper.
The organization of the paper is as follows:Section
2 presents a high level description of the Tiger hash
function. The attack strategy is described in section
3. Section 4 details the 1-bit pseudo near collision at-
tack on full round Tiger, while the work is concluded
in section 5.
2 HIGH LEVEL DESCRIPTION
OF TIGER HASH FUNCTION
Tiger has 2 distinct parts: a key schedule and a
state update transformation. A detailed description
of the function can be found in (Anderson and Bi-
ham, 1996). The notations followed in this article are:
⊕ (XOR), ∆
⊕
(XOR difference), ∆ (Modular differ-
ence), + (modulo 2
64
addition), * (modulo 2
64
mul-
tiplication), - (modulo 2
64
substraction), ¬ (bitwise
NOT), I (2
63
), I
′
(2
40
), I
′′
(2
81
).
427
Mallik D. and Mukhopadhyay D. (2010).
NEW PSEUDO NEAR COLLISION ATTACK ON TIGER.
In Proceedings of the International Conference on Security and Cryptography, pages 427-430
DOI: 10.5220/0002940104270430
Copyright
c
SciTePress

2.1 State Update Transformation
The state update transformation of Tiger starts from
an initial value of three 64 bit words and updates
them in three passes of eight rounds each and after 24
rounds an additional feedforward round is added. For
details of state update transformation see (Anderson
and Biham, 1996)
2.2 Key Schedule
Each round of Tiger uses one message word X
i
as its
round key. The 512 bit message block is divided into
8 byte message X
0
, X
1
, X
2
, X
3
, X
4
, X
5
, X
6
, X
7
which
are used as the keys of the first 8 rounds. The remain-
ing 16 rounds key are generated by an invertible op-
eration. The KeySchedule operation modifies its input
in two passes.
3 ATTACK STRATEGY
In this section we briefly discuss the attack strategy
of Kelsey et. al. and Mendel to perform collision
attacks on the Tiger hash function. However it may be
noted that the final feedforward step is omitted in both
cases. This attack strategy belongs to a general class
of cryptanalysis as presented in (Kelsey and Lucks,
2006) and (Mendel and Rijmen, 2007). The attack
can be stated as follows:
1. A differential characteristic in the key schedule
which holds with high probability is found. In
ideal case the probability should be 1.
2. Certain message bits are modified to obtain de-
sired difference value in the Tiger state variables
which can be canceled by the difference in mes-
sage words in the subsequent rounds.
3.1 Finding a Good Differential
Characteristic for Key Schedule of
Tiger
The objective of this step is to find key schedules with
certain desirable properties. We first observe possible
differences in the state variables for the i
th
step, which
can be canceled by suitable message differences in
steps i, i + 1 and i + 2. Such possible difference val-
ues are noted in table 1. The cancellation needs to
take place at the final round of the hash function. The
objective was that the message difference generated
by the keyscheduler should have a large number of 0s
at the starting and final rounds. To find such good dif-
ferentials, we linearize the operations in GF(2) and
Table 1: Canceling message and state variable differences.
State Variable Difference Message Difference
∆A
i−1
∆B
i−1
∆C
i−1
∆X
i+2
∆X
i+1
∆X
i
0 0 I 0 0 I
0 I 0 I 0 0
0 I I I 0 I
I 0 0 0 I 0
I 0 I 0 I I
I I 0 I I 0
I I I I I I
choose those which have a high probability of occur-
rence in the real hash function.
3.2 Message Modification by Meet In
The Middle
For any i
th
step of Tiger let the state variables be de-
noted by A
i−1
, B
i−1
, C
i−1
and the corresponding dif-
ferential pairs by A
∗
i−1
, B
∗
i−1
, C
∗
i−1
. The modular dif-
ference ∆(A
i−1
) = A
∗
i−1
− A
i−1
. Similarly, the other
differences ∆(B
i−1
) and ∆(C
i−1
) are defined. We as-
sume we are given all these values. Then the modular
difference δ = ∆(C
i+1
) (refer figure 1) can be forced
to any desired value with probability
1
2
using birthday
attack. We try all 2
32
possibilities of B
i+1
[even] to
generate 2
32
candidates for the ∆(even(B
i+1
)). Then
we use meet in the middle approach to solve the fol-
lowing equation. The algorithm can be stated as fol-
lows.
1. Store the 2
32
candidates for ∆odd (B
i
) in a table.
2. For all 2
32
candidates for ∆even(B
i+1
)
test if ∆odd (B
i
) exists with: ∆odd (B
i
) =
(∆even(B
i+1
) + δ)∗ mult
−1
− ∆(B
i−1
)
A CB
even
odd
X
i
even
odd
X
δ
i+1
i−1
i−1
i−1
Figure 1: Meet in The Middle Attack.
This technique takes some 2
32
evaluations of each
functions even and odd and 2
32
units of storage
space. From our assumption, we know the value
of C
i−1
. Fixing the value of X
i
[even], the value of
C
i
[even] gets known. Since the meet-in-the-middle
SECRYPT 2010 - International Conference on Security and Cryptography
428
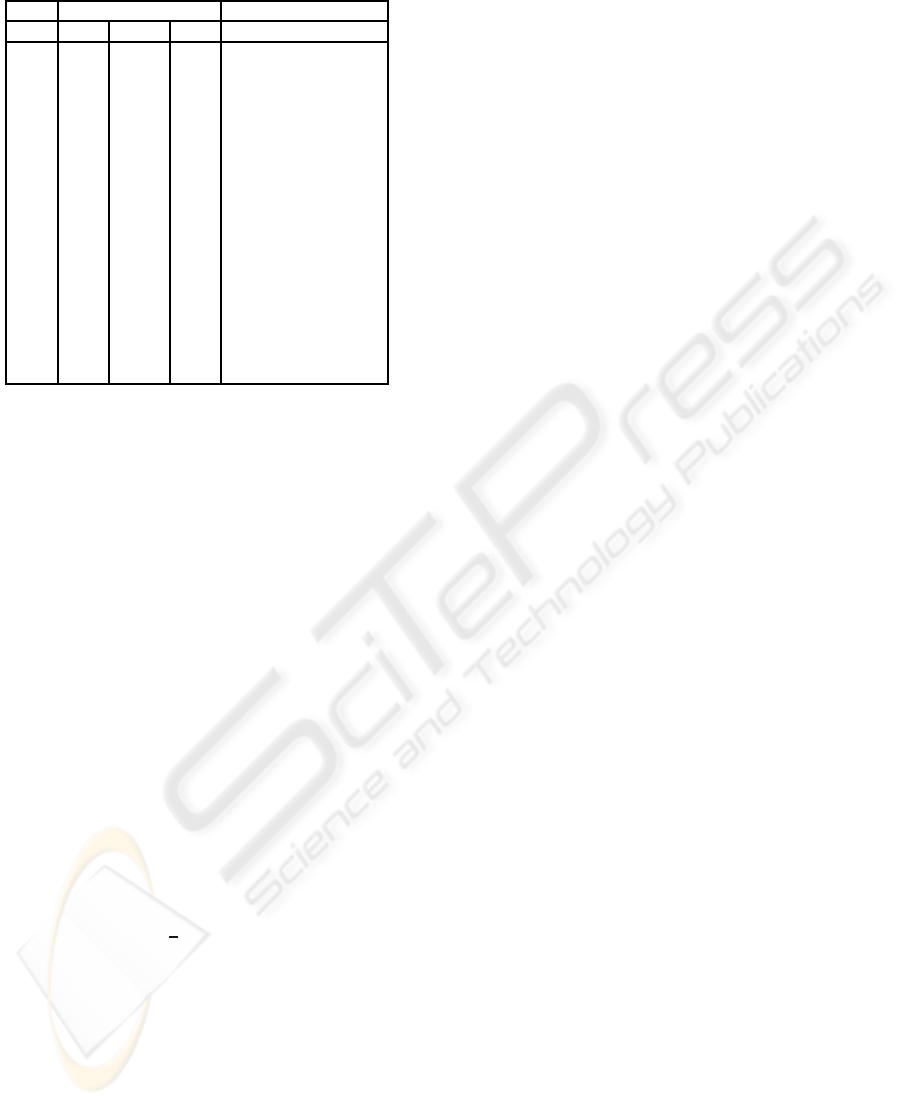
Table 2: Propagation of state variable.
step State Variable Message Difference
i ∆A
i
∆B
i
∆C
i
∆(X
i+1
)
-1 0 0 I I
0 0 0 0 0
1 0 0 0 0
2 0 0 0 0
3 0 0 0 I+I
′
4 * I + I
′
* I
5 * * * I
′′
6 * * * 0
7 * * * I
8 * * * 0
9 * * * I
10 * * K
⊕
0
11 * K
+
L
⊕
I
12 0 L
+
I 0
13 0 I 0 0
14 I 0 0 0
15 0 0 I I
attack produces ∆B
i+1
(even) and ∆B
i
(odd) satisfy-
ing, X
i
[odd] = C
i−1
[odd] ⊕ B
i
[odd] and X
i+1
[even] =
C
i
[even] ⊕ B
i+1
[even] we are able to compute 64 local
message bits.
4 1-BIT PSEUDO COLLISION ON
FULL ROUND OF TIGER
In this section we present a pseudo near collision of
full round Tiger including the feedforward round but
for different key schedule differential as observed in
(Mendel and Rijmen, 2007). Table 1 shows that mes-
sage differences (∆X
i
, ∆X
i+1
, ∆X
i+2
) = (I, 0, 0) can be
canceled out by introducing state variable difference
(0, 0, I) at (i − 1)
th
step. Now introducing message
difference I, 0, 0 at 16, 17, 18
th
round and setting all
the message differences of the final round of Tiger
to 0, we obtain the following key schedule differ-
ential by running the inverse key schedule opera-
tion: (I, 0, 0, 0, I + I
′
, I
′
, I
′′
, 0) → (I, 0, I, 0, 0, 0, 0, 0) →
(I, 0, 0, 0, 0, 0, 0, 0) The key schedule differential
holds with probability
1
8
which is quite high and con-
tains four and seven zeroes at the initial and final
round respectively. Therefore, this differential fol-
lows the property of good differential as mentioned in
section 4. In order to create collision after 23
rd
round
we have to create a collision after 16
th
round of Tiger
ie, (∆A
16
, ∆B
16
, ∆C
16
) = (0, 0, 0). Therefore the state
variable difference at 15
th
round should be (0, 0, I).
Now if we generate state variable difference (0, I, 0)
at 13
th
round then the difference propagates to 15
th
round and produces the desired difference. The state
variable propagation is shown in table 2. To create
∆B
13
= I we have to force ∆C
12
to I and as ∆A
13
= 0,
the difference ∆odd(B
13
) = odd (B
13
)−odd (B
13
⊕ I)
should be canceled out by creating its opposite mod-
ular difference L
+
at B
12
. In order to create the de-
sired difference ∆B
12
we force ∆C
11
to a low weight
Hamming difference L
⊕
(Hamming weight of L
⊕
is
10 to optimize the complexity of meet in the middle
attack) by message modification technique such that
the modular difference L
+
and the XOR difference L
⊕
are consistent. We use the same definition of consis-
tency as mentioned in Mendel and Rijmen.(Mendel
and Rijmen, 2007). Let L
′
be the set of all modular
differences L
+
which are consistent. For the propa-
gation of desired difference from C
12
to B
13
the mod-
ular differences should be consistent. Therefore we
construct the set L as follows:
L =
L
+
∈ L
′
: L
+
= odd(B
13
⊕ I) − odd(B
13
)
The size of the set L is related to the Hamming weight
of L
⊕
. It is observed from the round structure of
Tiger that to get the desired difference ∆C
13
= 0,
∆A
12
should be 0. Therefore from the construction of
Tiger it is observed that the difference ∆odd(B
12
) =
odd(B
12
)− odd(B
12
⊕ L
⊕
) should be canceled out by
introducing an opposite modular difference K
+
at B
11
by forcing ∆
⊕
C
10
to an XOR difference K
⊕
(of Ham-
ming weight 8) which is consistent to K
+
. We con-
struct the set K from the set K
′
which is the set of all
consistent modular differences K
+
as follows:
K =
K
+
∈ K
′
: K
+
= odd(B
12
⊕ L
⊕
) − odd(B
12
)
These sets are computed only one time in this attack.
It has complexity of about 2
33
.
4.1 Construction of Desired Differences
We have to know ∆A
8
, ∆B
8
and ∆C
8
for the meet-
in-the-middle attack to force ∆C
10
to K
⊕
. For this
we choose random values for B
3
and B
4
and com-
pute A
4
= (B
3
+ odd(B
4
)) ∗ mult, its corresponding
differential A
∗
4
and ∆C
4
= ∆even(B
4
). Since there is
no difference in X
3
, B
3
and C
3
we get ∆(B
4
) = I + I
′
.
Choosing random value for B
5
we can calculate the
vales of all the state variables of step 5. Again choos-
ing arbitrary values for X
6
, X
7
and X
8
we calculate
the values of A
8
, B
8
, C
8
and their corresponding dif-
ferential values A
∗
8
, B
∗
8
, C
∗
8
are also calculated. These
operations fix the message words X
5
, X
6
, X
7
and X
8
.
As the values of ∆A
8
, ∆B
8
and ∆C
8
are known
now, desired XOR difference ∆C
10
, can be con-
structed by using message modification technique.
For all modular difference in K
+
we do a message
modification step and check if ∆(C
10
) = K
⊕
. This ex-
periment holds with probability of 2
−8
, as the Ham-
ming weight of K
⊕
is 8. The message modification
NEW PSEUDO NEAR COLLISION ATTACK ON TIGER
429

technique holds with probability
1
2
because of Birth-
day Paradox. Therefore, success probability of the
attack is
1
2
∗ (2
−8
)∗ |K| =
1
2
. This step has complexity
of about 2
41
computations. This step fixes the mes-
sage words X
10
[even] and X
9
[odd].
Choosing some random values for X
9
[even](and
its corresponding differential pair), ∆A
9
, ∆B
9
and ∆C
9
which are needed for meet in the middle step to force
the value of ∆C
11
to L
⊕
are calculated. We again
apply message modification technique to construct
the target difference. For all modular difference in
L
+
we do a message modification step and check if
∆(C
11
) = L
⊕
. This experiment holds with probabil-
ity of 2
−10
, as the Hamming weight of L
⊕
is 10. The
message modification technique holds with probabil-
ity
1
2
. Therefore, success probability of the attack
is
1
2
∗ (2
−10
) ∗ |L| =
1
2
. This step has complexity of
about 2
41
computations. This step fixes X
10
[odd] and
X
11
[even].
To generate the message difference in 11
th
round
we again apply a message modification techniques.
This step fixes the message word X
12
[even] and
X
11
[odd]. XOR difference and modular difference
by I is interchangeable with probability 1 and the
message modification step succeeds with
1
2
. There-
fore this step succeeds with probability
1
2
and com-
plexity of 2
36.5
evaluation of the compression func-
tion.(Mendel and Rijmen, 2007)
4.2 Constructing the Message Word
The attack fixes the words X
6
to X
12
and X
13
[odd].
To compute the values of the message word X
8
to X
15
we choose random value for X
13
[even].
From our known values we can calculate X
14
and
X
15
from the following equations: X
14
= (X
6
−
(X
13
⊕ X
12
⊕ (¬(X
12
+ (X
11
⊕ (¬X
10
≫ 23))) ≫
23))) + X
13
, and X
15
= (X
7
⊕ (X
14
− X
13
)) − (X
14
⊕
0123456789ABCDEF) ≫ 23))) + X
13
. After know-
ing the values of X
8
. . . X
15
we run the inverse key
schedule operation of Tiger to compute X
0
to X
7
.
4.3 Constructing the Initial Values of
State Variables
After knowing the values of X
0
to X
7
we can run Tiger
rounds in backward direction to get the initial values.
As the valuesof A
8
, B
8
, C
8
are knownwe can calculate
the values of A
−1
, B
−1
, C
−1
by backward propagation.
To cancel out the message differences ∆X
0
we apply
an initial value difference ∆C
−1
= I.
5 CONCLUSIONS
In this paper we have identified a new key sched-
ule differential for the Tiger hash function. We have
shown how the key schedule differentials can be ap-
plied to obtain a 1-bit pseudo near collision attack of
complexity of 2
47
for full round Tiger. Finding of a
new key schedule differential for 1-bit pseudo near
collision attack shows security margins of Tiger is not
as high as it was expected.
REFERENCES
Anderson, R. J. and Biham, E. (1996). Tiger: A fast new
hash function. In Gollmann, D., editor, FSE, volume
1039 of LNCS, pages 89–97. Springer.
Dobbertin, H. (1998). Cryptanalysis of md4. J. Cryptology,
11(4):253–271.
Kelsey, J. and Lucks, S. (2006). Collisions and near-
collisions for reduced-round tiger. In FSE, volume
4047 of LNCS, pages 111–125. Springer.
Mendel, F., Preneel, B., Rijmen, V., Yoshida, H., and
Watanabe, D. (2006). Update on tiger. In IN-
DOCRYPT, pages 63–79.
Mendel, F. and Rijmen, V. (2007). Cryptanalysis of the tiger
hash function. In Kurosawa, K., editor, ASIACRYPT,
volume 4833 of LNCS, pages 536–550. Springer.
Rivest, R. L. (1990). The md4 message digest algorithm. In
Menezes, A. and Vanstone, S. A., editors, CRYPTO,
volume 537 of LNCS, pages 303–311. Springer.
Yu, H. and Wang, X. (2007). Multi-collision attack on
the compression functions of md4 and 3-pass haval.
In Nam, K.-H. and Rhee, G., editors, ICISC, volume
4817 of LNCS, pages 206–226. Springer.
SECRYPT 2010 - International Conference on Security and Cryptography
430
