
GETTING HELP IN A CROWD
A Social Emergency Alert Service
Andreas Geyer-Schulz, Michael Ovelg¨onne and Andreas C. Sonnenbichler
Information Services and Electronic Markets, Institute of Information Systems and Management
Karlsruhe Institute of Technology (KIT), D-76128 Karlsruhe, Germany
Keywords:
Emergency recommender, Social network analysis, Modularity clustering, Restricted random walk clustering,
Bystander effect.
Abstract:
This paper presents the conceptual design of an emergency alert service which addresses the problem of getting
help in a crowd. The design is based on the results of more than 30 years of research in social psychology on
the bystander effect and it addresses the obstacles for helping by directing an alert directly to the members of
the victim’s social group who happen to be near the location of the emergency event. The proposed emergency
recommender design combines the general availability of geo-location services with social clusters available
either from the analysis of social web-sites or from communication analysis. For this purpose, two recently
developed innovative clustering methods are used. The feasibility of the design is evaluated by simulating
emergency events on the MIT reality mining data set.
1 INTRODUCTION
On Saturday, the 12th of September 2009, 50-year
old Dominik Brunner was brutally murdered in a Mu-
nich S-Bahn station (Spiegel Online, 2009b). The
attack on Dominik Brunner was observed by 15 pas-
sengers (Spiegel Online, 2009c) and transmitted and
recorded by his mobile-phone on the open police
emergency channel (Spiegel Online, 2009a).
This tragic incident reminds social psychologists
of the murder of Kitty Genovese on March 13th, 3:20,
1964 in Queens, New York. Kitty Genovese was
stalked, stabbed, and sexually assaulted near her own
apartment building. During the attack on her she
screamed and broke free twice. 38 of her neighbors
witnessed the attack, but no one intervened. After 45
minutes one man called the police, but at this point in
time Kitty Genovese was dead.
This incident motivated the study of social pro-
cesses in emergency situations by Darley and Latan´e
(Latan´e and Darley, 1970) and it points to the short-
comings and problems of real emergency response
organizations and their management which very re-
cently have become the object of scientific research
e.g. (Yuan and Detlor, 2005), (Faraj and Xiao, 2006),
(Chen et al., 2008), and (Comfort et al., 2009). The
mobile phone of the victim transmitting and record-
ing to the end confirms Palen and Liu’s thesis of the
increasing availability of ICT and its use in an emer-
gency by citizens and also their observation, that the
traditional hierarchical command-and-control report-
ing system of emergency response organizations may
not be adequate and “does not include built-in consid-
erations for the important roles that members of the
public play as participants” (Palen and Liu, 2007, p.
729). Public participation in emergencies and disas-
ters is active and altruistic. First responders are of-
ten not the trained professionals of an emergency re-
sponse organization who are sent to the incident, but
the people from the local and surrounding communi-
ties. They provide first-aid, transport victims to the
hospital, and begin search and rescue (Palen and Liu,
2007, pp. 728-729). In the case of Dominik Brunner
we may speculate whether a fast activation of his so-
cial community parallel to the emergency call could
have saved his life.
The paper starts with a short review of the social
processes which Darley and Laten´e have identified
as obstacles for helping in emergencies in section 2.
These obstacles have become known as the bystander
effect: The more bystanders, the less likely the victim
will receive help. We address the bystander effect by
a social emergency alert service and discuss how so-
cial emergency alert services may help in improving
these processes in emergency settings by activating
the nearby members of the victim’s social network.
207
Geyer-Schulz A., Ovelgöenne M. and S. Sonnenbichler A. (2010).
GETTING HELP IN A CROWD - A Social Emergency Alert Service.
In Proceedings of the International Conference on e-Business, pages 207-218
DOI: 10.5220/0002982102070218
Copyright
c
SciTePress

Step 1
Notice that
something
is happening
Step 2
Interpret
event as an
emergency
Step 3
Take
responsibility
for helping
Step 4
Decide
how to
help
Emergency
Step 5
Provide
help
Distraction
Self-concerns
Stop fooling around kids,
we are here to eat.
I’m late for a very
important date.
Audience
inhibition
Costs
exceed
rewards
I’ll look like a fool.
What if I do something
wrong? He’ll sue me.
Lack of
competence
I’m not trained
to handle this,
and whom can I call?
Diffusion of
responsibility
Someone else must
have called the
police.
Ambiguity
Is she really sick
or just drunk?
Relationship
between
attacker and
victim
They have to resolve
their own family
problems.
Pluralistic
ignorance
No one else
seems
concerned.
Figure 1: The social help process: 5 steps leading to assistance.
For the process of giving and receiving help, we
propose to monitor social interactions and to iden-
tify the social clusters of the victims and to locate
the nearest members of the social cluster of the vic-
tim in an emergency for notification purposes. In sec-
tion 3 we present details on the social emergency alert
service for getting help in a crowd and in section 4
we discuss implementation variants of realizations of
such services based on readily available technology
by the telecommunication and Internet industry.
The architecture for the prototype of the service
which is currently implemented is presented in sec-
tion 5.
For social cluster identification, recently devel-
oped fast algorithms for graph clustering are pre-
sented in section 6.
Section 7 of this paper aims at assessing the
chances that the social emergency alert service pre-
sented has in reality. For this purpose, a first attempt
is made to answer three questions which play a cru-
cial role for the success of a social emergency alert
service:
1. Has the victim in an emergency a chance to trans-
mit a request for help?
2. Is someone of his social network nearby?
3. Will this person really help?
2 THE UNHELPFUL CROWD:
FIVE STEPS TO HELPING IN
AN EMERGENCY
The murder of Kitty Genovese in 1964 in Queens,
New York, in front of 38 witnesses who did not in-
terfere led Darley and Latan´e to start investigating
the social psychological processes at work in this in-
cident. Their research revealed that the more by-
standers, the less likely the victim will be helped. This
is the bystander effect: The presence of others inhibits
helping. One of the reasons for this is the diffusion of
responsibility (Darley and Latan´e, 1968). Darley and
Latan´e (Latan´e and Darley, 1970) provided a care-
ful analysis of the process of emergency intervention
shown in figure 1. Unfortunately, many obstacles to
helping must be overcome. At each step, however,
psychological factors are at work which explain why
people fail to help:
1. Noticing. The presence of others distracts at-
tention from the victim. People who live in big
cities may filter out people lying on sidewalks or
screams (stimulus overload (Milgram, 1970)).
2. Interpreting. People must interpret the meaning
of what they perceive. Their perception may be
ambiguous: Cries of pain may be taken for laugh-
ter, hypoglycemia may be taken for drunkenness
(e.g. (Clark and Word, 1972), (Piliavin et al.,
1975)). A perceivedrelationship between attacker
and victim may lead the observers to think that
everything is OK (Shotland and Straw, 1976). If
an emergency happens, the most powerful infor-
mation available is often what other people do.
However, if everybody looks on everybody else
to get clues on what to do, the whole group is suf-
fering from pluralistic ignorance and everybody
concludes that help is not needed (e.g. (Miller and
McFarland, 1987), (Monin and Norton, 2003)).
3. Take Responsibility. When help is needed, who
is responsible for providing it? The diffusion of
responsibility means that people belief that oth-
ers will or should help. The effect usually is
strengthened by anonymity and considerably re-
duced by a reduction in psychological distance.
Groups with members who know each other are
more helpful than strangers. See e.g. (Garcia
et al., 2002), (Rutkowski et al., 1983), (Baumeis-
ter et al., 1995).
ICE-B 2010 - International Conference on e-Business
208

4. Decide how to Help. Bystanders are more likely
to offer direct help if they feel competent to per-
form the actions required (e.g. (Shotland and
Heinold, 1985), (Cramer et al., 1988)).
5. Provide Help. Some people may feel too em-
barrassed to provide help in a public setting (au-
dience inhibition). However, when people think
they will be scorned by others for failing to pro-
vide help, the presence of an audience will in-
crease their helpful actions. See (Schwartz and
Gottlieb, 1980).
In addition, a series of other variables have a high
influence on helping behavior as experiments in so-
cial psychology have shown: Time pressure reduces
the tendency to help (e.g. (Darley and Batson, 1973),
(Batson et al., 1978)). Group membership and em-
pathy and attractiveness interact: empathy is a posi-
tive predictor for help for in-group members, whereas
attractiveness works for out-group members (St¨urmer
et al., 2005). Group membership positively influences
help for in-group members, and the group bound-
aries can be shifted by proper priming (Levine et al.,
2005). Group status and group identification influ-
ence the willingness of receiving help (Nadler and
Halabi, 2006).
But what can you do to receive help in a crowd?
Try to counteract the ambiguity of the situation by
making it clear that you need help, and try to reduce
the diffusion of responsibility by addressing a specific
individual for help, keep eye contact, point or direct
requests (e.g. (Moriarty, 1975), (Shotland and Steb-
bins, 1980)). Consistent with this is a recent study
of P. Markey (Markey, 2000) of people in Internet
chat rooms: If the number of individuals is large in a
chat room, individuals react slower to a plea for help.
However, addressing a specific individual by his name
leads to considerably faster help and eliminates this
effect.
Research on the bystander effect in social psychol-
ogy showed that even weak social links matter and in-
crease the chance of a victim to receive help consid-
erably. This fact is the main motivation to send alerts
to the geographically close members of the victim’s
social group.
The asymmetric perception of social links (e.g.
(Hoser and Geyer-Schulz, 2005)), the role of weak
ties, and the cultural norms of the community play a
major role in the formation of the social group of the
victim. The asymmetric perception of social links im-
plies that a person may not be really aware of possible
helpers in his loose social contacts. Taken together
with cultural norms, even professional acquaintances
are potential helpers. The role of weak ties for net-
works has been studied by M. Granovetter ((Gra-
novetter, 1973) and (Granovetter, 1982)). In the con-
text of information diffusion on open jobs Granovet-
ter observed that “it is remarkable that people receive
crucial information from individuals whose very exis-
tence they have forgotten” (Granovetter, 1973, p. 14).
This is an indication that an explicit list of emergency
contacts provided by the subscriber of such an emer-
gency service will considerably limit the effectiveness
of such a service, because of these social phenomena.
3 GETTING HELP IN A CROWD
- A SOCIAL EMERGENCY
ALERT SERVICE
Getting help in a crowd is a social emergency alert
service selecting nearby members of the social group
of the victim and notifying them about the victim’s
need for help and the victim’s location. With this
service we aim to activate the locally available social
network of the victim and to eliminate the bystander
effect.
The UML sequence diagram depicted in figure 2
shows the generic process in an emergency incident.
It is designed on a high-level, abstract way allowing
a variety of industrial implementations. We will ad-
dress this issue in section 4.
An emergencynotification is submitted by the vic-
tim by starting an application on his mobile device
(
LaunchEmergenyApplication
in figure 2) e.g. by
pressing the help-button shown in figure 5. The ap-
plication retrieves the current geo-position. Both,
the ID of the emergency caller and his geo-location
are then transmitted to the emergency alert service
(
EmergencyAlert
in figure figure 2).
For discovering the most likely person to help
in the victim’s social network, his social network
has to be known and possible helpers identified
(
GetHelperCluster
in figure 2). The network is ei-
ther built from social interaction data from e-mail,
sms, phone, and mobiles where the number of in-
teractions is taken as an indication of social near-
ness or from social web sites as for example Face-
book or Xing. However, the number of social interac-
tions may be ambiguous as a recent incident (Rungg,
2010) of a woman threatened by her former husband
with Googles Buzz has shown: So the possibility to
check for such unwanted relations must be provided
for the participants of the emergency alert service
(
FilterCandidates
in figure 2). Usually social net-
works tend to be very large. As emergencies are often
time-critical, it might take too long to calculate such a
network on-the-fly. The network is pre-built and up-
GETTING HELP IN A CROWD - A Social Emergency Alert Service
209
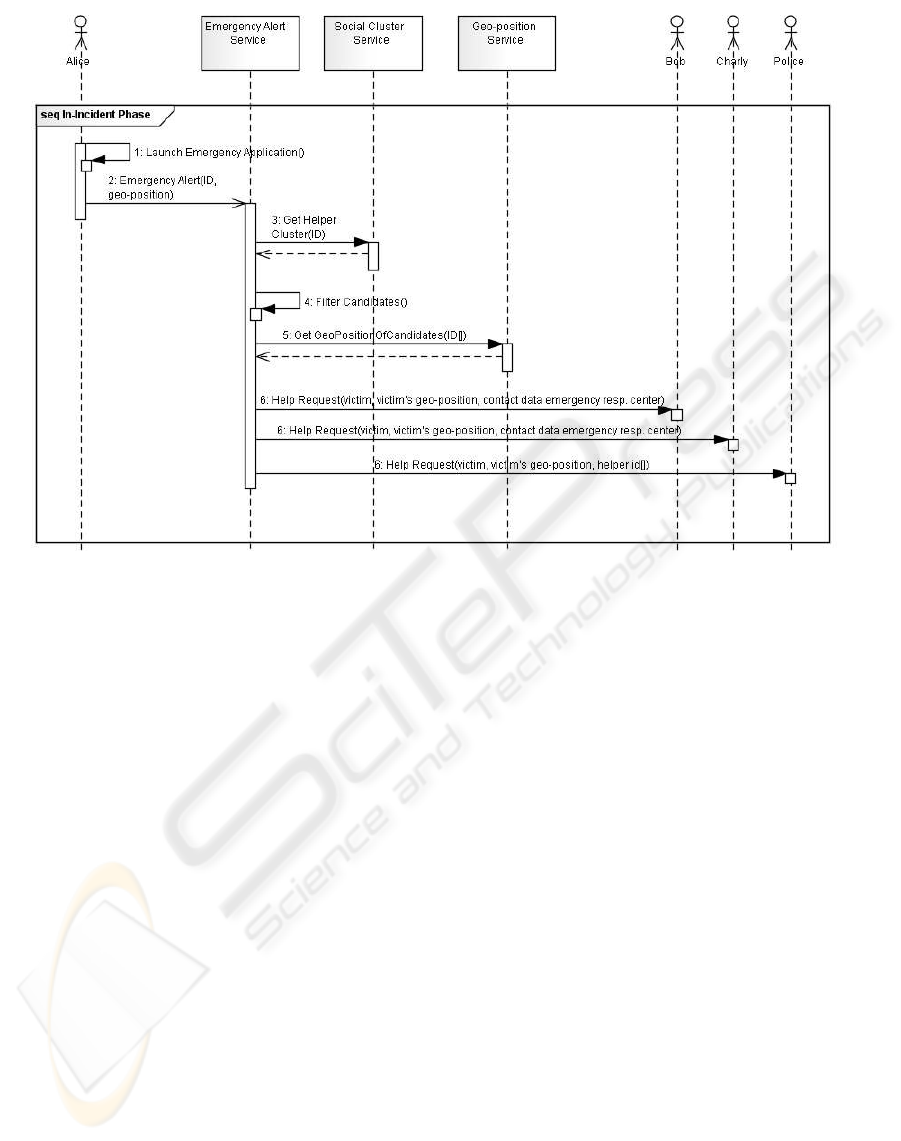
Figure 2: Sequence Diagram of a Generic Social Emergency Alert Service (in-incident).
dated regularly for all service subscribers. To find out
which persons in the social network are likely to help,
a clustering of the network is performed. Details for
this clustering are addressed in section 6.
Next, the current geo-position of the can-
didates is retrieved from a geo-position service
(
GetGeoPositionofCandidates
in figure 2). The
alert service uses the geo-data as a filter on the vic-
tim’s social cluster to find out, who of the possible
helpers is locally close enough. Section 7 deals with
details of having at least one member of the victim’s
social cluster in range.
The possible helpers in range and the emer-
gency response center are informed about the emer-
gency situation of the victim (several invocations of
HelpRequest
in figure 2). All possible helpers in
range are informed simultaneously. The victim’s
name, his geo-location and the shortest route as well
as the contact data for the emergency response center
are provided.
Finally, possible helpers and the emergency re-
sponse experts at the police’s emergency response
center may communicate, because of the information
forwarded by the emergency alert service (not shown
in figure 2). This facility has the potential of provid-
ing expert guidance to the socially close first respon-
ders on the scene. However, it also reveals the identity
of potential helpers to the emergency response center.
The privacy impact of this must be addressed for such
a service.
In section 2 obstacles to the five steps leading to
assistance have been described. The emergency alert
service presented addresses these obstacles directly:
1. The distraction obstacles can be avoided by notic-
ing, that an emergency incident takes place: Clear
signal words are part of the personal message to
the helpers. This makes it obvious, an emergency
case is happening and this is made clear to the
helper.
2. Self concerns are also addressed by the service:
Since the potential helper is directly addressed
and others know this from the incident protocol,
social norms lead to pressure to help.
3. Ambiguity is by-passed by the clear and unmistak-
able help request sent to the helpers.
4. As this message is personal, pluralistic ignorance
is eliminated. Experimental evidence for these
effects in internet chat rooms is provided by P.
Markey (Markey, 2000).
5. The relationship between attacker and victim can
not lead the helper to overlook the emergency
event, because of the unambiguous emergency
message.
6. Diffusion of responsibility is also reduced, since
the emergency alert message is directly and per-
ICE-B 2010 - International Conference on e-Business
210

sonally addressed to the helper. Because of this,
he is responsible and because of the incident pro-
tocol, others will know this and hold him respon-
sible.
7. Lack of competence may be addressed by provid-
ing fast expert backup for helpers from the police
emergency response center.
8. Expert guidance of how to help also addresses the
problems of audience inhibition and costs exceed
rewards.
4 IMPLEMENTATION VARIANTS
In this section we present implementation examples
how the Social Emergency Alert Service can be im-
plemented in an industrial environment.
4.1 Emergency Alerting
To be able to use the service, the user has to possess
a mobile device (e.g. a mobile phone). He can then
subscribe to the service. In case of an emergency, he
starts an application on his mobile device. Of course,
the start of the application must be made simple and
fast, as we do not expect it likely that the victim is able
to deal with complex applications in an emergency
situation. For the implementation third-party plat-
forms like Android can be used. Android (Android,
2010) is a mostly free and open-source OS platform
developed and driven by the Open Handset Alliance
(Open Handset Alliance, 2010). Further platforms
like Apples iPhone may be supported as well. Special
mobile devices combined with body-sensors, e.g. for
elderly people, linking the start of the application to a
hardwired button can be offered.
4.2 Geo-position Service
Geo-positions of both the victim and all possible
helpers of the victim’s social network need to be cal-
culated. Many of todays mobile phones are able to
calculate their geo-position by GPS (Global Position-
ing System). The service Google Latitude is an ex-
ample for a service that users can publish their cur-
rent geo-position and share it with friends. If a mo-
bile device does not include such a feature, several al-
ternative techniques have been described and imple-
mented. Even speed vectors can be calculated (for
example (Kikiras and Drakoulis, 2004; Borkowski
and Lempiainen, 2006)). By this, the expected geo-
position of somebody moving in a train can be found
out.
4.3 Building Social Networks and
Identifying Possible Helpers
For discovering the most likely person to help in an
emergency case the social network has to be known.
We present three possible realizations.
The social network can be built by monitoring
outgoing and incoming calls on the mobile device
of the subscriber. The emergency alert application
running on the mobile device collects this call data,
pools it and regularly (e.g. once a week) transmits it
via HTTP to the social cluster service (see figure 2).
There the call logs of all service subscribers are com-
bined and the network is calculated: Telephone num-
bers are represented as nodes, the calls are weighted
ties. Each call strengthens a tie. The advantage of
this solution is, that the network is independent from
the telephone provider. It works depending just on the
emergency alert application. The disadvantage is, that
the calculated social network consists only of sub-
scribers and their direct connections. Ties between
non-subscribers can not be observed technically.
Alternatively not the mobile devices monitor
the calls, but connection records from telephone
providers are used. Connection records are stored for
billing purposes. In the European Union an directive
forces the provider to save call logs from six month
up to two years (EU, 2006). These connection data
can be used to calculate the social networks. Every
connection is represented by a tie between the calling
parties (more concrete, their telephone numbers) as
nodes. Of course, the resulting network will be huge.
In section 7 we will show that feasible cluster algo-
rithms for such huge data sets exist. The advantage
of this solution is, that much more network data can
be collected so that the problem of missing links is
smaller. On the other hand this alternative can only be
realized if the calling logs are available to the emer-
gency alert provider. As we do not expect network
providers to give such information away, the most
likely approach for this alternative is, if the network
provider is identical with the emergency alert service
provider. The provider can then use the service as
an additional opt-in feature. Another disadvantage is,
that one network provider will probably not exchange
network or call log data with other providers. By this
the social network is limited to the customers of the
provider plus their direct links.
As an additional feature for both alternatives ad-
dress books in the customers’ devices can be used to
group telephone numbers. Different telephone num-
bers of one person can be combined and fused to one
node in the social network.
A third approach to build the social network is
GETTING HELP IN A CROWD - A Social Emergency Alert Service
211

to cooperate with existing social network platforms.
Data from Facebook, Xing, Myspace can be used.
The advantage of this solution is, that no subscriber or
network provider boundaries exist. The disadvantage
is, that people tend to accept more ’friends’ in social
platforms than they would accept offline. Addition-
ally most of these platforms do not weight their ties,
which makes it difficult to apply cluster algorithms.
In practice all three alternatives used to build a so-
cial network as discussed above can be complemented
with a list of emergency contacts provided by each
subscriber and, if available, with a list of dedicated
helpers for an event or for a community. In a Ger-
man small rural community, the community’s volun-
tary fire-fighters are an example of such a community.
We expect, that people in the same social group are
likely to help each other.
5 ARCHITECTURE OF THE
PROTOTYPE
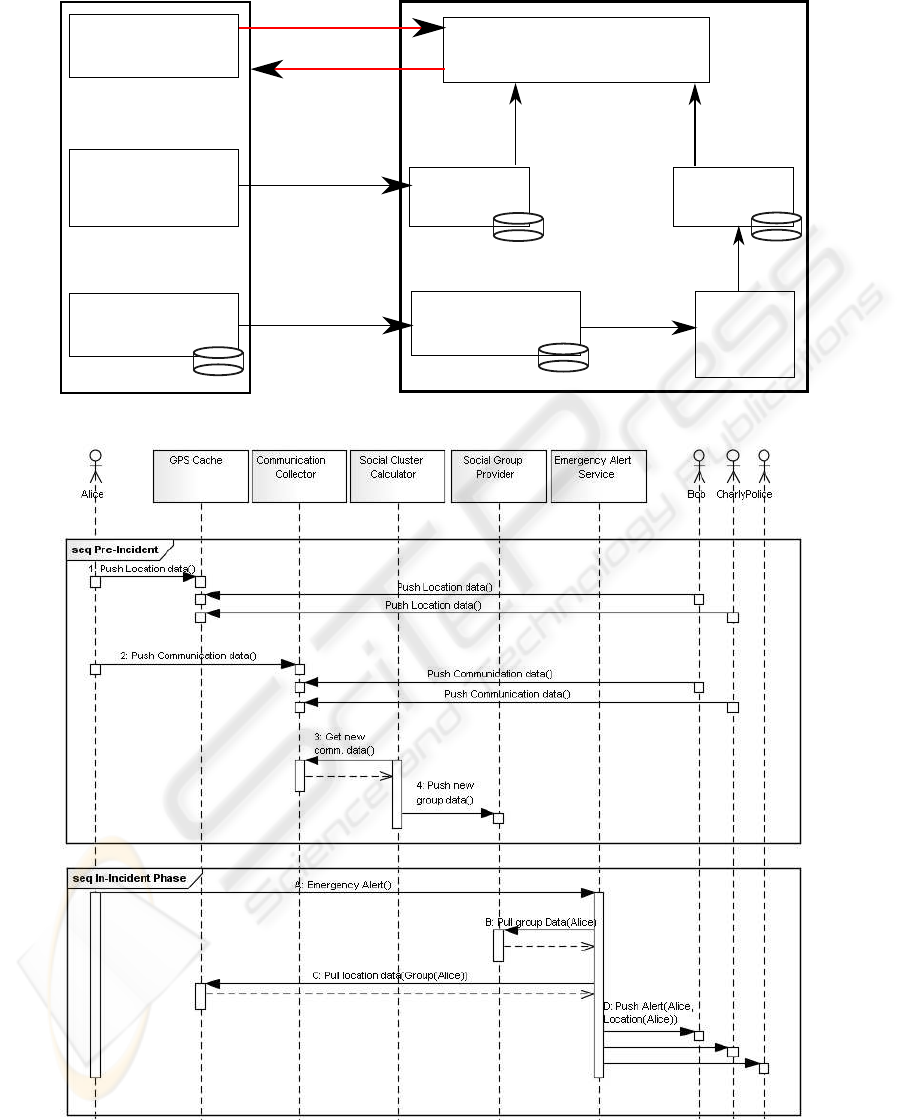
In figure 3 we present the architecture of a proto-
type of the service. The mobile application (Emer-
gency Alert Widget, GPS-Push Service, Communica-
tion Capture Service in figure 3) is implemented on
a Motorola Milestone smart phone using Android as
OS. The Service Provider is realized in Java using
Apache Service Mix as OSGi
1
provider.
Figure 4 depicts the sequence diagram of the pro-
totype. Each subscriber is identified by his unique
telephone number (ID). In the Pre-Incidence Phase
each subscriber submits his geo-location data to the
GPS Cache (step 1). We use a GPS Push Service
running as background service on the Android smart
phone to transmit the GPS coordinates via REST to
the GPS Cache. The transmission is done on a reg-
ular basis, e.g. every 10 minutes and if the position
changed by more than 10 meters. The GPS Cache
stores the latest transmitted geo-position of each sub-
scriber in a database. The Communication Capture
Service runs on the mobile device. It monitors all in-
going and outgoing calls and messages. This com-
munication data is collected in a local cache. Once a
day the smart phone submits the cached communica-
tion data via SOAP to the Communication Collector
(step 2). The Social Cluster Calculator pulls new data
from the Communication Collector on a daily basis. It
builds a communication network, clusters the groups
and stores the results in the Social Group Provider’s
1
The Open Services Gateway initiative is a module
system and service platform for Java. For details see
http://www.osgi.org
database (step 3 and 4). OSGi is used as the internal
Service Provider’s protocol.
In the In-Incident Phase the user in need (in our
example this is Alice) starts a widget on her smart
phone (see figure 5). A emergencyalert is transmitted
via REST to the Emergency Alert Service (step A).
The service pulls the helpers candidate list from the
Social Group Provider for Alice via OSGi (step B).
For each candidate the GPS Cache is searched for the
latest geo-position data of the candidate (step C). If
close enough, a MMS is sent out to the helper with
information about the victim and the victims geo-
position (depicted on a map).
Note, that Figure 4 is restricted to a proper emer-
gency alert. False alerts can be revoked by a similar
process (not shown in Figure 4) which is password
protected. However, pragmatically a set of passwords
is provided which act as silent signals. A small so-
lution consists of three passwords, the first signaling
a false alarm, the second signaling that the victim is
forced to revoke the alarm, and the third that there is
danger for the helpers.
6 IDENTIFYING SOCIAL
GROUPS BY CLUSTERING
SOCIAL NETWORKS
Calling persons willing to help is crucial for the pro-
posed system but their identification is not trivial.
Communication networks or ’friend’ networks of on-
line social network sites usually contain many links
that do not result from close personal relations. Links
may connect business partners or co-workers. On so-
cial network sites people ’friend’ others they rarely
know. Therefore, identifying social groups is an ap-
proach to separate close personal contacts from other
distant contacts that are less willing to help in a case
of emergency.
The appropriate cluster algorithms depend on the
network that needs to be analyzed. All algorithms
need to be highly efficient as the mentioned networks
are very huge (several million vertices). From com-
munication data weighted networks could be created
where an edge connects caller and the callee respec-
tively sender and receiver of a text message. The
edges can be weighted by the number of calls or mes-
sages. Walk context clustering is a suitable method
for this kind of network. It generates overlapping
clusters and can reflect that people might have several
groups of close contacts (family, friends, neighbors)
that are almost not connected with each other.
Cluster algorithms based on optimizing the mod-
ICE-B 2010 - International Conference on e-Business
212
Mobile Device
Emergency
Alert Widget
GPS Push
Service
Communication
Capture Service
GPS Cache
Communication
Collector
Social
Cluster
Calculator
Social Group
Provider
Emergency Alert Service
REST
Location data
<<every n minutes>>
SOAP
Communication data
<<daily>>
REST
Emergency Alert!
Emergency Alert,
Victim, Location
MMS
OSGi
Comm. data
<<daily>>
Social Groups
<<daily>>
OSGi
Location data
<<on request>>
Group data
<<on request>>
OSGi
OSGi
Service Provider
Cache
DB
DB
DB
Figure 3: Architecture of the Prototype.
Figure 4: Sequence Diagram of the Prototype.
ularity measure can not reflect the multitude of social
groups one person is integrated in. However, they are
able to deal with unweighted networks like the friend-
ship networks of social network sites.
GETTING HELP IN A CROWD - A Social Emergency Alert Service
213

Figure 5: Alert Widget on Phone.
6.1 Walk Context Clustering
Walk context clustering consists of two stages (see
algorithm 1). In the walk stage, a set of restricted
random walks is generated by starting a number of
walks at each vertex and repeatedly choosing the fol-
lowing vertices randomly among those vertices that
are linked by an edge which has a higher weight than
the previously taken one (see figure 6).
In the cluster construction stage, clusters get gen-
erated from the walks. Walk context clustering as-
signs a vertex to the cluster of another vertex if both
are part of the same walk. A level parameter l speci-
fies the fraction of vertices at the beginning of a walk
that are disregarded. The later a pair of vertices ap-
pears in a walk the stronger is their connection. The
interesting feature of walk-context clustering is that
the closeness of two persons can be measured by the
maximal level that assigns one person to the cluster of
the other one.
A recently developed database-backed update al-
gorithm for the walk stage maintains asymptotically
optimal clusters in near real-time (< 0.2 sec for a
single update on graphs with approximately 500000
nodes and 20 million edges) (Franke and Geyer-
Schulz, 2009).
Algorithm 1: Walk context clustering.
Data: undirected, weighted graph G = (V, E), con-
stant p
H Walk generation
walkSet ←
/
0 forall v ∈ V do
for counter ← 1 to p do
walk ← (i); last ← 0; i ← v while N =
{x|ω
ix
> last} 6=
/
0 do
j ← random element of N last ← ω
ij
ap-
pend j to walk w i ← j
walkSet ← walklist ∪walk
Data: walkSet ws, vertex v, level l
H Cluster Construction
cluster ←
/
0 forall w ∈ ws|v ∈ w∧ pos(v,w) > l do
forall x ∈ w|pos(x,w) > l do
cluster ← cluster ∪ x
Figure 6: Narrowing search space for successive vertices of
the restricted random walk algorithm. The walks terminates
when no neighbor is within the search space. Solid arrows
symbolize used transitions. Dashed arrows symbolize links
to possible successors that have not been chosen by the ran-
dom process.
6.2 Modularity Clustering
Newman and Girvan (Newman and Girvan, 2004)
proposed a quality function for graph clusterings. The
modularity Q of a clustering C = C
1
,...,C
z
(∀i, j :
C
i
∩C
j
=
/
0 and ∪
i
C
i
= V) of a graph G = (V,E) is
Q =
∑
i
(e
ii
− a
2
i
) (1)
with e
ij
=
{{v
a
,v
b
}∈E|v
a
∈C
i
∧v
b
∈C
j
}
2|E|
and a
i
=
∑
j
e
ij
.
The randomized greedy modularity clustering al-
gorithm (Ovelg¨onne and Geyer-Schulz, 2009) (see al-
gorithm 2) is a fast agglomerative hierarchical clus-
tering algorithm. It places each vertex in a separate
cluster and builds the complete dendrogram by re-
peatedly merging clusters. In each step it randomly
selects k clusters and searches among the clusters and
ICE-B 2010 - International Conference on e-Business
214

their neighbors for the pair that yields in the high-
est increase in modularity. The ∆Q of the merge of
two clusters i and j is ∆Q(i, j) = e
ij
+ e
ji
− 2a
i
a
j
=
2(e
ij
− a
i
a
j
). This algorithm is able to process even
very large networks in reasonable time. A graph with
about 300.000 vertices and 1 million edges is clus-
tered in roughly 10 seconds.
Algorithm 2: Randomized greedy modularity clustering.
Data: undirected, connected graph G = (V,E), constant k
H Initialize
forall v ∈ V do
forall neighbours n of v do
e[v, n] ← 1/(2∗edgecount)
a[v] ← rowsum(e[v])
H Build Dendrogram (Randomized Greedy)
for i = 1 to rank(e)-1 do
maxDeltaQ ← −∞ for j = 1 to k do search among
k communities for best join
c1 ← random community for all communi-
ties c2 connected to c1 do
deltaQ ← 2(e[c1,c2] − (a[c1] ∗a[c2])) if
deltaQ > maxDeltaQ then
maxDeltaQ ← deltaQ next join ←
(c1,c2)
join(nextjoin)
7 ASSESSMENT OF BENEFITS
7.1 Ability to Transmit Request for
Help
Emergency situations can result of various incidents,
e.g. crime, accidents, medical emergencies. By
their nature, accidents happen unexpected and sud-
den. Some medical emergencies as heart attacks do as
well. The ability to make an emergency call in these
cases will depend on the physical condition of the per-
son in need.
For victims of violent crime their ability to send an
emergency signal depends on the progress of crime.
In 25%, respectively 22%, of the robberies analyzed
by Smith (Smith, 2003) instant violence or attempts
to snatch property don’t give the opportunity to call
for help. However, in 37% of the robberies the of-
fender approached the victim and demanded money
or valuables without immediate violence. In many
cases later victims were also aware of an upcoming
threat. In those cases it would be possible to send an
emergency message.
7.2 Chance for Nearby Help
The helpfulness of the proposed system depends on
the availability of close social contacts in the proxim-
ity of the site of the emergency. The actual number of
persons in ones proximity in general and the number
of close contacts with a particular motivation to help
will surely depend on several factors, e.g. place and
time.
To gain insight into the availability of potential
help the MIT reality mining experiment (Eagle and
Pentland, 2005) provides an interesting data set. For
this experiment a group of 100 persons (75 students
or faculty of the MIT Media Laboratory and 25 stu-
dents of the MIT Sloan Business School) has been
equipped with smart phones with special software ap-
plications preinstalled. These applications recorded
phone numbers of incoming and outgoing calls, text
messages, and the id of the cellular tower the phones
were connected to during one academic year.
The phone call and text message data from the re-
ality mining data set can be used to construct a com-
munication network. Based on the assumption that
the communication intensity of two people reflects the
closeness of their relation, social groups can be iden-
tified by clustering this weighted network. The avail-
ability of nearby help from within the social group of
a person in need can be estimated by the number of
persons from the same social group whose phones are
connected to the same cellular tower as the person in
need.
For three consecutive months all communica-
tion prior to the specific month has been used to
build an undirected, weighted communication net-
work. The edge weights are the number of commu-
nication events (calls, text messages). This network
has been clustered by the walk context cluster algo-
rithm with the level parameter set to 0.8. The gener-
ated clusters had an average size of about 5.
The MIT reality mining data set contains a history
of time-stamped connection records of the participat-
ing persons. For each month 1000 connection records
have been randomly selected. Then, for each persons
in a connection record the number of persons of his
social cluster who have been connected to the same
cellular tower at the same time have been counted.
This simulation showed that on average more than
one close fellow student was available for help at any
time (see table 1). E.g. for September 2004 the prob-
ability of having at least one person from one’s social
group in the proximity was 78% - independent of time
of the day.
This is just a basic assessment for a particular
group of people that has several shortcomings. Due to
the lack of more detailed data it was not possible to as-
GETTING HELP IN A CROWD - A Social Emergency Alert Service
215

Table 1: Average number of other persons of same social group connected to same cellular tower for 1000 randomly selected
persons and points of time.
Day (6am-6pm) Evening (6pm-11pm) Night (11pm-6am)
Group Others Group Others Group Others
09/2004 1.16 3.74 1.17 2.73 0.95 1.51
10/2004 1.33 3.12 1.29 3.4 1.14 1.82
11/2004 2.2 3.18 1.53 2.16 1.76 1.03
sess if other social contacts than fellow students were
available for help. Proximity could just be estimated
by radio cells which have a radius of a few hundred
meters in urban areas and a radius up to about 35 km
in rural areas. But it is fair to regard the results as an
indication that people living in urban areas will usu-
ally have at least one of their social contacts in their
proximity.
7.3 Chance to Actually Receive Help
Once a request for help has been transmitted to a po-
tential helper in the proximity of the site of the emer-
gency the chance to actually receive help depends on
the willingness and the ability of the informed per-
sons to get to that place. The ability to get to a
specific site can be supported in various ways. For
example a map and route directions could be dis-
played together with the emergency message. The re-
search of Markey (Markey, 2000) showed that also in
computer-mediated communication settings help re-
quests that were directed to specific persons had a
high probability to receive fast response and the by-
stander effect was virtually eliminated.
8 CONCLUSIONS
In this paper a novel emergency alert service has been
introduced which addresses all obstacles to providing
help identified in the social emergency intervention
process discussed in section 2. The service is de-
signed to reduce psychological barriers that result in a
bystander effect and inhibit effective help for persons
in need. The analysis of emergency situations and
whereabouts of persons in relation to their respective
social group suggest that the described service can ac-
tually provide a benefit in practice. A first prototype
of this service is currently under development.
The main emphasis of this paper is on the reduc-
tion of the bystander effect. However, the following
challenges which are beyond the scope of this paper
are examples of what must be addressed thoroughly
for concrete industrial service offerings:
1. Legal issues: The service raises e.g. the problem
that potential helpers become liable to help and
failure to do so may be prosecuted.
2. Privacy: The service should be designed in order
to minimize the intrusion of privacy of service-
subscribers.
3. Emergency dialog: The emergency dialog could
be further automated e.g. by providing an auto-
matic classification of the incident type.
4. Geo-positioning problems: Geo-positioning is
still problematic in large buildings, tunnels, sub-
terranean areas (e.g. subway). Enhancements
could be based e.g. by embedding geo-position
senders in such structures or by image recogni-
tion techniques which exploit public geo-coded
images of such spaces.
ACKNOWLEDGEMENTS
The research leading to these results has received
funding from the European Community’s 7th Frame-
work Program FP7/2007-2013 under grant agreement
n
◦
215453 – WeKnowIt.
REFERENCES
Android (2010). Android. http://www.android.com/.
Batson, C. D., Cochran, P. J., Biederman, M. F., Blosser,
J. L., Ryan, M. J., and Vogt, B. (1978). Failure to help
when in a hurry: Callousness or conflict? Personality
and Social Psychology Bulletin, 4:97 – 101.
Baumeister, R. F., Chesner, S. P., Sanders, P. S., and Tice,
D. M. (1995). Who’s in charge here? group leaders
do lend help in emergencies. Personality and Social
Psychology Bulletin, 14:17 – 22.
Borkowski, J. and Lempiainen, J. (2006). Practical
network-based techniques for mobile positioning in
UMTS. EURASIP J. Appl. Signal Process., 2006:149–
149.
Chen, R., Sharman, R., Rao, H. R., and Upadhyaya, S. J.
(2008). Coordination in emergency response manage-
ment. Communications of the ACM, 51(5):66 – 73.
Clark, R. and Word, L. E. (1972). Why don’t bystanders
help? because of ambiguity? Journal of Personality
and Social Psychology, 24:392 – 400.
ICE-B 2010 - International Conference on e-Business
216

Comfort, L. K., Kilkon, K., and Zagorecki, A. (2009). Co-
ordination in rapidly evolving disaster response sys-
tems: The role of information. American Behavioral
Scientist, 48(3):295 – 313.
Cramer, R. E., McMaster, M. R., Bartell, P., and Dragna, M.
(1988). Subject competence and the minimization of
the bystander effect. Journal of Applied Social Psy-
chology, 18:1133 – 1148.
Darley, J. M. and Batson, C. (1973). ”From Jerusalem to
Jericho”: A study of situational and dispositional vari-
ables in helping behavior. Journal of Personality and
Social Psychology, 27(1):100 – 108.
Darley, J. M. and Latan´e, B. (1968). Bystander intervention
in emergencies: Diffusion of responsibility. Journal
of Personality and Social Psychology, 8(4):377 – 383.
Eagle, N. and Pentland, A. (2005). Reality mining: Sens-
ing complex social systems. Personal and Ubiquitous
Computing, 9:1 – 14.
EU (2006). Directive 2006/24/EC of the European Parlia-
ment and of the Council on the retention of data gener-
ated or processed in connection with the provision of
publicly available electronic communications services
or of public communications networks and amending
Directive 2002/58/EC.
Faraj, S. and Xiao, Y. (2006). Coordination in fast-response
organizations. Management Science, 52(8):1155 –
1169.
Franke, M. and Geyer-Schulz, A. (2009). An update al-
gorithm for restricted random walk clustering for dy-
namic data sets. Advances in Data Analysis and Clas-
sification, 3(1):63 – 92.
Garcia, S. M., Weaver, K., Moskowitz, G. B., and Darley,
J. M. (2002). Crowded minds: The implicit bystander
effect. Journal of Personality and Social Psychology,
83:843 – 853.
Granovetter, M. (1982). The strength of weak ties: a net-
work theory revisited. chapter 5, pages 105 – 130.
Sage Publications, Inc., Beverly Hills, California.
Granovetter, M. S. (1973). The strength of weak ties. The
American Journal of Sociology, 78(6):1360 – 1380.
Hoser, B. and Geyer-Schulz, A. (2005). Eigenspectral anal-
ysis of hermitian adjacency matrices for the analysis
of group substructures. The Journal of Mathematical
Sociology, 29(4):265 – 294.
Kikiras, P. and Drakoulis, D. (2004). An integrated
approach for the estimation of mobile subscriber
geolocation. Wireless Personal Communications,
30(2):217–231.
Latan´e, B. and Darley, J. (1970). The Unresponsive By-
stander: Why doesn’t he help? Appleton-Century-
Crofts, New York.
Levine, M., Prosser, A., Evans, D., and Reicher, S. (2005).
Identity and emergency intervention: How social
group membership and inclusiveness of group bound-
aries shape helping behavior. Personality and Social
Psychology Bulletin, 31(4):443 – 453.
Markey, P. M. (2000). Bystander intervention in computer-
mediated communication. Computers in Human Be-
havior, 16:183 – 188.
Milgram, S. (1970). The experience of living in cities. Sci-
ence, 167:1461 – 1468.
Miller, D. T. and McFarland, C. (1987). Pluralistic igno-
rance: When similarity is interpreted as dissimiliarity.
Journal of Personality and Social Psychology, 53:298
– 305.
Monin, B. and Norton, M. (2003). Perceptions of a fluid
consensus: Uniqueness bias, false consensus, false
polarization, and pluralistic ignorance in a water con-
servation crisis. Personality and Social Psychology
Bulletin, 29:559 – 567.
Moriarty, T. (1975). Crime, commitment, and the respon-
sive bystander: Two field experiments. Journal of Per-
sonality and Social Psychology, 31:370 – 376.
Nadler, A. and Halabi, S. (2006). Intergroup helping as sta-
tus relations: Effects of status stability, identification,
and type of help on receptivity to high-status group’s
help. Journal of Personality and Social Psychology,
91(1):97 – 110.
Newman, M. E. J. and Girvan, M. (2004). Finding and eval-
uating community structure in networks. Physical Re-
view E, 69(2):026113.
Open Handset Alliance (2010). Open handset alliance.
http://www.openhandsetalliance.com/.
Ovelg¨onne, M. and Geyer-Schulz, A. (2009). Randomized
greedy modularity clustering. Technical report, Karl-
sruhe.
Palen, L. and Liu, S. B. (2007). Citizen communication
in crisis: Anticipating a future of ict-supported public
participation. In CHI 2007 Proceedings, pages 727 –
736. ACM.
Piliavin, I. M., Piliavin, J. A., and Rodin, J. (1975). Costs,
diffusion, and the stigmatized victim. Journal of Per-
sonality and Social Psychology, 32(3):429 – 438.
Rungg, A. (2010). Privatsp¨are 2.0. Technical report, Finan-
cial Times Deutschland, 17.2.2010, p.25.
Rutkowski, G. K., Gruder, C. L., and Romer, D. (1983).
Group cohesiveness, social norms, and bystander in-
tervention. Journal of Personality and Social Psychol-
ogy, 44:545 – 552.
Schwartz, S. H. and Gottlieb, A. (1980). Bystander
anonymity and reaction to emergencies. Journal of
Personality and Social Psychology, 39:418 – 430.
Shotland, R. L. and Heinold, W. D. (1985). Bystander
response to arterial bleeding: Helping skills, the
decision-making process, and differentiating the help-
ing response. Journal of Personality and Social Psy-
chology, 49:347 – 356.
Shotland, R. L. and Stebbins, C. A. (1980). Bystander re-
sponse to rape: Can a victim attract help? Journal of
Applied Social Psychology, 10:510 – 527.
Shotland, R. L. and Straw, M. K. (1976). Bystander re-
sponse to an assault: When a man attacks a woman.
Journal of Personality and Social Psychology, 34:990
– 999.
Smith, J. (2003). The nature of personal robbery. Home
Office Research Study 254, Home Office Research,
Development and Statictics Directorate.
GETTING HELP IN A CROWD - A Social Emergency Alert Service
217

Spiegel Online (2009a). Notruf-Mitschnitt belegt Bru-
talit¨at der S-Bahn-Pr¨ugler. Technical report, Spiegel
Online.
Spiegel Online (2009b). S-Bahn-Fahrgast stirbt nach bru-
taler Attacke. Technical report, Spiegel Online.
Spiegel Online (2009c). T¨odlicher Angriff: Mehrere Men-
schen beobachteten M¨unchner S-Bahn-Attacke. Tech-
nical report, Spiegel Online.
St¨urmer, S., Snyder, M., and Omoto, A. M. (2005). Proso-
cial emotions and helping: The moderating role of
group membership. Journal of Personality and Social
Psychology, 88(3):532 – 546.
Yuan, Y. and Detlor, B. (2005). Intelligent mobile cri-
sis response systems. Communications of the ACM,
48(2):95 – 98.
ICE-B 2010 - International Conference on e-Business
218
