
SERVER-ASSISTED LONG-TERM SECURE
3-PARTY KEY ESTABLISHMENT
Kashi Neupane and Rainer Steinwandt
Department of Mathematical Sciences, Florida Atlantic University, Boca Raton, FL, U.S.A.
Keywords:
Server-assisted key establishment, Longterm security.
Abstract:
Consider a scenario where a server S shares a symmetric key k
U
with each user U. Building on a 2-party
solution of Bohli et al., we describe an authenticated 3-party key establishment which remains secure if a
computational Bilinear Diffie Hellman problem is hard or the server is uncorrupted. If the BDH assumption
holds during a protocol execution, but is invalidated later, entity authentication and integrity of the protocol
are still guaranteed.
1 INTRODUCTION
In the design of key establishment protocols it is com-
mon practice to make use of asymmetric building
blocks. A question naturally arising here, especially
when aiming at longterm guarantees, is the effect of a
violation of an underlying hardness assumption—for
instance a discrete logarithm computation might be-
come feasible a few years after a key establishment
protocol has been executed. In a server-assisted set-
ting, trying to integrate symmetric techniques as a
fall-back technique appears to be a natural approach,
and (Bohli et al., 2007a) propose a 3-round protocol
for two-party key establishment addressing this sce-
nario: their proposal builds on a symmetric encryp-
tion scheme which is secure in a sense reminiscent of
left-or-right indistinguishability. Given such a prim-
itive, Bohli et al.’s construction ensures semantic se-
curity of the session key if the server is uncorrupted
or a Decision Diffie Hellman assumption holds.
Our contribution. The 3-party protocol in the ran-
dom oracle model presented below enables the estab-
lishment of a common session key among 3 parties
within 3 rounds. The protocol builds on the Bilin-
ear Diffie Hellman (BDH) assumption and a symmet-
ric encryption scheme which is secure in the sense
of real-or-random indistinguishability. Provided that
at least one of these two hardness assumptions holds,
semantic security of the session key is ensured. In
case the BDH assumption is broken after completion
of the protocol, entity authentication and integrity are
still preserved. We did not make an attempt to avoid
the random oracle model, but tried to avoid the intro-
duction of new hardness assumptions respectively re-
quirements on the underlying symmetric encryption
scheme.
2 PRELIMINARIES
On the mathematical side, the main technical tool
is a bilinear pairing. Following the formalization of
(Boneh and Franklin, 2003), in the next section we
quickly review the relevant terminology—for more
details we refer to (Boneh and Franklin, 2003). Simi-
larly, in Section 2.2, we review the main idea of real-
or-random indistinguishability as discussed in (Bel-
lare et al., 2000a), and we refer to the latter for a more
detailed discussion.
2.1 Bilinear Maps and the Bilinear
Diffie Hellman Assumption
Let G
1
and G
2
be two groups of prime order q, such
that q > 2
ℓ
with the security parameter being ℓ. We
use additive notation for G
1
, multiplicative notation
for G
2
, and denote by ˆe : G
1
−→ G
2
an admissible bi-
linear map, i.e., ˆe has all of the following properties:
Bilinear. For all P,Q ∈ G
1
and all a,b ∈ Z we have
ˆe(aP,bQ) = ˆe(P,Q)
ab
.
Non-degenerate. For P 6
= O , we have ˆe(P,P) 6= 1,
i. e., ˆe(P,P) is a generator of G
2
.
Efficiently Computable. There is a polynomial time
algorithm which for all Q,R ∈ G
1
computes
ˆe(Q,R).
372
Neupane K. and Steinwandt R. (2010).
SERVER-ASSISTED LONG-TERM SECURE 3-PARTY KEY ESTABLISHMENT.
In Proceedings of the International Conference on Security and Cryptography, pages 372-378
DOI: 10.5220/0002983503720378
Copyright
c
SciTePress

To specify the Bilinear Diffie-Hellman (BDH) prob-
lem, we use a probabilistic polynomial time (ppt) al-
gorithm G : on input the security parameter 1
ℓ
, this
BDH parameter generator G outputs q and a descrip-
tion of G
1
, G
2
, and ˆe as above; in slight abuse of no-
tation we write hq, G
1
,G
2
, ˆei ← G (1
ℓ
). Descriptions
output by G are assumed to specify polynomial time
algorithms for efficiently computing in G
1
, G
2
and for
evaluating the bilinear map ˆe.
Next, for a ppt algorithm A we consider the fol-
lowing experiment:
1. The BDH parameter generator is run, yielding
BDH parameters
hq,G
1
,G
2
, ˆei.
2. Values a, b,c ← {0,...,q − 1} are chosen uni-
formly at random, and A obtains the output of G
along with aP, bP and cP as input.
3. Now A outputs a value g ∈ G
2
, and is successful
whenever g = ˆe(P,P)
abc
.
To measure the advantage of A in solving the BDH
problem we use the function Adv
bdh
A
= Adv
bdh
G ,A
(ℓ) :=
Pr
h
A (q, G
1
,G
2
, ˆe,P, aP,bP,cP) = ˆe(P,P)
abc
hq,G
1
,G
2
, ˆei ← G (1
ℓ
),
P ← G
1
\ {O },
a,b,c ← {0, . . . ,q− 1}
Definition 1 (BDH Assumption). A BDH instance
generator G satisfies the BDH assumption if for all
ppt algorithms A , the advantage Adv
bdh
A
is negligible
(in ℓ). In this case, we say that BDH is hard in groups
generated by G .
2.2 Real-or-random Indistinguishability
Our presentation of real-or-random indistinguishabil-
ity follows the one in (Bellare et al., 2000a), and we
refer to the latter paper for a more detailed discussion.
By a symmetric encryption scheme, we mean a collec-
tion S E = (Gen,Enc,Dec) of three polynomial time
algorithms:
Gen: a probabilistic algorithm that on input the secu-
rity parameter 1
ℓ
outputs a secret key k ∈ {0,1}
∗
;
Enc: a probabilistic algorithm that on input a secret
key k and a plaintext m ∈ {0,1}
∗
outputs a ci-
phetext c ∈ {0,1}
∗
;
Dec: a deterministic algorithm that on input a se-
cret key k and a ciphertext c outputs the corre-
sponding plaintext m or an error symbol ⊥. For a
valid secret key k output by Gen, we impose that
Dec
k
(Enc
k
(m)) = m for all plaintexts m ∈ {0, 1}
∗
.
To formalize the security notion needed later, we use
a real-or-random oracle E
k
(R R (·,b)) that on input
b ∈ {0,1} and a plaintext m ∈ {0,1}
∗
returns an en-
cryption c ← Enc
k
(m) of m, if b = 1. For b = 0,
an encryption c ← Enc
k
(r) of a uniformly at random
chosen bitstring r ← {0,1}
|m|
is returned, where |m|
denotes the length of m.
For a ppt algorithm A now consider the following
experiment where b ∈ {0,1} is fixed and unknown to
A : a secret key k ← Gen(1
ℓ
) is created, and A has
unrestricted access to E
k
(R R (·, b)). Further, A has
access to a decryption oracle D
k
(·) which executes
Dec
k
(·), subject to the restriction that no messages
must be queried to D
k
(·) that have been output by the
real-or-random oracle. We measure A ’s advantage as
the difference Adv
ror−cca
A
= Adv
ror−cca
A
(ℓ) :=
Pr
h
1 ← A
E
k
(R R (·,1)),D
k
(·)
(1
ℓ
)
k ← Gen(1
ℓ
)
i
−Pr
h
1 ← A
E
k
(R R (·,0)),D
k
(·)
(1
ℓ
)
k ← Gen(1
ℓ
)
i
Definition 2 (Real-or-random Indistinguishabil-
ity). A symmetric encryption scheme S E is secure
in the sense of real-or-random indistinguishability
(ROR-CCA), if for all ppt algorithms A , the advan-
tage Adv
ror−cca
A
is negligible (in ℓ).
3 SECURITY MODEL
To analyze the security of the proposed protocol, we
use a model based on the frameworkin (Bresson et al.,
2001), which in turn is derived from (Bellare et al.,
2000b). The latter paper by Bellare et al. also gives
more details on the variables that are used below to
describe protocol instances.
Protocol Participants. We denote by U
0
= S a ded-
icated server and by U = {U
1
,.....,U
n
} a polynomial
size set of users.
1
Both server and users are modeled
as ppt algorithms, and eachU ∈ U ∪{S} can execute a
polynomial number of protocol instances Π
s
U
concur-
rently (s ∈ N). To describe a protocol instance Π
s
U
,
seven variables are associated with it:
acc
s
U
: indicates if the session key stored in sk
s
U
has
been accepted;
pid
s
U
: stores the identities of those users in U with
which a key is to be established (including U);
sid
s
U
: stores a session identifier that can serve as pub-
lic identifier for the session key stored in sk
s
U
;
1
We assume user identities to be encoded as bitstrings
of identical length.
SERVER-ASSISTED LONG-TERM SECURE 3-PARTY KEY ESTABLISHMENT
373

sk
s
U
: stores the session key and is initialized with a
distinguished NULL value;
state
s
U
: stores state information;
term
s
U
: indicates if this protocol execution has termi-
nated;
used
s
U
: indicates if this instance is used, i.e., in-
volved in a protocol run.
Initialization. Before the actual protocol execu-
tions, an initialization phase without adversarial inter-
ference takes place. In this phase, for each userU ∈ U
a verification key/signing key pair (pk
U
,sk
sig
U
) for an
existentially unforgeable (UF-CMA secure) signature
scheme is generated, sk
sig
U
is handed to U, and each
userU obtains the public keys pk
U
′
for allU
′
∈ U . We
denote the signing resp. verification algorithm with
Sig resp. Ver. In addition, for each user U ∈ U , a se-
cret key k
U
← Gen(1
ℓ
) for the underlying symmetric
encryption scheme (Gen,Enc,Dec) is generated; this
key is given toU and the server S. Thus, after this ini-
tialization phase, the server shares a symmetric key
k
U
with each user U ∈ U .
Communication Network and Adversarial Capa-
bilities. The network is non-private, fully asyn-
chronous, and allows arbitrary point-to-point connec-
tions among the users and between users and the
server. The adversary A is modeled as ppt algorithm
with complete control over the communication net-
work. The following three oracles materialize the ad-
versary’s capabilities:
Send(U
i
,s
i
,M) : sends the message M to instance
Π
s
i
U
i
of user U
i
and returns the protocol message
output by that instance after receiving M. In ad-
dition, the Send oracle is used to initialize a pro-
tocol run: to initialize a protocol run of U
i
with
U
j
,U
k
∈ U and server S, the special message M =
{U
i
,U
j
,U
k
} is sent to an unused instance
∏
s
i
U
i
. Af-
ter such a query,
∏
s
i
U
i
initializes its pid
s
i
U
i
-value to
{U
i
,U
j
,U
k
}, sets used
s
i
U
i
:= TRUE and processes
the first step of the protocol.
Reveal(U,s) : returns the session key sk
s
U
if acc
s
U
=
TRUE and a NULL value otherwise.
Corrupt(U) : for a userU ∈ U this query returnsU’s
long term signing key sk
sig
U
as well as the symmet-
ric key k
U
shared between U and the server S; for
U = S, the list of all symmetric keys k
U
(U ∈ U )
is returned, along with the information to which
user each such key belongs.
In addition, A has access to a Test oracle, which can
be queried only once: the query Test(U,s) can be
made with an instance Π
s
U
that has accepted a ses-
sion key. Then a bit b ← {0, 1} is chosen uniformly
at random; for b = 0, the session key stored in sk
s
U
is
returned, and for b = 1 a uniformly at random chosen
element from the space of session keys is returned.
To exclude useless protocols, subsequently we
consider only correct key establishment protocols,
i. e., in the absence of active attacks a common ses-
sion key is established, along with common session
identifier and matching partner identifier. To define
what we mean by a secure key establishment proto-
col, we rely on the following notion of partnering.
Definition 3 (Partnering). Two instances
∏
s
i
U
i
and
∏
s
j
U
j
are partnered if sid
s
i
U
i
= sid
s
j
U
j
, pid
s
i
U
i
= pid
s
j
U
j
and
acc
s
i
U
i
= acc
s
j
U
j
= TRUE.
Making use of this definition, we can specify what we
mean by a fresh instance, i. e., an instance the Test or-
acle can be queried with:
Definition 4 (Freshness). An instance
∏
s
i
U
i
is
said to be fresh if the adversdary neither queried
Corrupt(U
j
) for some U
j
∈ pid
s
i
U
i
, nor Reveal(U
j
,s
j
)
for an instance
∏
s
j
U
j
that is partnered with
∏
s
i
U
i
.
We write Succ
A
for the event that the adversary
A queries Test with a fresh instance and correctly
guesses the random bit b used by the Test oracle and
refer to
Adv
ke
A
= Adv
ke
A
(ℓ) :=
Pr[Succ] −
1
2
as advantage of A .
Definition 5 (Semantic Security). A key establish-
ment protocol is said to be (semantically) secure, if
Adv
ke
A
= Adv
ke
A
(ℓ) is negligible for all ppt algorithms
A .
Finally, in formalizing entity authentication and in-
tegrity, we follow the definitions in (Bohli et al.,
2007b).
Definition 6 (Strong Entity Authentication). We say
that strong entity authentication to an instance Π
s
i
U
i
is provided if acc
s
i
U
i
=TRUE and for all uncorrupted
U
j
∈ pid
s
i
U
i
there exists with overwhelming probability
an instance Π
s
j
U
j
with sid
s
j
U
j
= sid
s
i
U
i
and U
i
∈ pid
s
j
U
j
.
Definition 7 (Integrity). A key establishment pro-
tocol fulfills integrity if with overwhelming probabil-
ity for all instances
∏
s
i
U
i
,
∏
s
j
U
j
of uncorrupted princi-
pals the following holds: if acc
s
i
U
i
= acc
s
i
U
j
=TRUE and
sid
s
i
U
i
= sid
s
j
U
j
, then sk
s
i
U
i
= sk
s
j
U
j
and pid
s
i
U
i
= pid
s
j
U
j
.
SECRYPT 2010 - International Conference on Security and Cryptography
374
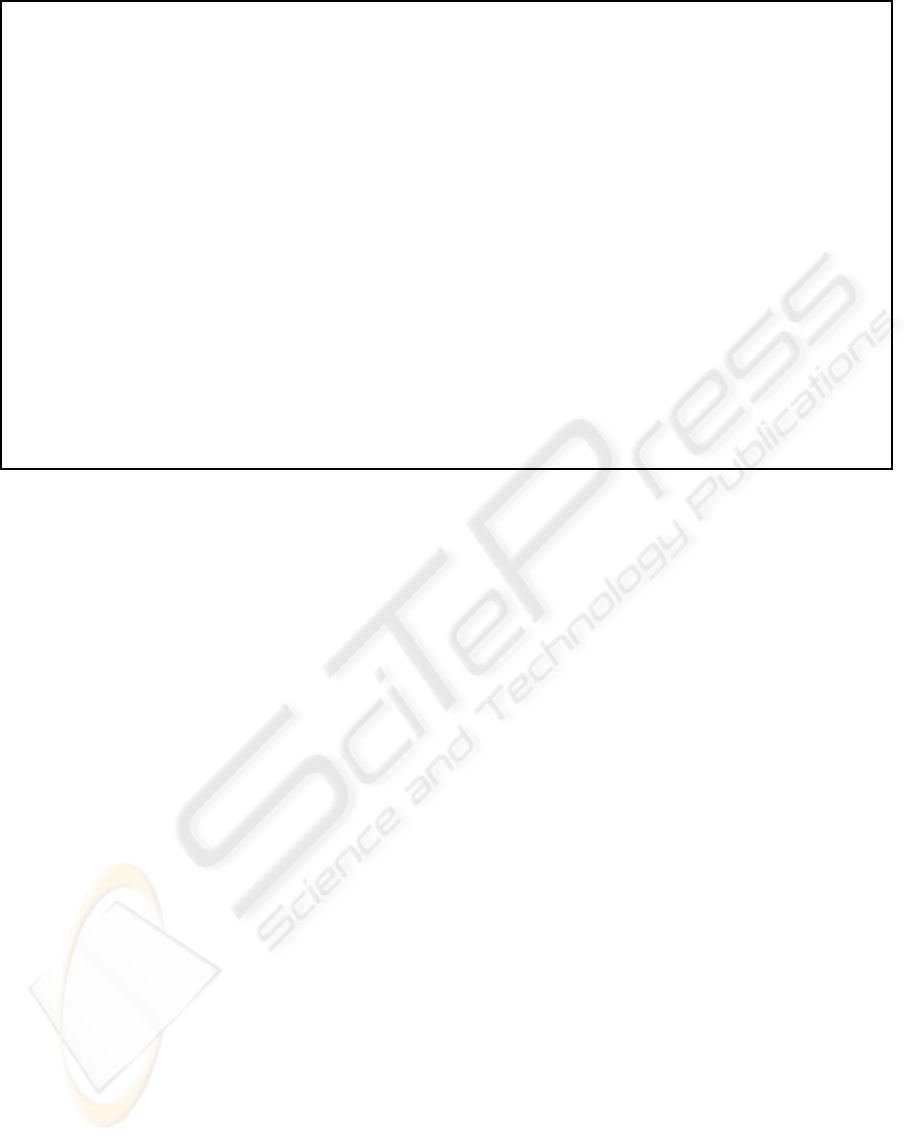
Round 1:
Computation: Each U
i
selects u
i
← {0,. . . , q − 1} uniformly at random, and computes u
i
P.
Broadcast: Each U
i
broadcasts (U
1
,U
2
,U
3
,u
i
P)
Round 2:
Computation: The server S selects k
srv
← {0,1}
ℓ
uniformly at random and for i = 1, 2,3 computes
c
i
:= Enc
k
U
i
(U
1
,U
2
,U
3
,u
i
P,k
srv
). Each U
i
computes k
usr
= H( ˆe(P,P)
u
1
u
2
u
3
)(= H( ˆe(u
2
P,u
3
P)
u
1
) =
H( ˆe(u
1
P,u
3
P)
u
2
) = H( ˆe(u
1
P,u
2
P)
u
3
)).
Broadcast: The server broadcasts (U
1
,U
2
,U
3
,c
1
,c
2
,c
3
).
Check: Each U
i
decrypts c
i
and checks consistency of the plaintext with the values sent in Round 1.
Round 3:
Computation: Each U
i
computes mk
i
:= k
srv
k k
usr
k U
1
k U
2
k U
3
, sets k
conf
i
:= H(mk
i
k 00), and σ
i
:=
Sig
sk
sig
(U
1
,U
2
,U
3
,u
1
P,u
2
P,u
3
P,k
conf
i
).
Broadcast: Each U
i
broadcasts (U
1
,U
2
,U
3
,σ
i
)
Check: Each U
i
verifies the signatures σ
j
( j 6= i), using the values from Round 1, the value k
conf
i
just
computed, and the public verification keys pk
U
j
.
Key derivation: If none of the checks failed, U
i
sets sid
U
i
:= H(mk
i
k 01), sk
U
i
:= H(mk
i
k 10), and then
acc
U
i
:=TRUE.
Figure 1: Long-term secure 3-party key establishment among users U
1
,U
2
,U
3
, invoking a server S.
4 THE PROPOSED 3-PARTY
PROTOCOL
The proposed protocol has three rounds with a total
of seven messages being sent, and makes use of a ran-
dom oracle H : {0,1}
∗
→ {0,1}
ℓ
. To describe the pro-
tocol we use the notation from Section 2 with P being
a generator of the additive group G
1
of prime order q,
as used in the BDH assumption. By Enc we denote
the encryption algorithm of a symmetric encryption
scheme that is secure in the sense of ROR-CCA, and
by S resp. V we denote the signature resp. verfi-
cation algorithm of an existentially unforgeable sig-
nature scheme. With this notation, the proposed pro-
tocol for establishing a common session key among
users U
1
, U
2
, U
3
, invoking a server S, is described in
Figure 1 (for ease of notation, we omit indices refer-
ring to a particular user instance and write only sid
U
instead of sid
s
U
etc.).
5 SECURITY ANALYSIS
The security of the protocol in Figure 1 can be en-
sured in the “long-term” provided that the underlying
signature scheme is existentially unforgeable and the
invoked symmetric encryption scheme is secure in the
sense of ROR-CCA. More specifically, we have the
following.
Proposition 1. Suppose the signature scheme used
in the protocol in Figure 1 is secure in the sense of
UF-CMA and the symmetric encryption scheme is se-
cure in the sense of ROR-CCA. Then the protocol in
Figure 1 is secure, if the invoked signature scheme is
existentially unforgeable and at least one of the fol-
lowing conditions holds:
• The server S is uncorrupted.
• The BDH assumption for the underlying BDH in-
stance generator holds.
If the above two assumptions hold during the protocol
execution (only), then the protocol in Figure 1 still
guarantees integrity and strong entity authentication.
Proof. Let q
send
and q
ro
be polynomial upper bounds
for the number of the adversary A ’s queries to the
Send oracle and random oracle H, respectively. We
begin by defining three events and argue that each of
them can occur with negligible probability only:
Forge: this is the event that A succeeds in forg-
ing a signature σ
i
of a protocol participant U
i
on a Round 3 message without having queried
Corrupt(U
i
). Let Adv
uf
= Adv
uf
(ℓ) be a negli-
gible upper bound for the probability that a ppt
adversary creates a successful forgery for the un-
derlying signature scheme. During the protocol’s
initialization phase, we can assign a challenge ver-
ification key to a user U ∈ U uniformly at ran-
dom, and with probability at least 1/|U | = 1/n
SERVER-ASSISTED LONG-TERM SECURE 3-PARTY KEY ESTABLISHMENT
375

the event Forge results in a successful forgery for
the challenge verification key. Thus
Pr[Forge] ≤ n · Adv
uf
,
i.e., Forge can occur with negligible probability
only.
Repeat: this is the event where the server S uses the
same value k
srv
more than once, or a user outputs
a value u
i
P with u
i
P = u
j
P for a value u
j
P that has
already been output by some (possibly the same)
user earlier. Both k
srv
and u
i
P are only chosen in
response to a Send query, and only one such value
is created per Send query. Consequently, we have
Pr[Repeat] ≤
q
send
∑
i=1
i− 1
2
ℓ
≤ q
2
send
/2
ℓ
,
i.e., Repeat can occur with negligible probability
only.
Collision: this is the event of a collision in the ran-
dom oracle H, i.e., H produces the same output
value for two different input values. As a Send
query causes at most two random oracle queries,
we can bound the total number of queries to H by
2· q
send
+ q
ro
. Therefore
Pr[Collision] ≤ (2· q
send
+ q
ro
)
2
/2
ℓ
is negligible.
As each of the events Forge, Repeat, Collision oc-
curs with negligible probability only, subsequently we
may assume they do not occur. Now, for proving se-
curity in the sense of Definition 3, game hopping turns
out to be convenient. The event of A to succeed in
Game i and the advantage of A in Game i will be de-
noted by Succ
Game i
A
and Adv
Game i
A
, respectively. First
we discuss the situation where the BDH assumption
holds; the case of having (only) an uncorrupted server
will be discussed thereafter.
Security if the BDH Assumption Holds. A short
sequence of games can be used to establish the desired
result in this case:
Game 0. This game is identical to the original attack
game for the adversary, with all oracles being sim-
ulated faithfully. In particular,
Adv
A
= Adv
Game 0
A
.
Game 1. Here we modify the simulation as fol-
lows: In Round 3, if none of the users in pid
i
is corrupted, k
usr
is chosen uniformly at ran-
dom from {0,1}
ℓ
, instead of being computed as
H( ˆe(P,P)
u
1
u
2
u
3
).
We claim that |Adv
Game 1
A
− Adv
Game 0
A
| is neg-
ligible. To see this, consider the following
algorithm B to solve the BDH problem: On
input a BDH challenge with group elements
(P,aP,bP, cP) ∈ G
4
1
, B will act as challenger for
the adversary A and choose three protocol in-
stances
∏
s
i
U
i
,
∏
s
j
U
j
,
∏
s
k
U
k
by guessing uniformly at
random among all ≤ q
send
instances queried to the
Send oracle.
With probability at least 1/q
3
send
, the adversary
A queries Test(U
i
,s
i
) with pid
s
i
U
i
= {U
i
,U
j
,U
k
}—
in all other cases B aborts. In Round 1, B re-
places the messages of U
i
,U
j
,U
k
with aP, bP and
cP accordingly, and as the Test session must not
be revealed, this is unnoticeable to A . Game 1
differs only from Game 0, if A queries H with
ˆe(P,P)
u
1
u
2
u
3
, and whenever A recognizes the ses-
sion key correctly, B chooses one of the ≤ q
ro
val-
ues queried to H uniformly at random and outputs
this value as potential solution to the BDH chal-
lenge. We obtain
Adv
Game 1
A
− Adv
Game 0
A
≤
Pr[Succ
Game 1
A
] − Pr[Succ
Game 0
A
]
≤ q
3
send
· q
ro
· Adv
bdh
A
,
i. e.,
Adv
Game 1
A
− Adv
Game 0
A
is bounded by a
negligible function as desired.
Game 2. Here we replace the session key sk
U
i
(as
well as sk
U
j
and sk
U
k
) with a uniformly at random
chosen bitstring in {0,1}
ℓ
. Game 2 and Game 1
only differ if the adversary queries the random or-
acle H with a bitstring of the form ∗ k k
usr
k ∗.
With no information about k
usr
∈ {0,1}
ℓ
other
than H(mk
i
k 00) and H(mk
i
k 01) being available
to A , we obtain
Adv
Game 2
A
− Adv
Game 1
A
≤
q
ro
+ 2· q
send
2
ℓ
.
By construction Adv
Game 2
A
= 0, and we recognize
the protcol in Figure 1 as secure, provided that the
BDH assumption holds.
Security if the Server is Uncorrupted. In other
words, A must not query Corrupt(S). For this sce-
nario, again game hopping allows to establish the de-
sired result:
Game 0. As in the previous setting, this game is
identical to the original attack game for the adver-
sary, with all oracles being simulated faithfully:
Adv
A
= Adv
Game 0
A
SECRYPT 2010 - International Conference on Security and Cryptography
376

Game 1. In this game we modify A in such a way
that it chooses first of all, independently and uni-
formly at random, three protocol instances Π
s
i
U
i
,
Π
s
j
U
j
, Π
s
k
U
k
of the at most ≤ q
send
instances queried
to the Send oracle. With probability at least
1/q
3
send
, the adversary A will query Test(U
i
,s
i
)
with pid
s
i
U
i
= {U
i
,U
j
,U
k
}—in all other cases just a
uniformly at random chosen bit b ∈ {0,1} is out-
put. We have Adv
Game 0
A
≤ q
3
send
· Adv
Game 1
A
.
Game 2. Now, in Round 2 of the protocol the sim-
ulator replaces the server’s message c
i
directed
to Π
s
i
U
i
with an encryption of a uniformly cho-
sen random bitstring of the appropriate length.
To bound |Adv
Game 2
A
−Adv
Game 1
A
| we derive from
the challenger the following algorithm C to attack
the ROR-CCA security of the underlying symmet-
ric encryption scheme: whenever the protocol re-
quires to encrypt or decypt a message using the
symmetric key k
U
i
, C queries its encryption or de-
cryption oracle, respectively, simulating Corrupt,
Reveal, Send and Test in the obvious way. Note
that C simulates the (by assumption uncorrupted)
server S, too. In particular, C knows k
srv
, and there
is no need for C to query its decryption oracle with
a message received from the real-or-random ora-
cle for computing the session key. Whenever A
correctly identifies the session key after receiv-
ing the challenge of the (simulated) Test oracle,
C outpus 1, i. e., claims that its encryption oracle
operates in “real mode”, whenever A guesses in-
correctly, C outputs 0.
Writing b
ror
and b
test
for the values of the real-
or-random oracle’s internal random bit and the
random bit of the (simulated) test oracle, respec-
tively, we obtain (with a slight abuse of notation)
Adv
ror−cca
C
=
Pr
h
1 ← C
b
ror
=1
i
− Pr
h
1 ← C
b
ror
=0
i
=
=
1
2
· Pr
h
1 ← A
b
test
=1
| b
ror
= 1
i
+
1
2
· Pr
h
0 ← A
b
test
=0
| b
ror
= 1
i
−
1
2
· Pr
h
0 ← A
b
test
=1
| b
ror
= 0
i
−
1
2
· Pr
h
1 ← A
b
test
=0
| b
ror
= 0
i
=
1
2
·
Pr
h
1 ← A
b
test
=1
| b
ror
= 1
i
+
1− Pr
h
1 ← A
b
test
=0
| b
ror
= 1
i
−
1− Pr
h
1 ← A
b
test
=1
| b
ror
= 0
i
−Pr
h
1 ← A
b
test
=0
| b
ror
= 0
i
=
1
2
·
Pr
h
1 ← A
b
test
=1
| b
ror
= 1
i
−Pr
h
1 ← A
b
test
=0
| b
ror
= 1
i
+
Pr
h
1 ← A
b
test
=1
| b
ror
= 0
i
−Pr
h
1 ← A
b
test
=0
| b
ror
= 0
i
≥
1
2
·
Adv
Game 0
A
− Adv
Game 1
A
.
In other words, we recognize |Adv
Game 2
A
−
Adv
Game 1
A
| as negligible as required.
Game 3. In this game, in Round 2 of the protocol
the simulator replaces the server’s message c
j
di-
rected to Π
s
j
U
j
with an encryption of a uniformly
chosen random bitstring of the appropriate length.
With the same argument as above, we recognize
Adv
Game 3
A
− Adv
Game 2
A
as negligible.
Game 4. Finally, in this game, in Round 2 of the pro-
tocol the simulator replaces the server’s message
c
k
directed to Π
s
k
U
k
with an encryption of a uni-
formly chosen random bitstring of the appropriate
length. Repeating the argument for Game 2 again,
we recognize
Adv
Game 4
A
− Adv
Game 3
A
as negligi-
ble.
Game 5. At this point we replace the session key
sk
U
i
(as well as sk
U
j
and sk
U
k
) with a uniformly
at random chosen bitstring in {0,1}
ℓ
. Game 4
and Game 3 only differ if the adversary queries
the random oracle H with a bitstring of the form
k
srv
k ∗. With no information about k
srv
∈ {0,1}
ℓ
other than H(mk
i
k 00) and H(mk
i
k 01) being
available to A , we obtain
Adv
Game 4
A
− Adv
Game 5
A
≤
q
ro
+ 2· q
send
2
ℓ
.
By construction Adv
Game 5
A
= 0, and we recognize
the protcol in Figure 1 as secure, provided that the
server S is uncorrupted.
Integrity. If three instances of honest users agree
on a common session identifier H(mk k 01), unless
the event Collision occurs they have obtained the same
“master key” mk—and therewith partner identifier.
With the session key being computed as H(mk k 10),
we see that equality of session identifiers with over-
whelming probability ensures identical session keys,
too.
Strong Entity Authentication. The session identi-
fier is derived from the “master key” mk as H(mk k
SERVER-ASSISTED LONG-TERM SECURE 3-PARTY KEY ESTABLISHMENT
377

01), and mk is derived from values u
j
P, u
k
P, received
from and signed by the intended partners; mk also in-
cludes the partner identifier. The partner instances
know the same values and derived with overwhelm-
ing probability an identical confirmation key k
conf
and
therewith an identical session identifier.
6 CONCLUSIONS
The server assisted 3-party protocol we presented can
be seen as expensive in the sense that shared keys
with a server, a signature scheme and two hardness as-
sumptions are involved. However, the security guar-
antee established is rather strong and the efficiency
as well as the hardness assumptions compare in our
opinion quite acceptably to Bohli et al.’s two-party
solution. Avoiding the introduction of new hardness
assumptions about the involved cryptographic primi-
tives can certainly be seen as a feature of the presented
protocol.
REFERENCES
Bellare, M., Desai, A., Jokipii, E., and Rogaway,
P. (2000a). A Concrete Security Treat-
ment of Symmetric Encryption. Available at
http://cseweb.ucsd.edu/∼mihir/papers/sym-enc.html.
Extended abstract in (Boneh and Franklin, 2001).
Bellare, M., Pointcheval, D., and Rogaway, P. (2000b). Au-
thenticated Key Exchange Secure against Dictionary
Attacks. In Preneel, B., editor, Advances in Cryptol-
ogy – Eurocrypt 2000, volume 1807 of Lecture Notes
in Computer Science, pages 139–155. Springer.
Bohli, J.-M., M¨uller-Quade, J., and R¨ohrich, S. (2007a).
Long-Term and Dynamical Aspects of Information Se-
curity: Emerging Trends in Information and Commu-
nication Security, chapter Long-term Secure Key Es-
tablishment, pages 87–95. Nova Science Publishers.
Bohli, J.-M., Vasco, M. I. G., and Steinwandt, R. (2007b).
Secure group key establishment revisited. Interna-
tional Journal of Information Security, 6(4):243–254.
Boneh, D. and Franklin, M. (2001). Identity-Based Encryp-
tion from the Weil Pairing. In Kilian, J., editor, Ad-
vances in Cryptology – CRYPTO 2001, volume 2139
of Lecture Notes in Computer Science, pages 213–
229. Springer-Verlag.
Boneh, D. and Franklin, M. (2003). Identity-Based
Encryption from the Weil Pairing. SIAM Jour-
nal of Computing, 32(3):586–615. Available
at http://crypto.stanford.edu/∼dabo/papers/bfibe.pdf;
extended abstract in (Boneh and Franklin, 2001).
Bresson, E., Chevassut, O., Pointcheval, D., and Quisquater,
J.-J. (2001). Provably Authenticated Group Diffie-
Hellman Key Exchange. In Proceedings of the 8th
ACM conference on Computer and Communications
Security CCS’01, pages 255–264. ACM.
SECRYPT 2010 - International Conference on Security and Cryptography
378
